Demisto, an innovator in Security Automation and Orchestration and Response technology, and a Winner in the 2017 ‘ASTORS’ Homeland Security Awards Program, has been included in the list of “Cool Vendors” in the “Cool Vendors in Security Operations and Vulnerability Management”1report by Gartner, Inc.
 According to Gartner, “Future security operations, incident response and threat intelligence teams will use more automation and more consistent processes, and will have to deal with an ever-increasing number of security tools.”
According to Gartner, “Future security operations, incident response and threat intelligence teams will use more automation and more consistent processes, and will have to deal with an ever-increasing number of security tools.”
“This will necessitate more orchestration capabilities and clearly predicts a bright future for SOAR technologies.” 1
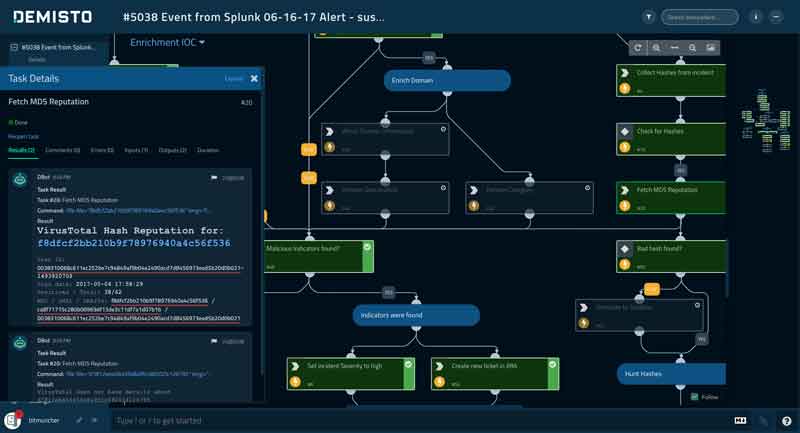
Demisto Enterprise integrates with more than 170 security products and enables organizations to build playbooks for different security operations.
By integrating other security products with Demisto, users can orchestrate actions across a suite of products in one window, automate response actions through playbooks, and run live security commands from a collaboration interface to remediate threats.
All of which can reduce mean time to response (MTTR) for security incidents and maximize ROI for the user company’s entire security product investment.
In addition, the case management and machine learning capabilities help security teams save resources and time while enforcing rigor and process to incident response.
(Learn More, courtesy of Demisto, Geektime and YouTube)
Demisto helps future-proof security operation centers (SOCs).
“We see being named a Gartner Cool Vendor as significant validation for Demisto’s unique solution that facilitates security incident response with orchestration and automation,” said Rishi Bhargava, Demisto co-founder and VP of Marketing.

“We’re experiencing rapid growth across various verticals, organizational sizes and geographies as companies adopt Demisto to address issues around alert overloads, analyst talent shortages and lack of product integration.”
“By alleviating such issues, Demisto helps companies reduce their overall mean time to respond to security incidents.”
Demisto’s solution has seen worldwide traction by helping SOC teams reduce the number of alerts requiring human review by as much as 95 percent.
It also solves the ever-growing problem of product fatigue – where analysts need to learn more and more products to mitigate threats throughout their infrastructure.
By working in a platform that integrates with all major security products such as SIEM, network, threat hunting, and end-point, it provides a comprehensive view into incident response.
Demisto Enterprise is designed keeping an enterprise scale in mind.
It is built on cutting edge yet proven technologies like including Golang, Docker and React.
These technologies enabled Demisto platform to be scalable, easy to manage and extend.
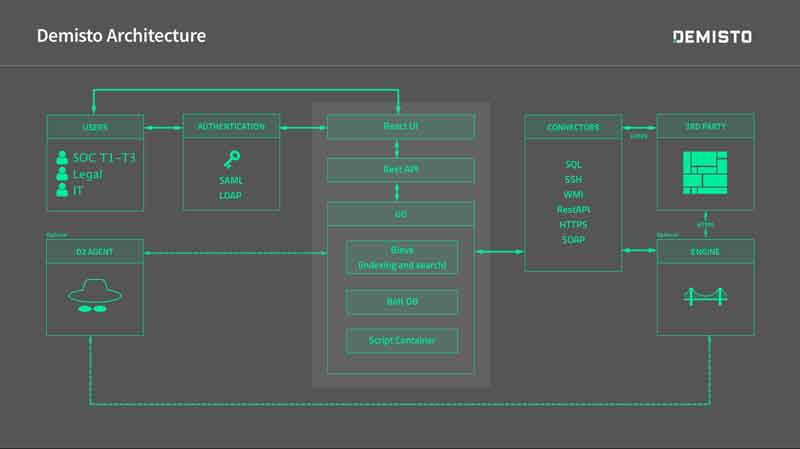
Enterprise Grade Architecture
Following are the core components of Demisto architecture:
Engine:
- Often in an enterprise multi-segment network scenario or SaaS deployment model, Demisto server may be not on the same network as the partner security product to be integrated.
- For these scenarios, the engine comes in very handy.
- Their engine is designed as a proxy that connects (outbound) to the Demisto main server using HTTPS and hence there is no need to open firewall ports to the engine.
- The engine, being in the same network, can connect to partner product directly.
Simplified Architecture and Multi-tenancy:
- Demisto is written in Golang using embedded BoltDB database and Bleve search.
- These components are shipped and installed with a single installer.
- At the same time, this architecture also enables very high scalability and multi-tenancy.
Modular UI and API:
- Demisto backend communicates with the web app using Rest API and hence any action that can be done from UI, can be done via Rest API.
- Their UI is implemented using ReactJS making it extremely fast loading and modular to give the best user experience.
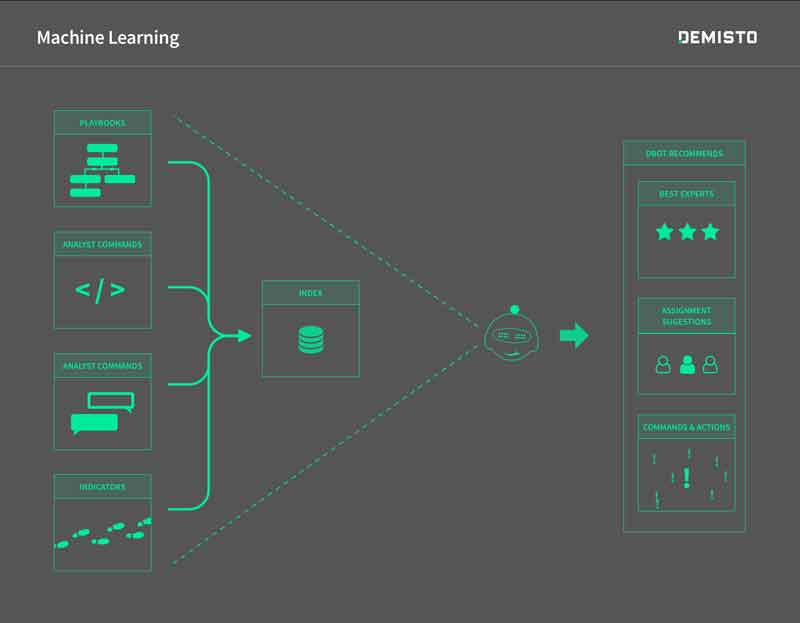
Machine Learning Powered IR
- All the playbook automation data, user generated forensics information and collaboration information is indexed in real time.
- The powerful indexing engine enables real-time query of the correlated information.
- In addition to the indexing, indicators like IP address, hashes of file, URL and other artifacts are correlated across incidents.
- These correlations are available to search and used for deeper investigations.
DBot learning engine applies learning algorithms like sequential pattern matching and more to generate – “Demisto Insights”.
- These insights include expert recommendations for best suited analysts for incident assignment and next set of commands to solve the incident.
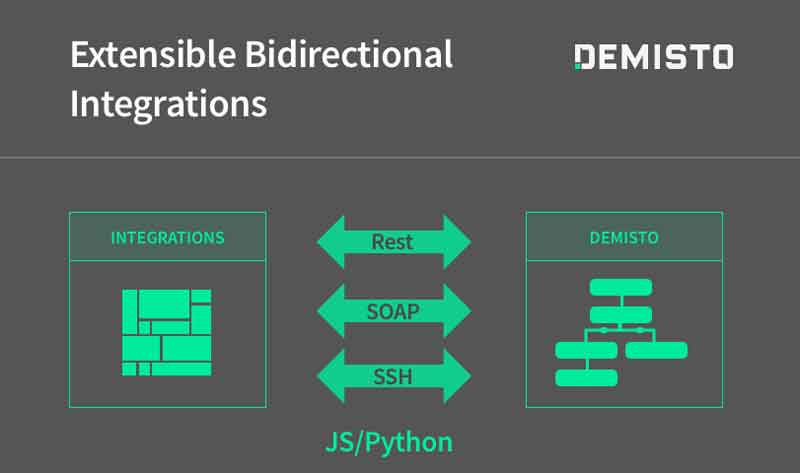
Extensible Integration Framework
- Demisto integrates with 100+ products out of the box already.
- In addition, Demisto Enterprise has been designed with a powerful SDK that enables building new integration easy and fast.
- There are no external tools or environments required to build new integrations.
- The new integrations can be built in Python or JavaScript.
- Demisto can integrate with partner products using any of the standard protocols and interfaces including Rest API, SOAP, SSH/CLI interface or even custom APIs.
- The SDK and sample code already has many examples of integrations using the above methods.
Once built, these integrations can be shared across within the customer environments or a larger community.
Demisto takes pride in the fact that the majority of their integrations are open source and we encourage customers and partners to leverage them to build new integrations.
Security and Isolation
Demisto Enterprise has been designed by security experts to make sure all the sensitive data is handled with right level of security controls.
Following are the key security considerations that have been implemented:
Complete isolation of each automation and integration:
- There is always a possibility an analyst makes an error in one of the automations.
- Demisto uses Docker to make sure all the automations and integrations are completely isolated during execution and inadvertent or malicious action does not harm the entire system.
Encrypted Credential Store
- Demisto provides a credential store for passwords for each integration so that common credentials are stored in the system and each analyst does not need to get access to the credentials.
Encrypted Communication
- All the communication with partner products and all sub-components within Demisto are encrypted.
Single Sign-on and Authentication
- Demisto support SAML 2.0 and LDAP authentication to make sure only authorized users can access the Demisto server.
Demisto Enterprise at a Glance
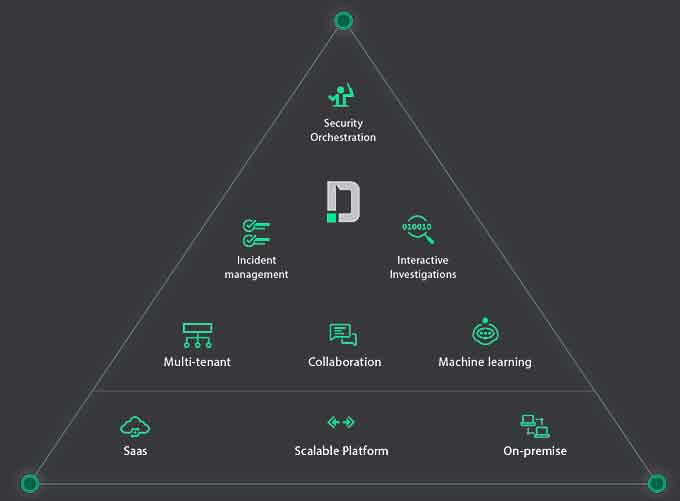
Demisto Enterprise is the first and only comprehensive Security Operations Platform to combine security orchestration, incident management, machine learning from analyst activities, and interactive investigation.
Demisto’s orchestration engine automates security product tasks and weaves in the human analyst tasks and workflows, enabling security teams to reduce mean time to response (MTTR), create consistent incident management process, and increase analyst productivity.
Demisto is backed by Accel and other prominent investors and has offices in Silicon Valley and Tel Aviv.
Demisto Takes Two in the 2017 ‘ASTORS’ Homeland Security Awards Program
-
Demisto
- Platinum ‘ASTORS’ Award Winner
- Demisto Enterprise
- Best Cyber Security for Incident Management

-
Demisto
- Gold ‘ASTORS’ Award Winner
- Demisto Enterprise
- Best Network Security Solution

Over 100 distinguished guests from National, State and Local Governments, and Industry Leading Corporate Executives from companies allied to Government, gathered from across North America and the Middle East to be honored from disciplines across the Security Industry in their respective fields which included representatives from:
- Recognized for their Innovative Training and Education Programs, Outstanding Product Development Achievements and Exciting New Technologies to address the growing Homeland Security Threats our Nation is facing.The Department of Homeland Security
- The Department of Justice
- The Security Exchange Commission
- State and Municipal Law Enforcement Agencies
- Leaders in Private Security
Nominations are now being accepted for the 2018 ‘ASTORS’ Homeland Security Awards at https://americansecuritytoday.com/ast-awards/.
American Security Today will be holding the 2018 ‘ASTORS’ Awards Presentation Luncheon to honor Nominees, Finalists and Winners on November 14, 2018 at ISC East 2018 in New York City.
To learn more about Demisto Enterprise, please visit the company’s website at https://www.demisto.com/product/
For ‘ASTORS’ Sponsorship Opportunities and More Information on the AST 2018 ‘ASTORS’ Homeland Security Awards Program, please contact Michael Madsen, AST Publisher at: mmadsen@americansecuritytoday.com or call 732.233.8119 (mobile) or 646-450-6027 (office).
Note 1 – Gartner, Inc., “Cool Vendors in Security Operations and Vulnerability Management,” by Kelly M. Kavanagh, et al, May 3, 2018.