By Stanley I, White and Ewart Williams
If you are not aware of something than that entity is invisible to you at the moment.
What goes unseen can possibly be the thing that does the most harm to you at that time.
A common expression uttered to the victim of surprise whether it be an intelligence agency or an average person is, “you didn’t see that coming.”
No agency or individual can detect everything.
However, the greater one’s awareness as well as their ability to act on it can make the difference between tragedy and success.
The records of the first human ambush that resulted in a loss of innocent life was detailed in the Old Testament book of Genesis, Chapter 4:8 which reads:

One day Cain suggested to his brother, ”Let’s go out into the fields “. And while in they were in the field, Cain attacked his brother, Abel, and killed him.
In Verse 10 the Lord asked Cain,” What have you done? ….Your brother’s blood cries out to me from the ground.”
This story provides a prime example of violence against the innocent and started the continual cycle of an adversary shedding innocent blood many times through seizing the opportunity and catching the victim by surprise.
Modern day violence found in the form of terrorism, criminal acts, workplace violence etc. thrive on the element of surprise.
Summarized below are three less known incidents of violence that took the lives of the innocent individuals through surprise actions:
The Gamboru and Ngala Attacks
This attack took place from May 5 to 6, 2014, in the towns of Gamboru and Ngala, Nigeria. During this time, more than 200 people were killed by the Boko Haram militia.
The attack took almost 12 hours, and the towns were almost completely destroyed survivors fled to the neighboring country of Cameroon.
The two towns had a security units that left to pursue schoolgirls who had been kidnapped in an earlier attack.
The attackers set fire to the towns and opened fire on civilians who were trying to escape.
(Fighters of outlawed armed group Boko Haram are being accused of killing hundreds of people in northeast Nigeria. A local senator in Borno State told Al Jazeera that gunmen stormed the town of Gamboru Ngala on Monday. Last month, Boko Haram kidnapped more than 270 school girls in the same area. Courtesy of Al Jazeera and YouTube. Posted on May 7, 2014.)
The Massacre of Trujillo
The massacre consisted of a series of violent assaults carried out between 1988 and 1994 in the town of Trujillo, Colombia.
These attacks were executed in the southwest region of Colombia by the Cali Cartel and aided by Colombia’s military and law enforcement units.
Approximate 250-300 people were murdered; these actions were intended to serve as a warning to union members and supporters of guerrilla forces.

The Cinema Rex Fire
On August 19, 1978, the Cinema Rex Theatre located in Abadan the western region of Iran was set on fire killing approximately 400 individuals.
This attack took place when hundreds of people were watching the Iranian movie “The Deer”.
The cinema was set on fire by four men who locked the ingress and egress points of the venue. All in attendance inside the cinema died from the blaze.
The exact motive behind the attack remains unknown, however the Iranian Revolution was believed to be the key factor contributing to the attack that remains one of the worst in Iranian history.

The above tragedies were conducted on a large scale, however, greater awareness on the behalf of the subject governments, security units and everyday citizens may not have thwarted these attacks but at least resulted in a lower loss of life.
The central goal of this paper is to introduce the reader to the concept of Protective Awareness.
In addition to analyzing the finer points of Protective Awareness the reader will be exposed to a physical security protocol modified to make the user the central asset secured as opposed to a structure, corporate campus, educational facility etc.
This method is called the 3 Zone Security Plan (3ZSP) and will be discussed later in this paper.
There is no tactic or protocol that can 100% remove the risk and the threat of violence from everyday life.
However, enhanced levels of awareness and preparation can greatly reduce risk of becoming a victim of violence.
Protective Awareness is a focused state of mind that involves the user analyzing the area in which he or she is located and the individuals occupying the subject area.
The user scans for suspicious individuals and actions; this tactic can deprive an adversary of the element of surprise while giving the user an opportunity to execute a countermeasure.
The user then formulates the necessary countermeasures to elevate their level of personal security/safety.
Protective Awareness consists of four foundational components, they are:
Knowledge of the 3 areas of interaction – the average person generally lives their life within one of three areas of interaction.
These areas are:
- Home – their place of residence
- Work- their place of employment
- Individual Specific- area specific to the individual (i.e. their school, their gym, their favorite venues and all areas outside of home and work) frequently spends time.

The user needs to know these areas and what constitutes safe normal behavior verses suspicious and threatening behavior.
These threatening behaviors are anomalies.
Rapid development of a security baseline
- The user needs to develop the ability to quickly establish security baselines that identify anomalies (signs, actions, cues of potential danger or threat) for the general 3 areas of interaction.
- Anomalies as they relate to physical security are generally caused by specific human action (the will to act, the means to act and the opportunity to act).
- The ability to detect anomalies allows the user to stay a step ahead of an adversary and remove themselves from danger prior to a crisis.
- This deprives the adversary the opportunity to act.
Define 3 zones of personal security
- The Protective Awareness user defines 3 concentrate zones around their person.
- The user first must assume the role as the asset under protection located in the center of the hot zone, which is encircled by the warm zone and the cold zone, the outermost zone that encircles both the warm and hot zone.
- This concept is borrowed from the physical security tactics of 3 Zone Security.
- This method provides the user with 3 layers of protection that must be penetrated by an adversary before they can harm the asset.
4 Categories of Countermeasures (aka The 4 Ds) as they relate to you the asset
- Deter
- To make a potential adversary decide not to attack you.
- This is due to your presence displayed through your awareness and confidence shown.
- You will show yourself to be too hard of a target.
- This will cause the attacker to find another victim.
- Detect
- This relates to your ability to scan 3 zones of security to detect potential threats and formulate possible countermeasures if needed.
- Delay
- To make an attacker hesitate prior to engaging giving you the user the opportunity to escape, call for assistance or execute a direct countermeasure.
- Strong verbal commands draw the attention of bystanders and let the adversary know you are alert and aware of their harmful intentions.
- Commands such as, “Back up!” “What are you doing?” “Help, move away from me!”
- Deny
- Relates to all countermeasure options to either avoid/elude the threat or to engage and overwhelm the threat to restore your original level of safety prior to the incident.

When the average person thinks about personal protection they often look at it as a single unit.
Many times it can boil down to the individual assuming their current state and location as safe because they are not engaged in conflict or a dangerous situation.
This can often lead to a person’s Protective Awareness being restricted to one area. This results in a false sense of security.
While this occurs a nearby threat goes unnoticed as it creeps closer.
This is the result of the individual mentally securing one immediate zone for personal observation prior to a crisis.
The 3 Zone Security Plan (3 ZSP) is used to provide physical security for a variety of locations such as houses of worship, educational facilities, corporate sites, etc.
The basic plan involves security planners confirming a given threat/hazard then conducting a vulnerability study of the subject location and finally generating a site-specific plan.
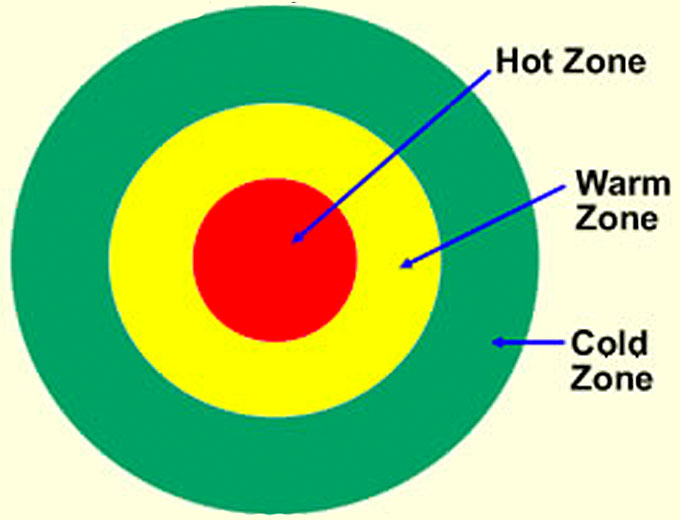
This plan divides the site into three concentric zones labeled cold, warm and hot.
The cold zone is the outer most zone that encircles the warm zone which in turn encircles the hot zone. The hot zone is final layer of protection for the asset under protection.
Each zone is protected by countermeasures and protocols that guard the subject asset, therefore the adversary must defeat 3 layers of protection.
The selected countermeasures and protocols seek to deter, detect, delay and deny an adversary the will to act, the means to act and the opportunity to act against the asset.
The purpose of this paper is to borrow certain methodologies from 3 ZSP and apply them to personal protection for an individual; this will make the user the asset protected by 3 security layers.

The underlying goal of this application is to broaden the users Protective Awareness resulting in greater security through the reduction of threats and risks.
The 3 zones of this plan as they apply to individual protection are as follows:
-
Cold Zone
- Is the area located immediately outside of the warm zone and extends as far as you can see.
- This is the zone that is often neglected during heightened states of awareness.
- In these times the average person usually focuses on warm and hot zone.
- An example of this can involve the user walking down a street, where at the end of the street there are police vehicles with their lights flashing.
- Then there is an explosion and small arms fire.
- The user then moves away from the threat as opposed to continuing closer and becoming a victim.
- The subject incident has occurred in the user’s cold zone.
-
Warm Zone
- Is the space between the user and the attacker, where the attacker can hit, kick or grab the user by taking 1 to 2 steps toward their person.
- This space is commonly referred to as the reaction zone.
- An example of this can involve a user engaged in a heated conversation with another individual who approximately 6 to 8 feet away inside the user’s warm zone.
- The user takes a step back and lowers the tone of his voice to deescalate the encounter while scanning the actions of the other person.
-
Hot Zone
- This is the space between the user and the attacker where the attacker can hit, kick or grab the user without taking a step toward their person.
- This zone is the easiest to focus on during states of heightened awareness and is also known as the area of personal space.
- An example of this can involve a user in an elevator that is full of people.
- Multiple people in the elevator are in the user’s hot zone.
- At this point the user raises his or her level of Protective Awareness and monitors the surrounding individuals for threatening behavior.
The 3 ZSP user must continually attempt to assess all three zones in times of non-crisis.
First, the user must know the three zones as they relate to their role as the asset; secondly, as the subject zones relate to others and a potential adversaries prior to and during a crisis.

The first and most critically skill the user must develop is how to generate a security baseline for the various environments they interact in, these environments are home, work and individual specific (areas and venues specific to you, i.e. your gym, your favorite hang out, park etc.).
This baseline establishes the guidelines the user will utilize to determine what are normal/safe activities for a given location.
By understanding what is normal and safe you will be able to detect anomalies (the activities that are out of place and potentially hazardous/threatening).
Summarized below are countermeasures the 3 ZSP user can deploy in the 3 zones to enhance their personal protective status.
These tactics and protocols should include but not be limited to:
- Regularly assess your own mental, physical and spiritual fitness (review your strengths and weaknesses) Know where you are most vulnerable.
- Regardless of the task assess your abilities to succeed “are you good to go?”
- Realize we are all creatures of habit change up your schedule and routes between your areas of interaction.
- Know where you are physically located at all times and be conscious of those around you.
- Verify the status of your cell phone reception and battery strength regularly.
- Have direct numbers of local fire, police and emergency services saved in your phone incase the regional 911 system is disabled.
- When driving regularly observe if the same vehicle is consistently behind you. If so make a series of right hand turns into well lighted and populated locations.
- If the vehicle is still behind you contact 911 or drive to the nearest Police Station.
- When entering a venue determine a second means of ingress/egress.
- Studies have determined that during an emergency people will usually attempt to evacuate a location by using the same route they entered the venue.
- By having established a second means of ingress and egress can avoid getting caught in the bottleneck generated by individuals escaping during an emergency.
- Always attempt to maintain space to maneuver when in a crowd and avoid being boxed in by others.
- When inside of a building make a mental note of areas of cover and concealment if an emergency requires you to shield yourself (i.e. vending machines, kiosks, concrete structures, dumpsters, automobiles, etc. will provide you some form of shielding from gun fire and secondary fragmentation generated by an explosion)
- Identify impromptu items that can be utilized as weapons against an adversary in a life or death situation.
- These include but are not limited to fire extinguishers, ink pens, paperweight, garbage cans, knives, forks, glass bottles, coffee pots, chairs etc.
- Create a “GO Bag” for your vehicle that includes but is not limited to: a blanket, flashlight with batteries kept separate, liter of water, first aid kit, disposable lighter, rain gear, multi-tool, 5-10 energy bars and an envelope of 50 to 100 dollars cash in dominations from singles to twenty dollar bills.
- Identify the locations of fire extinguishers, alarms systems, emergency lighting and fire doors.
- Identify the presence of wall mounted first aid kits and AED units.
- Receive basic first aid training.
- Receive basic self defensive training for realistic threats (Note: basic training in self defense will teach you how to repel and escape an attacker and stress survival/ self protection for you and loved ones. (The core goal of such training is not to win a contest but survival and the restoration of the level of safety you had prior to an attack)
- Train your Personal Awareness Skills- this requires an improvement of mental focus to assess the people, activities and environments for the enhancement of your safety levels.
- Regularly mentally wet test (i.e. virtually test various scenarios ) your tactical responses to a dangerous/hazardous situation at home, work and individual specific venues.
- Ask yourself, if this were to happen I would do this to protect myself and loved ones.
- Ask yourself do I have the will to act, the means to act and is there opportunity for me to act.

Security is an imperfect art; even on the most perfect day it cannot remove all aspects of danger or risk from an environment, especially during a crisis.
This is mainly due to the fact that security plans, strategies and tactics are all generated by human beings and all humans are flawed.
There is no tactic or protocol that can 100% remove all the risk and the threat of violence from everyday life.
However, the use of Protective Awareness and 3 ZSP modified for the individual user can greatly reduce an individual’s chances of becoming a victim of violence.
Effective countermeasures deployed by well trained individuals lay the foundation to limit the advantages of the adversary by removing his or her opportunity to execute their plans.
Through sound preparation confidence is acquired to execute.
The world today is and will remain an extremely dangerous and unpredictable place even on the of best days.
About the Authors:

Stanley I. White is currently the Counterintelligence Advisor for the IACSP as well as a private sector Safety Officer. Mr. White served as a Defensive Tactics Instructor at the Stamler Police Academy in Northern New Jersey for 16 years where trained personnel from numerous local, state and federal law enforcement agencies.
He also holds certifications as a Protection Specialist, Plainclothes Security Agent, Anti-Terrorism and Behavior Detection Officer. He is also an internationally published author on the topics of personal security and counter terrorism.
Mr. White is also the Private Officer International “Distinguished Service Award” recipient for 2018 and an American Security Today “Excellence in Homeland Security ” 2018 Platinum Award Winner. He can be reached for comment at swhite@atix.riss.net.
Ewart Williams is currently an Adjunct Professor in the Professional Security Studies Department at New Jersey City University.
Mr. Williams teaches/taught the following courses; Current Security Problems, Seminar on National Security, Domestic Terrorism, Introduction to Intelligence, Computer Security and Computer Forensics. Mr. Williams can be reached at Professor.E.Williams@gmail.com.
Stanley I. White Honored in the 2018 ‘ASTORS’ Homeland Security Awards Program
Stanley I. White
-
‘Excellence in Homeland Security’
-
Counterintelligence Advisor, the International Association for Counterrorism & Security Professionals (IACSP)
The Annual ‘ASTORS’ Awards Program is specifically designed to honor distinguished government and vendor solutions that deliver enhanced value, benefit and intelligence to end users in a variety of government, homeland security and public safety vertical markets.

The 2018 ‘ASTORS’ Awards Program drew an overwhelming response from industry leaders with a record high number of corporate and government nominations received, as well as record breaking ‘ASTORS’ Presentation Luncheon Attendees, with top firms trying to register for the exclusive high – end luncheon and networking opportunity – right up to the event kickoff on Wednesday afternoon, at the ISC East registration!
Over 130 distinguished guests representing National, State and Local Governments, and Industry Leading Corporate Firms, gathered from across North America, Europe and the Middle East to be honored among their peers in their respective fields which included:
- The Department of Homeland Security
- The Federal Protective Service (FPS)
- Argonne National Laboratory
- The Department of Homeland Security
- The Department of Justice
- The Security Exchange Commission Office of Personnel Management
- U.S. Customs and Border Protection
- Viasat, Hanwha Techwin, Lenel, Konica Minolta Business Solutions, Verint, Canon U.S.A., BriefCam, Pivot3, Milestone Systems, Allied Universal, Ameristar Perimeter Security and More!
The Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program highlighting the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition, and keep our Nation safe – one facility, street, and city at a time.
The 2019 ‘ASTORS’ Homeland Security Awards Program is Proudly Sponsored by ATI Systems, Attivo Networks, Automatic Systems, and Desktop Alert.
Nominations are now being accepted for the 2019 ‘ASTORS’ Homeland Security Awards at https://americansecuritytoday.com/ast-awards/.
Comprehensive List of Categories Include:
| Access Control/ Identification | Personal/Protective Equipment | Law Enforcement Counter Terrorism |
| Perimeter Barrier/ Deterrent System | Interagency Interdiction Operation | Cloud Computing/Storage Solution |
| Facial/IRIS Recognition | Body Worn Video Product | Cyber Security |
| Video Surveillance/VMS | Mobile Technology | Anti-Malware |
| Audio Analytics | Disaster Preparedness | ID Management |
| Thermal/Infrared Camera | Mass Notification System | Fire & Safety |
| Metal/Weapon Detection | Rescue Operations | Critical Infrastructure |
| License Plate Recognition | Detection Products | And Many Others! |
Don’t see a Direct Hit for your Product, Agency or Organization?
Submit your category recommendation for consideration to Michael Madsen, AST Publisher at: mmadsen@americansecuritytoday.com.
2018 Champions Edition
 See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
Enter Early to Maximize Media Coverage of your Products and Services at Kickoff, and Get the Recognition Your Organization Deserves!
And be sure to Register Early for the 2019 ‘ASTORS’ Awards Presentation Luncheon at ISC East 2019 to ensure your place at this limited- space event!

2018 ‘ASTORS’ Homeland Security Awards Luncheon at ISC East