
By Kevin Corbett, Director of U.S. Federal Business, CyberArk
Government agencies and departments face a wide range of security challenges – and they have a lot at risk.
Just consider the U.S. Office of Personnel Management data breach, Shadow Brokers’ leak of NSA exploit tools and the hacking of the 2016 Democratic National Committee email system.
(The hackers behind the country’s worst cyber attack is still a mystery, and some say the so-called “Shadow Brokers” are causing a chilling effect on the National Security Agency. Courtesy of NBC News and YouTube. Posted on Nov 13, 2017.)
Attackers are increasingly targeting government networks to compromise sensitive data, steal personally identifiable information and disrupt normal operations.
This coupled with the fact that government agencies are expanding their attack surfaces as they adopt new cloud and DevOps environments creates heightened levels of risk.
Where to Start
To help agencies address this risk, the National Institute of Standards and Technology (NIST) recently released version 1.1 of its CyberSecurity Framework, which incorporates feedback received from public comments and workshops over the past two years.
(Learn why organizations of all sizes and types should be using NIST’s voluntary Cybersecurity Framework, which is based on existing standards, guidelines, and best practices. Created through collaboration between industry, academia and government, the flexible Framework helps organizations manage their cybersecurity-related risk. Courtesy of National Institute of Standards and Technology and YouTube. Posted on Sep 14, 2016.)
Many of the CyberSecurity Framework’s refinements center around cyber hygiene—or actionable steps that organizations can take to “clean up” current weaknesses and potential vulnerabilities and improve overall security posture.
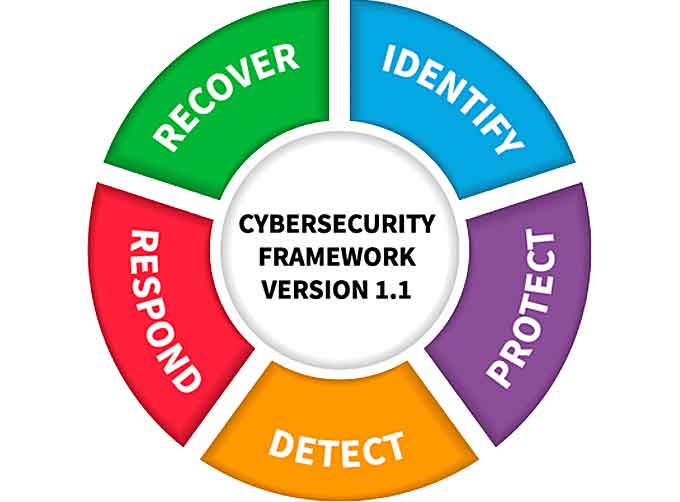
These steps are particularly important in the wake of incidents like the ones mentioned above.
Unfortunately, many of the incidents rocking headlines could have largely been prevented if basic security best practices had been applied.
As the CyberSecurity Framework underscores, one of the most effective, preventative steps agencies can take to bolster security programs is to secure privileged accounts, credentials and secrets.
Attackers continually look for new ways to exploit vulnerabilities, so a “set it and forget it” approach is sure to fail, especially when it comes to privileged access since an agency’s sensitive applications and systems can change as it grows or changes direction.
A Tried and True Cyber Hygiene Program
To help agencies and organizations establish and maintain strong a privileged access security program, CyberArk developed customized, step-by-step goals and an actionable process for achieving the highest level of protection against common attacks on privileged accounts, credentials and secrets.
(See how CyberArk’s integrated Privileged Account Security Solution secures all of your privileged accounts, delivers multiple layers of security, provides quantifiable results and saves you money. Courtesy of CyberArk and YouTube. Posted on Published on May 4, 2015.)
The CyberArk Privileged Access Security Hygiene Program helps agencies better establish and maintain effective privileged access security throughout ongoing infrastructure changes.
They can implement this program by following the seven below best practices.
-
Eliminate irreversible network takeover attacks
Irreversible network attacks are not only hard to identify, they’re also so intrusive that agencies are forced to rebuild to remove the attacker. To eliminate such attacks, make sure all privileged access to tier0 and tier1 is isolated and that it requires multi-factor authentication. Also, ensure there are no hash residuals by design.
-
Control and secure infrastructure accounts
 Default on-premises or cloud infrastructure accounts that are seldom used in day-to-day operations can provide attackers with excellent access opportunities, so it’s important to get to 100 percent managed accounts by determining how many local admins are vaulted on various servers and how your cloud infrastructure accounts are being secured.
Default on-premises or cloud infrastructure accounts that are seldom used in day-to-day operations can provide attackers with excellent access opportunities, so it’s important to get to 100 percent managed accounts by determining how many local admins are vaulted on various servers and how your cloud infrastructure accounts are being secured. -
Limit lateral movement
To prevent attackers from leveraging Pass-the-Hash techniques and stealing credentials by moving laterally across your infrastructure, completely remove all endpoint users from the local admins group on any IT Windows workstations.
-
Protect third-party application credentials

By compromising third-party applications, attackers can steal embedded, privileged credentials all while completely circumventing an agency’s defenses. Vault all privileged accounts used by third party applications to ensure protection.
-
Manage NIX SSH keys
Attackers can leverage unmanaged SSH keys to login with root access and take over the NIX technology stack, so make sure all SSH key pairs on Linux and Unix production servers are vaulted and rotated on a routine basis, as these systems often house highly sensitive assets.
-
Defend DevOps secrets

To ensure attackers can’t exploit your DevOps environment for more pervasive access, vault and automatically rotate your public cloud privileged accounts, keys and API keys as well as any credentials and secrets used by CI/CD tools such as Ansible, Jenkins and Docker.
-
Secure SaaS admins and privileged users
Confirm that all access to shared IDs is isolated and require multi-factor authentication to prevent attackers from gaining high-level and stealthy access to sensitive systems by stealing credentials used by SaaS administrators and privileged business users.
Remaining Vigilant
Recent research indicates that 57 percent of federal organizations experienced a data breach in the past year, in comparison to just 26 percent of non-U.S. government agencies worldwide.
Furthermore, 68 percent of respondents said their government organizations are “very” or “extremely” vulnerable to current cyber security challenges, while only 48 percent of global counterparts admit to the same.
(Cindy Provin, CEO of Thales eSecurity, discusses key findings from Thales eSecurity’s 2018 Data Threat Report, Global Edition. Courtesy of Thales eSecurity and YouTube. Posted on Jan 23, 2018.)
Government agencies and departments must do more to protect their critical assets by prioritizing the protection of their most important privileged accounts, credential and secrets.
Start by identifying any potential vulnerabilities in existing privileged access security programs and work to remediate those weaknesses by directly addressing the most common types of attacks used to exploit privileged access.
Most importantly, remember to continually reassess and improve upon privileged access security efforts as the cyber threat environment and any organizational requirements evolve over time.

Maintaining the optimum level of protection for privileged access requires staying vigilant.
About the Author:
As director of U.S. federal business at CyberArk, Kevin Corbett is passionate about helping agencies “think like an attacker” with an “assume breach” mentality in order to put proactive controls in place to protect their most sensitive credentials – the ones that attackers increasingly seek out to carry out attacks.
CyberArk Competes in 2018 ‘ASTORS’ Homeland Security Awards Program
AST focuses on Homeland Security and Public Safety Breaking News, the Newest Initiatives and Hottest Technologies in Physical & IT Security, essential to meeting today’s growing security challenges.
 The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.’
The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.’
As an ‘ASTORS’ competitor, CyberArk’s Privileged Access Security Solution, will be competing against the industry’s leading providers of Innovative Identification Management Solutions.
To Learn More about the ‘ASTORS’ Homeland Security Awards Program, see 2017 ‘ASTORS’ Homeland Security Award Winners Honored at ISC East.

Over 100 distinguished guests from National, State and Local Governments, and Industry Leading Corporate Executives from companies allied to Government, gathered from across North America and the Middle East to be honored from disciplines across the Security Industry in their respective fields which included representatives from:
- The Department of Homeland Security (DHS) Science and Technology Directorate (S&T)
- U.S. Customs and Border Protection
- The Department of Justice
- The Security Exchange Commission
- State and Municipal Law Enforcement Agencies
- The Royal Canadian Mounted Police
- Leaders in Private Security
The highlight of the 2018 AST Homeland Security Awards Season will be the 2018 ‘ASTORS’ Awards Presentation Luncheon to honor Nominees, Finalists and Winners on November 14, 2018 at ISC East 2018 at the Jacob Javits Exhibition Center in New York City.
Good luck to CyberArk on becoming a Winner of the 2018 American Security Today’s Homeland Security Awards Program!
To Learn More about CyberArk’s Privileged Access Security Solution, please visit https://www.cyberark.com/products/privileged-account-security-solution/core-privileged-account-security/.
Join us in Recognizing these Industry-Leading Firms for their Outstanding Product Development Achievements, Exciting New Technologies and Innovative Education Programs to address the growing Homeland Security Threats our Nation is facing.
Take advantage of this exclusive luncheon opportunity to Invite your Guests, Clients and Show Visitors to a lovely & affordable plated meal event in the heart of New York City, for a Fabulous Networking Opportunity!
ISC East is the Northeast’s largest security industry event and your ‘ASTORS’ Awards Luncheon registration includes complimentary attendee access to the show.
Already Exhibiting and/or Attending the 2018 ISC East Conference?
Join us to meet the 2018 ‘ASTORS’ Award Winning Company Executives & Government Agency Representatives.
Register today for the ‘ASTORS’ Homeland Security Awards Luncheon on November 14th, in New York City and give yourself & your clients a break from the show!
Gourmet luncheon choices available per person, or reserve a table – make an Impression on your Guests and Receive an Exclusive Discount Opportunity.




















