
Sophisticated nation-state adversaries who compromised a string of federal agencies in recent months used Kerberoasting to steal the passwords of agency employees and move laterally within compromised government networks, according to the latest guidance from the Department of Homeland Security.
In an Emergency Directive, the agency instructs federal agencies to “take action to remediate kerberoasting,” including engaging with third-party organizations that have experience “eradicating APTs from enterprise networks,” a reference to so-called “advanced, persistent threats.”

“If anyone had any doubts about whether the attackers are already inside your networks, then the last week’s events indicate that you must expect that attackers already came in through various back doors,” explains Tushar Kothari, CEO of Attivo Networks®.
Some notable highlights from industry and government also drive this point home.
“Once inside the network, attackers almost always escalate privileges and move laterally to perform reconnaissance and access the information they are interested in stealing,” added Marshall Heilman, SVP at Mandiant.
There are many solutions on the market that look at signatures or try to detect based on behaviors.

Alternatively, Attivo Networks, a leader in cyber deception and attacker lateral movement threat detection, and Four-Time Winner in the 2020 ‘ASTORS’ Homeland Security Awards Program, offers solutions that focus on the techniques, making prevention and detection much more effective and reliable.
The company’s portfolio includes best-in-class capabilities to deny, detect, and derail threats to prevent attackers from escalating privileges and moving laterally inside the network.
In some recent advanced attacks, detecting lateral movement is the most effective way to find adversaries inside your network.
(Sophisticated attackers are targeting credentials to escalate privileges. See how Attivo Networks provides an innovative solution that finds, cleans and monitors exposed credentials to reduce attack surfaces. Courtesy of Attivo Networks and YouTube.)
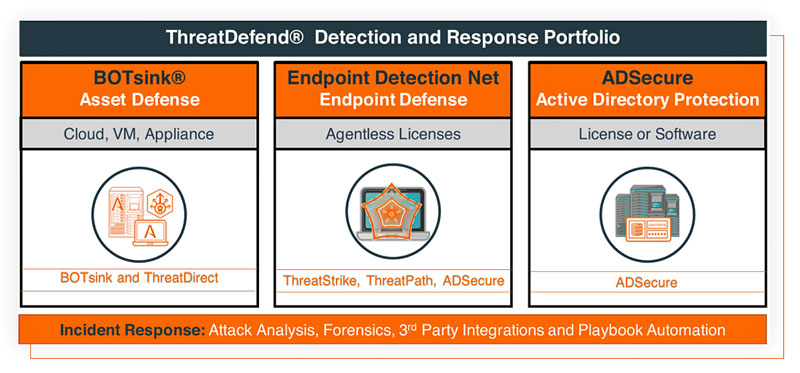
Endpoint Detection Net (EDN)
Attivo Networks ThreatDefend platform’s Endpoint Detection Net (EDN), the 2020 Platinum Award Winner for ‘Best Intrusion Detection & Prevention Solutions’ include:
-
Gaining in-depth visibility with the ADSecure solution into who is enumerating and discovering permissions from Active Directory
-
Preventing exposures of high privilege accounts, service accounts, domain controllers, etc. with the ADSecure solution
-
Gaining visibility with ThreatPath into Lateral Movement Paths (LMP) or exposed credentials on endpoints, and remediating these exposures.
-
Gaining visibility with ThreatStrike into attackers stealing credentials and using them
-
Preventing attackers from fingerprinting and discovering high-value database servers, file servers, etc., with the EDN Deflect function.
-
Protecting important files and documents from encryption and exfiltration, and network mapped shares, cloud mapped shares, etc., from attackers and ransomware

The ThreatDefend platform offers these and many more capabilities to defend the network from unrestricted lateral movement activities.
Given the current situation, Attivo is stepping up with immediate free access to these products for customers who need and want to immediately shore up their defenses to prevent attackers from progressing inside the network.
 Meanwhile, Attivo will continue to work with you on a longer-term deployment and operations plan.
Meanwhile, Attivo will continue to work with you on a longer-term deployment and operations plan.
Contact Attivo directly so they can recommend and provide the optimum solution at attivonetworks.com/endpoint-detection-net-offer/.
Attivo Networks a Multi-Award Winner in 2020 ‘ASTORS’ Awards Program
 American Security Today’s ‘ASTORS’ Homeland Security Awards program is in its Fifth Year and continues to recognize the Outstanding Innovations of top firms and agencies in the Homeland Security and Public Safety fields.
American Security Today’s ‘ASTORS’ Homeland Security Awards program is in its Fifth Year and continues to recognize the Outstanding Innovations of top firms and agencies in the Homeland Security and Public Safety fields.
2020 has been a very challenging year for everyone due to the COVID-19 pandemic and the much heralded AST ‘ASTORS’ Awards Winners Presentations and exclusive Luncheon at the Jacob Javits Center in NYC has been canceled and rescheduled for 2021 due to the virus.

However, the 2020 ‘ASTORS’ Homeland Security Awards Program was again a huge success and many new categories were added including a section for COVID-19 Detection and Innovation.
Attivo Networks
Best Intrusion Detection & Prevention Solution
-
Endpoint Detection Net (EDN)
-
The Attivo ThreatDefend® Platform EDN suite strengthens endpoint defensive capabilities by detecting and alerting on attack tactics that attackers use once they manage to compromise a system to spread to other devices on the network. The EDN suite helps reduce the cost of the attack and minimizes the personnel needed to respond to incidents.
-
Built on layered detection technology, the Attivo EDN offering makes every endpoint a decoy designed to disrupt an attacker’s ability to break out and further infiltrate the network.
-
It does this without requiring agents on the endpoint or causing disruption to regular network operations. Attivo used historical attack data and the MITRE ATT&CK framework as a way to understand the various methods attackers use to spread laterally from an endpoint.
-
The company then created a comprehensive solution designed to increase MITRE Security Assessment scores and to detect and stop unwanted intruders quickly.
(Hear from Carolyn Crandall and Tony Cole on how Endpoint Detection Net tackles endpoint security challenges head-on by making every endpoint a decoy designed to disrupt an attacker’s ability to break out and further infiltrate the network – all without requiring agents on the endpoint or causing disruption to regular network operations. Courtesy of Attivo Networks and YouTube.)
-
The Endpoint Detection Net solution elevates security control by accurately raising alerts and taking proactive measures to derail attackers.
-
Of particular interest are the many EPP/EDR partners that the solution integrates with that can block an infected system to prevent further compromises, such as McAfee, Crowdstrike, Forescout, and many more. The platform adds visibility and detection to existing security solutions, and the partner integrations enhance and accelerate investigations and incident response.
-
The EDN solution also enhances current EPP and EDR solutions by adding coverage for attack tactics, techniques, and procedures that bypass existing controls. While EPP and EDR work to prevent a compromise, if the attacker does succeed, the EDN solution is there to keep the attacker from laterally moving while remaining undetected.
Attivo Networks
Best IT Threat Intel Solution
-
ThreatDefend Platform with Informer UI
-
The Attivo Networks ThreatDefend® platform is a comprehensive detection solution for attack activities inside the network that offers in-network visibility and detection for on-premises, cloud, and remote locations across all attack surfaces and against any attack vector.
-
It detects lateral movement activity such as discovery and reconnaissance, port and service scans, data gathering from Active Directory, Man-in-the-Middle attacks, credential theft and reuse, and mapped share traversal.
-
The platform does this by deploying network, endpoint, application, data, and AD decoys and deceptive assets to create a fabric that misdirects and misinforms attackers.
-
The decoys record all attack activity while alerting security teams to the attack, reducing investigation and response times while capturing network, memory, and disk forensic data for intelligence development.
-
With the forensic capture of all attack data on the decoys, organizations gain robust data to develop threat intelligence for attacks that are targeting them specifically.
-
The platform includes analysis and filtering tools that correlate the attack data in chronological order and can display the attack in a graphical replay.
-
The ThreatDefend platform includes the Informer dashboard to accelerate investigations. The Informer dashboard correlates all information about a single in-network attack source and displays it in a simple, easy to use interface.

-
The readout includes the details about the system (such as system name, IP address, logged on user, etc.), a timeline view, and the events originating from the system in reverse chronological order that includes all event data.
-
Additionally, the dashboard shows first, second, and third-order hops from the system based on stored credentials and misconfigurations, and a means to initiate a partner integration to isolate the endpoint.
-
It even includes direct links to any forensic files and data captured by the decoys for quick downloads, such as packet capture files, malware analysis reports, memory forensics analysis, and the data and binary files themselves.
-
This dashboard aids in analysis and investigations by putting all the details the investigator would need in a single source, fully correlated, and ready to action.
-
Few providers can offer network, disk, and memory forensic capture at the time of the attack, coupled with the correlation of all event data and forensic evidence to create adversary intelligence to such a degree.
(Learn More about deception technology and the Attivo Networks ThreatDefend Deception and Response Platform. Courtesy of Attivo Networks and YouTube.)
Attivo Networks
Best Privileged Access Security Solution
-
ADSecure
-
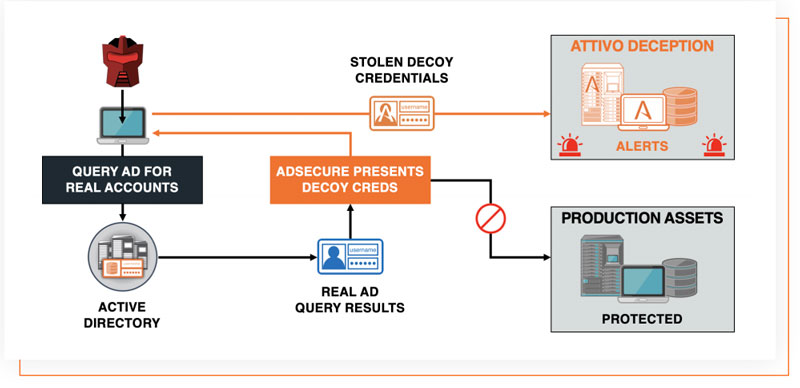
Inherently, there is no ideal way to secure Active Directory environments, however, the Attivo Networks ADSecure solution dramatically reduces risk by hiding real AD objects and returning fake data to an attacker, which, if used, diverts the attacker to a decoy environment.
-
When deployed as part of the Attivo Networks ThreatDefend® Platform, defenders can gather adversary intelligence as the solution redirects queries and activities into the decoy environment. They now gain the ability to collect and take action on company-centric threat intelligence.
-
The ADSecure solution is truly a revolutionary way to protect against successful Active Directory attacks, without interfering with production AD operations, requiring logs, or complex rights and permissions management.
-
Additionally, one of the best things about deployment is that one doesn’t have to touch or alter production Active Directory controllers for it to work. Implementation is exceptionally straightforward, with the majority of the setup time spent on strategy for how in-depth one wants to make the fake ADSecure environment and information.
ADSecure can be deployed as a standalone product or easily installed as an add-on license to the ThreatDefend Platform.
-
This method of prevention is an invaluable deterrent as attackers can no longer trust what they see or the tools they rely on.

*Attivo Networks is also a Returning Premier Sponsor of the 2020 ‘ASTORS’ Homeland Security Awards Program, and a Multi-Platinum Award Winner in the 2019, 2018 and 2017 ‘ASTORS’ Awards Program.
Attivo Networks®, a leader in cyber deception and lateral movement attack detection, delivers a superior defense for revealing and preventing unauthorized insider and external threat activity.

The customer-proven Attivo ThreatDefend® Platform provides a scalable solution for derailing attackers and reducing the attack surface within user networks, data centers, clouds, remote worksites, and specialized attack surfaces.
The portfolio defends at the endpoint, Active Directory, and throughout the network with ground-breaking innovations for preventing and misdirecting lateral attack activity. Forensics, automated attack analysis, and third-party native integrations streamline incident response.
To Learn More, visit Attivo Networks.
The 2020 ‘ASTORS’ Awards Program is sponsored by ATI Systems, Attivo Networks, Automatic Systems, Desktop Alert, X.Labs and Reed Expositions, every one a returning Sponsor from 2019.
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace with over 75,000 readers at the Federal, State and local levels of government as well as firms allied to government.
American Security Today brings forward a fresh compelling look and read with our customized digital publications that hold readers eyes throughout the story with cutting edge editorial that provides solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

The AST Digital Publications is distributed to over 75,000 qualified government and homeland security professionals in federal, state and local levels.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches both Private & Public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from Government at the federal, state and local level as well as from private firms allied to government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants & Dams, Bridges & Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting & Concert Stadiums, our Nation’s Schools & Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
To learn more about the 2020 ‘ASTORS’ Homeland Security Award Winners solutions, please be on the lookout for the 2020 ‘ASTORS’ CHAMPIONS Edition Fully Interactive Magazine – the Best Products of 2020 ‘A Year in Review’.
The Annual CHAMPIONS edition includes a review of the ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firms products and services, includes video interviews and more.
 It will be your Go-To source throughout the year for ‘The Best of 2020 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
It will be your Go-To source throughout the year for ‘The Best of 2020 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware and Networking Security – Just to name a few), the 2020 ‘ASTORS’ CHAMPIONS EDITION will have what you need to Detect, Delay, Respond to, and Mitgate today’s real-time threats in our constantly evolving security landscape.
It also includes featured guest editorial pieces from some of the security industry’s most respected leaders, and recognized firms in the 2020 ‘ASTORS’ Awards Program.
-
For a complete list of 2020 ‘ASTORS’ Award Winners, click here.
For more information about the Annual ‘ASTORS’ Awards or All Things American Security Today, please contact Michael Madsen, AST Publisher at mmadsen@americansecuritytoday.com.
1Gartner, Inc., “Innovation Insight for Extended Detection and Response,” by Peter Firstbrook and Craig Lawson, 19 March 2020
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos























