Guest Editorial by Scott Aken, CEO, Axellio
Introduction: A New Era of Data Encryption
In today’s increasing threat landscape, secure data transmission has become paramount, and end-to-end data encryption is vital to protecting our most sensitive information.
But this cryptographic armor simultaneously presents a paradox — the very shield that guards our data can obstruct our visibility of potential security threats lurking within our networks.
The recent introduction of a new version of the Transport Layer Security (TLS) protocol, TLS 1.3, brings this paradox into sharp focus.
Regarded as a groundbreaking advancement in encryption technology, TLS 1.3 offers a level of data protection that is considered unbreakable.
However, while it significantly fortifies data security, it also generates unexpected challenges in all networks today, particularly within Zero Trust architectures.
Two equally pivotal requirements are inherent to the Zero Trust model: end-to-end encryption and thorough inspection of all network traffic.
Today’s monitoring solutions often find these co-requisites challenging to accommodate fully; ironically, they are often diminished by the strength of TLS 1.3 encryption.
From TLS 1.2 to 1.3: An Evolution in Encryption
To fully grasp these intricacies, it’s crucial to understand the evolution of the TLS protocol and how it’s affected network monitoring.
The predecessor to the TLS protocol, Secure Sockets Layer (SSL), and early versions of TLS up to TLS 1.2, all offered encryption and decryption mechanisms that allowed for monitoring network traffic.
Passive monitoring of the initiation of encrypted connections was achievable, as was sharing the private key from the end devices with the monitoring application, thanks to the constant use of the same private key across all connections.
However, the landscape began to change with encryption technology advancements.
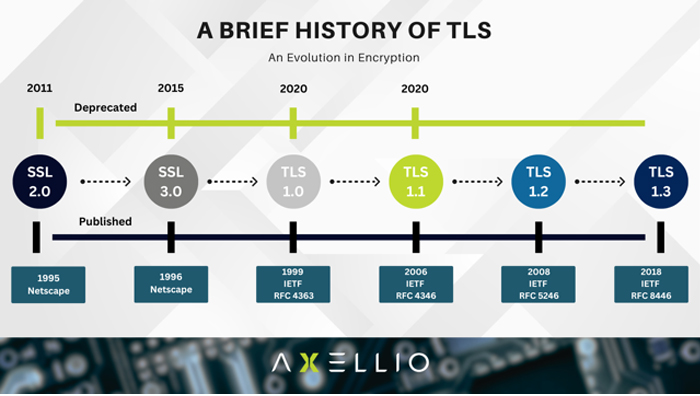
Despite a significant number of devices relying on them, SSL and earlier iterations of TLS, including TLS 1.0 and 1.1, have been discontinued.
The successor to SSL, the TLS protocol, is now the key mechanism securing data communication over all networks. It utilizes asymmetric cryptography, leveraging a public key, accessible to all users interacting with the server, and a private key, securely housed on the server, to decrypt information encrypted with the public key.
In light of the escalating exchange of sensitive and private information across our digital networks and the rising levels of security threats, a more robust encryption standard has become essential.
Coupled with a surge in security awareness, these factors have catalyzed the development of TLS 1.3. This newer protocol not only represents a significant stride in encryption but also ushers in substantial enhancements over its predecessors, setting a new benchmark in data security.
In contrast to earlier versions of TLS and SSL, where a compromised key could allow decryption of all past and future traffic, TLS 1.3 significantly mitigates this risk with its innovative key management approach.
With TLS 1.3, if a key is compromised, only a single conversation can be decrypted, while past and future communications remain secure. This represents a crucial shift in data protection, incorporating Perfect Forward Secrecy (PFS) and generating a unique session key for each user interaction.
The PFS approach plays a pivotal role in bolstering the security offered by TLS 1.3.
The Challenge of Visibility with TLS 1.3
The enhancements in TLS 1.3, while significantly enhancing security, simultaneously complicate network, device, and application visibility, are essential for cyber security in any environment and one of the main pillars of Zero Trust.

TLS 1.3’s PFS feature necessitates real-time access to each unique session key for decryption for each conversation, a demand most current monitoring systems cannot accommodate.
With the vast majority of traffic entering or leaving the corporate network now encrypted and about a quarter of this traffic already using TLS 1.3, the visibility challenge and the resulting security risk are no longer theoretical; they carry tangible and often severe ramifications.
A 2022 study by Enterprise Management Associates found that over 80% are interested in deploying TLS 1.3 due to its increased security, with the majority seeing the benefits, especially for remote employees.
However, almost all are concerned that TLS 1.3 would undermine their existing security controls, with 44% of organizations needing to roll back their TLS 1.3 implementations due to substantial losses in visibility into their networks.
This starkly underscores the delicate balancing act between enhancing encryption and retaining necessary visibility for effective security management.
Exploring Solutions to the Visibility Challenge
The dilemmas associated with TLS 1.3’s implementation have prompted discussions on navigating the resultant loss of visibility.
Various potential solutions are currently under consideration:
Endpoint Detection and Response (EDR) solutions:
-
Already widely deployed, it also adds the benefit that it has access to unencrypted content directly on the client or server. However, not all devices can host EDR solutions like many IoT devices, and advanced attackers have already successfully circumvented EDR controls.
-
Even though EDR systems provide a valuable layer of protection, other infrastructures such as networks or systems unable to support EDR applications, are still unprotected.
Inline Devices:
-
Organizations can maintain a degree of visibility by making monitoring systems part of the encryption chain by having them decrypt and re-encrypt.
-
However, this approach is processing intensive and difficult to scale, especially when multiple systems need traffic access, and can introduce latency and additional security vulnerabilities.
Network Segmentation:
-
Some organizations use TLS 1.3 security, by limiting TLS 1.3 usage to public/outbound communication only while restricting internal traffic to TLS 1.2.
-
Even though this requires additional decryption and encryption at the organization’s network edge, it maintains visibility within their internal networks through current monitoring means.
Out-of-Band Decryption Devices:
-
These devices can decrypt and inspect data without incurring performance penalties, offering a path forward for maintaining network visibility.
-
Their major advantage is that decryption for all monitoring systems is only done once, limiting delay and complexity, but may require re-thinking of the current monitoring approach. However, a secure distribution mechanism for all monitoring and analysis applications is essential.
Fingerprinting Tools:
-
Tools such as JA3 and JA3S provide a ‘fingerprint’ of client-server TLS handshake interactions without decrypting the communication.
-
Even though this can provide some indication of misuse of communication by a threat actor, it often does not provide enough detail for a conclusive analysis for triangulation or incident response.
-
Furthermore, its application is limited for encrypted connections, when HTTP/2 is used with multiple streams or with compression, and with HTTP/3 over Quick UDP Internet Connections (QUIC).
(Learn about Axellio® PacketXpress® – a network intelligence platform that captures, stores, analyzes, and distributes all network traffic in an extremely small footprint of over 100 Gbps. It is designed to enhance your existing security analysis applications’ performance, efficiency, and accuracy. Courtesy of Axellio and YouTube.)
The Bigger Picture: Future-proofing Cybersecurity with Balanced Encryption
The advent of TLS 1.3 brings to the forefront a need to balance between robust data encryption and the necessity for network visibility in maintaining effective cybersecurity defenses.
It’s crucial to understand that encryption is not inherently detrimental to security but is a complex tool that impacts the broader security framework.
Organizations can maintain their infrastructure security without compromising visibility by fostering a multifaceted approach to cybersecurity that integrates innovative methods for retaining visibility and a continuously evolving understanding of the role of encryption.
Conclusion: Embracing the Future of Encryption
In conclusion, the evolution from TLS 1.2 to 1.3 signifies a necessary and meaningful progression in encryption technology. TLS 1.3 significantly enhances the security of our data transmission, albeit with associated visibility challenges TLS 1.3 presents that demand careful navigation to preserve a robust security stance.
It underlines the pressing necessity to adapt and innovate in an evolving digital security landscape continually.
The industry needs to focus on marrying visibility and efficient end-to-end encryption, rather than treating them as separate challenges. This synergy will enable us to enjoy the best of both worlds without compromising on one for the other.
Both visibility and encryption are critical pillars in our quest for robust security.
Ultimately, grappling with these challenges necessitates embracing the complexity of the encryption landscape. This will equip us to tackle the future of digital security effectively.
As encryption technology continues to evolve, our strategies for maintaining visibility and control over our digital realms must keep pace.
The road ahead may not always be smooth, but the ultimate goal—a more secure digital world—is a challenge worth rising to.
About the Author
Scott Aken is the Chief Executive Officer of Axellio, which provides extremely high-performance, scalable, and compact time-series data solutions for the defense and intelligence community for simultaneous data ingest, storage, and distribution at speeds exceeding 100 Gbps.

Under Scott’s leadership, Axellio extended its portfolio from cyber security monitoring and forensic analysis into Signal Intelligence (SIGINT) data recording and distribution.
Scott’s background includes a wealth of expertise and a passion for securing and defending against cyber threats, with over 20 years in cybersecurity and mobile technologies.
Previously, Scott was president of Charon Technologies, a subsidiary of CACI International. Scott has also held key leadership roles in L-3 Communications and SAIC, developing corporate-wide cyber strategies and product and solution offerings and determining key investments.
Scott built his cyber expertise as a Special Agent with the FBI, where he conducted numerous cyber counterintelligence computer intrusion investigations and was a member of their elite Cyber Action Team.
Before his career at the FBI, Aken spent a decade working in the software and Internet industry, holding leadership positions at VeriSign/Network Solutions, GE, and Manugistics, Inc., a JDA Software company.
Related Technologies…
SolarWinds Takes Best Network Management Solution in 2022 ‘ASTORS’ Awards Program

American Security Today’s Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program, and now entering it’s Eighth Year, continues to recognize industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management and Response, Law Enforcement, First Responders, as well as federal, state and municipal government agencies in the acknowledgment of their outstanding efforts to Keep our Nation Secure.
SolarWinds Worldwide (First of Three)
 Best Network Management Solution
Best Network Management Solution
SolarWinds Network Configuration Manager
-
Successful threat mitigation requires continuous monitoring of network configuration changes and potential policy violations. Still, this process needs to be automated, fast, and reliable, and continuous real-time monitoring and alerts for automated detection and remediation of harmful security violations are essential.

-
SolarWinds® Network Configuration Manager (NCM) provides these benefits—and more. In addition to the “bread and butter” of compliance and configuration management, NCM offers compliance auditing and leverages baselines and differential viewers to help ensure devices are configured correctly. Automated change control workflow, bulk configuration updates, and automatic vulnerability assessments help teams efficiently identify and fix vulnerabilities, all in a single solution.
-
SolarWinds NCM offers several unique and powerful features to help agency IT Pros protect against vulnerabilities and prevent unauthorized network configuration changes. NCM uses Cisco® IOS® and ASA vulnerability scanning and NIST FISMA, DISA STIGs, and DSS PCI compliance assessments to improve network security.
-
Administrators can manage changes through automated workflows and set up two-level approval policies for configuration updates, helping ensure that only the right changes are made by the right people. Configuration baseline features help standardize compliant configurations and monitor configuration drift.
-
NCM’s change management auditing and real-time change notification features allow administrators to see who made a configuration change and when so they can quickly respond to the change and mitigate the issue if necessary.
(See how you can increase visibility to your network devices with SolarWinds® Network Configuration Manager. Save time and improve network reliability by automating network configuration and change management to reduce configuration errors, recover quickly from downtime, and improve security and compliance. Courtesy of SolarWinds and YouTube.)
-
The NCM software features hundreds of built-in compliance reports to help meet major auditing authority requirements, including DISA STIGs, NIST FISMA, and more. Meanwhile, THWACK®, the SolarWinds online user community, provides several free report templates that can be used to prepare for an inspection.
-
SolarWinds NCM is used by nearly every U.S. federal civilian agency, DoD branch, and intelligence agency. It is available on the U.S. General Services Administration (GSA) Schedule and other contract vehicles.
SolarWinds Worldwide (Second of Three)
 Best IT Access Control & Authentication Solution
Best IT Access Control & Authentication Solution
SolarWinds Access Rights Manager
-
The objective of access control is to reduce the risk of unauthorized access to files, data, and systems and is, therefore an important component of an organization’s security policy, and effective management is required to achieve compliance. However, access control tasks can be burdensome, resulting in insecure accounts, errors, and a lack of audit documentation.

-
SolarWinds Access Rights Manager (ARM) is designed to assist IT and security admins to quickly and easily provision, de-provision, manage, and audit user access rights to systems, data, and files, so they can help protect their organizations from the potential risks of data loss and data breaches. By analyzing user authorizations and access permission, admins get a visualization of who has access to what and when they accessed it, and with a few clicks, customized reports can be generated to demonstrate compliance with most regulatory requirements.
-
SolarWinds ARM automates access rights management, analysis, and enforcement by identifying insecure accounts while providing audit trails. It enhances security by monitoring, analyzing, and auditing Active Directory®, Azure AD, Exchange, SharePoint, OneDrive, and file servers to see what changes have been made, by whom, and when those changes occurred.
-
ARM helps prevent data leaks and unauthorized changes to sensitive files and data through the visualization of permissions on file servers, and simplifies Exchange monitoring and auditing to help prevent data breaches by tracking changes. ARM helps improve compliance and detect unauthorized changes.
-
SolarWinds ARM is being widely adopted across DoD and civilian government agencies. It’s available on the U.S. General Services Administration (GSA) Schedule and other government contract vehicles.
- (SolarWinds Access Rights Manager (ARM) helps IT and Security Admins meet compliance requirements with centralized provisioning, de-provisioning, management, and audit of user permissions and access to systems, data, and files while protecting their organizations from internal security breaches. Courtesy of SolarWinds and YouTube.)
-
SolarWinds ARM enhances security by monitoring, analyzing, and auditing Active Directory®, Azure AD, Exchange™, SharePoint, OneDrive, and file servers to see what changes have been made, by whom, and when those changes occurred, and customized reports can be generated to demonstrate compliance with most regulatory requirements.
-
The solution also provisions and deprovisions users using role-specific templates to help assure conformity of access privilege delegation in alignment with security policies.
-
ARM helps prevent data leaks and unauthorized changes to sensitive files and data by visualizing permissions on file servers.
-
SolarWinds ARM reduces IT workload through a web-based self-service portal puts access rights of data in the hands of data owners instead of admins.
SolarWinds Worldwide (Third of Three)
Best Security Incident & Event Management Solution (SIEM)
SolarWinds Security Event Manager
-
Threats to IT networks continue to accelerate and evolve. While enterprising hackers from external sources test the robustness of network security parameters, internal threats from careless and malicious insiders remain a major and ongoing concern.

-
It’s critical agencies take steps to combat these threats—and SolarWinds® Security Event Manager (SEM) is a powerful weapon. This comprehensive SIEM solution delivers dynamic, real-time log collection and analysis for immediate and actionable threat intelligence and can capture and analyze log data in real-time from multiple sources and specific incidents, allowing users to quickly identify and remediate threats, uncover policy violations, and resolve vital network issues.
-
In addition, SolarWinds SEM features other innovations not seen in traditional SIEM solutions, including in-memory correlation for immediate threat detection and remediation; USB Defender® technology to help identify rogue devices and enforce USB policies; and unique IT search capabilities for better remediation and audit reporting. SEM includes support for single sign-on and improved management.
(See a brief overview of the capabilities of SolarWinds Security Event Manager (formerly Log & Event Manager), and how you can use the SIEM tool to detect threats, quickly respond to cyber incidents, and report compliance from a consolidated interface. Courtesy of SolarWinds and YouTube.)
-
Like all SolarWinds software, SEM is built to scale and can support IT environments of all sizes. It employs a node-based license model that allows users to stay within their planned budgets as they deploy and expand their IT infrastructures across multiple data centers and geographies. A new Workstation Edition license makes monitoring logs from Windows workstations more affordable than ever.
-
SolarWinds SEM is used by nearly every U.S. federal civilian agency, DoD branch, and intelligence agency. It’s available on the U.S. General Services Administration (GSA) Schedule and other contract vehicles.
-
*SolarWinds has now been officially recognized with Multiple Award Wins for a total of Seven Consecutive Years – 2022, 2021, 2020, 2019, 2018, 2017, and 2016. Thank you for your continued confidence in AST!