
Attivo Networks, Triple-Award Winner in the 2017 ‘ASTORS’ Homeland Security Awards Program, is pleased to announce the company’s ThreatDefend Deception and Response Platform has been nominated to compete in multiple categories of the 2018 ‘ASTORS’ Awards Program.
In today’s connected society, attackers have proven that they can and will get into even the most resilient networks.
 For years, attackers have been successfully using deception tactics as a foundation for breaching networks.
For years, attackers have been successfully using deception tactics as a foundation for breaching networks.
They do this by masquerading as legitimate employees, using stolen credentials and deceptive measures to infiltrate a network, all the while remaining undetected for lengthy dwell times.
It is now time to turn the tables on attackers and use deception against them.
Outwitting an adversary is rarely accomplished without a balance of defensive and offensive measures, and deception brings the offense into the realm of cybersecurity with the ability to deceive and misdirect an attacker into revealing themselves.
All, without false positive alert fatigue and the burden of operational overhead associated with traditional detection methods.
Given its efficacy in detection and ability to gather intelligence to diffuse the attacker, deception is rapidly becoming a de facto security control for closing the detection gap and for being able to reliably answer the question of whether there are threats inside the network.
(See a brief introduction to deception technology and the Attivo Networks ThreatDefend Deception and Response Platform. Courtesy of Attivo Networks and YouTube. Posted on Jun 22, 2018)
What’s Different with Deception?
The challenge with current detection solutions is that they are reliant on signatures, pattern matching, or behavioral anomaly detection and as such, are limited in efficacy or take time to “get good.”
The learning and tuning process inherently produces false positive noise that will drain resources and create alert fatigue.
A new approach is needed, one that is accurate and actionable.
This new approach is deception, which delivers accurate, early detection, evidence-based alerts, and an effective solution for reducing the mean time to remediation.
Uniquely, it is also the only security control that is designed to slow down an attacker and to use their own attack techniques against them.
(Carolyn Crandall, Chief Deception Officer of Attivo Networks Interviews Tony Cole, Chief Technology Officer of Attivo Networks to discuss Why CISOs Need to Shift Focus to Detection. Courtesy of Attivo Networks and YouTube. Posted on Apr 19, 2018)
Why the ThreatDefend™ Deception and Response Platform
Throughout history, deception has been used in military warfare, sports, and gambling to outsmart the adversary.
Attivo Networks has now successfully applied threat deception in cybersecurity and is empowering organizations of all sizes and industries to gain the upper hand against attackers.
Made available as the Attivo ThreatDefend™ Deception and Response Platform, the solution provides a powerful security control for early threat detection and changing the asymmetry against attackers.
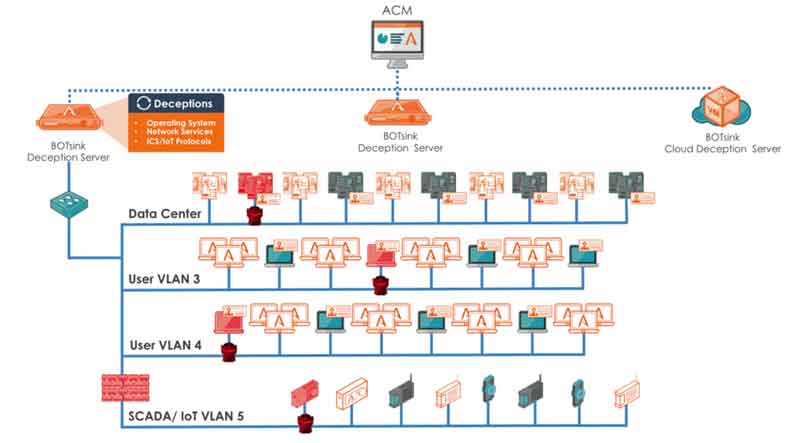
As the most comprehensive and scalable platform on the market, Attivo dynamic traps, bait, and lures provide threat deception for the wide range of today’s evolving attack surfaces including networks, cloud, data centers, remote offices, IoT, medical IoT, ICS-SCADA, and POS networks.
By turning the environment into a virtual “hall of mirrors,” deception disrupts an attacker’s reality and imposes increased cost as they are forced to decipher what is real versus fake.
One small mistake will reveal the attacker’s presence and force them to start over or abandon their efforts altogether.
The ThreatDefend approach also addresses the debate of whether deception is best suited at the endpoint or in network.
Simply put, you need both to catch all threat vectors and their attempts of reconnaissance or credential theft.
Additionally, ThreatDefend high-interaction deception technology engages attackers to gain threat intelligence, identify attack paths, analyze attacks, and automate incident response through 3rd party integrations.
(Learn More from Carolyn Crandall, Chief Deception Officer of Attivo Networks. Courtesy of Fox 5, Attivo Networks and YouTube. Posted on Jul 28, 2017)
Detection
The ThreatDefend platform is designed for the most sophisticated human and automated attackers and is unique in that it offers endpoint, network, data, application, Active Directory, and database deceptions to detect ever-changing attack methods.
Both small and large organizations can benefit from built-in machine-learning, which automates deployment and simplifies operations by auto-proposing deception campaigns.
This maintains the highest levels of authenticity and provides an automated refresh of the deception environment in order to amplify deceptions based on user behavior, reset the attack surface on-demand, avoid fingerprinting or simply reset the attack surface after a compromise.
Active Defense Unlike other detection solutions, the ThreatDefend platform does not stop with a detection alert and goes further to provide organizations with an Active Defense which gives them a better understanding of the attacker and automates incident handling.
(The Attivo ThreatPath™ solution provides an attack path vulnerability assessment based on likely attack paths that an attacker would traverse through misconfigured systems or credential misuse. A topographical illustration of the attack paths provides a straight-forward view of how an attacker can move laterally once they have engaged with their first end-point system. Clickable drill downs provide the details of weaknesses and IP addresses for systems needing to be isolated and/or fixed. Integrations with prevention systems can be leveraged for automated response actions and trouble tickets can be activated inside the dashboard. Courtesy of Attivo Networks and YouTube. Posted on Apr 12, 2018)
Based on engagement with an adversary, the ThreatDefend solution safely collects attacker TTPs, IOCs, and counterintelligence for insight into attacker capabilities, goals, and the information they are seeking to exfiltrate.
Additionally, through extensive 3rd party integrations the ThreatDefend platform shares IOC information, accelerates incident handling, and creates repeatable incident response playbooks for efficiency in threat remediation.
Information sharing and improving the ability to respond to threats has been a key topic for security teams.
 The ThreatDefend platform delivers upon this promise with extensive 3rd party integrations to share attack data and automate the incident handling and threat hunting processes.
The ThreatDefend platform delivers upon this promise with extensive 3rd party integrations to share attack data and automate the incident handling and threat hunting processes.
Furthermore, the platform provides visibility tools for understanding device adds and changes to the network, vulnerable attack paths based on exposed, orphaned, and misused credentials, and attack path replay for gaining a better understanding on how the attacker attacked and strategies he may have used.
DecoyDocs also adds counterintelligence on what types of documents attackers are targeting and through geo-location, where the documents are being accessed.
Ease of Use
 Attivo Networks provides the most flexible and fastest deployment options through the ThreatDefend platform, software distribution (SCCM, Casper) or host management (GPO or WMI- built-in windows tools), REST APIs and 3rd party integrations like McAfee EPO & ForeScout.
Attivo Networks provides the most flexible and fastest deployment options through the ThreatDefend platform, software distribution (SCCM, Casper) or host management (GPO or WMI- built-in windows tools), REST APIs and 3rd party integrations like McAfee EPO & ForeScout.
Network deception is out of band so there is no network interference to deploy, and endpoints are agentless for easy deployment.
The solution includes the ability to auto-propose deceptions based on machine learning of the environment, making deployment and ongoing management simple.
For example, a customer shared it took 15% of one person’s time over a day to deploy and didn’t require additional staff to manage ongoing operations.
Authenticity
Maintaining decoy, credential, and deception object authenticity and attractiveness is core to the efficacy and manageability of deception.
The ThreatDefend platform uses real operating systems and offers the ability to use the company’s production golden images to match the production environment seamlessly, making it impossible for the attacker to discern which systems are deceptive.
Endpoint deceptions will also validate with Active Directory to ensure the utmost authenticity of the deception credentials.
Attivo offers 50 various out of the box deception campaign options to support environmental authenticity.
Scalability
Customer deception deployments range from small environments of 30 people up to global Fortune 100 organizations.

The platform is recognized for its comprehensive network and endpoint deceptions that are field-proven for deployment in user networks, data centers, cloud, ROBO, and specialty environments such as IoT, ICS-SCADA, POS, telecom and more.
Customers have purchased virtual, cloud, or hardware appliance systems for network deception and agentless endpoint technology that is customer-proven with millions of endpoint deceptions deployed.
Market Validation
Attivo has an exceptional base of global Fortune customers, government, and midmarket customers.
Top verticals include financial, healthcare, technology, energy, retail, and professional services like law firms, staffing, entertainment, and training centers.
Based on analyst feedback, Attivo is the recognized leader in distributed deception platforms and has a considerable lead in technology maturity and customer base.
Attivo also won over 27 awards in 2017 for its technology leadership.
The company grew over 300% in 2017 and is in active discussions and POC engagements with over 350 enterprise companies and government agencies.
Its customer base is in the 3 digits, validating market demand and acceptance of this technology and Attivo’s approach to threat deception.
Customer Success/Example
It is clear, based on the adoption of Attivo technology, that customers are gaining value from early detection and the substantiated alerts, which provide them with actionable insights to efficiently understand and shut down attacks.
Below are a couple of example customer views on deception for cybersecurity and why they ultimately chose the Attivo ThreatDefend Platform.
Attivo Networks® Behind the Mask Interview with a University Director of Cybersecurity: Carolyn Crandall, Chief Deception Officer of Attivo Networks interviews George Insko, Director of Cybersecurity at University of Kentucky. Courtesy of Attivo Networks and YouTube. Posted on Apr 25, 2018)
George shares his experience with deception technology in Attivo Network’s Behind the Mask Series.
(Attivo Networks® Behind the Mask Interview with Cybersecurity Expert Sarath Geethakumar: Carolyn Crandall, Chief Deception Officer of Attivo Networks interviews cybersecurity expert Sarath Geethakumar. Courtesy of Attivo Networks and YouTube. Posted on Apr 25, 2018)
Sarath shares his experience with deception technology in Attivo Network’s Behind the Mask Series.
Summary
The Attivo Networks® ThreatDefend™ Deception and Response Platform deserves this award recognition based upon its efficiency in immediately providing detection value by accurately alerting on attacker engagement or attempts to use deception credentials.
Alerts are engagement-based and substantiated, eliminating false positives and accelerating incident response.
Given its ease of operations and scalable design, no additional staff is required to deploy or operate the solution, preventing scope creep and unexpected expenses.
Additionally, the ability to share attack information and automate incident response extends the value of existing security infrastructure.
Overall, Attivo deception provides efficient and accurate detection alerts of insider (employees, contractors, suppliers) and external attacker activity early, saving time, energy, cost, and negative impact from breaches.
The solution also uniquely empowers organizations with capabilities that they cannot achieve with other security controls: the capacity to outmaneuver the attacker, force them to execute flawlessly, and ultimately derail their efforts using their beloved approach of deception.
Attivo ThreatDefend Deception and Response Platform at a Glance
Comprehensive Deception and Decoy
 Make the Entire Network a Trap to Confuse and Misdirect Attackers into Revealing Themselves
Make the Entire Network a Trap to Confuse and Misdirect Attackers into Revealing Themselves
- Decoys appear identical to production assets, luring attackers into revealing themselves.
- Decoy configurations run real Linux, Mac, and Windows OS and are customizable to match the “golden image” of the production environment.
- Deception lures (bait) redirect attackers trying to infect endpoints, servers/VMs to engagement servers for detection.
- Bait includes deception credentials, ransomware bait, and other deception lures.
Deception Authenticity and Campaigns
 Camouflage for Dynamic Behavioral Deception
Camouflage for Dynamic Behavioral Deception
Discover, assign, and refresh decoys, credentials, and attacker bait dynamically with automated, self-learning deception campaigns.
- Intelligent deployment of deceptive assets to match the behavior of a user’s network.
- Continuously monitor, evolve, refresh, deceptive credential and lures.
- Self-healing technology dynamically respins decoys after engagement, preventing attacker fingerprinting and identification.
Automated Deception Campaign Deployment
 Adaptive Deception for Scalability and Auto-reset of Deception
Adaptive Deception for Scalability and Auto-reset of Deception
Attivo Adaptive Deception Campaigns provide breakthrough scalability, which is critical for large network deployment and for instantly resetting the attack surface to stop an attacker from successfully completing a breach.
- Automatically deploy deception campaigns created from environmental learnings
- On-demand resetting of deception synthetic network including decoys, lures, and credentials
- Create uncertainty for the attacker, escalate the chances of them making a mistake, and increase their costs as they are forced to restart or abandon their attack
Reduction of Attack Detection Time
 Prevent Data Exfiltration
Prevent Data Exfiltration
Prevent attackers from exfiltrating valuable company information and credentials and stop them before any damage can be done.
- Attack detection is provided real-time by accurately identifying infected clients, including sleeper and time-triggered agents, enabling remediation of the attack before damage can be done.
- No false positives. Alerts only occur when a hacker is engaged, and an attack on the BOTsink Solution has occurred.
Identify and Understand the Methods and Intent of Hackers
 Analysis and Forensics
Analysis and Forensics
After the attacker has engaged with the Attivo deception platform, they can either be automatically or manually quarantined and studied for detailed forensics. After quarantining the malware, the Attivo BOTsink allows the attack to fully detonate inside the controlled system, generating a full scale forensic analysis that can be exported into popular formats. The Attivo analysis engine will analyze:
- The techniques and methods of the attack
- Where the attacker is and which systems are infected
- Which systems will be infected next and how to quarantine the spread of the attack
The forensic ability of the Attivo deception platform allows for unparalleled visibility into any attack on your network.
Improve Incident Response with Actionable Alerts
 Substantiated Alerts Based on Attacker Engagement: No False Positives
Substantiated Alerts Based on Attacker Engagement: No False Positives
The Attivo BOTsink Solution provides accurate, actionable alerts, with the intelligence you need to take immediate action and stop BOTs and APTs in your network.
- There are NO legitimate reasons for a user to communicate with the Attivo BOTsink Solution, so any scans or attempts to engage it represent an attacker trying to find and target high-value network assets.
- If the BOTsink Solution doesn’t see anything, you can rest assured your assets are safe, and you have the coverage you need to identify a BOT or APT, as soon as it enters your network.
- The longer a BOT or APT engages the Attivo BOTsink Solution, the more data it collects and analyzes to support remediation and forensics.
- With the BOTsink Solution, you can quickly and efficiently strengthen your overall security and shut down BOTs and APTs to protect your IP and brand.
Defend Your Network
 Reporting and Automations to Block Attacks and Quarantine Devices
Reporting and Automations to Block Attacks and Quarantine Devices
- Captures and Analyzes Actionable Information—identifies the infected systems and collects and analyzes information on the time, type and anatomy of the attack.
- Provides Forensics—capturing and cataloging all attack activity to support understanding of the attack’s anatomy and objectives that can lead to a better overall security stance.
- Reporting and Seamless Eco-System Integration—Security professionals have the option to access detailed attack information through UI, PCAP files, Syslog, IOC, and CSV report formats or can automatically set configurations to block and quarantine through prevention system integrations.
Attivo Networks® provides the real-time detection and analysis of inside-the-network threats.
The Attivo ThreatDefend™ Deception and Response Platform detects stolen credentials, ransomware, and targeted attacks within user networks, data centers, clouds, SCADA, and IoT environments by deceiving an attacker into revealing themselves.
Comprehensive attack analysis and actionable alerts empower accelerated incident response.
Attivo Networks Wins Trifecta in the 2017 ‘ASTORS’ Homeland Security Awards Program

-
Attivo Networks
- Gold ‘ASTORS’ Award Winner
- Attivo Networks ThreatDefend Deception and Response Platform
- Best Critical Infrastructure Solution
-
Attivo Networks
- Platinum ‘ASTORS’ Award Winner
- Attivo Networks ThreatOps Solution
- Best Integrated Security Management Solution

-
Attivo Networks
- Gold ‘ASTORS’ Award Winner
- Attivo Networks ThreatDefend Deception and Response Platform
- Best Intrusion Detection & Prevention Solution

Over 100 distinguished guests from National, State and Local Governments, and Industry Leading Corporate Executives from companies allied to Government, gathered from across North America and the Middle East to be honored from disciplines across the Security Industry in their respective fields which included representatives from:
- The Department of Homeland Security
- The Department of Justice
- The Security Exchange Commission
- State and Municipal Law Enforcement Agencies
- Leaders in Private Security























