Guest OpEd by Gilad David Maayan
Incident response (IR) is a set of practices and tooling used and created for the purpose of responding to cyber security incidents.
The incident response plan (IRP) is a detailed plan that outlines all of the processes, tools, and roles involved in IR events.
In this article, you will learn about the four most critical phases every IRP should contain, including best practices for building your own IRP.
What Is an Incident Response Plan?
An incident response plan (IRP) is a plan that details how an organization should respond to a cyberattack.
It includes processes and tools for identifying attacks, prioritizing and defining responses, mitigating damage, and recovering from an attack.
An effective IRP focuses on responding to incidents or attacks as quickly and efficiently as possible.
Any good incident response plan should reduce:
-
Number of impacted users and systems
-
Length of attacks
-
Amount of damage caused
-
Recovery and restoration times
-
Mitigation and recovery costs
-
Organizational liability and damage caused to third-parties
Incident Response Phases
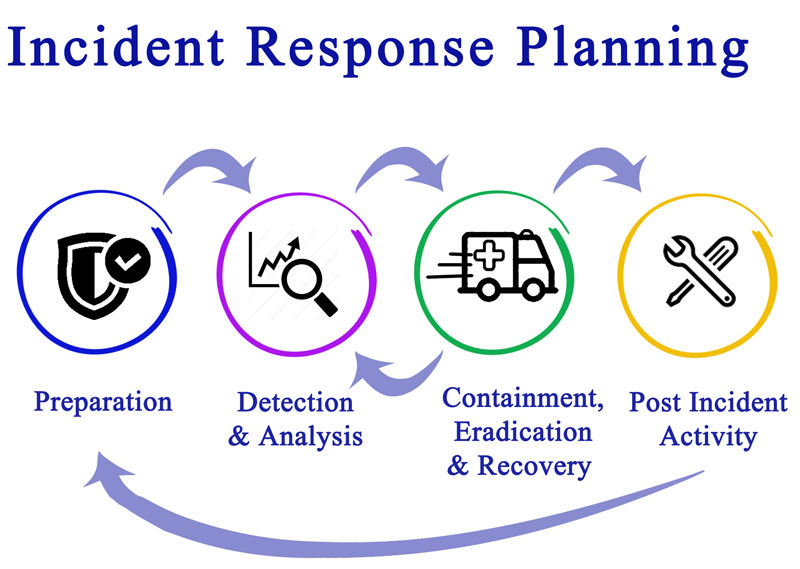
When creating an incident response plan, there are four phases you need to address.
These phases operate in a cycle, with the last providing feedback for the first.
1. Preparation
The preparation phase is when you collect information about your systems and vulnerabilities and take action to prevent incidents.
The more thoroughly you execute this phase, the lower your overall risk.
During this phase, you should inventory your assets, including networks, endpoints, servers, and data.
Evaluate the priority of your assets and understand how assets are currently protected or vulnerable.
For those assets that are vulnerable, you need to set up protective measures and ensure that you have adequate monitoring.
Once your inventory is complete, you need to determine how incidents are detected, analyzed, and handled.
During your first preparation phase, you should develop any policies that will be applied during an incident response event.
This includes assigning roles and responsibilities to team members.
2. Detection and Analysis
Detection is the identification of suspicious activity.
This identification can be based on monitoring and security tools, insider information, or publicly available threat information. ‘
Part of detection is collecting as much data as possible about the suspicious activity so that it can be analyzed.
Once enough data is collected, you can analyze the data to identify whether a suspected threat is real and if so what kind of threat it is.
This is often done by comparing the suspected activity against system baselines of expected behavior.
The results of your analysis define how you respond in the next phase.
3. Containment, Eradication, and Recovery
Containment aims to stop an attack before it spreads or creates more damage.
Eradication is the removal of any attackers or malware from your systems.
Recovery is the restoration of systems and data.
These three steps may be fluid or overlap, depending on the type of incident you’re experiencing.
During this phase, it is important to preserve any information you uncover about the attack.
This information can help you strengthen your systems after the incident is over.
Any evidence you collect is also needed for compliance or legal prosecutions.
4. Post-Incident Activity
The final phase is designed to help you review your incident response processes and improve your future protections and responses.
It involves your entire team meeting and providing feedback on what worked, what didn’t, and offering recommendations for how to improve the process.
A structured outline including the following questions is helpful:
-
What happened and when?
-
How effective was the response and how well was the plan followed?
-
What information would have made the response easier?
-
Was anything done that impeded response or interfered with recovery?
-
What improvements could be made?
-
How can information from this response be applied to future protections or responses?
-
Are any additional tools or procedures needed to ensure better protection?
Best Practices for Building an Incident Response Plan
Once you’re ready to build your IRP, there are a few best practices you should follow to ensure success.
Create a simple, well-defined process
An IRP needs to be both detailed and well defined to be effective.
Procedures should be clear and comprehensive and should be as accessible as possible.
You need your team members to be able to quickly understand any procedures you create and take action with minimal guidance or oversight.
Create a communication strategy
Incident responses are hectic and miscommunication or lack of communication can happen easily.
To avoid this, you should define a clear communication strategy that outlines communication channels and responsibilities.
This strategy should include what information is passed, who it is passed to, and when.
It should include operations, senior management, stakeholders, authorities, and customers.
Put your incident response plan to the test
 Once your plan is created, make sure to test it before a real incident occurs.
Once your plan is created, make sure to test it before a real incident occurs.
You can run practice drills or use training tools designed to be vulnerable to accomplish this.
These drills have the added benefit of instilling confidence in your team and can reduce stress during a response.
You should also test any tools you are or are planning to use to verify your configurations are correct.
Use a centralized approach
Centralizing your control and monitoring dashboards helps streamline your response, improves efficiency, and reduces the chance that threats are overlooked.
It can also help you more effectively analyze data since all monitoring sources are aggregated.
The easiest way to achieve centralization is through the use of tools designed for detection and response.
These tools can help you automate some of the response processes and often enable you to integrate external threat data in real time.
Conclusion
A well-defined IRP should include detailed information about what should happen during each response eventuality.
The four crucial phases of an IRP are preparation, detection and analysis, containment and eradication, and post-incident activity.
Anything else should be added according to the needs of the organization.
To help a wide range of professions and skillsets to make the most of the IRP, keep your documentation simple and concise.
Create a communication strategy to clarify roles and responsibilities during IPR events.
Be sure to test your plan, to ensure your plan and your personnel are kept abreast of the latest cyber security standards.
Knowledge can be the difference between a secured operation and a breach.

About the Author
Gilad David Maayan is a technology writer who has worked with over 150 technology companies including SAP, Samsung NEXT, NetApp and Imperva, producing technical and thought leadership content that elucidates technical solutions for developers and IT leadership.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos