
Horizon3.ai, a leading cybersecurity firm focusing on autonomous penetration testing, and a Platinum ‘ASTORS’ Winner in AST’s 2022 Homeland Security Awards Program, has issued its inaugural cybersecurity threatscape report titled: “Year in Review 2022: Through the Eyes of the Attacker.”
 The report reveals three major attack themes and ten of the most common misconfigurations, vulnerabilities, and weaknesses attackers are likely to detect and exploit.
The report reveals three major attack themes and ten of the most common misconfigurations, vulnerabilities, and weaknesses attackers are likely to detect and exploit.
Findings are derived from nearly 7,000 penetration tests (pentests) using the award-winning NodeZero™ platform.
NodeZero™ provides continuous autonomous penetration testing as a true SaaS offering to proactively find and fix internal and external attack vectors before attackers can exploit them.
The NodeZero™ portal provides organizations with a graphical representation of actual attack paths that an attacker could use to chain together misconfigurations, vulnerabilities, and weaknesses to compromise their network.
It also provides the insight necessary to mitigate risk by prioritizing exploitable weaknesses with their corresponding fix actions, enabling customers to verify that each weakness has been remediated.
(See how NodeZero provides continuous autonomous penetration testing as a true SaaS offering. With NodeZero, cybersecurity teams can proactively find and fix attack vectors before attackers can exploit them. Courtesy of Horizon3.ai and YouTube.)
NodeZero™ enables companies to run multiple pentests in a year to find, fix and verify what is reachable, vulnerable, and exploitable in their environment and verify their security posture regularly. In doing so, they achieved a level of detection previously reserved only for the most well-funded companies and organizations.
The “Year in Review 2022: Through the Eyes of the Attacker” report, was extracted from nearly 1 million assets evaluated in tests conducted by companies that deploy industry-leading security tools, employ experienced cybersecurity practitioners, and implement compliance policies,
A staggering 7% of those assets contributed to or would be directly affected by a critical impact as defined by the Mitre Corporation, an event that would cause program failure and an inability to achieve the customers’ minimum acceptable requirements, with over 200,000 different attack paths to impact.
Testing revealed conclusively that security teams, tools, and policies all require tuning and enforcement and that to accurately assess the effectiveness of an organization’s posture, it is crucially important to continually attack the environment in the same way a malicious cyber threat actor would.
Three Main Attack Themes and Ten Most Commonly Exploited Vulnerabilities
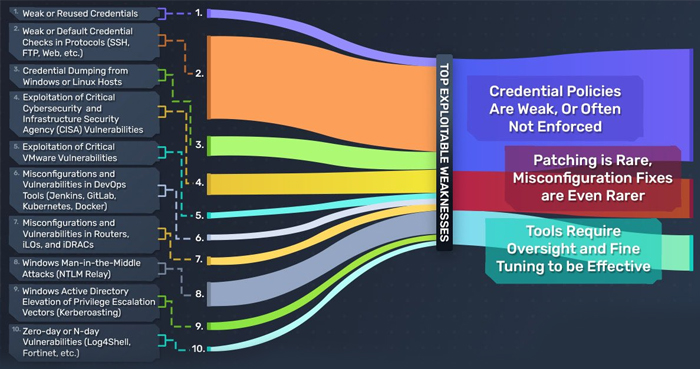
The three main themes or causes of exploitable weaknesses, vulnerabilities, and misconfigurations identified were:
-
Credential policies are weak or often not enforced: most often, attackers don’t “hack” in using sophisticated tools or exploits, they “live off the land” and log in with legitimate credentials. Recent research showed that 62% of all detections indexed by the fourth quarter of 2021 were malware-free.
-
Patching is rare, but fixes to misconfigurations are even rarer: many organizations found exploitable vulnerabilities that are several years old and have relatively easy fixes in the form of vendor-provided patches, including from CISA’s Top 15 Routinely Exploited Vulnerabilities list and Known Exploited Vulnerabilities catalog.
-
For example, NodeZero exploited the Remote Desktop Services RCE Vulnerability (CVE-2019-0708) “BlueKeep” 552 times this past year and EternalBlue (CVE-2017-0144) 565 times.
-
Critical VMware vulnerabilities were exploited 365 times, and misconfigurations and vulnerabilities were also common in popular DevOps tools and resources such as Jenkins (58 instances), GitLab (41 instances), Docker (50 instances), and Kubernetes (54 instances).
-
-
Tools need oversight and tuning to work effectively: “But my EDR should’ve stopped that….” was a common refrain among participants whose large investments in EDR solutions failed during pentests.
-
Many companies could not detect an unauthorized host such as NodeZero in their environment and prevent it from dumping a SAM database full of credentials. Often, it was not the tool itself that failed but rather a failure to properly configure the tool that resulted in the exposure of assets.
-
For example, NodeZero was able to use Windows MITM attacks (NTLM Relay) 1,450 times and captured 138,662 credentials.
-
Each of the top 10 vulnerabilities and weaknesses that NodeZero™ enumerated and exploited was the direct result of these three weaknesses. Each led to critical impacts, deeper implications, and ultimately to positive action by the customer to remediate them.
These top 10 vulnerabilities detected in 2022 were:
-
Weak or reused credentials
-
Weak or default credential checks in protocols (SSH, FTP, Web, etc.)
-
Credential dumping from Windows or Linux hosts
-
The exploitation of critical Cybersecurity Agency and Critical Infrastructure Agency (CISA) vulnerabilities
-
The exploitation of critical VMware vulnerabilities
-
Misconfigurations and vulnerabilities in DevOps tools (Jenkins, GitLab, Kubernetes, Docker)
-
Misconfigurations and vulnerabilities in Routers, iLOs, and iDRACs
-
Windows Man-in-the-Middle attacks (NTLM relay)
-
Windows Active Directory Elevation of Privilege Escalation Vectors (Kerberoasting)
-
Zero-day or N-day vulnerabilities (Log4Shell, Fortinet, etc.)
“These findings underscore why it’s so crucial to regularly pentest all internal and externally exposed assets and points of entry,” explained Snehal Antani, CEO and co-founder of Horizon3.ai.
“Many of the vulnerabilities and weaknesses that companies believe they’ve already addressed are, in fact, welcoming entry points for threat actors. Every organization should regularly ask themselves what their threat environment looks like, whether their security tools are appropriately configured and effective, and most importantly – whether their assets and environments are secure.”
“While we are honored by the numerous awards, accolades, and customer wins that the last year has brought, the ability to help customers find, fix and verify the vulnerabilities and weaknesses that would otherwise make their organizations easy prey for threat actors is the singularly rewarding mission that everyone at Horizon3.ai thrives on.”
(Learn More about ‘The Threat of Cyber Warfare’ featuring Horizon3.ai CEO and Cofounder Snehal Antani. Courtesy of Horizon3.ai and YouTube.)
The “Year in Review 2022: Through the Eyes of the Attacker” report also offers mitigation strategies and policy recommendations for each of the three main attack themes.
For example, among recommendations regarding weak or unenforced credential policies, Horizon3.ai recommends that organizations take the following proactive measures:
-
Increase training for employees on basic cyber security, including the dangers of credential reuse and weak or easily guessed passwords.
-
Institute password policies that include sophistication and length requirements. Horizon3.ai recommends its customers require passwords to have at least 15 characters in length and use at least one upper case letter, number, and special characters. Consider using a password manager with multifactor authentication.
-
When creating a temporary password for a new user or a user that requires an account unlock, require the password to be used within a specific timeframe before the account becomes disabled. Horizon3.ai recommends locking the account after 24 hours if the temporary password is not utilized.
-
Require the use of multifactor authentication for logging into environments and segmented networks when possible. This ensures a high degree of certainty that a cyber threat actor will not be able to gain access to systems unless they also have control of the second device, such as a registered cellphone or another device to confirm a login attempt.
-
Implement a configuration management process that directs default credentials are changed before systems are deployed in a production environment.
-
Disable the accounts of current or former employees who no longer require access. Oftentimes, cyber threat actors are disgruntled employees or former employees that would like to seek retribution against an organization and already have access. Disabling and not deleting the former user account allows the organization to retain any files or data that individuals may have generated while limiting the organization’s risk.
-
And lastly, verify that each of the above guidelines are implemented, enforced, and effective by attacking your environmental teams, tools, and rules using NodeZero.
To view the new Horizon3.ai complete report, please visit https://go.horizon3.ai/2022-Year-in-Review.
Horizon3.ai’s mission is to help you find and fix attack vectors before attackers can exploit them.
NodeZero™, its autonomous penetration testing solution, is an unlimited, self-service SaaS offering that is safe to run in production, available on demand, and requires no persistent or credentialed agents.
See your enterprise through the eyes of the attacker, identify your ineffective security controls, and ensure your limited time and resources are spent fixing problems that matter.
Not just a compliance checkbox; this is effective security. Founded in 2019 by industry and U.S. National Security veterans, Horizon3.ai is headquartered in San Francisco, CA.
Horizon3.ai Takes Platinum in 2022 ‘ASTORS’ Homeland Security Awards

American Security Today’s Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program, and now entering it’s Eighth Year, continues to recognize industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management and Response, Law Enforcement, First Responders, as well as federal, state and municipal government agencies in the acknowledgment of their outstanding efforts to Keep our Nation Secure.
Horizon3.ai
 Best Cyber Analytics Solution
Best Cyber Analytics Solution
-
NodeZero
-
The mission of Horizon3.ai is to help organizations find and fix attack vectors before bad actors can exploit them.
-
NodeZero is an autonomous penetration testing platform, which continuously assesses an enterprise’s attack surface, identifying ways an attacker could chain together harvested credentials, misconfigurations, dangerous product defaults, and exploitable vulnerabilities to compromise systems and data.
-
Most security tools are noisy and full of false positives, requiring persistent credentialed agents and imposing an enormous training and maintenance demand on IT and security teams. Meanwhile, security teams are overwhelmed with non-contextual reports and dashboards, which wastes a lot of valuable time and resources chasing vulnerabilities that don’t pose a real threat to their business.
-
NodeZero is a true self-service SaaS offering that is safe to run in production and requires no persistent or credentialed agents.
(See how NodeZero provides continuous autonomous penetration testing as a true SaaS offering. With NodeZero, our autonomous penetration testing solution, cybersecurity teams can proactively find and fix attack vectors before attackers can exploit them. Courtesy of Horizon3 AI and YouTube.)
-
NodeZero can help organizations identify ineffective security controls and ensure limited resources are spent fixing problems that can actually be exploited, giving IT administrators and network engineers ‘security superpowers,’ to operate like ethical hackers with 20 years of experience and act as a force multiplier for MSP and MSSP partners.
-
*NodeZero is a new competitor to the 2022 ‘ASTORS’ Homeland Security Awards Program.
Homeland Security remains at the forefront of our national conversation as we experience an immigration crisis along our southern border and crime rates that are dramatically higher than before the Pandemic across the United States.

These challenges have become a national priority with an influx of investments in innovative new technologies and systems.
Enter American Security Today, the #1 publication and media platform in the Government Security and Homeland Security fields, with a circulation of over 75,000 readers and many tens of thousands more who visit our AST website at www.americansecuritytoday.com each month.
The pinnacle of the Annual ‘ASTORS’ Awards Program is the Annual ‘ASTORS’ Awards Ceremony Luncheon Banquet, an exclusive, full-course plated meal event, in the heart of New York City.

This year’s exclusive sold-out ‘ASTORS’ luncheon featured representatives of law enforcement, public safety, and industry leaders who came together to honor the selfless service of those who stand on the front lines, and those who stand beside them – providing the capabilities and technologies to create a safer world for generations to come.
This year marks the 20th anniversary of the Department of Homeland Security (DHS), which came out in force, to discuss comprehensive collaborations between private and public sectors that have led to the development of intelligence and technologies which serve to protect our nation.

The continually evolving ‘ASTORS’ Awards Program emphasized the trail of Accomplished Women in Leadership in 2022, as well as the Significance and Positive Impact of Advancing Diversity and Inclusion in our Next Generation of Government and Industry Leaders.
The keynote address was provided by U.S. Customs and Border Protection (CBP) Office of Field Operations (OFO) Deputy Executive Assistant Commissioner (DEAC) Diane Sabatino, who described the changes to CBP through the tragedy of 9/11 and the relentless commitment to its mission and ongoing investment in the latest technologies and innovations to protect our borders and Homeland.
The resounding theme of the DEAC’s remarks was her pride in the women and men of the CBP and their families who support them.

AST was also joined by Legendary Police Commissioner William Bratton, who spoke, as always, about his love for the City of New York, the Profession of law enforcement to which he has dedicated his life, and for which he continues to drive thought leadership and innovation.
New York City Police Department (NYPD) Chief of Department Kenneth Corey, came out to address Luncheon attendees and shared some of his experiences and the changes in policing he’s witnessed over his more than three decades of service.

FDNY Chief Joseph Jardin honored the men and women of the FDNY, not only those who currently serve but all of those who have selflessly served, with a special recognition of those lost on 9/11.
Chief Jardin spoke about the continuing health battle of many following 9/11 with cancer and respiratory disease, yet now knowing the full consequences, would not have made a different decision to respond.
As Chief Jardin noted, mission-driven service is in the lifeblood of every firefighter, volunteer and sworn and has been so throughout the history of the Fire Service.
Former head of the FBI’s active shooter program, Katherine Schweit joined AST to sign complimentary copies of her book, ‘STOP THE KILLING: How to End the Mass Shooting Crisis,’ thanks to the generosity of our 2022 ‘ASTORS’ Awards Sponsors.
The 2022 ‘ASTORS’ Awards Program was Proudly Sponsored by NEC National Security Systems (NSS), ATI Systems, Automatic Systems of America, guardDog AI, Fortior Solutions, IPVideo Corporation, Rajant Corporation, RX Global, and SIMS Software!
We were pleased to welcome the esteemed New York City Fire Department (FDNY); the New York City Police Department (NYPD); and the NYC Hospital Police, as well as Executive Management from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), and many other DHS agencies, Federal law enforcement agencies, and private/public partnerships such as the National Association of Women Law Enforcement Executives (NAWLEE), the 30×30 Initiative, a coalition of professionals advancing the representation of women in policing; and Operation Lifesaver, Inc. (OLI) (rail safety advocates).

The prestigious Annual ‘ASTORS’ Homeland Security Awards Program highlights the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition and keep our Nation safe – one facility, street, and city at a time.

In 2022 over 240 distinguished guests representing Federal, State, and Local Governments, and Industry Leading Corporate Firms gathered from across North America, Europe, and the Middle East to be honored among their peers in their respective fields.
Each year, to keep our communities safe and secure, security dealers, installers, integrators, and consultants, along with corporate, government, and law enforcement/first responder practitioners, convene in New York City to network, learn and evaluate the latest technologies and solutions from premier exhibiting brands at ISC East, the Natural Disaster & Emergency Management Expo (NDEM EXPO), and the ASIS NYC Expo.
ISC East is the Northeast’s leading security & public safety event, hosted in collaboration with sponsor Security Industry Association (SIA) and in partnership with ASIS NYC.

 Corporate firms, the majority of which return year to year to build upon their Legacy of Wins, include:
Corporate firms, the majority of which return year to year to build upon their Legacy of Wins, include:
Advanced Detection Technologies, AMAROK, ATI Systems, Axis Communications, Automatic Systems, BriefCam, Canon U.S.A., Cellbusters, CornellCookson, CyberArk Fortior Solutions, guardDog.ai, Hanwha Techwin of America, High Rise Escape Systems, IPVideo Corporation, Konica Minolta Business Solutions, NEC National Security Systems, NICE Public Safety, OnSolve, PureTech Systems, Quantum Corporation, Rave Mobile Safety, Regroup Mass Notification, Robotic Assistance Devices, Rajant Corporation, SafeLogic, Select Engineering Services LLC, Singlewire Software, SolarWinds Worldwide, Teledyne FLIR, Valor Systems, and West Virginia American Access Control Systems, just to name a few!
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old-school basics to what is Today – a fast-changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace with over 75,000 readers at the Federal, State, and local levels of government as well as firms allied to the government.
American Security Today brings forward a fresh compelling look and read with our customized digital publications that hold readers’ eyes throughout the story with cutting-edge editorial that provides solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

AST Digital Publications are distributed to over 75,000 qualified government and homeland security professionals, in federal, state, local, and private security sectors.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches both Private & Public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture, and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from Government at the federal, state, and local levels as well as from private firms allied to the government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website, and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants & Dams, Bridges & Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting & Concert Stadiums, our Nation’s Schools & Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
To learn more about ‘ASTORS’ Homeland Security Award Winners solutions, Be On the LookOut for the 2022 ‘ASTORS’ CHAMPIONS Edition Fully Interactive Magazine – the Best Products of 2022 ‘A Year in Review’.
The Annual CHAMPIONS edition includes a review of ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firm’s products and services, including video interviews and more.

It will serve as your Go-To Source throughout the year for ‘The Best of 2022 Products and Services’ endorsed by American Security Today, and can satisfy your agency’s and/or organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection, and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware, and Networking Security – to name a few), the 2021 ‘ASTORS’ CHAMPIONS EDITION will have what you need to Detect, Delay, Respond to, and Mitigate today’s real-time threats in our constantly evolving security landscape.
It will also include featured guest editorial pieces from some of the security industry’s most respected leaders, and recognized firms in the 2022 ‘ASTORS’ Awards Program.
For more information on All Things American Security Today, as well as the 2023 ‘ASTORS’ Awards Program, please contact Michael Madsen, AST Publisher at mmadsen@americansecuritytoday.com.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos




















