Illusive Networks, a leader in deception-based cybersecurity solutions and a Competitor in the 2018 ‘ASTORS’ Homeland Security Awards Program, has announced Attack Surface Manager (ASM), the first automated solution to continually reduce the attack surface, and proactively lower the likelihood of targeted cyberattack success.
Illusive ASM discovers hidden elements throughout the network that enable lateral movement and otherwise facilitate advanced attacks.
(Learn More. Illusive stops targeted attacks before they stop you. It’s now possible, turn on the table on attackers with Illusive Attack Surface Manager. Courtesy of Illusive Networks and YouTube)
In today’s fast-changing business environments, it is difficult for security teams to identify and control credentials and other sensitive data elements that proliferate during normal day to day operations.
Attackers don’t need to know how your network is physically constructed.
They want to know how to move from one system to another, and where to find the coveted crown jewels.
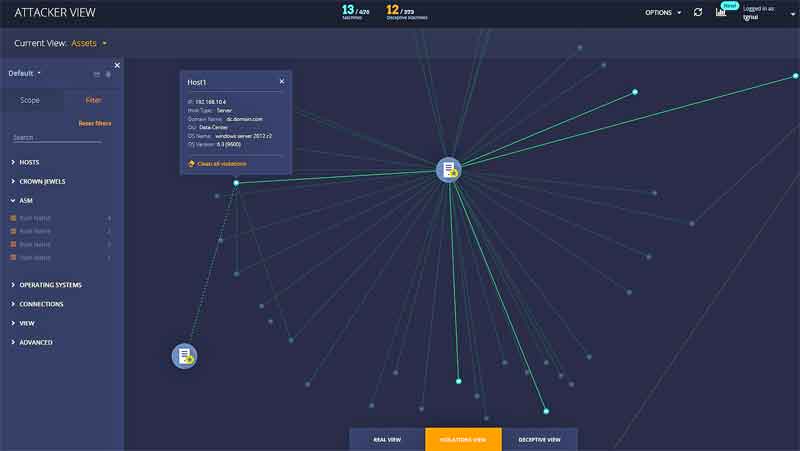
Illusive creates a visual map as the attacker would want to see your network.
By weaving deceptions across the IT landscape, Illusive Deceptions Everywhere®creates an alternative reality that disrupts the progress of an APT.
Attackers can’t tell reality from illusion. Every endpoint becomes a trap.
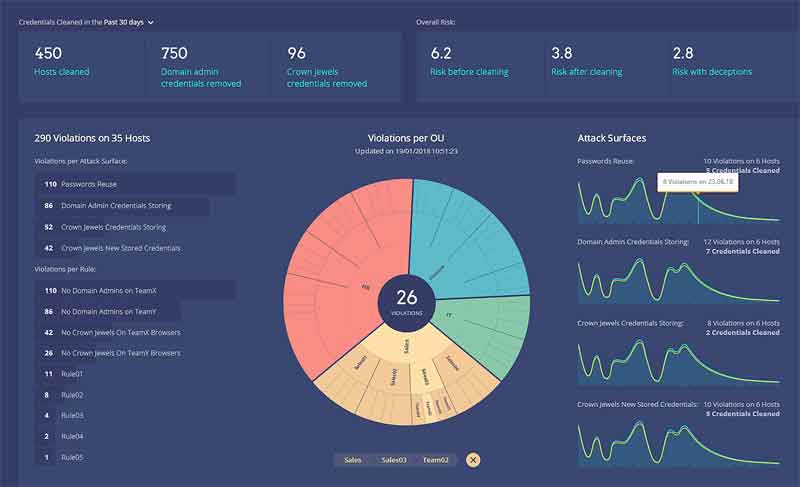
Attack Surface Manager (ASM) automatically identifies these risks, revealing policy violations, and enabling security professionals to proactively deprive attackers of the keys they need to reach critical assets.

“Nearly every security breach that I’ve investigated involved the theft and abuse of credentials,” says Charles Carmakal, vice president of cyber incident response firm Mandiant.
“ASM enables organizations to identify and decrease the exposure of credentials, reducing the ability for attackers to move laterally once in an environment.”
“For years, organizations have felt at the mercy of sophisticated attackers who maneuver their network undetected for months,” said Ofer Israeli, CEO, Illusive Networks.
“By removing the very elements attackers need to progress, ASM stops the attack before it creates a business crisis.”
“This significant new release continues our progress in addressing the complete advanced attack lifecycle.”
(Learn More. Hear from Ofer Israeli, CEO, Illusive Networks, speaking about “Own your destiny – proactive approach to cybersecurity” at Team8’s Rethink Cyber Singapore 2017. Courtesy of Team8 and YouTube)
In a recent CyberEdge survey, only 38% of respondents stated they were confident in their ability to avoid a successful cyberattack in the coming twelve months.
ASM was developed in response to customer requirements to eliminate standing threats missed by traditional cyber defense offerings, and represents continued progress toward Illusive’s vision of applying deception-based technology against all stages of advanced cyber-attacks, including prevention, detection, response, and remediation.
“Deception solutions will play a greater role in the future of enterprise threat defense,” according to Gartner.

“Detection is often a prerequisite for higher-quality deceptions. However, organizations are beginning to use deceit to actively thwart or isolate malware botnets, threat actors and suspicious connections.1
“While some organizations may need large-scale analytics solutions or advanced threat hunting teams,” Israeli continued.
“These investments take time to bear fruit.”
“We provide an extremely lightweight, nimble, and easy to deploy solution that automatically adapts to changes in the environment, and immediately enhances an organization’s ability to avoid the heavy toll targeted attacks can take.”
Key Benefits of Illusive ASM
Organization using ASM preemptively manage and reduce attack risk through:
- Continuous minimization of the attack surface, even when user populations and systems are rapidly changing
- Unprecedented visibility to their access footprint and credential-related policy violations that facilitate attacker mobility
- Efficient and scalable credential management of credentials through intelligent automation
- The ability to prioritize remediationby understanding the risk and criticality of each violation
- Early detection of advanced attackers by reducing attack vectors in the environment, decreasing real credentials, and increasing the odds of detection
- Rapid correction of policy violations by both automated and manually-driven methods
Illusive ASM enhances the company’s award-winning deception-based cybersecurity platform, which uses intelligent automation and machine learning to support creation, deployment, and refresh of deceptions at massive scale.
The agentless system allows swift and easy deployment of deceptions with minimal manpower required for both roll-out and daily operations.
As soon as attackers attempt to use any form of deceptive information, Illusive detects and alerts enterprise security teams and integrates real-time, contextual forensic data directly into the incident record, enabling rapid and informed incident analysis and response.
“The combination of ASM’s ability to reduce the exposure of credentials in advance of attacks, with Illusive’s existing ability to plant convincing and realistic deceptions throughout an environment, will help organizations better prepare for attacks, and detect threat actors earlier in the attack lifecycle,” concluded Carmakal.
“Illusive continues to innovate technology that helps organizations reduce their attack surface and mitigate the risk of data breaches.”
Illusive Networks Competes in 2018 ‘ASTORS’ Homeland Security Awards Program
AST focuses on Homeland Security and Public Safety Breaking News, the Newest Initiatives and Hottest Technologies in Physical & IT Security, essential to meeting today’s growing security challenges.
 The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.’
The 2018 ‘ASTORS’ Homeland Security Awards Program, is organized to recognize the most distinguished vendors of Physical, IT, Port Security, Law Enforcement, Border Security, First Responders, (Fire, EMT, Military, Support Services Vets, SBA, Medical Tech) as well as the Federal, State, County and Municipal Government Agencies – to acknowledge their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.’
As an ‘ASTORS’ competitor, the Illusive Networks will be competing against the industry’s leading providers of Innovative Cyber Security Solutions.
To Learn More about the ‘ASTORS’ Homeland Security Awards Program, see 2017 ‘ASTORS’ Homeland Security Award Winners Honored at ISC East.

Over 100 distinguished guests from National, State and Local Governments, and Industry Leading Corporate Executives from companies allied to Government, gathered from across North America and the Middle East to be honored from disciplines across the Security Industry in their respective fields which included representatives from:
 The Department of Homeland Security
The Department of Homeland Security- The Department of Justice
- The Security Exchange Commission
- State and Municipal Law Enforcement Agencies
- Leaders in Private Security
American Security Today will be holding the 2018 ‘ASTORS’ Awards Presentation Luncheon to honor Nominees, Finalists and Winner on November 14, 2018 at ISC East in New York City.
Nominations are now being accepted for the 2018 ‘ASTORS’ Homeland Security Awards at https://americansecuritytoday.com/ast-awards/.
Over the past 12 months, Illusive has received recognition by The Wall Street Journal in its inaugural Tech Companies to Watch, was honored as a finalist in CRN’s Tech Innovators Awards, named as one of CRN’s ’25 Coolest Network Security Vendors’, by Momentum Partners as one of ten cybersecurity companies on their Watch List and more recently, by InformationWeek as a Top Vendor to Watch in 2018.
To Learn More about how Illusive Networks is pioneering deception-based cybersecurity with its patented Deceptions Everywhere® technology which neutralizes targeted attacks and Advanced Persistent Threats (APT) by creating a deceptive layer across an enterprise network, please visit https://www.illusivenetworks.com/.
 By providing an endless source of false information, Illusive disrupts and detects attacks with real-time forensics and without disruption to business, while real-time forensic and risk insights support more effective and efficient incident resolution.
By providing an endless source of false information, Illusive disrupts and detects attacks with real-time forensics and without disruption to business, while real-time forensic and risk insights support more effective and efficient incident resolution.
1 Gartner, “Top 10 Strategic Technology Trends for 2018: Continuous Adaptive Risk and Trust,” David W. Cearley, Neil MacDonald, et al., 8 March 2018.