Guest OpEd by Gilad David Maayan
With advances in technology consumers are increasingly relying on applications and devices to perform daily tasks. These technologies have become essential to our lives and sometimes happiness.
This reliance results in a growing awareness of security and thus growing customer demand for products that provide secure and dependable services.
In order to maintain customer loyalty, companies must increase their focus on secure software development. This development concerns application vulnerabilities as well as the processes and approaches you take to manage vulnerabilities.
In this article, we’ll look at some of the challenges faced by development teams and provide some tips for addressing them.
Importance of Secure Software Development
Leaving software vulnerabilities, like poor encryption, unaddressed or unprotected when pushing products to production, will often leave you poorer in time and productivity.
Not addressing these issues before releasing a product, will eventually require you to devote additional time and effort.
Such costs will be tied to either patching flaws or to repairing damages done by vulnerability exploits. This can impede general productivity and negatively impact applications currently in production.
Secure development can play a huge role in your company’s bottom line. Security flaws and breaches can lead to fines and sanctions for lack of regulatory compliance.
It can also lead to loss of consumer trust. If users feel they can’t rely on your products to keep them or their information safe, you will lose customers and profits.
Challenges and Considerations
Developers face a variety of challenges in creating secure software.
Below, you’ll find a review of the challenges, as well as some suggestions that might help create viable solutions.
Speed of Agile Development
Many software development teams have adopted agile methodologies to speed product creation and release.
While this strategy can boost production, the short timelines it imposes can have negative consequences. Pushing for quick release of software can lead to accidental inclusion of vulnerabilities.
It can also encourage developers to ignore issues in order to meet deadlines. Teams may be motivated to cut short security testing procedures or even try to bypass security altogether.
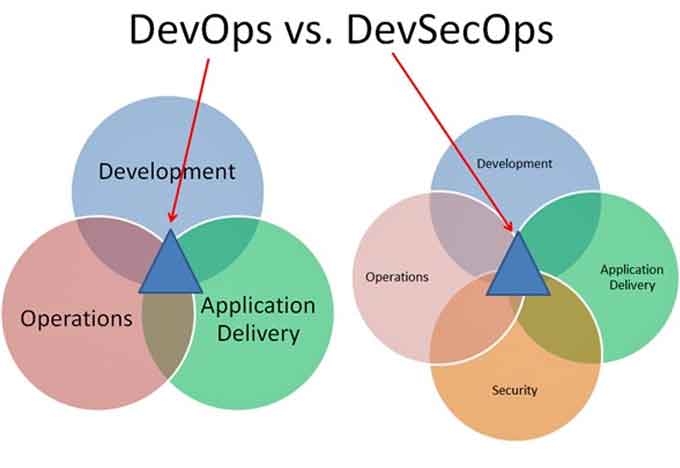
Employing a DevSecOps strategy to shift security left can prevent vulnerabilities from occurring in the first place. Doing so will help your entire team better incorporate security concerns and practices into their work and promote collaboration on security tasks.
Adopting a broad variety of tools can help you ensure that most, if not all, vulnerabilities and flaws are evaluated and eliminated.
Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), manual testing, and threat modeling are all practices that you should include.
Also, consider using an application vulnerability management system. It can help you keep track of test results and centralize analysis, making sure that any issues found are addressed appropriately.
(Check Out Brinqa – A 2019 ‘ASTORS’ Homeland Security Award Winner is an integrated solution that combines correlation of vulnerabilities, threat intelligence and business context with risk analysis and scoring to prioritize remediation efforts and measure program effectiveness. Courtesy of Brinqa and YouTube.)
Risks of Using Open Source Components
Many, if not most, products use open source components; either libraries, frameworks, or individual code snippets. Being prebuilt, these can significantly reduce development time but often also introduce unknown dependencies.
Many open source components are used in a “black box” fashion.
Developers know what the component does but do not necessarily know exactly how it works. This can lead to the introduction of vulnerabilities stemming from insecure code as well as inconsistencies in patching and versioning.
Additional issues can arise if developers are not mindful of the download origin of their components or their version numbers. Such a lack of uniformity adds complexity that can be difficult to track and manage.
It is more likely to lead to missed updates or conflicts between components.
To reduce the number of dependencies created, you should only use open source components when you are unable to code something yourself. Importing functions or libraries for simple tasks can create avoidable vulnerabilities.
You should avoid building or deploying code from the Internet whenever possible. Rather, you should download the components you need and use the same versions across the board.
This can help you ensure that your component has not been tampered with. It will make patching and updating simpler.
Using application vulnerability tools that perform Software Composition Analysis (SCA) can help you locate and track vulnerable components.
Vulnerabilities in Code
Every programming language has its own unique vulnerabilities that can affect the security of your application.
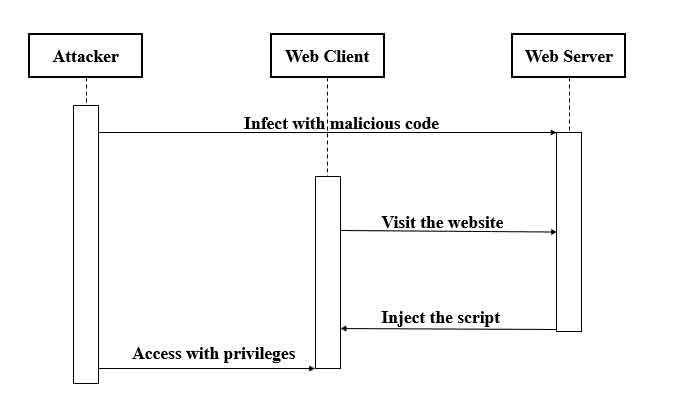
For example, injection attacks with JavaScript or SQL or Cross-Site Scripting (XSS) with PHP and Ruby.
Injection attacks allow an attacker to read or modify databases by submitting code through unfiltered user input mechanisms. XSS allows attackers to execute scripts in user browsers, redirecting users to malicious sites or stealing information through cookies.
Not being aware of the specific vulnerabilities that your chosen language faces has risks. This lack of knowledge means you are more likely to unknowingly include exploitable functionality.
Making yourself and your team aware of language specific issues can minimize your application’s security risks. Using APIs to filter user interactions can further reduce the opportunities provided to attackers.
Sanitize shell commands and user inputs by comparing input to approved regular expressions. This can eliminate the chance of code injection.
Apply the principle of least privilege to restrict access to sensitive data or vulnerable components. Doing so will limit the damage that successful attacks can cause.
Lack of AppSec Planning
AppSec refers to application security, the process of securing all the software a business uses.
Lack of proper planning around AppSec can quickly lead to unmanageable security flaws. Without a plan you are likely to see a diffusion of responsibility around security. This diffusion can leave unclear expectations of duties or requirements for production ready products.
Lack of planning can mean that teams revert to ineffective methods. Included in this are reliance on manual testing or traditional development methods.
These tests and methods are often insufficient and inefficient and can conflict with modern security processes and tools.
(Learn More about application security. Courtesy of VERACODE.)
Start by creating clear guidelines for who is responsible for each security task. Implement explicit benchmarks for security expectations.
As part of your plan, you should include procedures for tracking the progress of vulnerability identification and resolution. For example, using playbooks which standardize steps to be taken in a scenario.
In doing so, you can ensure that issues are not overlooked or forgotten and simplify future patching.
Conclusion
Development teams face a wide variety of challenges when creating software products.
The vulnerabilities you need to address will vary, according to language, functionality, deployment, etc. Despite this variability, the challenges covered here are applicable to nearly all applications.
They are a good place to start in ensuring that your development practices are secure.
By employing these practices, you can reduce the vulnerabilities present in your software. With this, you can rest easy knowing you and your customers are safer.
About the Author

Gilad David Maayan is a technology writer who has worked with over 150 technology companies including SAP, Samsung NEXT, NetApp and Imperva, producing technical and thought leadership content that elucidates technical solutions for developers and IT leadership.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos
Subscribe to the AST Daily News Alert Here.
Main Image source