
With the explosive growth of non-traditional endpoints on government networks, it is critically important to gain a consolidated view not only of all government-owned PCs, laptops, servers and mobile devices, but also connected contractor and guest devices, IoT endpoints, operational technology (OT) systems, virtual machines—even rogue devices.
Forescout Technologies, a leader in device visibility and control, and a Winner in the 2019 ‘ASTORS’ Homeland Security Awards Program, offers a unique, is transforming enterprise-wide network segmentation with a new cloud-based offering.
Forescout eyeSegment will help organizations accelerate network segmentation projects, driven by the need to secure critical applications, mitigate increased exposure due to IoT devices, and limit the lateral movement and blast radius of threats across flat networks.

“The demands on today’s security organizations are greater than ever before. Attackers are proving again and again their ability to take advantage of the dissolving network perimeter and move unrestricted across company networks,” explained Michael DeCesare, CEO and president, Forescout Technologies.
“EyeSegment puts the security teams back in control.”
“Understanding what is on the network is in our DNA, and we are now using that visibility-first approach to give our customers the edge against attackers with true, enterprise-wide network segmentation.”
(Network segmentation doesn’t have to be difficult. Confidently design, build and deploy network segmentation at scale with Forescout eyeSegment. Courtesy of Forescout Technologies and YouTube.)
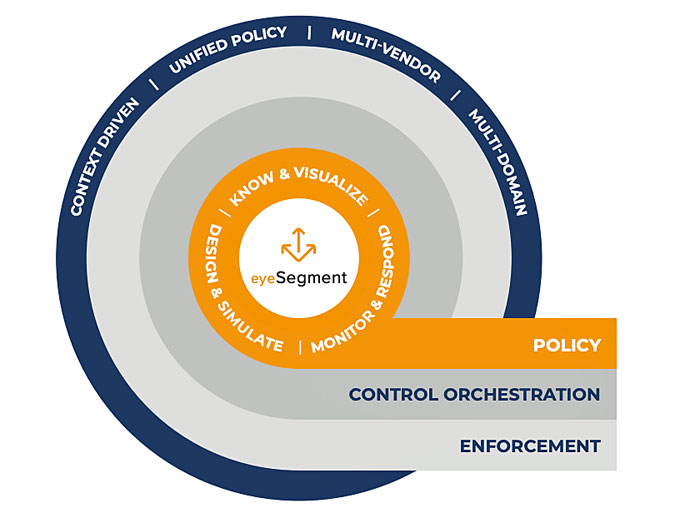
Forescout eyeSegment allows organizations to define and implement holistic network segmentation to secure the increasingly complex and interconnected enterprise network across campus, data center, cloud and OT.
eyeSegment Key Capabilities Include:
Translate every IP-connected entity into context and groups:
-
eyeSegment builds on Forescout eyeSight’s ability to automatically translate every IP-connected entity into a logical taxonomy of users, devices, applications and services.
-
Additional context from third-party systems, such as vulnerability and compliance information, can be integrated to this taxonomy to enable a customer to define policy in business terms and drive device segmentation decisions across the entire enterprise.
-
This capability closes the gap between infrastructure controls and business segmentation policy.
Visualize device communication and behavior:
-
eyeSegment then marries traffic flows to how these entities are communicating across all networks from campus, data center, cloud and OT in business terms.
-
Frequent baseline communication can be used to create a segmentation policy.
-
This accelerates segmentation design planning based on in-depth understanding of traffic flow baselines and anomalies.

Design and visualize policies and gauge impact:
-
Customers can proactively design, fine-tune and simulate policies before enforcing segmentation controls.
-
This allows organizations to determine how specific policies would impact the rest of their network from a single policy layer before implementing the controls to understand overall business efficacy.
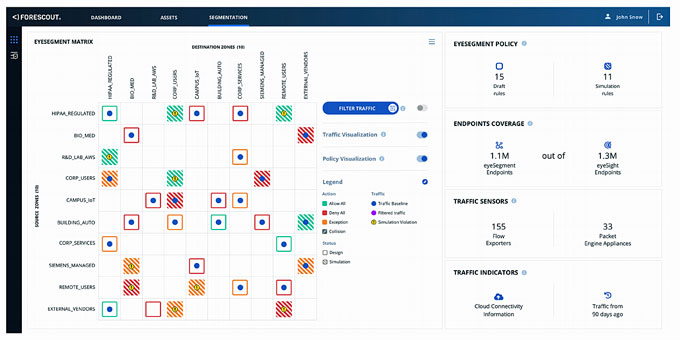
Monitor and automatically respond to policy violations:
-
eyeSegment allows customers to centrally monitor traffic flows between segmentation zones, validate Zero Trust controls, and automatically react to policy violations with restrictive controls, alerting and/or logging.
-
This approach allows customers to implement enterprise-wide segmentation policies quickly and only target violations which eliminates disruption.
Orchestrate heterogenous enforcement solutions:
-
Combined with eyeControl and eyeExtend, eyeSegment can orchestrate policy-based control actions across multiple segmentation enforcement points, such as next-generation firewalls, wired and wireless network infrastructure, software defined networking and cloud infrastructure, as well as agent-based segmentation technologies.
-
This allows customers to choose best of breed options across their enterprise to carry out restrictive enforcement
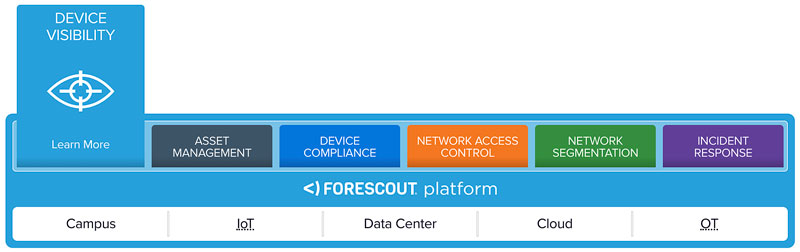
The Forescout device visibility and control platform offers a unique, agentless approach to network security, enabling government agencies to see all of these devices on their networks.
It continuously discovers, profiles and classifies devices, users, applications and operating systems while monitoring managed devices, personally owned devices and other endpoints.
The Forescout platform uses this contextual device intelligence to apply policy-based controls upon devices and orchestrate incident response and device remediation among multiple third-party security solutions.
In addition, Forescout excels at meeting or exceeding key technical and interoperability standards of military and civilian customers.
(How many devices do you have connecting to your network? What’s your IoT X Factor? Find out with ForeScout. Courtesy of Forescout Technologies and YouTube.)
Forescout uses its device visibility and control capabilities to improve and automate asset management, device compliance, network access control, network segmentation and incident response.
The solution currently scales to two million devices per deployment across the extended enterprise, including: campus, IoT, data center, cloud and OT.
Government agencies and contractors have a multitude of commercial technologies to consider for their network security, but often choose Forescout for the comprehensive device visibility and control capabilities it provides.
In addition to allowing users to automate and enforce policy-based network access control, device compliance, asset management, network segmentation and incident response, Forescout also provides an extensive range of automated controls that preserve the user experience and keep business operations running efficiently.
Part of the disruptive nature of the Forescout solution stems from the fact that it supports heterogeneous network infrastructure (switches, firewalls, wireless routers and cloud gateways).
It deploys very quickly, offering complete visibility in days, and full deployment in weeks (67 days on average)—with or without 802.1X authentication.
This technology-agnostic approach also extends to third-party IT management and security products, allowing government agencies and contractors to not only retain the products they currently use, but to also quickly embrace new technologies and vendors.
(Hear from Pedro Abreu, Forescout Chief Strategy & Product Officer, and Damiano Bolzini, VP Industrial & OT, as they discuss the future of OT security and the convergence of IT and OT with Nasdaq. Courtesy of Forescout Technologies and YouTube.)
Forescout extends value and improves effectiveness of these solutions by sharing contextual device insights and applying appropriate network and endpoint controls.
The new ways that the Forescout platform is being used includes providing granular visibility and risk assessment beyond traditional campus environments into data centers and the cloud, allowing a single-pane-of-glass view of security posture.
It is also provides accurate visibility and assessment of agentless IoT devices and operational technologies, with the ability to automate segmentation of these systems using native integration with switches as well as third-party integrations with leading next-generation firewalls.
Other innovative ways third-party tools are using the Forescout platform include integrating with ServiceNow® to provide an accurate, real-time device inventory and accelerate incident response.
(Learn More, hear from Michael DeCesare, CEO & President at Forescout, as he talks with Jeff Frick at RSA 2019 from the Forescout booth in Moscone North in San Francisco, CA. Courtesy of SiliconANGLE theCUBE and YouTube.)
The Forescout solution also feeds device intelligence to Splunk® and other security information and event management solutions for advanced event correlation and planning.
A broad range of security and IT management tools leverage the platform’s device visibility and control capabilities through Forescout eyeExtend products.
These and other use cases allow the combined solution to accelerate incident response, reduce the risk of operational disruption from security incidents or breaches, ensure and demonstrate security compliance and increase operational efficiency.
With the acquisition of SecurityMatters, and recent the release of SilentDefense 4.0 the Forescout platform now extends its visibility and control capabilities deep in to operational technologies and industrial control system (ICS) environments.
This allows Forescout capabilities to extend beyond IP-based systems, with deep packet inspection of over 100 IT and OT protocols for auto-classification of medical, industrial, building automation and IoT devices.
Forescout Takes Platinum in 2019 ‘ASTORS’ Homeland Security Awards Program

Forescout Technologies
-
Best Device Visibility and Control Solution
-
Forescout Device Visibility and Control Platform
-
The Forescout platform provides complete situational awareness and device visibility which enables an accurate device inventory, continuous compliance enforcement, policy-based access control, the ability to orchestrate actions to reduce cyber risk and rapid response to security incidents.
-
*Forescout was also recognized in the 2018 ‘ASTORS’ Homeland Security Awards Program.

The 2019 ‘ASTORS’ Awards Program surpassed expectations with a record number of nominations received from industry leaders and government agencies, and drew over 200 attendees to the ‘ASTORS’ Awards Presentation Banquet – an exclusive gourmet luncheon and networking opportunity which filled to capacity, before having to turn away late registrants.

The event featured an impassioned and compelling keynote address by William J. Bratton, former police commissioner of the New York Police Department (NYPD) twice, the Boston Police Department (BPD), and former chief of the Los Angeles Police Department (LAPD), as he walked attendees through 50 years of American policing history, the impacts on the communities, and the evolution of critical communication capabilities in our post 9/11 landscape.
Commissioner Bratton, one of the world’s most respected and trusted experts on risk and security issues and Executive Chairman of Teneo Risk a global advisory firm, was recognized as the ‘2019 ‘ASTORS’ Person of the Year’ for his Lifetime of Dedication and Extraordinary Leadership in Homeland Security and Public Safety.
Why the 2019 ‘ASTORS’ Homeland Security Awards Program?

American Security Today’s comprehensive Annual Homeland Security Awards Program is organized to recognize the most distinguished vendors of physical, IT, port security, law enforcement, and first responders, in acknowledgment of their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.’
Over 200 distinguished guests representing Federal, State and Local Governments, and Industry Leading Corporate Firms, gathered from across North America, Europe and the Middle East to be honored among their peers in their respective fields which included:
- The Drug Enforcement Administration (DEA)
- National Center for Missing and Exploited Children (NCMEC)
- United States Marine Corps
- The Federal Protective Service (FPS)
- Argonne National Laboratory (ANL)
- United States Postal Inspection Service
- DHS S&T
- United States Marshals Service (USMS)
- The Port Authority of New York & New Jersey Police (PAPD)
- The Department of Justice (DOJ)
- The New York State Division of Homeland Security & Emergency Services (NYS DHSES)
- United States Border Patrol
- AlertMedia, Ameristar Perimeter Security, Attivo Networks, Automatic Systems, Bellevue University, BriefCam, Canon U.S.A., CornellCookson, Drone Aviation, FLIR Systems, Hanwha Techwin, HID Global, IPVideo Corp., Konica Minolta Business Solutions, LenelS2, ManTech, Regroup Mass Notifications, SafeLogic, SolarWinds, Senstar, ShotSpotter, Smiths Detection, TCOM LP, Trackforce, Verint, and More!
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace with over 75,000 readers at the Federal, State and local levels of government as well as firms allied to government.
American Security Today brings forward a fresh compelling look and read with our customized digital publications that hold readers eyes throughout the story with cutting edge editorial that provides solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

The AST Digital Publications is distributed to over 75,000 qualified government and homeland security professionals in federal, state and local levels.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches both Private & Public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from Government at the federal, state and local level as well as from private firms allied to government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants & Dams, Bridges & Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting & Concert Stadiums, our Nation’s Schools & Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
To learn more about the 2019 ‘ASTORS’ Homeland Security Award Winners solutions, please go to the 2019 ‘ASTORS’ Championship Edition Fully Interactive Magazine – the Best Products of 2019 ‘A Year in Review’.
The ‘ASTORS’ Champion Edition is published annually and includes a review of the ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firms products and services, includes video interviews and more.
 It is your Go-To source throughout the year for ‘The Best of 2019 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
It is your Go-To source throughout the year for ‘The Best of 2019 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware and Networking Security – Just to name a few), the 2019 ‘ASTORS’ CHAMPIONS EDITION will have what you need to Detect, Delay, Respond to, and Mitgate today’s real-time threats in our constantly evolving security landscape.
It also includes featured guest editorial pieces from some of the security industry’s most respected leaders, and recognized firms in the 2019 ‘ASTORS’ Awards Program.
Forescout Technologies is a leader in device visibility and control.
The company’s unified security platform enables enterprises and government agencies to gain complete situational awareness of their extended enterprise environment and orchestrate actions to reduce cyber and operational risk.
For information about advertising opportunities with American Security Today, please contact Michael Madsen, AST Publisher at mmadsen@americansecuritytoday.com.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos






















