The 2021 ‘ASTORS’ Homeland Security Awards Presentation Luncheon was an exclusive event featuring two hundred representatives of law enforcement, public safety, and top industry leaders who came together to honor the selfless service of those who stand on the front lines, and those who stand beside them – providing the capabilities and technologies to create a safer world for generations to come. (Continued)
SIMS Software

-
Best Security Workforce Management Platform
-
SIMS
-
SIMS Software is widely recognized as the industry leader in security information management systems, to the government and defense industries with a track record spanning nearly four decades.

-
SIMS flagship product, Security Information Management System (SIMS) manages visitors, classified contracts, classified information tracking, and control, as well as personnel security clearance processing and monitoring at all levels, including Top Secret and Sensitive Compartmented Information (SCI) requirements.
-
The company was founded by a Navy Veteran in 1983 and remains the pre-eminent industrial security information management tool for the Defense Industrial Base and extensive high-profile government agencies however, the relevance of the companies capabilities doesn’t end in the DoD world.
-
In today’s modern threatscape, holistic security goes beyond protecting the perimeter fence and preventing break-ins or triggering alarm bells, it’s about locking down the lifeblood of our organizations.
-
It is critical to know who controls and has access to highly sensitive data and where it resides, particularly during the COVID-19 era with a dispersed workforce in many cases working remotely.
-
As such, our security toolsets must evolve, as has SIMS. For example, Insider Threat has become a widely used buzzword, but how do you define what it means?
-
Being able to report, review, track trends over time and analyze individuals for questionable and repeated abnormal behavior patterns is paramount.
And it is just as important to be able to share that data across the proper functional representatives inside your organization that can roll up into a Dashboard to present statistics in real-time, all at your fingertips for proper investigation and decisioning.
-
SIMS provides all the features and functionality necessary to run a powerful, paperless industrial security program with a single system of record, so clients are able to escape the development costs and interoperability issues associated with in-house solutions.

-
*American Security Today (AST) is delighted to welcome New Premier Awards Sponsor SIMS Software to the 2021 ‘ASTORS’ Homeland Security Awards Program.
Singlewire Software (First of Four)

-
Best IT Disaster Preparedness & Recovery Solution
InformaCast Command Center
-
To help organizations prepare for and manage disasters, Singlewire Software has added InformaCast Command Center to its InformaCast Mobile and InformaCast Fusion offerings.
-
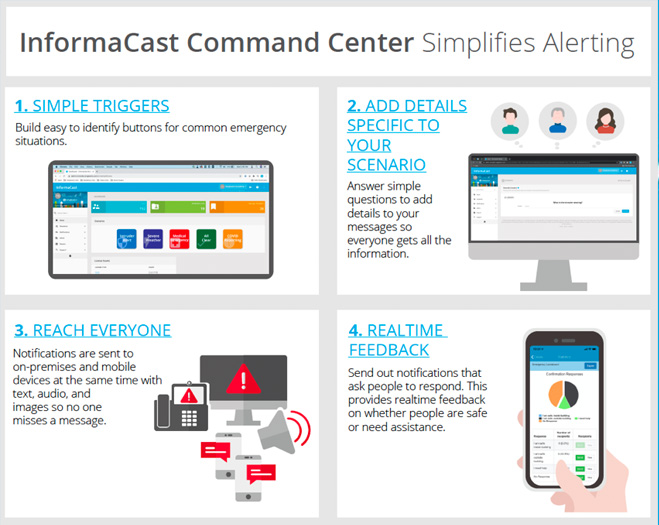
Command Center helps organizations prepare for disasters by giving them the opportunity to identify the disasters that will have the most impact on their operations, whether it be an active shooter, chemical spill, severe weather, medical emergency, or any other disaster they are likely to encounter.
-
Each identified event can be assigned a button with customizable text, colors, and graphics to make it as easy to identify as possible.
-
The buttons will appear in the InformaCast web console or within the InformaCast Mobile app so no matter where someone is they can trigger a notification the moment they see an incident occur.
(Quickly send notifications in the event of an emergency with InformaCast Command Center. Build icons on the homepage for crisis scenarios such as fires, severe weather, medical emergencies, active shooter, and more. Courtesy of Singlwire Software and YouTube.)
Singlewire Software (Second of Four)

-
Best Mass Notification Solution – Application
-
InformaCast Fusion with Zoom Phone
-
InformaCast Fusion with Zoom Phone from Singlewire Software gives the 1 million people utilizing Zoom Phone the ability to leverage the mass notification power of InformaCast Fusion for security and communication.

-
In an emergency, every moment matters, and organizations need communication systems that reach all their people quickly, and the faster a message goes out, the more time security personnel have to respond to and manage the situation at hand.
-
Using InformaCast Fusion, Zoom Phone users can now trigger mass notifications that reach all of their people.
-
InformaCast Fusion with Zoom Phone can be used to enhance security with emergency alerts in enterprise businesses, healthcare, manufacturing, K12, higher education, and other industries that need assistance reaching all of their people quickly during a crisis.
-
Organizations can use it to activate lockdowns, share details about approaching severe weather and send alerts about active shooter situations, as well as other emergency scenarios they are likely to face.
Singlewire Software (Third of Four)

-
Best Mobile Technology Solution
-
InformaCast Mobile
-
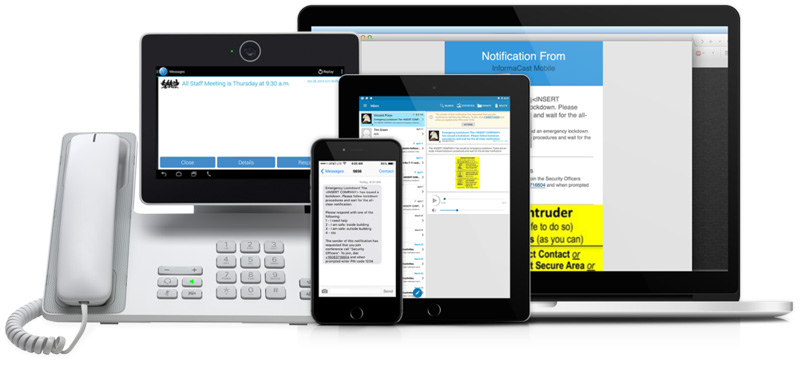
InformaCast Mobile is a cloud-based mobile app that offers organizations an easy way to reach all of their people on their mobile devices with mass notifications.
-
InformaCast Mobile users can launch notifications directly from their mobile devices. With the InformaCast Command Center feature, organizations can pre-build buttons for common emergency scenarios to quickly access notifications and provide detailed information, like the location of the incident or a description of an intruder.
-
Flexible message templates mean organizations can create notifications for any kind of situation they are likely to encounter, from active shooters and severe weather to network outages and medical events.
-
Messages can be sent in multiple formats including SMS text messages, push notifications, emails, and audio messages. The more formats used the more likely it is that someone sees the message quickly and takes appropriate action.
-
InformaCast Mobile also offers geofencing capabilities to alert everyone within a certain area and even trigger alerts when particular users enter or leave a designated location.
(InformaCast Mobile mass notification software is a great solution for navigating reopening and a return from the coronavirus pandemic shut down. Courtesy of Singlwire Software and YouTube.)
Singlewire Software (Fourth of Four)

-
Best COVID-19 Communications Solution
-
InformaCast Fusion
-
At the onset of the COVID-19 pandemic one of the biggest challenges was sharing information with workers.
-
As companies closed and local and federal guidelines shifted, organizations without solid communication tools suffered and put people at risk as unorganized responses led to confusion, downtime, and in severe cases the exposure to the disease.
-
The mass notification capabilities of InformaCast Fusion from Singlewire Software helped organizations stay in touch with employees to keep them up to date about health and safety guidelines as well as operational changes caused by the pandemic.

-
With the ability to reach on-premises and mobile devices from a single system, organizations could still reach all of their people whether facilities were open or closed, using text, audio, and visual cues to send messages to desk phones, IP speakers, desktop computers, mobile devices, digital signage and more.
-
With a wide variety of channels being used, people see messages quickly and take action. During an event like the pandemic, this is critical when trying to maintain business continuity.
(InformaCast mass notification software by Singlewire Software is a comprehensive emergency mass communication solution. InformaCast allows its users to leverage on-site devices to IP phones, monitors, overhead paging systems, panic buttons, and others to reach on-premises employees, while also leveraging mobile devices, Microsoft Teams and Cisco Webex Teams to remote workers. InformaCast has 3 different services levels, Fusion, Advanced and mobile to send emergency notifications, communicate promptly with employees and guests as well as create bell schedules and automated weather alerting. Courtesy of Singlwire Software and YouTube.)
-
*Singlewire Software was also recognized with Multiple Awards in the 2020 ‘ASTORS’ Awards, as well as Awards in the 2019, and 2018 ‘ASTORS’ Homeland Security Awards Program.
Siren Operated Sensors (SOS)
-
Best Fire & Safety System
-
-
SOS Silent
-
SOS Silent Emergency Gate Access Systems are the fastest way for emergency vehicles to gain access to gated facilities, campuses, and residential communities.
-
-
-
This pure and simple system allows responders to focus on driving and on the emergency ahead without pushing a remote, looking up a code, stopping to use a key, or changing the channel on their radio to trigger the gate.

-
Using RFID the SOS Silent System will open gates quickly, silently, and automatically when emergency response vehicles come within range of the gate and can be adjusted from 10 to 600 feet to customize each gate entrance.
-
The SOS Silent also has a backup entry system to open with the “YELP” siren.
-
SOS Silent ensures first responders can get to community members in need with no life-threatening delays. No stopping, no getting out of the vehicle, no codes to remember, no remotes to push, no keys to lose, and no cost to the municipalities.
-
*Siren Operated Systems has now been recognized for Five Consecutive Years in the Annual ‘ASTORS’ Homeland Security Awards Programs.
SolarWinds Worldwide (First of Three)
-
Best Security Incident & Event Management (SIEM)
-
Threats to IT networks continue to accelerate and evolve and while enterprising hackers from external sources test the robustness of network security parameters, internal threats in the form of careless and malicious insiders remain a major and ongoing concern.
-
It is critical that agencies take steps to combat these threats—and SolarWinds® Security Event Manager (SEM), formerly Log & Event Manager is a powerful weapon. This comprehensive SIEM solution delivers dynamic, real-time log collection and analysis for immediate and actionable threat intelligence.
(See a brief, high-level overview of the capabilities of SolarWinds Security Event Manager and how you can use the SIEM tool to detect threats, quickly respond to cyber incidents, and report compliance from a consolidated interface. Courtesy of Solarwinds Worldwide and YouTube.)
-
SEM can capture and analyze log data in real-time from multiple sources and specific incidents, allowing users to quickly identify and remediate threats, uncover policy violations, and resolve vital network issues, and users can quickly shut down breached systems, block IP addresses, kill unexpected processes, and disable user accounts.
-
SEM includes an easy-to-use, point-and-click interface and data visualization tools to quickly search log data, perform event forensics, and identify the cause of security incidents or network problems.
-
Like all SolarWinds software, SEM is built to scale and can support IT environments of all sizes, and employs a node-based license model that allows users to stay within their planned budgets as they deploy and expand their IT infrastructures across multiple data centers and geographies.
-
SolarWinds SEM is used by nearly every U.S. federal civilian agency, DoD branch, and intelligence agency. It is available on the U.S. General Services Administration (GSA) Schedule and other contract vehicles.
SolarWinds Worldwide (Second of Three)
-
Best Network Security Solution
-
Successful threat mitigation requires continuous real-time monitoring of network configuration changes and potential policy violations, and alerts for automated detection and remediation of harmful security violations is essential.
-
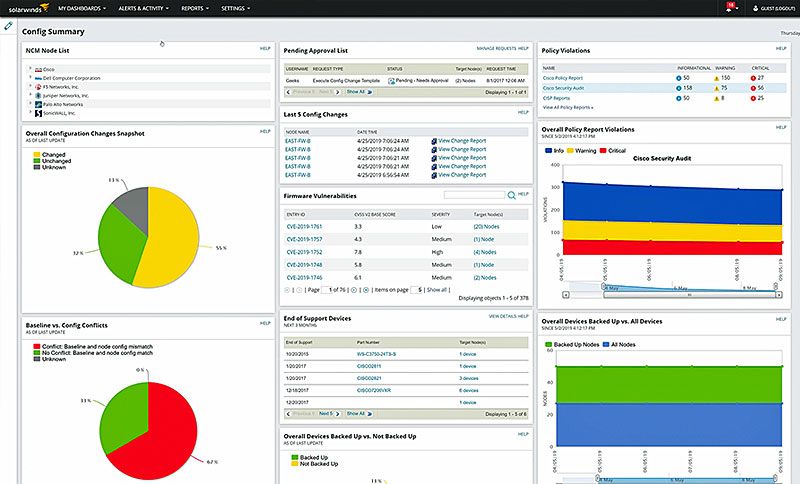
SolarWinds® Network Configuration Manager (NCM) offers compliance auditing and leverages baselines and differential viewers to help ensure that devices are configured correctly, with an automated change control workflow, bulk configuration updates, and automatic vulnerability assessments to help teams efficiently identify and fix vulnerabilities – all in a single solution.
-
NCM offers several unique and powerful features to help agency IT professionals protect against vulnerabilities and prevent unauthorized network configuration changes, and uses Cisco® IOS® and ASA vulnerability scanning and NIST FISMA, DISA STIGs, and DSS PCI compliance assessments to improve network security.
-
The software itself features hundreds of built-in compliance reports to help meet major auditing authority requirements, including DISA STIGs, NIST FISMA, and more, and THWACK®, SolarWinds’ online user community, provides a number of free report templates that can be used to prepare for an inspection.
-
NCM is built for IT environments of all sizes and can easily scale to meet growing infrastructure needs. Licensing depends on the total number of devices an IT pro manages, including firewalls, routers, switches, or any other device that supports remote access and a command line interface.
(Increase visibility to your network devices with SolarWinds® Network Configuration Manager. Save time and improve network reliability by automating network configuration and change management to reduce configuration errors, recover quickly from downtime, and improve security and compliance. Courtesy of SolarWinds and YouTube.)
SolarWinds Worldwide (Third of Three)

-
Best IT Access Control & Authentication System
-
SolarWinds Access Rights Manager (ARM) is designed to assist IT and security admins to understand and act on high-risk access and minimize the impact of insider threats.

SolarWinds® Access Rights Manager (ARM) is designed to deliver customized Active Directory (AD) and Azure AD reports—showing who has access to what, and when they accessed this data.
-
SolarWinds ARM enhances security by monitoring, analyzing, and auditing Active Directory®, Azure AD, Exchange™, SharePoint, OneDrive, and file servers to see what changes have been made, by whom, and when those changes occurred, and customized reports can be generated to demonstrate compliance with most regulatory requirements.
-
The solution also provisions and deprovisions users using role-specific templates to help assure conformity of access privilege delegation in alignment with security policies.
-
ARM helps prevent data leaks and unauthorized changes to sensitive files and data through visualization of permissions on file servers.
-
SolarWinds ARM reduces IT workload through a web-based self-service portal, put access rights of data in the hands of data owners instead of admins.
(SolarWinds Access Rights Manager (ARM) helps IT and Security Admins meet compliance requirements with centralized provisioning, de-provisioning, management, and audit of user permissions and access to systems, data, and files while protecting their organizations from internal security breaches. Courtesy of SolarWinds and YouTube.)
-
*SolarWinds has now been recognized with Multiple Awards in all Six Annual ‘ASTORS’ Awards Programs.
Stellar Cyber

-
Best Cyber Analytics Solution
-
National Security requires scanning every potential ingress point for cyberattacks. Networks are the prime vector for cyberattacks, and network security focuses on spotting those attacks. Stellar Cyber addresses the challenge that network security is broken because it creates too many alerts and alert fatigue.
-
The good thing about network security (network detection and response, or NDR) tools is that they capture evidence of attacks from the true source – the network that connects everything, including servers, endpoints, users and the cloud.
-
The bad thing is that most network security tools create a torrent of alerts, leaving security analysts overwhelmed with alerts and spending all of their time chasing them down instead of responding to real security exploits.
-
Stellar Cyber’s Open XDR platform distills related alerts into contextual incidents so analysts can move quickly to responding to remediating real attacks.
-
Stellar Cyber’s platform was the first Open XDR platform – that is, it collects data from other, existing security tools (including NDR tools), or customers can deploy Stellar Cyber’s patented sensors that extract the relevant security data at ingestion, minimizing storage costs.
-
Stellar Cyber’s platform then normalizes their data for ingestion by its AI engine, and automatically correlates that data to spot breaches that might go unnoticed in security systems that require manual correlation of data from multiple consoles.
(See how Stellar Cyber’s Open-XDR Platform solves the tool, data, and people challenges in the security industry today. Courtesy of Stellar Cyber and YouTube.)
Strata Identity

-
Best Cloud Identity Orchestration Solution
-
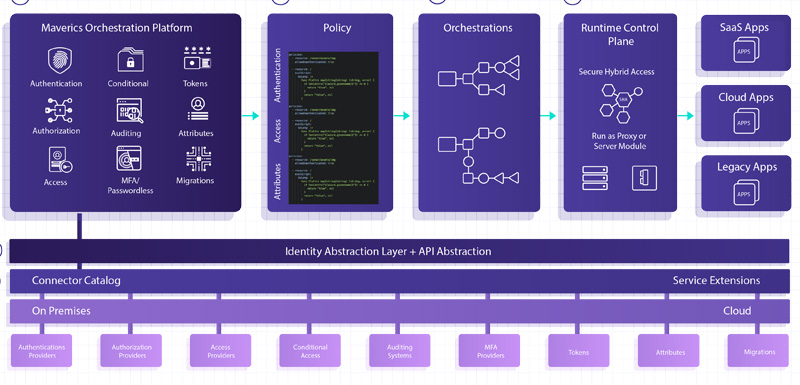
Maverics Identity Orchestration Platform
-
The cloud has created an identity management crisis, with companies being forced to simultaneously manage on-premises and several different cloud provider systems to enforce security policies.
-
Strata’s Maverics Identity Orchestration Platform™ creates an identity control plane that enables customers to enforce a global access policy at scale across multiple distributed clouds and on-premises systems.
-
It is not another Single-Sign-On (SSO), directory, or authentication solution, it is the first distributed, standards-based identity orchestration solution that automates multi-cloud and hybrid cloud identity management, and represents a brand new approach to distributed identity management.
-
Maverics eliminates the need for companies to replace their existing identity systems or rewrite apps in order to make them compatible with new identity systems, which avoids years of integration and migration time and costs.
-
Strata’s ‘migration factory’ approach enables organizations to “lift-and-shift” apps, whether it’s one or one thousand (or more), quickly to the Cloud.
-
By design, Maverics connects to any identity system, transparently migrates users and credentials, replicates and synchronizes policies and configurations, and abstracts authentication and session management.
(With Strata’s Maverics Identity Orchestrator™, enterprise identity management is simplified as you can migrate and modernize your identity systems without painful application rewrites. You’ll save hundreds of hours, and millions of dollars on your upcoming project. Courtesy of Strata Identity and YouTube.)
StrikeReady

-
Best Threat Intelligence Solution
-
StrikeReady
-
StrikeReady addresses both cyber security skill gaps & the talent shortage via an AI-driven virtual assistant – CARA (Cyber Awareness and Response Assistant).

-
CARA assists defenders to reason and respond to threats using institutional knowledge, and accelerates the SOC to be leaner, efficient and mature.
-
CARA was designed to not only assist, but also empower cybersecurity teams that are overburdened with an endless tally of incidents, alerts, and an ever-changing threat landscape.
-
It can join any team – SOC, Incident Response, Threat Intel, Security Engineering, Red Team, Security Operations, and more — and offer expert assistance.
-
With CARA, defenders can quickly respond to incidents, proactively defend against emerging threats, or operate at lightning speed as they continue to perform any security operations-centric task.
Teledyne FLIR
Best CBRNE Detection Solution
-
identiFINDER R700
-
The Teledyne FLIR identiFINDER R700, introduced in June 2021, is a Backpack Radiation Detector (BRD) that fills a need in the operational deployment of radiation detectors.

-
The R700 builds upon years of tried and true spectroscopic algorithms applied to a man-portable backpack detection system for accurate and reliable results.
-
The R700’s lightweight, flexible and portable design allows users to configure the system as either an unmarked backpack or a stationary device, enabling mission sets from wide-area searches to temporary checkpoints.
-
With its nondescript backpack form-factor and phone-based user interface, operators detect radiological threats covertly, even in a crowd.
-
The identiFINDER R700 which is a recent recipient of a U.S. government award, provides the capabilities required to successfully perform wide-area searches quickly and efficiently while offering exceptional sensitivity, communication, and trusted spectroscopic algorithms in a lightweight, ergonomic form-factor.
(The FLIR identiFINDER R700 Backpack Radiation Detector (BRD) offers new spectroscopic broad-search capabilities. Once dismounted, the identiFINDER R700 provides the capabilities required to successfully perform wide-area searches quickly and efficiently while offering exceptional sensitivity, communication, and trusted spectroscopic algorithms in a lightweight, ergonomic form-factor. Courtesy of Teledyne FLIR and YouTube.)
-
*FLIR Systems has now been recognized in all Six Consecutive Years of the Annual ‘ASTORS’ Homeland Security Awards.
TiniFiber
-
Best Security Wire & Cable Solution (Tie**)
-
TiniFiber
-
TiniFiber is a breakthrough innovation in fiber optic cabling that delivers some of the smallest, strongest, and most flexible armored fiber optic cable on the market to meet aviation cabling project requirements in the tightest congested airport pathways.
-
TiniFiber® protects the fragile fiber optic glass within the cable jacket with a U.S. Patented Micro Armor Fiber™ cable which has a similar outer diameter (OD) of a standard fiber cable but 75% smaller and 65% lighter than the aluminum interlock armor (AIA).
For example, a typical AIA 12 strand armored cable can cause many challenges for airport installation and maintenance, including a minimal bend radius which when stressed, can crack the glass within the cable.
Additionally, AIA is heavy to handle, requires multiple technicians to roll out, and requires large reels to ship to sites, which takes up mission-critical space within the pathways.
12 Strand Fiber Optic Armor Competitive Analysis – Based on 1000 Feet:
-
*Tinifiber was also recognized in the 2019, and 2018 ‘ASTORS’ Homeland Security Award.
True Security Design
-
Best Law Enforcement Training Solution
-
Remote & On-Demand Police Training Subscription
-
In 2021 True Security Design released Remote Live Training and an On-Demand Police Training Subscription services to address Budget, Social Distancing and Scheduling Issues Departments are Facing.

-
These remote services enable police agencies to train their staff around any of the covid lockdown and social distancing guidelines.
-
With the subscriptions entire police agencies are addressing budget cuts by training their entire staff for the cost of a single officer training, stretching scarce training dollars, and providing training to every officer in an agency regardless of size for the same price.
-
With the On-Demand service, police officers can take the training at any time overcoming scheduling obstacles they commonly face and benefit the individual officer their agency and the communities they serve.
(Addressing the entire officer, the mind, the body, and the spirit of your people is not just a good idea, it should be the focus, and this on-demand police training subscription does exactly that. Courtesy of True Security Design and YouTube.)
-
*True Security Design was also recognized in the 2019, and 2018 ‘ASTORS’ Awards Program, and Lt. Joseph Pangaro, the President and CEO of True Security Design, was recognized in the 2020 ‘ASTORS’ Awards Program.
TrueFort
-
Best App & Cloud Workload Protection Solution
-
TrueFort Fortress
-
Applications are the lifeblood of a business – regardless of how or where they’re delivered and accessed. Yet, while enterprises spend millions on new solutions, breaches and exfiltration continue to rise in frequency, profile, and impact
-
TrueFort has developed an innovative, application-centric approach that overcomes the security blind spots inherent in traditional application security tools to provide unparalleled visibility and protection for modern application environments.
-
TrueFort Fortress was designed specifically for the complex, dynamic nature of modern application workloads that span multi-cloud, hybrid, and data centers, applying deep, continuous analytics and machine intelligence to identify threats, align and apply controls in real-time, and adapt at machine speed to application and architecture changes, all while minimizing false positives.
-
TrueFort Fortress greatly reduces business risk by supporting zero or lean trust application environments that protect themselves, and the platform’s patented automation and intelligence monitors, alerts and responds to threats in real-time and establishes a trust profile for every application.

Next-gen application & workload protection. Adaptive trust technology gives your applications the power to protect themselves intelligently and in real-time across your entire application landscape.
-
TrueFort Fortress detects and prevents advanced persistent threats (APTs), insider threats, account compromise, and more.
-
Application security teams use Fortress to achieve unparalleled security visibility to inform and improve their security strategy and architecture decisions.
-
Identity governance teams use Fortress for visibility into all of the software service account identities being used, as well as the usage patterns.
-
For threat hunters, TrueFort Fortress provides out-of-the-box searching and querying capabilities against application contextual data that significantly reduces the typical setup time required to begin threat hunting.
-
For audit and compliance, Fortress provides the visibility and controls necessary to satisfy regulatory, industry, and corporate compliance policies.
-
(Hear from Sameer Malhotra, CEO & Founder of TrueFort, as he describes application challenges and how TrueFort can reduce clients’ security attack surface with application risk posture. Courtesy of TrueFort and YouTube.)
TruU
-
Best IT Access Control & Authentication System
-
TruU Platform
-
Still Using Passwords? TruU’s Passwordless Multi-Factor Authentication (MFA) can do better.
-
80% of breaches start with compromised credentials
-
$2.1 Trillion Global cost of data breaches in FY 2019
-
-5% Drop in stock price the day a breach is announced
-
-
TruU offers a Passwordless Workforce Identity Management Solution designed to use a unique combination of self-sovereign biometrics and behavioral biometrics, to create the most frictionless access user experience for physical resources and computing systems.
-
Enjoy complete and robust passwordless authentication for your entire workforce and eliminate the possibility of phished or stolen passwords with TruU.
-
Integrate into major enterprise identity stores and IT infrastructure and ensure compatibility with your environment.
Valor Systems
-
Best Emergency Response Program for Federal/State or Local
-
Valor Incident Management System
-
The Valor Incident Management System (Valor IMS), is an integrated suite of modern computer programs designed to automate and enhance the flow of critical information amongst communications operators, the response units in the field, support units, and the public.

-
Valor IMS serves emergency response and records management needs of government, corporate security, and university safety/security organizations, with an interactive situational awareness incident management platform to complement synergistic operations among all stakeholders.
-
Valor Systems Integrated Public Safety
and Security Software Platform offers CAD, RMS, Mobile, and citizen reporting applications that can work independently and/or collectively in concert as one unified platform based on a client’s budget, operational needs, and installation timeframe, with systems that can be installed locally on a customer’s computer network or accessed as a Software as a Service (SaaS) hosted on CJIS compliant, secured “cloud” network.
(See a brief introduction to the Valor Incident Management System (Valor IMS). Courtesy of Valor Solutions and YouTube.)
Versa Networks

-
Best Network Security Solution (Tie**)
-
Versa SASE (Software as a Service) is an industry-first solution that delivers leading Secure SD-WAN services and private connectivity for employees who are remote or working from home, so they can securely connect to applications in both private and public cloud services.
-
This new solution is based on the Versa Operating System (VOS™), a comprehensive and advanced next-generation virtual appliance that powers Secure SD-WAN networks on-premises and in the cloud for thousands of customers globally.
-
To protect the enterprise, which now has an expanded threat perimeter with the majority of connections being remote, Versa SASE offers the industry’s widest range of security functions in a Secure SD-WAN solution, which includes stateful firewall, DOS protection, next-generation firewalls, IPS, and URL filtering on end users’ client devices connecting privately to company resources hosted in private data centers, the public cloud, and Software as a service (SaaS) locations.
(Available via the cloud, on-premises, or as a blended combination of both, Versa SASE connects Work-from-Home users to Enterprise branches securely and reliably to applications in the cloud or data centers around the world. Courtesy of Versa Networks and YouTube.)
West Virginia American Access Control Systems

-
Best Integrated Security Management System
-
The West Virginia American Access Control Systems (AACS) Series 400 makes security easy.

-
Designed to easily replace existing swing doors without additional construction, the AACS Series 400 is a fully customizable, ADA compliant security portal solution, trusted to meet the high-security needs of America’s most secure facilities for years.
-
Additionally, the AACS Series 400 portal now outfitted with Temperature Scanning capabilities automatically scans the user’s body temperature, and if the temperature exceeds the threshold the user is denied access to the building.
-
WVAACS security portals are 100% Made in the USA with US components.
-
*WVAACS was also recognized in the 2020, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs.
WireSecure
-
Best Identification Management Solution
-
WireSecure
-
While cyberattacks are a constant threat, impersonation remains one of the most prolific forms of fraud.

-
In the US alone, billions of dollars of fraudulent losses have been incurred by participants in M&A and real estate transactions, customers of financial institutions, investors, and other high-value targets.
-
WireSecure offers a new approach to identity management and authentication for wire transactions that applies AI and biometrics to make wire transactions more secure – while doing it in the context of how people work.
-
Frictionless and innovative, WireSecure digital ID credentials combine best-in-class facial recognition technology with government-issued ID and financial information to create an irrefutable form of identification.
-
In essence, WireSecure creates secure communities – where identities have been validated and accounts are verified, so that exchanges can be conducted in a secure manner.
(See how to create secure, verified communities to prevent fraud, provide confidentiality, and automate financial transactions. Courtesy of WireSecure and Vimeo.)
Yubico

-
Best Cyber Security Solution
-
The YubiKey 5 FIPS Series is the industry’s first set of multi-protocol security keys with support for FIDO2 and WebAuthn, along with smart card (PIV/CAC), to receive FIPS 140-2 validation, Overall Level 1 and Level 2, which enables government agencies and regulated industries to meet the highest authenticator assurance level 3 (AAL3) requirements from the new NIST SP800-63B guidance.

-
The addition of the YubiKey 5 NFC, YubiKey 5C NFC, and YubiKey 5Ci into the FIPS series lineup significantly expands coverage for mobile-first environments that many organizations have been waiting for.
-
The YubiKey 5 FIPS Series hardware authenticator, offers one-touch strong authentication, does not require a battery or network connectivity, and reduces password support incidents by 92% to dramatically lower IT support cost.
-
This combination of desktop and mobile functionality allows U.S. government agencies and contractors, as well as other highly-regulated entities, to modernize their existing authentication framework and achieve phishing-resistant passwordless authentication for all users.
(See how easy it is to set up the YubiKey 5 FIPS Series YubiKey in just 4 easy steps to protect your online accounts, and you’ll be on your way to a safer online experience. Courtesy of Yubico and YouTube.)
-
*Yubico was also recognized in the 2020, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs, respectively.
** In the rare event of a Tie in the Annual ‘ASORS’ Awards Program, this result occurs based on overall differing goals and technology applications of the products or services, or overall similarities of the products.
AST is Proud to Introduce the 2021 ‘ASTORS’ Excellence and Government Awards
Thomas Richardson
-
Excellence in Public Safety
-
-
FDNY Chief of Department
-
Chief Richardson is a 40-year veteran and true servant leader who served tirelessly as a Battalion Chief in the aftermath of 9/11 – after having lost 343 of his colleagues, Chief Richardson never sounding retreat or surrender to those who tried to harm our Country.
-
-
Richard Blatus
-
Excellence in Public Safety
-
-
FDNY Assistant Chief of Operations
-
Assistant Chief of Operations Blatus, also a 40-year Department veteran who also served as a Battalion Chief in the aftermath of 9/11 attacks, Chief Blatus continues to lead, to inspire, and to mentor firefighters.
-
-
James Albrecht
-
Excellence in Public Safety
-
A retired NYPD Captain, First Responder, and Incident Command Management Member at the World Trade Center on September 11, 2001, and many other major events across New York City.
-
Captain Albrecht is also a Retired Police Chief who served as the Chief of Criminal Investigations for the United Nations and European Union police agencies in Kosovo, and is presently a Professor of Criminal Justice and Homeland Security at Pace University in New York City.
Derrick Driscoll
-
Excellence in Homeland Security
-
-
United States Marshals Service Deputy Director COO & Chief Risk Officer (Ret)
-
-
-
Deputy Director Driscoll is a 27-year veteran of federal law enforcement recognized for his relentless and global pursuit of criminals and criminal organizations.
-
Derrick now uses that same drive to build strategic alliances in the private sector, serving as the Principle of Strategic Alliances for Peraton’s Civil & Health Sector, where he leads the sector’s federal government strategy and engagement.
(Derrick Driscoll, United States Marshals Service. Courtesy of WMAR-2 News and YouTube.)
Frank Larkin
-
Excellence in Public Safety
-
In honor of Mr. Larkin’s career service to our Nation as a United States Secret Service Special Agent and First Responder to the World Trade Center; as a Navy SEAL and extraordinary leader who now leads a global effort to recognize early signs of TBI in our service members to prevent generations of grief to families and to society in the absence of these future leaders. His efforts result from the loss of his beloved son Ryan, a Navy SEAL to suicide following repeated undiagnosed percussive injuries.
-
Navy SEAL Special Warfare Operator First Class (SO1) Ryan F. Larkin, a decorated Navy SEAL operator and explosives breacher, Ryan was regularly exposed to high-impact blast waves throughout his 10 years of service. Ryan was a decorated U.S. Navy SEAL that had served his country honorably, including four combat deployments.
-
Ryan started experiencing headaches and other health issues and was diagnosed with PTSD. From research of him and his family it seems that his frustrations with his PTSD diagnosis, continued medication changes, and no improvement were beginning to wear thin on him.
-
Ryan was honorably discharged from the Navy and sought out continued treatment at the VA. It seems as though his frustrations with his deteriorating health continued. He suffered nightmares, insomnia, and daily headaches.
-
Ryan was vocal about his concerns and expressed that there was more going on within his brain. He also voiced that if something were to happen to him then he would like his brain to be donated to science for further research. After Ryan passed his family did just that. They had Ryan’s brain tissue donated for research.
-
It was found that the “invisible wounds of war” that are so frequently discussed were a very real part of Ryan. His brain showed Traumatic Brain Injury (TBI), and lesions called astroglial scarring, which are lesions closely related to blast exposures. These microscopic tears are undetectable via standard MRI or PET scan.
(Listen to surviving dad Frank Larkin share lessons learned on the lookback in an effort to save lives in honor of his son, Ryan. At TAPS they say that “postvention is a critical component of any comprehensive suicide prevention strategy.” Learn about suicide risks and protective factors as well as our field-leading TAPS Suicide Postvention Model at https://www.taps.org/suicide. Courtesy of Tragedy Assistance Program for Survivors and YouTube. Posted on Oct 8, 2020.)
Are you a Veteran in crisis or concerned about one?
If you have been thinking about suicide, it is important to get help right away. If you need to talk with someone right now, resources are available 24/7.
 Please call the Veterans Crisis Line to reach caring, qualified responders with the Department of Veterans Affairs, (many of them are Veterans themselves), at 1-800-959-8277.
Please call the Veterans Crisis Line to reach caring, qualified responders with the Department of Veterans Affairs, (many of them are Veterans themselves), at 1-800-959-8277.
For survivors in need of immediate suicide postvention support, please contact us at 800-959-8277 or call the National Suicide Prevention Lifeline at 1-800-273-8255.
To Learn More about Mr. Larkin’s personal story, please go to https://americansecuritytoday.com/a-personal-reflection-on-the-impact-of-9-11/. Courtesy of PWPORG.org.
John Merrill
-
Excellence in Homeland Security
-
-
Deputy Director, Technology Centers Division (Acting) at U.S. Department of Homeland Security
-
-
-
John Merrill currently serves as the Acting Director of the DHS First Responders and Detection (FRD) division as well as the Next-Gen First Responder (NGFR) Apex Program Director.
-
Leading FRD, Merrill oversees the Countering Weapons of Mass Destruction Office (CWMD), Federal Law Enforcement Training Center (FLETC) and First Responders.
-
Under his leadership, NGFR has developed and integrated cutting-edge technologies – allowing for a timely, efficient and safe response to disasters of all sizes.
-
Merrill has successfully established a model for the program that expands industry involvement and collaboration with the Nation’s first responders.
-
He advocates on behalf of first responders, encouraging industry partners to collaborate directly with responders on R&D, testing, and evaluation, and to “walk a mile in their shoes.”
(Learn More about how the DHS Science and Technology Directorate (S&)T is mobilizing innovation to secure our world. From sensors to cybersecurity to technology for first responders, we work with you to find tomorrow’s solutions, today. Courtesy of DHS Science and Technology Directorate.)
Kevin Becker, PsyD, LCP
-
Excellence in Scientific Research
-
-
Trauma Counselor, and Owner of ORI Consulting
-
-
-
In recognition of Dr. Becker’s lifetime of service as a practitioner and as a psychologist helping individuals, organizations, and governments prepare for, respond to, and recover from crisis and traumatic events, and the human impact of trauma, crisis, and disaster for organizations and individuals.
(Hear Dr. Kevin Becker, keynote speaker at Newtown Sandy Hook Community Connections Day posted on Jul 10, 2017. Courtesy of ORI Consulting and YouTube.)
National Center for Disaster Medicine and Public Health (NCDMPH)
-
Excellence in Public Safety
-
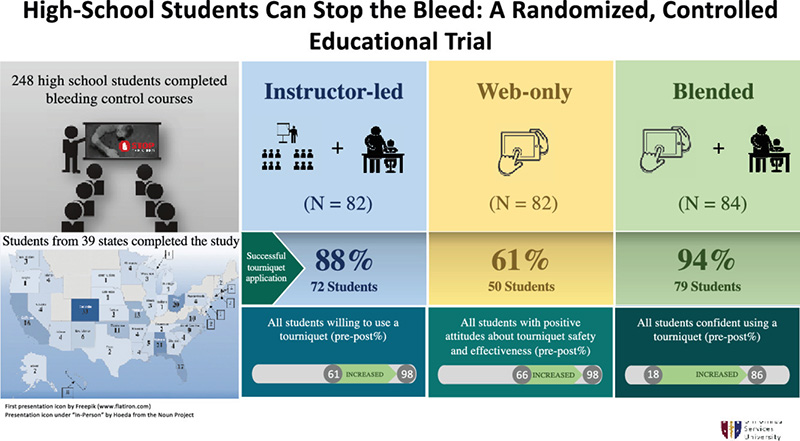
Trauma is the leading cause of death for young Americans, and there have been calls to teach children about hemorrhage control however little was known about adolescents’ ability to perform hemorrhage control, and the ideal way(s) to teach them.
-
The origins of FAST were developed using battlefield lessons-learned, evidence-based research, and student, medical, and educational expert input, and with the experience of Dr. Craig Goolsby, Professor & Vice Chair, Dept of Military & Emergency Medicine; Science Director, NCDMPH at Uniformed Services University, who has an extensive background in emergency medicine, medical education, combat casualty care, first aid, mass casualty, and disaster medicine.
-
The evidence-based nature of FAST was successfully documented through focus groups and educational research (with both high school students and teachers), which led to the development of the three training modalities to include live-actor videos featuring high school students.
-
Excellence in Public Safety
-
FAST is a school-age training initiative offered in multiple modalities, designed to enhance a bystander’s ability to take decisive, lifesaving action to assist victims with traumatic injuries.
-
FAST training provides the knowledge necessary to stabilize the injured and control severe bleeding in the minutes until first responders arrive on scene.
(The FAST education program is based on funding provided by the Department of Homeland Security (DHS) Science and Technology Directorate (S&T) to the National Center for Disaster Medicine and Public Health (NCDMPH). The FAST course and digital materials, developed by the American Red Cross in collaboration with NCDMPH, will be offered at no charge to high school students under the age of 19, thanks to the S&T grant. Courtesy of the DHS Science and Technology Directorate and YouTube.)
DHS Science & Technology (First of Four)
-
Excellence in Public Safety
-
The DHS Science and Technology Directorate (S&T) awarded a grant to the National Center for Disaster Medicine and Public Health (NCDMPH) to develop the school-age trauma training that became First Aid for Severe Trauma (FAST).
-
FAST is the first national STOP THE BLEED® course designed specifically for high school students and made available through the American Red Cross, thanks to the S&T grant.
-
While FAST is available for anyone, the course and digital materials are offered at no charge to high school students under the age of 19.
DHS Science & Technology (Second of Four)
-
Excellence in Public Safety
-
-
Wildland Fire Sensor Technology
-
The Wildland fires present a significant threat to the United States, and the DHS Science and Technology Directorate (S&T) is fighting fire with technology.
-
Wildland Fire Sensor Technology could provide the public with the advanced notice necessary to reduce the loss of life and property while giving communities the information and time necessary to make life-saving evacuations.
-
-
(Learn More, courtesy of the DHS Science and Technology Directorate and YouTube.)
DHS Science & Technology (Third of Four)
- Excellence in Homeland Security
-
In the event of a radiological or nuclear incident, emergency response agencies and HAZMAT teams could utilize this new technology to set up community reception centers to screen members of the public for potential exposure to radioactive contaminants.

-
Two inventors from the DHS National Urban Security Technology Laboratory (NUSTL) have developed a personal radiation detector (PRD) that could be placed beneath an entry ramp to detect radioactivity on the shoes of people being pre-screened before entering main screening areas.
-
This innovative and unique new device emits an alarm sound that is both louder than, and distinctive from other alarms, to ensure it can be easily heard and distinguished from other devices.
-
Additionally, the remote alarm box does not require any batteries nor external power and can be stored indefinitely without maintenance so that it is immediately ready for use in an emergency.
DHS Science & Technology (Fourth of Four)
-
Excellence in Homeland Security
-
DHS S&T identifies research the agency will conduct to understand the opportunities, as well as the risks, that accompany the rapidly changing AI/ML technology landscape and its impacts to DHS missions, and incorporate the technological advancements in AI/ML to enhance the efficiency and effectiveness of the DHS operational components and the broader Homeland Security enterprise.

-
S&T’s three strategic goals are to 1) drive next-generation AI/ML technologies for cross-cutting homeland security capabilities; 2) facilitate the use of proven AI/ML capabilities in homeland security missions; and 3) build an interdisciplinary AI/ML-trained workforce.
-
The Strategic Plan aligns with the DHS Artificial Intelligence Strategy, which lays out goals to govern the Department’s approach to integrating AI into the DHS mission.
View Part 1Intro & Winners A – D View Part 2 Winners E – Na
View Part 3 Winners NE – Si NEXT View Part 5 Winners Excellence