
In addition to DEAC Sabatino, AST was also joined by Legendary Police Commissioner William Bratton who spoke, as always, about his love for the City of New York, the Profession of law enforcement to which he has dedicated his life, and for which he continues to drive thought leadership and innovation.
Commissioner Bratton, the Executive Chairman of Risk Advisory at Teneo, has had the privilege of leading six departments, two of the largest in the country, New York and Los Angeles, including New York twice! From his earliest days in uniform in Boston, Massachusetts, he has been dedicated to identifying the catalysts for crime and working toward prediction and prevention.

Commissioner Bratton is one of the world’s most respected and trusted experts on risk and security issues, and was recognized as the ‘2019 ‘ASTORS’ Person of the Year’ for his Lifetime of Dedication and Extraordinary Leadership in Homeland Security and Public Safety.
During his almost 50-year career in law, he instituted progressive change and dramatic drops in crime while leading six police departments, including seven years as Chief of the Los Angeles Police Department and two nonconsecutive terms as the Police Commissioner of the City of New York.
He is the only person ever to lead the police agencies of America’s two largest cities.
Prior to assuming his role at Teneo Risk Advisory, Commissioner Bratton was the 42nd police commissioner of the City of New York from January 2014 to September 2016, during which, he oversaw 32 months of declining crime, including historic lows for murders and robberies.
(Hear directly from Commissioner William Bratton. Courtesy of American Security Today and Vimeo.)
The 2022 ‘ASTORS’ Homeland Security Awards Presentation Luncheon was an exclusive event featuring well over two hundred representatives of law enforcement, public safety, and top industry leaders who came together to honor the selfless service of those who stand on the front lines, and those who stand beside them – providing the capabilities and technologies to create a safer world for generations to come. (Continued)
Dedrone (First of Two)
 Best Persistent Aerial Monitoring Solution
Best Persistent Aerial Monitoring Solution
-
Dedrone Airspace Security Solution
-
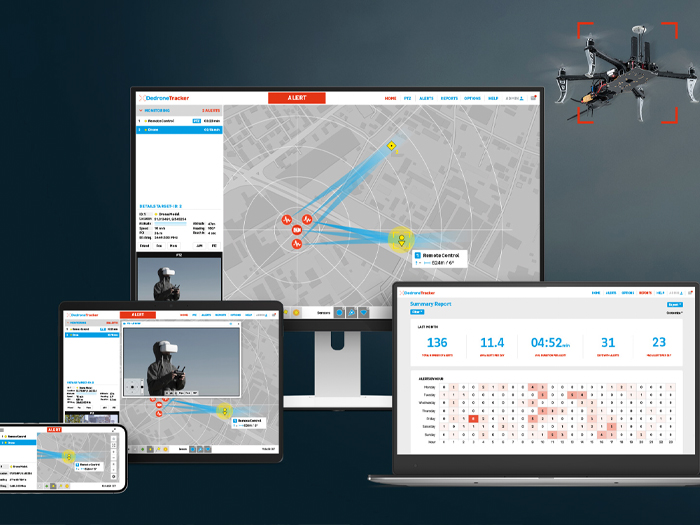
As drone use rises, so does the need to effectively monitor, track and mitigate drone threats.
-
Dedrone detects, identifies, locates, and offers critical insights into the nearly 300 different drone types (the largest variety of commercial, consumer, and homemade drones from over 65 manufacturers) that can infiltrate airspace.
-
Drone detection is complex as drones come in various shapes, sizes, and control mechanisms, and radio frequencies can also vary. Dedrone offers an all-in-one, flexible cloud-based or on-prem/air-gapped solution for airspace security that includes sensors, tracker software, comprehensive AI/ML-based detection capabilities, mitigation functionality, and advanced analytics.
-
Dedrone is the most prolific drone security company in the world, working across 33 countries to deliver best-in-class detection, identification, tracking, and mitigation of Small Unmanned Aircraft Systems (sUAS), and their solutions are used by the governments of four G-7 nations, nine U.S. federal agencies, including the Department of Defense, and internationally by more than 65 critical infrastructure sites, 20 airports, 50 correctional facilities, and ten Fortune 500 companies.
(We don’t always see drones in our sky, but drones can threaten our everyday life. Watch to learn how your city officials can use an effective counter-drone solution, Dedrone, to protect citizens from careless, clueless, and criminal drones. Courtesy of Dedrone and YouTube.)
Dedrone (Second of Two)
 Best Law Enforcement, Counter Terrorism, Crime Prevention Program for Federal/State/Local
Best Law Enforcement, Counter Terrorism, Crime Prevention Program for Federal/State/Local

-
DedroneRapid-Response, is the first of its kind, multi-layered, mobile AI-powered drone detection unit, offering Dedrone’s AI-powered technology — capable of detecting, identifying, locating, and analyzing nearly 300 unique drone types—in a mobile platform attached to a tower that can be easily towed and maneuvered on a trailer using an SUV or truck.
-
DedroneRapidResponse provides critical capabilities to ensure public safety at large-crowd events, including sports, parades, concerts, political gatherings, crime scenes, police activity, and more.
-
The DedroneRapidResponse solution was used to protect the 2022 Firestone Grand Prix, an IndyCar motor race, to effectively improve safety for drivers, race crews, and spectators during the event, including detecting nine drone infractions of the no-fly zone with three incidents occurring during the Indy season opener, making it easy for St. Petersburg PD to effectively assess and manage these threats.
(St. Petersburg Police partnered with Dedrone to use mobile drone detection technology to secure the 2022 Firestone Grand Prix. A drone that falls onto the racetrack could pose a deadly hazard to the racecars traveling at high speeds. Courtesy of St. Pete PD and YouTube.)
-
Using cloud-enabled software, DedroneRapidResponse pinpoints the drone, providing insights into its load and the pilot’s location as soon as a drone is turned on, giving security teams a significant head-start on a pilot about to fly into a “no fly zone.”
-
The tower is deployable in under 30 minutes and offers a range of 5km detection through a multi-layered solution with two cameras to track multiple drones simultaneously. Additionally, Dedrone can easily network multiple trailers to deliver optimal drone security for even larger public events.
-
*Dedrone was also recognized as an ‘ASTORS’ Award Champion in the 2021, and 2019 ‘Homeland SecurityAwards Programs.
Dispersive Holdings
 Best Cyber Critical Infrastructure Solution
Best Cyber Critical Infrastructure Solution
-
DispersiveCloud Converged SaaS for Zero Trust Networking
-
Critical infrastructure companies are high-visibility targets for any hostile cyber operations. Unfortunately, many such entities have let their infrastructure lag, have poor processes, and lack adequately trained personnel making them unlikely to withstand a nation-state-sponsored attack.

-
Equally problematic is the growing dependence on public cloud and SaaS applications which open up additional vectors of attack and further erode the IT team’s control.
-
DispersiveCloud is a one-of-a-kind SaaS that leverages proven battlefield concepts of RF frequency hopping and spread spectrum communications to secure TCP/IP networks and the Internet. With 51 patents granted, including 9 in the European Union and 3 pending, the technology is resistant even to sophisticated nation-state or quantum computing threat actors.
-
This allows governments, critical infrastructure enterprises, and cloud operators to achieve the full benefits of zero-trust networking regardless of the level of trust with the underlying infrastructure.
-
Dispersive can establish dynamic virtual active/active multipath networks with rolling encryption keys and granular access controls. In addition, orchestration, control, and data planes can be separated, thereby further protecting data flows from potential interception and future analysis. Managed attribution can also keep virtual endpoints, users, and network resources obfuscated, making them virtually impossible to detect. Finally, proper access control and device posture checking can be implemented to prevent unauthorized access.
(See how DispersiveCloud, a hosted secure access service edge (SASE) cloud offering leverages the same self-healing high-performance next-generation network fabric as DispersiveFabric, minus the complexity, and provides advanced VPN and SD-WAN services in a single solution without any upfront infrastructure investment. Courtesy of Dispersive Holdings and YouTube.)
-
DispersiveCloud is both intelligent and predictive, enabling dynamic routing and management capability with smart deflection and redirection of traffic from impacted resources and network nodes to mitigate against availability issues and DDoS attacks.
-
Importantly, performance can be enhanced, even across high latency, low bandwidth environments, enabling alternative communication pathways such as mobile hotspot, ADSL, broadband, satellite, MPLS, LTE, and others to maintain business continuity – even in the face of primary network disruption.
-
*Dispersive Holdings is a new competitor to the 2022 ‘ASTORS’ Homeland Security Awards Program.
Durabook Americas (First of Three)

Best Handheld Mobile Device Solution
-
The Durabook R11 Fully Rugged tablet is designed and built for the mobility and durability so important to law enforcement, first responders, and emergency services personnel, and features the latest Intel® 12th Generation processors and Intel Iris® Xe graphics, to deliver outstanding performance and visuals, all wrapped into its neat, compact form.

-
When lives and serious injuries are at stake – reliable, fast communications are essential. The Durabook R11 provides the high-speed data transmission capability of Thunderbolt™ 4, Intel® Wi-Fi 6E, and Bluetooth® V5.2, ensuring smooth, congestion-free processing at all times.
-
When your work office includes rain, cold, bright sunlight, and other environmental challenges, the robust design of the R11 tablet equips field workers with the confidence to do their jobs in even the harshest environments and temperatures. Drop-tested from 4 feet, MIL-STD-810H and MIL-STD-461F certified, optional ANSI C1D2 certified, and with an IP66 rating for maximum protection against dust, dirt, and water ingress, the R11 can be trusted to perform. At all times. In all conditions.
Durabook Americas (Second of Three)
Best Data Storage Security Solution
-
Z14I Fully Rugged Laptop
-
Data storage security for any company, organization or government institution revolves around two issues: storage and security – the Durabook Z14 Fully Rugged laptop supplies both in spades.

-
The Z14I is a veritable storage revolution providing users with a plethora of capacity, equipped with the latest NVMe PCIe SSD technology, providing up to 1TB of storage, while its PCIe offers speeds 4x faster than SATA III.
-
It can accommodate two more internal SATA III SSD drives to maximize onboard storage, and the device provides a media bay for several setup options, such as an optical disk drive, a second battery, or a third SSD storage.
-
Security comes in two forms: digital and physical, and teaming up, they create a formidable obstacle in keeping users’ stored data secure and safe. Digitally speaking, the unit features: Intel® vPro™ Technology (per CPU options), TPM 2.0, NIST BIOS compliance, an easily removable SSD, Smart card reader, stealth and night-vision mode, and Kensington lock.
-
Physically, its IP65 rating means it protects against dust and water ingress. It is both MIL-STD 810H (drop, shock, vibration, rain, dust, altitude, freeze/thaw, high/low temperature, temperature shock, humidity, explosive atmosphere, solar radiation, salt fog, fungus resistance) and MIL-STD-461G (conduction, radiation, conducted susceptibility, radiated susceptibility) certified. Plus, it is ANSI C1D2 Hazardous Location certified (allowing use in potentially explosive environments found in oil and gas, petrochemical, aviation, and other industries) for use in Class I, Division 2, Groups A, B, C, and D environments.
-
An abundance of storage capacity, both inborn and added on, with superior protection from both physical and digital calamities, make the Durabook Z14I Fully Rugged laptop as secure a means to store any amount of data as they come.
(Combined with the latest 11th Generation Intel® Core™ processor and graphics capabilities, the Z14I rugged laptop can handle data-intensive tasks at speed. It has been built to withstand even the harshest of environments. Its IP65 rating protects against dust, and water ingress, MIL-STD 810H certification, and resistance up to six feet drop make the Z14I more rugged than other comparable devices on the market. Courtesy of Durabook Federal and YouTube.)
Durabook Americas (Third of Three)
Best Mobile Technology Product
-
S14I Rugged Laptop
-
Law enforcement, first responders, and emergency services personnel, who put their lives on the line, should rightfully expect to perform their duties with top-of-the-line equipment, including mobile technology products. The Durabook S14I Rugged laptop provides them with just that.

-
Along with its latest 11th generation Intel® CPUs and class-leading 4’ drop spec/IP53 rating, the S14I combines military-grade durability, field-worker functionality, computing performance, and long battery life, and is built with a robust mechanical design and rigorously tested components, to meet MIL-STD-810H requirements.
-
The Durabook S14I tough rugged laptop effortlessly breaches the boundary between semi-rugged and fully rugged devices, and comes equipped with the latest NVMe PCIe SSD technology providing up to 1TB of storage. It can accommodate two additional internal SATA III SSD drives to maximize the onboard data storage. When storage performance or data redundancy and reliability are crucial, the S14I shines.
-
The unit has a Full HD 1080p display and Durabook’s proprietary DynaVue® technology. With brightness enhanced up to 1,000 nits and light-filtering technology providing a high contrast ratio (CR) to eliminate reflection, every imagery detail is delivered with the utmost clarity – day or night, indoors or out.
-
The Durabook S14I is equipped with a smart card reader, fingerprint scanner, and hardware-based encryption (Trusted Platform Module (TPM 2.0)) to ensure storage security. In addition to software-based encryption, hardware-based encryption can be applied. Within the advanced configuration settings on some BIOS configuration menus, users can choose to enable or disable a Trusted Platform Module (TPM 2.0).
(The all-new Durabook S14I features the latest 11th Generation Intel® CPUs and class-leading 4’ drop spec/IP53 rating, pushing semi-rugged devices to a whole new level. The S14I is engineered to combine military-grade durability, field-worker functionality, computing performance, and long battery life for non-stop use, making it suitable for use in locations where rain or dust may be a regular occurrence. Courtesy of Durabook Federal and YouTube.)
- *Durabook (formerly GammaTech Computer Corporation), was also recognized as an ‘ASTORS’ Award Champion in the 2021, and 2017 Homeland Security Awards Programs.
ECAMSECURE, a GardaWorld Company
Best Access Control & Authentication System (**Tie)
-
Virtual Gate Guard
-
Virtual Gate Guard is a compact, mounted access control solution with dual hi-resolution digital cameras that provide an edge-to-edge 180° field of vision secure points of entry.

-
Virtual Gate Guard deploys AI to detect vehicles and their drivers upon entry, and exit of a facility’s gated areas and provides an autonomous response, while also allowing for vivid two-way audio/video calls.
-
The comprehensive access control package is ideal for corporate campuses, parking structures, exterior areas, lobbies, buildings, and anywhere that increased visibility is needed at a fraction of the cost.
-
Virtual Gate Guard is cellular optimized, meaning that no WiFi is required, and provides cloud storage for a year of event recording.
(See how ECAMSECURE focuses on the right mix of human and technology integration to deploy innovative security solutions quickly. By using its clients’ constraints as the starting point for its creative security solutions, the company is able to cut through the obstacles that hold others back. From 24/7 virtual watchmen to machine-learning technology and smart monitoring, ECAMSECURE customizes solutions that meet the needs, budgets, and realities of each situation, no matter how quickly or often it changes. Courtesy of ECAMSECURE and YouTube.)
-
*ECAMSECURE is a new competitor in the 2022 ‘ASTORS’ Awards Program.
Ermetic
Best Cloud-Native Application Protection Platform
-
Ermetic Cloud Infrastructure Security Platform
-
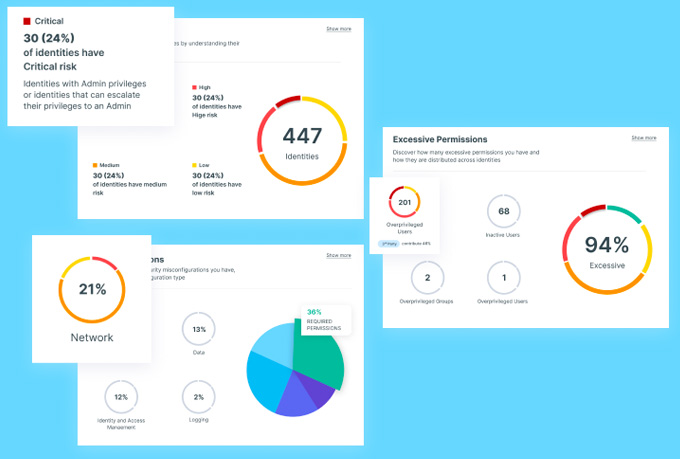
Ermetic is an identity-first cloud infrastructure security platform that provides multi-cloud protection in an easy-to-deploy SaaS solution.
-
According to Gartner, the #1 threat to cloud infrastructure is entitlements and permissions, because identifying risky permissions and misconfigurations is hugely difficult and requires insight into the access that all users and services have and actually need.
-
Addressing this at scale calls for visibility into thousands of identities, policies, and resources – and mitigating the risks revealed.
-
Using Ermetic, enterprises can enforce least privilege access in their cloud for all identities, across the entire technology stack, and manage their security posture with ease.
-
Ermetic helps Security and DevOps stakeholders work together to ensure cloud security without impact to application continuity or speed to market.
(See Ermetic’s comprehensive and accurate solution for managing human and service identities in cloud infrastructure environments, and for achieving the least privilege at scale in action. The platform offers deep, actionable visualization of all identities and entitlements, full risk context, and advanced analytics that reveal hidden dangers, and empowers teams through prioritization and automatic remediation of risky privileges and excessive permissions. Courtesy of Ermetic and YouTube.)
-
*Ermetic was also recognized in the 2021 ‘ASTORS’ Homeland Security Awards Program.
Everbridge
Best Critical Event Management Solution
-
Business Operations and People Resilience Solutions
-
Everbridge Business Operations and People Resilience is a risk monitoring solution that integrates threat intelligence technology and resources around all-hazards information collection and analysis, enhancing the organization’s ability to monitor, analyze, and respond to threats.
-
Combining thousands of the most trustworthy data sources with an experienced team of analysts at our Risk Intelligence Monitoring Center (RIMC), Everbridge Business Operation’s targeted real-time alerting streamlines the ability to monitor and analyze worldwide incidents and events, dramatically increasing the ability to respond to risks that threaten your people, organization, and supply chain.
-
Its hyper-local profiling capabilities enable businesses to get details on even small-scale events while filtering out the noise that might otherwise obscure them.
-
Its proven analytical process combines automation, machine learning, and analysts to quickly generate relevant risk intelligence with a high degree of confidence and minimal duplication.
-
Everbridge helps ensure organizational duty-of-care wherever your employees live, work, and travel with scalable capabilities to suit hundreds of thousands of assets and millions of contacts, in this comprehensive and configurable risk management solution that enables organizations to proactively monitor and analyze domestic or worldwide incidents and events, dramatically increasing the ability to respond to risks that threaten people, organizations and overall security.
-
*Everbridge was also recognized as a Platinum ‘ASTORS’ Award Champion Winner in 2021, 2019, 2018, and 2017 Awards Programs.
Evolv Technology
Best Pedestrian Entrance Control
-
Evolv Express
-
Traditional security screening was not designed for today’s dynamic threats, so unlike metal detectors, manual bag checks, wanding, and other traditional solutions, Evolv Express® offers an innovative approach to physical security screening.

-
Evolv Express accelerates physical security screening while maintaining the highest degree of weapons detection accuracy.
-
It eliminates the friction that visitors, fans, patrons, employees, and students typically experience moving through security by screening them in a touchless manner.
-
This helps reduce the security risk of crowded security lines. It also drastically reduces false alarm rates and human errors by security guards.
(Evolv provides a secure and seamless screening experience, making it possible for venues of all kinds to keep visitors safe from concealed weapons, public health threats, and intruders. Founded in 2013 and manufactured in the United States, Evolv has a proven track record in screening people for threats without sacrificing the visitor experience. People screening that’s intelligent, low-profile, and highly accurate — that’s what they do. Courtesy of Evolv Technology and YouTube.)
-
*Evolv Technology was also recognized as an ‘ASTORS’ Awards Champion in the 2021, 2020, 2019, and 2018 ‘Homeland Security Awards Programs.
Forcepoint
Best Phishing Defense Solutions
-
Zero Trust Content Disarm and Reconstruction
-
Forcepoint is leading the shift from outdated and ineffective malware and ransomware detection strategies to a proven prevention strategy rooted in Zero Trust principles.
-
With its Zero Trust Content, Disarm, and Reconstruction (ZT CDR) solution, Forcepoint gives IT and security teams a fresh new way to proactively protect their organization from ever-increasing malware and ransomware threats.
-
Forcepoint ZT CDR differentiates itself from traditional security inspection solutions by, instead of trying to detect the presence of malware; it assumes nothing can be trusted. It extracts only valid business information from files – either discarding or storing the originals and any malware they might contain – and then builds brand new, fully functional files to carry the information to its destination.
-
Pivoting from detection to prevention in this way is especially important with the recent evolution in hybrid workforces and digital transformation, and their resultant usage of content and electronic information everywhere.
-
By leveraging a data-first approach to malware threat removal, ZT CDR is revolutionary for mitigating the threat of compromised data that could lead to breaches.
(It’s no secret that much of the world’s malware and ransomware makes its way to organizations through infected files. See briefly how Zero Trust Content Disarm and Reconstruction (CDR) strips malware from office documents, images, and PDFs to put an end to Zero Day malware. Courtesy of Forcepoint and YouTube.)
-
*Forcepoint was also a recognized in the 2021, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs respectively.
Fortior Solutions
Best Access Control & Authentication Solution
-
The Fortior Solutions RAPIDGate Program is a patented, award-winning, and SAFETY Act-Designated identity, access, and security solution that boasts 99.97% uptime, and serves the government, military, and critical infrastructure sectors, fulfilling end-to-end identity management needs and accommodating a wide set of compliance specifications.

-
The RAPIDGate program is a complete vendor management solution that includes verification of company sponsorship, company enrollment, multi-language kiosk-based registration, individual biographic and biometric collection, equipment, commercial background screenings, DOJ/FBI NCIC/III checks (subject to approval of the relevant government authorities)
-
The RAPIDGate® and RAPID-RCx® programs provided unparalleled perimeter control at some of the most security-conscious organizations in the world including, the U.S. Army, U.S. Coast Guard, U.S. Navy, U.S. Marine Corps, and NASA among others.
(See RAPIDGate®, a high-assurance identity management program for vendors, contractors and service providers who require escorted or authorized access to secure facilities or sensitive corporate resources, and guard against threats such as unauthorized access, identity theft, fraud or cyber-crime. Courtesy of Fortior Solutions and Vimeo.)

-
*Fortior Solutions (formerly SureID), is also a Returning Premier Sponsor for their Second Consecutive Year, and was recognized as an ‘ASTORS’ Award Champion in the 2021 and 2016 Homeland Security Awards Programs.
Fūsus
 Best Investigation/ Surveillance/Detection Solution
Best Investigation/ Surveillance/Detection Solution
-
Fūsus Real-Time Crime Center in the Cloud
-
The Fūsus Real-Time Crime Center in the Cloud’s (RTC3s) is now the most widely used & trusted Real-Time Crime Center platform in U.S. Law Enforcement. It is a unique solution, the only truly open, technology-agnostic platform on the market.
-
RTC3 enables law enforcement and security agencies to create a unified intelligence ecosystem that integrates and enhances all public safety and investigations assets.
-
Scalable and affordable for agencies of any size, it can integrate public and private cameras, ALPR systems, gunfire detectors, CAD, and much more into a single platform.
(Fūsus RTC3 extracts and unifies live video, data, and sensor feeds from virtually any source, enhancing the situational awareness and investigative capabilities of law enforcement agencies. Courtesy of Fusus and YouTube.)
-
The Fūsus Real-Time Crime Center in the Cloud’s (RTC3s) video intelligence and map-based awareness interface serves as the central integration point for Law Enforcement agencies’ surveillance, security, and life safety technology.
-
Whether it’s a UAV, a traffic camera, a private cell phone video, a building security camera, or a bomb disposal robot, Fūsus can extract the live video feed and send it to your emergency operations center and officers in the field.
-
Fūsus RTC3 creates a public safety ecosystem that combines video with other utilities like Computer Aided Dispatch (CAD) data, gunfire detectors, real-time officer geolocator feeds, a registry map of all the public and private cameras in your region, a multi-media tips line for the public, and a digital evidence vault for investigators.
(See how Fūsus Real Time Crime Center In The Cloud Works in Collaboration with Connect Atlanta, a new public safety program enabling the people of Atlanta to help keep their community safe. Participation greatly enhances emergency preparedness by enabling police, fire, and public safety professionals to better assess and rapidly respond to criminal activity and emergency situations. It also enables investigators to gather evidence easily in the event of an incident. Courtesy of Fusus and YouTube.)
-
*Fūsus was also recognized in the 2021, and 2020 ‘ASTORS’ Homeland Security Awards Programs.
Gallagher
 Best Integrated Solution for HSP D-12/FIPS 201 Compliance
Best Integrated Solution for HSP D-12/FIPS 201 Compliance
-
Command Centre PIV Solution
-
The Gallagher Command Centre PIV Solution delivers exceptional security and the fastest form of authentication for US Federal Government customers. With one smart, centrally managed platform, Command Centre PIV meets the HSPD-12/FIPS-201 compliancy requirements from both a 13.01 and 13.02 topology.

-
Gallagher Command Centre PIV is an enterprise-grade Physical Access Control System (PACS) that provides robust, real-time authentication of all federally issued high-assurance credentials. It natively supports reading and verifying the complete secure certificate information on government cards and is scalable to meet organizational requirements – no matter how big the site, or the number of cardholders involved.
-
Command Centre is the chosen platform for many of the world’s most high-consequence sites, and it’s easy to see why. Across military and defense, federal, state, and local government, commercial, education, healthcare, and transportation, Command Centre’s curb-to-core technology has been proven to protect lives, create efficiencies, and save organizations thousands of dollars each year.
(Gallagher Command Centre delivers an enterprise-grade Physical Access Control System (ePACS), offering robust, high assurance certificate-based credential authentication with Curb-to-Core capabilities. Courtesy of Gallagher and YouTube.)
-
Command Centre PIV is an access control solution that does it all, enabling federal organizations to manage complete site security from one highly intelligent platform and has been proven to save time, resources, energy, and money, all while delivering superior security that keeps even the most sensitive of sites protected.
-
*Gallagher was also recognized in 2021, 2020, and 2019 ‘ASTORS’ Awards Programs, respectively.
Genasys (First of Two)
 Best Alert Notification System
Best Alert Notification System
-
Genasys Emergency Management (GEM)
-
The Genasys Emergency Management (GEM) from Genasys is the only unified critical communications platform that combines hardware, software and geo-data analytics. Genasys’ unified multichannel system empowers government agencies and organizations to deliver real-time, geo-targeted alerts, notifications, information before, during, and after public safety threats.
-
GEM enables the delivery of emergency notifications through multiple channels, including voice calls, SMS, email, desktop alerts, social media, IPAWS, and other delivery methods, to help ensure critical communications are received by at-risk individuals and populations.
-
GEM software adds a powerful and intuitive orchestration and management layer on top of existing physical and digital infrastructure to extend the clarity, reach and range of life safety communications.
(See how Genasys Emergency Management software adds a powerful and intuitive orchestration and management layer on top of existing physical and digital infrastructure—enhancing clarity, reach and range when managing critical events. Courtesy of Genasys Inc and YouTube.)
Genasys (Second of Two)
 Best Long-Range Acoustic Hailing Solution
Best Long-Range Acoustic Hailing Solution
-
LRAD 950NXT
-
The LRAD 950NXT is one of the world’s most advanced acoustic hailing device.

-
The 950NXT’s field upgradeable software has comprehensive functionality with easy-to-use controls.
-
The 950NXT enables operators to identify possible threats on the live video feed, position the 950NXT’s IP-addressable full pan & tilt to target the threat, and then broadcast attention-commanding warning tones and voice messages with exceptional clarity from the safety of a command and control center.
-
When integrated with radar or motion sensors, the 950NXT provides automated security alerts and becomes a fully functional, unmanned perimeter security and first response system that can alleviate the unnecessary use of force, resolve uncertain situations, and save lives.
(See a test demonstration of the LRAD 950-RXL System at the Davis Dam on the Colorado River about 70 miles downstream from Hoover Dam, and stretches across the border between Arizona and Nevada. Courtesy of Genasys and YouTube.)
-
*Genasys Inc. (formerly LRAD) has now been recognized as a Multiple ‘ASTORS’ Awards Champion for their Seventh Consecutive Year in the Annual ‘Homeland Security Awards Program. Thank you for your continued confidence in American Security Today.
Global Elite Group
Best Airport/Aviation Security Solution
-
Global Elite Airport/ Aviation Security Solution
-
Global Elite Group, a Securitas company, is a New York-based aviation security company offering protection for individuals, businesses, events, and properties worldwide.
-
The company oversees the security of over 60 clients across the aviation industry, including international and regional airlines.
-
Since Global Elite Group, was founded, a lot of growth has taken place, and this once-regional provider has a far-reaching reputation today for delivering outstanding value and a customized approach for each client’s needs.

-
Global Elite Group was acquired by Securitas Transport Aviation Services USA for USD $22 million, reflecting the growth and value of the company since it began.
Global Elite’s reputation outside of its aviation security offerings is excellent for delivering security services, emergency management, and consulting services to governments and businesses around the globe.
-
Global’s foundation offerings focus on aviation security, which makes up 95% of its business portfolio and has been the driver for developing a complete range of AVSEC services that are tailored to the express needs of each customer, from aircraft guarding and airside escorting, baggage pilferage investigations/prevention and cargo guarding, escorting & screening, to emergency response support, passenger behavioral assessments and verification, and even explosives/narcotics canine units.
-
*Global Elite Group has now been recognized for their Sixth Consecutive Year as an ‘ASTORS’ Award Champion in the Annual Homeland Security Awards Programs, respectively.
GrammaTech
Best SBOM (Software Bill of Materials) Solution
-
CodeSentry
-
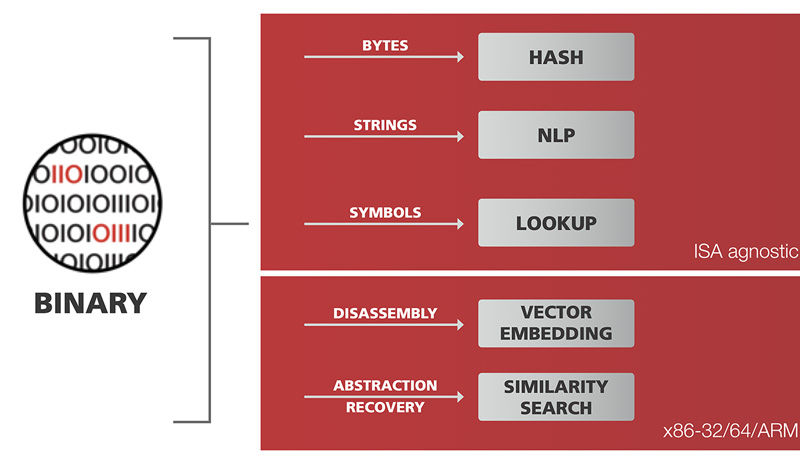
Enterprise organizations are using hundreds of pre-packaged
commercial-off-the-shelf (COTS) business applications for communication, project management, productivity, billing, HR/payroll, ERP, CRM, BI, and more using open-source software components to innovate faster, accelerate time-to-market and lower development costs; however, research finds that 100% of widely used applications contained vulnerable open source components.
-
The security risk to organizations from a vulnerable software supply chain is high. Hackers are actively exploiting vulnerabilities in widely reused open-source libraries within applications, and they have already leveraged apps like Slack, Zoom, Microsoft Office.
-
While organizations have traditionally trusted software vendors to manage security risk associated with the applications they produce, the increasing frequency of software supply chain attacks is forcing enterprises to proactively address risk themselves.
-
GrammaTech CodeSentry quickly analyzes COTS applications to identify the use of open source components and detects any associated security vulnerabilities. CodeSentry generates standard format SBOMs (SPDX and CycloneDX), derives a proprietary security score, and detects zero-day and N-day vulnerabilities, even when source code is unavailable.
-
CodeSentry features an easy-to-use upload interface and multiple output formats that are accessible to IT, risk, and security professionals without programming experience. For high-security businesses and government agencies, CodeSentry is available as an on-premises solution. Others can use the scalable, Software-as-a-Service (SaaS) option.
-
GrammaTech has extensive experience conducting advanced research in application security for defense agencies including the DOD, DARPA, Army and Navy. CodeSentry originated from one of these advanced research projects. GrammaTech’s researchers developed highly complex algorithms that can identify all software components, including custom code, vendor libraries, third-party code, and OSS for software mapping and look-up and N-day and zero-day vulnerabilities. These algorithms work even when source code is unavailable.
(At least 90% of corporations use third-party software, and 95% of proprietary or custom software applications they create contain third-party components. To overcome this blind spot in assessing third-party software inventory and risk, CodeSentry allows security professionals to measure and manage the risk associated with open source vulnerabilities in third-party software quickly and easily. Courtesy of GrammaTech and Youtube.)
-
*GrammaTech was also recognized in the 2021, and 2020 ‘ASTORS’ Homeland Security Awards Program.
guardDog .AI (First of Three)

Best Vulnerability Management Solution
-
guardDog AI-Powered Autonomous Detection and Response
-
For the first time, guardDog ai has provided the world with a cybersecurity system that is accessible to virtually everyone. It can see the risks device management solutions don’t cover and can thwart the attempted exploits it detects in less than 2 milliseconds.
-
guardDog.ai is a cloud-based software service plus a companion device that works together to simplify network security.
-
The solution exposes invisible threats on networks in ‘edge territory,’ and the devices attached to them, with patented technology to address and prevent cybersecurity threats before they compromise network environments.
-
guardDog’s Protective Cloud Services (PCS) is an AI-powered network security solution that doesn’t require cyber security expertise to operate.
-
Once activated, users’ Fido device goes to work by detecting threats and vulnerabilities on your network.
-
From there, the users’ cloud dashboard displays incidents by threat level and shows them information on how to resolve the issues before they become a problem.
(Learn More. Edge Territory is the invisible space between networks. For example connecting to a hotel or cafe Wi-Fi, or working from home can leave your sensitive or private data vulnerable. Any device on a network can also create openings for danger, such as a webcam or digital doorbell. guardDog makes the blind space visible. Combined with their AI-powered cloud solution, your guardDog device is always up to date, protecting you against the latest threats. With guardDog you can see the invisible threat and do something to stop it. Courtesy of Good Day Orange County and YouTube.)
guardDog Solutions (Second of Three)
Best Cyber Analytics Solution
-
No Cybersecurity Experience Required! guardDog.ai installation is a snap, and protection is a power light away.

-
Secure a home, a small office, a large enterprise, or any other organization with a cyber security management solution made easy that offers services to match the user’s needs.
-
How it Works: Unbox your Fido device, connect to your network, and register. From the moment the power light appears, protection begins. Fido gets to know your network and your devices.
-
It recognizes intruders and defends your network and devices. When someone attacks, it deploys automated countermeasures. User’s networks and devices are scanned vigilantly to protect against the known, and the unknown.
guardDog Solutions (Third of Three)
Best Threat Intelligence Solution
-
guardDog AI-Powered Autonomous Detection and Response
-
Coverage for “edge territory.” guardDog.ai make sit possible to detect and proactively thwart cybersecurity risks that device management can’t see – the threats in the edge territory that require an overlay that’s as simple as “plug and protect” for consumers and businesses.
-
It uses a cloud AI database to see and thwart attempted exploits before they can enter the network and succeed in planting virus, phishware or ransomware attempts.
-
The ability to thwart attempted exploits in less than 2 milliseconds. Every business, government, healthcare institution, home consumer, or other organization, is grappling to find security solutions that are adapt to this changing world. guardDog.ai is pioneering innovations that can truly meet these new and perpetual challenges.
-
Last year alone, there were over 12,000 new vulnerability exploits that emerged, and no human could really keep up with that.

-
guardDog’s ai-powered service learns about these attacks and keeps users’ Fido devices up to date.
-
The training never stops to prevent a crisis before it happens.
-
guardDog.ai has developed a cloud-based software service with a companion device that works together to simplify network security.
-
The solution exposes invisible threats on networks, and the devices attached to them, with patented technology to address and prevent cybersecurity threats before they compromise network environments.

-
*AST is delighted to welcome guardDog.ai, a 2021 ‘ASTORS’ Awards Champion, as a New Premier Awards Sponsor in the 2022 ‘ASTORS’ Homeland Security Awards Program.
Gurucul

Best Security Incident & Event Management Solution (SIEM)
-
Gurucul Next-Gen SIEM
-
SIEM plays a major role for enterprises looking to reduce the overall security attack surface (and false positives) and resource burdens on security teams. But as attackers get more sophisticated and networks more complex, SIEM tools must evolve as well.
-
The conventional SIEM paradigm presents Events and Incidents, as identified by rules-based analytics, without context. But Gurucul takes a different approach to SIEM.

-
Gurucul’s Next-Gen SIEM is cloud-native, built for speed and scale, and helps to modernize security operations by delivering ultra-high-fidelity detection and automated response. It leverages over 2500 Machine Learning Models powered by data science to produce actionable risk intelligence, and doesn’t rely on signatures, rules, or patterns.
-
It allows organizations to identify zero-day threats in real-time and is designed to provide both contextual and situational awareness to detect and stop malicious behavior before cyber criminals or rogue insiders can do harm.
-
Gurucul’s Next-Gen SIEM includes a variety of key features, including a cutting-edge lightweight SaaS architecture with cloud elasticity and predictable costs, real-time threat detection, the industry’s most advanced data-science powered Machine Learning behavior analytics, and the market’s most diverse security content library.
-
Furthermore, its advanced and intuitive UX provides contextual investigation and intelligent timeline views, blazing fast searches, and risk-based responses. The open, flexible, and extensible platform also unifies SIEM, XDR, UEBA, SOAR, NTA, and Identity and Access Analytics with a single seamless and consolidated view. It supports an open choice of big data repositories and can be deployed flexibly on any leading big data infrastructure.

-
This protects existing IT investments, eliminates data duplication, and reduces storage fees. Customers can simply layer Gurucul’s advanced security analytics engine on top of their existing or new Hadoop, Cloudera, Hortonworks, MapR and Elastic/ELK deployments.
-
Finally, Gurucul’s Next-Gen SIEM is built to scale. Many agencies have over 250,000 employees. One health insurance customer uses Gurucul to analyze 8 million identities and 500 big data nodes. Another health insurer is using Gurucul to apply advanced analytics to over 15 million identities belonging to employees, partners and customers, and a large financial institution has deployed Gurucul advanced security analytics with its custom cloud big data lake on AWS to risk score access and activity, reduce access risks, and detect unknown threats.
-
*Gurucul is a returning ‘ASTORS’ Award Champion, having secured Wins in the 2020, 2019, 2018, and 2016 Homeland Security Awards Programs, respectively.
Hanwha Vision
 Best Thermal, Infrared Camera Solution
Best Thermal, Infrared Camera Solution
-
TNM-C4960TD Bi-Spectrum Camera
-
The TNM-C4960TD Bi-spectrum camera is part of Hanwha Vision’s continually expanding line of dual-head, visible sensor/thermal imaging-based cameras.

-
The product family includes models for indoor electronic body temperature monitoring to new devices suited for outdoor applications, including transportation, traffic monitoring, and refineries.
-
Using a thermal imager makes a camera like the TNM-C4960TD well-suited to the “always-on” 24/7 monitoring requirements of many government applications, especially in no light or challenging conditions, such as nighttime, fog, or extreme weather. Like all Hanwha Techwin products, the camera is NDAA-compliant.
Key features of the TNM-C4960TD include a built-in 25mm fixed lens (FoV: 17.4° thermal) and 10.9~29mm motorized varifocal lens (FoV: 42°~15° visible), triple codec-compatible (H.265/H.264/MJPEG), Wise Stream III (visible), WiseStream II (thermal), and
Wide Dynamic Range of 120dB.
(Meet Hanwha Vision’s new Bi-Spectrum AI Thermal Cameras! (TNM-C4960TD, TNM-C4950TD, TNM-C4940TD). Courtesy of Hanwha Techwin America and YouTube.)
-
*Hanwha Vision (formerly Hanwha Techwin America) was also recognized as a Multi ‘ASTORS’ Awards Champion in the 2021, 2020, 2019, and 2018 Security Awards Programs.
High Rise Escape Systems
Best Disaster Preparedness, Disaster Recovery System
-
Guardian Evacuation System
-
The Guardian Evacuation System developed a fixed and/or portable escape system to attach to a structure, designed to mitigate means of egress for anyone living or working above the 2nd floor, including: government buildings, embassies, barracks, hospitals, air traffic control towers, apartments, condominiums, hotels, industrial and job sites, theme parks, cranes, oil platforms, ships and more.

-
High Rise Escape Systems (HRES) accomplished this in a combination of several simple, low-tech devices that require no power, are inexpensive, have a long shelf-life and are easy to use.
-
Using a Controlled Descent Device (CDD) which works like a pulley, a user slides a one of two permanently attached escape harnesses over them, exits off of a balcony/roof structure or out of a window and the CDD slowly lowers them automatically at the rate of 3 feet per second.
-
As the first user descends, the opposite end of the cable automatically retracts and reloads the CDD with the remaining escape harness for the next evacuee.
-
Then the process repeats. Everyone gets out.
-
The United States Military has been utilizing High Rise Escape Systems Guardian Escape Systems on Air Traffic Control Towers for years, which includes the Ellsworth AFB, Dyess AFB, Vandenburg AFB, Edwards AFB, Tinker AFB, Maxwell AFB and Patrick AFB as well as Army and Air National Guard installations such as Alpena CRTC, Grayling Air Gunnery Range & Selfridge ANG.
(See the HRES device in action as designed for the Dyess AFB ACT Tower which is much safer than taking the stairs or the elevator. Courtesy of Dyess AFB & YouTube.)
-
*HRES has now been recognized as an ‘ASTORS’ Award Champion in its Sixth Consecutive Homeland Awards Programs, respectively.
Horizon3.ai
 Best Cyber Analytics Solution
Best Cyber Analytics Solution
-
NodeZero
-
The mission of Horizon3.ai is to help organizations find and fix attack vectors before bad actors can exploit them.
-
NodeZero is an autonomous penetration testing platform, which continuously assesses an enterprise’s attack surface, identifying ways an attacker could chain together harvested credentials, misconfigurations, dangerous product defaults, and exploitable vulnerabilities to compromise systems and data.
-
Most security tools are noisy and full of false positives, requiring persistent credentialed agents and imposing an enormous training and maintenance demand on IT and security teams. Meanwhile, security teams are overwhelmed with non-contextual reports and dashboards, which wastes a lot of valuable time and resources chasing vulnerabilities that don’t pose a real threat to their business.
-
NodeZero is a true self-service SaaS offering that is safe to run in production and requires no persistent or credentialed agents.
(See how NodeZero provides continuous autonomous penetration testing as a true SaaS offering. With NodeZero, our autonomous penetration testing solution, cybersecurity teams can proactively find and fix attack vectors before attackers can exploit them. Courtesy of Horizon3 AI and YouTube.)
-
NodeZero can help organizations identify ineffective security controls and ensure limited resources are spent fixing problems that can actually be exploited, giving IT administrators and network engineers ‘security superpowers,’ to operate like ethical hackers with 20 years of experience and act as a force multiplier for MSP and MSSP partners.
-
*NodeZero is a new competitor to the 2022 ‘ASTORS’ Homeland Security Awards Program.
Hornetsecurity
 Best Email Security Solution
Best Email Security Solution
-
365 Total Protection Enterprise Backup
-
68% of companies expect Microsoft 365 to keep them safe from email threats, yet 50% use third-party solutions. There seems to be a disconnect between the expectations that businesses have of Microsoft 365’s email security, and the reality: While 2 out of every 3 expect Microsoft to keep them safe from email threats, half of all respondents resort to third-party solutions to supplement email security, and 82% of all respondents who use third-party email security solutions reported no breaches.
-
Companies and organizations worldwide need to protect their data against the ever-evolving slew of cyber-attacks that their employees can fall victim to, the bulk of which are sent by email.
-
Therefore, it is critical for them to have a robust cloud security system that provides comprehensive email protection combined with backup, disaster recovery, and business continuity functionality.
(Learn More. Hear from Andy Syrewicze, Technical Evangelist, Microsoft MVP and VMware vExpert, as he takes us through and identifies if the basics are enough to secure your Microsoft 365 email inbox. Courtesy of Hornetsecurity and YouTube.)
-
Hornetsecurity meets this need by providing a complete email security, backup, and recovery solution that sets their minds at rest: 365 Total Protection Enterprise Backup.
- *Hornetsecurity is a new competitor in the 2022 ‘ASTORS’ Homeland Security Awards Program.
i-PRO Americas
 Best Vehicle Mounted Law Enforcement Solution
Best Vehicle Mounted Law Enforcement Solution
-
i-PRO WV-VCF41P 4K Sensor Panoramic In-Car Front Camera for Law Enforcement Vehicles
-
The i-PRO WV-VCF41P is a new 4K Panoramic Front Camera for police vehicles. A component of i-PRO’s powerful ICV4000 in-car video (ICV) system, the new camera is ideal for law enforcement agencies seeking wide-angle coverage and high-resolution capture of video evidence from the vehicle.

-
Unlike traditional forward-facing cameras, the WV-VCF41P provides a full 150-degree field of view. The innovative lens is specifically designed to minimize distortion and edge warping, resulting in the widest angle offered. Behind the lens, the camera’s 4K sensor is i-PRO’s highest resolution sensor for mobile video evidence applications. This advanced lens and sensor combination accurately records events as they unfold across the entire scene in front of the vehicle. With support for detailed forensic zooming into areas of interest without image blurring, the WV-VCF41P presents the clearest possible evidence.
-
Policing with an in-car video system is more demanding than ever, with the expectation that each interaction and event will be captured on video. Many in-vehicle cameras offer a limited field of view between 55 and 85 degrees, and are unable to record what occurs to the extreme left and right of the central focus.

-
The compact design of the versatile WV-VCF41P fits behind the rearview mirror so it does not obstruct the driver’s view. Its 32:9 aspect ratio image reduces storage requirements by cropping away unnecessary areas, such as the sky or a vehicle’s hood, allowing agencies to concentrate on the relevant parts of the evidence. A simple Power over Ethernet connection allows for easy installation, and a built-in G-force sensor provides automatic activation upon impact which reduces the cost and complexity of installing a separate sensor.
-
*i-PRO Americas is a new competitor in the 2022 ‘ASTORS’ Awards Program.
iboss
Best Cyber Analytics Solution
-
iboss Zero Trust Edge Cloud Security Platform
-
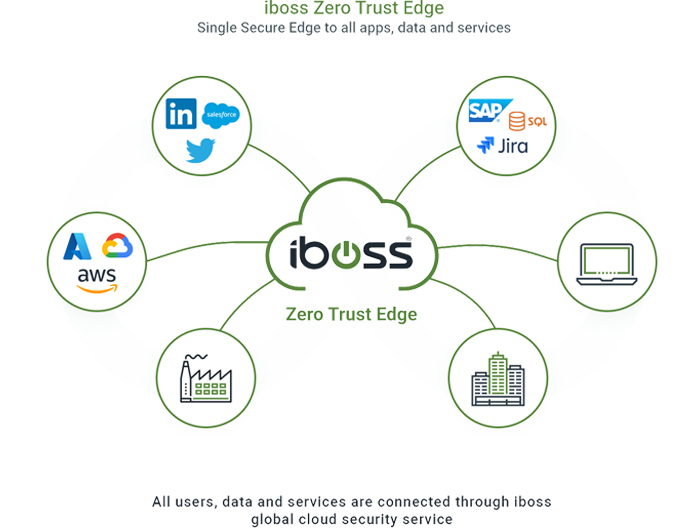
The iboss Zero Trust Edge is a pure implementation of the NIST Zero Trust Architecture defined in the NIST 800-207 publication.
-
Zero Trust allows organizations to protect their resources, including applications, data, and services, by ensuring access to those applications is only possible through a security service edge.
-
The iboss cloud is a Zero Trust platform that sits in front of all resources and only allows approved users to connect to those resources, ensuring that no application, data, or service is directly accessible and protects organizations from data loss and breaches.
-
The iboss platform also makes it possible for users to access applications and resources from wherever they work and wherever the resource is located, making access to information seamless and transparent to end-users while ensuring an organization gets the visibility and protection required to ensure they are reducing risk and increasing their security posture.
-
The transition to Zero Trust allows organizations to move from perimeter-based security, or a castle-and-moat security strategy where protection is centered around buildings, to a world where security is baked into each and every connection to every resource being accessed by those who need it.
(Hear from Paul Martini, iboss CEO and CTO, on how to securely connect your modern workforce to data from anywhere using any device. Courtesy of iboss and YouTube.)
-
*iboss was also recognized in the 2021, and 2020 ‘ASTORS’ Homeland Awards Program.
INKAS® Aerospace and Defense (First of Two)

Best Emergency Vehicle Solution
-
The INKAS® Sentry is a multi-purpose, multi-terrain vehicle that is actively used worldwide by government organizations, law enforcement agencies, border control agencies, command and control operations, armored personnel troops, emergency medical crews, SWAT teams, and more.

-
Designed from the ground up as a multi-purpose tactical and emergency vehicle, the INKAS® Sentry is a unique and innovative vehicle, precision-engineered to ensure passenger safety in volatile situations.
-
The Sentry features flexible interior configurations to suit the tactical seating arrangements of active-duty personnel and can integrate a vast array of equipment and systems into one complete solution that can be deployed and operated directly from the vehicle – enabling tactical teams to respond faster in time-sensitive scenarios that involve hostages, criminals, terrorists, or active emergencies where lives may be at risk.
-
Each vehicle can be customized according to the mission’s requirements. From tactical intervention in hostage situations and counter-terrorism operations to medical evacuations and rescue operations in remote and dangerous regions, to fully integrated mobile command centers – the INKAS® Sentry can be tailored to suit the needs of each client and mission. Its high level of flexibility ensures that teams have access to a mission-ready tactical vehicle, fully equipped to handle any emergency at all times.
(The INKAS® Sentry APC is a defense vehicle designed to serve in extreme climate conditions. Specifically designed for SWAT, law enforcement and border patrol agencies, the Sentry APC is powered by a 6.7L V8 Diesel engine with six-speed manual transmission and is characterized by a high level of off-road performance. Courtesy of Inkas Armored and YouTube.)
INKAS® Aerospace and Defense (Second of Two)
Best Vehicle Mounted Security Systems
-
INKAS® Signal and Drone Jamming System
-
Optionally integrated into INKAS’ famous high-security armored vehicles, the INKAS® Signal and Drone Jamming System enables convoys and units to be fully aware of their surroundings, and maintain 360-degree protection at all times from threats such as hidden IED bombs and landmines, ambushes with firearms, and unfriendly drones within the operational area.

-
INKAS® Aerospace and Defense is continually developing new solutions and expanding the capabilities of its comprehensive signal jamming systems, which interrupt mobile, satellite, radio, GPS signals, and more – protecting vehicles carrying government officials, law enforcement officers, emergency responders, special forces, military, and VIP individuals from countless threats. While the systems are highly portable, they can also be used to protect stationary facilities, of any kind.
-
Combining state-of-the-art technology with field-proven systems, INKAS delivers an innovative solution that leverages ultra-broadband vehicle-integrated jammers which are capable of simultaneously interrupting signals between 20M Hz and 6,000M Hz, with consistent coverage across all bands and frequencies. The jammers continuously emit a wide variety of signals concurrently to interrupt cellphone signals to deactivate IED bomb detonation, interrupt GPS signals to prevent tracking, interrupt WiFi signals to neutralize and disarm unmanned drones, and more, with many more sophisticated solutions available upon request.
-
Tailored to the requirements of each specific client, INKAS offers various configurations of bands, jamming techniques, output power, and advanced features such as high-gain Omnidirectional antennae that provide full coverage and continuous protection in all weather and road conditions.
-
INKAS® is a new competitor in the 2022 ‘ASTORS’ Homeland Security Awards Program.
Intelligent Waves
 Best Network Management Solution
Best Network Management Solution
-
Phantom Next Generation Cyber-Defense Solution
-
Intelligent Waves (IW) has introduced several leading-edge disruptive cybersecurity innovations.

-
Phantom provides the ability for organizations to access foreign points of presence to conduct remote open-source information gathering and research while at the same time protecting organizations and individuals from exposure to foreign intelligence, achieved by combining the GRAYPATH software-defined obfuscated network with the managed attribution capability of the Phantom platform in a secure but unclassified package.
-
Phantom Next-Generation is unique in that it provides the U.S. Department of Homeland Security, Department of Defense, and Special Operations the ability to access foreign points of presence to gather open-source information and do research while protecting organizations and individuals from foreign intelligence.

-
Additionally, due to its secure, cloud-based nature, the unclassified telework capability does not require access to a classified facility or network. As such, government cyber-defense agencies can utilize a globally mobile workforce more effectively. Phantom enables “anonymous browsing” of remote internet services from any location, by securing access and managing public network attribution, effectively increasing operational security while reducing risks to private networks and assets.
-
*Intelligent Waves was also recognized in the 2021 ‘ASTORS’ Awards Program.
IPVideo Corporation (First of Four)
Best Sound & Chemical Incident Detection
-
HALO 3C IoT Smart Sensor
-
HALO SMART SENSOR 3C has expanded security features to include a Panic Button, 2-way Audio Communications, Emergency Escape and Alert Lighting, Motion Detection, and People counting while still maintaining individual privacy.
-
These innovative new solutions add to the existing award-winning security features of gunshot detection, noise alerts, and emergency keyword alerting and still does not any form or camera or record audio – making it the perfect security add-on to address facility privacy areas and protect the privacy of the individual.
(Learn how the HALO IOT Smart Sensor will detect vape in bathrooms, locker rooms, etc. HALO Smart Sensor can monitor the air in your facility for chemicals, temperature, quality, and more! Courtesy of IPVideo Corporation and YouTube.)
IPVideo Corporation (Second of Four, Plus Two 2022 New Product of the Year Awards)
Best Indoor Emergency Help Station/Technology
-
The HALO IOT Smart Sensor 3C is the third evolution of the product, which had originally gained notoriety as the #1 Vaping and Vaping with THC detection device, and allows its users to capture comprehensive Health, Safety, and Vaping awareness with an all-in-one device.

-
Used for health and safety, HALO is a vape detector, an air quality monitor, and a complete security device for privacy areas where you do not want to use a camera or microphone.
-
With a single device HALO provides; Building Health Monitoring, Indoor Air Quality Monitoring, Vape Detection, THC Detection, Gunshot Detection, Emergency Key Word Alerting, Audible Alerting, Panic Button Alerting, triggered 2-way Audio Communications, Emergency Escape and Alert Lighting, Motion Detection, Occupancy Alerting, Chemical Alerting, VOC Alerting, Tamper Alerting as well as Light Level, Temperature and Humidity Alerting.
-
The HALO IOT Smart Sensor 3C was also recognized with a 2022 ‘ASTORS’ Best New IoT Product of the Year Award.
IPVideo Corporation (Third of Four)

-
Best Security Operations Center (SOC)
-
Virtualguarding.com
-
VirtualGuarding.com was formed through a longstanding partnership of experienced technology, law enforcement, and security guard firms, to provide clients with constant 24/7 security, at the fraction of the cost of traditional security guards.

-
VirtualGuarding .com serves a wide variety of markets, including K-12 schools, higher education, healthcare, municipalities, HOAs, gated community, car dealerships, commercial buildings, and many more.
-
With the expertise, technology, and mindset cultivated by years of experience, VirtualGuarding.com provides your business with the best remote technology solutions, backed by extensive support and peace of mind knowing your facility is utilizing 24/7 monitoring by top professionals.
-
Your facility receives 360 degrees of security with advanced features such as immediate live audio trespasser deterrents, remote door monitoring for unsecured entrances and exits, and the hybrid use of human intelligence and artificial intelligence.
(VirtualGuarding is a new, remote guarding service that combines in-person security guards paired with advanced video analytics to help better protect your property. Courtesy of VirtualGuarding and YouTube.)
-
If immediate assistance is needed, the company’s highly trained remote security guards address events by utilizing two-way communication, dispatching an on-site guard, or dispatching local law enforcement authorities.
-
Emergency applications can also be applied for communication via smartphones to any employee or resident. With VirtualGuarding.com, they guard more, you spend less.
IPVideo Corporation (Fourth of Four)

-
Best Vehicle Mounted Security Systems
-
VURO AI
-
VURO AI (VuroAI Smart Video Telematics) is LIVE AI-powered video monitoring of vehicles and their drivers.

-
Improve Driver Safety with VURO AI: Drivers are monitored by our AI-powered detection algorithms. Dangerous behaviors like drowsiness, distraction, cellphone usage, harsh acceleration, and harsh deceleration will trigger alerts to both the driver and the fleet manager in real time.
-
Identify Drivers: Facial recognition technology is used to verify the identity of registered drivers at the start of the trip, during the trip, and when incidents happen and protect fleets and insurance companies from liability issues.
-
Event-Trigger Button: An event-trigger button allows the driver to send an immediate email notification of a driving event and auto-upload an immediate video clip to the cloud.
(See the ViewScan from IPVideo Corporation, a completely passive weapons detection system that emits no radiation and is safe for anyone to walk through. Courtesy of IPVideo Corporation and YouTube.)
-
VURO AI Smart Video Telematics was also recognized with a 2022 ‘ASTORS’ Best Driver Safety Product of the Year Award.

-
*Recognized as a Multiple ‘ASTORS’ Awards Champion in the 2021, 2020, 2019, and 2018 ‘ASTORS’ Awards Programs, AST is delighted to welcome *IPVideo Corporation as a New Premier Awards Sponsor to the 2022 ‘ASTORS’ Homeland Security Awards Program.
Iris ID Systems
Best Facial/Iris Recognition System
-
IrisBar 600 -Advanced Multi-Biometric OEM Module
-
The all-new IrisBar from Iris ID is the latest product release designed to help travelers skip the hassle when they need to identify and authenticate.

-
It was created in response to industry insiders communicating a need for a product to deliver an efficient user experience. Ready for enrollment programs and security check in’s including at the airport or for immigration, the iBAR 600 is a complete and seamless OEM module that streamlines the verification process.
-
With an impressive capture volume, the multimodal iris & face collection iBAR 600 is adept at providing crisp and accurate images at various angles – even capturing someone in a wheelchair.
-
Upon kiosk approach, users will meet an intuitive and user-friendly 1.3″ circular LCD interactive screen, it instinctively attracts a user’s eyes to begin the identification process. With activation, cameras on the LCD zoom and out, and subtitles are featured on the bottom of kiosk screens as an additional instructional guide.
-
The iBAR600 is a smart, image capture standards-compliant biometric system designed to work with a legacy kiosk or gate implementation within aviation or transportation sectors. Other applications include national ID, Border Control, and ATM/VTM.
(See the new IrisBar from Iris ID designed to help travelers skip the hassle when they need to identify and authenticate. Ready for enrollment programs and security check in’s at airports or for immigration, the IrisBar is a complete and seamless OEM module that streamlines the verification process. Courtesy of Iris ID Systems and YouTube.)
-
*Iris ID was also recognized as an ‘ASTORS’ Awards Champion in the 2021, 2020, 2019, 2018, and 2016 Annual Awards Programs.
Kingston Technology (First of Three)

-
Best Data Storage Security Solution
-
IronKey Vault Privacy 80 External SSD
-
As innate as unlocking a smartphone and simple drag & drop file transfers, Kingston IronKey Vault Privacy 80 External SSD (IKVP80ES) is designed to protect data while being user-friendly.

-
Featuring an intuitive color touch-screen and multi-password (Admin and User) option with numeric PIN or passphrase modes, IKVP80ES is superior to using the internet and Cloud services to safeguard data.
-
The IKVP80ES drive is FIPS 197 certified with XTS-AES 256-bit encryption using a Common Criteria EAL5+ (CC EAL5+) certified secure microprocessor and is TAA compliant.
-
IKVP80ES makes for the perfect companion when you need secured data and content out in the field or on the go to enable portable productivity and convenience all in the palm of your hand.
(Meet the IronKey Vault Privacy Encrypted External SSD with Touch Screen Keypad – IronKey Vault Privacy 80 External SSD. Courtesy of Kingston Technology and YouTube.)
Kingston Technology (Second of Three)

-
Best Secure Data Storage for Military and Government
-
IronKey Vault Privacy 80 External SSD
-
The IronKey Vault Privacy 80 External SSD (IKVP80ES) is Kingston’s first innovative OS-independent hardware-encrypted external SSD with touch screen for data protection.

-
IKVP80ES safeguards against Brute Force attacks and BadUSB with digitally-signed firmware. Brute Force attack protection crypto-erases the drive if the Admin and User passwords are entered incorrectly 15 times* in a row by default.
-
Admin can enable a User password and set up security options, such as configuring password requirements by setting the maximum number of shared attempts, minimum password length of 6-64 characters, and alphanumeric password rules with the IKVP80ES.
-
Additionally, you can utilize the ‘space’ character making it easier to remember a passphrase as a list of words, a memorable quote, or lyrics from a favorite song.
-
Otherwise, use the IKVP80ES PIN pad to unlock just as you would on a mobile device and to reduce failed login attempts and frustration by tapping the “eye” button to view the password as entered.
-
As an added feature, when a User password is forgotten, the Admin password can be used to access data and restore User access to the IKVP80ES.
Kingston Technology (Third of Three)

-
Best Encryption Solution
-
IronKey Vault Privacy 80 External SSD
-
Whether it’s sensitive government business, important company information, client documents, or high-res images and videos, the IKVP80ES drive is ideal for small-to-medium businesses (SMB) to content creators.
-
IKVP80ES comes bundled with two USB 3.2 Gen 1 adapter cables, USB Type-C®2 to Type-A and Type-C to Type-C, to allow for easy connection to computers and other devices.
-
IKVP80ES makes for the perfect companion when you need secured data and content out in the field or on the go to enable portable productivity and convenience all in the palm of your hand.
(Take a look at the additional features and menu options available with the IronKey Vault Privacy 80 External SSD. Courtesy of Kingston Technology and YouTube.)
-
*Kingston Technology was also recognized in the 2020, 2019, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Konica Minolta Business Solutions
Best Integrated Security Management System (Plus 2022 New Product of the Year)
-
FORXAI Secure Access
-
FORXAI Secure Access enables automated, secure point-of-entry workflows that combine facial identification with mask detection, thermal temperature screening, and tailgating.

-
These workflows utilize an artificial intelligence (AI) rules-based engine designed for various types of government organizations.
-
Developed by Konica Minolta’s North American Business Innovation Center with support from Konica Minolta Labs U.S., FORXAI Secure Access leverages the intelligent edge capabilities of the company’s MOBOTIX security cameras, internally developed AI algorithms, innovative facial recognition technology, and system integration solutions.
-
This convergence of technologies offers clients a comprehensive, flexible solution that guards against unauthorized access, automates the access process for authorized staff, residents, constituents, and visitors, and provides additional capabilities related to virus prevention and reporting.
-
FORXAI Secure Access provides an extensible platform that can be tailored to the specific needs of the facility.
(How can you improve your video security? Make sure you have high-resolution images, a wide field of vision, detection features, and so much more with the FORXAI Video Security Solution for your monitoring, secure access, and optimal oversight of your facilities and operations. Courtesy of KonicaMinoltaUS and YouTube.)
-
With intelligent internet-protocol (IP) design, Konica Minolta customizes its Intelligent Surveillance options to proactively address your monitoring and security needs – indoor, outdoor, in low light, in challenging weather conditions, or with thermal imaging – to ensure you have visibility to all activity around your buildings and their perimeters.
-
The company’s smart systems and intelligent video streaming capabilities allow for maximum coverage and maximum security.
-
FORXAI Secure Access was also recognized with a 2022 ‘ASTORS’ Best New Monitoring Product of the Year Award.
-
*Konica Minolta Business Solutions has now been recognized as an ‘ASTORS’ Awardss Champion for its Sixth Consecutive Year in the Annual ‘Homeland Security Awards Program.
Liberty Defense
Best Metal/Weapons Detection Solution (**Tie)
-
HEXWAVE
-
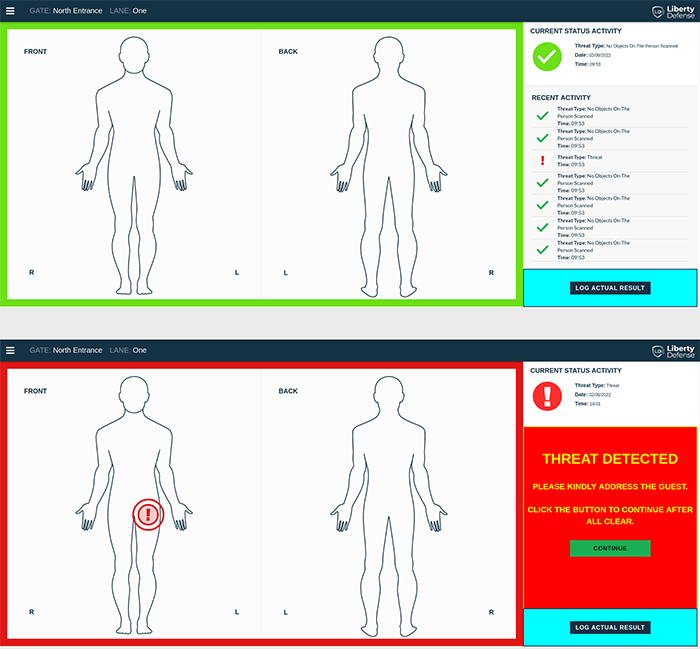
Utilizing advanced imaging technologies along with AI and deep learning algorithms to provide automatic threat detection technology, HEXWAVE is a next-generation security screening solution that goes beyond metal detectors to allow for the detection of non-metallic improvised threats, as well as novel threats of tomorrow.
-
HEXWAVE is a walkthrough security people-screening portal that automatically detects hidden weapons and other potential threats, including both metal and non-metal items such as 3D-printed ghost guns, as well as improvised liquid, powder, or plastic explosives.
-
HEXWAVE uses millimeter wave, video-rate 3D imaging, and Artificial Intelligence technologies to detect potential threats, providing security operators with a real-time, automatic go/no-go decision.
-
Guests, employees, or passengers do not need to divest cell phones, keys, wallets, or jackets when passing through the system, providing a quicker and more seamless security experience.
-
Other items of interest can also be detected by training the AI algorithms to detect objects that should not be brought in or out of secure locations.
(Many Americans can’t remember going through an airport that didn’t include enhanced security measures. While mostly effective in keeping people safe, they are time-consuming and inconvenient. After the terror attacks of 9/11, the security protocol in airports changed, but many of the enhanced measures evolved over time. Courtesy of CBN News and YouTube.)
-
Liberty Defense is currently testing its technology onsite with a Major League Baseball (MLB) stadium, a large state university, one of the largest Hindu temples in North America, one of the top US airlines, and major international airports.
- *Liberty Defense is a returning ‘ASTORS’ Awards Champion having secured a Win in the 2019 Homeland Security Awards Program.
LogRhythm
Best Security Incident & Event Management Solution (SIEM)
-
LogRhythm SIEM
-
With LogRhythm’s SIEM Platform, customers can mature their security operations and protect their critical assets, by delivering comprehensive security analytics; security information and event management (SIEM); user and entity behavior analytics (UEBA); network detection and response (NDR); and security orchestration, automation, and response (SOAR) within a single, integrated platform for rapid detection, response, and neutralization of threats.
-
These capabilities deliver rapid time-to-value from day one, significantly reducing the mean time to detect (MTTD) and mean time to respond (MTTR) to threats from weeks or months to hours or days.
-
LogRhythm’s SIEM Platform enhances the analyst experience and visibility while simultaneously simplifying the process of onboarding cloud and on-prem data sources for more holistic monitoring.
-
LogRhythm is continuously improving the LogRhythm SIEM Platform, and its 2022 version releases provide new features designed to help security teams overcome everyday obstacles by simplifying deployment, abridging data collection, enhancing detection capabilities, automating routine tasks, and improving the analyst experience.
-
The results of this security-first, customer-centric approach not only set LogRhythm apart from other vendors in the industry; they set LogRhythm’s users apart from other organizations with cybersecurity initiatives.
(Learn More about the LogRhythm SIEM Platform. Courtesy of BitLyft and YouTube.)
-
LogRhythm participated in a Total Economic Impact Study of the LogRhythm SIEM Platform conducted by Forrester Consulting, which revealed organizations using the platform realize an average return on investment (ROI) of 258% over a three-year period, allowing the platform to pay for itself in less than six months.
-
*LogRhythm is a new competitor to the 2022 ‘ASTORS’ Homeland Security Awards Program.
Mimecast (First of Two)
 Best Phishing Defense Solutions
Best Phishing Defense Solutions
-
Mimecast Awareness Training
-
Hackers experience considerable success by taking advantage of the remote and hybrid workforce. Mimecast’s State of Email Security Report found that 75% of companies were hurt by a ransomware attack last year.

-
As hackers begin to redefine their tactics, stepping up their attacks and taking advantage of the increased number of attack vectors at their fingertips, Mimecast Security Awareness Training (AT) platform offers creativity and humor that keep end users engaged from start to finish, and research found employees who receive consistent cyber awareness training are five times more likely to spot and avoid clicking on malicious links.
-
Developed by top leadership from the U.S. military, law enforcement, the entertainment industry, and the intelligence community, Mimecast AT is developed with tactical security tests, like mock phishing emails, to test employee knowledge about cybersecurity best practices.
-
Mimecast AT educational videos cover various topics on phishing, remote/hybrid work, passwords, PII privacy, PCI, HIPAA, ransomware, CEO/wire fraud, data in motion, office hygiene, and GDPR, among others. The platform also collects insights on knowledge, behavior, and sentiment.
(With up to 95 % of security breaches involving human error, only 11% of global companies conduct monthly security awareness training. See how to target your weakest link – human error – with Mimecast’s fun-loving Awareness Training modules. Courtesy of Mimecast and YouTube.)
-
With human error involved in 90%+ of all security breaches, Mimecast AT combines video content with tactical security tests to help organizations across all industries and sizes reduce security risks associated with employee human error, and additionally data collected from training modules indicate the risk of human error, which is then used to provide additional training for employees who need it most.
Mimecast (Second of Two)
Best Email Security Solution
-
Mimecast X1 Platform
-
Mimecast’s X1 Platform provides world-class email security efficacy built on 20 years of experience.
-
With the processing of 2.4 billion emails daily, Mimecast gains visibility and holds the industry’s most robust view of the email threat landscape.
-
Mimecast’s X1 Precision Detection is engineered to apply the latest advancements in AI and machine learning to enable intelligent detection of emerging and unknown threat types, and the filtering out of malicious emails optimizes the efficacy of Mimecast’s AI and Machine Learning along with aiding their experts in making smart decisions about communications that fall into the gray area between safe or malicious.
(Whether you’re looking for robust (Secure Gateway) or agile (Cloud Integrated) Email Security that can support any email environment, see how you can find it from Mimecast Email Security & Resilience solutions. Courtesy of Mimecast and YouTube.)
-
Mimecast aims to stop bad things from happening to good organizations, and with the adoption of Mimecast’s X1 solution, 40,000 customer organizations and their employees can Work Protected™.
-
The combination of Mimecast’s reliance on digital dependency and threat actor behavior is core to their mission.
-
Mimecast X1 is the foundation of the Mimecast Product Suite, and powers fully integrated services that deliver industry-leading protection for communications, people, and data, making information actionable, and providing the reliability, resilience, and scale that the modern threat landscape demands.
-
Mimecast is a new competitor to the 2022 ‘ASTORS’ Homeland Security Awards Program.
MSA Security®, An Allied Universal® Company
Best Gunshot Detection Solution
-
Firearms Detection Canine Teams
-
MSA Security Firearms Detection Canines (FDCs) are trained to detect odors associated with firearms, whether they have been previously fired, recently cleaned, or never fired at all, and include cleaning solvents, oils, and holster materials for an effective and versatile solution.

-
Beyond their accuracy, canines are not limited by power cords, battery access, or adverse weather conditions; they create a strong deterrent and can be deployed in any number of scenarios to meet the needs of the evolving threat spectrum.
-
Each MSA Firearms Detection Canine is paired with a qualified handler with law enforcement or military experience, and they work together for the entirety of their careers, ensuring a strong working bond and the most effective response to the presence of an unauthorized firearm.
-
FDC Teams are mobile, dynamic, and responsive to the threat. Should the canine detect an odor associated with a firearm, it will track the scent and follow it to the source, providing a passive “sit” indication, or a behavior change. At this point, the handler will follow the client’s predetermined security protocols, with the ultimate goal of preserving life safety.
(Learn why you’ll find MSA Canine Detection Teams working everywhere sniffing out potential threats from both stationary and mobile explosive odors in professional sports stadiums, airports, amphitheaters, cargo facilities, loading docks, and more. Courtesy of MSA Security and YouTube.)
-
MSA Security has led the security industry for thirty-five years with the highest caliber Explosive Detection Canine teams in the private sector, and their canine trainers and security experts diligently monitor the threat spectrum and tailor their solutions time and again to address the latest trends and tradecraft.
-
In addition to all the firearm-specific odors listed above, canines are trained to detect all five families of commercial and military-grade explosives and homemade explosives frequently used by hostile actors. As the threat spectrum continues to evolve, MSA will continue to refine and enhance our canines to meet the security needs of the moment, from gunshot detection to explosive detection and beyond.
-
MSA Security® is a new competitor to the 2022 ‘ASTORS’ Awards Program; however, Allied Universal® has been recognized for the last Four Consecutive Years in the Annual Homeland Security Awards Program.
View Part 1 Winners A – Da NEXT View Part 3 Winners N – Sl
View Part 4 Winners So – Z View Part 5 Government Excellence
Part 6 Innovation & Leadership
The 2022 ‘ASTORS’ Awards Program was Proudly Sponsored by NEC National Security Systems (NSS), ATI Systems, Automatic Systems of America, guardDog AI, Fortior Solutions, IPVideo Corporation, Rajant Corporation, RX Global, and SIMS Software!
- **IN A RARE TIE Event (thrice occurring) is a result of either extremely differing objectives and/or very similar technology applications.





















