SolarWinds, the 2022 Platinum ‘ASTORS’ Homeland Security Award Winner for Best IT Access Control & Authentication Solution, recently Nominated to Compete in the 2023 ‘ASTORS’ Awards Program, is pleased to announce its Next-Generation Build System aligns with the National Institute of Standards and Technology (NIST®) Secure Software Development Framework (SSDF) and Software Supply Chain Security Guidance.
The software development and build process improvements were accelerated over the past year in response to the highly sophisticated SUNBURST cyberattack, which targeted SolarWinds and other technology companies.
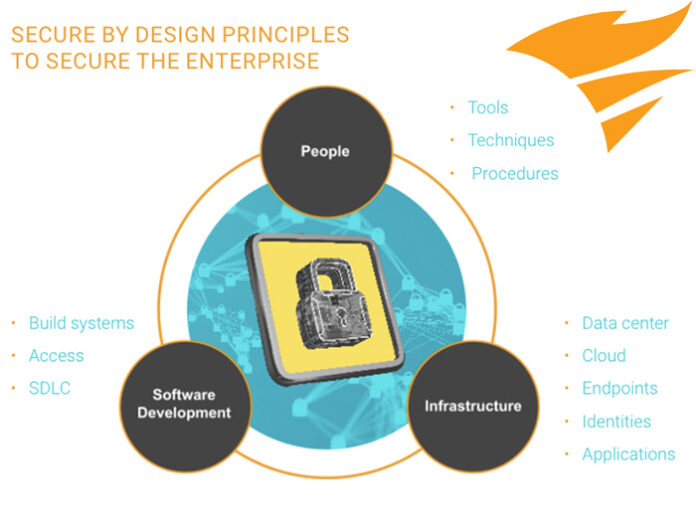
SolarWinds launched its Secure by Design initiative in 2021 in response to the SUNBURST supply chain attack that took advantage of a backdoor implanted in a supplier to target and compromise organizations indirectly around the globe.
The Next-Generation Build System includes new software development practices and technology to strengthen the integrity of the ‘build’ environment.
This consists of the first-of-its-kind “parallel build” process, where the development of SolarWinds takes place through multiple highly secure duplicate paths to establish a basis for integrity checks.
Because the software build process at SolarWinds used at the time of the SUNBURST attack is common throughout the technology industry, SolarWinds released components of the new build system as open-source software, enabling other organizations to benefit from the company’s learnings and help establish a new industry standard for secure software development.

“Communicating transparently and collaborating within the industry is the only way to effectively protect our shared cyber infrastructure from evolving threats,” explained Sudhakar Ramakrishna, President and CEO, SolarWinds.
“Our Secure by Design initiative is intended to set a new standard in software supply chain security via innovations in build systems and build processes. We believe our customers, peers, and the broader industry can also benefit from our practices.”
This initiative is a multi-pronged strategic approach featuring proprietary technology, products, and processes designed to strengthen the company and industry further.
A key component of this initiative is the company’s Next-Generation Build System, which leverages a unique parallel build process where software is developed in multiple secure, duplicate, and ephemeral environments.
(Learn More. Sophisticated threat actors are becoming more active, organized sophisticated ransomware events are more common, and supply chain vulnerabilities continue to emerge. Today’s attacks show us risk mitigation takes organizational input and knowledge. Security and risk management should be part of everyone’s role. Timothy Brown, SolarWinds CISO, and Paul Gray, GVP of Engineering discuss SolarWind’s ongoing evolution to Secure by Design, the lessons they’ve learned, and their actions. Courtesy of SolarWinds and YouTube.)
SolarWinds aligned the Next-Generation Build System with four key tenets of Secure by Design principles:
Dynamic operations
-
Building only short-term software build environments that self-destruct after completing a specific task.
Systematic build products
-
Ensuring build products can be made deterministically so any newly created byproducts will always have identical, secure components.
Simultaneous build process:
-
Creating software development byproducts, such as data models, in parallel to establish a basis for detecting unexpected product modifications.
Detailed records:
-
Tracking every software build step for complete traceability and permanent proof of record.

“The SSDF guidelines will be an important step in strengthening our nation’s overall cybersecurity posture,” added SolarWinds Chief Information Security Officer and VP of Security, Tim Brown.
“At SolarWinds, we’ve implemented our Secure by Design initiative with the goal of becoming a leader in enterprise software security.”
“This has included aligning our software development processes with NIST’s Secure Software Development Framework and CISA’s Enduring Security Framework as outlined by the National Cybersecurity Strategy.”
The SolarWinds Next-Generation Build System consistently meets or exceeds the proposed standards of the NIST Secure Software Development Framework by:
-
Conducting software builds in parallel by utilizing three isolated and distinct build environments, where each build step is signed and verified before going through a secure validation environment built to perform a variety of scans and security checks to validate the product before release
-
Advancing beyond zero trust by adopting and implementing an assume breach position to eliminate implicit trust in applications and services
-
Utilizing ephemeral operations in the software development process to eliminate dependencies and remove the opportunity for malicious threat actors to establish a “home base” in systems
-
Deploying automated tools designed to run on a recurring basis to scan for vulnerabilities throughout the development process, including through open-source software vulnerability checks, static code analysis, and dynamic application security testing
-
Generating a software bill of materials (SBOMs), which provides a comprehensive picture of all the components, libraries, tools, and processes used in the build process
-
Following responsible disclosure protocols for verified and validated vulnerabilities
President Biden signed Executive Order 14028 in May 2021 to implement stronger cybersecurity standards in the Federal Government and improve the software supply chain.
Executive Order directed NIST to develop, update, and implement zero-trust architecture and framework guidance to enhance the security of the software supply chain while also directing the Office of Management and Budget (OMB) to order adherence to NIST guidelines.
 Key aspects of the SolarWinds Secure by Design initiative have been Recognized by industry peers and experts for security innovation by winning the CSO50 Award for IT Infrastructure Monitoring and Management.
Key aspects of the SolarWinds Secure by Design initiative have been Recognized by industry peers and experts for security innovation by winning the CSO50 Award for IT Infrastructure Monitoring and Management.
The SolarWinds Next-Generation Build System has also received Recognition from the 2023 BIG Innovation Awards and the Cloud Security Awards, with a judge stating the company’s cutting-edge technology sets “a new standard for excellence in the industry.”
SolarWinds has called for increased information sharing across the industry and more robust public-private partnerships to combat increasingly sophisticated nation-state cyberattacks.
To support collaboration among the public and private sectors, SolarWinds recently hosted a panel discussion in Washington, D.C., highlighting several key ways to help the industry stay secure.
This includes working together to create a strong defense, supporting responsible disclosure to increase information sharing, and ensuring the industry invests in the people skills needed to defend against the newest threats.
(Hosted by SolarWinds CISO and VP of Security Tim Brown, this event includes a bipartisan panel of government leaders discussing the United States National Cybersecurity Strategy, its related frameworks, and the nature of today’s cyber risks. Courtesy of SolarWinds and YouTube.)
SolarWinds is a leading provider of simple, powerful, secure IT management software built to accelerate customers’ digital transformation.
The company’s solutions provide organizations worldwide—regardless of type, size, or complexity—with a comprehensive and unified view of today’s modern, distributed, and hybrid network environments.
SolarWinds continuously engage with tech professionals (IT service and operations professionals, DevOps and SecOps professionals, and database administrators (DBAs)) to understand the challenges they face in maintaining high-performing and highly available IT infrastructures, applications, and environments.
(Whether you need to deliver a custom service across clouds, support physical hardware, optimize multiple database platforms, conduct security operations, or perform ticketing and service management, SolarWinds can unify all of this into one platform and make it much simpler to manage. All these things are interconnected and must work together seamlessly for your business to function at its best. SolarWinds is here to facilitate and encourage collaboration between teams, build consensus, and help solve problems faster. They’re always listening, always evolving, and always empowering their users. Courtesy of SolarWinds and YouTube.)
The insights gained from them, in places like the THWACK community, allow SolarWinds to address customers’ needs now and in the future.
With a focus on the user and commitment to excellence in end-to-end hybrid IT management, SolarWinds has established itself as a worldwide leader in solutions for observability, IT service management, application performance, and database management.
To learn more, please visit www.solarwinds.com.
SolarWinds Nominated in Eighth Consecutive ‘ASTORS’ Homeland Security Awards Programs

American Security Today’s Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program, and now entering its Eighth Year, continues to recognize industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management and Response, Law Enforcement, First Responders, as well as federal, state and municipal government agencies in the acknowledgment of their outstanding efforts to Keep our Nation Secure.
SolarWinds Worldwide (First of Three)
 Best IT Access Control & Authentication Solution
Best IT Access Control & Authentication Solution
SolarWinds Access Rights Manager
-
The objective of access control is to reduce the risk of unauthorized access to files, data, and systems and is, therefore, an important component of an organization’s security policy, and effective management is required to achieve compliance. However, access control tasks can be burdensome, resulting in insecure accounts, errors, and a lack of audit documentation.

-
SolarWinds Access Rights Manager (ARM) is designed to assist IT and security admins to quickly and easily provision, de-provision, manage, and audit user access rights to systems, data, and files, so they can help protect their organizations from the potential risks of data loss and data breaches. By analyzing user authorizations and access permission, admins get a visualization of who has access to what and when they accessed it, and with a few clicks, customized reports can be generated to demonstrate compliance with most regulatory requirements.
-
SolarWinds ARM automates access rights management, analysis, and enforcement by identifying insecure accounts while providing audit trails. It enhances security by monitoring, analyzing, and auditing Active Directory®, Azure AD, Exchange, SharePoint, OneDrive, and file servers to see what changes have been made, by whom, and when they occurred.
-
ARM helps prevent data leaks and unauthorized changes to sensitive files and data through the visualization of permissions on file servers and simplifies Exchange monitoring and auditing to help prevent data breaches by tracking changes. ARM helps improve compliance and detect unauthorized changes.
-
SolarWinds ARM is being widely adopted across DoD and civilian government agencies. It’s available on the U.S. General Services Administration (GSA) Schedule and other government contract vehicles.
- (SolarWinds Access Rights Manager (ARM) helps IT and Security Admins meet compliance requirements with centralized provisioning, de-provisioning, management, and audit of user permissions and access to systems, data, and files while protecting their organizations from internal security breaches. Courtesy of SolarWinds and YouTube.)
-
SolarWinds ARM enhances security by monitoring, analyzing, and auditing Active Directory®, Azure AD, Exchange™, SharePoint, OneDrive, and file servers to see what changes have been made, by whom, and when those changes occurred, and customized reports can be generated to demonstrate compliance with most regulatory requirements.
-
The solution also provisions and deprovisions users using role-specific templates to help assure conformity of access privilege delegation in alignment with security policies.
-
ARM helps prevent data leaks and unauthorized changes to sensitive files and data through visualization of permissions on file servers.
-
SolarWinds ARM reduces IT workload through a web-based self-service portal, put access rights of data in the hands of data owners instead of admins.
SolarWinds Worldwide (Second of Three)
 Best Network Management Solution
Best Network Management Solution
SolarWinds Network Configuration Manager
-
Successful threat mitigation requires continuously monitoring network configuration changes and potential policy violations. Still, this process needs to be automated, fast, and reliable, and continuous real-time monitoring and alerts for automated detection and remediation of harmful security violations is essential.

-
SolarWinds® Network Configuration Manager (NCM) provides these benefits—and more. In addition to the “bread and butter” of compliance and configuration management, NCM offers compliance auditing and leverages baselines and differential viewers to help ensure devices are configured correctly. Automated change control workflow, bulk configuration updates, and automatic vulnerability assessments help teams efficiently identify and fix vulnerabilities, all in a single solution.
-
NCM offers several unique and powerful features to help agency IT Pros protect against vulnerabilities and prevent unauthorized network configuration changes. NCM uses Cisco® IOS® and ASA vulnerability scanning and NIST FISMA, DISA STIGs, and DSS PCI compliance assessments to improve network security.
-
Administrators can manage changes through automated workflows and set up two-level approval policies for configuration updates, helping ensure that only the right changes are made by the right people. Configuration baseline features help standardize compliant configurations and monitor configuration drift. NCM’s change management auditing and real-time change notification features allow administrators to see who made a configuration change and when so they can quickly respond to the change and mitigate the issue if necessary.
(See how you can increase visibility to your network devices with SolarWinds® Network Configuration Manager. Save time and improve network reliability by automating network configuration and change management to reduce configuration errors, recover quickly from downtime, and improve security and compliance. Courtesy of SolarWinds and YouTube.)
-
The NCM software features hundreds of built-in compliance reports to help meet major auditing authority requirements, including DISA STIGs, NIST FISMA, and more. Meanwhile, THWACK®, the SolarWinds online user community, provides several free report templates that can be used to prepare for an inspection.
-
SolarWinds NCM is used by nearly every U.S. federal civilian agency, DoD branch, and intelligence agency. It is available on the U.S. General Services Administration (GSA) Schedule and other contract vehicles.
SolarWinds Worldwide (Third of Three)
Best Security Incident & Event Management Solution (SIEM)
SolarWinds Security Event Manager
-
Threats to IT networks continue to accelerate and evolve. While enterprising hackers from external sources test the robustness of network security parameters, internal threats from careless and malicious insiders remain a major and ongoing concern.

-
It’s critical agencies take steps to combat these threats—and SolarWinds® Security Event Manager (SEM) is a powerful weapon. This comprehensive SIEM solution delivers dynamic, real-time log collection and analysis for immediate and actionable threat intelligence. It can capture and analyze log data from multiple sources and specific incidents in real-time, allowing users to quickly identify and remediate threats, uncover policy violations, and resolve vital network issues.
-
In addition, SolarWinds SEM features other innovations not seen in traditional SIEM solutions, including in-memory correlation for immediate threat detection and remediation; USB Defender® technology to help identify rogue devices and enforce USB policies; and unique IT search capabilities for better remediation and audit reporting. SEM includes support for single sign-on and improved management.
(See a brief overview of the capabilities of SolarWinds Security Event Manager (formerly Log & Event Manager), and how you can use the SIEM tool to detect threats, quickly respond to cyber incidents, and report compliance from a consolidated interface. Courtesy of SolarWinds and YouTube.)
-
Like all SolarWinds software, SEM is built to scale and can support IT environments of all sizes. It employs a node-based license model that allows users to stay within their planned budgets as they deploy and expand their IT infrastructures across multiple data centers and geographies. A new Workstation Edition license makes monitoring logs from Windows workstations more affordable than ever.
-
SolarWinds SEM is used by nearly every U.S. federal civilian agency, DoD branch, and intelligence agency. It’s available on the U.S. General Services Administration (GSA) Schedule and other contract vehicles.
-
*SolarWinds has been officially recognized with Multiple Award Wins for Seven Consecutive Years – 2022, 2021, 2020, 2019, 2018, 2017, and 2016. Thank you for your continued confidence in AST!

















