
American Security Today’s Annual ‘ASTORS’ Awards, the preeminent U.S. Homeland Security Awards Program, now in its Seventh Year, continues to recognize industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management and Response, Law Enforcement, First Responders, as well as federal, state and municipal government agencies in the acknowledgment of their outstanding efforts to Keep our Nation Secure.
An exclusive sold-out event featured at ISC East, well over two hundred representatives of law enforcement, public safety, and industry leaders came together to honor the selfless service of those who stand on the front lines, and those who stand beside them – providing the capabilities and technologies to create a safer world for generations to come.
This year marks the 20th anniversary of the Department of Homeland Security (DHS), which came out in force, to discuss comprehensive collaborations between private and public sectors that have led to the development of intelligence and technologies which serve to protect our nation.

The keynote Address was provided by U.S. Customs and Border Protection (CBP) Office of Field Operations (OFO) Deputy Executive Assistant Commissioner (DEAC) Diane Sabatino, a 24-year veteran who began her federal career as an Immigration Inspector at John F. Kennedy (JFK) International Airport in 1998, and now leads the Office of Field Operations with more than 31,000 employees, overseeing a budget of more than 6.6 billion dollars.
DEAC Sabatino described the changes to CBP through the tragedy of 9/11 and the relentless commitment to its mission and ongoing investment in the latest technologies and innovations to protect our borders and Homeland.
The resounding theme of the DEAC’s remarks was her pride in the women and men of the CBP and their families who support them.

With oversight of the identity management portfolio, described by DEAC Sabatino as Identity as a Service (IDaaS), the key to frictionless travel and the reduction of fraud, she shared a personal story related to a national study on identical and fraternal twins from 1978.
As an identical twin, DEAC Sabatino and her sister participated in the study, and she shared that it may have been a harbinger of her future career!
The prestigious Annual ‘ASTORS’ Homeland Security Awards Program highlights the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition and keep our Nation safe – one facility, street, and city at a time.
The program is specifically designed to honor distinguished government and vendor solutions that deliver enhanced value, benefit, and intelligence to end-users in a variety of government, homeland security, enterprise, and public safety vertical markets.
“‘ASTORS’ nominations are evaluated on their technical innovation, interoperability, specific impact within the category, overall impact to the industry, relatability to other industry technologies, and application feasibility outside of the industry,” explained AST’s Editorial Director Tammy Waitt.
“‘ASTORS’ Awards Winners are selected by our American Security Today Expert Panel of Judges, and the ‘ASTORS’ Homeland Security Awards are presented at the Platinum, Gold, Silver, and Bronze levels.”

And without further ado, American Security Today is Proud to Introduce the 2022 ‘ASTORS’ Homeland Security Awards Winners.
Acoustic Technology Inc. (ATI Systems)
 Best Mass Notification System – Hardware
Best Mass Notification System – Hardware
-
Mobile Solutions for Giant Voice
-
When an emergency strikes, effective dissemination of information promptly can be critical, and emergency communications for disasters require rapid deployment of Giant Voice (GV) systems.

-
ATI Systems, a world-leading provider of reliable emergency warning & mass notification systems (MNS), offers outstanding Giant Voice Solutions for Military, Community, and Campus clients with the essential tools for emergency planning and preparedness, which includes their Mobile High Powered Speaker Station (HPSS) which is Rapidly Deployable on an Outdoor Siren Trailer, their Transportable High Powered Speaker Station (THPSS), and their Deployable High Powered Speaker Stations (DHPSS).
-
Through acoustic design and modeling, the company provides optimal sound coverage and superior voice intelligibility for both outdoor and indoor areas to ensure the safety of its clients worldwide.
 *ATI Systems is also a Returning Premier Sponsor for the Sixth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a 2021, 2020, 2019, 2018, and 2017 ‘ASTORS’ Platinum Award Champion.
*ATI Systems is also a Returning Premier Sponsor for the Sixth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a 2021, 2020, 2019, 2018, and 2017 ‘ASTORS’ Platinum Award Champion.
Advanced Detection Technology
 Best Under Vehicle Surveillance System
Best Under Vehicle Surveillance System
-
All New Hardwired LowCam® VI100 UVIS
-
In 2020, Advanced Detection Technology, LLC, introduced the LowCam® VI100 system, the first-ever, battery-powered Under Vehicle Inspection System (UVIS) for those in charge of safety and security at special events.

-
With its “no strings attached” feature touting no cables and no cords and military-grade equipment, security personnel has been able to take this level of improvised security with them easily and quickly, set up and use within minutes without highly trained or specialized personnel, and without the expensive price tag, wherever and whenever they need it.
-
At any point during the inspection, security personnel can choose to review, zoom in on the screen image, or swipe left or right between vehicles since the images are quickly and wirelessly transferred to a 14-inch, sunlight-readable rugged tablet. It’s as intuitive as using a smartphone.
-
Fast forward to 2022, and Advanced Detection has launched a hardwired version of the affordable, portable LowCam® VI100 UVIS with up to 250 feet of stand-off cable, complete with a 21.5-inch monitor and workstation, which allows for longer, continuous inspections without swapping batteries.
(See a brief overview of its military-grade products and intuitive interface that produce a best-in-class, ultra-high-definition inspection image, delivering a front-to-back and side-to-side field of view. Courtesy of Advanced Detection Technology and YouTube.)
-
Advanced Detection Technology, LLC, a leading manufacturer of Under Vehicle Inspection Systems (UVIS) and Under Train Inspection Systems (UTIS), has been providing global solutions for nearly 20 years, with products proven effective in helping governments, major sporting events, corporations, and military installations around the world decrease threats of terrorism, drugs, weapons smuggling, and data theft 24/7.
-
Advanced Detection is a Returning ‘ASTORS’ Awards Champion, having secured Wins for their Sixth Consecutive Year; in the 2022, 2021, 2020, 2019, 2018, and 2017 Homeland Security Awards Programs, respectively.
AMAROK (First of Two)
 Best Fencing Solution
Best Fencing Solution
-
Portable Electric Guard Dog Fence
-
AMAROK’s award-winning Electric Guard Dog™ fence now offers a portable version as the perfect solution for temporary uses.

-
Flexible and fully monitored, it includes an alarm panel and keypad to permit controlled access. It’s solar-powered, so no digging is required, and installation, service, and maintenance are included.
-
AMAROK’S full-perimeter solar-powered electric fences and integrated security solutions cost up to 90 percent less than traditional security guards and are truly an ultimate crime prevention solution.
AMAROK (Second of Two)
 Best Perimeter Protection Solution
Best Perimeter Protection Solution
-
Portable Electric Guard Dog Fence
-
AMAROK’s full-perimeter solar-powered electric fences and integrated security solutions cost up to 90 percent less than traditional security guards and are truly an ultimate crime prevention solution.
(Find out why AMAROK is the Ultimate Perimeter Security Solution, and how the Electric Guard Dog Fence stops crime before it happens. Courtesy of AMAROK and YouTube.)
-
AMAROK (formerly ‘The Electric Guard Dog’) was also Recognized as an’ ‘ASTORS’ Awards Champion in the 2021, 2020, and 2019 Homeland Security Awards Programs.
Athena Security
 Best Metal/Weapons Detection Solution
Best Metal/Weapons Detection Solution
-
Athena Weapons Detection System
-
Athena’s Concealed Weapons Detection System (WDS) is engineered to detect a wide range of mass casualty threats like handguns, shotguns, and rifles without requiring individuals to stop as they pass through the detector.
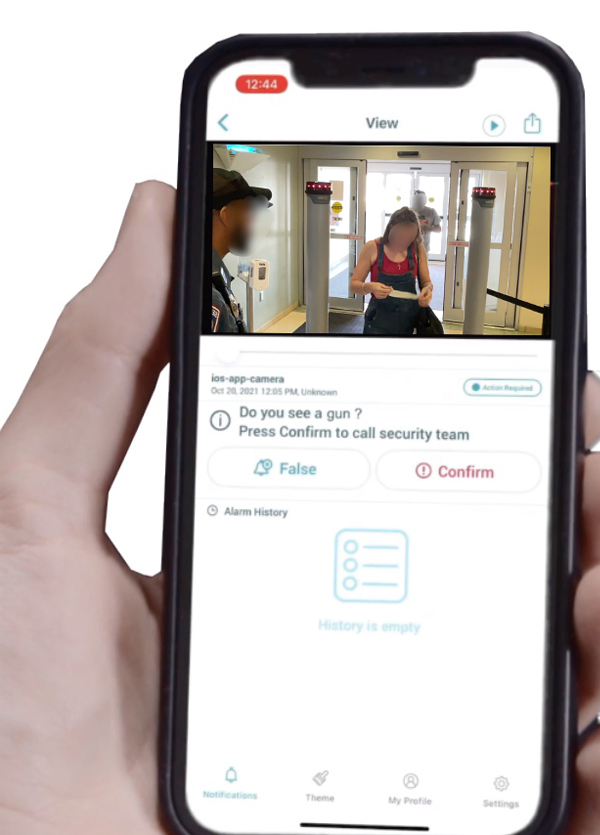
Expect Athena’s System to be a workforce multiplier by improving the operational efficiency of your security team. It is best to use this system as an initial triage, with people walking single file through the checkpoint. Then, upon an alert, a security professional can do a secondary screening.
-
Furthermore, there is no need to have individuals remove phones, wallets, or other extraneous items from their pockets due to the proprietary multiple-sensor detection method.
-
Alert notifications can be sent in real-time to a Security Operation Center, mobile phone App, computer-based browser, Video Management System (VMS), Access Control System, and can also be further integrated with other business software.
-
Most clients choose to send proactive alerts after they have been confirmed by the guards running the system to a predetermined escalation path if someone walks in with a weapon. The alert contains the location, date/time stamp, and image.
-
The system passes the Federal Standard 100% while allowing both auditory and visual alert options as seen in the best practices of Homeland Security for WDS.
(Learn how to speed up your concealed weapons detection scanning without breaking the bank. Athena Security launches its entryway security system and shows a client how long it takes currently at their location 15 secs and with our new entryway security system technology to scan for concealed weapons in only one second. Courtesy of Athena Security and YouTube.)
-
Athena Security is a New Competitor to the 2022 ‘ASTORS’ Awards Program.
AttackIQ
Best Breach & Attack Simulation
-
AttackIQ Security Optimization Platform
-
The AttackIQ Security Optimization Platform enables risk and security practitioners to continuously assess and improve critical security controls within their production environment, optimizing their end-to-end security posture and providing trend reporting for demonstrable improvement over time.
-
By surfacing better, automated insights, teams can make smarter investment decisions and deliver on both business continuity and greater program effectiveness.
(Learn how AttackIQ’s Security Optimization Platform helps security teams achieve cybersecurity readiness through automated security control validation. Courtesy of AttackIQ and YouTube.)
-
AttackIQ was also recognized as a 2021 ‘ASTORS’ Awards Champion.
Automatic Systems America
Best Pedestrian Entrance Control Solution
-
FirstLane Speed Obstacle Gate
-
Automatic Systems America continues to evolve its award-winning FirstLane obstacle swing door speed gate to offer customized solutions that meet customer requirements for even the most unique installations.

-
Thanks to its black-painted steel housing, combined with the elegance of glass, FirstLane speed gate meets stylish and architectural trends.
-
FirstLane provides a high bi-directional flow and safety without compromise.
-
Its exclusive DIRAS detection system ensures precise user tracking for maximum safety and security.
-
Even more intuitive and easy to use thanks to the new dynamic LED lighting, FirstLane combines high throughput with state-of-the-art detection.
(Automatic Systems’ FirstLane swing speed gates offer a new modern and elegant design, whilst guaranteeing high reliability. Thanks to its black painted steel housing, combined with the elegance of glass, FirstLane speed gates capture stylish and architectural trends.. Courtesy of Automatic Systems and YouTube.)
-
With the current social distancing and contactless requirements, the SlimLane EPR. while protecting its users.
*Automatic Systems is also a Returning Premier Sponsor for the Sixth Consecutive Year in the ‘ASTORS’ Awards Program, and a Platinum ‘ASTORS’ Awards Champion in all Seven Homeland Security Awards Programs. Thank you for your continued confidence in AST!
Axis Communications (First of Three)
Best Body Worn Video Solution
-
AXIS W101 Body Worn Camera
-
The AXIS W101 Body Worn Camera gives you exceedingly sharp images in every frame and clear audio with noise suppression. It’s robust, water-resistant, easy to use, and mounts securely to your clothing.

-
It starts and stops fast – with a touch, comes in white for discretion or black for when your priority is deterrence, and provides location tracking.
-
And it buffers up to 120 seconds before you switch it on, so you’ll catch the whole encounter. It has stealth mode for surreptitious recording.
-
And a battery life of up to 15 hours at 1080p, charging on-the-go with any USB-C charger, and fast offloading make it ready to go when you are and a snap to put away.
-
The AXIS W101 Body Worn Camera comes with an easy-to-use mobile app – the AXIS Body Worn Assistant – for viewing and labeling in the field, making it easier to find and retrieve evidence, and enables users to start reporting out in the field by categorizing a recording and attaching notes to it. And evidence is easy to find and retrieve.

-
The AXIS W101 Body Worn Camera also lives up to official FBI standards for cybersecurity with end-to-end encryption. Axis Edge Vault protects the Axis device ID and simplifies the authorization of Axis devices on the network.
-
Signed video allows video recordings to be traced back to the Axis camera from where it originated, so it’s possible to verify that the footage wasn’t tampered with after it left the camera.
-
And open standards and cost-efficient docking stations with a separate controller make it easy to add as many cameras as you want anytime.
(See why the AXIS W101 Body Worn Camera is an easy-to-use, lightweight, and robust body-worn camera that lets you store and manage video your way. Courtesy of Axis Communications and YouTube.)
Axis Communications (Second of Three)
 Best Image Technologies Solution
Best Image Technologies Solution
-
AXIS XPQ1785 Explosion-Protected PTZ Camera
-
The AXIS XPQ1785 is a robust, high-performance positioning camera designed for safe operation in vast, potentially combustible environments.
-
This camera delivers outstanding 24/7 long-range monitoring, offering 2 MP/HDTV 1080p image quality at up to 60 fps, and features 32x optical zoom; it provides continuous 360° pan and tilt at up to 200°/sec, meaning it can not only turn in a complete circle to prevent any blind spots around it, but it can also see straight ahead, below, and above its position so absolutely nothing is missed.

-
AXIS XPQ1785 also features Forensic WDR for clarity even when there are both dark and light areas in the scene, as well as Lightfinder for high-quality color images recorded in near darkness and clear, sharp images of moving objects. Plus, Axis Zipstream significantly lowers bandwidth and storage requirements.
-
One of the most unique features of the AXIS XPQ1785 is its built-in early smoke and fire detection analytic. With this, the camera is able to detect smoke and the early signs of a fire all while doing what it’s supposed to be doing in its chosen application. While the AXIS XPQ1785 is not intended to replace smoke detectors, it ultimately doubles as a smoke detector and a top-of-the-line surveillance camera, providing heightened value for the entire security ecosystem.
-
Powered by 110 or 230 V AC, this high-performance PTZ offers long-distance connections using fiber optics or Ethernet cabling, and, thanks to direct mains power input, it’s simple to install and there’s no need for an external power supply. Featuring a built-in long-life wiper, great images are guaranteed even in snow and rain making this camera ideal in environments exposed to dirt, grime, and adverse weather conditions.
-
AXIS XPQ1785 supports electronic image stabilization (EIS), which greatly improves video quality in situations where the camera is subject to vibration such as gusty winds or passing vehicles. Furthermore, EIS allows for the installation of the camera out of reach on high walls or columns with minimum impact on image quality. It is also certified for use anywhere in the world, with both North American Class/Div as well as ATEX and IECEx certifications.
(Ideal for health, safety, and environment (HSE) applications within potentially combustible areas, this robust PTZ camera is certified for Class I/II/III Div 1 and Zone 1,21. It has worldwide certifications for use in hazardous areas (NEC, CEC, IECEx, ATEX, and more). Courtesy of Axis Communications and YouTube.)
Axis Communications (Third of Three)
Best Investigation/ Surveillance/Detection Solution
-
AXIS D4100-E Network Strobe Siren
-
The AXIS D4100-E Network Strobe Siren is the world’s first network strobe siren, helping to deter intruders, ensure on-site safety and improve operational efficiency with the power of light and sound.

-
It comes with various light and sound patterns to ensure the right level of protection for specific environments, and based on the open Axis platform, this fully networked product can be connected to any Axis device, Axis VMS, or to third-party VMS and issue warnings and notifications with strobe lighting and/or siren alarms.
-
This strobe siren allows integrators to choose from various white and RGBA light patterns and pre-configured sounds to best manage alerts for varying applications. Additionally, this robust, IP66-, NEMA-4X- and IK10-rated device offers an optional sunshield for daytime outdoor use, ensuring that strobe alerts are visible at all times of day.
(See how you can signal and alarm with the power of light and sound. The power of light and sound with the world’s first IP strobe siren. From deterrence to operational efficiency, it fits multiple use cases and integrates flexibly. Courtesy of Axis Communications and YouTube.)
-
AXIS D4100-E not only provides a multitude of security benefits, but it is also cost-efficient to install, configure, and maintain. A strobe light and a siren in one device means integrators spend less time on installation, and the need for fewer cables and other mounting accessories cuts cabling costs even more.
-
*Axis Communications, a Canon Company, has also been recognized as an ‘ASTORS’ Awards Champion for their Sixth Consecutive Year, in the 2021, 2020, 2019, 2018, and 2017 Homeland Security Awards Programs respectively.
BackBox
Best Network Automation Solution
-
Centralized Multi-Vendor Network Automation
-
BackBox provides intelligent, accessible automation to help continuously improve the health, performance, and compliance of network security infrastructure.
-
It automates backups and disaster recovery, software updates and patch management, validation and remediation of configuration compliance with security standards such as CIS and NIST, and the continuous grooming and optimization of firewall and other device configurations.
-
Built on an open API structure, BackBox readily integrates with other tools employed by network administrators, cybersecurity infrastructure teams, and cloud or data center operations teams.
-
Out of the box, BackBox supports thousands of devices from over 180 different network manufacturers and is easily extensible for new device types. It offers REST API code examples to incorporate with third-party solutions and ticketing systems and works simultaneously with physical and virtual devices across multi-cloud and on-premises environments.
-
BackBox supports customers with industry-leading experience and a passion for fundamentally improving enterprise network operations.
-
*BackBox is a New Competitor to the 2022 ‘ASTORS’ Awards Program.
BriefCam

Best Video Analytics Solution
-
BriefCam Video Analytics Platform
-
The comprehensive BriefCam® Video Content Analytics Platform empowers people, companies, and communities to realize the value of their surveillance investment, by making video searchable, actionable, and quantifiable.

- BriefCam solutions not only enable users to review hours of video in minutes and respond immediately to critical situational changes in the environment, but also to quantitatively analyze video to derive actionable insights for data-driven safety, security, and operational decision-making, all while effectively balancing sensitivity, accuracy, and efficiency.
-
BriefCam’s innovative and extensible platform offers a robust portfolio of critical video analytics, capabilities, superior performance, and unmatched accuracy, effectively supporting both on-demand and real-time analytics requirements for full camera coverage.
-
For accelerated time to target, optimized investigative productivity, and seamless scalability for the evolving security needs of communities and companies, the BriefCam platform integrates with a variety of leading VMS providers, and offers flexible deployment options, including standalone or multi-site, all-in-one or distributed large-scale, on-premises or cloud, as well as edge and hybrid deployments.
-
The complete BriefCam Platform delivers intelligent video analytics through three solution modules: REVIEW, RESPOND, and RESEARCH, and empowers real-time decision-making and situational awareness through real-time alerts based on complex object classification and recognition filter combinations.
(There are more than 350 million video surveillance cameras worldwide recording around the clock, every day, producing overwhelming amounts of video data that is largely untouched. What if you could drive exponential value from your video content by making it searchable, actionable, and quantifiable? Courtesy of BriefCam and Vimeo.)
-
*BriefCam was also recognized as an ‘ASTORS’ Awards Champion in the 2021, 2020, 2019, and 2018 Awards Programs.
Canon U.S.A. (First of Two)

Best IT Access Control & Authentication Solution
-
uniFLOW Online
-
The solution is recognized for its usability, flexible and straightforward design, advanced scanning, robust security features, and enhanced cloud functionality.

-
uniFLOW Online helps customers control access to their systems and critical information.
-
Combining multifunctional devices with a print management solution prevents unauthorized use and keeps valuable and confidential information safe.
-
With uniFLOW Online, administrators can ensure users have identified themselves at the imageRUNNER ADVANCE DX device and leverage the secure Scan-to-Email print functionality.
-
Documents are only printed when a user is physically standing at a device and authenticates, regardless of whether they submitted the print job from their desktop PC or mobile device.
(Did you know that using cloud-based servers for your document workflows saves you money? uniFLOW Online gives you this and much more such as providing a user-friendly interface allowing you to manage and track your organization’s print activity. Courtesy of uniFLOW Online and YouTube.)
Canon U.S.A. (Second of Two)

Best Device Visibility and Control Solution
-
Canon Office Cloud
-
Aligning with its commitment to being a strong technology partner for helping users in modernizing core IT systems, Canon Office Cloud service has achieved a moderate-level FedRAMP Authority to Operate (ATO).
-
Efficiently manage print infrastructure, gain print activity insights, use security features while printing and scanning, and help reduce associated IT costs.

-
Canon Office Cloud is a cloud-based platform with Managed Print Services (MPS) capabilities designed to help Canon customers, as well as users of many third-party printer, manage their compatible print device fleet and output.
-
Powered by uniFLOW Online and Netaphor SiteAudit solutions, these cost-efficient MPS solutions can help users efficiently manage print infrastructures, gain print activity insights, use security features2 while printing and scanning, and reduce associated IT costs.
-
Additionally, uniFLOW Online’s ability to securely hold print jobs can help reduce the risk of both information disclosures of unattended prints, and the touching of another user’s printed documents.
-
*Canon U.S.A. has now been recognized as a Multiple ‘ASTORS’ Awards Champion for their Sixth Consecutive Year in the Annual Homeland Security Awards Program.
-
Additionally, Axis Communications, a Canon Company, has also been recognized in the 2021, 2020, 2019, 2018, and 2017 ‘ASTORS’ Awards Programs, respectively.
Carbyne

Best Public Safety Workforce Management
-
APEX Cloud-Native Mission-Critical Call Management
-
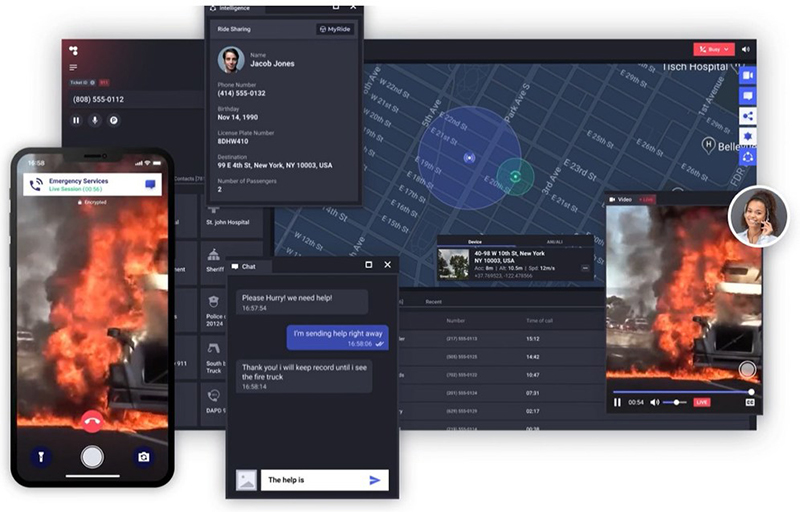
Carbyne is a leading global provider of cloud-native mission-critical contact center solutions, used by local and federal government agencies to cover over 400 million people globally, and helps 911 call takers process 150 million emergency calls each year.
-
Carbyne’s technologies enable government agencies and emergency response teams to connect with callers as well as connected devices via highly secure communication channels without needing to download a consumer app.
-
Carbyne provides a unified cloud-native solution that provides live actionable data that can lead to more efficient and transparent operations and ultimately save lives.
-
Carbyne’s cloud-native APEX solution enables governments and emergency response teams to continue to operate fully remotely even when a natural disaster occurs, allowing emergency centers to continue to operate fully under any condition, even after forced evacuation due to severe weather conditions or a spread of a pandemic.
-
Carbyne’s technology allows emergency operators, EMTs, 911 call takers, and callers to receive and share texts, live videos, and images while pinpointing the exact locations of individuals in emergencies. Now, when a citizen reports an emergency, the operator can automatically retrieve the caller’s phone number.
-
Once the number is retrieved, the call taker at the emergency center, through Carbyne’s platform, can send a text containing a video activation link to the caller. By clicking the link, the caller permits access to the mobile device camera and establishes a live video connection with the emergency call center.
(See how with Carbyne APEX, your contact center will become more agile than ever before. Legacy technology doesn’t have flexibility, so they’ve built APEX to be a responsive solution. With its quick, pain-free integration and a simple, user-friendly one-screen interface Carbyne APEX is bringing contact centers into the present and beyond. Courtesy of Carbyne and YouTube.)
-
Carbyne is redefining how 911 emergency contact centers and government service teams operate by moving everything to the cloud, making them more resilient to outages. Unlike legacy on-premises technology, Carbyne’s technology remains online and fully functional even when your center suffers natural disasters and infrastructure issues.
-
Carbyne helps emergency call centers go digital and delivers mobile technology to 911 call centers when they can’t get into the office. Working remotely was essential during the pandemic and critical during crises like mass shootings and natural disasters such as floods and wildfires.
-
It also gives first responders the information they need to make the right decisions by improving situational awareness. Description of suspects, dangerous conditions, number of injured, and obstacles are important details that can now be gleaned when calling 911.
The same goes for caller locations. In a crisis, callers often lose track of their location or do not have a specific location to provide. The saying “see something, say something” takes on new meaning with Carbyne’s technology. For example, boaters lost at sea, migrants lost on the border, passengers on mass transit, and individuals in unfamiliar surroundings can be located within seconds using Carbyne’s platform.
-
*Carbyne is a returning ‘ASTORS’ Champion, having secured Wins in the 2018 and 2017 Awards Programs.
Cellbusters

Best Cell Phone Detection Solution
-
Zone Protector
-
The Zone Protector™ from Cellbusters provides maximum protection for your environment by continuously scanning for cell phone and user-selectable RF transmissions, and is far more sophisticated than a cell phone detector.
-
Comparable to a spectrum analyzer, the Zone Protector™ has the ability to scan user-definable frequency ranges along with the ability to alert, notify, control a third party device, or simply log as soon as it detects relevant transmission activity.

-
Precise frequency filtering technology, managed and controlled by a 32-bit microprocessor, enables the Zone Protector™ to deliver accurate detection with virtually zero false positives.
-
Once cellular or appropriate RF activity is detected, the Zone Protector™ can be set to activate a choice of alerting options or to silently log all detected activity.
-
Additionally, Cellbusters Zone Protector has now been updated to detect 5G phones, proving a leading edge in the market, and protects investment in this technology for years to come.
(See a quick overview of the Zone Protector and the Zone Manger, both cell phone detection technology from Cellbusters. Courtesy of Cellbusters and YouTube.)
-
*Cellbusters has officially been recognized as an ‘ASTORS’ Awards Champion in all Seven ‘ASTORS’ Awards Programs. Thank you for your continued confidence in American Security Today!
Clearview AI (First of Three)

Best Investigation/ Surveillance/Detection Solution
-
Clearview 2.0 Facial Intelligence Platform
-
Clearview AI has revolutionized investigations with facial recognition technology that taps into publicly available open-source intelligence to search images on the Internet for highly accurate, rapid leads and insights you can’t get anywhere else . . . in just seconds.
-
New innovations to the product include the addition of an investigative workflow to help streamline investigations.
-
Agencies using Clearview AI for investigations report they are finding leads in decades-old cold cases with the touch of a button. They are finding witnesses, victims, suspects, and associates to accelerate case closures and bring justice to victims.
-
*Clearview’s exceptionally accurate algorithm achieved >99.8% accuracy across all demographics and ranked number 1 in the U.S. according to the National Institute of Standards and Technology (NIST) testing (NIST FVRT 1:1 10/2021, 1:N 11/2021).
*Clearview AI is the first “Search Engine for Faces” that searches the Internet to find matches.
(Facial recognition has made incredible strides in accuracy thanks to AI. Sometimes there are many misunderstandings about facial recognition and Clearview AI. The company’s founder, Hoan Ton-That pushes forward with a relentless focus on Changing the Face of AI for good. In this keynote, he lays out a vision for facial recognition and AI that leverages public internet data to deliver transformative change to law enforcement, public safety and consent-based applications for crime prevention. The highlight of the session is a riveting demonstration of Clearview AI featuring a live face search. These live searches typically serve up surprises for the search candidates as Clearview AI finds unexpected or near-impossible match images that have been used to solve countless crimes, such as crimes against children, financial fraud, and drug trafficking. Courtesy of Ai4 and YouTube.)
Clearview AI (Second of Three)

Best Facial/IRIS Recognition Solution
-
Clearview 2.0 Facial Intelligence Platform
-
Clearview AI provides the largest known database (>20B) of facial images sourced from public-only web sources, including news media, mugshot websites, public social media, and other open sources.
-
Clearview AI allows investigators and analysts to utilize images of poor quality from CCTVs, ATM cameras, and with inadequate lighting with its in-app image enhancement tools. This means images produced during a case investigation that would have previously been thought unusable, can now be used to generate leads.
-
The new investigative workflow built into Clearview AI streamlines investigations, while documenting every step in facial intelligence lead identification process for transparency, auditing and to demonstrate impact and investigative outcomes.
(Ukrainian officials are using new facial recognition software from the U.S.-based company, Clearview AI, to help identify invading Russian soldiers. NBC News’ Josh Lederman explains how Clearview is giving Ukraine the technology for free and how well it works. Courtesy of NBS News and YouTube. Posted on May 20, 2022.)
Clearview AI (Third of Three)

Best Artificial Intelligence & Machine Learning Solution
-
Clearview AI
-
Clearview AI has been awarded another U.S. patent – its second in 2022 – for its unique, highly accurate, and bias-free facial recognition algorithm.
-
The “Scalable Training Data Preparation Pipeline And Efficient Distributed Trainer For Deep Neural Networks In Facial Recognition” patent (U.S. Patent No. 11,443,553) issued by the U.S. Patent and Trademark Office (USPTO), was awarded to Clearview AI for its ability to create highly accurate, bias-free facial recognition algorithms from publicly available information.
-
Most facial recognition technologies use standard celebrity datasets for training, which do not contain a representative sample of all demographics. By contrast, Clearview AI can create a data set that represents all demographics with its unique data preparation and distributed training algorithms.
-
Clearview AI is a new competitor in the 2022 ‘ASTORS’ Awards Program.
Clopay Corporation

Best Fire & Safety System
-
SmokeShield™ Fabric Smoke & Fire
-
Clopay Corporation (formerly CornellCookson and Cookson Doors), a leading rolling door and grille manufacturer has launched SmokeShield™ Fabric Smoke and Fire, one of the most versatile fire protection and smoke mitigation products on the market, designed to save lives and prevent property damage.

-
SmokeShield™ offers an innovative way to compart-mentalize open areas, to create a smoke and fire barrier with fire safety closures that enhance life safety by enclosing atrium areas, corridors, or other openings in fire barrier and smoke barrier walls.
-
Using SmokeShield™, fire and smoke are immediately compartmentalized to enable specifiers and building owners to limit deadly smoke migration, adding precious time to occupancy evacuation plans and minimizing property and inventory losses.
-
With one of the smallest footprints on the market, its lightweight fabric construction promotes practicality for restricted floor plans while being aesthetically pleasing. Exposed components are finished to match, complement, or contrast their surroundings with a custom powder coat finish, and the guides can be easily recessed into jambs and concealed by wood, masonry, sheetrock, or other fascia materials to make fasteners and shadow lines invisible.
(Also available, SmokeShield® Elevator is an award-winning, innovative solution designed to prevent smoke and hot gases from entering elevator shafts. This hoistway closure is the result of almost 100 years of experience developing products that are specifically designed for fire protection and safety. The SmokeShield® Elevator is perfect for virtually any elevator opening, and you can customize it to complement your building. Courtesy of Cookson Doors and YouTube.)
-
Clopay Corporation (formerly CornellCookson), was also recognized as an ‘ASTORS’ Awards Champion in the 2021 and 2019 Homeland Security Awards Programs.
Cloudastructure (First of Seven, Plus 2022 New Product of the Year)

Best Cloud IoT Cyber Solution
-
GearBox IoT Cybersecurity Solution
-
Among its many IoT cybersecurity talents, GearBox™ can instantly detect non-compliant National Defense Authorization Act (NDAA) hardware.

- All Cloudastructure AI surveillance and/or remote guarding installations now include a GearBox™ pre-scan of all existing network hardware and devices to minimize risk.
-
The “plug-and-play” tool inventories all IoT devices, performs risk analysis and offers a roadmap and remedy prioritization.
-
Cloudastructure’s GearBox was also recognized with a 2022 ‘ASTORS’ Best New IoT Product of the Year Award.
Cloudastructure (Second of Seven)

Best IP Video Surveillance Solution
-
Cloudastructure Smart Surveillance
-
Cloudastructure is a cloud-based surveillance platform integrated with powerful analytics, that uses machine learning (ML) computer vision to recognize objects, faces and more, to allow users to rapidly search video footage much like one does on the web through the company’s sophisticated object tagging capabilities.
-
The Cloudastructure cloud-based platform also offers an alternative to on-premises solutions, which can be costly to operate and scale and require on-site monitoring.
-
Cloudastructure, clients can securely store their recorded, and live video feeds in the cloud through a browser, so they can safely index, access, monitor, and review their surveillance footage in the cloud, 24/7 from any internet-enabled device.
(Learn how adding cloud-based AI to your surveillance system enables you to protect the people and places that matter most. Increase occupancy, property performance, cost-savings, and peace of mind across your real estate portfolio. Courtesy of Cloudastructure and YouTube.)
Cloudastructure (Third of Seven)

Best Video Management Solution
-
Cloudastructure Smart Surveillance
-
Ideal for multi-site businesses or properties, Cloudastructure offers a unified view of all locations on a cloud-native architecture.
-
The platform ensures clients have live and forensic visibility to all of their locations, accessible anywhere in the world from their mobile phones.
-
The company’s computer vision AI/ML analytics is cloud-based for accuracy, and can be searched by person, license plate, object, etc., and video is stored in the cloud for instant access and retained for 30 days or more as needed.
Cloudastructure (Fourth of Seven)

Best Cloud Computing/Storage Solution
-
Cloudastructure Smart Surveillance
-
Cloudastructures’ award-winning Artificial Intelligence architecture features are some of the most advanced in the industry. Unlike competitors, their analytics are conducted on GPU’s for highest possible accuracy, every object in every frame is indexed and tagged, and all features are proprietary and developed in-house. No third-party vendors.
(At Cloudastructure, they believe that security should be proactive: deterring crime, not just solving whodunnits, and that security should be affordable for every property and business. Utilizing scalable cloud-based solutions and featuring state-of-the-art AI/ML analytics, Cloudastructure offers premiere end-to-end security that combines 21st-century surveillance, cybersecurity, smart parking, and remote guarding on one platform. We pair it with an affordable value proposition by taking proprietary servers out of the equation and offering contract-free, month-to-month pricing and unlimited 24/7 support. Courtesy of Cloudastructure and YouTube.)
Cloudastructure (Fifth of Seven)

Best Video Analytics Solution (**Tie)
-
Cloudastructure Smart Surveillance
-
Cloudastructure AI Analytic Feature advanced vehicle and people detection: counting, classification, license plate recognition, wrong way detection; Tagger capabilities, meaning the system tags every object for fast, easy search (i.e. persons, vehicles, backpacks, etc.)
-
Cloudastructure Smart Video Surveillance provides rule-based alerts – based on time of day, person ID, or license plate ID, and can search by Face/Person (facial recognition) or by color (blue shirt), for a seamless operation requiring no plug-ins, logins, or passwords to alternate platforms/vendors.
Cloudastructure (Sixth of Seven)

Best Video Data Storage Solution
-
Cloudastructure Smart Surveillance
-
Economical and easy-to-install, Cloudastructure’s cloud video surveillance solution works with all camera types* and protects tenants and property from thieves, vandals, or trespassers in restricted areas.
-
Clients receive customized alerts to violations in real-time. Rapid search and utilize AI analytics to identify perpetrators from their phones or laptops.
-
Clients can download footage to law enforcement with just a click.
-
*Excludes proprietary consumer-based WiFi cameras or discontinued cameras.
(Cloud-based video surveillance keeps the enterprise safe and secure. Securely store, index, and access footage in the cloud, so users always know what is happening, 24/7 from any internet-enabled device. Courtesy of Cloudastructure and YouTube.)
Cloudastructure (Seventh of Seven)
 Best Cyber Critical Infrastructure Solution
Best Cyber Critical Infrastructure Solution
-
GearBox IoT Cybersecurity Solution
-
GearBox, acquired in 2022 by Cloudastructure, is a cybersecurity solution aimed at the Industrial IoT and Operational Technology arena.
-
GearBox is comprised of an on-premise appliance that manages, synchronizes, orchestrates, and secures IoT defined networks, as well as a cloud-based portal which enables “In Application” data management and reporting.
(See a brief overview of just how simple and easy it is to connect and use GearBox. Courtesy of Chad Zerangue and Vimeo.)
-
*Cloudastructure was also recognized in the 2021 ‘ASTORS’ Homeland Security Awards Program.
Crisis24 (First of Two)

Best Risk, Crisis Management Solution (**Tie)
-
Crisis24 Crisis Management Platform
-
Crisis24, a GardaWorld company, is an integrated provider of risk and resiliency solutions in the industry, with a team that maintains an elite global client roster, providing integrated solutions for the world’s most influential people, disruptive brands, and prominent organizations—including over 50% of Fortune 500 companies, 35% of France 40 (CAC 40) companies, 5 of the top 20 wealthiest families in the U.S., and other high-profile individuals, organizations, and enterprises.
-
One key example of how the team has made a significant impact on the industry this past year is through its uniquely integrated approach to crisis risk management. By combining all essential services under one roof, Crisis24 provides seamless and comprehensive crisis management solutions.

-
From pre-incident preparation and planning to ongoing risk monitoring, training, risk mitigation technology, on-the-ground responses in times of emergencies, and executive protection services worldwide, they supply premium products and services to clients to protect their people, organization, assets, and cyber elements.
-
Some notable statistics include 27 million people protected, 11,000+ journey trips managed, 500+ million days of protection at corporations and residences, 48,000+ assets monitored, 11 million intelligence alerts issued, and 15,000+ incident reports delivered annually.
-
A few recent examples include a global social networking service needing detailed, trustworthy, and up-to-date threat intelligence for the areas in which its users live; one of the world’s leading scientific and pharmaceutical suppliers facing challenges assessing its vulnerabilities; and Europe’s largest private employer needing a duty of care plan for their global operations.
-
Crisis24’s Global Protective Solutions team is an industry leader in its quality of knowledge and services, with over 400 protective operations conducted per month and a 24/7 Protective Operations Center exclusively dedicated to supporting client protection operations worldwide.
(Securing what matters to you in an ever-evolving world. This is Global Protective Solutions. Courtesy of Crisis24 and YouTube.)
-
Recently, Crisis24 was awarded a contract to support the development, recruitment, and management of a leading cryptocurrency exchange’s global protective solutions program based on the team’s reputation and ability to shift gears as global travel priorities change.
-
While each program is strategically tailored to a client’s needs, this particular program included 24/7 secure vehicle and driver services locally and globally, around-the-clock program management from the team’s Global Operation Center, and an on-demand security detail to back the organization’s embedded team as needed.
Crisis24 (Second of Two)

Best Risk, Crisis Management Solution (**Tie)
-
Actionable Risk Management Methodology
-
Security risk management is multi-faceted, which is why Crisis24’s tailored approach draws on more than 50 areas of expertise to effectively mitigate and respond to risks, whether those risks are related to people, organizations, assets, or cyberspace.
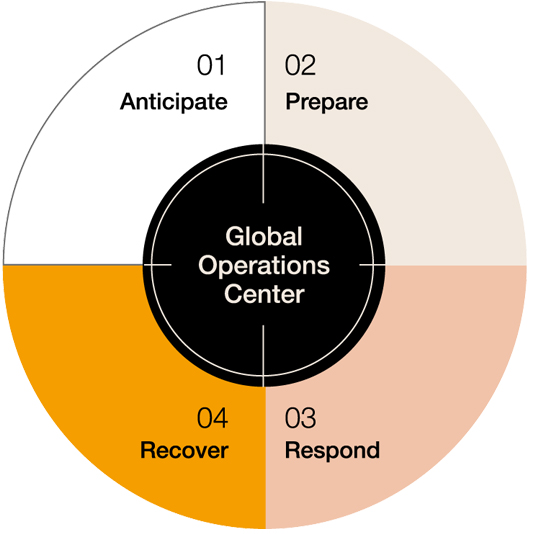
-
Crisis24 is powered by a uniquely integrated methodology and responsive approach that helps clients predict, oversee, comprehend, plan, operationalize and respond to every challenge in a timely and precise manner, anywhere in the world.
-
Backed by its Global Operations Centers, the Crisis24 Risk Management Platform uses state-of-the-art technology so you can stay connected with the latest and most comprehensive intelligence.
(Crisis24’s solutions and expertise help you deliver duty of care and prepare for all facets of risk. Courtesy of Crisis24 and YouTube.)
-
*Crisis24 is a new competitor in the 2022 ‘ASTORS’ Homeland Security Award.
CyberArk

Best Identification Management Solution
-
CyberArk Identity Security Platform
-
The CyberArk Identity Security Platform is an end-to-end identity access management solution that enforces privilege, enables access, and secures DevOps.
-
The CyberArk Identity Security platform is centered on privileged access management and offers the most complete and flexible set of least privilege-based identity and access capabilities, and is used to protect agencies across all three branches of the U.S. federal government – including multiple Department of Defense deployments

-
The CyberArk Identity Security platform is centered on privileged access management and offers the most complete and flexible set of least privilege-based identity and access capabilities, and is used to protect agencies across all three branches of the U.S. federal government – including multiple DoD deployments.
-
CyberArk delivers a comprehensive privileged access management solution designed to eliminate advanced cyber threats by identifying existing privileged accounts across networks, then proactively managing, monitoring, and protecting those accounts to reduce risk and improve security and compliance.
-
CyberArk continuously scans and monitors environments to discover and manage privileged credentials, isolates those credentials, so they are never exposed to an end-user, isolates privileged sessions to safeguard critical systems, and automatically records and stores those sessions to enhance audit capabilities.
(In today’s hybrid and multi-cloud world, where every identity represents a potential attack path to an organization’s most valuable assets, traditional network barriers are not enough to secure the perimeter. That’s the importance of a robust Identity Security strategy. See how your organization can embrace a Zero Trust approach to protecting an ever-expanding number and diversity of identities. Courtesy of CyberArk and YouTube.)
- *CyberArk was also recognized as a 2021, 2020, 2019, and 2018 ‘ASTORS’ Awards Champion in the Annual Homeland Security Awards Programs, respectively.
Cybersixgill
Best Threat Intelligence Solution
-
Cybersixgill Platform
-
The deep and dark web is designed for obscurity, hiding a vast criminal network with illicit transactions equivalent to the world’s third-largest economy. Here is where attacks get planned; here is where the tools to conduct them are bought and sold. But threat intelligence doesn’t penetrate this shadowy network.
-
Without information or insight into these hidden schemes, security teams make decisions using irrelevant, incomplete, or even obsolete information.

-
Those who do probe the deep and dark web may do so manually, and so may miss important chatter pointing to threats against their enterprise. As every aspect of business operations goes digital, the attack surface expands, making it increasingly difficult to stay current.
-
In the face of these challenges, using automated threat intelligence tools and processes that scour the web becomes ever more critical, and Cybersixgill uniquely enables customers to leverage its cyber threat intelligence (CTI) in three critical ways:
-
Exposing threats by covertly infiltrating and scraping data from limited-access underground sources in any format, language, or platform, enriching each item with critical context to derive valuable threat intelligence that is timely, accurate, and relevant.
-
Preempting attacks, as its collection mechanisms are fully autonomous, capturing emerging threats, TTPs, and IOCs in real-time as they first surface, ensuring that users receive the earliest possible intel of potential threats before they can materialize into an attack.
-
Streamlining defense and remediation activities, by tailoring its threat intelligence to meet each customer’s needs, correlating their assets with its data to trigger automated alerts and actionable playbooks, workflows, prioritization, and remediation processes within an organization’s existing security stack.
(See how Cybersixgill continuously exposes the earliest indications of risk before OSINT distributes them; before incident responders report them; and before a threat actor executes their mission. Courtesy of Cybersixgill and YouTube.)
-
As soon as Cybersixgill customers begin using its solutions, they eliminate the dark-web “bottleneck” that slows their threat responses and can diminish their security. Their teams can perform analyses in hours instead of weeks, and their insights are much more comprehensive and effective thanks to the increased data from more sources that we provide in near-real time.
-
Cybersixgill customers also save money on personnel – or avoid gaps in staffing amid the perennial cybersecurity talent shortage. This is because its automated solutions do so much of the work for them. Our customers report saving hundreds of thousands of dollars in personnel alone.
- *Cybersixgill is a new competitor to the 2022 ‘ASTORS’ Awards Program.
Cyemptive Technologies (First of Ten)
Best Cloud Computing/Storage Solution
-
Cyemptive Cloud Fortress
-
Cyemptive Cloud Fortress allows existing public cloud networking, compute, or storage to be securely accessed and/or securely hosted by Cyemptive in one of its Security Operation Centers (SOC) or one of their partners SOC.

-
This solution will secure all communications and Data in Flight between the organization’s sites and remote workforce to the Cyemptive Cloud as a proxy service to public cloud resources.
-
The Cyemptive SOC hosting CCF uses its trusted Zero-Trust, Defense-in-Depth (D-i-D) blueprints to establish secure layers of protection for all Data at Rest, Data in Use, and Data in Flight to and from organizational users and hosted platforms.
-
Using patented technologies and blueprints, Cyemptive is able to pre-emptively stop and eradicate outside attacks from infiltrating organizational systems.
Cyemptive Technologies (Second of Ten)
Best Cyber Perimeter Solution
-
Cyemptive Perimeter Fortress & Cyemptive Zero Trust Access
-
The experience of having your firewall compromised and fooled in real-time is a common problem that often goes unnoticed.
-
If you are not seeing thousands of attacks per day defended in your current firewall, then there is a high chance you are not seeing or detecting the ones getting through.

-
Cyemptive’s Perimeter Fortress (CPF) defense technology successfully stops many of today’s most advanced global hackers in seconds.
-
CPF handles root-level attacks and base firmware attacks with ease using their patented cyberslice technology, and found over 300 zero days in 2019 alone.
-
The company’s integrated protection platform prevents the most elite hackers from compromising your perimeter defenses.
Cyemptive Technologies (Third of Ten)
Best Intrusion Detection & Prevention Solution
-
Cyemptive Perimeter Fortress
-
Cyemptive Perimeter Fortress (CPF) is an external and internal perimeter defense solution which stops today’s most advanced threats and provides security at the network.

-
CPF prevents network, root-level, and firmware attacks while protecting the external and internal perimeters, creating an effective Defense-in-Depth framework before the attack takes place.
-
While other competitive solutions in the IDS/IPS space seek to “chase” the attack after it has entered the network, CPF’s external and internal perimeter solution can eliminate, identify, and log both known and unknown Zero-Day attacks for tracking and tracing on a pre-emptive basis.
-
Competitive intrusion detection platforms were built to defend against today’s computing attacks and lack the technology to defend against supercomputers and quantum computers. This is where Cyemptive’s Zero Trust platform excels against all solutions including its seconds-based pre-emptive technology that does not rely on signatures and eliminates threats before the can infiltrate networks.
Cyemptive Technologies (Fourth of Ten)
Best Preventative Cyber Solution
-
Cyemptive Suite of Solutions
-
Cyemptive’s cybersecurity solutions are guaranteed to protect your computing environments before or immediately following a compromise.
-
Cyemptive’s solutions capabilities can eliminate or reduce organizational risk, cost and reputation exposure while providing financial performance guarantees.

-
Cyemptive’s automated solutions pre-emptively stop threats where human-dependent and AI solutions do not, and are developed on and End-to-End Zero Trust framework to take pre-emptive action and eliminate threats even if root or admin access is given out.
-
Cyemptive provides the only solution suite that can eliminate, identify, and log both known and unknown Zero-Day attacks for tracking and tracing.
-
Combined together, Cyemptive’s Patented and Patent-pending CyberSlice, CyberScan and CyberSLA Technologies, provide a path to next generation superior cyber-hygiene.
Cyemptive Technologies (Fifth of Ten)
Best Zero Day Cyber Platform
-
Cyemptive Perimeter Fortress
-
Unlike the competition, Cyemptive’s patented technologies protect against both known and unknown “Zero-Day” attacks. Cyemptive’s automated solutions pre-emptively stop both known and unknown threats before or immediately after compromise, whereas human-dependent and AI solutions react and analyze only known threats after compromise has occurred.
-
Cyemptive protects against threats such as Advanced Persistent Threats, Automated Threats, and Zero-Day attacks, including Supercomputer, Quantum Computing, and Artificial Intelligence Attacks.

-
Superior cyber-hygiene includes all of the current industry best practices, while also establishing the next level of best practice by pre-emptively protecting against supercomputer, quantum, automated, persistent threats AND capturing and stopping Zero-Day, known and unknown attacks.
-
Cyemptive provides the only solution that pre-emptively contains and eliminates attempted compromises within seconds. No other cybersecurity company guarantees threat elimination within seconds to minutes from known and unknown Zero-Day attacks.
Cyemptive Technologies (Sixth of Ten)
Best Anti-Malware Solution
-
Cyemptive Enterprise Scanner
-
Cyemptive Enterprise Scanner (CES) uses Cyemptive’s CyberScan© technology to examine and fingerprint the data in files, identifying and eliminating both known and unknown threats at the file content level before they become a problem.

-
CES’s unique ability to correlate files containing malicious code with other “trigger” files, at massive scale, prevents sophisticated malware activation that others do not detect.
-
Traditional solutions fall short in effectiveness because they rely on static signatures, API monitoring, checksums, and white lists based on industry-reported known attacks only.
-
CES consistently outperforms competitors’ detection results by detecting, isolating and reporting on both industry-reported known PLUS Zero-Day malware variants of all types without false-positives reported by other cybersecurity solutions.
-
Exabyte scaling ensures the enterprise scanner for any size dataset and built-in self-healing enables maximum protection against malware at all layers of the attack surface.
Cyemptive Technologies (Seventh of Ten)
Best Cyber Critical Infrastructure Solution
-
Cyemptive Suite of Solutions
-
Cyemptive’s cybersecurity solutions are guaranteed to protect your computing environments in seconds to minutes for both known and unknown Zero-Day attacks, backed by Acceptive’s unique Service Level Agreements (SLA’s).
-
Cyemptive’s solutions capabilities can eliminate or reduce organizational risk, cost and reputation exposure while providing financial performance guarantees.

-
All Cyemptive solutions are developed on and End-to-End Zero Trust framework while others use a vulnerable authentication Zero Trust model only, to take pre-emptive action and eliminate threats even if root or admin access is exposed.
-
Cyemptive’s automated solutions pre-emptively stop threats where human-dependent and AI solutions do not. When Cyemptive’s solutions are implemented with our Defense-in-Depth blueprint, the pre-emptively protect entire computing environments for all three states of data: Data at Rest, Data in Use, and Data in Flight.
-
Combined together, Cyemptive’s Patented and Patent-pending CyberSlice, CyberScan, and CyberSLA Technologies provide a path to next generation superior cyber-hygiene.
Cyemptive Technologies (Eighth of Ten)
Best Network Security Solution
-
Cyemptive Perimeter Fortress
-
Public clouds offer connectivity and ease of use for Networking (Data in Flight), Compute (Data in Use), and Storage (Data at Rest), however, since these services provide all types of data usage, they have inherent problems keeping data secure.

-
Where is your data? Who has access to it? How can resources be secured? All public cloud access today is secured with Access Controls which do NOT completely secure data and satisfy the questions above.
-
The Cyemptive Cloud Fortress (CCF) is a unique solution approach that can provide security at ALL levels of data use, with its complete Cloud Fortress solutions secure and protect public cloud resources starting with simple transparent services that soon can be transitioned into the highest levels of security for sensitive data and to protect intellectual property.
Cyemptive Technologies (Ninth of Ten)
Best Security Incident & Event Management Solution
-
Cyemptive SIEM (CSM)
-
The Cyemptive Security Information and Event Manger (CSM) solution is an active threat response system designed for security operations data collection, real-time action response, analysis, and alerting.

-
Today’s SIEMs are designed and built for static infrastructure with human response solutions. Cyemptive changes the SIEM with threat extermination in seconds and SIEM technology to understand and real-time report on not only threats that were exterminated but threat tracing data with full correlation and isolation data timings within seconds to minutes from when the attack occurred.
-
The CSM solution is built on its CyberSlice© technology and implemented onsite or in our Security Operation Centers (SOC) including multiple layers of Defense in Depth (D-i-D) to ensure data is collected, stored, and processed securely with immutability.
-
Cyemptive uses patented technology and service offerings with End-to-End Zero Trust architecture to collect, secure, consolidate, analyze, and alert on unique sensor, telemetry, and log data from all Cyemptive solutions deployed in an organization’s environment.
-
Since threats have been isolated and eliminated in seconds, we are able to provide precision-based, real-time SIEM analytics for rapid tracking, alerting, and reporting.
-
Other solutions employ Cross”X” / eXtended Detection and Response (XDR) in an attempt to detect threats AFTER they are in the environment and Managed Detection and Response (MDR) to manage all the data collection AFTER the threats can infiltrate an environment along with managing false-positives due to static signatures, while Cyemptive can provide the data in real-time.
(Learn about Cyemptive Technologies and what makes them different. Cyemptive can make cybersecurity simple. Courtesy of Cyemptive Technologies and YouTube.)
Cyemptive Technologies (Tenth of Ten)
 Best Cyber Security Solution
Best Cyber Security Solution
-
Cyemptive Zero Trust Access (CZTA) enables an unprecedented additional protection layer and provides a revolutionary approach for VPNs (Virtual Private Networks).

-
Cyemptive was the first to detect VPN networks being compromised and quickly informed the DHS of the issues, and have discovered more than 10 security holes in existing VPN technologies that are not getting detected by current leading technology perimeter defense firewalls.
-
CZTA is an optional add-on module to Cyemptive Perimeter Fortress technology solution leading a revolutionary defense for VPNs and your remote workforce.
-
This Cyemptive protection tool is prepared for and can prevent quantum computing-based attacks from penetrating VPNs.
-
Cyemptive was also recognized in the the 2021 ‘ASTORS’ Homeland Security Awards Program.
Cymulate
 Best Breach & Attack Simulation (BAS) Platform
Best Breach & Attack Simulation (BAS) Platform
-
Cymulate Extended Security Posture Management Platform
-
Cymulate’s Breach and Attack Simulation solution, is part of its industry-setting Extended Security Posture Management (XPSM) platform and leverages the MITRE ATT&CK® framework end-to-end.
-
It enables companies to challenge, assess and optimize their cyber-security posture against the evolving threat landscape, simply and continuously, and helps security professionals control their environment and provides out-of-the-box, expert and threat intelligence-led RISK assessments, simple to use for all skill levels, updated 24/7.
-
It provides an open framework for ethical hackers to create and automate red and purple team exercises and security assurance programs tailored to their environment and security policies.
-
Cymulate’s Breach and Attack Simulation solution is the first vendor to be deployed with three additional fundamental security pillars: Attack Surface Management, Continuous Automated Red Teaming (CART) and Advanced Purple Teaming in one solution.
(Cymulate’s powerful continuous and automatic Extended Security Posture management solutions give cybersecurity professionals the confidence they need to make data-driven and intelligence-led decisions. With easy-to-understand dashboards constantly assessing their attack surface, endpoint security, web gateways, email gateway, and more, security professionals can explain and rationalize their security posture with up-the-minute information. Courtesy of Cymulate and YouTube.)
-
This year Cymulate launched a co-managed solution, Amplify, which is an extension of its BAS solution. Amplify is a human powered offering designed to accelerate the implementation and optimization of their continuous security assurance. By providing an on-hand advisor, Amplify augments in-house security teams to better leverage Cymulate’s platform and manage the optimization of a network’s cyber-security posture, end-to-end across the entire MITRE ATT&CK® framework.
-
Cymulate eliminates blind spots by assessing the current security posture of an organization and establishes a security baseline for visibility and control, and for Cymulate’s customers with stretched security teams, Amplify helps them close security gaps quickly and efficiently, rationalizing technology, helping upskill staff and improving processes.
-
Cymulate also recently added to its holistic security controls validation and posture assessment platform, dynamic dashboards which provide context by consolidating insights from across thousands of attack campaigns and scenarios, to empower security managers to make educated decisions in their cybersecurity strategy, prioritize workloads and reduce the risk substantially and quickly.
-
Cymulate, deployed by hundreds of customers including Fortune 500 companies, achieved 100% in revenue growth globally, and about 200% growth in North America in 2021 new bookings.
(See how you can operationalize threat intelligence and the MITRE ATT&CK framework for continuous purple teaming, to continuously challenge, assess, and optimize your security controls across the full cyber kill chain. Automated, comprehensive & prescriptive. Courtesy of Cymulate and YouTube.)
CYREBRO
 Best IT Security Operations Center (SOC)
Best IT Security Operations Center (SOC)
-
CYREBRO Interactive SOC Platform
-
CYREBRO is an online centralized interactive SOC platform that integrates all of a company’s security events with strategic monitoring, threat intelligence, and IR, offering full control and visibility across the entire attack surface.
-
It integrates all of its client’s security networks into one central command with full clarity, providing real-time recommendations to help them prioritize recommended actions and keep the organization secure.
-
CYREBRO is pioneering a new paradigm of the traditional Security Operations Center (SOC) to offer high-level protection to companies of all sizes. It is recreating the SOC as a platform that allows companies to effectively monitor and assess threats, and prioritize them according to their level of urgency.
(Find out how CYREBRO, transforms cybersecurity chaos into meaningful clarity. Instantly. Always. Allowing you to get the peace of mind and resilience you deserve. Courtesy of CYREBRO and YouTube.)
-
CYREBRO secures companies by providing 24/7/365 strategic monitoring, proactive threat intelligence, forensic investigation, incident response, and optimization.
-
CYREBRO is tech-agnostic and has the capability to integrate systems across any security technology to provide full security network coverage.
- *CYREBRO is a new competitor to the 2022 ‘ASTORS’ Awards Program.
Cytta Corp.
Best Wireless Video Surveillance Network Solution
-
IGAN 2.0
-
Cytta Corp. is a company that specializes in high-bandwidth, mission-critical video streaming and integrated communications capabilities for first responders.
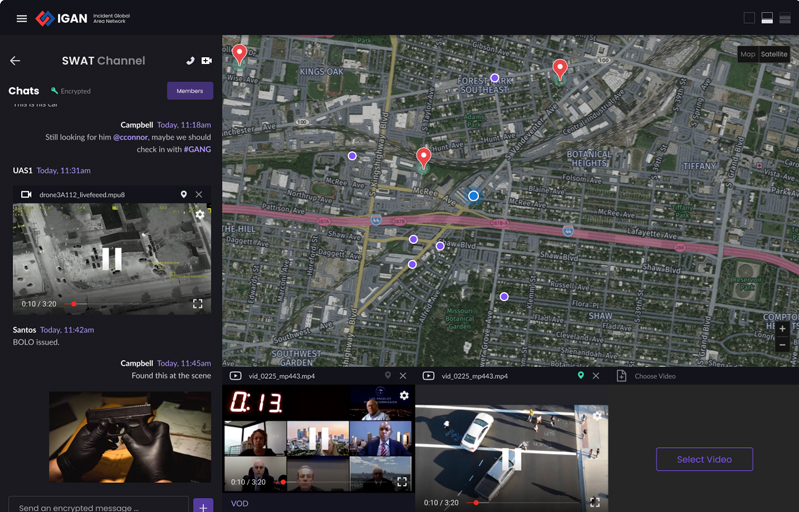
-
Cytta recently launched the next-generation of their Incident Global Area Network (IGAN) Command System – which is now a fully integrated multimedia connectivity platform including an ‘advanced interactive mapping’ feature.
-
When equipped with IGAN 2.0, first responders can receive real-time, high-definition audio and video, during any incident, as well as other relevant actionable intelligence on an ongoing basis.
-
In practice, this means when law enforcement tracks a suspect, they can construct a map of every location visited and incorporate any related media collected from surveillance cameras, drones, and other apparatus.
-
Version 2.0 of IGAN follows over a year of live beta testing, development, and interaction through multiple police incident deployments.
-
IGAN 2.0 is currently being utilized by the Dallas Police Department, the Chino Police Department, and the North Texas Public Safety Unmanned Response Team (NTXPSURT).
(Meet IGAN 2.0, a highly secure, (FIPS 140-2 and CJIS Compliant) SaaS-based advanced INCIDENT COMMAND SYSTEM (ICS) offering real-time, integrated communications integrating multiple video and voice devices, including video cameras, smartphones, tablets, computers, and 2-way radios. IGAN resides in Cytta’s secure cloud or can be privately hosted on a customer’s server. Courtesy of Cytta Corp and YouTube.)
-
*Cytta Corp. is also a new competitor in the 2022 ‘ASTORS’ Homeland Security Awards Program.
D-Fend Solutions (First of Two)
 Best Counter-UAS Solution
Best Counter-UAS Solution
-
EnforceAir
-
Unidentified drones entering unauthorized airspace and more specifically crossing borders and state lines have become a frequent occurrence that can pose a serious security threat.

-
Military agencies, public safety organizations, government agencies, border security, and critical infrastructure environments rely on aerial monitoring technology to help reduce the threat of rogue drones and to amplify situational awareness at these borders. Sophisticated aerial monitoring is also crucial in sensitive environments like airports and for VIP protection.
-
EnforceAir, D-Fend Solutions’ advanced, anti-drone, radio frequency (RF)-based cyber solution, passively and continuously scans and monitors unique communication signals used by commercial drones, without producing false positives.
-
Once detected, EnforceAir can understand drone information and protocols, for a classification process, and tag specific drones as authorized or unauthorized.
(See how D-Fend’s Solutions RF cyber C-UAS empowers security agencies to protect sensitive sites with quick detection and control capabilities, as permitted by regulations and performed by authorized personnel, for safety and continuity. Courtesy of D-Fend Solutions and YouTube.)
-
The EnforceAir system can obtain relevant information, determine the type of drone, and accurately determine the drone position, including the take-off position and often also the pilot position, in real-time, which can help security officials deal with the drone pilots.
-
This cyber aerial monitoring solution delivers accurate location, is not affected by weather, and may operate without a clear line-of-sight. Additionally, there is no need for human intervention to identify threats.
-
EnforceAir continues to showcase the most viable aerial monitoring solution for these high-risk situations. D-Fend Solutions’ EnforceAir had public case studies from the past year including detecting and mitigating a rogue drone during an open-air mass in Slovakia, as well as safeguarding world leaders at the G7 Summit in Cornwall, England.
(Slovak news report of how D-Fend Solutions’ EnforceAir anti-drone system successfully identified and fended off a rogue drone at Pope Francis’ mass with 60,000 worshippers. Courtesy of D-Fend Solutions and YouTube.)
D-Fend Solutions (Second of Two)
 Best Persistent Aerial Monitoring Solution
Best Persistent Aerial Monitoring Solution
-
National and homeland security personnel face a wide variety of scenarios and drone threats. In response to these threats EnforceAir anti-drone technologies, feature counter-drone, cyber, and radio frequency (RF)-based takeover technology to provide users with operational agility and flexibility.
-
EnforceAir, in either autonomous or manual mode, detects, locates, and identifies rogue drones in your airspace and then neutralizes the threat by allowing you to take full control of the drone and land it safely in a predefined zone.
-
Since the system does not rely upon jammers or kinetic technology, EnforceAir avoids collateral damage, interference, disruption, and disturbance, and continuity prevails as communications, commerce, transportation, and everyday life smoothly proceed.
-
EnforceAir is lightweight, and its core elements can be easily transferred, mounted, and configured within minutes, enabling personnel to go anywhere at any time, including vehicle, stationary and tactical installations.
(D-Fend Solutions focuses on the real threats from potentially dangerous drones so that varied organizations worldwide can maintain full control of drone incidents in complex environments and be prepared for future threats. The EnforceAir anti-drone system, automatically executes radio frequency, and cyber takeovers of rogue drones for safe landings and safe outcomes. Courtesy of D-Fend Solutions and YouTube.)
-
D-Fend was also recognized as an ‘ASTORS’ Award Champion in the 2021 Homeland Security Awards Program.
Darktrace (First of Two)
 Best Cyber Critical Infrastructure Solution
Best Cyber Critical Infrastructure Solution
-
Darktrace DETECT/OT
-
The increase in cyber-attacks from both cyber-criminals and nation-state actors jeopardizes the critical infrastructure and utilities on which society relies, presenting real-world threats to economic and national security. As seen from the attack on Colonial Pipeline, attacks now run at machine speed, outpacing human security teams’ ability to detect and respond to malicious activity.

-
Overwhelmed security teams can no longer keep up with the speed of cyber-attacks that threaten to shut down power grids and disrupt how we work. The boundaries of modern-day businesses are blurred, particularly with the convergence of IT and OT/ICS technologies due to increased remote working in industrial and manufacturing environments. Security teams in this space must defend an increasingly complex attack surface because of rapid digital transformation and an explosion in IoT.
-
For organizations operating critical infrastructure across all 16 sectors designated by the Cybersecurity and Infrastructure Security Agency, Darktrace Detect/OT (formerly the Darktrace Industrial Immune System), uses Self-learning AI to fill this critical gap. Darktrace’s Self-Learning AI offers security teams a breadth of contextual understanding and visibility, autonomously identifying and mitigating against these risks rather than just alerting these organizations that they are vulnerable.
-
At its core, Darktrace Detect/OT exists to deliver AI-powered technology that can autonomously defend these organizations that humans depend on in daily life from sophisticated, stealthy, and machine-speed cyber-attacks. This immune system technology uses Self-learning AI to understand ‘normal’ behavior for each unique business, detect anomalous events or behaviors, and build a robust and bespoke cyber-defense based on enforcing this ‘normal.”
-
Today, this ability for the machine to fight back is, on average, stopping ransomware within one second of detecting threatening activity. By stopping threats in their tracks, companies using Darktrace self-learning AI do not have to shut down systems for days on end and do not have to pay hefty ransoms to criminals.
(Learn how Darktrace’s technology vision is of a Cyber AI Loop; a system that improves cyber security and augments humans at every stage of an attack life cycle, from the pre-incident phase with PREVENT, to DETECT and RESPOND for an in-progress attack, and – coming in 2023 – HEAL, for the post-incident phase, after an attack has taken place. Courtesy of Darktrace and YouTube.)
-
Self-learning AI technology protects over 6,800 organizations – from renewable energy suppliers to education and healthcare providers – letting them focus on their respective goals. Darktrace technology sets it apart from not only every other cybersecurity solution on the market today but also from other approaches to AI.
Darktrace (Second of Two)
 Best Cyber Security Solution
Best Cyber Security Solution
-
Darktrace RESPOND
-
Every other cyber company learns from historical attack data to stop known attacks from getting inside an organization.
-
Darktrace’s Self-Learning AI doesn’t rely on historical data. Instead, it analyzes and determines ‘normal’ behaviors for users and devices across a digital estate. By evolving its understanding to learn the businesses, not the breach, Darktrace is fundamentally different from other vendors.
-
Through its Autonomous Response technology Darktrace RESPOND (formerly Darktrace Antigena), Darktrace’s AI uses this understanding to identify anomalous behavior and interrupt attacks in real time before they escalate into a crisis and disrupt business operations.
-
From internet-connected machinery to email, endpoints, and SaaS applications, Darktrace can protect the entire business, wherever data lives. Darktrace RESPOND can enforce normal 24/7, whether the organization experiences an out-of-hours ransomware attack or an insider exfiltrating sensitive data. Darktrace globally responds to a threat every three seconds.
(Darktrace AI-powered solutions have resulted in over 115 patent applications filed and significant research published to contribute to the cyber security community. Darktrace’s technology continuously learns and updates its knowledge of ‘you’ for an organization and applies that understanding to achieve an optimal state of cyber security. It delivers the first-ever Cyber AI Loop, fueling a continuous end-to-end security capability that can autonomously prevent, detect, and respond to novel, in-progress threats in real-time. Darktrace was named one of TIME magazine’s ‘Most Influential Companies’ in 2021. Courtesy of Darktrace and YouTube.)
- Darktrace RESPOND can defend any technology in any environment. With coverage areas ranging from network to the cloud to email and SaaS, Darktrace RESPOND continues to augment the world’s ability to respond to complex and novel cyber-attacks.
-
With the critical visibility allowed by Self-learning AI, this autonomous response technology has recently been extended to protect endpoints and better integrate with Zero Trust architectures through partnerships with Microsoft and AWS.
-
Darktrace RESPOND intercepts complex, multi-step ransomware attacks, combatting malicious activity at machine speed, anywhere within an enterprise. In the wake of the ransomware breach of Colonial Pipeline, Darktrace protects customers from similarly damaging attacks across all 16 critical infrastructure sectors designated by the Cybersecurity and Infrastructure Security Agency.
As cyber-attacks get faster, more advanced, and more automated, security teams are overwhelmed and outpaced. Autonomous Response changes the stakes for defenders by giving security teams the ability to contain fast-moving threats, even when they are not in the office or online and cannot respond fast enough.
-
Darktrace’s AI does not replace human security teams – it augments them, giving them greater resources to focus on strategic tasks. It helps businesses make micro-decisions so humans can focus on higher-priority responsibilities.
-
*Darktrace is a Returning Competitor in the 2022 ‘ASTORS’ Homeland Security Awards Program, having secured a Win in the 2019 ‘ASTORS’ Awards Program.
NEXT View Part 2 Winners De – M View Part 3 Winners NE – Sl
View Part 4 Winners So – Z View Part 5 Government Excellence
Part 6 Innovation & Leadership
The 2022 ‘ASTORS’ Awards Program was Proudly Sponsored by NEC National Security Systems (NSS), ATI Systems, Automatic Systems of America, guardDog AI, Fortior Solutions, IPVideo Corporation, Rajant Corporation, RX Global, and SIMS Software!
- **IN A RARE TIE Event (thrice occurring) is a result of either extremely differing objectives and/or very similar technology applications.


















