Attivo Networks, Triple-Award Winner in the 2017 ‘ASTORS’ Homeland Security Awards Program, is pleased to announce the company’s ThreatDefend Deception and Response Platform has been nominated to compete in multiple categories of the 2018 ‘ASTORS’ Awards Program.
You can’t go a day without finding an article on the impending threat to the energy sector and a country’s critical control operations.
 Cyberattacks on these targets can and have resulted in disruption of critical local, regional, and national government and commercial infrastructures.
Cyberattacks on these targets can and have resulted in disruption of critical local, regional, and national government and commercial infrastructures.
As a result, when they are breached, the impact on societies they serve stands to be catastrophic.
The damages to property and ensuing theft will amount tens of billions of dollars, and the loss of life will be significant.
The threat risk for an attack on industrial control systems can be as big as a high-profile attack on the energy grid, but it can also appear in less obvious places – like universities, casinos, and even sports centers which often operate with similar environments and infrastructure of a small city.
With Supervisory Control and Data Acquisition (SCADA) systems becoming increasingly vulnerable to sophisticated and persistent hackers, current security solutions no longer offer the protection needed to defend against a cyber attack.

Continuous Threat Management
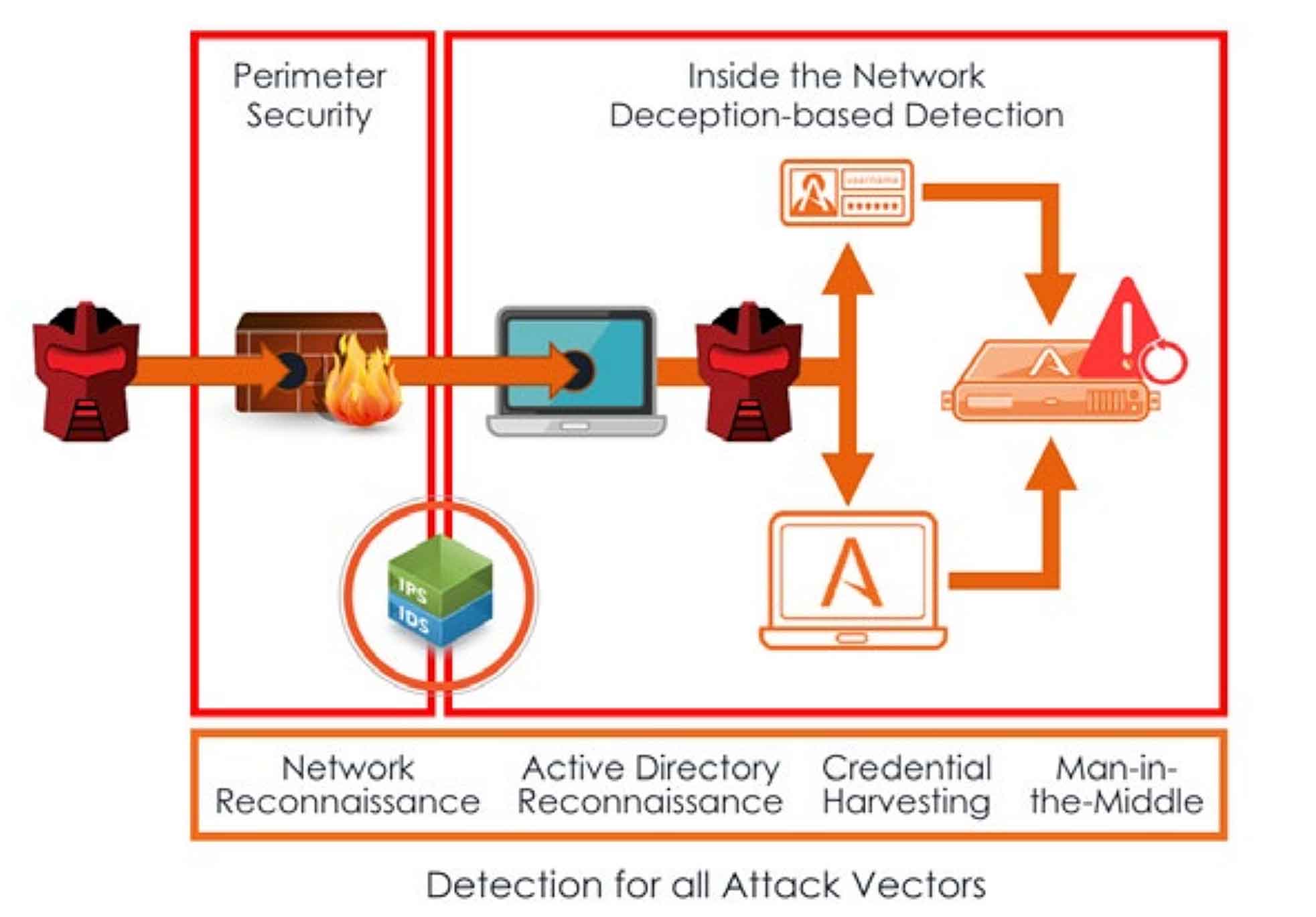
An effective strategy to secure your SCADA network is to take a defense-in-depth approach with deception technology.
Deception is a different and highly effective solution for protecting SCADA environments.
Since it does not rely on knowing the attack signatures or patterns, it does not need to monitor all traffic to look for suspicious behavior.
Deception also does not require software to be loaded or maintained on the SCADA device.
Instead, deception is used to confuse, delay, and redirect the enemy by incorporating ambiguity and by misdirecting their operations.
(See a brief brief introduction to deception technology and the Attivo Networks ThreatDefend Deception and Response Platform to Learn More. Courtesy of Attivo Networks and YouTube.)
Attivo has had numerous discussions with enterprise, education, and government agencies on how to improve the state of cyber detection within Industrial Control Systems (ICS)-SCADA environments.
SCADA systems had originally been designed to monitor critical production processes without consideration to security consequences.
Security had been generally handled by keeping the devices off the network and the Internet using “air gaps” where malware could only be transmitted by the thumb drives used by technicians.
However, today vulnerable SCADA systems are increasingly being connected to the corporate IT infrastructure and Internet, making them easily accessible to a remote attacker.
Examples of this would be the Sandworm malware that attacked Telecommunications and Energy sectors, Havex malware that infected a SCADA system manufacturer, and BlackEnergy malware that attacks ICS products manufactured by GE, Siemens, and Advantech.
These attacks primarily targeted the operational capabilities of these facilities. With the increased malicious and sophistication of malware, concerns are now escalating to fears of an irreversible disaster.
(On December 23 2015, 230,000 people in Ukraine were left in the dark for six hours after hackers compromised several power distribution centres which provide electricity to residents in Ukraine. The attackers used spear phishing emails and variants of the BlackEnergy 3 malware to gain a foothold into the IT networks of the electricity companies and knock real-world systems offline. Courtesy of Fox News and YouTube. Posted on Mar 22, 2016)
This incident was the first recorded successful cyber-attack on an electric grid – and if a power outage at the beginning of winter doesn’t sound too bad, just consider the impact if such a breach were to affect the country’s hospitals.
Attivo has also worked with these organizations on deploying threat deception and in how they can apply deception to their NIST 800-82 Revision 2 requirements in order to strengthen their overall security posture and comply with security expectations and regulation.
Adoption of the ThreatDefend™ platform for ICS-SCADA environments as a default security control is soaring based upon its unique ability to efficiently close the detection gap, provide early detection, and accelerate incident response to attacks targeting industrial control systems.
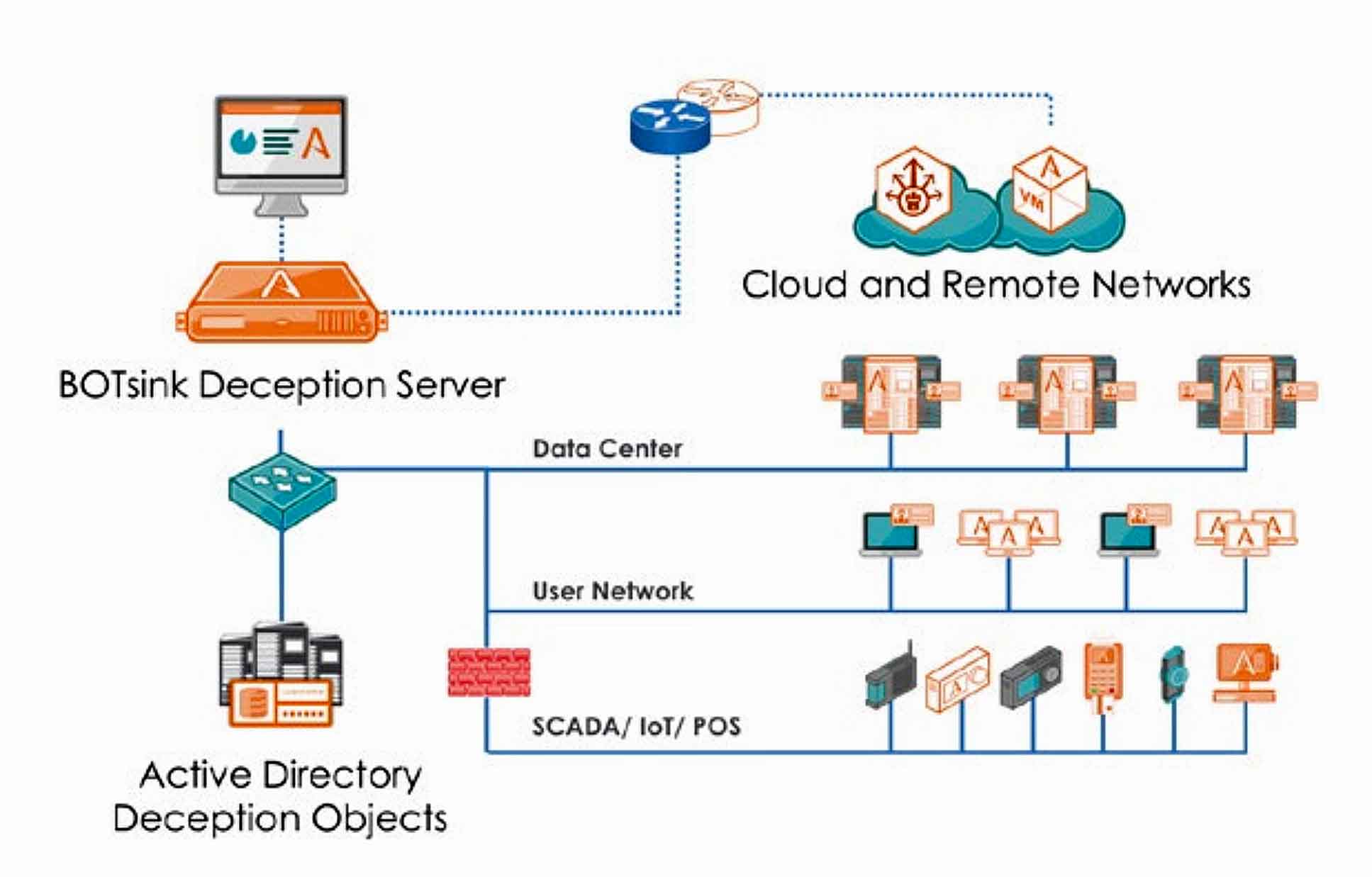
The solution is designed for threat detection on ICS-SCADA devices that are used to monitor and control manufacturing operations and critical infrastructure across a wide variety of industries.
ICS-SCADA support and deception authenticity customization is included within the ThreatDefend™ BOTsink solution, which also provides support for enterprise network, public, private, and hybrid cloud, IoT, and POS in-network threat detection.
With this solution, Attivo provides customers early and accurate threat detection for businesses, process controls, and field sensors.
Organizations get early and accurate visibility into reconnaissance and stolen credential attacks as well as external, insider, and third-party threats as they move laterally through the network.
Regardless of whether the attack originates from a phishing email, USB device or through another point of access, the platform sets traps and provides the visibility required to quickly detect, stop, and remediate an attack.
The ThreatDefend platform is an innovative and highly effective solution for protecting ICS- SCADA environments.
Since it does not rely on known attack signatures or patterns, it does not need to monitor all traffic to detect suspicious behavior and sits out of band so there is no impact to network performance.
Deception also does not require software to be loaded or maintained on a SCADA device.
ICS-SCADA deceptions are completely customizable to the environment for authenticity and are extremely simple to deploy and maintain in both upstream and downstream operations.
Deception techniques are then applied to confuse, delay, and redirect the adversary by deceiving, misinforming, and misleading them into engaging with the deception environment.
Once engaged, the solution raises a high-fidelity alert with the full TTPs and IOCs of an attack and creates forensic reports.
Through extensive 3rd party integrations, incident response is automated with attack information sharing and automations for blocking, isolation, and threat hunting.
Security teams will also benefit from network visibility and attack time-lapsed replay tools to better understand changes and attacks on the network, and how to improve their overall security posture.
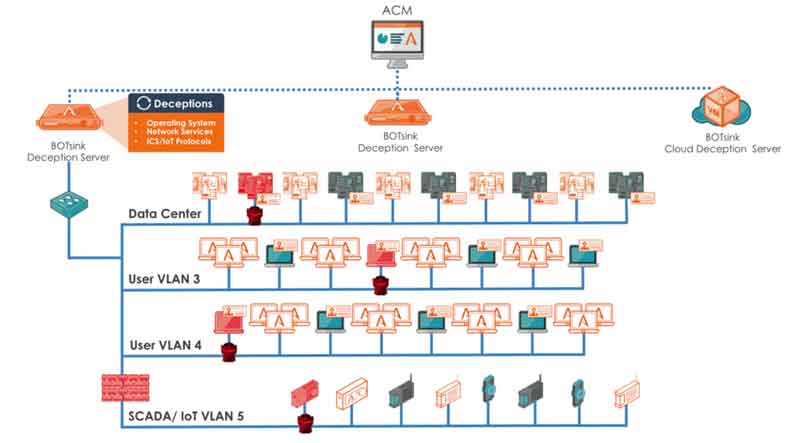
Built-in machine-learning will automate deployment and simplify operations by auto-proposing deception campaigns.
This maintains the highest levels of authenticity and provides automated refresh of the deception environment in order to amplify deceptions based on user behavior, reset the attack surface on-demand, to avoid fingerprinting or to simply reset the attack surface after a compromise.
Additionally, the ThreatDefend platform provides the ThreatPath™ solution, which assesses likely attack paths, so organizations can understand configuration and credential vulnerabilities attackers can leverage for lateral movement.
This information can then be used for attack prediction to strengthen an organization’s security posture.
(The Attivo ThreatPath™ solution provides an attack path vulnerability assessment based on likely attack paths that an attacker would traverse through misconfigured systems or credential misuse. A topographical illustration of the attack paths provides a straight-forward view of how an attacker can move laterally once they have engaged with their first end-point system. Clickable drill downs provide the details of weaknesses and IP addresses for systems needing to be isolated and/or fixed. Integrations with prevention systems can be leveraged for automated response actions and trouble tickets can be activated inside the dashboard. Courtesy of Attivo Networks and YouTube)
With flexibility to support a broad variety of ICS-SCADA devices, this solution provides easy and accurate detection of threats and lateral movement across the board.
Alerts are engagement-based so the security team can take immediate action and will not be faced with false positives and corresponding alert fatigue.
Third-party integrations with major prevention, endpoint, and SIEMs simplify incident response with automated blocking, quarantine and threat hunting, saving security teams time and energy in responding to and remediating attacks.
Better protecting our ICS-SCADA environments is critical to maintaining operations but also in preserving human safety.
Whether it is an attack at a ball game, tampering with underground pumps at a casino, or an attack on a fuel sensor, the Attivo ThreatDefend platform is playing a critical role in ICS-SCADA cybersecurity defense by providing early detection and actionable insights to derail an attacker before they can cause material harm.
All, without the need to add additional personnel to operate and maintain.

“We are proud to be the first in the industry to provide customers a globally scalable, deception-based threat detection solution for SCADA protection,” explains Tushar Kothari, CEO of Attivo Networks.
“Many of our customers from the energy industry have requested the extension of our Attivo Deception Platform into their production and manufacturing control networks so they can get real-time visibility and the ability to promptly identify and remediate infected devices.”
“As one stated, ‘a breach on those networks can be catastrophic and Attivo wants to do everything we can to prevent a disaster or risk to lives.”
Attivo ThreatDefend Deception and Response Platform at a Glance
Comprehensive Deception and Decoy
 Make the Entire Network a Trap to Confuse and Misdirect Attackers into Revealing Themselves
Make the Entire Network a Trap to Confuse and Misdirect Attackers into Revealing Themselves
- Decoys appear identical to production assets, luring attackers into revealing themselves.
- Decoy configurations run real Linux, Mac, and Windows OS and are customizable to match the “golden image” of the production environment.
- Deception lures (bait) redirect attackers trying to infect endpoints, servers/VMs to engagement servers for detection.
- Bait includes deception credentials, ransomware bait, and other deception lures.
Deception Authenticity and Campaigns
 Camouflage for Dynamic Behavioral Deception
Camouflage for Dynamic Behavioral Deception
Discover, assign, and refresh decoys, credentials, and attacker bait dynamically with automated, self-learning deception campaigns.
- Intelligent deployment of deceptive assets to match the behavior of a user’s network.
- Continuously monitor, evolve, refresh, deceptive credential and lures.
- Self-healing technology dynamically respins decoys after engagement, preventing attacker fingerprinting and identification.
Automated Deception Campaign Deployment
 Adaptive Deception for Scalability and Auto-reset of Deception
Adaptive Deception for Scalability and Auto-reset of Deception
Attivo Adaptive Deception Campaigns provide breakthrough scalability, which is critical for large network deployment and for instantly resetting the attack surface to stop an attacker from successfully completing a breach.
- Automatically deploy deception campaigns created from environmental learnings
- On-demand resetting of deception synthetic network including decoys, lures, and credentials
- Create uncertainty for the attacker, escalate the chances of them making a mistake, and increase their costs as they are forced to restart or abandon their attack
Reduction of Attack Detection Time
 Prevent Data Exfiltration
Prevent Data Exfiltration
Prevent attackers from exfiltrating valuable company information and credentials and stop them before any damage can be done.
- Attack detection is provided real-time by accurately identifying infected clients, including sleeper and time-triggered agents, enabling remediation of the attack before damage can be done.
- No false positives. Alerts only occur when a hacker is engaged, and an attack on the BOTsink Solution has occurred.
Identify and Understand the Methods and Intent of Hackers
 Analysis and Forensics
Analysis and Forensics
After the attacker has engaged with the Attivo deception platform, they can either be automatically or manually quarantined and studied for detailed forensics. After quarantining the malware, the Attivo BOTsink allows the attack to fully detonate inside the controlled system, generating a full scale forensic analysis that can be exported into popular formats. The Attivo analysis engine will analyze:
- The techniques and methods of the attack
- Where the attacker is and which systems are infected
- Which systems will be infected next and how to quarantine the spread of the attack
The forensic ability of the Attivo deception platform allows for unparalleled visibility into any attack on your network.
Improve Incident Response with Actionable Alerts
 Substantiated Alerts Based on Attacker Engagement: No False Positives
Substantiated Alerts Based on Attacker Engagement: No False Positives
The Attivo BOTsink Solution provides accurate, actionable alerts, with the intelligence you need to take immediate action and stop BOTs and APTs in your network.
- There are NO legitimate reasons for a user to communicate with the Attivo BOTsink Solution, so any scans or attempts to engage it represent an attacker trying to find and target high-value network assets.
- If the BOTsink Solution doesn’t see anything, you can rest assured your assets are safe, and you have the coverage you need to identify a BOT or APT, as soon as it enters your network.
- The longer a BOT or APT engages the Attivo BOTsink Solution, the more data it collects and analyzes to support remediation and forensics.
- With the BOTsink Solution, you can quickly and efficiently strengthen your overall security and shut down BOTs and APTs to protect your IP and brand.
Defend Your Network
 Reporting and Automations to Block Attacks and Quarantine Devices
Reporting and Automations to Block Attacks and Quarantine Devices
- Captures and Analyzes Actionable Information—identifies the infected systems and collects and analyzes information on the time, type and anatomy of the attack.
- Provides Forensics—capturing and cataloging all attack activity to support understanding of the attack’s anatomy and objectives that can lead to a better overall security stance.
- Reporting and Seamless Eco-System Integration—Security professionals have the option to access detailed attack information through UI, PCAP files, Syslog, IOC, and CSV report formats or can automatically set configurations to block and quarantine through prevention system integrations.
Attivo Networks® provides the real-time detection and analysis of inside-the-network threats.
The Attivo ThreatDefend™ Deception and Response Platform detects stolen credentials, ransomware, and targeted attacks within user networks, data centers, clouds, SCADA, and IoT environments by deceiving an attacker into revealing themselves.
Comprehensive attack analysis and actionable alerts empower accelerated incident response.
Attivo Networks Wins Trifecta in the 2017 ‘ASTORS’ Homeland Security Awards Program

-
Attivo Networks
- Gold ‘ASTORS’ Award Winner
- Attivo Networks ThreatDefend Deception and Response Platform
- Best Critical Infrastructure Solution
-
Attivo Networks
- Platinum ‘ASTORS’ Award Winner
- Attivo Networks ThreatOps Solution
- Best Integrated Security Management Solution

-
Attivo Networks
- Gold ‘ASTORS’ Award Winner
- Attivo Networks ThreatDefend Deception and Response Platform
- Best Intrusion Detection & Prevention Solution

Over 100 distinguished guests from National, State and Local Governments, and Industry Leading Corporate Executives from companies allied to Government, gathered from across North America and the Middle East to be honored from disciplines across the Security Industry in their respective fields which included representatives from:
- The Department of Homeland Security
- The Department of Justice
- The Security Exchange Commission
- State and Municipal Law Enforcement Agencies
- Leaders in Private Security