American Security Today (AST) is pleased to announce it’s Annual ‘ASTORS’ Homeland Security Awards Program has had 100% Returning Premier Sponsors, including Attivo Networks, a world leader in deception for cybersecurity threat detection.
Attivo Networks was recognized with Multiple Awards in the 2019 ‘ASTORS’ Awards Program for the company’s ThreatDefend™ Deception and Response Platform – Deception Technology for early post-compromise threat detection and accelerated incident response.
NO NONSENSE THREAT DETECTION
Detecting threats needs to be comprehensive, however it doesn’t have to be complicated.
Designed for simplicity, Attivo Networks redirects attackers away from the target assets and provides high-fidelity alerting and intelligence on malicious activity and insider policy violations.
(Threat Detection is a universal challenge for organizations of all sizes and from all industries. Traditional security controls are failing and the cybersecurity community needs a new approach for detecting threats early and accurately. Explore how deception technology is solving organization’s threat detection challenges through the narrative of our wolf-in-sheep’s-clothing. Courtesy of Attivo Networks and YouTube. Posted on Mar 18, 2020.)
Attivo deception provides immediate value by providing “eyes inside the network” visibility and accurate detection alerting based upon decoy engagement or attempts to use deception credentials, most notably early in the attack cycle.
For years, attackers have successfully used deception tactics for breaching networks masquerading as legitimate employees, using stolen credentials and deceptive measures to infiltrate a network.
Attackers are able to accomplish these ends all while remaining undetected for lengthy dwell times, challenging security teams as they have to be successful 100% of the time, whereas an attacker only has to get lucky once.
It’s now time to turn the tables on attackers and use deception against them.
(Hear from Carolyn Crandall, Chief Deception Officer at Attivo Networks and Kevin Fiscus, Prinicipal Instructor at the SANS Institute, and Founder of Cyber Defense Advisors, as he shares his research findings on the cost savings associated with deception technology. Courtesy of Attivo Networks and YouTube. Posted on Sep 4, 2020.)
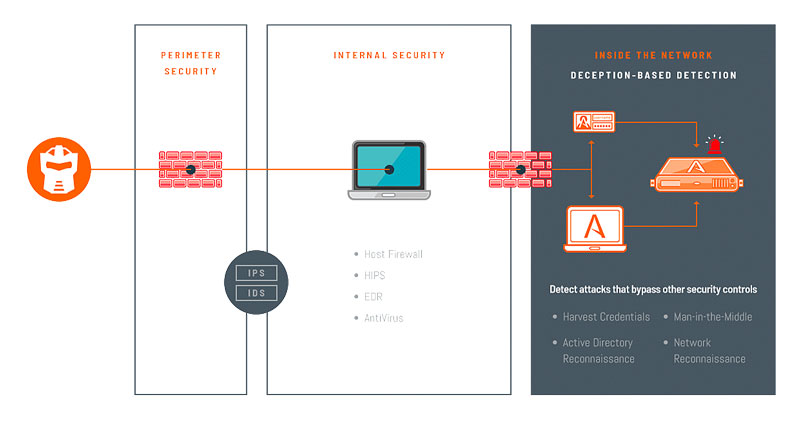
The Attivo Networks ThreatDefend® platform is a comprehensive detection solution for attack activities inside the network.
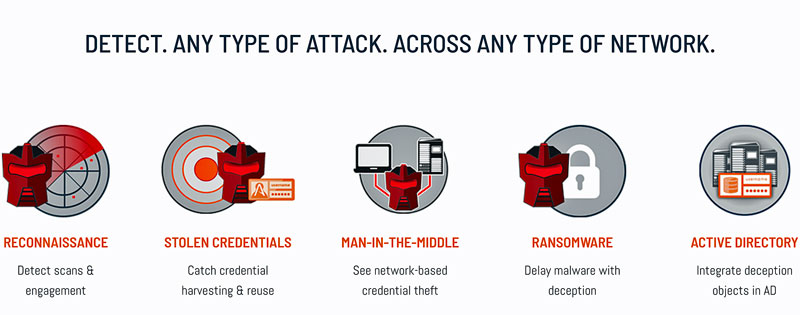
The platform offers in-network visibility and detection for on-premises, cloud, and remote locations across all attack surfaces and against any attack vector.
It detects lateral movement activity such as discovery and reconnaissance, port and service scans, data gathering from Active Directory, Man-in-the-Middle attacks, credential theft and reuse, and mapped share traversal.
The platform does this by deploying network, endpoint, application, data, and AD decoys and deceptive assets to create a fabric that misdirects and misinforms attackers.
These decoys blend in with the production environment but do not impact normal operations and remain hidden from employees conducting normal work activities.
(See a brief introduction to deception technology and the Attivo Networks ThreatDefend Deception and Response Platform. Courtesy of Attivo Networks and YouTube.)
Attivo Networks ThreatDefend® platform does not rely on signatures or behavioral anomalies to detect attacks but instead relies on attacker engagement with the decoy environment, thus minimizing false positives.
The decoys record all attack activity while alerting security teams to the attack, reducing investigation and response times while capturing network, memory, and disk forensic data for intelligence development.
With the forensic capture of all attack data on the decoys, organizations gain robust data to develop threat intelligence for attacks that are targeting them specifically.
This company-centric threat intelligence is 100% applicable and immediately valuable since it pertains directly to the organization and covers attacks that are happening to it at the moment.
The platform includes analysis and filtering tools that correlate the attack data in chronological order and can display the attack in a graphical replay.
The ThreatDefend platform also includes the Informer dashboard to accelerate investigations.
The Informer dashboard correlates all information about a single in-network attack source and displays it in a simple, easy to use interface.
The readout includes the details about the system (such as system name, IP address, logged on user, etc.), a timeline view, and the events originating from the system in reverse chronological order that includes all event data.
Additionally, the dashboard shows first, second, and third-order hops from the system based on stored credentials and misconfigurations, and a means to initiate a partner integration to isolate the endpoint.
It even includes direct links to any forensic files and data captured by the decoys for quick downloads, such as packet capture files, malware analysis reports, memory forensics analysis, and the data and binary files themselves.
This dashboard aids in analysis and investigations by putting all the details the investigator would need in a single source, fully correlated, and ready to action.
DECEPTION TECHNOLOGY IN THE SECURITY STACK
The ThreatDefend platform also offers DecoyDocs that provide a counterintelligence function to provide information on the intent of the attacker and the information it is targeting.
DecoyDocs have a beaconing technology that phones home whenever anyone opens them, either inside or outside of the network.
When opened inside the network, the DecoyDocs sends all host data to the platform and generates an alert.
If the attackers exfiltrate the DecoyDocs, it will send the Internet-facing external address of every system that opens it back to the ThreatDefend platform with geo-location information.
The platform can export the forensic artifacts and output the event data to other analysis platforms, log aggregators, or SIEMs for further investigation and correlation to enhance threat intelligence development overall.
Partner integrations also allow for direct exchange with other platforms for threat hunting and data exchange.
These include partner integrations with SIEM solutions such as Splunk, McAfee ESM, or LogRythm, data enrichment with partners like Webroot and Virustotal, being a certified McAfee DXL partner, and being a certified Cisco pxGrid grid partner.
Few providers can offer network, disk, and memory forensic capture at the time of the attack, coupled with the correlation of all event data and forensic evidence to create adversary intelligence to such a degree.

“As attackers become more sophisticated, it’s critical to not only detect their presence but also gain valuable adversary intelligence to anticipate the attacker’s strategy,” explains Tushar Kothari, CEO of Attivo Networks.
“With the Informer solution from Attivo, defenders now have a more complete view of the attack, can predict where the attacker will move, and can adjust their defenses accordingly to mitigate the risk of a breach.”
The Informer solution is provided within the ThreatDefend™ platform and benefits the security analysts and incident response teams by:
-
Delivering an accurate chronological session view of all attacker activity from specific IP addresses as well as host system and network characteristics.
-
Capturing forensic information inclusive of volatile memory, registry, and file changes along with lateral movement and network activities.
-
This provides a consolidated view of the source of an attack for the analyst to access, reducing containment, eradication, and recovery times.
-
Additionally, necessary access to forensic artifacts are presented in a clear, concise indexable manner that responders and analysts will recognize and can take action on.
-
-
Providing critical attack details such as memory forensics, endpoint activity, initial compromise intelligence, network packet captures, exploit code, targeted files and system logs that are all collated with a single view and can be easily accessed by all team members.
-
The dashboard saves responders valuable time by displaying detection information in an actionable format and by organizing the attack data for faster intelligence analysis and a means to retrace attacker activities.
-
-
Displaying all lateral movement paths that the attacker has access to, showing potential target systems and open attack paths an attacker would try to compromise and exploit.
-
Triggering automated response through native integrations or predefined ThreatOps™ playbooks, accelerating incident response to increase efficiency and reduce effort.
(See how Attivo Networks ThreatStrike End-Point Deception Solution is a customizable and non-intrusive technology that is used to identify targeted attacks of infected end-points, infected servers/VMs, the use of deception stolen credentials, and ransomware attacks on networked drives. The solution also provides for suspicious email submission for threat detection. Courtesy of Attivo Networks and YouTube.)
By utilizing the Informer solution, organizations of all sizes will gain a demonstrable improvement in their ability to detect in-network threats quickly and to dramatically reduce a defender’s time to respond from hours to minutes.
With clear, concise, and consolidated adversary intelligence, post-incident activity readouts, remediation activities, and other necessary steps typically undertaken after a potential incident or breach will become more streamlined and actionable, saving organizations valuable time and cost.
To learn more about the Informer solution and how to apply its capabilities towards an Active Defense strategy for advanced threat detection, please visit: https://attivonetworks.com/solutions/incident-response/.
Attivo Networks a Multi-Award Finalist in 2020 ‘ASTORS’ Awards Program

The Annual ‘ASTORS’ Awards Program is specifically designed to honor distinguished government and vendor solutions that deliver enhanced value, benefit and intelligence to end users in a variety of government, homeland security and public safety vertical markets.
The Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program highlighting the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition, and keep our Nation safe – one facility, street, and city at a time.
90% of ‘ASTORS’ Award Winners return to compete in the Annual ‘ASTORS‘ Homeland Security Awards Program, and 100% of ‘ASTORS’ Sponsors have returned year to year to reap the benefits of their participation in the industry’s largest and most comprehensive Annual Awards Program.

The 2019 ‘ASTORS’ Awards Program surpassed expectations with a record number of nominations received from industry leaders and government agencies, and drew over 200 attendees to the ‘ASTORS’ Awards Presentation Banquet – an exclusive gourmet luncheon and networking opportunity which filled to capacity, before having to turn away late registrants.

The event featured an impassioned and compelling keynote address by William J. Bratton, former police commissioner of the New York Police Department (NYPD) twice, the Boston Police Department (BPD), and former chief of the Los Angeles Police Department (LAPD), as he walked attendees through 50 years of American policing history, the impacts on the communities, and the evolution of critical communication capabilities in our post 9/11 landscape.
Commissioner Bratton, one of the world’s most respected and trusted experts on risk and security issues and Executive Chairman of Teneo Risk a global advisory firm, was recognized as the ‘2019 ‘ASTORS’ Person of the Year’ for his Lifetime of Dedication and Extraordinary Leadership in Homeland Security and Public Safety.
The 2020 ‘ASTORS’ Awards Program is sponsored by ATI Systems, Attivo Networks, Automatic Systems, Desktop Alert, X.Labs and Reed Expositions, every one a returning Sponsor from 2019.
Why the ‘ASTORS’ Homeland Security Awards Program?

American Security Today’s comprehensive Annual Homeland Security Awards Program is organized to recognize the most distinguished vendors of physical, IT, port security, law enforcement, and first responders, in acknowledgment of their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.’
Over 200 distinguished guests representing Federal, State and Local Governments, and Industry Leading Corporate Firms, gathered from across North America, Europe and the Middle East to be honored among their peers in their respective fields which included:
- The Drug Enforcement Administration (DEA)
- National Center for Missing and Exploited Children (NCMEC)
- United States Marine Corps
- The Federal Protective Service (FPS)
- Argonne National Laboratory (ANL)
- United States Postal Inspection Service
- DHS S&T
- United States Marshals Service (USMS)
- The Port Authority of New York & New Jersey Police (PAPD)
- The Department of Justice (DOJ)
- The New York State Division of Homeland Security & Emergency Services (NYS DHSES)
- United States Border Patrol
- AlertMedia, Ameristar Perimeter Security, Attivo Networks, Automatic Systems, Bellevue University, BriefCam, Canon U.S.A., CornellCookson, Drone Aviation, FLIR Systems, Hanwha Techwin, HID Global, IPVideo Corp., Konica Minolta Business Solutions, LenelS2, ManTech, Regroup Mass Notifications, SafeLogic, SolarWinds, Senstar, ShotSpotter, Smiths Detection, TCOM LP, Trackforce, Verint, and More!
From innovative Military Cyber Programs, to Local, State and Federal Public Safety and Emergency Management Initiatives, New Physical and IT Products and Services, and Security Professional, Threat Assessment, Emergency Preparedness, Law Enforcement and Homeland Security Education and Training Opportunities – Join your ‘ASTORS’ Award-Winning Peers and Receive the Recognition You Deserve!
 Excellence in Public Safety and Government Security Award Nominations are also encouraged, such as those 2019 Honored Winners which includes the DEA, U.S. Marine Corps, DHS S&T, Federal Protective Service, DHS S&T NUSTL, U.S. Marshals Service, U.S. Border Patrol, The Port Authority of NY/NJ, and the NYS Division of Homeland Security & Emergency Services.
Excellence in Public Safety and Government Security Award Nominations are also encouraged, such as those 2019 Honored Winners which includes the DEA, U.S. Marine Corps, DHS S&T, Federal Protective Service, DHS S&T NUSTL, U.S. Marshals Service, U.S. Border Patrol, The Port Authority of NY/NJ, and the NYS Division of Homeland Security & Emergency Services.
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace with over 75,000 readers at the Federal, State and local levels of government as well as firms allied to government.
American Security Today brings forward a fresh compelling look and read with our customized digital publications that hold readers eyes throughout the story with cutting edge editorial that provides solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

The AST Digital Publications is distributed to over 75,000 qualified government and homeland security professionals in federal, state and local levels.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches both Private & Public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from Government at the federal, state and local level as well as from private firms allied to government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants & Dams, Bridges & Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting & Concert Stadiums, our Nation’s Schools & Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
To learn more about the 2019 ‘ASTORS’ Homeland Security Award Winners solutions, please go to the 2019 ‘ASTORS’ Championship Edition Fully Interactive Magazine – the Best Products of 2019 ‘A Year in Review’.
The ‘ASTORS’ Champion Edition is published annually and includes a review of the ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firms products and services, includes video interviews and more.
 It is your Go-To source throughout the year for ‘The Best of 2019 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
It is your Go-To source throughout the year for ‘The Best of 2019 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware and Networking Security – Just to name a few), the 2019 ‘ASTORS’ CHAMPIONS EDITION will have what you need to Detect, Delay, Respond to, and Mitgate today’s real-time threats in our constantly evolving security landscape.
It also includes featured guest editorial pieces from some of the security industry’s most respected leaders, and recognized firms in the 2019 ‘ASTORS’ Awards Program.
Attivo Networks Scores Big in 2019 ‘ASTORS’ Awards

Attivo Networks
-
Best Cyber Security Solution
-
ThreatDefend™ Deception and Response Platform
-
Best ICS/SCADA Cyber Security Solution
-
ThreatDefend™ Deception and Response Platform
-
Best IT Intrusion Detection & Prevention Solution
-
ThreatDefend™ Deception and Response Platform
-
The ThreatDefend Deception Platform is a modular solution comprised of Attivo BOTsink® engagement servers, decoys, and deceptions, the ThreatStrikeTM endpoint deception suite, ThreatPathTM for attack path visibility, ThreatOpsTM incident response orchestration playbooks, and the Attivo Central Manager (ACM), which together create a comprehensive early detection and active defense against cyber threats.
Attivo Networks is also a Returning Premier Sponsor in their Third Consecutive ‘ASTORS’ Homeland Security Awards Program.
Attivo Networks®, the leader in deception technology, provides an active defense for early detection, forensics, and automated incident response to in-network attacks.
The portfolio includes expansive network, endpoint, application, and data deceptions designed to efficiently misdirect and reveal attacks from all threat vectors.
Advanced machine-learning makes preparation, deployment, and operations fast and simple to operate for organizations of all sizes.
To Learn how deception technology can help your organization solve their threat detection challenges, please visit please visit attivonetworks.com/.
For more information about the 2020 ‘ASTORS’ Awards or All Things American Security Today, please contact Michael Madsen, AST Publisher at mmadsen@americansecuritytoday.com.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos