1 in 10 people have admitted they would take as much company information with them as possible before leaving their job.
A recent survey of more than 320 IT security experts conducted by Gurucul, a leader in behavior based security and fraud analytics technology, and a returning competitor in the 2019 ‘ASTORS’ Homeland Security Awards Program, exposed just that.
More than 15 percent of people surveyed said they would delete files or change passwords upon exiting a company.
Most organizations place their focus on defending against and detecting external cyberattacks.
However, a more insidious threat is on the rise.
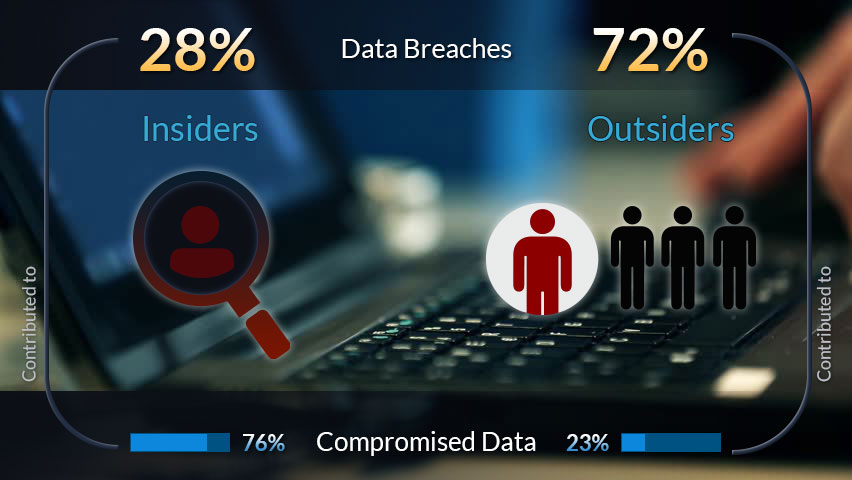
Information security professionals say that insider attacks are far more difficult to detect and prevent than external attacks, making them a big concern for companies.
With identities and entitlements often in a state of excess due to manual processes built upon static identity management rules and roles, it is more common than not that users inside the perimeter have access to information NOT required for them to do their job.
This gives them the capability to perform abusive tasks within the company.

However, insider threats are not always caused by users within the organization.
They can also occur when credentials of employees are shared or compromised, which often goes undetected.
“Gurucul mitigates these risks is by employing behavioral analytics,” explains Craig Cooper, COO of Gurucul.
“By combining user and entity behavior analytics, and identity analytics, companies can not only monitor, detect and remove excess access before it is too late, but they can also monitor employee actions by detecting unusual or risky behavior.”
“By detecting when users are acting in ways that contradict their normal behavior and job function, our customers are able to intervene.”
 Gurucul’s Risk Analytics (GRA), the 2018 ‘ASTORS’ Award Winner for Best User & Entity Behavior Analytics (UEBA), was also recently recognized as a Representative Vendor in Gartner’s 2019 Market Guide for Online Fraud Detection1.
Gurucul’s Risk Analytics (GRA), the 2018 ‘ASTORS’ Award Winner for Best User & Entity Behavior Analytics (UEBA), was also recently recognized as a Representative Vendor in Gartner’s 2019 Market Guide for Online Fraud Detection1.
Gartner acknowledged Gurucul as a solution for Fraud Analytics.
According to Gartner, one of the factors driving the continued growth of the online fraud detection market is a, “Maturing of fraud strategies among retailers and financial institutions to not simply carry out risk assessment at the point of payment, but also to assess risk throughout the customer journey.”
“While not all institutions have achieved this level of capability maturity in their fraud detection strategies, it is being actively explored and considered.”
“It is also driving demand in the OFD space for vendors specializing in services that can be applied across the entire customer journey, such as behavioral analytics.”
Providing Online Fraud Detection
Unlike online fraud detection platforms that rely primarily on static rule-based detection, with machine learning as a separate solution component or that use machine learning to optimize rule sets and proactively suggest new, more effective rules, Gurucul relies exclusively on machine learning with open analytics to create and manage any customer specific fraud models, in addition to a large out-of-the-box models library.
Gurucul ingests huge volumes of data generated by users/entities across multiple channels from on-premise and cloud applications to identify anomalous and potentially fraudulent behavior that spans time, place, devices, access and transaction actions.
The Gurucul Fraud Analytics risk engine continuously scores this activity against historical behavior, static and dynamically created peer groups, and third party intelligence to generate risk prioritized alerts for investigation.

The risk score can also be used to automate remediation responses by enforcing security policies or making real-time business decisions to prevent fraud before it occurs.
For example, if identity theft or account takeover is suspected, the corresponding user account can be blocked or challenged with step-up authentication.

In the case of suspicious third-party funds transfers associated with money mule fraud, a hold can be placed on the account to prevent the transaction from being executed.
“We believe being cited as a Representative Vendor in the Gartner Market Guide for Online Fraud Detection underscores the importance of behavioral analytics in detecting and preventing online and cross-channel fraud,” said Nilesh Dherange, CTO of Gurucul.
“We further believe our ability to predict, detect, prevent and respond to fraud in real-time across a variety of use cases is the primary reason why Gurucul has been deployed in the financial services, payments, insurance and retail sectors.”
(Hear from Gurucul customers as they share their experience with our Behavior Based Security Analytics and Intelligence technology in their own words. Courtesy of Gurucul and Vimeo.)
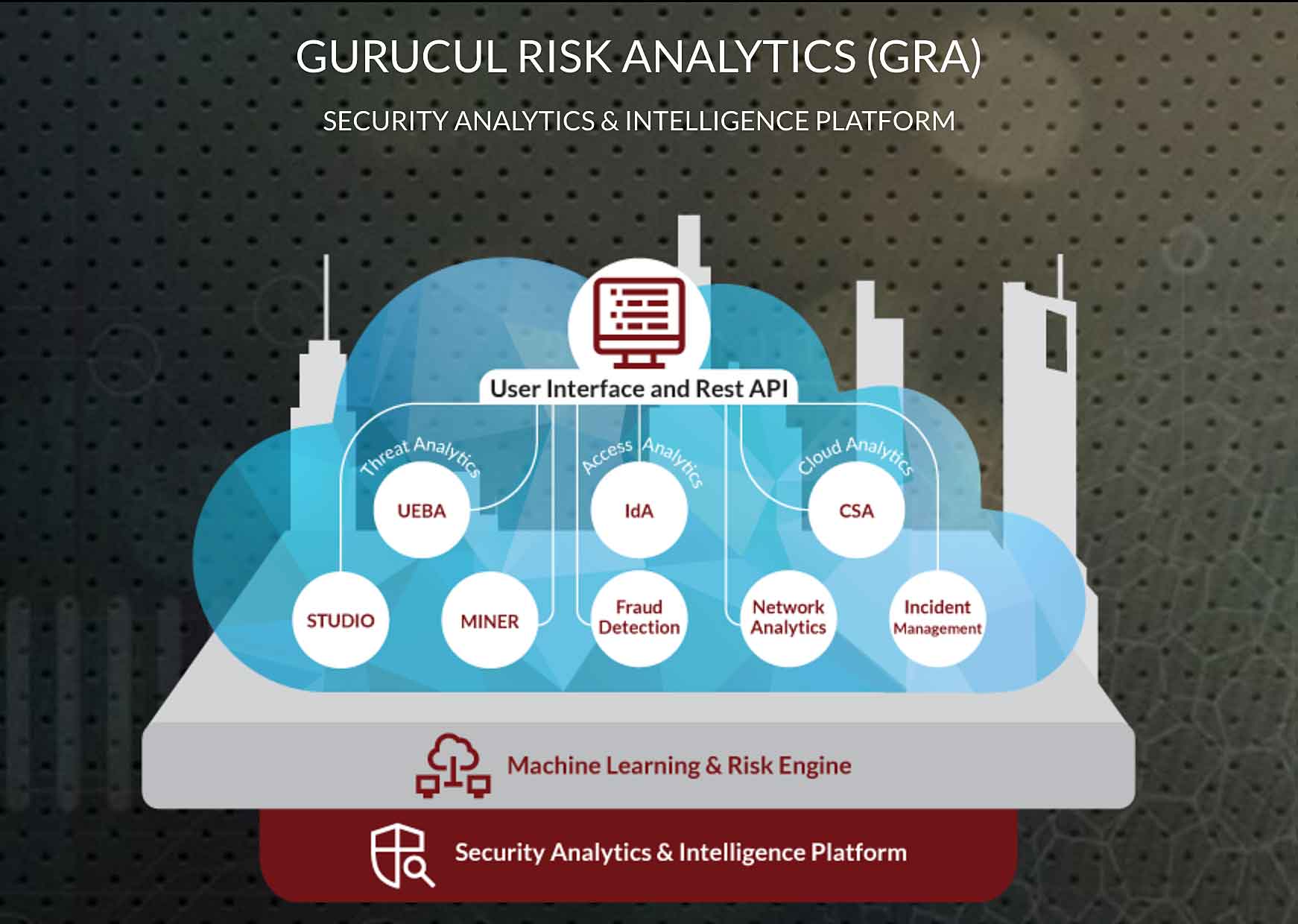
Gurucul Risk Analytics (GRA)
The IT footprint of organizations is rapidly expanding well beyond traditional data center and endpoints.
A multitude of new cloud applications, mobile and IoT devices with proprietary operating systems are interconnecting with the network and other devices.
Traditional approaches that use rules, policies and pattern-based monitoring are insufficient for detecting malicious activity in these distributed, highly complex, and traffic intensive environments.
Plus they require security analysts to sift through thousands of alerts.
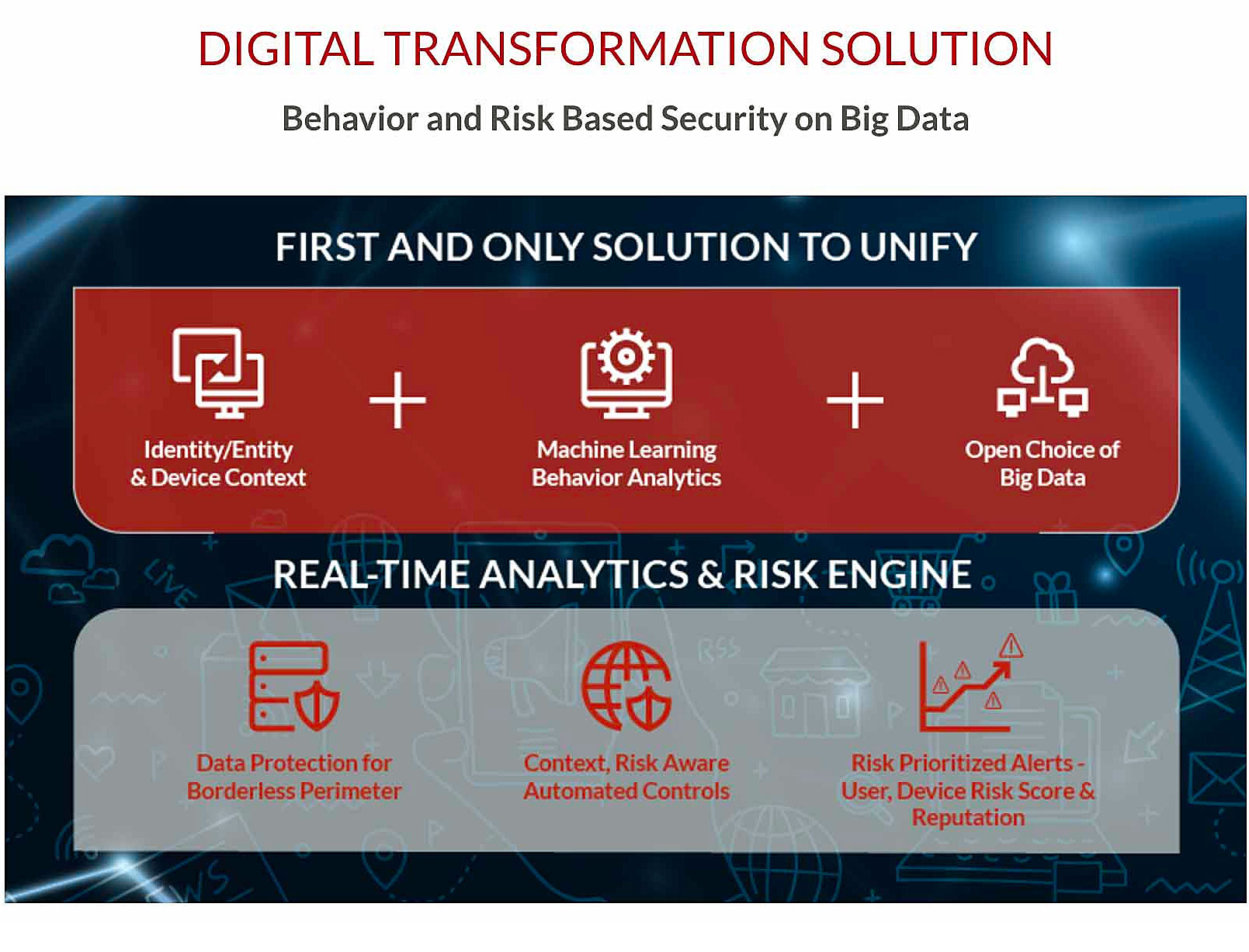
Gurucul has developed an innovative behavior based, big data driven security analytics platform with pre-built machine learning models and AI driven threat intelligence capabilities that spans the entire enterprise threat surface.
This includes, cloud platforms and applications, networks, mobile endpoints, IoT devices, POS systems, ATMs, sensors, medical devices and more.
Gurucul’s AI-driven approach performs the work of hundreds of analysts, at machine speed, saving time, money, and greatly reducing cyber risk.
(See how using identity to monitor for threats, Gurucul provides Actionable Risk Intelligence™ to protect against targeted and under-the-radar attacks. Gurucul is able to proactively detect, prevent, and deter advanced insider threats, fraud and external threats to system accounts and devices using self-learning, behavioral anomaly detection algorithms. Courtesy of Gurucul and Vimeo.)
The Gurucul Risk Analytics (GRA) platform ingests and analyzes massive amounts of structured and unstructured data on user/entity behaviors from virtually any data source and applies identity-centric, model-driven data science, machine learning, anomaly detection and predictive risk-scoring algorithms to identify not just anomalous behavior, but risk-scored activity indicative of security threats.
It can detect stealth threats like malicious insiders, fraud attempts, and account compromise attacks.
For instance, Gurucul GRA can and has predicted the departure of disgruntled employees based on their behavior, while preventing them from exfiltrating company data, committing fraud and sabotaging systems.
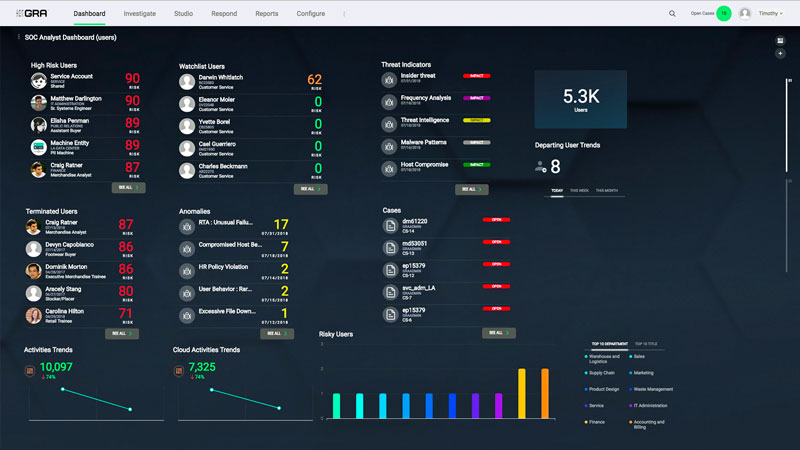
To address specific business requirements and use cases, Gurucul GRA provides out-of-the-box dashboards for fraud analytics, cloud analytics, access analytics, network analytics, and customizable business roles including SOC Analyst, Network Analyst, DLP Analyst, etc.
Each dashboard is easily personalized using drag and drop widgets to provide data and visualizations tailored to each user’s needs and preferences.
Gurucul has the largest machine learning (ML) library in the industry with over 1300 pre-packaged models.
These include unsupervised, supervised and deep learning algorithms, and versions that are pre-tuned to predict and detect specific threats that impact financial, healthcare and retail organizations.
Organizations can easily customize ML models or build their own using Gurucul STUDIO™, which provides canvas-based drag-and-drop components for analysts or administrators to design behavior/threat models without having to write code.
GRA also provides a centralized analytics platform and SDKs for data scientists to build and import their own custom models.
Unlike competitors that require analysts to know what they are looking for, the 1300+ machine learning models allow Gurucul GRA to detect unknown threats and fraud in real-time and accurately identify the subset of anomalous behavior that places the organization at risk, saving time and resources through significantly reduced alerts and false positives.
This vast ML library also enables organizations to automate responses to high risk activity and reduce security “friction”.
For example, Gurucul GRA can be used to improve the end user experience by doing away with passwords while increasing security.
To accomplish this, Gurucul GRA’s continuous, model-driven authentication process renders in-the-moment decisions about a users’ confirmed identity before allowing the session or requested action to continue. Authentication is no longer a singular event, but an engaged process that persists throughout the user’s experience in the environment.
Gurucul is the only Security Analytics vendor that closes the user intelligence gap by combining Identity Analytics (IdA) with User and Entity Behavior Analytics (UEBA).
This combination reduces the attack surface for accounts while eliminating unnecessary access rights and privileges.
Contextualizing this data with the user’s peer groups enables Gurucul to pinpoint malicious insider activity and cyber intrusions, while minimizing operational overhead for access governance and administration.
Unlike alternatives, Gurucul supports an open choice of big data, allowing customers to use existing data lakes, reducing processing time, data replication and costs. Gurucul GRA is not priced on data volume.
Gurucul’s unique Self-Audit capabilities empower users to proactively monitor and report any suspicious access, fraud and activity on their own accounts.
According to the recent Forrester Wave™: Security Analytics Platforms report, enterprises looking for a robust security analytics tool with strong security user behavior analytics and data protection should consider Gurucul.
Gurucul provides unmatched ROI for a wide variety of customers and use cases.
For instance, in preparation for 2018 Super Bowl, Gurucul customer Allina Health had to protect data on football players and VIPs and deployed Gurucul GRA in one week.
GRA monitored thousands of employees across 90 clinics, 12 hospitals and 15 retail pharmacies, over 2 million patient records, and 50M daily transactions.
In a task no SIEM could ever accomplish, GRA correlated seemingly unconnected events in time/space, analyzed cyber risk, and alerted at machine speed to identify risky activity that prevented “snooping” and data exfiltration before those attempts could succeed.
At Allina Health, GRA also identifies, tracks and monitors IT inventory, including laptops, IoT devices and medical equipment that are turned on/off intermittently, even devices not previously registered under IT security.
(Tom Brady lost the game but not his data. See ‘Super Bowl LII: Protecting Players’ and VIP Data’, to understand how Allina Health used Gurucul’s Risk Analytics (GRA) to protect Players’ and VIP medical records at the Super Bowl in Minneapolis, featuring Bill Scandrett, CISO, Allina Health. Courtesy of Gurucul and Vimeo.)
Gurucul’s User and Entity Behavior Analytics (UEBA) was able to answer these questions: “Are you snooping on other employees? Are you looking at VIP records?”
UEBA can really tie different events together and trigger them combined as an alert to say okay, we have a VIP event here in combination with data exfiltration. This might be something we seriously need to look at.
As a Fortune 100 Health Insurance Provider, Aetna also uses Gurucul GRA for its model-driven security capabilities to respond to threats at machine speed.
Aetna can now automate and change controls on demand, not hours later, after the fact.
Since data quantity doesn’t increase cost, Aetna uses a big data lake and GRA risk-scores all users and assets, enabling automated downstream controls, provisioning and real-time, personalized access decisions.
(Aetna uses Gurucul Risk Analytics to automate front line security controls. View this customer testimonial to learn more about Aetna’s success implementing Gurucul User and Entity Behavior Analytics (UEBA) and Identity Analytics. Courtesy of Gurucul and Vimeo.)
Gurucul GRA scales to meet very large company demands.
A large health insurer uses GRA to analyze 8 million identities and 500 big data nodes.
Another health insurance company uses GRA on top of hundreds of Hortonworks big data nodes to apply advanced analytics to over 40 million identities belonging to employees, partners and customers.
A financial institution uses GRA with its own custom cloud big data lake on AWS to risk score access and activity, reduce access risks and detect unknown threats.
Another insurance firm uses GRA Self Audits for over 60,000 end users to raise security awareness, provide deterrence and collaborate with users to detect identity theft and abuse.
Gurucul was the first to innovate the User and Entity Behavior Analytics (UEBA) category and extend behavior analytics from on-premises to the cloud.
Saryu Nayyar, Gurucul CEO, published the second edition of her book “Borderless Behavior Analytics – Who’s Inside? What’re They Doing?” with contributions from Jim Routh, CSO of CVS; Bill Scandrett, CISO of Allina Health; Vishal Salvi, CISO of Infosys; and Devin Bhatt, CISO of US Federal, and was recognized as a Thought Leader in SC Media’s Reboot Leadership Awards.
Today, Gurucul GRA is the only Behavior Based Security Analytics solution that brings cyber security risk detection and scoring to the entire extended enterprise including mobile, IoT, PoS, medical devices and more.
It is also the only behavior based security analytics solution to be offered as a service through the cloud.
Organizations shifting from traditional data centers to cloud based solutions use GRA-powered Gurucul SaaS to secure their cloud-first initiatives.
As a single solution, Gurucul GRA manages cloud, hybrid, and enterprise security risk, and scales rapidly to meet the needs of any size organization.

For more information about how Gurucul can defend against insider attacks see https://gurucul.com/solutions/insider-threat.
To Learn More about Gurucul Fraud Analytics, visit https://gurucul.com/products/fraud-analytics.
(1) Gartner, Inc. “Market Guide for Online Fraud Detection” by Jonathan Care and Akif Khan, 30 April 2019.
Gurucul Competes in the 2019 ‘ASTORS’ Homeland Security Awards Program
Gurucul
-
2018 Best User & Entity Behavior Analytics (UEBA)
-
Gurucul Risk Analytics (GRA)
-
Gurucul was also recognized in the 2016 ‘ASTORS’ Homeland Security Awards Program
The Annual ‘ASTORS’ Awards Program is specifically designed to honor distinguished government and vendor solutions that deliver enhanced value, benefit and intelligence to end users in a variety of government, homeland security and public safety vertical markets.

The 2018 ‘ASTORS’ Awards Program drew an overwhelming response from industry leaders with a record high number of corporate and government nominations received, as well as record breaking ‘ASTORS’ Presentation Luncheon Attendees, with top firms trying to register for the exclusive high – end luncheon and networking opportunity – right up to the event kickoff on Wednesday afternoon, at the ISC East registration!
Over 130 distinguished guests representing National, State and Local Governments, and Industry Leading Corporate Firms, gathered from across North America, Europe and the Middle East to be honored among their peers in their respective fields which included:
- The Department of Homeland Security
- The Federal Protective Service (FPS)
- Argonne National Laboratory
- The Department of Homeland Security
- The Department of Justice
- The Security Exchange Commission Office of Personnel Management
- U.S. Customs and Border Protection
- Viasat, Hanwha Techwin, Lenel, Konica Minolta Business Solutions, Verint, Canon U.S.A., BriefCam, Pivot3, Milestone Systems, Allied Universal, Ameristar Perimeter Security and More!
The Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program highlighting the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition, and keep our Nation safe – one facility, street, and city at a time.
The 2019 ‘ASTORS’ Homeland Security Awards Program is Proudly Sponsored by ATI Systems, Attivo Networks, Automatic Systems, and Desktop Alert.
Limited Time Remaining to Enter the 2019 ‘ASTORS’ Homeland SecurityAwards at https://americansecuritytoday.com/ast-awards/.
Comprehensive List of Categories Include:
| Access Control/ Identification | Personal/Protective Equipment | Law Enforcement Counter Terrorism |
| Perimeter Barrier/ Deterrent System | Interagency Interdiction Operation | Cloud Computing/Storage Solution |
| Facial/IRIS Recognition | Body Worn Video Product | Cyber Security |
| Video Surveillance/VMS | Mobile Technology | Anti-Malware |
| Audio Analytics | Disaster Preparedness | ID Management |
| Thermal/Infrared Camera | Mass Notification System | Fire & Safety |
| Metal/Weapon Detection | Rescue Operations | Critical Infrastructure |
| License Plate Recognition | Detection Products | And Many Others! |
Don’t see a Direct Hit for your Product, Agency or Organization?
Submit your category recommendation for consideration to Michael Madsen, AST Publisher at: mmadsen@americansecuritytoday.com.
2018 Champions Edition
 See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
Nominations for the AST 2019 ‘ASTORS’ Homeland Security Awards Program will officially open as of January 1st, 2019 at americansecuritytoday.com.
Enter Early to Maximize Media Coverage of your Products and Services at Kickoff, and Get the Recognition Your Organization Deserves!
And be sure to Register Early for the 2019 ‘ASTORS’ Awards Presentation Luncheon at ISC East 2019 to ensure your place at this limited- space event!

2018 ‘ASTORS’ Homeland Security Awards Luncheon at ISC East