NIST Addressing Future Post-Quantum Cybersecurity Threats Today
QuSecure™, Inc., a leader in post-quantum cybersecurity (PQC), has announced its QuProtect™ PQC solution supports all of the post-quantum cryptography algorithms selected by the National Institute of Standards and Technology (NIST)...
BlackCat Targets Microsoft Exchange Signaling a Disturbing New Trend
Guest Editorial by Jon Hencinski, Director, Threat Detection & Response, Expel
On June 13, Microsoft posted this blog, “The many lives of BlackCat ransomware,” detailing the history of one of the most...
Ex-CIA Programmer Convicted of Vault 7 WikiLeak Breach (Videos)
July 14, 2022 – In Breaking News – FOX NEWS
A former CIA programmer was convicted Wednesday of federal charges in connection to the massive Vault 7 theft of secret information provided...
What Is the Log4j Vulnerability and Why It’s NOT an Easy Fix
Guest OpEd by Gilad David Maayan, CEO and Founder of Agile SEO
Log4j is a very popular logging package for Java. It is widely used by high-profile applications and services, including software...
Decision Makers Held Back from Delivering on IT Security Strategy
Delinea has announced a global survey of 2,100 IT Security Decision Makers (ITSDMs) findings which reveals that 60% of respondents believe their overall security strategy does not keep pace with the...
3 Steps to Build Hybrid Workplace Connection thru Virtual Experiences
Guest OpEd by Adam Riggs, Frameable Inc. CEO, @AARiggs
Offices around the globe are reopening, but the new workplace experience is sharply different than we remember.
After years of work-from-home arrangements, employees feel...
What Are Some of the Security Challenges in Smart Manufacturing?
The internet of things (IoT) has brought about a colossal change in the extent to which technological connectivity features in our everyday lives.
Furthermore, the industrial internet of things (IIoT) has...
Darktrace Nominated to Compete for Double ‘ASTORS’ Awards in 2022
Darktrace, a global leader in cyber security artificial intelligence, is pleased to announce two of the company's Cyber and Industrial Cyber Products have been nominated to compete in the 2022 'ASTORS'...
Darktrace Launches ‘PREVENT’ to Proactively Protect Organizations
Darktrace, a New Competitor in the 2022 'ASTORS' Homeland Security Awards Program, has launched Darktrace PREVENT™, an interconnected set of AI products that deliver a proactive cyber security capability to help...
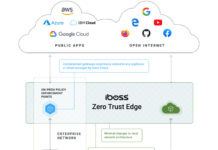
iboss Returns to Compete in 2022 ‘ASTORS’ Homeland Security Awards
iboss, a cloud security company that provides organizations and their employees fast and secure access to the internet on any device, from any location, in the cloud, who took home the...