By Jim Hansen, Vice President of Products & Security, SolarWinds
The Department of Defense is going on the offense.
The DoD Cybersecurity Discipline Implementation Plan outlines several key “Lines of Effort” to strengthen government agencies’ security postures.
Those four Lines—strong authentication, device hardening, reduce attack surface, and alignment to cybersecurity/computer network defense service providers—can be used collectively to blunt adversaries’ efforts and reduce external attack vectors.
 Since the plan was unveiled in 2015, attacks have become more prevalent and sophisticated.
Since the plan was unveiled in 2015, attacks have become more prevalent and sophisticated.
Over the past couple of years, we’ve seen cybersecurity incidents affecting the United States Navy, the Internal Revenue Service, the Office of Personnel Management, the Securities and Exchange Commission, and more.
What tools and strategies will IT managers need to implement the tasks outlined in the Lines of Effort?
Let’s look at each Line to see what administrators can do to address the DoD’s requirements.
Strong authentication
According to the plan, “(r)educing anonymity as well as enforcing authenticity and accountability for actions on DoD information networks improves the security posture of the DoD.”
Administrators are advised to focus primarily on protecting web servers and web applications through public key infrastructure (PKI) user authentication.
Accomplishing this requires keeping lists of privileged and non-privileged users up-to-date and using PKI to deactivate or delete accounts that are no longer relevant or in use.
Each account must meet a level of access required for users to do their jobs; those that do not need access to a particular dataset, for example, should not be granted permission to retrieve those files.
Maintaining these lists can be quite challenging given employee turnover and changing responsibilities, but it is a critical factor in ensuring strong user authentication.
Device hardening
Administrators must map each device on their networks to a secure baseline configuration. Network visibility and IP address management software tools should be used as a starting point.
These tools allow administrators to map, profile, and monitor the devices running on their networks and IP address usage.
It’s important to have a unified view of all network connections, applications, dependency relationships, and more, so administrators can easily identify and isolate issues as they arise.
(Get a quick overview of SolarWinds® IP Address Manager (IPAM) and learn why automated and consolidated DHCP/DNS and IP address management is a must-have in today’s dynamic networks. SolarWinds IPAM provides centralized management, monitoring, alerting, and reporting on your entire IP infrastructure, all from an intuitive web console. It’s simplified IP space management in one easy-to-use solution. Courtesy of SolarWinds and YouTube.)
Information assurance teams should then perform regular scans to continually validate that configuration and ensure it is operating properly.
Vulnerability assessment scans check for necessary patches and other potential holes that could compromise security.
Any anomalies should be compiled and tracked.
This information can be used to develop a plan of action and milestones detailing when the anomalies were discovered, their severity, and recommendations on how to mitigate the problems.
The issues with the highest severity rating should be addressed immediately.
(Hear from a SolarWinds customer explains how IPAM is used to identify IP Address issues quickly cutting down on time to find root cause of the problem. Courtesy of SolarWinds and YouTube. Posted on Dec 26, 2018.)
Reduce attack surface
The third Line of Effort states, “Commanders and Supervisors will mitigate the threat of Internet-based adversaries by eliminating Internet-facing servers from the DoDIN (Department of Defense Information Network) core, ensuring Internet-facing servers in DoD demilitarized zones (DMZ) are operationally required, and removing trust relationships with external authentication services.”
To comply with these directives, managers who oversee user access to applications or systems via the commercial internet should migrate those services away from the DoDIN core and into a computing environment that requires less security.
This Line of Effort also notes the importance of device monitoring: “Commanders and Supervisors must ensure only authorized devices are able to access the DoD infrastructure physically and locally.”
Administrators should implement user device tracking to monitor for rogue or unauthorized devices.
(User Device Tracker (UDT) from Award-Winning SolarWinds, delivers automated endpoint tracking to help you quickly locate users or devices, as well as alert you when rogue devices enter the network. It also provides valuable switch port management capabilities to help you identify available ports, capacity plan your network, and manage port access. Courtesy of SolarWinds and YouTube.)
Alignment to cybersecurity/computer network defense service providers
This final Line calls for “monitoring activity at the perimeter, on the DoDIN, and on all DoD information networks (which) ensures rapid identification and response to potential intrusions.”
Here, a Security Information and Event Management (SIEM) system is essential.
With a SIEM, administrators can monitor logs, events, and a host of other factors that can have direct impact on network security.
(SolarWinds Log & Event Manager (LEM) delivers powerful Security Information and Event Management (SIEM) capabilities in a highly affordable, easy-to-deploy virtual appliance. It combines real-time log analysis, event correlation and a groundbreaking approach to IT search to deliver the visibility, security and control you need to overcome everyday IT challenges. SIEM software has never been easier to use or more affordable. Courtesy of SolarWinds and YouTube.)
By combining SIEM with network traffic analysis and server monitoring software, administrators can gain more complete views of everything happening on their networks—both inside and on the perimeter.
Though the cyberthreat landscape has evolved significantly over the past couple of years, so have the tools and strategies agencies can use to combat internet adversaries.
Today, administrators have a number of weapons to support and enforce their efforts around the DoD’s Cybersecurity Discipline Implementation Plan.
Deploying them effectively can help agencies gain considerable advantages over their adversaries.
(This SolarWinds customer shares how IPAM allows him to monitor IP addresses in his network and improve monitoring of those addresses. Courtesy of SolarWinds and YouTube. Posted on Dec 26, 2018.)
Author: Jim Hansen is VP of Products, Security, SolarWinds
SolarWinds Achieves Hat Trick in the 2018 ‘ASTORS’ Homeland Security Awards Program
SolarWinds
-
Best Network Security Solution
-
SolarWinds
Network Configuration Manager
SolarWinds® Network Configuration Manager (NCM), the Platinum Award Winner for Best Network Security Solution Three Years Running in the Annual ‘ASTORS’ Homeland Security Awards Program, provides automated continuous monitoring and alerts for network configuration changes, potential policy violations, and remediation of harmful security violations.
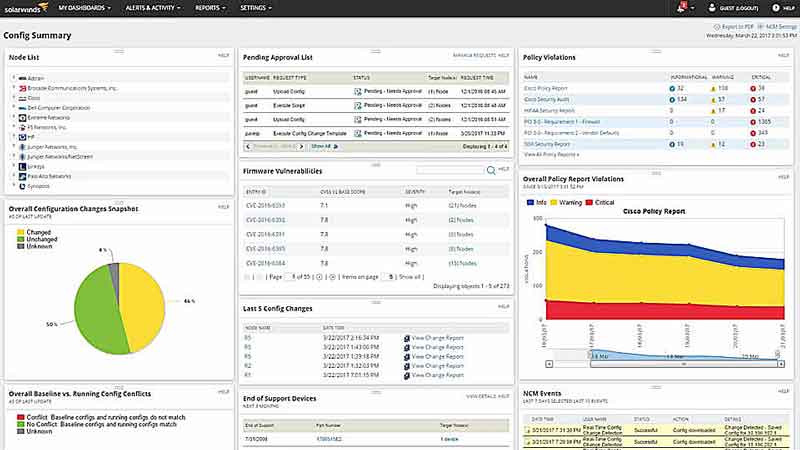
SolarWinds NCM also offers compliance auditing to help ensure that devices are configured correctly; automated change control workflow and bulk configuration updates; and automatic vulnerability assessments allow teams to identify and fix vulnerabilities – and all in a single solution.
SolarWinds NCM offers several unique and powerful features to help agency IT professionals protect against vulnerabilities and prevent unauthorized network configuration changes and uses Cisco® IOS® and ASA vulnerability scanning and NIST FISMA, DISA STIGs, and DSS PCI compliance assessments to improve network security.
Government IT compliance requirements are complex and ever-changing, and agencies must respond to constant data calls for compliance reporting.
SolarWinds NCM is built for IT environments of all sizes, can easily scale to meet growing infrastructure needs, and is used by nearly every US federal civilian agency, DoD branch, and intelligence agency, available on the US General Services Administration (GSA) Schedule, Department of Defense ESI, and other contract vehicles.
SolarWinds
-
Best Security Incident & Event Mgmt Solution (SIEM)
-
SolarWinds Log & Event Manager
-
*SolarWinds was also recognized in the 2016 and 2017 ‘ASTORS’ Platinum Award Programs
SolarWinds® Log & Event Manager (LEM) is a powerful, comprehensive SIEM solution that delivers dynamic, real-time log collection and analysis for immediate and actionable threat intelligence.
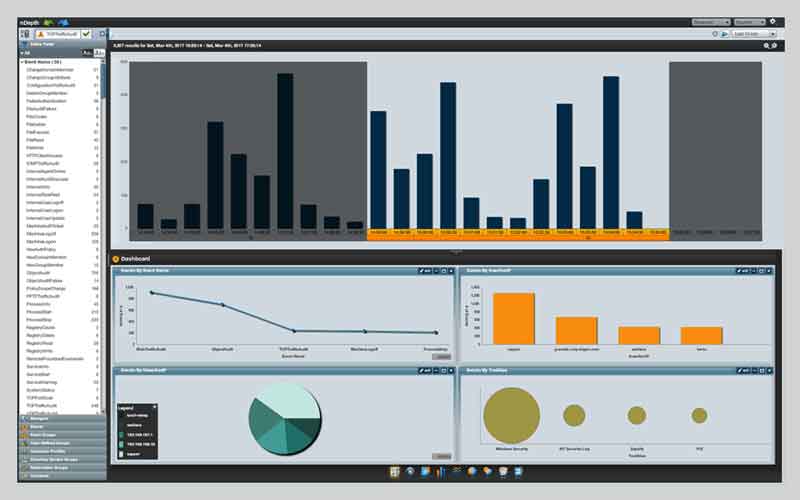
SolarWinds LEM can capture and analyze log data in real-time from multiple sources and specific incidents, allowing users to quickly identify and remediate threats, uncover policy violations, and resolve vital network issues.
Response time is a critical factor and SolarWinds LEM has unique built-in Active Responses that allow users to take automatic actions for fast, hands-free threat mitigation. Users can quickly shut down breached systems, block IP addresses, kill unexpected processes, and disable user accounts.
SolarWinds LEM features other innovations not seen in traditional SIEM solutions, such as in-memory correlation for immediate threat detection and remediation; USB Defender® technology to help identify rogue devices and enforce USB policies; and unique IT search capabilities for better remediation and audit reporting.
SolarWinds LEM includes support for single sign-on and improved management.
When responding to a threat, users need intuitive interfaces and features, without sacrificing power or capabilities—the hallmarks of LEM.
The SolarWinds LEM solution includes an easy-to-use, point-and-click interface and data visualization tools to quickly search log data, perform event forensics, and identify the cause of security incidents or network problems.
2018 ‘ASTORS’ Homeland Security Awards Program
The Annual ‘ASTORS’ Awards Program is specifically designed to honor distinguished government and vendor solutions that deliver enhanced value, benefit and intelligence to end users in a variety of government, homeland security and public safety vertical markets.

The 2018 ‘ASTORS’ Awards Program drew an overwhelming response from industry leaders with a record high number of corporate and government nominations received, as well as record breaking ‘ASTORS’ Presentation Luncheon Attendees, with top firms trying to register for the exclusive high – end luncheon and networking opportunity – right up to the event kickoff on Wednesday afternoon, at the ISC East registration!
Over 130 distinguished guests representing National, State and Local Governments, and Industry Leading Corporate Firms, gathered from across North America, Europe and the Middle East to be honored among their peers in their respective fields which included:
- The Department of Homeland Security
- The Federal Protective Service (FPS)
- Argonne National Laboratory
- The Department of Homeland Security
- The Department of Justice
- The Security Exchange Commission Office of Personnel Management
- U.S. Customs and Border Protection
- Viasat, Hanwha Techwin, Lenel, Konica Minolta Business Solutions, Verint, Canon U.S.A., BriefCam, Pivot3, Milestone Systems, Allied Universal, Ameristar Perimeter Security and More!
The Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program highlighting the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition, and keep our Nation safe – one facility, street, and city at a time.
The 2018 ‘ASTORS’ Homeland Security Awards Program was Proudly Sponsored by ATI Systems, Attivo Networks, Automatic Systems, Desktop Alert, and Royal Holdings Technologies.
2018 Champions Edition
 See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
Nominations for the AST 2019 ‘ASTORS’ Homeland Security Awards Program will officially open as of January 1st, 2019 at americansecuritytoday.com.
Enter Early to Maximize Media Coverage of your Products and Services at Kickoff, and Get the Recognition Your Organization Deserves!
And be sure to Register Early for the 2019 ‘ASTORS’ Awards Presentation Luncheon at ISC East 2019 to ensure your place at this limited- space event!