Axiomatics Federal, the leader in fine-grained dynamic authorization for customers and partners of the federal government, is delighted to announce Axiomatics’ Policy Server has been named a Finalist in the 2018 ‘ASTORS’ Homeland Security Awards, the Most Comprehensive Awards Program in the Industry.
Attribute Based Access Control (ABAC) is becoming a dominant model in performing access control for Federal agencies.
The dynamic and fine-grained control provided by an ABAC model ensures that only authorized individuals can access sensitive data.
(See how externalized dynamic authorization from Axiomatics can help you protect your most critical assets, and promote information sharing agency-wide. Courtesy of Axiomatics and YouTube. Posted on Apr 26, 2017.)
Digital policies, an integral part of ABAC, ensures that the applications in the enterprise are adhering to the security, regulatory, and business policies established by a federal agency.
The Axiomatics Policy Server (APS) is the purest implementation of ABAC on the market today, combining access control decision making with digital policy management.
APS is a market leader for two reasons.
First, its designers deliberately engineered APS to be an abstract service layer for your enterprise.
By using its robust application programming interface (API), the service is highly decoupled from both the application and the data tiers.
This means that the authorization service needs no prior knowledge of who or what is requesting access to an object, or knowledge of the object being requested.
Second, APS uses open standards for communication between its internal and external nodes.
Axiomatics and APS were the first to be fully XACML 3.0 compliant, and XACML is the OASIS standard for an attribute-based access control policy language and architecture.
Taken together, these two unique features allow for APS to be loosely integrated into a Federal agency’s architecture.
Therefore, as technologies progress, expensive rip-and-replace technical refreshes are not required.
The authorization service, or it subscribers, can be updated and/or replaced without having to affect other components, particularly in models that have tightly-coupled Identity and Access Management (IdAM) components.
This level of service abstraction, which ultimately saves the Federal government time and money, is a trending model across the IdAM community.
The Axiomatics Policy Server, first released in 2008, was ten years ahead of its time.
(See how your agency can go beyond identity based attributes to make fine grained access control decisions with Attribute Based Access Control (ABAC). Courtesy of Axiomatics and YouTube. Posted on Mar 2, 2018.)
Key Features of the Axiomatics Policy Server
Visibility and Control
- The Axiomatics Policy Server facilitates the creation, maintenance and governance of fine-grained, context-aware access control policy creation and deployment, while enabling a central management point for access control.
- It’s also an efficient streamlined approach that reduces cost and time for software deployment and the burden of maintenance.
Policy Authoring, Simplified
The tool comes with multiple policy editors to help meet the needs of policy lifecycle management in individual departments, and supports different types of collaborative workflows for policy maintenance.
The product suite is best-in-class due to the ease of use of the web-based graphical user interface for policy creation, editing and management.
Cloud, On-Premise or Hybrid Deployment
Multiple deployment models fit the needs of your organization, whether on-premise, hybrid or cloud.
Axiomatics Policy Server in the cloud makes it even easier for organizations to get started with externalized dynamic authorization while realizing the benefits of the cloud such as elastic scalability, reduction in TCO, and co-location with AWS-based applications.
Access the Axiomatics Policy Server in the AWS Marketplace here.

Developer Tools and SDKs
Axiomatics Policy Server (APS) editions come with rich APIs and software developer tool kits (SDKs) making it the most versatile and flexible solution on the market for implementation of Attribute Based Access Control (ABAC).
Axiomatic’s SDKs are available for customers on the company’s support web.
Multi-project Capability
An administrator can create separate projects, assign members and services to these projects, and manage them as required.
This helps address policy creation, governance and compliance issues faced by large enterprises and government agencies within an Attribute Based Access Control (ABAC) implementation.
Authorization Services
Any number of our authorization services can be deployed together within a domain to meet business continuity and high-availability requirements.
These include the Axiomatics Policy Decision Point, our SQL-based service and the Axiomatics Reverse Query.
Top Federal Government Security Trends for 2018 are Dominated by DevOps, Information Dissemination, Safeguarding Sensitive Data and Data Monitoring
Axiomatics Federal released its inaugural federal security update covering the latest trends and challenges for federal security agencies in 2018, earlier this year.

“Secure data sharing remains a challenge among intelligence agencies and many other federal departments when dealing with highly sensitive information, ” said Craig Gilley, president of Axiomatics Federal, Inc.
“Data sharing across departments, agencies, as well as state/local governments must meet the requirements of each agency, while ensuring that overall mission objectives are met.”
Axiomatics federal security leaders amassed these trends, which include:
DevOps
-
DevOps will become more prevalent for large federal agencies who are accustomed to building their own software in 2018.
-
This is mainly being driven by security concerns and the risk management framework.
-
By having uniform development tools across the enterprise, security and operational risks can be mitigated for mission-critical applications since all the DevOps tools and processes have been evaluated, tested and approved.
Information Dissemination between Federal Agencies
-
Federal government entities are amassing large volumes of data and the direction given by the Office of the Director of National Intelligence (ODNI) means that best efforts must be made to share this data throughout the intelligence community, with exceptions needing to be justified and approved.
-
To process these exceptions, agencies require metadata that describes aspects of the data to differentiate it from shareable data and policies must exist that can evaluate the characteristics (attributes) of the requester of the data, the data being requested, and what the requester wants to do with the data.
-
An Attribute Based Access Control (ABAC) model can achieve this by considering the context of the access control request.
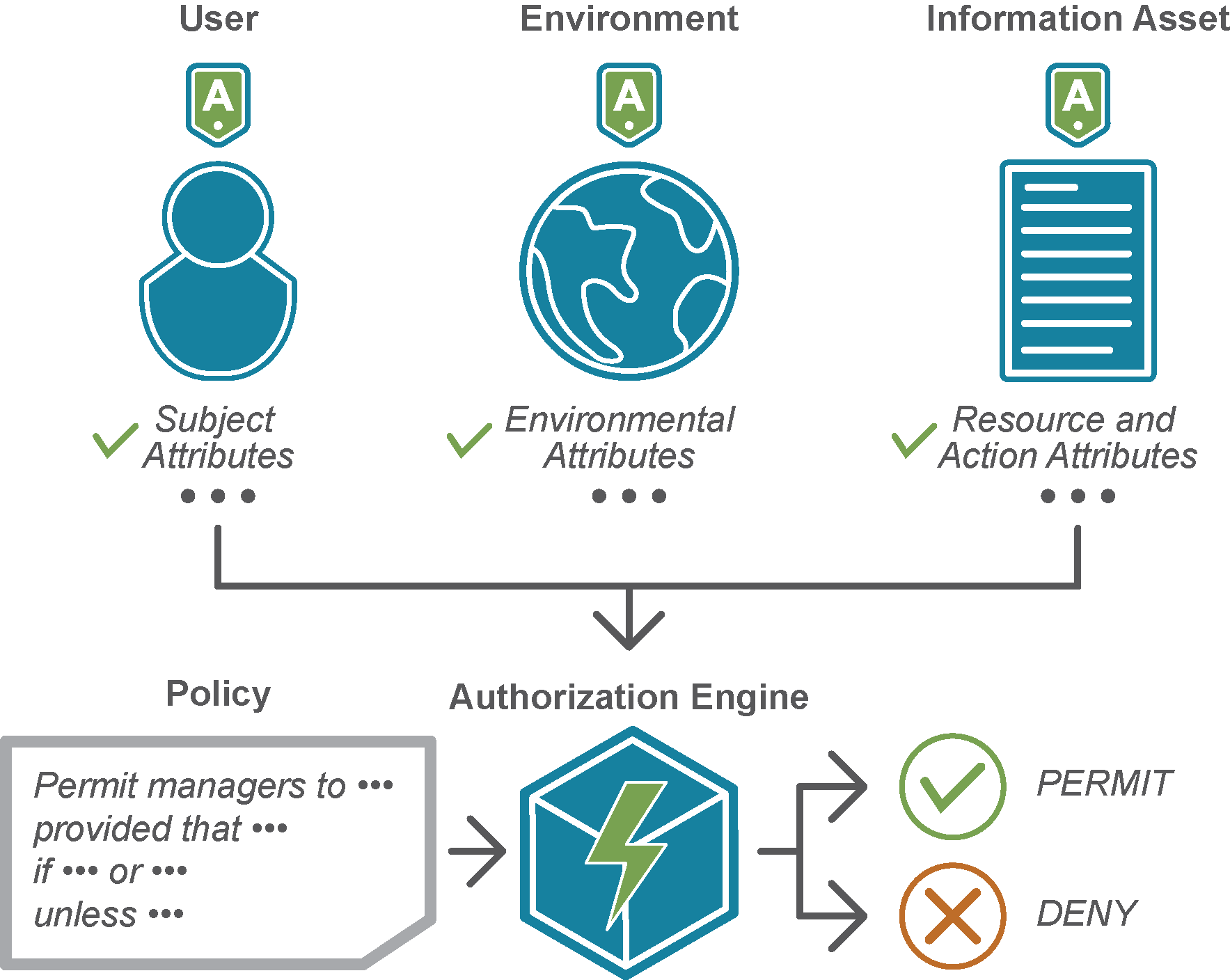
Securing Big Data Environments
-
Federal agencies have been inundated with so much data that they now need some level of data classification to determine if these data systems contain sensitive or regulated data that requires additional security.
-
The rise of big data systems in the cloud adds an extra level of complexity.
-
These systems will become much more distributed, making it difficult to manage the environment.
-
Big data technologies are also continuing to evolve quickly – new data formats, new access techniques and protocols are difficult to keep up with from a security perspective.
-
A key is to keep track of where the sensitive data is so that appropriate protections can be applied.
Data Monitoring to Prevent Security Breaches
-
Data monitoring will be a big theme as it continues to grow over time. Organizations should consider using data analytics, machine learning and Artificial Intelligence (AI), to identify anomalies that would otherwise go unnoticed by humans, helping to eliminate internal security threats.
-
ABAC systems provide a wealth of activity log data that is used to enhance reporting and monitoring systems.
“As the data explosion continues to have its effect on federal agencies, being able to manage and specify properly who should have access to data is a major priority,” said Gilley.
“By implementing an ABAC approach, organizations can progress toward a responsibility to provide mindset to better disseminate and share actionable intelligence to the community.”
Axiomatics Federal at a Glance
IAM teams in the federal government are finding that Attribute Based Access Control is key to meeting regulatory and compliance requirements.
Meet Mission Critical Objectives
Attribute Based Access Control (or ABAC) allows agencies to perform run-time access control based on digital policies derived from organizational, enterprise, or business policies.
This dynamic authorization model can define, for example, a mission-critical policy about a user’s access rights to a data record, taking into consideration the user’s identity, role within a government organization, credentials, and when he/she should be granted access.
Endorsed by NIST and NCCoE
 Endorsed by the National Institute of Standards and Technology (NIST) and the National Cybersecurity Center of Excellence (NCCoE), ABAC has quickly become the standard access control model for the Federal Government, ensuring sensitive data remains secure across innumerable applications and databases. solving many of the data leakage challenges that are present today.
Endorsed by the National Institute of Standards and Technology (NIST) and the National Cybersecurity Center of Excellence (NCCoE), ABAC has quickly become the standard access control model for the Federal Government, ensuring sensitive data remains secure across innumerable applications and databases. solving many of the data leakage challenges that are present today.
Combat Insider Threat
U.S. federal agencies can address Insider Threat and other access control challenges by managing access to sensitive data with dynamic authorization at the application, API, and data layers, from one centrally managed point.
Powered by Dynamic Authorization
ABAC is powered by the eXtensible Access Control Mark-up Language (XACML) standard, of which Axiomatics is a major contributor. Axiomatics products are all standards-based, enabling government agencies to effectively share information and collaborate securely.
CDM Contract Affiliate
As a CDM contract affiliate and GSA listed organization, Axiomatics’ works with the Federal Government, its contractors, and security integrators to deploy ABAC.
The Axiomatics authorization suite allows agencies to maintain complete control and visibility over access control, while providing a single point of management for digital policies that govern data access.
As regulations and security postures change, organizations can adjust policies once and have them apply agency-wide.

Why the Axiomatics Policy Server
The Axiomatics Policy Server is an industry-leading solution to control access to critical applications by using externalized dynamic authorization.
Customers benefit from using the Axiomatics Policy Server, as it provides a complete solution and the fastest decision point on the market for enterprise-wide roll out of policy-based access control by leveraging an Attribute Based Access Control approach.
The Axiomatics Policy Server is a part of Axiomatics extensive portfolio of fine-grained dynamic authorization solutions.
Axiomatics Federal, a wholly owned subsidiary of Axiomatics, is a U.S. company with offices in Reston, Virginia, and works closely with federal government agencies and partners to meet mission-critical access control needs with a policy-based approach delivery through externalized dynamic authorization management.
Complex government agencies require complete control over the access of their most sensitive data to reduce the threat of insider threat and maintain compliance with security directives and privacy laws.
Axiomatics Federal a Finalist in 2018 ‘ASTORS’ Homeland Security Awards Program
AST focuses on Homeland Security and Public Safety Breaking News, the Newest Initiatives and Hottest Technologies in Physical & IT Security, essential to meeting today’s growing security challenges.
 The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.
The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.
As an ‘ASTORS’ competitor, the Axiomatics Policy Server is competing against the industry’s leading providers of Innovative Access Control & Authentication Solutions.
To Learn More about the ‘ASTORS’ Homeland Security Awards Program, see 2017 ‘ASTORS’ Homeland Security Award Winners Honored at ISC East.

Over 100 distinguished guests from National, State and Local Governments, and Industry Leading Corporate Executives from companies allied to Government, gathered from across North America and the Middle East to be honored from disciplines across the Security Industry in their respective fields which included representatives from:
 The Department of Homeland Security(DHS) Science and Technology Directorate (S&T)
The Department of Homeland Security(DHS) Science and Technology Directorate (S&T)- U.S. Customs and Border Protection
- The Department of Justice
- The Security Exchange Commission
- State and Municipal Law Enforcement Agencies
- The Royal Canadian Mounted Police
- Leaders in Private Security
The highlight of the 2018 AST Homeland Security Awards Season is the 2018 ‘ASTORS’ Awards Presentation Luncheon to honor Nominees, Finalists and Winners on November 14, 2018 at ISC East 2018 at the Jacob Javits Exhibition Center.
Good luck to Axiomatics Federal on becoming a 2018 ‘ASTORS’ Homeland Security Awards Program Winner!
To Learn More on Axiomatics Federal and the Axiomatics Policy Server, please visit www.axiomatics.com/federal. For more information on Axiomatics, go to www.axiomatics.com.
Join us in Recognizing these Industry-Leading Firms for their Outstanding Product Development Achievements, Exciting New Technologies and Innovative Education Programs to address the growing Homeland Security Threats our Nation is facing.