
Guest OpEd by Danna Bethlehem Coronel, Director, Product Marketing, Identity & Access Management (IAM) at Thales
The days of network perimeter security are long gone. With corporate boundaries vanishing, the real battle to protect the network has moved to the realm of identity and access management (IAM).
Network perimeter security has lost importance because organizations have moved to the cloud and are rapidly adding apps and services to support their employees and customers in an always-connected world.
While cloud-based environments have turned businesses into more agile and efficient organizations, they have also exposed them to considerable risk.
Identities: valuable asset and lucrative target
Without robust access and authentication controls, it is easy to lose visibility into the thousands of identities operating within a modern company’s network.
Each user can have multiple identities to access an array of systems, while machines, non-human entities like apps and services, also hold various digital identities required for accessing data.
Digital identities have become a valuable asset for businesses, but they are also a lucrative target for cybercriminals. Most advanced attacks are actively leveraging compromised or stolen account credentials to circumvent security.
However, businesses are not effectively protecting these digital identities.
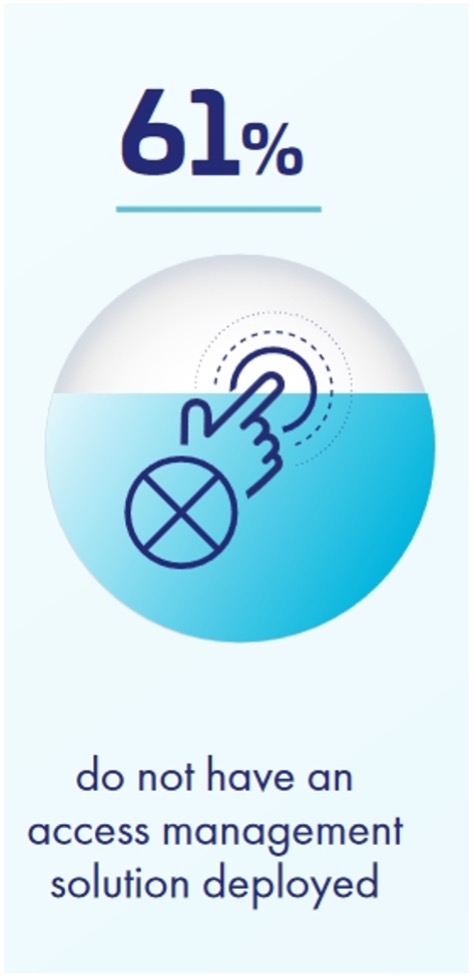
The Thales Access Management Index 2021 report indicates that 61% of the surveyed organizations do not have in place an access management solution, making identities an easy target for attackers.
Many of the most recent high-profile breaches, like the SolarWinds attack, used compromised identities and elevated privileges to bypass cybersecurity defenses.
Now is the time for organizations to invest in an IAM solution. The technology behind access management and authentication is evolving and has matured enough to address all emerging threats and reduce overall business risks.
All organizations have to do is select the IAM tool that fits their business and risk environment.
(Thrive with simple, secure access to all your apps, from anywhere with SafeNet Trusted Access. With SafeNet Trusted Access, you can accelerate organizational growth, minimize risks, and modernize your IT infrastructure with a modern authentication and access management platform. Let Thales help you centralize access management and authentication, reduce costs and avoid IT vendor lock-in for access to cloud and hybrid environments. Courtesy of Thales Cloud Security and YouTube.)
What are IAM tools?
IAM tools identify and validate users, applications, and devices. They then grant the appropriate authorities and permissions.
IAM tools are the backbone of modern cybersecurity, especially in the cloud. In fact, IAM is the key ingredient for zero-trust security. Zero trust cannot function without solid identity and access management.
Identity has become the new perimeter security because no matter where an asset is, it takes an identity with the proper permissions to access it.
Strong IAM tools can keep assets safe regardless of how many clouds make up an organization’s network or how many identities it manages.
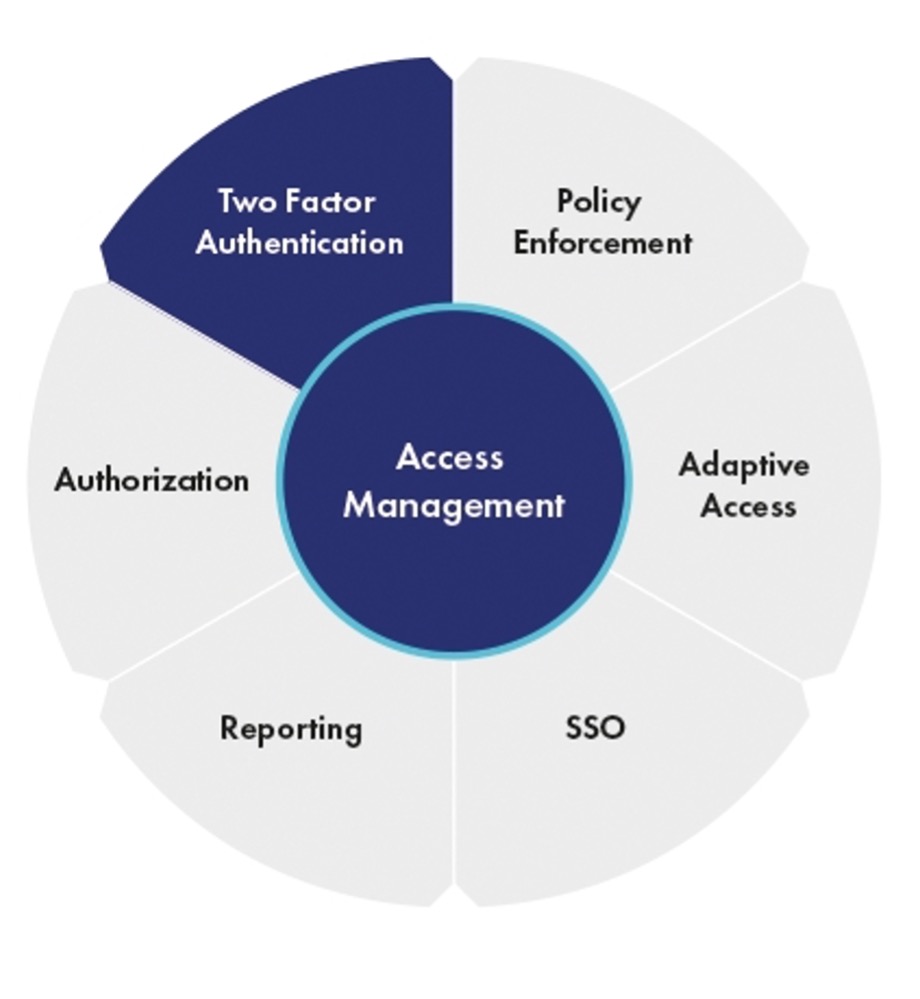
IAM tools control the following aspects of a connection request:
Access
-
Determine if the user trying to log in is allowed to do so.
Permission
-
If access is granted, they are assigned an authority that determines what part of a network, which application, or what database they will be allowed to access.
Roles
-
The user account will be assigned a specific role that will determine what they will be able to do with the allowed asset: read, write, execute, or all.
Monitoring
-
Finally, the tools monitor and report on account activities to make sure no one is misusing their privileges or abusing the rights they have been granted.
(Do you have secure access to all of your cloud services? According to the 2020 Access Management Index, 58% of IT and security professionals believe cloud apps are the biggest targets for cyberattacks. Courtesy of Thales Cloud Security and YouTube.)
What to look for in an IAM tool
A robust IAM tool should be able to answer three questions:
-
Who is allowed access?
-
Which digital identity should have access to what?
-
How are they proving the validity of credentials to access an account?
An IAM tool should also offer the following features:
-
Cross-application and cross-network authentication
-
Enforce appropriate access policies with ease
-
Ease of implementation and administration
-
Integration with all systems on a network including legacy ones
-
Capability to support ‘remote IT’ scenarios such as remote onboarding of new users, remote provisioning and remote monitoring
-
Help achieve compliance with regulations like HIPAA and GDPR which require strict security rules
Criteria for selecting an IAM tool
With so many vendors offering a variety of solutions, selecting the one that will help your organization to protect identities can be a tedious exercise.
The following criteria may make your life easier.
-
Interface with Active Directory or LDAP implementations to improve user account management – many organizations are still reliant on legacy Microsoft-based applications and servers.
-
Integrate Single Sign-On (SSO) with adaptive and Multi-Factor Authentication (MFA) – Integrating MFA with SSO enables you to define stronger security policies for accessing systems that are very sensitive.
-
Complexity – how normal, day-to-day activities function with these tools, such as registering new tokens and new users, setting up protection for a new application, modifying security policies, and figuring out why a user can’t log into corporate applications.
-
Reporting – offer the ability to schedule specific reports and have real-time monitoring for alerts and other activities.
-
Adaptive authentication – contextual, risk-based authentication based on various attributes, such as time, location, role, and sensitivity of data.
-
Mobile support – as more workers use their mobile devices for their computing needs, IAM tools should support logins from mobile devices and web-based applications. Enterprises may also want a way to store multiple factors on users’ phones and tablets, so they don’t have to carry traditional, hardware-based key fob tokens.
-
Multiple token support – support a wide collection of hardware and software tokens as additional authentication factors. This gives more flexibility to be used in a variety of authentication situations.
-
FIDO support – FIDO offers a passwordless, MFA authentication experience and removes the need to store the digital identity on any site.
How Thales benefits our customers
Thales SafeNet Trusted Access is a cloud-based access management solution that makes it easy to manage access to both cloud services and enterprise applications with an integrated platform combining single sign-on, multi-factor authentication, and scenario-based access policies.
(Learn More about SafeNet Trusted Access – Securing cloud access with contextual policies. Courtesy of Thales Cloud Security and YouTube.)
SafeNet Trusted Access simplifies user access to cloud services, streamlines cloud identity management, and helps eliminate password hassles for IT and users while providing a single pane view of access events across your app estate to ensure that the right user has access to the right application at the right level of trust.
About the Author
As the Director of Product Marketing and Identity & Access Management (IAM) at Thales, Danna Bethlehem Coronel leads product marketing for the company’s IAM product line.
This includes the articulation of the company’s product strategy and messaging, campaign development, through leadership, and PR, partner marketing, analyst relations, and sales enablement.
Related Technologies…
Strata Identity Takes Platinum in 2021 ‘ASTORS’ for Best Cloud Identity Orchestration Solution

American Security Today’s Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program, and now in its Sixth Year, continues to recognize industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management and Response, Law Enforcement, First Responders, as well as federal, state and municipal government agencies in the acknowledgment of their outstanding efforts to Keep our Nation Secure.
Strata Identity

-
Best Cloud Identity Orchestration Solution
-
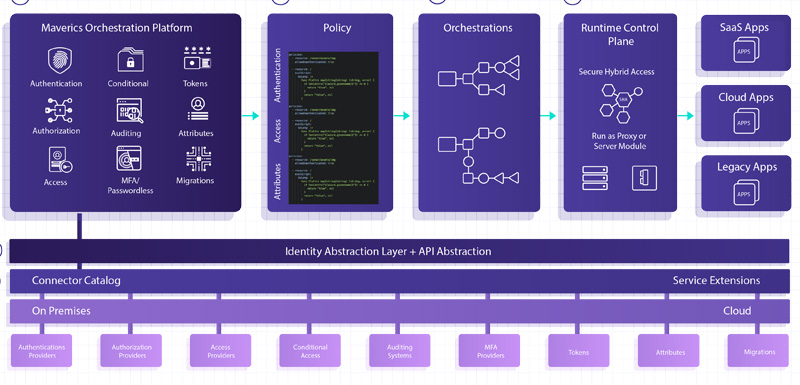
Maverics Identity Orchestration Platform
-
The cloud has created an identity management crisis, with companies being forced to simultaneously manage on-premises and several different cloud provider systems to enforce security policies.
-
Strata’s Maverics Identity Orchestration Platform™ creates an identity control plane that enables customers to enforce a global access policy at scale across multiple distributed clouds and on-premises systems.
-
It is not another Single-Sign-On (SSO), directory, or authentication solution, it is the first distributed, standards-based identity orchestration solution that automates multi-cloud and hybrid cloud identity management, and represents a brand new approach to distributed identity management.
-
Maverics eliminates the need for companies to replace their existing identity systems or rewrite apps in order to make them compatible with new identity systems, which avoids years of integration and migration time and costs.
-
Strata’s ‘migration factory’ approach enables organizations to “lift-and-shift” apps, whether it’s one or one thousand (or more), quickly to the Cloud.
-
By design, Maverics connects to any identity system, transparently migrates users and credentials, replicates and synchronizes policies and configurations, and abstracts authentication and session management.
(With Strata’s Maverics Identity Orchestrator™, enterprise identity management is simplified as you can migrate and modernize your identity systems without painful application rewrites. You’ll save hundreds of hours, and millions of dollars on your upcoming project. Courtesy of Strata Identity and YouTube.)
The Annual ‘ASTORS’ Awards highlights the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition and keep our Nation safe – one facility, street, and city at a time.

AST Honors Thomas Richardson, FDNY Chief of Department; Dr. Kathleen Kiernan, President of NEC National Security Systems; and Richard Blatus, FDNY Assistant Chief of Operations, at the 2021 ‘ASTORS’ Awards Luncheon at ISC East.
The United States was forever changed 20 years ago on September 11th, and we were fortunate to have many of those who responded to those horrific tragedies join us at the 2021 ‘ASTORS’ Awards Luncheon.
In the days that followed 9/11, the critical needs of protecting our country catapulted us into new and innovative ways to secure our homeland – which is how many of the agencies and enterprise organizations that are today ‘ASTORS’ Awards Champions, came into being.

Our keynote speaker featured a moving and informative address from TSA Administrator and Vice-Admiral of the United States Coast Guard (Ret), David Pekoske; to our attendees who traveled from across the United States and abroad, on the strategic priorities of the 64,000 member TSA workforce in securing the transportation system, enabling safe, and in many cases, contactless travel.

Legendary Police Commissioner William Bratton of the New York Police Department, the Boston Police Department, and former Chief of the Los Angeles Police Department was also live at the event, meeting with attendees and signing copies of his latest work ‘The Profession: A Memoir of Community, Race, and the Arc of Policing in America,’ courtesy of the generosity of our 2021 ‘ASTORS’ Awards Premier Sponsors.
The 2021 ‘ASTORS’ Awards Program was Proudly Sponsored by AMAROK, Fortior Solutions and SIMS Software, along with Returning Premier Sponsors ATI Systems, Attivo Networks, Automatic Systems, and Reed Exhibitions.
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast-changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace with over 75,000 readers at the Federal, State, and local levels of government as well as firms allied to the government.
American Security Today brings forward a fresh compelling look and read with our customized digital publications that hold readers’ eyes throughout the story with cutting-edge editorial that provides solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

AST Digital Publications are distributed to over 75,000 qualified government and homeland security professionals, in federal, state, local, and private security sectors.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches both Private & Public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture, and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from Government at the federal, state, and local level as well as from private firms allied to the government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website, and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants & Dams, Bridges & Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting & Concert Stadiums, our Nation’s Schools & Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
(See just a few highlights of American Security Today’s 2021 ‘ASTORS’ Awards Presentation Luncheon at ISC East. Courtesy of My Pristine Images and Vimeo.)
To learn more about ‘ASTORS’ Homeland Security Award Winners solutions, be on the lookout for the 2021 ‘ASTORS’ CHAMPIONS Edition Fully Interactive Magazine – the Best Products of 2021 ‘A Year in Review’.
The Annual CHAMPIONS edition includes a review of Annual ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firm’s products and services, including video interviews and more.

It will serve as your Go-To Source throughout the year for ‘The Best of 2021 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and/or organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection, and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware and Networking Security – Just to name a few), the 2021 ‘ASTORS’ CHAMPIONS EDITION will have what you need to Detect, Delay, Respond to, and Mitigate today’s real-time threats in our constantly evolving security landscape.
It will also include featured guest editorial pieces from some of the security industry’s most respected leaders, and recognized firms in the 2021 ‘ASTORS’ Awards Program.
-
For a complete list of 2021 ‘ASTORS’ Award Winners, begin HERE.
For more information on All Things American Security Today, as well as the 2021 ‘ASTORS’ Awards Program, please contact Michael Madsen, AST Publisher at mmadsen@americansecuritytoday.com.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos





















