By Howard Dawson, Writer & Tech Enthusiast
Virtual Private Networks (VPN) are vital applications for those who want to keep their Web browsing data private.
They allow for safe surfing of the internet and to access materials that would normally be inaccessible due to one’s location.
They are popularly used with streaming sites, such as Netflix and Hulu, and are popular with those who need complex protection for monetary transactions including Cryptocurrency purchases.
(What is VPN? A virtual private network extends a private network across a public network, and enables users to send and receive data SECURELY across shared or public networks safely. Connecting at the coffee shop? Bus station? Airport? Hospital? Then you probably need a VPN. Courtesy of Modern Dad and YouTube.)
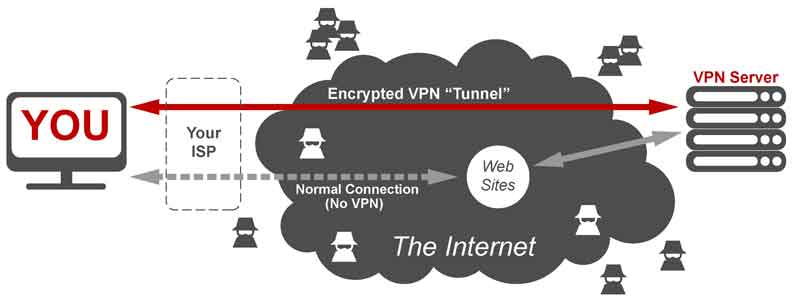
VPNs use VPN protocols to hide or randomize IP address, keep personal data inaccessible to Web entities, and protect data using sophisticated encryption methods.
So what are these VPN protocols and which are the most secure?
Point-to-Point Tunneling Protocol (PPTP)
PTP is the oldest VPN protocol. Microsoft first introduced it in the days of Windows 95 and dial-up networks.
It is perhaps the most commonly used protocol, but that does not mean it’s the best.
On the positive side, it is easy to set up, is one of the fastest protocols, and its clients are built into many platforms that access windows properties.
It can be used for Internet and Intranet (with a building or a business’s private network) connectivity.
As for negatives, there are many. PPTP is only as good as its built-in protections.
As with many Microsoft products, it has encountered many security issues over the years.
Additionally, as a Microsoft product, it is not known to what degree Microsoft and its corporate partners have access to data that flows through it.
It is widely known that the NSA has decrypted PPTP and actively monitors its traffic.
According to SurfShark, it is an old and vulnerable protocol that is best avoided.
Secure Socket Tunneling Protocol (SSTP)
SSTP is another Microsoft product. It was released as part of Windows Vista Service Pack 1.
It remains a proprietary product, which is easy to set up and use with Windows but is inaccessible to Apple products. SSTP also works well with Linux when properly configured, but it provides no support for the platform.
SSTP allows for a number of configurations including the secure AES encryption. This automatically makes it a better choice than PPTP.
However, like PPTP, it suffers from the same possibility of Microsoft back door gateways. Of course, this remains inferred and not in any way proven.
If you are a die-hard Windows user, SSTP is a viable option, but there are better and more secure choices available.
Layer 2 Tunneling Protocol (L2TP/IPsec)
L2TP is another VPN with a long history. Developed in the 1990s by Cisco and Microsoft, it is a tunneling protocol without encryption.
While this sounds like a recipe for disaster, L2TP is usually paired with a security protocol known as IPsec, which is the AES standard.
Although of the same age as PPTP, it does not suffer the same vulnerabilities.
L2TP is easy to set up and runs at respectable speeds for most applications. It is built into the operating systems of many computers and mobile devices, allowing for ease of integration.
L2TP does not match PPTP in this area, but the security more than makes up for the speed difference.
One of the main flaws of L2TP is that it uses UDP port 500. Simply put, it sticks out like a sore thumb and cannot be disguised.
It is easily found by security factors and it has a difficult time navigating good firewalls. Even worse, it can be outright blocked by some systems.
Although it can be configured to forward the port to get around firewalls, this is beyond the skill set of most casual users.
L2TP, when paired with IPSec, is a respectable choice for non-technical users, there are still better options.
Internet Key Exchange (IKEv2/IPsec)
The original version of IKE was released in the mid-2000s as a joint venture between Microsoft and Cisco.
IKEv2 is an updated version focused on the mobile market, with support for a wide range of technologies including Windows, Blackberry (for which it has native support), iOS, and most others.
Like L2TP it is a tunneling protocol often paired with IPSec to allow for improved security.
While IKEv2 is one of the fastest protocols and is very stable. However, it is less popular than one would think due to its narrow support options.
Again as a Microsoft product, one does not know if there are purposeful vulnerabilities backed into the technology.
IKEv2 serves best in mobile applications in 3G or 4G LTE as it can switch seamlessly between mobile and WiFi connections.
This keeps connections secure and viable no matter the environmental issues. If the majority of your VPN needs are mobile, you could do far worse than IKeV2.
OpenVPN
OpenVPN is one of the newest and safest protocols. Although it was originally developed in 2001 by James Yonan, the most recent stable release was in April 2018.
It is a true open source protocol, so it does not come with the same security questions attached to corporately developed VPNs.
OpenVPN runs on OpenSSL and TLS with a raft of other technologies providing support. It is highly configurable and can run on any port.
As an open source system, it does not have a native platform, allowing access to all platform clients. As long as a platform develops an OpenVPN client, it can use it, and at this point, all of the major players have.
With leading security, ease of access from almost every platform, and a highly configurable and flexible system, OpenVPN could position itself as the industry standard within a few years.
The only real hurdle is that it is not integrated into most computer and mobile systems, so there is a learning curve with installation and configuration.
OpenVPN is the best choice, as your VPN provider allows access to it. It can be a nightmare to set up manually.
In Summary
-
Do not use PPTP. Its speed does not make up for its many security vulnerabilities.
-
If you are a Windows user, SSTP is a viable option.
-
L2TP is a good system for a basic user. It has enough speed and security to keep everyone happy.
-
IKEv2is a fast and secure option if your VPN needs are for mobile devices.
-
OpenVPN is easily the best option as long as connection is available and it can be set up automatically.

















