Quantifying Asset Values, Threats, Vulnerabilities and Risks
Guest Editorial by Doug Haines
Every year or so, I get a medical check-up and every year the doc says, “Why don’t we schedule that colonoscopy for you now”. The idea of doing a “deep dive” sends shivers up my spine.
But you know what, he’s right every year or so you need to check your health on a deeper level. (Pardon the pun). Well, the same goes for your facility’s physical health.
I mean, after all, that’s what vulnerability assessments are all about.
They are designed to judge what kind of shape you’re in and then a prescription to fix what ails you.
Without a quantitative method for risk assessment and analysis, the question of “Am I or are we in good health – from a security stand-point”, cannot be truthfully answered.
In order to accomplish its purpose or function, every organization must protect personnel and critical assets from all threats, both natural and man-made.
Spending limited funds to protect personnel, assets, and equipment is a delicate balancing act in risk management.
The question always arises: “Am I getting enough BANG for my buck?” Responding, “I think so,” simply won’t cut it.
A quantitative risk analysis and vulnerability assessment methodology called ABRA (Asset Based Risk Analysis, pronounced ah-Bra) has been developed by Haines Security Solutions.
It identifies and measures risks and determines the most cost-effective countermeasures for mitigating those risks.
Although this method was originally designed to address terrorist threats, ABRA 2.0, if you will, uses the same process to effectively address criminal activity, sabotage, and espionage threats.
Risk Management
In risk management, the estimates calculated from a quantitative assessment are used as the basis for making decisions.
The following definition of risk management is used in the security engineering field:
Evaluating alternative countermeasures and design options and selecting from among them. This involves consideration of political, social, economic, and engineering information with risk-related information to develop, analyze, and compare acceptable options and to select the appropriate response to a potential threat. The selection process requires placing value on such issues as; the amount of risk considered acceptable, the reduction in risk due to applied countermeasures, and the reasonableness of the costs of countermeasures.
Because risk is quantifiable, it becomes a yardstick that can be used to make decisions about allocating resources (funding and people).
In ABRA, risk is associated with the protection of assets (personnel or property) rather than reinforcing the facility or building construction itself.
Security countermeasures are selected based on their likelihood of lowering risks to the asset as well as their cost effectiveness.
In many cases, risk analysis and risk management become an optimization analysis that examines risk reduction values (due to the implementing of countermeasures) and the associated costs to implement the identified countermeasures through a simple cost–benefit study.
Although performing a detailed risk assessment is normally a complicated task.
Following the ABRA methodology makes it much more manageable, because the results are site specific and tailored to an organization’s needs.
In turn, the results of the analysis can be used to make informed decisions in the allocation of resources to mitigate those risks.
ABRA Methodology
The primary purpose of ABRA is to quantitatively measure threats, assets, vulnerabilities, and risks associated with large and/or small facilities.
 It can be used for any asset where there are people or property needing protection (such as a child care centers, churches, government buildings, private businesses, schools, warehouses, etc.).
It can be used for any asset where there are people or property needing protection (such as a child care centers, churches, government buildings, private businesses, schools, warehouses, etc.).
It establishes a security baseline, explores upgrades, recalculates vulnerabilities and risks, and recommends optimized features or improvements for facilities.
In essence, ABRA identifies current levels of vulnerability and risk and then identifies improved levels with the implementation of specified countermeasures.
Basically, a snapshot of where the organization is today and where it could be in the future after countermeasures are implemented.
In addition, ABRA identifies the associated cost and impact of the improvements.
ABRA includes the performance of six sub-analyses: threat, target, vulnerability, optimization, risk, and cost–benefit.
Threat Analysis
Threat analysis is based on information collected during the site visit.
The information produces a threat rating, which measures the threat likelihood (the probability an attack will occur), and an effectiveness rating (the probability that an attack will be successful).
Target Analysis
Target analysis is designed to evaluate and measure the value of all targets to the user and to the aggressor. Targets could include any type of asset or target.
The end result of the target analysis is a numeric rating based on the target value or criticality to the user and the target value or usefulness to the aggressor.
Vulnerability Analysis
Vulnerability analysis is designed to quantitatively evaluate and measure how vulnerable a specific asset is to a specific threat.
This phase of ABRA identifies the countermeasures currently in place for a specific target and assigns a value based on the countermeasures effectiveness in mitigating threats (Baseline Vulnerability Rating [BVR]).
Optimization Analysis
Optimization analysis is the reapplication of the vulnerability analysis after implementing hypothetical improvements resulting from countermeasures that could be used for a specific asset.
Hypothetical countermeasures could include programmatic or procedural options.
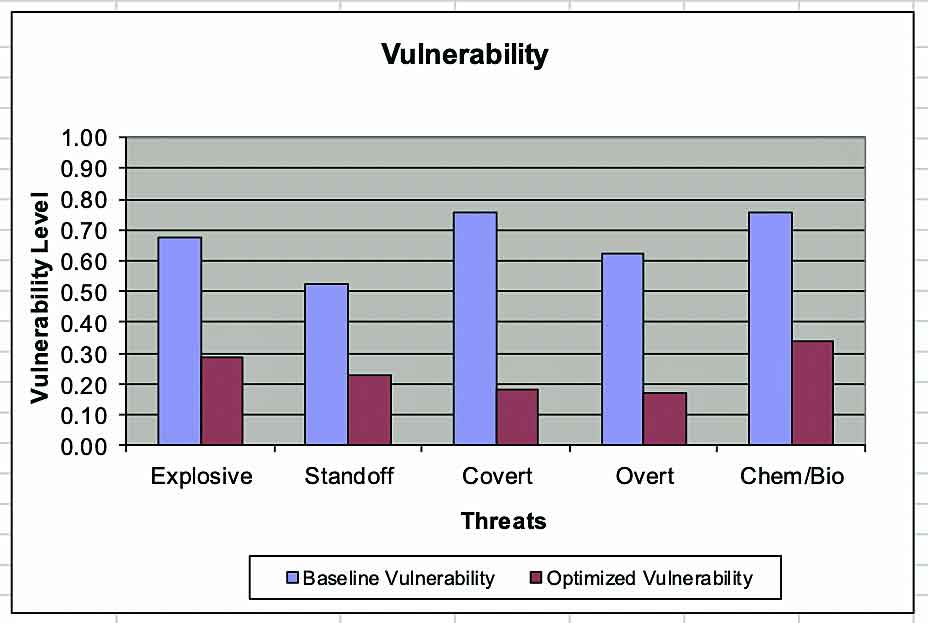
The end result is an optimized vulnerability rating (OVR) associated with the specific target being analyzed.
Based on the optimization analysis, the average vulnerability and risk rating can be identified and stated as a percentage.
Risk analysis is the aggregation of the threat, target, vulnerability, and optimization analyses to determine the calculated value of risk associated with a specific asset that is being targeted by a specific threat.
Cost–Benefit Analysis
Cost–benefit analysis compares the potential results of specific countermeasures for reducing or mitigating threats against specific assets.
The cost–benefit analysis is based on cost versus reduction in vulnerability and risk.
Defense-in-Depth
ABRA uses the process of defense-in-depth, also known as layers of defense, as a means to gauge the value of protection afforded each asset.
Defense-in-depth assumes that each layer of defense provides an opportunity to deter, detect, delay, or prevent aggressors from reaching their ultimate goal.
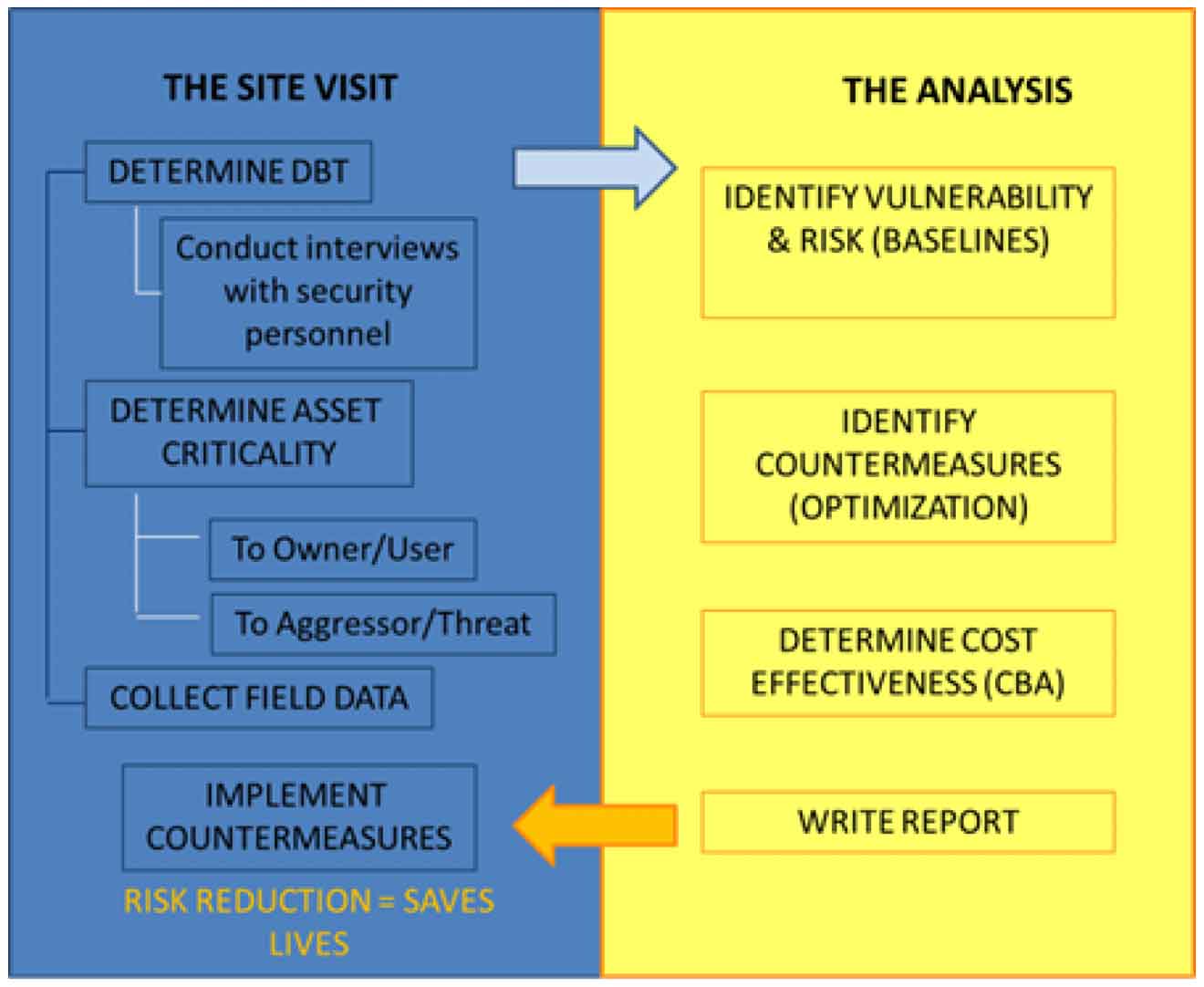
ABRA considers four primary layers of defense when computing the overall value of vulnerability and risk:
- Layer 1: facility or compound perimeter (property line)
- Layer 2: asset enclave perimeter (if there is one)
- Layer 3: asset exterior (e.g., building elevation or exterior)
- Layer 4: an enclaved area within the asset (e.g., cashier’s cage, secured vault)
ABRA goes further than simply identifying whether a particular layer exists. It also considers all countermeasures associated with each layer.
In most cases, each layer includes 40–50 individually rated countermeasures, all of which are assessed and considered in the ABRA process.
 In many cases, an asset assessed as part of this effort will not include all four layers.
In many cases, an asset assessed as part of this effort will not include all four layers.
A building asset without a physical barrier delineating the property line, for example, will not include Layer 1, and unless the building has its own enclave, it will not include Layer 2.
In all cases, the asset will have a Layer 3.
If the asset is a building and the building has interior spaces that have been identified as critical areas with controlled access, then it will include Layer 4.
In situations involving a stand-alone asset (e.g., water tank, transformer, antenna tower), only Layers 1, 2, and 3 would be considered, with Layer 3 being the asset itself.
Measurement
ABRA is a quantitative assessment using mathematical equations to calculate and measure asset value, threat likelihood, vulnerability and risk versus the standard vulnerability assessment process, which is a qualitative or subjective assessment which normally focuses on compliance to regulatory requirements.
Both methodologies identify vulnerabilities and recommend countermeasures to mitigate those vulnerabilities; however, ABRA goes further because it identifies current values of vulnerability and then reassesses those values of vulnerability based on implementation of recommended countermeasures.

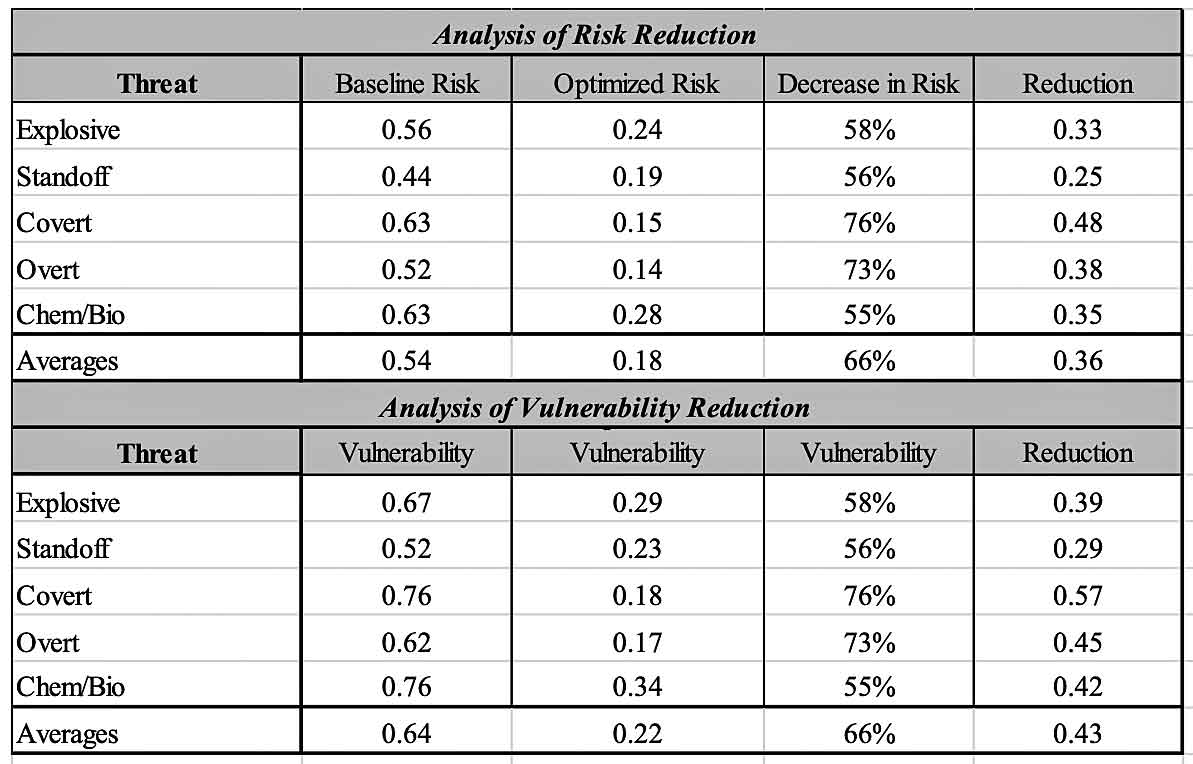
Not only does ABRA provide quantitative measurements of vulnerability and risk, it also provides cost estimates for the recommended countermeasures developed as part of the ABRA if they were to be implemented.
Knowing the BVR and comparing it to the OVR and then calculating the cost to reach the OVR, the ABRA methodology produces a cost–benefit analysis that can be used to prioritize countermeasures or compare one facility to another.
To summarize, ABRA quantifiably measures vulnerability and risk, prioritizes recommended countermeasures, prioritizes facilities, and compares cost and countermeasure effectiveness.
Most importantly, ABRA lets the customer know how vulnerable the asset is, what to do to reduce the vulnerability, how effective the recommendations will be in reducing the vulnerability, and at what cost.
ABRA Approach
Regardless of the type of analysis or study, the resulting recommendations need to be based on a given threat.
As it relates to designing physical measures to counter the identified threats, the HSS team performing ABRA must have a clear understanding of the design basis threat (DBT) to make appropriate and cost- effective recommendations.
The performance of ABRA is not driven by regulation or design standards; therefore, the DBT must be identified before recommendations can be generated.
A typical assessment team is made up of subject matter experts specializing in physical and technical security, law enforcement, forced-entry tactics, electronic security systems, antiterrorism, force protection, engineering, criminal and terrorist intelligence, logistics, and quantitative analysis.
The analysts work with customers to identify the criticality of assets within an organization. Sometimes, the customer has already identified single-points of failure as their most critical assets.
SPFs come in many shapes and sizes. Tangible locations are usually easily and readily identifiable; such as, a building or an energy system node.
SPFs within processes or procedures are a little more difficult to identify. None the less, the ABRA methodology can be applied to both physical and procedural vulnerabilities and risks.
Unlike qualitative or subjective assessment methodologies that focus on regulatory compliance, ABRA quantifies vulnerabilities and risk, determines the cost effectiveness of specific improvements, and helps prioritize countermeasures.
 This in turn allows decision makers to plan for and seek hard-to-get funding.
This in turn allows decision makers to plan for and seek hard-to-get funding.
The ABRA methodology was selected as Best Risk Analysis Methodology in Government Security by a panel of experts at Security Today and was presented a Platinum GOVIES in 2017.
Request a Sample Case Study here.
Assessing facilities without assessing thier supporting infrastructure especially when it comes to energy systems is a disservice to the client and his/her constituents.
It’s kind of like going for the annual check-up and when referred not going to the follow-up appointment with the cardiologist. You’re going to have problems later.
With that in mind, HSS has also developed a risk analysis methodology, called Critical Asset and Infrastructure Risk Analysis® (CAIRA – pronounced Sear-rah) that is geared toward assessing energy systems (electricity, natural gas/fossil fuels, steam and non-drinking water) that support facilities and their critical infrastructure.
CAIRA was selected as the Best Risk Analysis Methodology in Homeland Security for 2018, by industry experts, and received a Platinum ‘ASTORS’ Award from American Security Today.
(Doug Haines, CEO, Haines Security Solutions(USA) spoke to BW|Businessworld’s Sapna Bhardwaj on the sidelines of Smart Cities India. He spoke on ‘How to Prevent Mass Casualties through Building Design’ through 5 Strategies. Courtesy of BWBusinessworld and YouTube.)
HSS is recognized as a center of expertise within the security community for risk assessment, providing services for many Federal; State, local government agencies and private companies around the globe, and is a founding member of International Centers of Security Training Excellence (ICSTE).

Each ICSTE member company offers courses in one of several security verticals yet provides a location for other members to present their courses upon request.
At its River Park location in Oxnard, CA architects, engineers, facility managers, planners and security professionals learn about antiterrorism countermeasures in building design, the integration of security technologies in the built environment, and risk analysis strategies.
The CPK-United BV (also an ICSTE founding member) training facility in Hilversum, The Netherlands gears its curriculum towards fashion retail, hospitality (hotel and nightclubs) and port security guard activities, executive protection and crisis management.

Tactics for patrolman and SWAT are taught by former police officers at the Greenville, NY training center, where a firing range and urban mock-up are on site.
In 2017, HSS’s Physical Security Engineering Training and Certification (PSET&C) program was recognized as the Best Homeland Security Education Program, by American Security Today and received a coveted Platinum ‘ASTORS’ Award.
For more information about ABRA, CAIRA, ICSTE or other services can be found on the company’s website at www.hainessecuritysolutions.com.
About the Author

Doug Haines, owner of Haines Security Solutions, LLC (HSS), is a United States Air Force veteran with over 45 years of law enforcement and security related experience, which includes teaching building design principles to architects, engineers, facility managers, planners, and security professionals.
HSS specializes in conducting quantitative risk and vulnerability assessments of federal, state and local facilities worldwide and other security related consulting services.
HSS also develops security criteria, conducts entry control point and security forces manpower studies, drinking water systems and critical energy infrastructure risk/vulnerability assessments, and develops, plans and conducts table-top and full scale antiterrorism, force-on-force, emergency response and disaster preparedness exercises.
(Learn More about Haines Security Solutions capabilities. Courtesy of Haines Security and YouTube)
Haines Security Solutions a Double Winner in the 2018 ‘ASTORS’ Homeland Security Awards Program
Haines Security Solutions
-
Most Innovative New Solution of the Year
-
Student & Faculty Emergency Response Training [SaFERST]
-
Best User & Best Risk Analysis Methodology
-
Critical Asset & Infrastructure Risk Analysis (CAIR Methodology)
-
*Doug Haines and Haines Security Solutions were also recognized in the 2017 ‘ASTORS’ Awards Program with Platinum Wins.
The Annual ‘ASTORS’ Awards Program is specifically designed to honor distinguished government and vendor solutions that deliver enhanced value, benefit and intelligence to end users in a variety of government, homeland security and public safety vertical markets.

The 2018 ‘ASTORS’ Awards Program drew an overwhelming response from industry leaders with a record high number of corporate and government nominations received, as well as record breaking ‘ASTORS’ Presentation Luncheon Attendees, with top firms trying to register for the exclusive high – end luncheon and networking opportunity – right up to the event kickoff on Wednesday afternoon, at the ISC East registration!
Over 130 distinguished guests representing National, State and Local Governments, and Industry Leading Corporate Firms, gathered from across North America, Europe and the Middle East to be honored among their peers in their respective fields which included:
- The Department of Homeland Security
- The Federal Protective Service (FPS)
- Argonne National Laboratory
- The Department of Homeland Security
- The Department of Justice
- The Security Exchange Commission Office of Personnel Management
- U.S. Customs and Border Protection
- Viasat, Hanwha Techwin, Lenel, Konica Minolta Business Solutions, Verint, Canon U.S.A., BriefCam, Pivot3, Milestone Systems, Allied Universal, Ameristar Perimeter Security and More!
The Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program highlighting the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition, and keep our Nation safe – one facility, street, and city at a time.
The 2018 ‘ASTORS’ Homeland Security Awards Program was Proudly Sponsored by ATI Systems, Attivo Networks, Automatic Systems, Desktop Alert, and Royal Holdings Technologies.
Early Bird Nominations are now being accepted for the 2019 ‘ASTORS’ Homeland SecurityAwards at https://americansecuritytoday.com/ast-awards/.
Comprehensive List of Categories Include:
| Access Control/ Identification | Personal/Protective Equipment | Law Enforcement Counter Terrorism |
| Perimeter Barrier/ Deterrent System | Interagency Interdiction Operation | Cloud Computing/Storage Solution |
| Facial/IRIS Recognition | Body Worn Video Product | Cyber Security |
| Video Surveillance/VMS | Mobile Technology | Anti-Malware |
| Audio Analytics | Disaster Preparedness | ID Management |
| Thermal/Infrared Camera | Mass Notification System | Fire & Safety |
| Metal/Weapon Detection | Rescue Operations | Critical Infrastructure |
| License Plate Recognition | Detection Products | And Many Others! |
Don’t see a Direct Hit for your Product, Agency or Organization?
Submit your category recommendation for consideration to Michael Madsen, AST Publisher at: mmadsen@americansecuritytoday.com.
2018 Champions Edition
 See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
Enter Early to Maximize Media Coverage of your Products and Services at Kickoff, and Get the Recognition Your Organization Deserves!
And be sure to Register Early for the 2019 ‘ASTORS’ Awards Presentation Luncheon at ISC East 2019 to ensure your place at this limited- space event!