Blue Ridge Networks, a past Platinum Award Winner in the Annual ‘ASTORS’ Homeland Security Awards Program, is delighted to announce that the company’s new LinkGuard Platform has been nominated to compete in the 2018 ‘ASTORS’ Award Program.
 Organizations today are undergoing digital transformations to improve business processes, and leveraging the internet to connected previously air-gapped systems.
Organizations today are undergoing digital transformations to improve business processes, and leveraging the internet to connected previously air-gapped systems.
But open-protocol information technologies (IT) have also made it easier for adversaries to access and exploit operational technologies (OT) such as physical security and surveillance systems within decentralized offices, medical equipment, remote systems and other network connected devices and systems associated with the Internet of Things (IoT).
The convergence of OT/IT means organizations are highly susceptible to lateral attacks from these connected systems, leaving core business functions, critical infrastructure, and sensitive data vulnerable to wide-scale disruption.
The LinkGuard platform allows organizations to cloak critical data networks, making them invisible and inaccessible to everyone that doesn’t have previously verified access using Autonomous Network Segmentation.

This methodology prevents hacker reconnaissance and eliminates the high risk of unauthorized access to critical infrastructure while enabling secure connectivity – wherever it’s needed, without costly or time-consuming IT overhead.
“LinkGuard adheres to a Zero Trust methodology which provides the highest level of security possible,” shared John Higginbotham, CEO of Blue Ridge Networks.
“This solution is an incredible asset to organizations in a very wide range of industries who are looking to seamlessly protect critical infrastructure operations.”

“The concept of zero trust is straightforward,” explained Maureen Gray, Chief Operations Officer at Blue Ridge Networks.
“A zero trust architecture eliminates the concept of a trusted network within a defined boundary to the outside and instead creates a much smaller perimeter around an agency’s most sensitive assets.”
“The advantage here is that a zero trust architecture enables much more granular security and control of the most valuable data or assets, providing a more secure environment overall.”
How it Works
LinkGuard is an operationally transparent and versatile overlay solution that enables organizations to seamlessly connect, isolate, contain, cloak, and manage any ethernet enabled connected device over any transport, anywhere in the world – with minimal network configuration changes.
The LinkGuard platform is comprised of the BorderGuard hardware appliance that serves as the root of trust for the entire platform, and RemoteLink and EdgeGuard products that extend the proven security architecture to dispersed offices, remote sites and users, devices and more.
LinkGuard’s security architecture has protected critical infrastructure for government and commercial customers for more than 20 years.
LinkGuard helps mitigate vulnerabilities and harden systems in three ways:
Prove
- Mutual mandatory authentication based on cryptographic identities ensures that a connection originates from an authorized and secure device according to the established policies.
- This eliminates IP spoofing, session hijacking and a variety of other attacks.
Protect

- Full packet encryption of data in motion is protected and not accessible to anyone other than the authorized parties as established by the policy.
- This enables secure communications and prevents data theft – even over untrustable means of communication.
Prevent
- Isolation and containment of systems and devices within the secure enclaves are completely segmented, preventing any attacker or malicious payload from penetrating the cryptographic boundary.
- Systems are also cloaked and invisible to attackers – drastically reducing the attack surface using obfuscation.
- Even previously compromised systems are protected because the information with in the enclave is contained and only accessible by another authorized party.
LinkGuard single handedly stops a wide range of attacks on OT and IoT devices by seamless segmenting the network and upholding automatic, robust security policies.
With the LinkGuard solutions, workgroups can also remotely access the connected devices for diagnostics, maintenance, and more.
(Learn More from Tom Gilbert, CTO of BlueRidge Networks. Courtesy of IoT Evolution and YouTube. Posted on Apr 17, 2018.)
Blue Ridge Networks’ LinkGuard Key Benefits
- Increased Efficiency – Minimal IT configuration and provisioning plus independence from traditional IT tools increases efficiency of both OT staff and users and drastically decreases operational expenses.
- Tried and Tested – Originally developed to protect high value critical operations and assets for the US Government.
- Reduced Network Complexity – Protects critical operations autonomously without dependence on complex traditional IT solutions like firewalls, VPNs, Access Control Lists, and VLANs.
- Seamless Integration with Existing Infrastructure – Overlays existing IT infrastructure with little to no modification to the underlying network infrastructure.
- Simple and Cost-Effective – Eliminates the need for pre-configuration and traditional IT tools that require staff to manage, drastically decreasing CapEx and OpEx.
- Built-in Two-Factor Authentication – Mitigates the vulnerability of exposure by not requiring a user to depend on a password, or shared secret, for authentication.
- Managed Services Option – Further decreases the complexity of secure networking: deploy LinkGuard as a managed service to allow IT teams to focus on more critical tasks.
Blue Ridge Networks’ LinkGuard solution, protects organizations from critical OT and IoT data networks and the communications between the devices and people that need access to them.
With LinkGuard, organizations can isolate, contain, and cloak critical infrastructure within cryptographic boundaries (secure enclaves) which mitigates the risk of unauthorized access to the devices and prevents data exfiltration.

Based on the Zero Trust methodology, LinkGuard enables complete and autonomous protection of your critical network by enabling your network to shield itself from cyber attacks without knowledge of the attack vector and without user intervention.
Because only previously verified users are able to access resources using LinkGuard, network admins are relieved of constant network monitoring and response.
LinkGuard’s proven security architecture has protected critical infrastructure for government and commercial customers for more than 20 years.
The operationally transparent and versatile overlay solution enables organizations to seamlessly connect, isolate, contain, cloak, and manage any ethernet enabled connected device over any transport, anywhere in the world – with minimal network configuration changes.
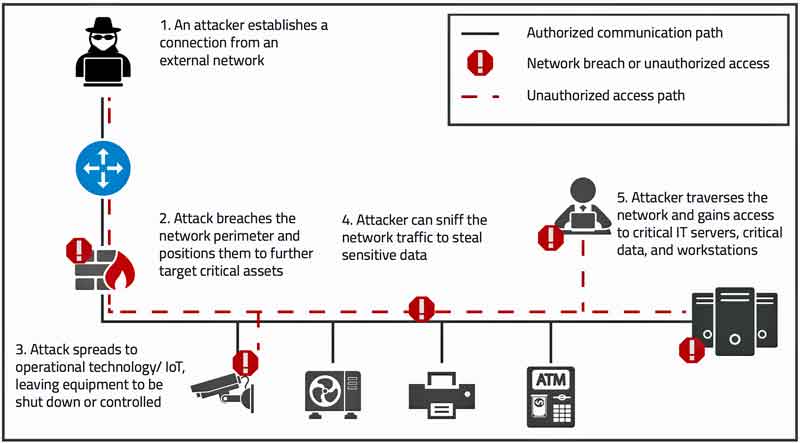
Attack Scenario Challenge: Secure connected devices and communications
Connected operational technology (OT) or Internet of Things (IoT) devices provide a wealth of opportunity for productivity and efficiency, but they also increase the attack surface by introducing weak points within an organizations network infrastructure. From these devices, attackers can traverse the network and bypass IT security defenses to steal critical data or gain control of connected devices.
Without Blue Ridge Networks
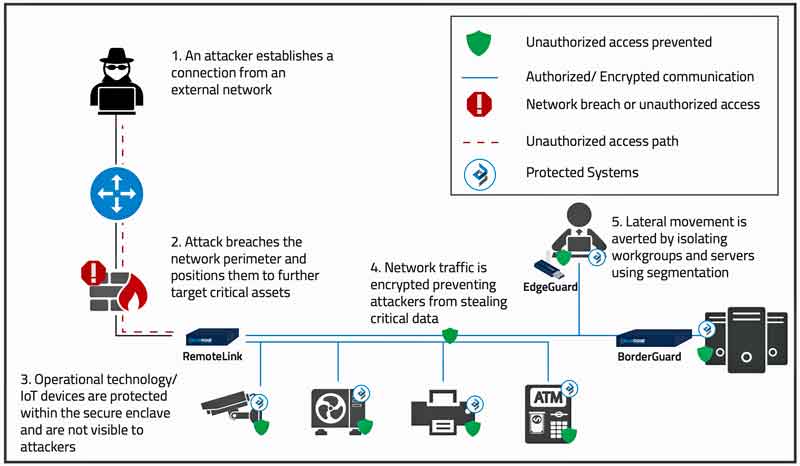
Solution: Isolate and contain critical assets
Deploying Blue Ridge Networks’ LinkGuard solution enables:
- Isolation and containment of devices, systems and workgroups using micro segmentation based on cryptographic identities
- Cloaking of infrastructure within BorderGuard enabled secure enclaves
- Encrypted communications between authorized systems within secure enclaves
Result: Protected and cloaked devices with ubiquitous access
With LinkGuard you can:
- Prevent and contain unauthorized access to connected devices, systems, and data
- Mitigate attacks on IoT devices
- Enable secure communications from authorized devices and users
- Reduce costs with seamless and flexible security and low configuration changes
With Blue Ridge Networks
Blue Ridge solutions have protected critical operations for some of the largest US government, financial, healthcare, and other critical infrastructure customers for more than twenty years with no reported breaches.
Based in Northern Virginia, Blue Ridge Networks is a visionary cybersecurity pioneer that provides autonomous cybersecurity for the connected world.
Blue Ridge Networks Competes in 2018 ‘ASTORS’ Homeland Security Awards Program
AST focuses on Homeland Security and Public Safety Breaking News, the Newest Initiatives and Hottest Technologies in Physical & IT Security, essential to meeting today’s growing security challenges.
 The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.
The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.
As an ‘ASTORS’ competitor, Blue Ridge Networks Linkguard will be competing against the industry’s leading providers of Innovative Cyber Critical Infrastructure Solutions.
To Learn More about the ‘ASTORS’ Homeland Security Awards Program, see 2017 ‘ASTORS’ Homeland Security Award Winners Honored at ISC East.

Over 100 distinguished guests from National, State and Local Governments, and Industry Leading Corporate Executives from companies allied to Government, gathered from across North America and the Middle East to be honored from disciplines across the Security Industry in their respective fields which included representatives from:
 The Department of Homeland Security(DHS) Science and Technology Directorate (S&T)
The Department of Homeland Security(DHS) Science and Technology Directorate (S&T)- U.S. Customs and Border Protection
- The Department of Justice
- The Security Exchange Commission
- State and Municipal Law Enforcement Agencies
- The Royal Canadian Mounted Police
- Leaders in Private Security
American Security Today will be holding the 2018 ‘ASTORS’ Awards Presentation Luncheon to honor Nominees, Finalists and Winners on November 14, 2018 at ISC East 2018 in New York City.
Last Call for the 2018 ‘ASTORS’ Homeland Security Awards at https://americansecuritytoday.com/ast-awards/.
The highlight of the 2018 AST Homeland Security Awards Season will be the 2018 ‘ASTORS’ Awards Presentation Luncheon to honor Nominees, Finalists and Winners on November 14, 2018 at ISC East 2018 at the Jacob Javits Exhibition Center.
 Good luck to Blue Ridge Networks on becoming a 2018 ‘ASTORS’ Homeland Security Awards Program Winner!
Good luck to Blue Ridge Networks on becoming a 2018 ‘ASTORS’ Homeland Security Awards Program Winner!
To Learn More LinkGuard and Blue Ridge Networks, please visit https://www.blueridgenetworks.com/ or call 1-800-722-1168.
Join us in Recognizing these Industry-Leading Firms for their Outstanding Product Development Achievements, Exciting New Technologies and Innovative Education Programs to address the growing Homeland Security Threats our Nation is facing.
Take advantage of this exclusive luncheon opportunity to Invite your Guests, Clients and Show Visitors to a lovely & affordable plated meal event in the heart of New York City, for a Fabulous Networking Opportunity!
ISC East is the Northeast’s largest security industry event and your ‘ASTORS’ Awards Luncheon registration includes complimentary attendee access to the show.
Already Exhibiting and/or Attending the 2018 ISC East Conference?
Join us to meet the 2018 ‘ASTORS’ Award Winning Company Executives & Government Agency Representatives.
Register today for the ‘ASTORS’ Homeland Security Awards Luncheon on November 14th, in New York City and give yourself & your clients a break from the show!
Gourmet luncheon choices available per person, or reserve a table – make an Impression on your Guests and Receive an Exclusive Discount Opportunity.