
A gigantic criminal network that was able to generate fake ad views and clicks to defraud millions of dollars from ad networks and advertisers over the past four years has been taken down by the FBI, working with major big tech companies.
This complex and ever-shifting global network of malicious bots, codenamed ‘3ve’ (pronounced ‘Eve’), infected at minimum 1.7 million computers at any given time, counterfeited more than 10,000 websites, and generated between 3 to 12 billion requests per day to sell fake online advertising.
(Learn More. CNBC’s Eamon Javers reports on a whitepaper from cybersecurity firm White Ops on digital advertising fraud coming from Russia. The “Squawk on the Street” crew weighs in. Courtesy of CNBC and YouTube. Posted on Dec 20, 2016.)
The coordinated efforts enabled law enforcement agencies to take down several of the criminal scheme’s botnets, and the U.S. Attorney’s Office for the Eastern District of New York to open a 13-count indictment against eight suspects believed to be behind this operation, three of whom are already under arrest and awaiting extradition to the US.
The 13-count indictment charges Aleksandr Zhukov, Boris Timokhin, Mikhail Andreev, Denis Avdeev, Dmitry Novikov, Sergey Ovsyannikov, Aleksandr Isaev and Yevgeniy Timchenko with criminal violations for their involvement in perpetrating the widespread digital advertising fraud.
The charges include wire fraud, computer intrusion, aggravated identity theft and money laundering.
Ovsyannikov was arrested last month in Malaysia, Zhukov was arrested earlier this month in Bulgaria, and Timchenko was arrested earlier this month in Estonia, all pursuant to provisional arrest warrants issued at the request of the United States, and are await extradition.
The remaining defendants are at large.

A white paper released by Google and cyber-security firm White Ops titled ‘The Hunt for 3ve’ outlines the eight suspects who are believed to be the main operators of the ad fraud scheme under codename ‘3ve’, which cyber-security and advertising industry experts have been tracking since last year.
“Today, we have helped the industry create real consequences for actors behind mass exploitation,” said White Ops CEO Sandeep Swadia.
“Fraud operations like 3ve bring distrust and instability to the Internet by compromising everyday people’s computers, stealing from businesses, and robbing content publishers.”
“The dismantling of 3ve, along with law enforcement’s actions to hold the individuals accountable, is an important milestone for the digital advertising ecosystem and for billions of humans who rely on a safe and open Internet.”
3ve comprised three complex sub-operations, each designed to evade detection.
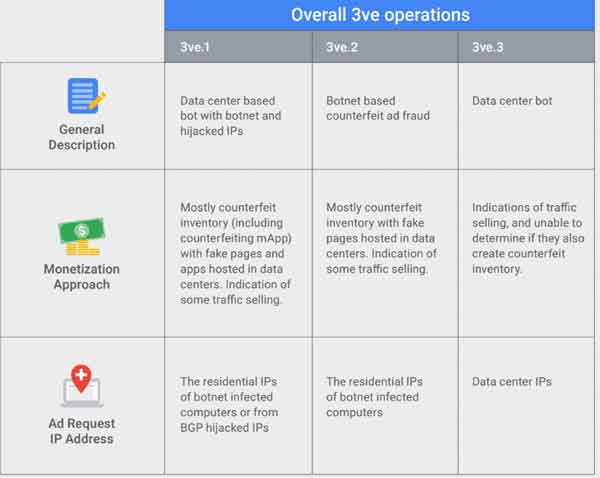
The operators behind 3ve built an intricate and evasive system by exploiting various techniques, such as infecting everyday users’ computers, remote controlling hidden browsers, stealing corporate IP addresses and counterfeiting websites.
3ve generated revenue by selling ad spaces on counterfeited premium websites and sending fake audiences to real websites.
“3ve was remarkably sophisticated,” added Tamer Hassan, CTO of White Ops.
“It showed every indication of a well-organized engineering operation with best practices in software development.”

“It exhibited reliability, resilience and scale, rivaling many state-of-the-art software architectures. To unravel the internal mechanics of such a fraud operation requires a multi-layered approach of real-time detection and prevention.”
To combat 3ve, White Ops and Google formed a broad allianceof nearly 20 companies spanning ad tech, security, and internet infrastructure worked together to better understand this threat.
All the while, White Ops deployed countermeasures to protect its customers and worked with the alliance to covertly hunt for 3ve, eventually dismantling it.
“Too often, the fight against fraud seems like a game of whack-a-mole,” added Swadia.
“Fraudsters, when discovered but not caught, can go underground, only to pop up across the street later.”
“This time it was different. We are truly grateful to all companies for their spirit of unity and collaboration in this endeavor.”
Additionally unsealed in federal court in Brooklyn were seizure warrants authorizing the FBI to take control of 31 internet domains, and search warrants authorizing the FBI to take information from 89 computer servers, that were all part of the infrastructure for botnets engaged in digital advertising fraud activity.
The FBI, working with private sector partners, redirected the internet traffic going to the domains (an action known as ‘sinkholing’) in order to disrupt and dismantle these botnets.
“As alleged in court filings, the defendants in this case used sophisticated computer programming and infrastructure around the world to exploit the digital advertising industry through fraud,” stated Richard P. Donoghue, United States Attorney for the Eastern District of New York.

“This case sends a powerful message that this Office, together with our law enforcement partners, will use all our available resources to target and dismantle these costly schemes and bring their perpetrators to justice, wherever they are.”
Mr. Donoghue thanked the FBI Cyber Division for its extraordinary efforts in carrying out the multi-year investigation.
“As alleged, these individuals built complex, fraudulent digital advertising infrastructure for the express purpose of misleading and defrauding companies who believed they were acting in good faith, and costing them millions of dollars,” added William F. Sweeney, Jr., Assistant Director-in-Charge, Federal Bureau of Investigation, New York Field Office (FBI).
“This kind of exploitation undermines confidence in the system, on the part of both companies and their customers.”
“Thanks to the hard work of our legal attachés and law enforcement partners overseas, with the cooperation of our international and U.S.-based private sector partners, the defendants will face justice for their alleged crimes.”
The Criminal Scheme
The internet is, in large part, freely available to users worldwide because it runs on digital advertising: website owners display advertisements on their sites and are compensated for doing so by intermediaries representing businesses seeking to advertise their goods and services to real human customers.
In general, digital advertising revenue is based on how many users click or view the ads on those websites.
As alleged in court filings, the defendants in this case represented to others that they ran legitimate companies that delivered advertisements to real human internet users accessing real internet webpages.
In fact, the defendants faked both the users and the webpages: they programmed computers they controlled to load advertisements on fabricated webpages, via an automated program, in order to fraudulently obtain digital advertising revenue.
The Datacenter-Based Scheme (Methbot)
As alleged in the indictment, between September 2014 and December 2016, Zhukov, Timokhin, Andreev, Avdeev and Novikov operated a purported advertising network (“Ad Network #1”) and, with Ovsyannikov’s assistance, carried out a digital ad fraud scheme.
Ad Network #1 had business arrangements with other advertising networks whereby it received payments in return for placing advertising placeholders (“ad tags”) on websites.
Rather than place these ad tags on real publishers’ websites, however, Ad Network #1 rented more than 1,900 computer servers housed in commercial datacenters in Dallas, Texas and elsewhere, and used those datacenter servers to load ads on fabricated websites, “spoofing” more than 5,000 domains.
To create the illusion that real human internet users were viewing the advertisements loaded onto these fabricated websites, the defendants programmed the datacenter servers to simulate the internet activity of human internet users: browsing the internet through a fake browser, using a fake mouse to move around and scroll down a webpage, starting and stopping a video player midway, and falsely appearing to be signed into Facebook.
Furthermore, the defendants leased more than 650,000 Internet Protocol (“IP”) addresses, assigned multiple IP addresses to each datacenter server, and then fraudulently registered those IP addresses to make it appear that that the datacenter servers were residential computers belonging to individual human internet users who were subscribed to various residential internet service providers.
As a result of this scheme, Ad Network #1 falsified billions of ad views and caused businesses to pay more than $7 million for ads that were never actually viewed by real human internet users.
The Methbot crimes, a major bot farm orchestrated by a group of Russia-based operators that defrauded major U.S. media companies and brand advertisers, was in operation until White Ops exposed its IP addresses in December 2016.
The Botnet-Based Scheme (3ve.2 Template A)
As also alleged in the indictment, between December 2015 and October 2018, Ovsyannikov, Timchenko and Isaev operated a purported advertising network (“Ad Network #2”) and carried out another digital ad fraud scheme.
In this scheme, the defendants used a global “botnet”¾a network of malware-infected computers operated without the true owner’s knowledge or consent¾to perpetrate their fraud.
The defendants developed an intricate infrastructure of command-and-control servers to direct and monitor the infected computers and check whether a particular infected computer had been flagged by cybersecurity companies as associated with fraud.
By using this infrastructure, the defendants accessed more than 1.7 million infected computers, belonging to ordinary individuals and businesses in the United States and elsewhere, and used hidden browsers on those infected computers to download fabricated webpages and load ads onto those fabricated webpages.
Meanwhile, the owners of the infected computers were unaware that this process was running in the background on their computers.
As a result of this scheme, Ad Network #2 falsified billions of ad views and caused businesses to pay more than $29 million for ads that were never actually viewed by real human internet users.
The Botnet Takedown
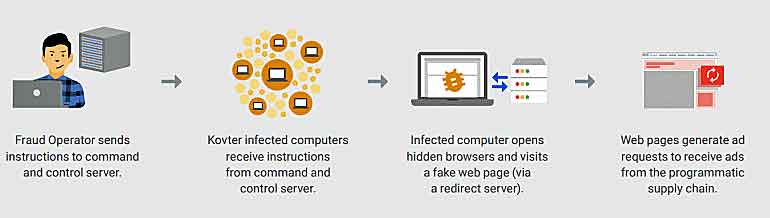
Following the arrest of Ovsyannikov by Malaysian authorities, U.S. law enforcement authorities, in conjunction with various private sector companies, began the process of dismantling the criminal cyber infrastructure utilized in the botnet-based scheme, which involved computers infected with malicious software known in the cybersecurity community as “Kovter.”
Kovter Malware
- Kovter malware is spread through email attachments and drive-by downloads.
- The ad fraud scheme that utilizes the Kovter botnet runs a hidden Chromium Embedded Framework (CEF) browser on the infected machine that the user cannot see.
- A C2 server tells the infected machine to visit counterfeit websites.
- When the counterfeit webpage is loaded in the hidden browser, requests are made for ads to be placed on these counterfeit pages.
- The infected machine receives the ads and loads them into the hidden browser.
- The FBI executed seizure warrants to sinkhole 23 internet domains used to further the charged botnet-based scheme or otherwise used to further the Kovter botnet.
The FBI also executed search warrants at 11 different U.S. server providers for 89 servers related to the charged botnet-based scheme or Kovter.
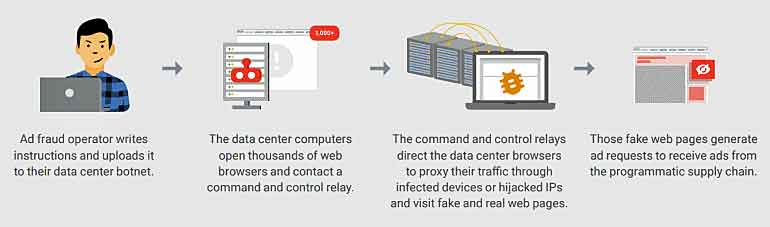
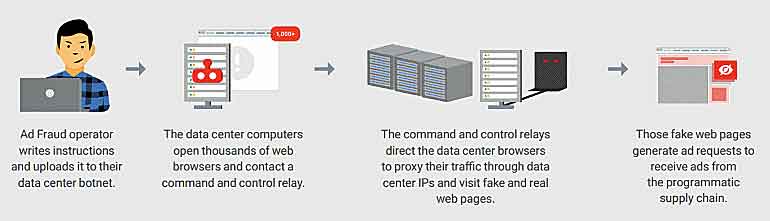
In addition, as part of its investigation, the FBI discovered an additional cybercrime infrastructure committing digital advertising fraud through the use of datacenter servers located in Germany and a botnet of computers in the United States infected with malicious software known in the cybersecurity community as “Boaxxe, or Miuref.”
Boaxxe/Miuref Malware
- Boaxxe malware is spread through email attachments and drive-by downloads.
- The ad fraud scheme that utilizes the Boaxxe botnet is primarily located in a data center.
- Hundreds of machines in this data center are browsing to counterfeit websites. When these counterfeit webpages are loaded into a browser, requests are made for ads to be placed on these pages.
- The machines in the data center use the Boaxxe botnet as a proxy to make requests for these ads.
- A command and control (C2) server sends instructions to the infected botnet computers to make the ad requests in an effort to hide their true data center IPs.
The FBI executed seizure warrants to sinkhole eight domains used to further this scheme and thereby disrupt yet another botnet engaged in digital advertising fraud.
Finally, the United States, with the assistance of its foreign partners, executed seizure warrants for multiple international bank accounts in Switzerland and elsewhere that were associated with the schemes.

“This investigation highlights public- and private-sector collaboration across the globe, and again confirms the absolute necessity for interagency information-sharing,” said James P. O’Neill, Commissioner, New York City Police Department (NYPD).
“Criminals – especially those operating via the internet – do not concern themselves with jurisdictional boundaries, so it is critical that the law-enforcement community works together to achieve our shared goal of protecting the people we serve.”
“I thank and commend the U.S. Attorney for the Eastern District, and all the investigators with the FBI Cyber Division and the NYPD. Together, we are ensuring that the vital systems and technologies of our economy are kept safe.”
Our collaborative effort with Google & key industry partners led to the takedown of one of the largest, most sophisticated #adfraud operations ever seen. More on “3ve” here: https://t.co/x1xPkJWizW
— White Ops (@WhiteOps) November 27, 2018
To Learn More, please visit the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) joint Technical Alert (TA18-331A) which provides technical specs on this major online ad fraud operation, which involves the control of over 1.7 million unique Internet Protocol (IP) addresses globally, when sampled over a 10-day window.
U.S. Computer Readiness Team (US-CERT) Solutions Provided in TA18-331A are as follow:
If you believe you may be a victim of 3ve and its associated malware or hijacked IPs, and have information that may be useful to investigators, submit your complaint to www.ic3.gov and use the hashtag 3ve (#3ve) in the body of your complaint.
DHS and FBI advise users to take the following actions to remediate malware infections associated with Boaxxe/Miuref or Kovter:
-
Use and maintain antivirus software.
- Antivirus software recognizes and protects your computer against most known viruses.
- Security companies are continuously updating their software to counter these advanced threats.
- Therefore, it is important to keep your antivirus software up-to-date.
- If you suspect you may be a victim of malware, update your antivirus software definitions and run a full-system scan.
- (See Understanding Anti-Virus Software for more information.)
-
Avoid clicking links in email.
- Attackers have become very skilled at making phishing emails look legitimate.
- Users should ensure the link is legitimate by typing the link into a new browser.
- (See Avoiding Social Engineering and Phishing Attacks.)
-
Change your passwords.
- Your original passwords may have been compromised during the infection, so you should change them.
- (See Choosing and Protecting Passwords.)
-
Keep your operating system and application software up-to-date.
- Install software patches so that attackers cannot take advantage of known problems or vulnerabilities.
- You should enable automatic updates of the operating system if this option is available.
- (See Understanding Patches and Software Updates for more information.)
-
Use anti-malware tools.
- Using a legitimate program that identifies and removes malware can help eliminate an infection.
- Users can consider employing a remediation tool.
- A non-exhaustive list of examples is provided below.
- The U.S. Government does not endorse or support any particular product or vendor.
















