
CMMC: First Steps for Any Organization Seeking Certification
Guest OpEd by James Norris, HumanTouch LLC
Cyber Risk Maturity, the process of managing cyber threats better every day, is not as hard to implement as it sounds.
In my experience as a Registered Practitioner (RP) working with a Registered Provider Organization (RPO), Maturity requires a good amount of trial and error followed by implementation and adaptation.
Think about when you watch someone grab the wrong part of the hot coffee pot – you conclude that is not a process you want to emulate, and when you pour your cup of coffee, you don’t get burned.
Any registered practitioner knows what not to do when building a network infrastructure and securing it, but it can be harder to figure out the right steps to take when there are so many moving variables and options on the marketplace.
My rule of thumb is this: Do Not Trust.
For the same reason you wouldn’t get your medical examinations from your dry-cleaner, you should find certified professionals to lead you to compliance.
It takes time and caution to find trustworthy and suitable suppliers.
The Department of Defense (DoD) must verify that its Defense Supply Chain (DSC) shows Cyber Risk Maturity to some Level before awarding a contract, because the entire security ecosphere depends on the supply chain’s participation in top cybersecurity standards.
With this in mind, the Cybersecurity Maturity Model Certification Accreditation Body (CMMC-AB) has been tasked with overseeing the process for approving RPOs and their RPs.
(The Cybersecurity Maturity Model Certification (CMMC) was introduced to the world in Summer of 2019 by the Office of the Under Secretary of Defense (OUSD). #CMMC consists of a new assessment model, audit procedures, and certification standards for addressing the state of cybersecurity throughout the Defense Industrial Base (DIB). This presentation is intended to dive into the details of the document, highlight key takeaways for DoD contractors, and preparations for Level 3. Courtesy of Summit 7 Systems and YouTube. Posted on Feb 6, 2020.)
Technology and strategies are constantly evolving to fight cybercrime and to keep our crown jewels safe within the cyber kingdom, because cybercriminals are trying equally hard to steal our tools and exploit our known vulnerabilities.
Cyber Risk Management is a responsibility each business owner owes to their employees, customers, and investors; it is our duty to work for a stronger posture every day.
If you look at the categories in the CMMC-AB Marketplace, you will notice the number of RPOs, RPs, and CMMC 3rd Party Assessor Organizations (C3PAO) is slim compared to the 300,000 organizations in the DSC.
There are not enough provisional assessors to handle the demand we are moving towards in the CMMC’s response to high levels of cybercrime, which is why it’s imperative to start maturing your Cyber Risk Management today.
By working to achieve a higher security standard right now, there will be fewer steps towards other valuable certifications like the Health Insurance Portability and Accountability Act of 1996 (HIPAA) or Payment Card Industry Data Security Standard (PCI DSS), since most compliance frameworks will already have common requirements.
Not only do these ensure the safety of the supply chain, but they give a competitive advantage when seeking new contracts.
The NIST 800-series has been viewed as successful best practices by many businesses, even those not currently under any requirement, and there is talk of similar requirements soon going beyond the DSC.
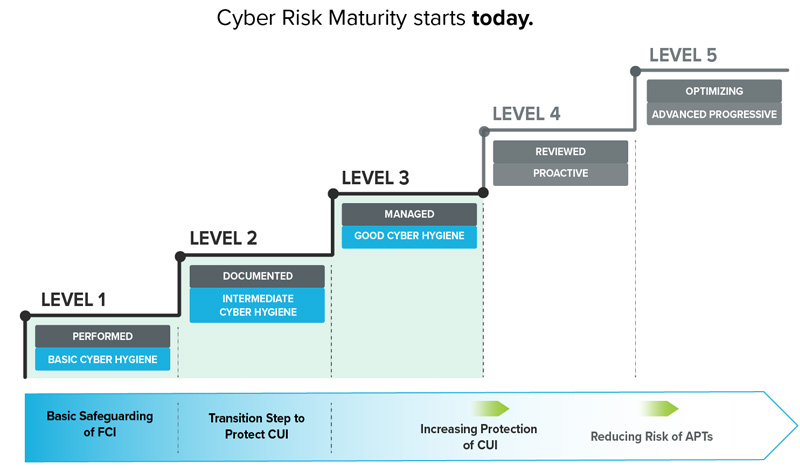
If you are like most of the industry and looking to meet Maturity Level (ML) 1-3, then you are likely asking how to meet the requirements of these levels, and probably getting some confusing answers.
That’s why I have been corresponding with business owners of small and micro small subcontractors, as well as executives at the big prime contractors – to understand the effects of the CMMC requirements already appearing in contracts and see how these requirements are playing out in real-time.
A lot of bigger contractors have Security Operation Centers (SOC) and other in-house capabilities that satisfy the requirements of CMMC.
When I ask the primes how they are supporting their supply chain in the effort to mature Cyber Risk Management capabilities, most of them are simply providing education to small businesses.
I know that a good business owner will look at many options before making the best decision for their business, and that starts with better education in Cyber Risk Management.
A lot of the questions about CMMC requirements are already being asked and answered across platforms that share it at no cost to you. Beyond just FAQs, there are so many additional resources available for free.
If you have not already, turn to your local Manufacturing Extension Partnership (MEP) for state funding to get your first phase of Cyber Risk Maturity in motion.
Most organizations that have been through a Cyber Maturity process will likely recommend working with an RPO if you want to get your money’s worth.
To help with questions left unanswered, our partners at ECS have created a buyers guide that delves into translating the requirements and understanding the goals. There are also resources like CyberAssist under NDISAC that will make it much easier to fill out a self-assessment questionnaire for NIST SP 800-171.
(Learn More. The Defense Federal Acquisition Regulation Supplement (#DFARS) 252.204-7020 is one of the three newly released clauses and requires contractors to provide the Government access to its facilities, systems, and personnel any time the #DoD is renewing or conducting a Medium or High #cybersecurity assessment. This clause also includes a flowdown requirement that states a contractor is now required to ensure all tiered subcontractors have results of a current assessment in SPRS in accordance with the DFARS 7019 clause. Courtesy of Summit 7 Systems and YouTube. Posted on Nov 6, 2020.)
Most contracts requiring you to upload your score into Supplier Performance Risk Score (SPRS) are not requiring the incumbent or awardee to have the controls 100% satisfactory – this is simply an exercise to record progress and map maturity.
Cybersecurity used to be treated as a pillar of consideration for DoD contracts before the move towards CMMC – now it is the foundation.
Find a good partner to translate the controls and help maintain your business as an asset before it becomes a liability. There are great vendors that listen, understand your need, and then communicate a solution clearly and treat your problems like their own.
To make the process of finding solutions that are optimized for your needs, I advise OSCs to start with consultants and advisors that are listed in the CMMC-AB marketplace. They have all have signed off on the Code of Professional Conduct (CoPC), which holds them accountable as CMMC professionals.
Cyber Maturity needs to go into all business decisions going forward if that business plans on staying afloat.
Do whatever you can now to ensure that your organization is prepared for what will come down the pipeline from the DoD. It’ll pay off in the long-term, winning you more contracts and costing national security less in the fight against cybercrime.
About the Author

James Norris is a Registered Practitioner (RP) at HumanTouch, LLC. He is committed to helping Organizations Seeking Certification understand the nuances of the Cybersecurity Maturity Model Certification, specifically small to medium businesses whose livelihood depend on compliance.
He has been under the wing of an Original Working Committee Group Member of the CMMC-AB learning the ropes of emerging regulations.
Norris’s passion and enthusiasm for cybersecurity and navigating organizations through their journey to certification is undeniable.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos

















