SlashNext, a leader in real-time phishing site detection for businesses, and a 2018 ‘ASTORS’ Homeland Security Award Winner for Best Phishing Defense Solutions, has released new survey results suggesting a dangerous lack of understanding, and widespread gaps in protection against modern, fast-moving phishing attacks.
 A revealing analysis of cybersecurity decision-makers survey data, shows that most companies lack adequate safeguards against phishing threats on the internet and many don’t fully understand the prevalence and risks of this growing threat.
A revealing analysis of cybersecurity decision-makers survey data, shows that most companies lack adequate safeguards against phishing threats on the internet and many don’t fully understand the prevalence and risks of this growing threat.
As such, most organizations are disturbingly in the dark when it comes to understanding their exposure to modern phishing tactics, and in evaluating what solutions are required to keep employees protected and to reduce the risk of breaches.
The SlashNext 2018 Phishing Survey reveals that 95 percent of respondents underestimate how frequently phishing is used at the start of attacks to successfully breach enterprise networks.
Only 5 percent of respondents realize that phishing is at the start of over 90 percent of successful breaches.
In fact, phishing is one of the most used and most successful attack vectors, but despite multi-level security controls and phishing awareness training for employees, most organizations remain unaware of their increasing vulnerability to these threats.
Most phishing sites stay online for just four to eight hours, with some up for only minutes, according to the 2018 Webroot Threat Report.
Such brief durations demand that organizations use real-time anti-phishing solutions that can detect a malicious phishing site in real time, rather than putting faith in static threat feeds that cannot keep up with the volume and short lifecycles of today’s fast-moving phishing threats on the Web.
(See how SlashNext cybersecurity solution detects and blocks phishing attacks beyond email. Courtesy of SlashNext and YouTube. Posted on Jul 25, 2018.)
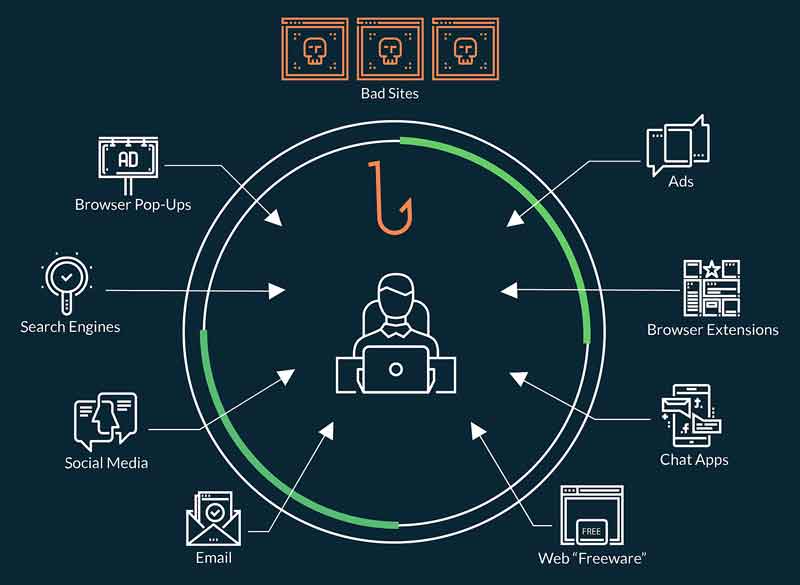
While phishing attacks are often equated with phishing emails, however, sophisticated phishing attacks today are delivered via social media, malvertising, browser-pops, IM, rogue browser plug-ins, ads, search results, pop-ups, IM and chat applications, and apps.
Users encounter these threats on the Web or in free apps, where even a single mistaken click can open their companies up to costly data breaches or extortion attempts.
Cybersecurity defenses are weaker in these other areas and workers have become prone to clicking on phishing links when operating in an “arena of trust” outside of their inbox.
Over half of respondents to the SlashNext survey named the growing number of phishing attack vectors beyond email as a “Top 3” concern in terms of potential phishing threats.

The other top concerns involved the growing sophistication and realism of spoofed sites, and the difficulties in training employees to spot these new types of phishing threats.
“Phishing tactics have evolved to using very fast-moving phishing sites and attack vectors that evade existing security controls,” explains Atif Mushtaq, CEO and founder of SlashNext.
“And with such legitimate-looking phishing sites manipulating users, there is little to protect employees, not even phishing awareness training.”
“The solution involves a phishing detection system that can analyze and detect malicious sites like a team of cybersecurity researchers, but do it in real-time to protect users.”
(Find out how you can stop web-based phishing threats from luring your employees. SlashNext’s cybersecurity technology detects and blocks phishing attacks in real-time before they can cause any damage. Courtesy of SlashNext and YouTube. Posted on Jul 25, 2018.)
SlashNext Real-Time Phishing Detection Closes the Phishing Gap
SlashNext protects your employees from the growing number of zero-hour phishing threats on the Web.
With over 46,000 new phishing sites going live each day, and most disappearing within 4-8 hours, today’s attacks move faster than static threat feeds and defenses can typically block them.
SlashNext closes the gap with definitive real-time phishing site detection. Regardless of phishing attack vector, SlashNext definitively detects phishing sites the moment they’re browsed, producing a dynamic block list for automated blocking by your URL filtration / blocking defenses.
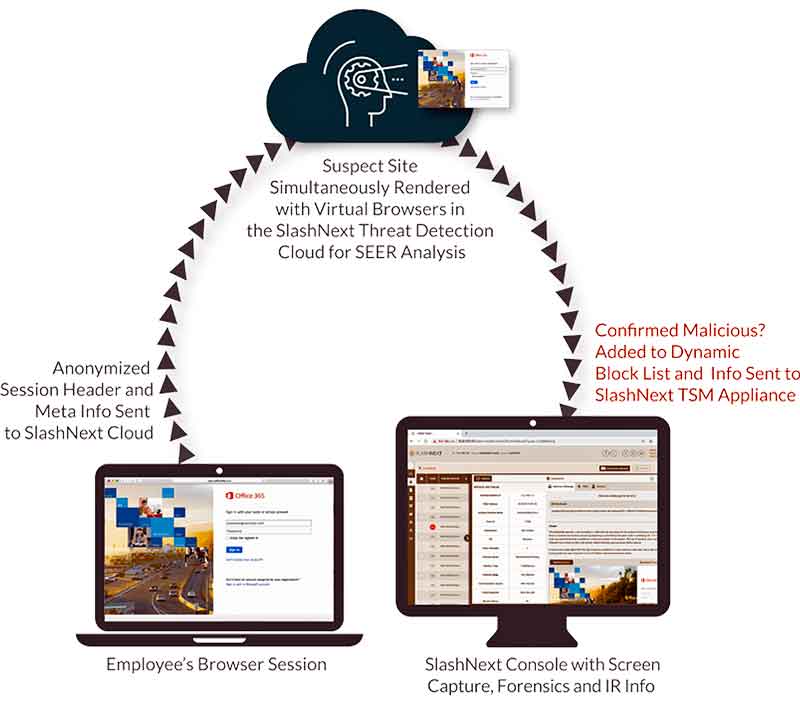
How it Works
-
SlashNext monitors employee Internet traffic with an appliance that connects to a SPAN port. The SlashNext TSM appliance selects traffic for further analysis and sends anonymized session header and meta info to the SlashNext Threat Detection Cloud for real-time SEER™ analysis (Session Emulation & Environment Reconnaissance).
-
SlashNext renders suspect sites with virtual browsers in our purpose-built cloud. SEER technology inspects the site like a team of cybersecurity researchers using highly advanced text analysis, visual analysis, and active site interrogation to thoroughly analyze the suspect site.
-
SEER analysis features are fed into patent-pending progressive machine learning algorithms which deliver a single, definitive verdict: malicious or benign. There’s no threat probability scores and virtually no false positives.
-
Malicious URLs and domains are instantly added to a dynamic block list for your blocking infrastructure, typically firewalls, web proxies, or DNS. Incident information, including site screen capture, site artifacts, PCAP data, and more are instantly available in the local SlashNext console.
Additional key findings from the SlashNext 2018 Phishing Survey include:
- Nearly two-thirds of respondents (64 percent) cite shortfalls in employee awareness and training as their top concern for protecting workers against social engineering and phishing threats.
- Nearly half of respondents (45 percent) believe they experience 50 or more phishing attacks per month. 14 percent believe they experience more than 500 phishing attacks per month.
- Only one-third of respondents (32 percent) agree or strongly agree that their current threat feeds and block lists are adequate to protect users from new phishing sites.
- Four out of ten (39 percent) cite the inability of their current defenses to reliably detect phishing attacks as a top concern.
- 87% of respondents are currently evaluating or planning to evaluate real-time phishing site detection technologies.

The SlashNext 2018 Phishing Survey was conducted by Survata, an independent research firm based in San Francisco, and was taken by 300 IT security decision-makers in mid-sized firms in the U.S. between Sept. 21, 2018 and Sept. 26, 2018.
SlashNext at a Glance
 SlashNext is pioneering a more effective approach to real-time phishing site detection and protection, with patent-pending SEER™ phishing detection technology, to detect malicious phishing sites in seconds with the power of adaptive machine learning in the cloud.
SlashNext is pioneering a more effective approach to real-time phishing site detection and protection, with patent-pending SEER™ phishing detection technology, to detect malicious phishing sites in seconds with the power of adaptive machine learning in the cloud.
SlashNext integrates seamlessly with customers’ URL filtration/blocking infrastructure for immediate phishing protection against today’s short-lived but highly-targeted phishing attacks, regardless of attack vector.
SlashNext founder and CEO Atif Mushtaq previously spent nine years as a Senior Scientist at FireEye, where he was one of the main architects of FireEye’s core malware detection technology.
SlashNext Takes Home the Gold in the 2018 ‘ASTORS’ Homeland Security Awards Program
SlashNext
-
Best Phishing Defense Solutions
-
SlashNext Real-Time Phishing Detection
-
The Annual ‘ASTORS’ Awards Program is specifically designed to honor distinguished government and vendor solutions that deliver enhanced value, benefit and intelligence to end users in a variety of government, homeland security and public safety vertical markets.

The 2018 ‘ASTORS’ Awards Program drew an overwhelming response from industry leaders with a record high number of corporate and government nominations received, as well as record breaking ‘ASTORS’ Presentation Luncheon Attendees, with top firms trying to register for the exclusive high – end luncheon and networking opportunity – right up to the event kickoff on Wednesday afternoon, at the ISC East registration!
Over 130 distinguished guests representing National, State and Local Governments, and Industry Leading Corporate Firms, gathered from across North America, Europe and the Middle East to be honored among their peers in their respective fields which included:
- The Department of Homeland Security
- The Federal Protective Service (FPS)
- Argonne National Laboratory
- The Department of Homeland Security
- The Department of Justice
- The Security Exchange Commission Office of Personnel Management
- U.S. Customs and Border Protection
- Viasat, Hanwha Techwin, Lenel, Konica Minolta Business Solutions, Verint, Canon U.S.A., BriefCam, Pivot3, Milestone Systems, Allied Universal, Ameristar Perimeter Security and More!
The Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program highlighting the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition, and keep our Nation safe – one facility, street, and city at a time.
The 2018 ‘ASTORS’ Homeland Security Awards Program was Proudly Sponsored by ATI Systems, Attivo Networks, Automatic Systems, Desktop Alert, and Royal Holdings Technologies.
2018 Champions Edition
 See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
Nominations for the AST 2019 ‘ASTORS’ Homeland Security Awards Program will officially open as of January 1st, 2019 at americansecuritytoday.com.
Enter Early to Maximize Media Coverage of your Products and Services at Kickoff, and Get the Recognition Your Organization Deserves!
And be sure to Register Early for the 2019 ‘ASTORS’ Awards Presentation Luncheon at ISC East 2019 to ensure your place at this limited- space event!