Guest OpEd by Dean C. Alexander, professor/director of the Homeland Security Research Program at Western Illinois University and author of the recent book Family Terror Networks (2019)
Terrorists, whether inside or external to a family network, do not operate in a void. Nor are terrorists invisible.
They have jobs, family, friends, neighbors, coworkers, classmates, and other individuals in their lives.
Terrorist operatives shop, use banks and credit cards, rent storage units, acquire components for explosives, and buy weapons.
These contacts might be aware of the radicalization and extremist activities of others in their social network.
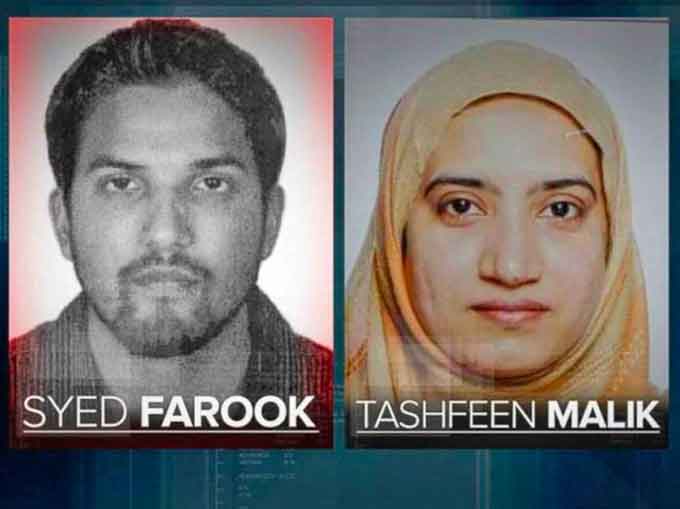
(Where did Syed Rizwan Farook and Tashfeen Malik get their radical views and their assault weapons? CBS News correspondent Carter Evans spoke with Farook’s father and tries to trace the path from quiet students to deeply religious mass murderers. Courtesy of CBS Evening News and YouTube. Posted on Dec 6, 2015.)
Operatives may enroll at educational institutions, take part in activities at recreation centers, attend religious services, and contribute to civic institutions.
Participation in such institutions may mask malevolent activities such as terrorism.
Some extremists leave electronic footprints (online, landline/mobile phones), which contribute to the prospects of detention.
Also, radicals use encrypted technologies making identification more difficult.
(The owner of the building granted ABC News and other media permission to go inside San Bernardino shooting suspects Syed Farook and Tashfeen Malik’s apartment following its seach by the FBI and SWAT teams. Courtesy of ABC News and YouTube. Posted on Dec 4, 2015.)
Terrorists can be discovered at locations where radicalization and recruitment transpire, such as religious, educational, and recreational institutions; workplaces, and prisons.
One can also find radicals at meetings and demonstrations aligned with an extremist group’s ideology.
Also, terrorists are sometimes recognizable through indicators such as vehicle/residential identifiers (bumper stickers and no trespassing signs) and physical/verbal identifiers (tattoos and extremist-infused rants).
Even lone wolves rarely live in complete isolation, often articulating their animus online and interacting with others through that medium, and, occasionally, in person.
Law enforcement can come across individual extremists while investigating traditional criminal acts.
These crimes might be precursor crimes so the terrorist can gain funds or materials to use in a prospective terror attack.
These crimes may involve counterfeiting or identity theft. False documents and misuse of identification could hide illicit activities.
After the 2016 Berlin truck attack, law enforcement found the perpetrator’s (fake) identity papers and fingerprints in the truck used in the massacre.
The terrorist met his demise in Italy after police asked him to show identification at a train station.
(Anis Amri, 24, pulled a gun on police after being asked for ID at a Milan, Italy, checkpoint. Courtesy of ABC News and YouTube. Posted on Dec 23, 2016.)
Additionally, a person may conduct a breach or an attempted intrusion of a secure location. Proprietary documents or materials may be stolen or diverted for future use to gain access to a site.
Other actions indicative of mobilization toward terrorism—a state in which one concludes using violence is justified and necessary—here or abroad include referencing an interest in a martyrdom operation, expressing plans to travel to a war zone or elsewhere overseas to join a terror group, seeking guidance for justifying violent acts, and recruiting others to join a cabal.
Other opportunities to find individuals involved in terrorism include routine police duties, such as conducting traffic stops, responding to calls for service, seeking witnesses to crimes, and investigating activities.
Tips alleging suspicious behavior may arise from an individual’s employees, coworkers, friends, neighbors, and strangers. Alternatively, individuals can be involved in suspicious travel domestically or internationally.
At some stage, radicals may articulate their extremist perspectives to others.
They may vocalize their calls for violence online, offline, or both. Those active online may follow extremist websites, social media networks, blogs, and online forums.
(Anis Amri, the Tunisian who rammed a truck into a Berlin Christmas market this week, was well known by police and even counter-terrorism agencies. Courtesy of euronews and YouTube. Posted on Dec 23, 2016.)
Additionally, they may get guidance online on multiple terror tools, such as communications, radicalization, recruitment, fundraising, explosives, tactics, targeting, and financing their operations.
Radicalization processes can occur quickly, so the time between radicalization and a kinetic incident may not prove particularly attenuated.
In other circumstances, an otherwise marginalized person may also have mental issues. Such a condition could be observable by family and acquaintances.
Police come across radicals in other venues and circumstances. For instance, police may see an individual dealing with a known criminal or terrorism suspect.
Likewise, police may follow up on a person who previously participated in terrorism or other crimes.
Law enforcement interacts with suspects through referrals from informants, businesses, nonprofits, nongovernmental organizations, and the public.
Police may interact with a terror suspect online or offline undercover activities.
Police get unsolicited tips from family members about their kin’s prospective plot.
At times, an officer receives a direct threat from a perpetrator, either in person and online.
Behaviors associated with the eight signs of terrorism include individuals conducting surveillance, gathering information, testing security, acquiring funds and supplies, acting suspiciously, impersonating police or security personnel, undertaking dry runs, and getting into position to undertake an attack.
These indicators of terrorism can arise at various stages of the terror cycle, depending on the operative(s) and their sophistication.
(Learn More. Terrorist operations usually begin with extensive planning. You can help prevent and detect terrorism — and other types of crime — by watching out for suspicious activities and reporting them to the proper authorities. Be alert for the eight signs of terrorism! The CELL CIAC – Colorado Information Analysis Center. Courtesy of robpatozz and YouTube. Posted on Oct 15, 2009.)
Moreover, suspicious activities can be distinguished by whether they are readily observable, observable, or hidden.
Similarly, these worrying actions can be differentiated among immediate, medium-term, and long-term concerns.
Depending on the classification, police will need to respond to these behaviors with varying levels of urgency.
Other points to weigh are whether these troubling activities are dangerous on their own accord (independent factors) or only with others (dependent factors).
Using encrypted technologies and digital currencies such as Bitcoin impedes the discovery of terrorists and their networks.
(A Long Island woman is accused of laundering bitcoin and other cryptocurrencies and wiring the money overseas to help the Islamic State group, then planned to travel to Syria.according to federal prosecutors. Courtesy of Fox News and YouTube. Posted on Dec 15, 2017.)
Extremists directly associated with a formal group tend to have good terror tradecraft, including communications, targeting, making explosives, and performing the attack.
In contrast, lone wolves or cabals are less adept at evading detection owing to absence of training.
(See a brief introduction to the Counter Extremism Project. Courtesy of the Counter Extremism Project and YouTube. Posted on Sep 24, 2014.)
Police challenges exist even when authorities suspect that an individual is involved with extremism.
For instance, constant surveillance is time consuming and costly financially and in terms of manpower.
The likelihood of catching terrorist fugitives depends on many factors, including the skillfulness of the terror operative, their support network, whether they make their way to a safe zone or ungovernable area, the capabilities of intelligence and law enforcement communities, and the public’s contribution in ferreting out the operation.
Terror incidents may take place in areas where the perpetrators live.
(Using exclusive surveillance footage obtained from MGM Resorts, we pieced together the last days of Stephen Paddock, the Las Vegas gunman. He plays video poker, laughs with hotel staff and hauls bag after bag of weapons into his suite. Courtesy of The New York Times and YouTube. Posted on Mar 22, 2018.)
Alternatively, an attack may happen many miles away from their homes, including overseas.
Analogously, both before and after an attack, individuals can be involved in hiding or moving across country.
By appreciating the characteristics of terror financing, law enforcement and others can gain insight into whether an individual might be involved in terrorism. Terrorists source their funds from licit and illicit means.
The sources of such legally obtained funds include personal accounts, family, friends, corporate donations, loans, legal donations, litigation settlements, government entitlements, and crowdfunding.
Illicit funding sources for terrorists include drugs, weapons, human trafficking, human smuggling, extortion, fraud, robbery, theft, pickpocketing, cigarette or commodity smuggling, traditional commerce, charities, and state sponsorship.
Foreign fighters have financed their travels by using their savings, funds from jobs, student loans, funds from family for university, stolen checks, and proceeds from litigation settlements.
(Sky News goes behind the scenes of West Midlands Police’s counter-terror operation, and shown a stash of deadly weapons seized by officers over the last two years, including a crossbow and a meat cleaver. Courtesy of Sky News and YouTube. Posted onJan 18, 2019.)
Funds designated for terrorist conduct may be moved through the following modes: cash, traveler’s checks, checks, wire transfers, money service business (licensed/unlicensed), hawalas, new payment systems (internet, mobile, digital currencies, pre-loadable cards), and casinos, among others.

In sum, terrorists do not operate invisibly—they leave physical and digital footprints. These presences in the physical and digital worlds present law enforcement with opportunities for their discovery.
About the Author:
Dean C. Alexander is Director, Homeland Security Research Program and Professor, Homeland Security at the School of Law Enforcement and Justice Administration at Western Illinois University. Prof. Alexander’s teaching, research, and speaking activities encompass terrorism, security, and legal issues.
He has lectured in ten countries, including to law enforcement and military officials, including at the National Intelligence University, NATO’s Centre of Excellence Defence Against Terrorism, Illinois Statewide Terrorism and Intelligence Center, Oregon Fusion Center, Michigan State Police, Milwaukee Police Department, McAllen Police Department, and Northern California Regional Intelligence Center, among others.
Prof. Alexander’s professional experience includes executive, business development, and legal positions in the United States and abroad, including Chile, Israel, and the United Kingdom. He worked as a consultant to the World Bank, Organization of American States, homeland security firms, and investment companies.
Since publishing on terrorism in 1991, Prof. Alexander has written several books on the subject, including: Family Terror Networks (2019), The Islamic State: Combating the Caliphate Without Borders (2015), Business Confronts Terrorism: Risks and Responses (Wisconsin, 2004) and Terrorism and Business: The Impact of September 11, 2001 (Transnational, 2002).
Prof. Alexander has been interviewed by domestic and international media. Prof. Alexander is on the Advisory Board of Security Magazine. He was a founding Advisory Council member of the Marsh Center for Risk Insights, research fellow at the Chesapeake Innovation Center, and served on the Anti-Terrorism Advisory Council executive board for the Central District of Illinois
Learn More…
The Bombing of Pan Am Flight 103

By the Federal Bureau of Investigation (FBI)
30 Years Later, Still Actively Seeking Justice
Most Americans were awakened to the reality of terrorism on September 11, 2001, but more than a decade earlier, a few days before Christmas in 1988, Pan Am Flight 103, bound to New York from London and carrying mainly U.S. citizens, was blown out of the sky by a terrorist bomb over the small Scottish town of Lockerbie.
(Thirty years ago, the bombing of Pan Am Flight 103 sent a shock wave around the world. In many ways, the reverberations are still being felt today. As FBI and Scottish investigators continue to actively pursue leads, many of those affected by the 1988 bombing recall the events as if they happened yesterday. Courtesy of the Federal Bureau of Investigation and YouTube. Posted on Dec 14, 2018.)
Mothers and fathers, grandparents, children as young as 2 months old, and college students returning home from a study abroad program lost their lives in what was the largest terrorist attack in American history until 9/11.
The bombing, believed to be carried out by Libyan intelligence officers in retaliation for U.S. actions against then-Libyan dictator Muammar Gaddafi, was a transformative event for the FBI, one that changed the way the Bureau investigates terrorism and assists victims of crimes.
Continue reading… The Bombing of Pan Am Flight 103
(Learn More… Courtesy of WSLS 10 and YouTube. Posted on Feb 5, 2019.)
Editor’s note: Our thoughts and prayers are with the family of Trooper Dowell, both blood and blue. Thank you for your bravery in serving the citizens of Virginia with pride and distinction. You will not be forgotten.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos



















