
By Nico Fischbach, Global Chief Technology Officer for Forcepoint
Federal agencies are undergoing a massive transition from legacy IT technologies to the cloud.
Many CIOs have been focused on moving their organizations to hybrid, multi-cloud environments dependent on many different cloud providers for specific purposes.
But that’s what CIOs are actually sanctioning.
What about all of the unsanctioned cloud applications and services that employees might be using without the knowledge of federal IT managers?
Federal Agencies’ Shadow IT Challenge
The use of unsanctioned cloud applications – a phenomenon known as “shadow IT” – is growing.
A recent Ponemon survey, sponsored by Forcepoint, (titled Cloud Adoption in the U.S. Federal Government), revealed that 55% of federal agencies have strongly embraced the cloud, yet many of those agencies continue to struggle with cloud security.
Meanwhile, 71% said that visibility and governance remain challenges to properly securing use of cloud services and 69% reported that less than half of their cloud service providers are FedRAMP authorized.
These results indicate that agencies are running the risk of exposing themselves to vulnerabilities at the expense of digital modernization.
They need a better way to balance their efficiency and security needs.
(See how Forcepoint Cloud Access Security Broker (CASB) automatically discovers cloud application use, analyzes the risks and enforces appropriate controls for SaaS and production applications, to ensure the safe and productive use of cloud apps across all users and endpoints. Courtesy of Forcepoint and YouTube.)
The Need for Better Visibility and Control
This starts with providing IT teams with better visibility into and control over all of the cloud-based applications in use within their organizations.
Unfortunately, this is often easier said than done.
Employees are used to being able to simply pull out their credit cards and download applications to their mobile devices and PCs for the sake of expediency.
Sometimes, IT is the last to know when new applications are accessed—if they know at all.
Given this difficult situation, managers are faced with two unsavory options.
They could choose to stop the use of any non-sanctioned cloud application, but that could cause rancor amongst employees who are only trying to do their jobs more efficiently, not intentionally open up security holes.
Or, they could allow use of the unsanctioned applications while scrambling to figure out whether or not they have any vulnerabilities and how to support them.
Neither of these scenarios is ideal.
The former creates friction between IT and the employee base, while the other puts undue pressure on IT managers who are already strapped for time and resources.
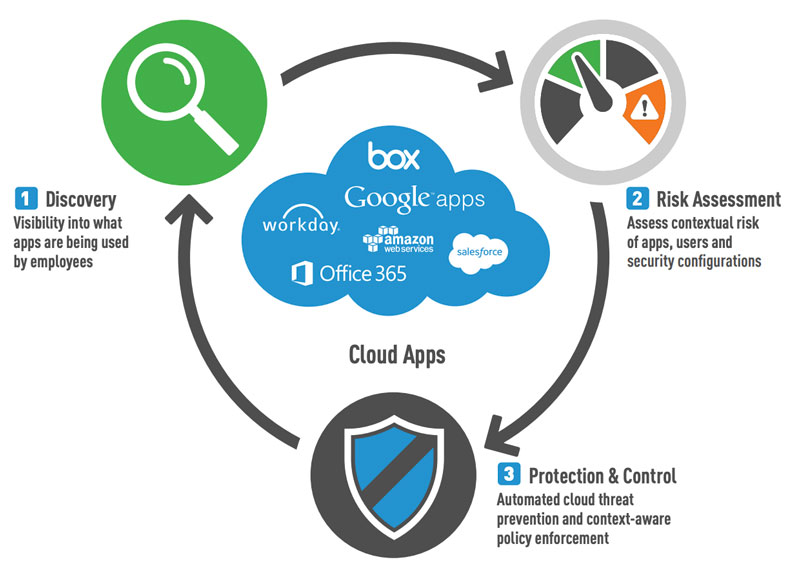
Cloud Access Security Brokers Offer a Viable Third Option
Cloud Access Security Brokers (CASBs) provide a viable alternative. CASBs operate between the end user and the hosted service provider, ensuring that any data that passes between the two is encrypted and exchanged securely.
They can be used to actively monitor every application on an agency’s network, giving managers a clear view of all of the different services that users are accessing.
CASBs can also ensure that applications adhere to an agency’s established security protocols.
This is done automatically, without the need for IT to spend an inordinate amount of time trying to establish the security bona fides of the hosted service provider.
Finally, a CASB can collect and analyze information about the various risk levels of each solution.
This allows IT managers to block access to applications that could pose a risk to the organization, while allowing use of those that adhere to an agency’s security standards.
(What is a Cloud Access Security Broker (CASB)? Find out in this brief introduction. Courtesy of Forcepoint and YouTube.)
Visibility is a Vital Component
CASBs can be used to address the growing shadow IT phenomenon.
They provide a wide window into not only the types of applications that are being used on the network, but how individuals are using those applications.
For example, many agencies are already using some form of behavioral analysis to monitor how their users are interacting with applications on their networks.
They establish a baseline pattern of “normal” user behavior and compare any deviations in those patterns to that baseline.
For instance, one person may routinely sign into the same applications, from the same IP address and browser, on a regular basis – that’s their normal behavioral pattern.
Even a slight deviation in that pattern could indicate that something’s wrong – perhaps the user’s credentials have been compromised.
CASBs can be used in conjunction with behavioral analytics to form a security stronghold that’s virtually unmatched.
Managers can refer to their CASBs to see which applications a user is accessing, the type of data they’re working with, and so on.
They can detect anomalies in these patterns and establish whether or not that user should be considered high risk.
If any red flags are detected, the manager knows to act upon them immediately.
(EMEA Chief Security Strategist, Duncan Brown, shares how attackers will have a renewed focus on Public Cloud accessible systems and data in 2020. Courtesy of Forcepoint and YouTube.)
The Best of Both Worlds
A recent report suggested that the average organization shares confidential information with more than 500 third parties.
While that number might be slightly lower for government institutions, the point remains that the number of applications being used is a big one – and it’s only going to grow.
As the use of cloud services increases, agencies need a way to balance their love of the cloud with the need for tight security. CASBs can provide them with the best of both worlds.
About the Author

Nicolas (Nico) Fischbach is the Global Chief Technology Officer at Forcepoint.
Nico is leading Forcepoint’s cloud-first transformation as the CTO for the company’s cloud security business, where he oversees technical direction and innovation.
Before joining Forcepoint, he spent 17 years at Colt, a global B2B service provider, and was responsible for company-wide strategy, architecture and innovation.
Learn More…
(Forcepoint CTO Nico Fischbach, speaking at RSA, talks about how CISOs are now focusing on a risk-based model for security. Courtesy of Forcepoint and YouTube.)
Forcepoint Takes Platinum in 2019 ‘ASTORS’ Homeland Security Awards Program

Forcepoint
-
-
Best Vulnerability Management
-
-
Forcepoint Cloud Access Security Broker (CASB)
-
The Forcepoint Cloud Access Security Broker (CASB) is a proactive, data-centric, integrated solution, enable efficient and robust security for agencies who are moving to the cloud.
-
*Forcepoint was also a Winner in the 2018 ‘ASTORS’ Homeland Security Awards Program.
The 2019 ‘ASTORS’ Awards Program surpassed expectations with a record number of nominations received from industry leaders and government agencies, and drew over 200 attendees to the ‘ASTORS’ Awards Presentation Banquet – an exclusive gourmet luncheon and networking opportunity which filled to capacity, before having to turn away late registrants.

The event featured an impassioned and compelling keynote address by William J. Bratton, former police commissioner of the New York Police Department (NYPD) twice, the Boston Police Department (BPD), and former chief of the Los Angeles Police Department (LAPD), as he walked attendees through 50 years of American policing history, the impacts on the communities, and the evolution of critical communication capabilities in our post 9/11 landscape.
Commissioner Bratton, one of the world’s most respected and trusted experts on risk and security issues and Executive Chairman of Teneo Risk a global advisory firm, was recognized as the ‘2019 ‘ASTORS’ Person of the Year’ for his Lifetime of Dedication and Extraordinary Leadership in Homeland Security and Public Safety.
Why the 2019 ‘ASTORS’ Homeland Security Awards Program?

American Security Today’s comprehensive Annual Homeland Security Awards Program is organized to recognize the most distinguished vendors of physical, IT, port security, law enforcement, and first responders, in acknowledgment of their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.’
Over 200 distinguished guests representing Federal, State and Local Governments, and Industry Leading Corporate Firms, gathered from across North America, Europe and the Middle East to be honored among their peers in their respective fields which included:
- The Drug Enforcement Administration (DEA)
- National Center for Missing and Exploited Children (NCMEC)
- United States Marine Corps
- The Federal Protective Service (FPS)
- Argonne National Laboratory (ANL)
- United States Postal Inspection Service
- DHS S&T
- United States Marshals Service (USMS)
- The Port Authority of New York & New Jersey Police (PAPD)
- The Department of Justice (DOJ)
- The New York State Division of Homeland Security & Emergency Services (NYS DHSES)
- United States Border Patrol
- AlertMedia, Ameristar Perimeter Security, Attivo Networks, Automatic Systems, Bellevue University, BriefCam, Canon U.S.A., CornellCookson, Drone Aviation, FLIR Systems, Hanwha Techwin, HID Global, IPVideo Corp., Konica Minolta Business Solutions, LenelS2, ManTech, Regroup Mass Notifications, SafeLogic, SolarWinds, Senstar, ShotSpotter, Smiths Detection, TCOM LP, Trackforce, Verint, and More!
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace with over 75,000 readers at the Federal, State and local levels of government as well as firms allied to government.
American Security Today brings forward a fresh compelling look and read with our customized digital publications that hold readers eyes throughout the story with cutting edge editorial that provides solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

The AST Digital Publications is distributed to over 75,000 qualified government and homeland security professionals in federal, state and local levels.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches both Private & Public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from Government at the federal, state and local level as well as from private firms allied to government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants & Dams, Bridges & Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting & Concert Stadiums, our Nation’s Schools & Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
To learn more about the 2019 ‘ASTORS’ Homeland Security Award Winners solutions, please go to the 2019 ‘ASTORS’ Championship Edition Fully Interactive Magazine – the Best Products of 2019 ‘A Year in Review’.
The ‘ASTORS’ Champion Edition is published annually and includes a review of the ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firms products and services, includes video interviews and more.
 It is your Go-To source throughout the year for ‘The Best of 2019 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
It is your Go-To source throughout the year for ‘The Best of 2019 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware and Networking Security – Just to name a few), the 2019 ‘ASTORS’ CHAMPIONS EDITION will have what you need to Detect, Delay, Respond to, and Mitgate today’s real-time threats in our constantly evolving security landscape.
It also includes featured guest editorial pieces from some of the security industry’s most respected leaders, and recognized firms in the 2019 ‘ASTORS’ Awards Program.
Forcepoint is a global human-centric cybersecurity company transforming the digital enterprise by continuously adapting security response to the dynamic risk posed by individual users and machines.
To Learn how the Forcepoint Human Point system delivers Risk-Adaptive Protection to continuously ensure trusted use of data and systems, please visit www.forcepoint.com.
Based in Austin, Texas, Forcepoint protects the human point for thousands of enterprise and government customers in more than 150 countries.
For information about advertising opportunities with American Security Today, please contact Michael Madsen, AST Publisher at mmadsen@americansecuritytoday.com.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos























