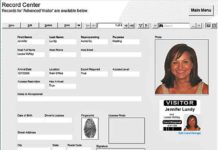
X-Force Red Finds Security Threats in Visitor Management System Kiosks
March 4, 2018 – In Breaking News – WIRED
DANIEL CROWLEY HAS a long list of software platforms, computers, and internet-of-things devices that he suspects he could hack.
As research director of IBM’s offensive security group...
What Are the Most Secure VPN Proto-cols & Why? (Learn More, See Video)
By Howard Dawson, Writer & Tech Enthusiast
Virtual Private Networks (VPN) are vital applications for those who want to keep their Web browsing data private.
They allow for safe surfing of the internet and to...
NIST Guide to ‘Mobile Device Security: Cloud and Hybrid Builds’ Now Live
NIST Cybersecurity Practice Guide SP 1800-4 Mobile Device Security: Cloud and Hybrid Builds, is now final.
If sensitive data is stored on a poorly secured mobile device that is lost or stolen, an attacker...
Drowning in a Tsunami of Digital Evidence? Here’s Your Lifeline
By Rod Guy, VP of Strategy, NICE Public Safety
Today, crime solving hinges on digital evidence and the volume, velocity and variety of digital evidence is growing exponentially.
From body-worn cameras and CCTV,...
Strategies & Solutions to Enforce DoD’s Cybersecurity ‘Lines of Effort’
By Jim Hansen, Vice President of Products & Security, SolarWinds
The Department of Defense is going on the offense.
The DoD Cybersecurity Discipline Implementation Plan outlines several key “Lines of Effort” to strengthen government...
21 Terrifying Cyber Crime Statistics
By Jack Foster, Author at VPN Geeks
Unfortunately, with technology on the rise, there’s more room for cyber crime in 2019.
According to the Cyber Security Breaches Survey 2018, 43% of businesses were a victim of...
Gurucul Takes Platinum in 2018 ‘ASTORS’ Awards (Multi-Video)
Gurucul, a leader in behavior based security and fraud analytics technology for on-premises and the cloud, has been named the Platinum Award for 'Best User & Entity Behavior Analytics (UEBA) Solution'...
Arming Against Attack: Three Strategies to Fight Foreign Hackers
By Paul Parker, Chief Technologist, Federal and National Government, SolarWinds
As we move closer to the United States midterm elections, cybersecurity has become a hot topic of conversation.
From Facebook to the Department...
Pivot3 Sees Over 50% Growth in 2018, Named 2018 ‘ASTORS’ Award Finalist
Pivot3, a hyperconverged infrastructure (HCI) performance and technology leader and a Finalist in the 2018 'ASTORS' Homeland Security Awards Program, has announced the company experienced more than 50-percent growth in bookings...
Fortanix & Alibaba Launch SDKMS Runtime Encryption Key Mngmt
Fortanix, a leader in Runtime Encryption®, and a Finalist in the 2018 ‘ASTORS’ Awards Program, is partnering with Alibaba Cloud, the cloud computing arm of Alibaba Group, to integrate its Self-Defending Key Management Service™...