For years, attackers have successfully used deception tactics for breaching networks.
They masquerade as legitimate employees, using stolen credentials and deceptive measures to infiltrate a network, all while remaining undetected for lengthy dwell times.
Security investments are typically made in preventing an attack and exfiltration.
This leaves a giant blind spot for organizations as attackers that bypass the perimeter can then move laterally and steal credentials as they quietly establish a foothold, gain privileges, and recon the network in search of their targets.
Threats arise from in a variety of factors and can come in the form of external threat actors.
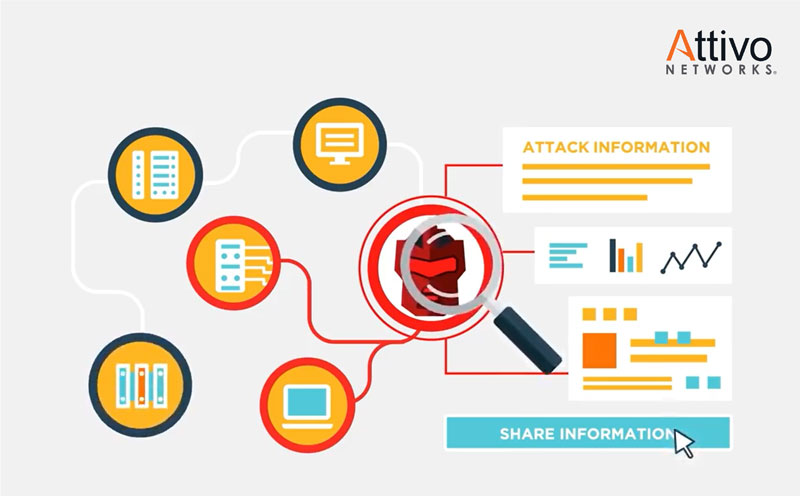
Knowing that an attacker is operating inside your network is valuable.However, knowing an attacker’s methods and gaining the threat intelligence to shut down current attacks and prevent future attacks, provides the empowerment to truly defend your networks and data centers. (Courtesy of Attivo Networks)
External adversaries, insiders, contractors, and suppliers are all capable of creating risk and potentially breaching an organization.
Since they all are within the perimeter, many traditional security controls are ineffective or unreliable as they try to learn behaviors and alert on suspicious behavior.
A different approach to in-network detection must be applied.
These security controls must be capable and accurate in detecting nefarious, policy violation, and risks from human error.
Deception closes the in-network detection gap by placing attractive endpoint lures, data deceptions, and traps throughout the network, giving organizations immediate visibility needed to derail these attacks and remediate compromised devices.
(See a brief introduction to deception technology and Attivo Networks ThreatDefend™ Deception and Response Platform. Courtesy of Attivo Networks and YouTube.)
Why Deception
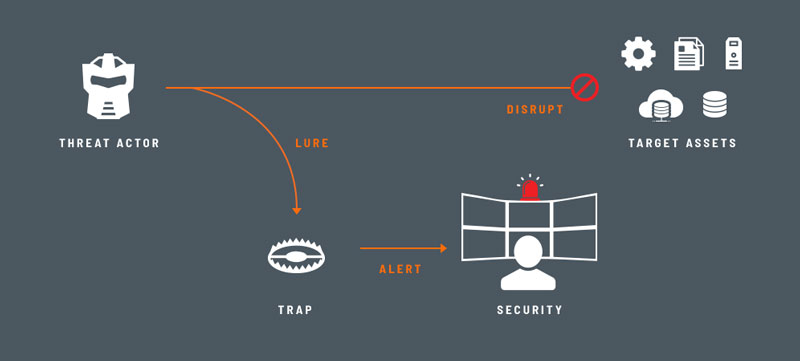
Deception works by using deceive traps and lures designed to attract an attacker into engaging and away from production assets.
Decoys are projected throughout the network along with endpoint credentials, mapped shares, deception data or applications that will breadcrumb the attacker back to an engagement server that will alert on the presence of an attacker.
DECEPTION ARCHITECTURE
Believability is critical to enticing the attacker, and as such Attivo Networks uses real operating systems, services, and applications that mirror match the production environment.
Golden image software can also be used for 100% matching, and integration with Active Directory will also validate deception credentials for authenticity.
Deception technology plays a critical role in changing this paradigm by detecting attacks that have bypassed other security controls, early and accurately, regardless of the methods used to compromise the network.
Since deception uses traps and lures to detect an adversary, the solution is not reliant on signatures or database look up.
This makes deception scalable and capable of reliably detecting attackers using ever-changing attack methods and targeting rapidly evolving attack surfaces.
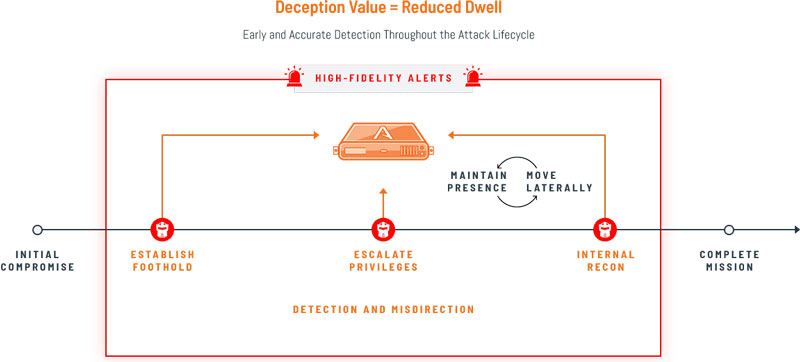
One simple touch of the deception environment provides a substantiated alert with details of attempted actions.
Deception technology provides the “eyes within the network” visibility to threats that have bypassed perimeter defenses.
(Learn More about the Attivo Networks ThreatDefend Deception and Response Platform. Courtesy of Attivo Networks and YouTube.)
By laying a maze of decoys, lures, and mis-directions security teams can accurately and efficiently detect early reconnaissance, lateral movement, and credential theft, improving detection time and reducing attacker dwell time.
This is where the Attivo ThreatDefend platform has proven its value with its ability to detect any attacker using any attack vector on any attack surface.
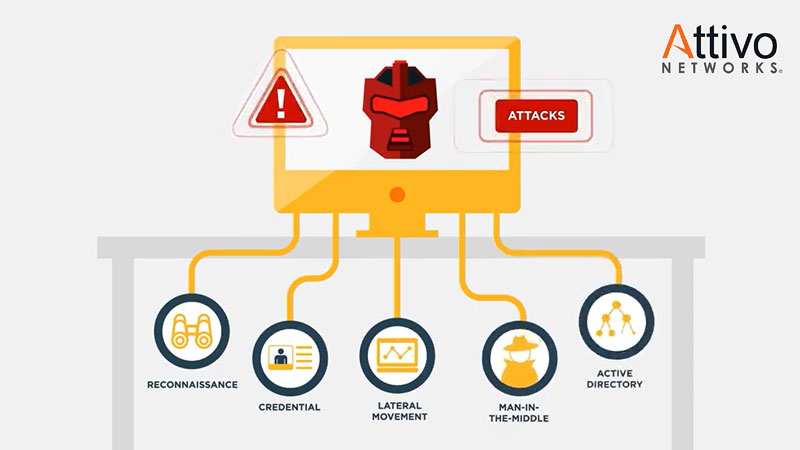
The Attivo ThreatDefend platform starts with deception, providing inside-the-network intrusion detection to threats that have bypassed traditional security controls by deploying network, endpoint, application, and data decoys and deception.
Unlike signature or behavioral-based security controls, deception-based intrusion detection occurs when the attacker engages with a deceptive asset.
Because deception technology is not reliant signature lookups, pattern matching, or behavioral analysis, it retains its effectiveness even against APTs and ever-changing attack methods.
Deception provides high-fidelity alerts based on confirmed activity, increasing accuracy and reducing false positives.
As organizations shift their focus to endpoint security, they have found the ThreatDefend platform to be a force multiplier, gaining visibility and insight into endpoint attacker activity that has bypassed other endpoint security controls.
(See how the Attivo’s ThreatPath™ solution provides an attack path vulnerability assessment based on likely attack paths that an attacker would traverse through misconfigured systems or credential misuse. A topographical illustration of the attack paths provides a straight-forward view of how an attacker can move laterally once they have engaged with their first end-point system. Clickable drill downs provide the details of weaknesses and IP addresses for systems needing to be isolated and/or fixed. Integrations with prevention systems can be leveraged for automated response actions and trouble tickets can be activated inside the dashboard. Courtesy of Attivo Networks and YouTube.)
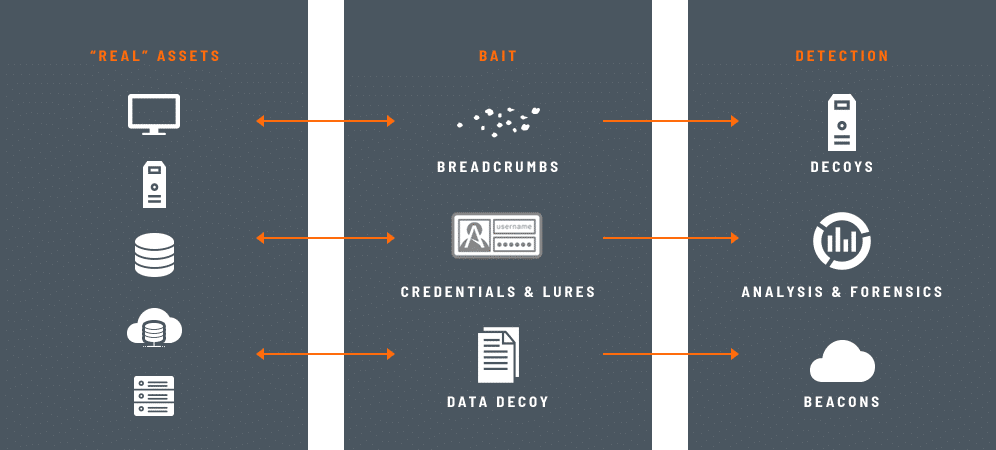
The key to successful deception lies in creating decoys that appear identical to production assets and blend in seamlessly with the environment.
Combined with endpoint credential lures and breadcrumbs as well as deceptive applications and data, the deception fabric detects attackers during lateral movement, reconnaissance, credential theft, and attempts of data theft.
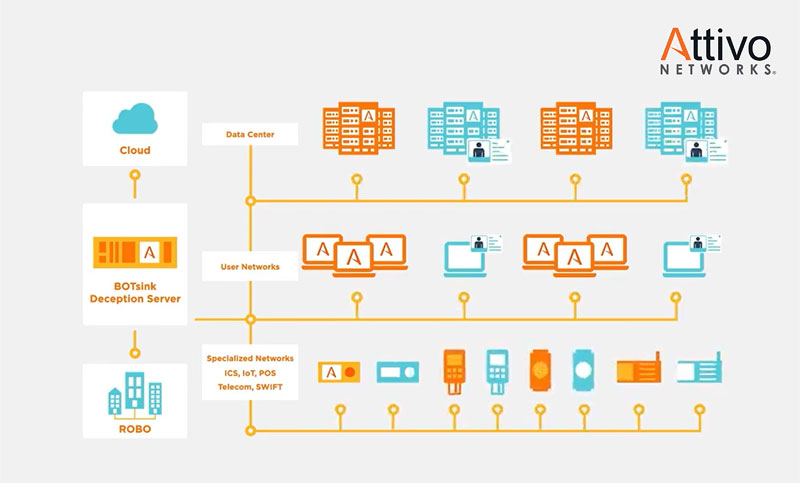
The ThreatDefend platform is not limited to on-premises networks but also offers early intrusion detection within a wide variety of cloud environments, including specialty cloud deceptions such as containers, cloud-specific credentials, access keys, storage buckets, and serverless functions.
Additionally, the ThreatDefend platform detects intrusions into OT and specialty environments such as ICS-SCADA, IoT, medical IoT, point-of-sale, telecom, and network infrastructure devices.
Organizations can automatically block and isolate threats immediately or opt to collect additional adversary intelligence within the safety of the deception environment.
The platform uses high-interaction deception to capture all attack activity, including TTPs and IOCs and can show time-lapsed attack replays.
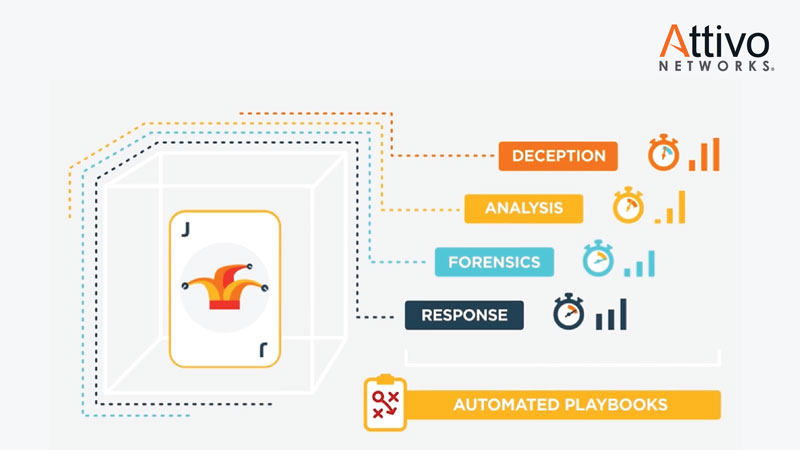
The Attivo Networks ThreatDefend takes deception even further and into the area of active defense, which incorporates automated attack analysis, forensics, and native integrations for accelerated incident response.
With the Informer solution, attacker activity is consolidated into a single dashboard that provides an accurate chronological session view of all attacker activity and forensic artifacts are presented in a clear, concise, indexable manner that responders and analysts will recognize and can take action on.
(See how the Attivo Networks ThreatOps Platform works hand-in-hand with the BOTsink engagement server for in-network threat detection, attack analysis, and acceleration of incident response. Courtesy of Attivo Networks an YouTube.)
Extensive native 3rd-party integrations accelerate incident response with automated blocking, isolation, and threat hunting for additional compromised systems.
Attivo provides additional intrusion detection and counterintelligence capabilities through DecoyDocs, deceptive data loss tracking (DLT) documents that generate detection and geolocation alerts when stolen and opened.
Collectively, this gives the SOC team a thorough understanding of attacker capabilities, goals, and motivation – while attackers think that they are escalating the attack.
Organizations can then take this intelligence and use it build a predictive defense, strengthen their overall security posture, and share with law enforcement and industry peers.
Security teams are also finding tremendous value in deception for “silent” threat hunting.
Post compromise, this allows teams to strategically place deception to determine if threats are eradicated and to set additional traps in the event the attacker tries to return.
On average, an attacker has 100 days in which to discover your systems, harvest data, review files, modifying data sets, exfiltration…
Anything and everything they need to return – however, Deception can promptly detect them if they do.
There are many unique business and technology advantages to implementing the ThreatDefend platform for Intrusion Detection:
Business: Strengthens Digital Risk Management
-
Early and accurate detection of in-network threats, exposed attack paths, and devices additions that increase risk.
-
Continuous network and endpoint vulnerability assessments, additional resiliency validation during pen testing, plus the ability to test whether existing security controls and risk parameters are reliably working.
-
Aggregated detection, threat intelligence, and reporting across all attack surfaces regardless of program or environment.
-
Tracking and substantiation of policy violations, which can be instrumental for insider and supplier threats and within shared cloud security models.
Technology Advantages: IT Risk Mitigation
-
Early detection of attacker reconnaissance, credential theft, lateral movement, and attempted data theft even if it’s from an unknown attacker.
-
Network, endpoint, application and data/database deceptions, directory services, mapped shares, cloud deceptions, Big Data, network and telecommunications, etc.
-
Ubiquitous detection across all attack surfaces from legacy to modern day
-
Accurate and actionable alerts: substantiated with full TTPs and IOCs, simplifying and accelerating incident response.
-
Machine-learning preparation, deployment, and management keeping deception authentic.
Overall, The ThreatDefend platform provides a unique approach to intrusion detection with engagement-based deception technology that detects threats early and throughout the attack lifecycle. In addition to not generating false positives, the solution will also pick up policy violations and misconfigurations that create risk.

This detection value is not limited to traditional attack surfaces, but also provides much needed visibility and detection capabilities in emerging attack surfaces such as the cloud, IoT, medical IoT, ICS-SCADA, POS, telecom, and more.
Additionally, with Attivo deception, organizations can easily collect and analyze adversary intelligence to anticipate where attackers will move next and accelerate incident response.
Over 30 native integrations automate incident response, including blocking, isolation, and threat hunting.
This intelligence can also be used to alert other industry organizations of the attack, shared with law enforcement, and/or applied to strengthen overall defenses.
Attivo Sweeps 2018 ‘ASTORS’ Homeland Security Awards with Record Eight Wins

Attivo Networks was honored with a record-breaking Seven 2018 ‘ASTORS’ Homeland Security Awards, (four Platinum, three Gold Awards), in American Security Today’s esteemed ‘ASTORS’ Awards, plus an Extraordinary Leadership Award, for the company’s outstanding innovation in the field of deception technology and their ongoing development and investment to the ThreatDefend™ Deception & Response Platform.
Attivo Networks
-
Best IT Intrusion Detection & Intrusion Prevention Solution
-
Attivo Networks ThreatDefend™ Deception and Response Platform
-
Best Cyber Incident Response
-
Attivo Networks ThreatDefend™ Deception and Response Platform
-
Best ICS/SCADA Cyber Security
-
Attivo Networks ThreatDefend™ Deception and Response Platform
-
Best Cyber Critical Infrastructure Solution
-
Attivo Networks ThreatDefend™ Deception and Response Platform
-
-
Best Integrated Security Mgmt System
-
-
ThreatDefend™ Deception Platform and ThreatPath™ Solution
-
Best IT Threat Intelligence Solution
-
ThreatDefend™ Deception Platform and ThreatPath™ Solution

-
Best Vulnerability Management System
-
ThreatDefend™ Deception Platform and ThreatPath™ Solution
-
*Attivo Networks was also recognized as a Triple-Winner in the 2017 ‘ASTORS’ Awards, and is a Proud Sponsor of the 2018 ‘ASTORS’ Homeland Security Awards Program.
The Annual ‘ASTORS’ Awards Program is specifically designed to honor distinguished government and vendor solutions that deliver enhanced value, benefit and intelligence to end users in a variety of government, homeland security and public safety vertical markets.

The 2018 ‘ASTORS’ Awards Program drew an overwhelming response from industry leaders with a record high number of corporate and government nominations received, as well as record breaking ‘ASTORS’ Presentation Luncheon Attendees, with top firms trying to register for the exclusive high – end luncheon and networking opportunity – right up to the event kickoff on Wednesday afternoon, at the ISC East registration!
Over 130 distinguished guests representing National, State and Local Governments, and Industry Leading Corporate Firms, gathered from across North America, Europe and the Middle East to be honored among their peers in their respective fields which included:
- The Department of Homeland Security
- The Federal Protective Service (FPS)
- Argonne National Laboratory
- The Department of Homeland Security
- The Department of Justice
- The Security Exchange Commission Office of Personnel Management
- U.S. Customs and Border Protection
- Viasat, Hanwha Techwin, Lenel, Konica Minolta Business Solutions, Verint, Canon U.S.A., BriefCam, Pivot3, Milestone Systems, Allied Universal, Ameristar Perimeter Security and More!
The Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program highlighting the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition, and keep our Nation safe – one facility, street, and city at a time.
The 2018 ‘ASTORS’ Homeland Security Awards Program was Proudly Sponsored by ATI Systems, Attivo Networks, Automatic Systems, Desktop Alert, and Royal Holdings Technologies.
Nominations are being accepted for the 2019 ‘ASTORS’ Homeland SecurityAwards at https://americansecuritytoday.com/ast-awards/.
Comprehensive List of Categories Include:
| Access Control/ Identification | Personal/Protective Equipment | Law Enforcement Counter Terrorism |
| Perimeter Barrier/ Deterrent System | Interagency Interdiction Operation | Cloud Computing/Storage Solution |
| Facial/IRIS Recognition | Body Worn Video Product | Cyber Security |
| Video Surveillance/VMS | Mobile Technology | Anti-Malware |
| Audio Analytics | Disaster Preparedness | ID Management |
| Thermal/Infrared Camera | Mass Notification System | Fire & Safety |
| Metal/Weapon Detection | Rescue Operations | Critical Infrastructure |
| License Plate Recognition | Detection Products | And Many Others! |
Don’t see a Direct Hit for your Product, Agency or Organization?
Submit your category recommendation for consideration to Michael Madsen, AST Publisher at: mmadsen@americansecuritytoday.com.
2018 Champions Edition
 See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
See the 2018 ‘ASTORS’ Champions Edition – ‘Best Products of 2018 ‘ Year in Review’ for in-depth coverage of the outstanding products and services of firms receiving American Security Today’s 2018‘ASTORS’ Homeland Security Awards.’
Enter Early to Maximize Media Coverage of your Products and Services at Kickoff, and Get the Recognition Your Organization Deserves!
And be sure to Register Early for the 2019 ‘ASTORS’ Awards Presentation Luncheon at ISC East 2019 to ensure your place at this limited- space event!