Attivo Networks®, Triple-Award Winner in the 2017 ‘ASTORS’ Homeland Security Awards Program, a Finalist in the 2018 ‘ASTORS’ Awards, and a leader in deception for cyber security threat detection, includes new advanced capabilities that use machine learning to automatically generate and deploy the most authentic deception that covers an extensive set of attack vectors at scale.
 The most recent product release lowers the total cost of ownership by completely automating the deployment and maintenance of the most authentic and comprehensive deception environment.
The most recent product release lowers the total cost of ownership by completely automating the deployment and maintenance of the most authentic and comprehensive deception environment.
It accomplishes all of this transparently and without adding any agents to the production environment.
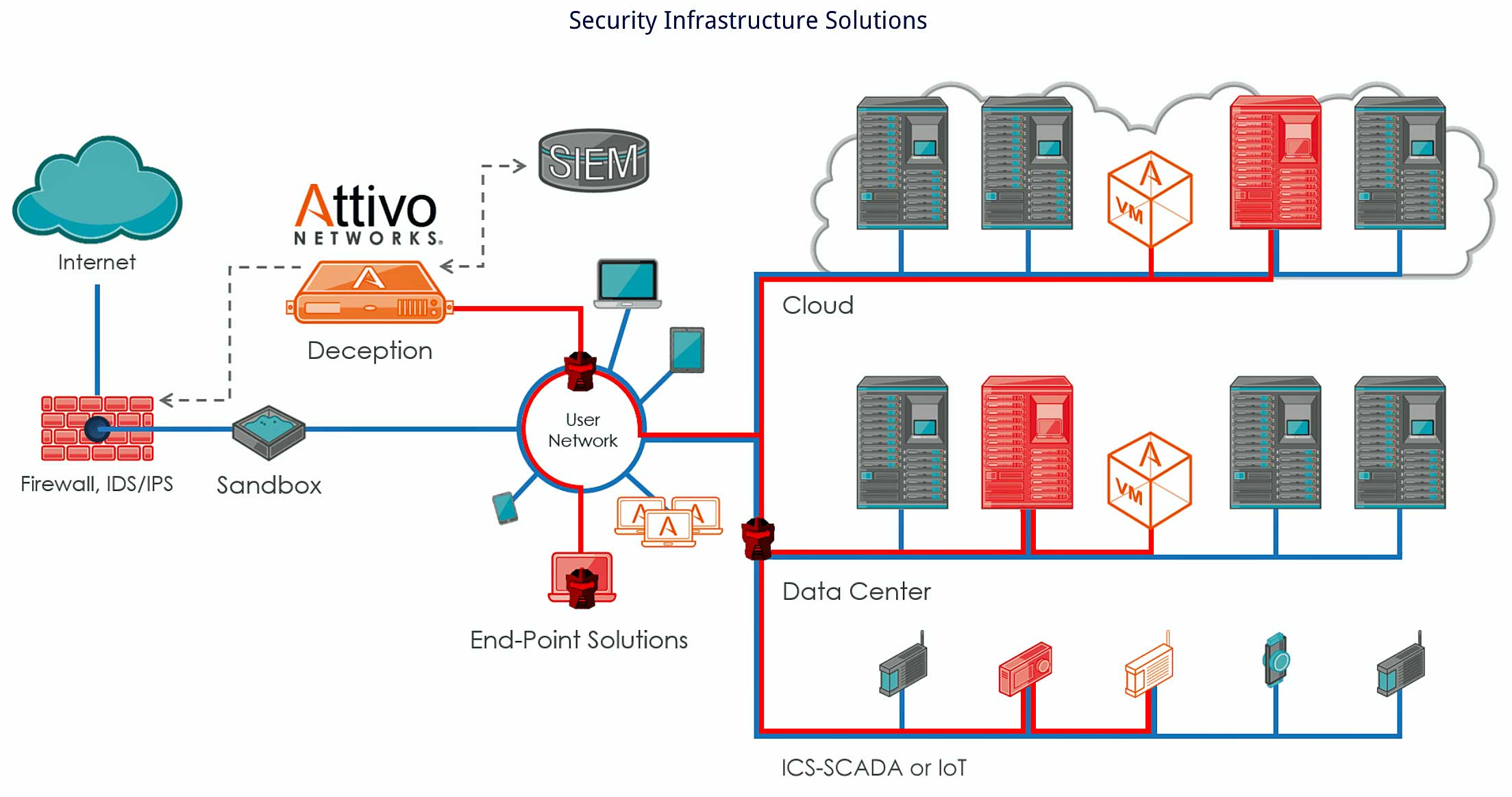
This is a new generation of the ThreatDefend™ platform that extends a customer’s ability to ubiquitously cover its on premise, remote, and cloud operations in a simple and consistent manner.
It is the latest in deception technology and completely integrates into any customer’s security workflow.

“Deception needs to be not only dynamic in its authenticity and attractiveness to the attacker, but also needs to be extremely scalable and simple to create, manage, and operate without the use of any agents,” explains Tushar Kothari, CEO of Attivo Networks.
“With the incorporation of machine-learning, Attivo can now automatically generate new campaigns at the push of a button to refresh the environment for renewed attractiveness and decoy placement.”
“It really can’t get much easier than this.”
The overall management of deception boils down to three critical components: automatic deception generation, deployment, and maintenance.
The original use of honeypots and early forms of deception credential management were either plagued with scalability and management challenges or compromised authenticity for ease of use.
Customers no longer need to compromise.
(See a brief introduction to deception technology and the Attivo Networks ThreatDefend Deception and Response Platform. Courtesy of Attivo Networks and YouTube. Posted on Jun 22, 2018)
The following product enhancements make this as easy as 1-2-3.
1) Generate Deceptions:
-
Machine-learning is utilized to learn the assets, applications, and device profiles and automatically generates a matching deception environment.
-
This technology is able to distinguish the difference between IoT devices, SCADA environment, and an enterprise network as well as different credential naming conventions.
 2) Intelligent and Agentless Deployment:
2) Intelligent and Agentless Deployment:
-
As deception continuously learns the environment, the technology matches network behavior, mimics devices, and deploys deceptive credentials and assets that are mirror-match authentic.
-
Deception campaigns can be automatically deployed and/or can be reviewed and executed at the push of a button.
-
The Attivo Networks agentless endpoint credential technology provides an extensive offering of deception breadcrumbs and non-invasive decoys without the need for additional CPU or traditional software infrastructure management.
-
The company’s ThreatDirect™ deception solution family projects deception at scale throughout the network without the need for additional hardware or infrastructure, making it extremely effective for deploying deception in cloud, remote offices/branch offices, or micro-segmented networks.
-
3) Continuous Operation:
-
Every aspect of the deception environment is monitored to determine when the solution should deploy updates, refresh credentials, and deploy new deception decoys.
-
Additionally, Attivo deception dynamically expands the deception surface upon suspicion of foul play and following any attack, new deception is deployed to automatically refresh the deception environment.
-
This prevents “fingerprinting” by attackers who would then know what to avoid.
Ultimately, behavioral deception based upon machine learning means that all deception elements can blend seamlessly into the environment and become indistinguishable from production assets; that deceptive environments can continuously evolve and scale; and that attackers cannot defeat the deception by profiling.
All, with easy automated management, deployment, and operation.
(Learn More from Tony Cole, Attivo Networks CTO, as he discusses deception technology at InfoSec Europe in London. Courtesy of Attivo Networks and YouTube. Posted on Jul 20, 2018.)
Attivo Networks® provides the real-time detection and analysis of inside-the-network threats.
The Attivo ThreatDefend™ Deception and Response Platform detects stolen credentials, ransomware, and targeted attacks within user networks, data centers, clouds, SCADA, and IoT environments by deceiving an attacker into revealing themselves.
Comprehensive attack analysis and actionable alerts empower accelerated incident response.
The concept of deception campaigns is not new.
However, the ability to do this accurately and at scale without human intervention has evolved and as such, has firmly earned Attivo Networks the business of organizations across all major verticals including the finance, healthcare, retail, energy, legal, travel, and entertainment industries.
The company grew 300 percent year over year in 2017 and has secured more than 100 customers across US, EMEA, and APAC markets.
Attivo Networks Named a Finalist in 2018 ‘ASTORS’ Homeland Security Awards Program
AST focuses on Homeland Security and Public Safety Breaking News, the Newest Initiatives and Hottest Technologies in Physical & IT Security, essential to meeting today’s growing security challenges.
 The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.
The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.
As an ‘ASTORS’ competitor, Attivo Networks ThreatDefend™ platform is competing against the industry’s leading providers of Innovative Cybersecurity, Cyber Critical Infrastructure, Intrusion Detection and Prevention, and Vulnerability Management Solutions.
To Learn More about the ‘ASTORS’ Homeland Security Awards Program, see 2017 ‘ASTORS’ Homeland Security Award Winners Honored at ISC East.

Over 100 distinguished guests from National, State and Local Governments, and Industry Leading Corporate Executives from companies allied to Government, gathered from across North America and the Middle East to be honored from disciplines across the Security Industry in their respective fields which included representatives from:
 The Department of Homeland Security(DHS) Science and Technology Directorate (S&T)
The Department of Homeland Security(DHS) Science and Technology Directorate (S&T)- U.S. Customs and Border Protection
- The Department of Justice
- The Security Exchange Commission
- State and Municipal Law Enforcement Agencies
- The Royal Canadian Mounted Police
- Leaders in Private Security
The highlight of the 2018 AST Homeland Security Awards Season is the 2018 ‘ASTORS’ Awards Presentation Luncheon to honor Nominees, Finalists and Winners on November 14, 2018 at ISC East 2018 at the Jacob Javits Exhibition Center.
Good luck to Attivo Networks on becoming a Winner of the 2018 American Security Today’s Homeland Security Awards Program!
 To learn more about ThreatDefend and Attivo Networks wide range of offerings, please visit the company’s website at https://attivonetworks.com/
To learn more about ThreatDefend and Attivo Networks wide range of offerings, please visit the company’s website at https://attivonetworks.com/
Please join us in Recognizing these Industry-Leading Firms for their Outstanding Product Development Achievements, Exciting New Technologies and Innovative Education Programs to address the growing Homeland Security Threats our Nation is facing.