According to the White House, strengthening the cybersecurity of federal networks, systems, and data is one of the most important challenges the United States faces as a nation.
Controlling, monitoring, and auditing privileged access is extremely important to accomplish this mission by mitigating the risks posed by insider threats, preventing data breaches, and meeting compliance requirements.
The government has implemented a wide variety of mandates and programs, such as FISMA, the Cybersecurity Strategy and Implementation Plan (CSIP), and the DoD Cyber culture and Compliance Initiative (DC3I) to protect information security assets.
Today, most agencies are using multiple disjointed tools that are costly to maintain and don’t integrate to provide the right information and insight on users and assets to successfully enable collaboration.
Therefore, it is getting more difficult for CISOs to assess their agencies’ risks and to determine how to allocate already-stretched resources.
A most troubling trend in widely publicized breaches of government information systems has been the misuse or exploitation of privileged accounts.
To mitigate the risks of breach through privileged accounts, organizations must be empowered to efficiently manage this access.
Comprehensive Unix & Linux Privilege and Session Management to Protect Your Most Critical Systems

It’s no secret that Unix and Linux systems present high-value targets for external attackers and malicious insiders alike.
You can expect to be breached if you share credentials, provide unfettered root access, or let files and sessions go unmonitored.
Gaining root or other privileged credentials makes it easy for attackers to fly under the radar and access sensitive systems and data.
And the risk only increases as attack surfaces expand, perimeters vanish, attackers get smarter, and compliance pressures mount.
PowerBroker for Unix and Linux is an enterprise-class, gold-standard privilege management solution that helps security and IT organizations achieve compliance, control privileged access, and prevent and contain breaches that can effect Unix and Linux systems.
BeyondTrust PowerBroker for Unix and Linux allows IT organizations to efficiently delegate Unix and Linux privileges and authorization without disclosing passwords for root or other accounts, record all privileged sessions for audits—including keystroke information—and achieve privileged access control requirements without relying on native tools or sudo.
(Learn More. Courtesy of BeyondTrust and Vimeo)
PowerBroker for Unix & Linux from BeyondTrust is part of a holistic platform that protects your organization with comprehensive layers of control, auditing, and analytics.
- Monitor and audit sessions for unauthorized access, changes to files and directories, and compliance
- Reduce attack surfaces by eliminating credential sharing, enforcing least privilege, and elevating commands without requiring users to have root access.
- Analyze behavior to detect suspicious user, account and asset activity.
- Centralize management, policy and reporting.
Most of all, PowerBroker reduces the time-consuming redundancies and complex security exposures created by locally managed, ad-hoc tools like Sudo.
PowerBroker. The end-to-end privilege management solution that delivers visibility, control, and protection for Unix and Linux systems – with the simplicity of a single, centralized, console.
Benefits of BeyondTrust PowerBroker for Unix and Linux include:

- Enhanced security through fine-grained, policy-based control of privileged accounts
- Enables segregation of duties by compartmentalizing IT tasks
- Replaces, and simplifies migration from existing open-source tools such as sudo with a commercially supported solution
- Achieve policy driven command elevation and auditing—down to the system level—with no change to the user experience
- Enables compliance through keystroke logging and DVR-style recording of all activity performed by the user
- Centralize single pane of glass management
- Common Criteria Certified
PowerBroker enables organizations to improve server security while simplifying privileged access management deployments and reducing costs.
Forrester recently recognized BeyondTrust as Industry Leaders in their latest PIM Wave report.
(Enterprise passwords are the keys to your IT kingdom, and abuse or misuse of those credentials is the cause of most data breaches today. Courtesy of BeyondTrust and Vimeo)
PowerBroker privileged access management platform for Unix and Linux systems has received Common Criteria certification.
Achievement of this certification helps to assure that government agencies and global enterprises can confidently procure and use PowerBroker for Unix & Linux to secure their environments against the threat of privileged account compromise without the added cost and complexity of additional product testing.
- Common Criteria is the foundation for the widest-available mutual international recognition of secure IT products.
- Its goals include improving the availability of security-enhanced IT products and supporting more efficient procurement of solutions.
(PowerBroker Endpoint Least Privilege closes security gaps left by other solutions, providing you with comprehensive visibility and control over user, account and system security. Courtesy of BeyondTrust and Vimeo)
The Leidos (formerly SAIC) Common Criteria Testing Laboratory conducted the testing of PowerBroker for Unix & Linux, and the National Information Assurance Partnership (NIAP), the United States approving authority, granted the Common Criteria certificate (# 10691) that became effective on August 30, 2016.
PowerBroker for Unix and Linux achieved protection profile certification in Enterprise Security Management—Policy Management Version 2.1, and U.S. Government Approved Protection Profile—Protection Profile for Enterprise Security Management-Access Control Version 2.1.
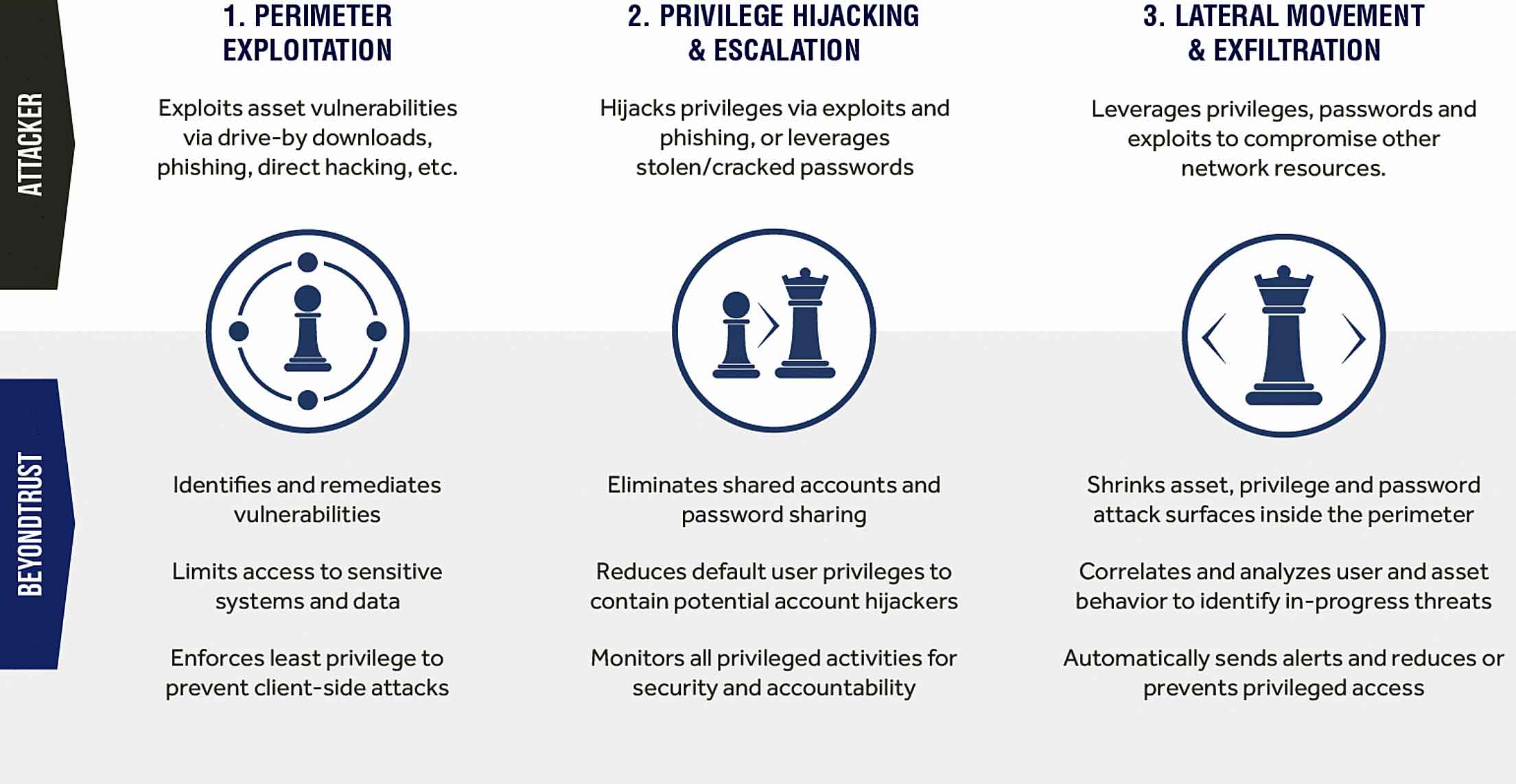
When deployed as part of the PowerBroker Server Privilege Management solution, PowerBroker for Unix & Linux enables you to disrupt all stages of the cyber attack chain.
The solution combines best-in-class privilege, password and vulnerability management on top of a centralized reporting and analytics platform.
As a result, you can efficiently reduce your organization’s attack surface, prevent lateral movement by attackers, and actively detect and respond to in-progress breaches.
With over 30 years of experience in server privilege management, BeyondTrust knows what it takes to protect your critical, tier-1 systems, and help you reduce risk and achieve compliance.
BeyondTrust at a Glance
BeyondTrust is a global information security software company that helps organizations prevent cyber attacks and unauthorized data access due to privilege abuse.
Their solutions give you the visibility to confidently reduce risks and the control to take proactive, informed action against data breach threats.
And because threats can come from anywhere, BeyondTrust built a platform that unifies the most effective technologies for addressing both internal and external risk: Privileged Access Management and Vulnerability Management.
BeyondTrust’s security solutions are trusted by over 4,000 customers worldwide, including half of the Fortune 100.
BeyondTrust Competes in 2018 ‘ASTORS’ Homeland Security Awards Program
AST focuses on Homeland Security and Public Safety Breaking News, the Newest Initiatives and Hottest Technologies in Physical & IT Security, essential to meeting today’s growing security challenges.
 The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.
The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.
As an ‘ASTORS’ competitor, PowerBroker for Unix & Linux will be competing against the industry’s leading providers of Innovative Access Control & Authentication Systems.
To Learn More about the ‘ASTORS’ Homeland Security Awards Program, see 2017 ‘ASTORS’ Homeland Security Award Winners Honored at ISC East.

Over 100 distinguished guests from National, State and Local Governments, and Industry Leading Corporate Executives from companies allied to Government, gathered from across North America and the Middle East to be honored from disciplines across the Security Industry in their respective fields which included representatives from:
 The Department of Homeland Security
The Department of Homeland Security- The Department of Justice
- The Security Exchange Commission
- State and Municipal Law Enforcement Agencies
- Leaders in Private Security