
By Mohammed Murad, Vice President Global Sales and Business Development at LG Electronics USA, Iris ID Systems
Any enterprise organization has to approach security on two fronts – physical and the logical. Until recently, there’s been little linking of these separate needs.
Security has long been aimed at protecting physical assets such as people, facilities, equipment and inventory.
But securing sensitive data residing on servers, either local or in the cloud, has been more problematic.
Firewalls and anti-virus software have helped protect logical data from outside hackers.
But how can an organization be certain the person accessing an on-premises workstation truly is authorized to do so?
It can’t work by maintaining physical and logical security in separate silos.
It’s time for truly integrated solutions.
 Access control, surveillance cameras and intrusion systems on the physical security side combine to help keep unauthorized people out of buildings.
Access control, surveillance cameras and intrusion systems on the physical security side combine to help keep unauthorized people out of buildings.
On the logical side, the latest Personal Identification Verification (PIV) cards containing smart chips with employees’ photos, fingerprints, PINs and other details are a big step forward.
But cards and PINs can be stolen or lent and fingerprints can be spoofed or simply inaccurate.
What’s needed is a reliable and accurate end-to-end solution that bridges physical and logical security needs.
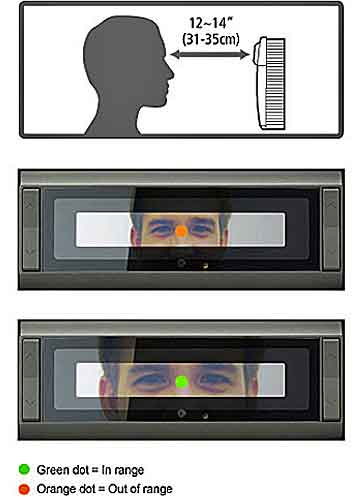
Identity verification based on a person’s iris offers that bridge.
Imagine this scenario:
- As an employee arrives at work he looks into an iris reader.
- The system recognizes her in the database and instruct the access control system to open the door.
- Inside, an iris reader integrates with the elevator operating system to make sure the employee gets to her restricted floor.
- There’s another reader directly outside her office.
- Finally, one more iris reader integrated with software on her work station ensures only she can access the computer and its data.
By using an iris for identity authentication, the need for employees to remember and frequently change passwords can be eliminated.
Employee credentials are easier to manage and security is improved.
Iris ID has begun demonstrating such an end-to-end system.
And we’re already working to provide a third-party solution to computer manufacturers looking to add another layer of security beyond what passwords and other biometrics provide.
(Learn More. Courtesy of Iris ID and YouTube)
What makes this door-to-computer system work is the uniqueness of the iris and the accuracy of iris-based identity authorization systems.
The iris, the colored part of the human eye surrounding the pupil, is like a snowflake – each one is unique.
A subject’s left and right iris are as different from each other as they are from any other individual’s. Even genetic twins have different iris patterns.
Studies have shown iris recognition provides an unmatched false accept rate of 1 in 1.2 million events.
Other biometrics, such as fingerprint and facial recognition, provide less accuracy and return far more “possible” matches requiring human interpretation.
Another reason this all works is the integration that’s now possible between the many security systems.
Enterprise organizations requiring the highest level of identity authentication are integrating iris readers into their access systems.
These readers can be deployed in lieu of card readers or used with them for added security.
Iris ID technology already integrates with leading access control platforms including Lenel’s OnGuard, Honeywell’s ProWatch and Software House’s C•CURE.
Integration has taken on added importance as multiple systems create multiple problems. Added stand-alone systems require more monitoring and maintenance.

That’s why enterprise users are looking for integrated systems to provide end-to-end solutions, such as the earlier example of an employee using iris recognition and the access control system for physical and logical access.
Another easy integration benefit comes from adding a time and attendance system connected to the iris readers.
The reports go directly to human resources, where software makes computing payroll more convenient.
It also eliminates a costly payroll fraud known as “buddy punching,” where one employee punches in or out for a friend not at work.
Iris recognition is being used around the world for many other uses such as border control, national IDs, healthcare enrollment and voter registration.
(Learn More. 60 minutes demonstrates Iris ID Systems CAM4000 for Advanced Iris Identity authentication at the high security Large Hadron Collider. Courtesy of 60 Minutes, Iris ID and YouTube. Posted on Nov 9, 2015)
Other biometric providers may offer one or two of the components of a total solution.
But Iris ID has the technology to provide complete solutions.
As the industry leader, Iris ID will continue to push the boundaries making our iris recognition systems the ideal choice for any application requiring fast, simple-to-use and highly accurate identity authentication.
And here’s a bonus – these solutions are no longer just the stuff of spy movies or for use by secret government facilities.
The cost has dropped to the point the technology can be employed by virtually any organization, anywhere.
Learn More…
SimplyWork Fights Fraud with Iris ID IrisAccess Integrated Time Clocks















