
Guest Editorial by Will Plummer, Military Veteran and Chief Security Officer at RaySecur
As businesses across the globe have grown in their reliance on digital infrastructure, so too has the number of criminal attacks on that infrastructure, creating an unprecedented amount of cybercriminal activity.
Consequently, companies have had to step up their vigilance and proactive defenses to fend off possible attacks. Companies of all stripes—particularly those in the oil, gas, and nuclear energy industries—have enacted extensive measures to bolster cybersecurity.
However, the threats to digital systems are no longer exclusively digital. A new cyber threat has emerged with the ability to infiltrate an organization’s wireless network under the guise of a seemingly innocuous package in the mail.
Known as “phygital” attacks, these tactics capitalize on lapses in physical security that frequently stem from a lack of collaboration between CISOs and CSOs.
Without a united effort from both parties, cybercriminals can bypass standard cyber defenses before releasing malicious code or stealing confidential information.
What is a Phygital Attack?
The word “phygital” is a portmanteau of “physical” and “digital,” which is apt since these attacks typically involve a physical device that wreaks digital havoc.
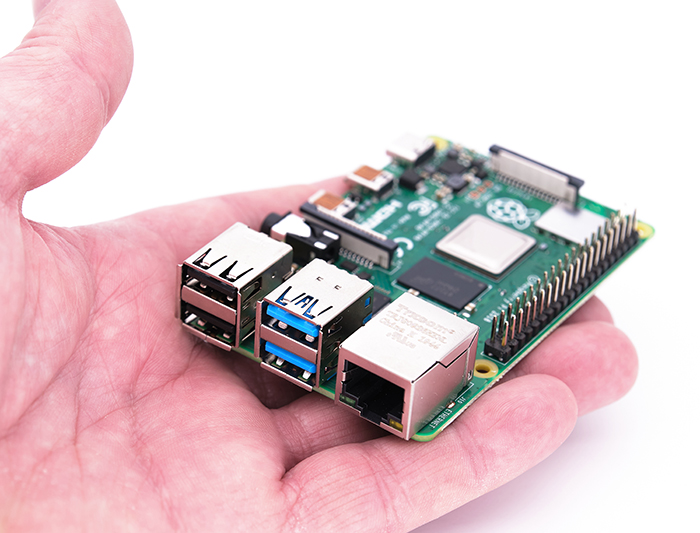
One of the most popular types of phygital attacks is “warshipping,” in which the attacker sends a digital device through the mail.
Warshipping can involve a USB drive, a Wi-Fi adapter, or a mini-computer, such as a Raspberry Pi, small enough to fit in a modestly sized cardboard package. What makes warshipping particularly dangerous is the low cost: for less than $100, a cybercriminal can acquire and assemble the components of a war shipping device.
Once the item reaches its destination, a modem transmits GPS coordinates to the attacker and scans the organization’s network for entry points. That scenario represents a nightmare for virtually any company.
After gaining access to the organization’s network, cybercriminals can uncover more vulnerabilities and essentially create an ongoing back door for further attacks. At that point, the cybercriminal could launch a full-scale ransomware attack and cause massive disruption.
These attacks are particularly worrisome in today’s climate of remote and hybrid work since packages tend to sit in mailrooms or on top of employees’ desks for days or even weeks.
Companies related to critical infrastructure, including utilities, oil and gas, and nuclear energy industries, have been a primary target for cybercriminals for years. For example, in 2021, a ransomware attack famously triggered a temporary shutdown of the Colonial Pipeline.
Despite the ongoing threat of cyberattacks, the public utilities sector in particular remains vulnerable to phygital attacks, particularly warshipping.
Mitigation Strategies for Phygital Attacks
Thankfully, there are multiple ways to effectively mitigate the risk of a phygital attack.
The first step is educating your employees about warshipping and other phygital tactics. This way, they won’t be caught off-guard when you introduce a series of new policies regarding company mail.
1. Process Incoming Mail Immediately
Organizations must treat all incoming packages as they would visitors to their workplace. Would you let a stranger walk straight up to the desk of your CISO? To prevent potentially dangerous materials from entering secure areas or sitting in your office for several days, process all incoming packages immediately and inspect them for unsolicited devices.
The fewer incoming packages your office receives, the less vulnerable you are to phygital attacks. For this reason, you may consider introducing a policy against employees receiving personal mail at work. Unsolicited packages will become apparent very quickly.
Likewise, let’s say a package arrives that simply looks sketchy. Maybe it’s addressed to someone who doesn’t work there and has never worked there, or the sender appears unfamiliar or dubious. These are both signs that you return the package immediately to the sender.
2. Safeguard Your Wi-Fi

Securing Networks & IoT Devices with Autonomous Detection and Response from guardDog AI.
Warshipping operates under the notion that the package will be left inside your mailroom, where the hidden device will have plenty of time to hack into your Wi-Fi and intercept your data.
So, you must protect your Wi-Fi with WPA2 authentication along with a virtual private network (VPN) and multi-factor authentication (MFA) for your employees. Realistically speaking, WPA2 authentication cannot give you 100% protection from warshipping.
However, it can give you additional time to identify and dispose of phygital devices while cybercriminals try to find their way around these additional security barriers.
Even with Wi-Fi protection in place, organizations must still monitor their networks for suspicious devices and activity. Fortunately, network discovery software can detect suspicious traffic and new devices when they connect to your network.
(Get an understanding of the world’s most cost-effective cyber security Ai with a revealing interview from guardDog AI founder Peter Bookman. Courtesy of F1 FibreFast and YouTube.)
Network discovery software can help you identify warshipping devices well before cybercriminals have obtained any sensitive data.
3. Scan Mail for Phygital Devices
Again, incoming mail deserves the same security protocols as new visitors to your building. With this in mind, organizations would be wise to implement scanning measures for incoming mail as soon as they receive it.
3D mail scanners, for example, can detect electronic devices in packages as well as hazardous powders or liquids without the use of harmful X-rays.
(See this interview with Will Plummer, RaySecur CSO at ISC West 2022 where by Chuck Harold asks, “what’s different about RaySecur and the scanning technology that is used?” Courtesy of RaySecur and YouTube.)
Organizations in the oil, gas, and nuclear energy industries and related critical infrastructure have harnessed scanning technology to monitor personnel for many years. With this in mind, it’s not unreasonable to consider implementing a similar process in your company’s mailroom.
Bridging the Gap
As digital integration sweeps the globe, cybercriminals will take further advantage of the physical blind spots that naturally result from this monumental shift.
It’s up to CISOs and CSOs to work together and collectively neutralize both digital and physical points of entry.
Before implementing such initiatives, both parties must commit to fully understanding the threat of phygital attacks. In the meantime, cybercriminals will continue exploiting the widespread lack of phygital knowledge to carry out their nefarious schemes.
About the Author

RaySecur
Will Plummer is 25-year veteran of the US Army, where he earned a Bronze Star with Valor as a Master Explosive Ordnance Disposal (EOD) Technician, and commanded multiple Special Operations units with multiple combat deployments.
He has an MA from the Naval War College and a BA from the University of California at Chico. Currently, Will serves as the Chief Security Officer for next-generation mail screening technology provider RaySecur.
Plummer leads the company’s physical security efforts, overseeing a team of EOD professionals, and managing clients’ threat mitigation efforts.
Related Technology…
guardDog .AI a Triple Platinum Winner in the 2022 ‘ASTORS’ Homeland Security Awards

American Security Today’s Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program, and now entering it’s Eighth Year, continues to recognize industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management and Response, Law Enforcement, First Responders, as well as federal, state and municipal government agencies in the acknowledgment of their outstanding efforts to Keep our Nation Secure.
guardDog .AI (First of Three)

Best Vulnerability Management Solution
-
guardDog AI-Powered Autonomous Detection and Response
-
For the first time, guardDog ai has provided the world with a cybersecurity system that is accessible to virtually everyone. It can see the risks device management solutions don’t cover and can thwart the attempted exploits it detects in less than 2 milliseconds.
-
guardDog.ai is a cloud-based software service plus a companion device that works together to simplify network security.
-
The solution exposes invisible threats on networks in ‘edge territory,’ and the devices attached to them, with patented technology to address and prevent cybersecurity threats before they compromise network environments.
-
guardDog’s Protective Cloud Services (PCS) is an AI-powered network security solution that doesn’t require cyber security expertise to operate.
-
Once activated, users’ Fido device goes to work by detecting threats and vulnerabilities on your network.
-
From there, the users’ cloud dashboard displays incidents by threat level and shows them information on how to resolve the issues before they become a problem.
(Learn More. Edge Territory is the invisible space between networks. For example connecting to a hotel or cafe Wi-Fi, or working from home can leave your sensitive or private data vulnerable. Any device on a network can also create openings for danger, such as a webcam or digital doorbell. guardDog makes the blind space visible. Combined with their AI-powered cloud solution, your guardDog device is always up to date, protecting you against the latest threats. With guardDog you can see the invisible threat and do something to stop it. Courtesy of Good Day Orange County and YouTube.)
guardDog Solutions (Second of Three)
Best Cyber Analytics Solution
-
No Cybersecurity Experience Required! guardDog.ai installation is a snap, and protection is a power light away.

-
Secure a home, a small office, a large enterprise, or any other organization with a cyber security management solution made easy that offers services to match the user’s needs.
-
How it Works: Unbox your Fido device, connect to your network, and register. From the moment the power light appears, protection begins. Fido gets to know your network and your devices.
-
It recognizes intruders and defends your network and devices. When someone attacks, it deploys automated countermeasures. User’s networks and devices are scanned vigilantly to protect against the known, and the unknown.
guardDog Solutions (Third of Three)
Best Threat Intelligence Solution
-
guardDog AI-Powered Autonomous Detection and Response
-
Coverage for “edge territory.” guardDog.ai make sit possible to detect and proactively thwart cybersecurity risks that device management can’t see – the threats in the edge territory that require an overlay that’s as simple as “plug and protect” for consumers and businesses.
-
It uses a cloud AI database to see and thwart attempted exploits before they can enter the network and succeed in planting virus, phishware or ransomware attempts.
-
The ability to thwart attempted exploits in less than 2 milliseconds. Every business, government, healthcare institution, home consumer, or other organization, is grappling to find security solutions that are adapt to this changing world. guardDog.ai is pioneering innovations that can truly meet these new and perpetual challenges.
-
Last year alone, there were over 12,000 new vulnerability exploits that emerged, and no human could really keep up with that.

-
guardDog’s ai-powered service learns about these attacks and keeps users’ Fido devices up to date.
-
The training never stops to prevent a crisis before it happens.
-
guardDog.ai has developed a cloud-based software service with a companion device that works together to simplify network security.
-
The solution exposes invisible threats on networks, and the devices attached to them, with patented technology to address and prevent cybersecurity threats before they compromise network environments.

-
*AST is delighted to welcome guardDog.ai, a 2021 ‘ASTORS’ Awards Champion, as a New Premier Awards Sponsor in the 2022 ‘ASTORS’ Homeland Security Awards Program.
American Security Today’s Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program, and now entering it’s Eighth Year, continues to recognize industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management and Response, Law Enforcement, First Responders, as well as federal, state and municipal government agencies in the acknowledgment of their outstanding efforts to Keep our Nation Secure.
Homeland Security remains at the forefront of our national conversation as we experience an immigration crisis along our southern border and crime rates that are dramatically higher than before the Pandemic across the United States.

These challenges have become a national priority with an influx of investments in innovative new technologies and systems.
Enter American Security Today, the #1 publication and media platform in the Government Security and Homeland Security fields, with a circulation of over 75,000 readers and many tens of thousands more who visit our AST website at www.americansecuritytoday.com each month.
The pinnacle of the Annual ‘ASTORS’ Awards Program is the Annual ‘ASTORS’ Awards Ceremony Luncheon Banquet, an exclusive, full-course plated meal event, in the heart of New York City.

This year’s exclusive sold-out ‘ASTORS’ luncheon featured representatives of law enforcement, public safety, and industry leaders who came together to honor the selfless service of those who stand on the front lines, and those who stand beside them – providing the capabilities and technologies to create a safer world for generations to come.
This year marks the 20th anniversary of the Department of Homeland Security (DHS), which came out in force, to discuss comprehensive collaborations between private and public sectors that have led to the development of intelligence and technologies which serve to protect our nation.

The continually evolving ‘ASTORS’ Awards Program emphasized the trail of Accomplished Women in Leadership in 2022, as well as the Significance and Positive Impact of Advancing Diversity and Inclusion in our Next Generation of Government and Industry Leaders.
The keynote address was provided by U.S. Customs and Border Protection (CBP) Office of Field Operations (OFO) Deputy Executive Assistant Commissioner (DEAC) Diane Sabatino, who described the changes to CBP through the tragedy of 9/11 and the relentless commitment to its mission and ongoing investment in the latest technologies and innovations to protect our borders and Homeland.
The resounding theme of the DEAC’s remarks was her pride in the women and men of the CBP and their families who support them.

AST was also joined by Legendary Police Commissioner William Bratton, who spoke, as always, about his love for the City of New York, the Profession of law enforcement to which he has dedicated his life, and for which he continues to drive thought leadership and innovation.
New York City Police Department (NYPD) Chief of Department Kenneth Corey, came out to address Luncheon attendees and shared some of his experiences and the changes in policing he’s witnessed over his more than three decades of service.

FDNY Chief Joseph Jardin honored the men and women of the FDNY, not only those who currently serve but all of those who have selflessly served, with special recognition of those lost on 9/11.
Chief Jardin spoke about the continuing health battle of many following 9/11 with cancer and respiratory disease, yet now knowing the full consequences, would not have made a different decision to respond.
As Chief Jardin noted, mission-driven service is in the lifeblood of every firefighter, volunteer and sworn and has been so throughout the history of the Fire Service.
Former head of the FBI’s active shooter program, Katherine Schweit joined AST to sign complimentary copies of her book, ‘STOP THE KILLING: How to End the Mass Shooting Crisis,’ thanks to the generosity of our 2022 ‘ASTORS’ Awards Sponsors.
The 2022 ‘ASTORS’ Awards Program was Proudly Sponsored by NEC National Security Systems (NSS), ATI Systems, Automatic Systems of America, guardDog AI, Fortior Solutions, IPVideo Corporation, Rajant Corporation, RX Global, and SIMS Software!
We were pleased to welcome the esteemed New York City Fire Department (FDNY); the New York City Police Department (NYPD); and the NYC Hospital Police, as well as Executive Management from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), and many other DHS agencies, Federal law enforcement agencies, and private/public partnerships such as the National Association of Women Law Enforcement Executives (NAWLEE), the 30×30 Initiative, a coalition of professionals advancing the representation of women in policing; and Operation Lifesaver, Inc. (OLI) (rail safety advocates).

The prestigious Annual ‘ASTORS’ Homeland Security Awards Program highlights the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition and keep our Nation safe – one facility, street, and city at a time.

In 2022 over 240 distinguished guests representing Federal, State, and Local Governments, and Industry Leading Corporate Firms gathered from across North America, Europe, and the Middle East to be honored among their peers in their respective fields.
Each year, to keep our communities safe and secure, security dealers, installers, integrators, and consultants, along with corporate, government, and law enforcement/first responder practitioners, convene in New York City to network, learn and evaluate the latest technologies and solutions from premier exhibiting brands at ISC East, the Natural Disaster & Emergency Management Expo (NDEM EXPO), and the ASIS NYC Expo.
ISC East is the Northeast’s leading security & public safety event, hosted in collaboration with sponsor Security Industry Association (SIA) and in partnership with ASIS NYC.

 Corporate firms, the majority of which return year to year to build upon their Legacy of Wins, include:
Corporate firms, the majority of which return year to year to build upon their Legacy of Wins, include:
Advanced Detection Technologies, AMAROK, ATI Systems, Axis Communications, Automatic Systems, BriefCam, Canon U.S.A., Cellbusters, CornellCookson, CyberArk Fortior Solutions, guardDog.ai, Hanwha Techwin of America, High Rise Escape Systems, IPVideo Corporation, Konica Minolta Business Solutions, NEC National Security Systems, NICE Public Safety, OnSolve, PureTech Systems, Quantum Corporation, Rave Mobile Safety, Regroup Mass Notification, Robotic Assistance Devices, Rajant Corporation, SafeLogic, Select Engineering Services LLC, Singlewire Software, SolarWinds Worldwide, Teledyne FLIR, Valor Systems, and West Virginia American Access Control Systems, just to name a few!
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old-school basics to what is Today – a fast-changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace with over 75,000 readers at the Federal, State, and local levels of government as well as firms allied to the government.
American Security Today brings forward a fresh compelling look and read with our customized digital publications that hold readers’ eyes throughout the story with cutting-edge editorial that provides solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

AST Digital Publications are distributed to over 75,000 qualified government and homeland security professionals, in federal, state, local, and private security sectors.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches both Private & Public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture, and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from Government at the federal, state, and local levels as well as from private firms allied to the government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website, and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants & Dams, Bridges & Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting & Concert Stadiums, our Nation’s Schools & Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
To learn more about ‘ASTORS’ Homeland Security Award Winners solutions, Be On the LookOut for the 2022 ‘ASTORS’ CHAMPIONS Edition Fully Interactive Magazine – the Best Products of 2022 ‘A Year in Review’.
The Annual CHAMPIONS edition includes a review of ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firm’s products and services, including video interviews and more.

It will serve as your Go-To Source throughout the year for ‘The Best of 2022 Products and Services’ endorsed by American Security Today, and can satisfy your agency’s and/or organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection, and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware, and Networking Security – to name a few), the 2021 ‘ASTORS’ CHAMPIONS EDITION will have what you need to Detect, Delay, Respond to, and Mitigate today’s real-time threats in our constantly evolving security landscape.
It will also include featured guest editorial pieces from some of the security industry’s most respected leaders, and recognized firms in the 2022 ‘ASTORS’ Awards Program.
For more information on All Things American Security Today, as well as the 2023 ‘ASTORS’ Awards Program, please contact Michael Madsen, AST Publisher at mmadsen@americansecuritytoday.com.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos






















