
Cerebellum, by Veracity Industrial Networks has been nominated to compete in the 2018 ‘ASTORS’ Homeland Security Awards for Cyber Critical Infrastructure Solution.
Veracity, founded and led by a veteran team with deep cybersecurity experience is changing the paradigm of Industrial Operational Technology (OT) Networks with a next generation platform that provides enterprise class security through a centralized command center for industrial control systems (ICS).
What is Veracity Cerebellum:
In the human brain, the cerebellum receives information from the sensory systems, the spinal cord, and other parts of the brain and then regulates motor movements.

The cerebellum coordinates voluntary movements, resulting in smooth and balanced muscular activity. It is also important for learning motor behaviors.
The Veracity “Cerebellum” platform is designed to serve a similar function for industrial networks.
Veracity’s Cerebellum provides a system level approach that responds to sensory data and orchestrates the pre-designed production process response.
Cerebellum is designed for operational and engineering efficiency; a logical workflow-based approach to network configuration, orchestration, security and resilience.
(Veracity is driving innovation and redefining what is possible with the future of industrial networking cybersecurity. In 79 seconds, find out who Veracity Industrial Networks is and what they do! Courtesy of Veracity Industrial Networks and YouTube)
What Does Veracity Cerebellum Offer:
-
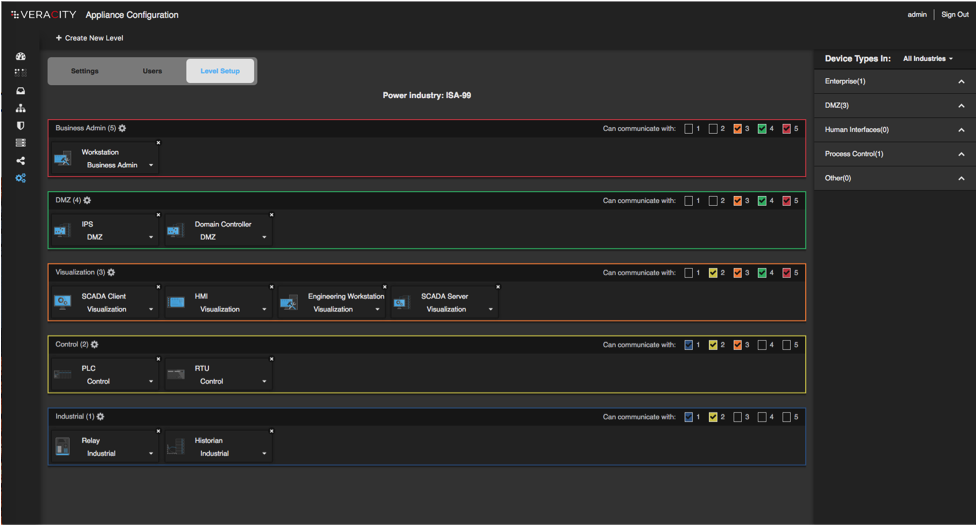
Security Level Model
- Cerebellum provides the first fully functional visual based security level model builder.
- The security level allows for a user to quickly build the Purdue Manufacturing Model, ISA-95, ISA-99, or even create a model from scratch.
- The user can quickly define the functional levels in their model and drag & drop device types from the industry library to their respective functional levels.
- Finally, the user can easily define rules for each level (e.g. communication between levels).
-
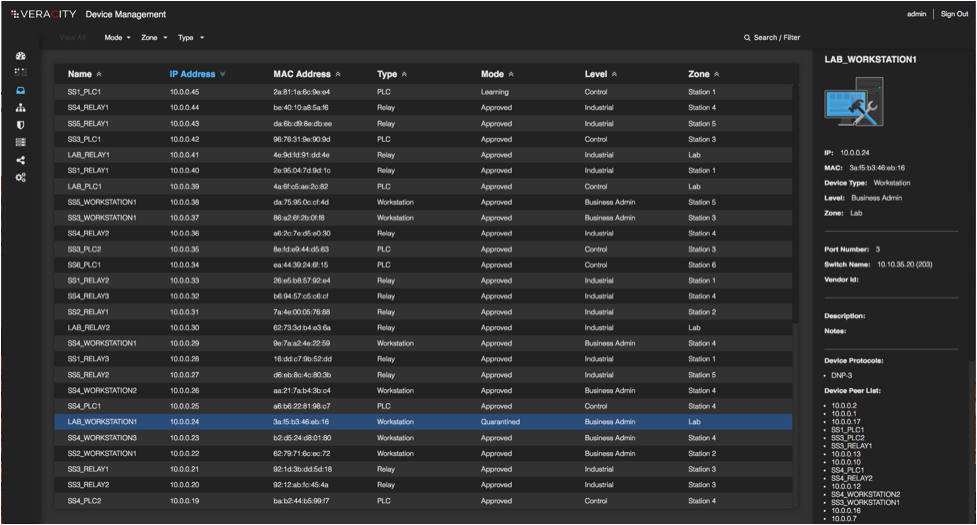
Authorize Networked Devices
- Cerebellum makes device management simple.
- With Veracity’s INDUSTRIAL SDN™, 100% of all devices connected to the network are identified.
- During the learning/identification mode, the system is also characterizing the network devices to classify the functional role and device type (e.g., PLC, RTU, SCADA Server, etc.).
- Device management provides information to the user to define whether a device should be authorized or not.
- The user can also decide to quarantine a device (e.g., an unauthorized integrator laptop).
-
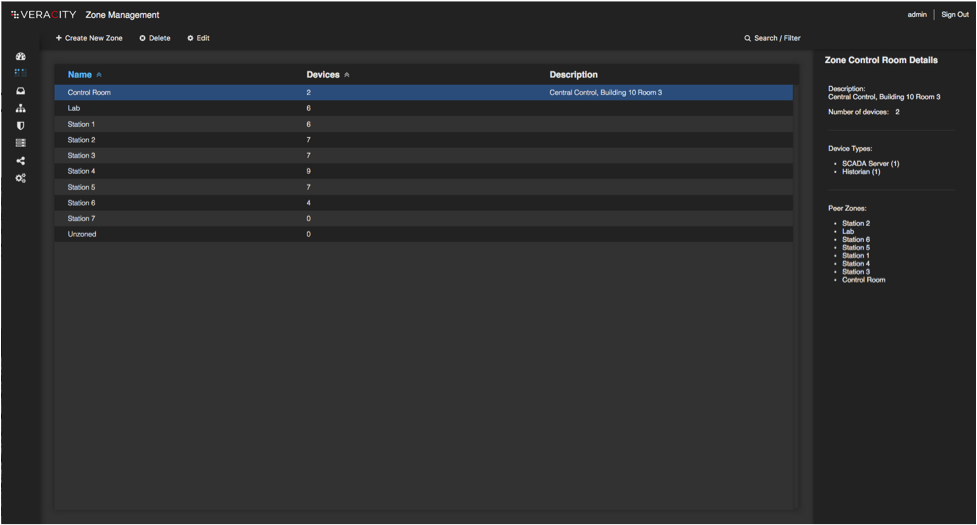
Security Zone Management
- Cerebellum provides an innovative approach to network segmentation via the creation of security zones.
- This workflow-based approach allows the user to easily create security zones or logical groups and assign devices to those groups.
- This can be accomplished in multiple ways from Cerebellum’s single pane of glass – by asset/network drag and drop or command line interface.
-
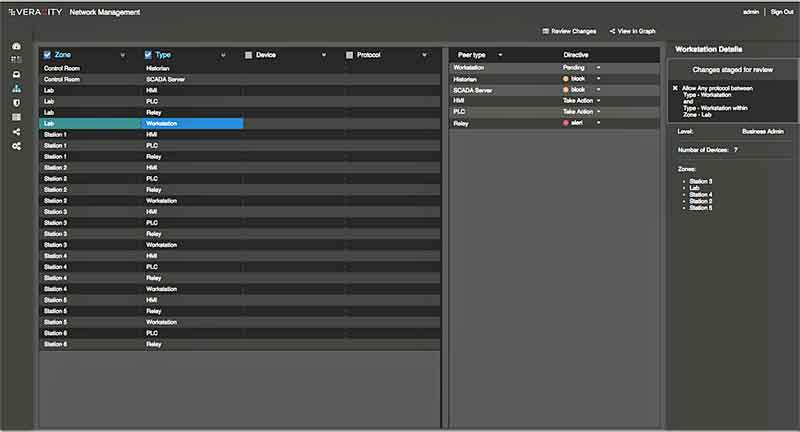
Authorized Communication
- Cerebellum provides an innovative approach to traffic engineering which the abstracts complexity at scale while allowing fine-grained control.
- The user can manage traffic at a high level – e.g. what zone to zone communications are permitted – or via very granular rules such as “a specific PLC is allowed to communicate with a specific HMI over DNP-3.”
-
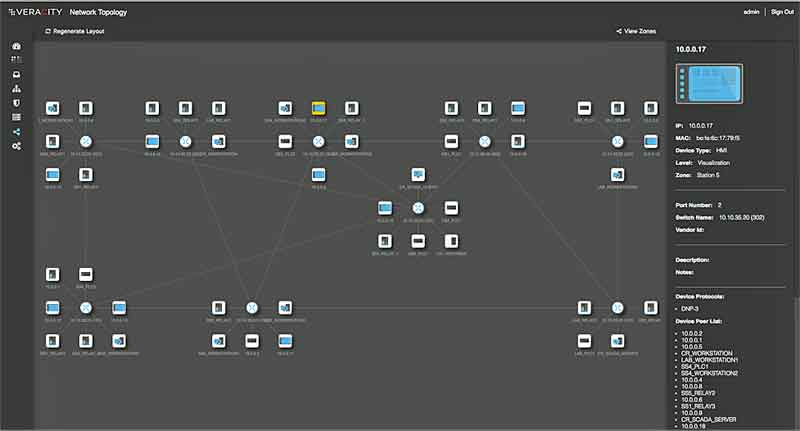
Visual Validation
- Where engineers are very comfortable working with spreadsheet-like interfaces for managing complex data, what is lacking is a visual representation.
- Visual validation is an important step to identify the rules that are being configured in a simplified and consumable manner.
- This enables the user to maximize their efficiency and accuracy.
-
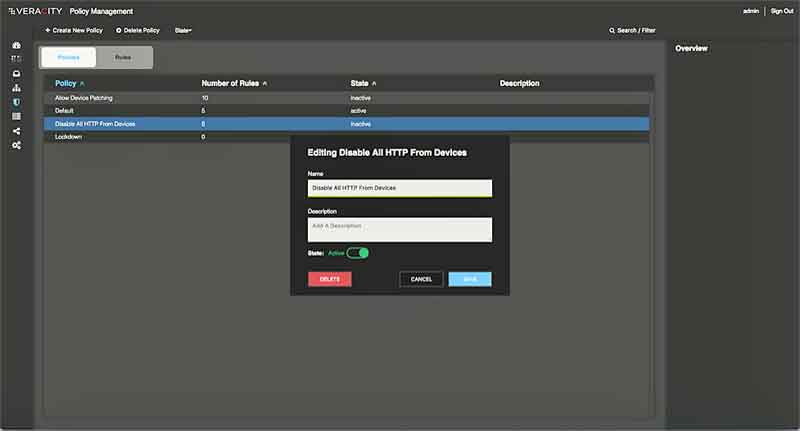
System Policy Management
- In addition to simplified traffic engineering via zones and device types, Cerebellum provides dynamic, API-based control by allowing configuration change sets to be grouped as policies.
- These policies can be enabled or disabled at any time, vastly simplifying operational workflows.
- For instance, during normal operation it may not be required to allow engineering workstations network access to control (e.g., PLCs) devices.
- The system will support both a default policy of denying that access alongside an operational policy of allowing that access, and switching between them can be done via a remote but authorized process driven by a change management workflow or via a few clicks in the user interface.
Veracity delivers a resilient, secure industrial network that provides an on premises, centralized configuration, control, and monitoring solution that tracks all connected devices and their communications.
The Veracity Cerebellum platform is an award-winning, secure-by-default network that moves beyond the detection and alerting of cyber events into a resilient network that reduces the attack surface by design.
The Veracity Industrial SDN network massively reduces the complexity of the network by repurposing the switch infrastructure to ensure communication between devices is determined by the system’s design.
Veracity provides an innovative and comprehensive platform for critical networks that enables your business mission.
(Learn More. Join Veracity for this informative webinar, featuring Mike Smith, former Senior Cyber Policy Advisor to the Assistant Secretary in the Office of Electricity Delivery and Energy Reliability at the U.S. Department of Energy to discuss malware used in the 2015 and 2016 cyber-attacks on the Ukrainian power grid, which is modular, reusable and poses a serious threat to our nation’s critical infrastructure. Courtesy of Veracity Industrial Networks and YouTube. Posted on Dec 27, 2017)
Veracity started its journey in April of 2015 and by the end of calendar year 2017 had accomplished a number of important milestones:
-
Completed a “Seed D” round of funding for the company, with strategic investors Microsemi Corporation and Schweitzer Engineering Labs.
-
Delivered product to the U. S. Department of Energy as part of the “Chess Master” project in July of 2017.
- This important project will build on the successful commercial release of utility rated software defined network (SDN) technology under the previous CEDS project, Watchdog, and produce a solution operators can use to quickly establish and apply network policies.

-
Added key members to the Veracity team, including Jay Williams, Executive Vice President of Revenue Generation.
- He was previously Vice President of Cyber National Industrial Cyber Security Business Development Manager for Siemens Industry and Blue Lang, Senior Product Manager, former Chief Architect and Engineering Leader for the SDN Enterprise Controller at Cisco Systems.

-
Established a thought leadership position within the industry.
- Veracity’s CEO Paul Myer and CTO Roger Hill have become sought after industry experts in the growing industrial cybersecurity space.
-
Acquired numerous accolades and awards including:
- “Best Industrial Cybersecurity Solution” in the 2017 GSN HSA Program in the Cybersecurity Products and Solutions category
- CSO Magazine’s “10 Emerging ICS and IIoT Cybersecurity Companies to Watch”
- IIOT World’s “Top ICS/SCADA Cybersecurity Startups to Watch”
- Cybersecurity Ventures’ “Cybersecurity 500” (#242)
- OCTANe 2017 High Tech Innovation Award Finalist
Veracity Industrial Networks Competes in 2018 ‘ASTORS’ Homeland Security Awards Program
AST focuses on Homeland Security and Public Safety Breaking News, the Newest Initiatives and Hottest Technologies in Physical & IT Security, essential to meeting today’s growing security challenges.
The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.’
As an ‘ASTORS’ competitor, Veracity Industrial Networks will be competing against the industry’s leading providers of Innovative Cyber Critical Infrastructure Solutions.
To Learn More about the ‘ASTORS’ Homeland Security Awards Program, see 2017 ‘ASTORS’ Homeland Security Award Winners Honored at ISC East.
Over 100 distinguished guests from National, State and Local Governments, and Industry Leading Corporate Executives from companies allied to Government, gathered from across North America and the Middle East to be honored from disciplines across the Security Industry in their respective fields which included representatives from:
 The Department of Homeland Security
The Department of Homeland Security- The Department of Justice
- The Security Exchange Commission
- State and Municipal Law Enforcement Agencies
- Leaders in Private Security



















