
New and enhanced mobile phishing and content protection capabilities are being transitioned to the government and private-sector, the Department of Homeland Security (DHS) Science and Technology Directorate (S&T) has announced.
A recently released update of the San Francisco-based Lookout, Inc. Mobile Endpoint Security platform offers enhanced endpoint and new mobile phishing protections. The enhanced platform, funded in part by S&T, is now available for iOS and Android operating systems.

“Most enterprise mobility management solutions require mobile endpoint security technology to continuously validate security and protect their mobile devices and applications,” said S&T Mobile Security Research and Development (R&D) Program Manager Vincent Sritapan.
“These advancements in mobile threat defense will protect sensitive data, such as personally identifiable information, on mobile devices and enterprise networks and greatly increase the security of the federal government’s mobile systems for mission-critical activities.”
An important new and first-of-its kind feature for mobile devices—phishing protection—was introduced to block mobile phishing attacks designed to steal user credentials or deliver malware.
Beyond simply detecting phishing attempts in SMS messages, the system also detects and prevents attacks that hide inside mobile apps, social media messages, and in personal and corporate email.
It inspects all outbound connections at the network level when a user attempts to connect, but does not inspect message content and therefore does not compromise end-user privacy.
(See how a mobile phishing attack, an example of a web & content based threat, can give attackers access to sensitive corporate data and put your enterprise at risk. Courtesy of Lookout Mobile and YouTube. Posted on Apr 5, 2018.)
The phishing protection system then alerts the user in real-time if the connection is harmful, preventing exposure to risky content such malicious apps or websites with known vulnerabilities.
“These new capabilities will alert device users, mobile enterprise administrators and security personnel to a wide range of mobile threats and allow them to remediate those threats and protect sensitive data from being compromised through mobile devices,” said Sritapan.
The rapid growth of mobile device and app use and the constantly expanding mobile ecosystem requires continuous validation and threat protection.
Vulnerabilities discovered in new devices and apps may be used by hackers as vectors to access sensitive government information and attack legacy enterprise network systems.
“Simply managing a mobile device is not enough to protect sensitive government information,” Sritapan said.
“The device also must have mobile endpoint security that alerts IT and security personnel to potential attacks. Without proper mobile security, agencies cannot adequately protect against data compromises.”
Additionally, government mobile devices are an attractive avenue to attack backend systems containing data on millions of Americans and sensitive information relevant to government functions.
Network-based attacks can exfiltrate sensitive data even when enterprise managers and app developers follow security best practices.
(Phishing is both different and more problematic on the mobile device than traditional endpoints. Most corporations are relatively well protected from email-based phishing attacks, through traditional firewalls, secure email gateways, and endpoint protection. In addition, people today are getting better at identifying phishing attacks. Mobile, however, has made identifying and blocking phishing attacks considerably more difficult for both individuals and existing security technologies. Enterprises seeking comprehensive protection against phishing attacks across all vectors, including the mobile device, need to look beyond status quo options. Lookout Mobile Endpoint Security offers the next level of defense required. Courtesy of Lookout Mobile and YouTube. Posted on Apr 5, 2018.)
The five links in the mobile phishing kill chain
It only takes one errant tap to compromise a mobile device.
That tap may be on a malicious URL that was truncated in the browser window, a URL an app accessed in its backend to unknowingly connect to a malicious ad network, or a link in personal email created to trick a user into offering corporate credentials — that enables an attacker to move laterally in your infrastructure towards your valuable data.
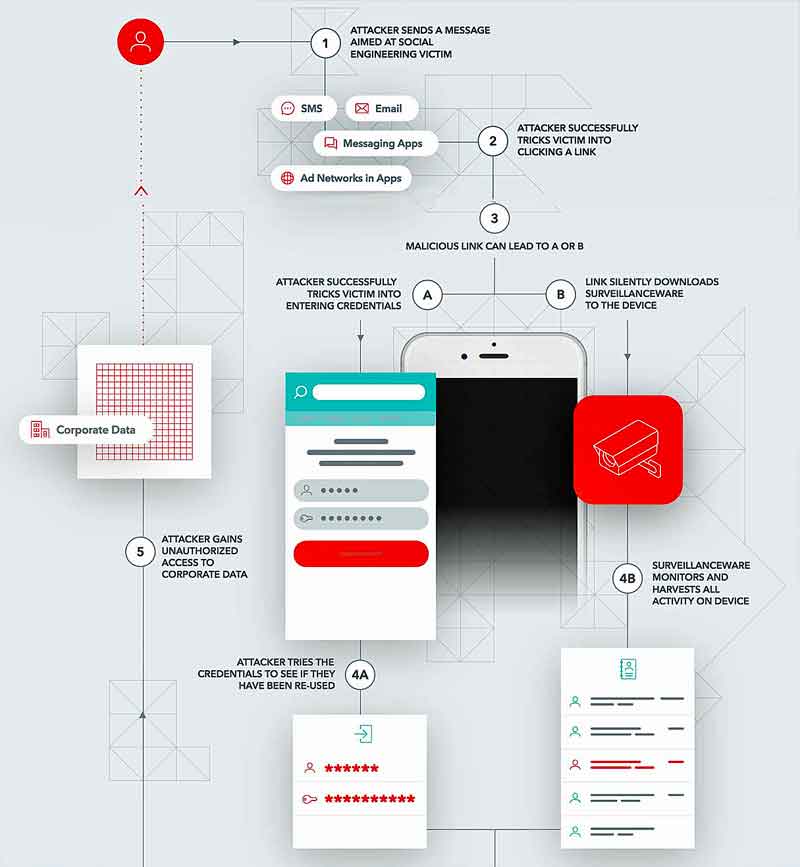
The newly enhanced system’s capabilities will provide confidence to mobile system managers and government mobile device users in protecting their data.
In the coming months, new features will be added to the Mobile Endpoint Security platform to allow:
- Visibility into malicious and risky third-party apps
- Improve detection of side-loaded apps (the transferring files between two devices) and advancing network-based threats such as man-in-the-middle attacks
- Provide a new investigation functionality for third-party apps, and
- Add a mobile vulnerability management system

















