Guest Editorial by Hajra Khan
Our lives have become all about better and faster connectivity. No matter where we are or what we are doing, we’re always connected to the internet.
But do we understand the price we pay for this constant connectivity?
With this seamless, unhindered connectivity, endless data is being shared across platforms and further used by those platforms as well, such as data centers, cloud databases, and Internet of Things (IoT) devices.
This boundless connectivity and data sharing have a great role to play in digital transformation and advancement.
But, at the same time, it comes at a high cost of making our online privacy inevitably much more vulnerable.
Why are Data Breaches becoming more common than ever before?
Data breaches are an everyday occurrence, and they are growing at an astonishing rate.

You’ll understand the gravity of the situation better if we told you what Gil Shwed, Check Point’s Founder and CEO, uncovered in the company’s cybersecurity predictions for the year 2020.
“Attacks are constantly increasing: over the past year, our ThreatCloud Managed Security Service blocked nearly 90 billion compromise attempts per day – compared with six billion daily searches on Google.”
In fact, these breaches and cyber-attacks have become so common that the FBI has had to soften its policy on ransom payments.
The agency acknowledges that in some cases, ransom payment may be the best route to protect shareholders, employees, and customers.
An average internet user may exclude himself from the equation.
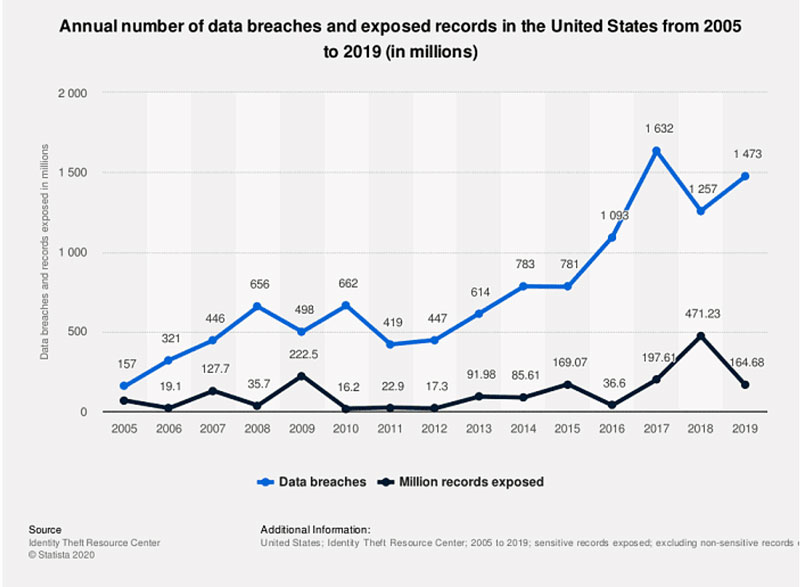
But you need to think why these attacks are increasing with every passing day.
One of the most crucial reasons is the way we share our personal information using multiple platforms – including online social media forums, recruitment agencies, smart and IoT devices, and communication platforms such as WhatsApp, Skype, Slack, etc.
That’s why it is becoming increasingly easier for hackers to design targeted attacks. But, on the other hand, it’s becoming that much harder to protect our online privacy.
These are shocking facts, but they are nothing in comparison to what goes on behind the scenes.
There are several other factors that influence the rise in data breaches and the leak of user information.
Let’s have a look at them as well.
Artificial Intelligence (AI)
Artificial intelligence has undoubtedly enhanced threat response mechanisms helping to block millions of cyberattacks through deep learning security algorithms, biometric identification as well as system automation.
However, as it is, the bad guys have the same technology at hand that can identify the difference between the patterns of coincidence or behavior.
It can also learn to disguise a behavior, manipulate the defense mechanisms, and push past the security protocols.
AI is largely the basis for the exponential hike in cybercrimes as hackers are frequently using it to probe networks, seek out weaknesses, and create more evasive and complex malware.
Moreover, AI Fuzzing (AIF) and Machine Learning (ML) poisoning are expected to add more fuel to the fire.
AI Fuzzing and Machine Learning Poisoning
AI fuzzing has enhanced the enterprises’ ability to identify and fix exploitable vulnerabilities within their systems.
But it has also helped cyber-criminals to initiate, automate, and expedite zero-day attacks.
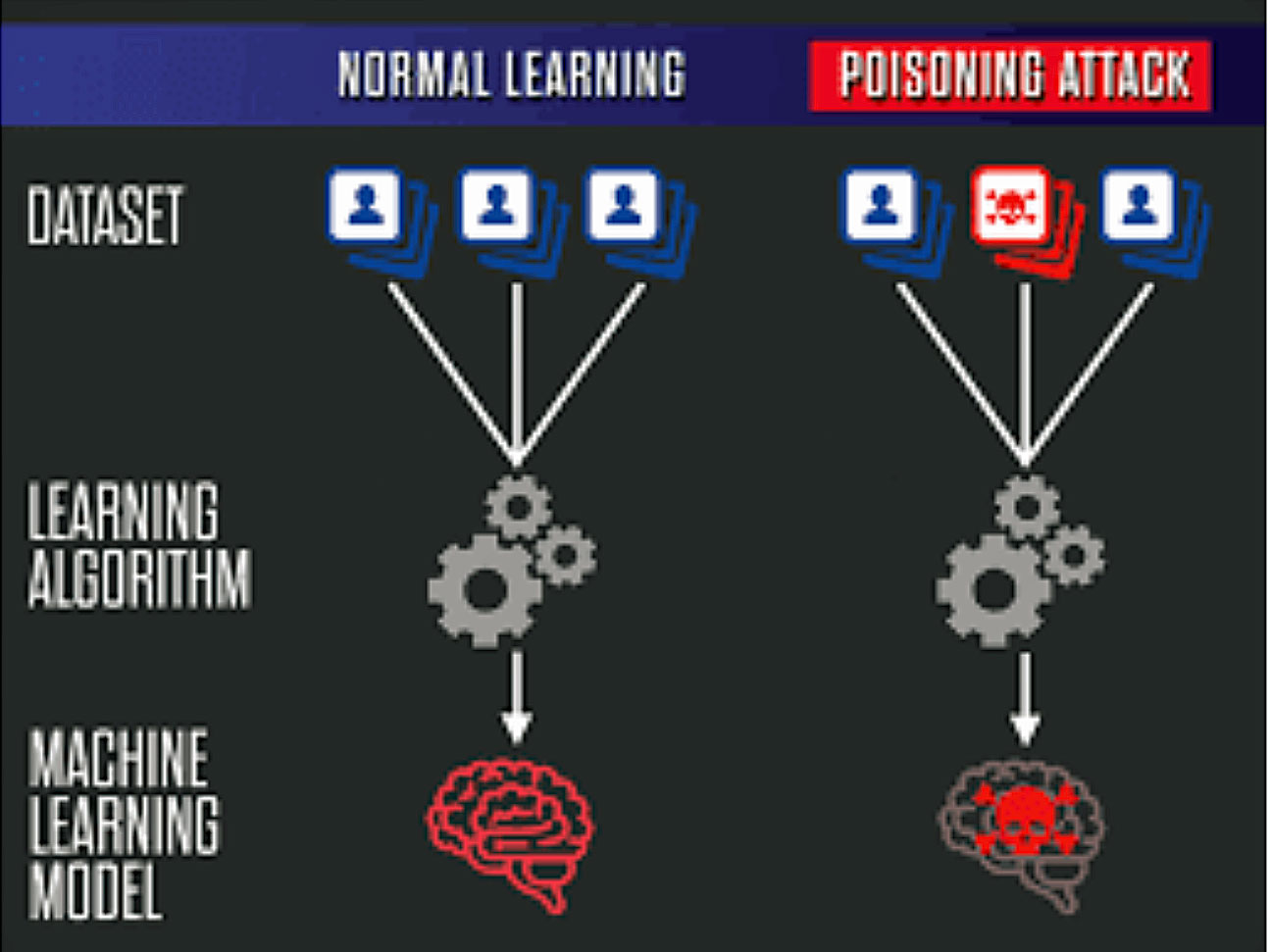
On the other hand, hackers are also targeting machine learning logic models and feeding stealthy instructions into them, thereby weakening the entire system and making it vulnerable to cyber-attacks.
Deployment of 5G Technology
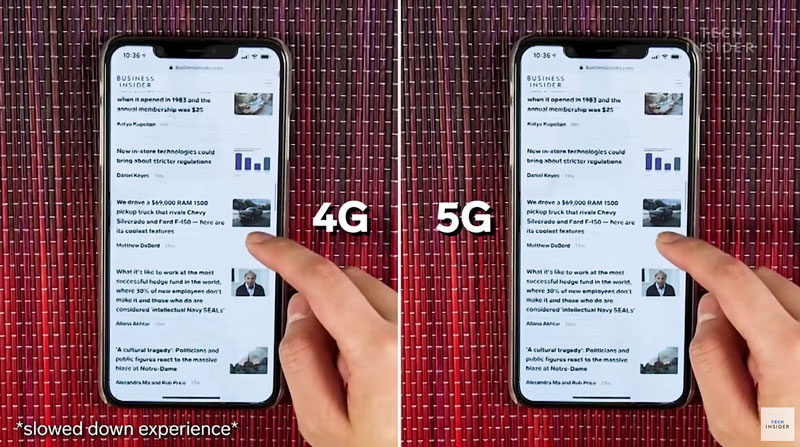
5G Technology is being rolled out rather fast and furiously, which will take the percentage increase in connectivity to a whole new level.
With download speeds up to 100 times faster than 4G and hyper network densification, it is up to you to take a wild guess at what that would do to an already momentous volume of information sharing.
Unfortunately, with the 5th generation mobile network, the era of 5th generation cyberattacks has also begun.
At the moment, the cybersecurity infrastructure is nowhere near ready to take on the enormous onslaught of malware attacks that are anticipated to run rampant as more and more people convert to 5G.
Though, cloud-based antivirus cybersecurity solutions have helped to fend off a large number of malware attacks before they can cause much damage.
But with 5G technology, the adoption of IoT devices will also shoot up, giving rise to unbridled information sharing, both deliberate and unwitting.
This is where the major concerns lie as the IoT devices’ connectivity to cloud networks is still a weak link in security.
Liken that to a haven on earth for cybercriminals where consumers will never know what hit them.
Summing Up
The purpose of this article is to make common internet users aware of the potential cybersecurity vulnerabilities that are growing at a steady rate.
“Over-connectivity” has become a thing.
So, while you enjoy the seamless connectivity, you must also know that you’re up against many genius minds with only one thing on their minds – to get their hands on your sensitive information.
To ensure security at their end, users must control the extent of personal information they put out there.
Furthermore, they should also opt for the latest in antivirus technology to warrant maximum protection against cyber-attacks. Remember that caution is always better than cure.
The Author, Hajra Khan can be reached at khan.hajra@gmail.com.
Learn More…
5G Cyber Security: THREATS AND POSSIBLE SOLUTIONS