
American Security Today’s ‘ASTORS’ Homeland Security Awards program is in its Fifth Year and continues to recognize the Outstanding Innovations of top firms and agencies in the Homeland Security and Public Safety fields.
2020 has been a very challenging year for everyone due to the COVID-19 pandemic and the much heralded AST ‘ASTORS’ Awards Winners Presentations and exclusive Luncheon at the Jacob Javits Center in NYC has been canceled and rescheduled for 2021 due to the virus.

However, the 2020 ‘ASTORS’ Homeland Security Awards Program was again a huge success and many new categories were added including a section for COVID-19 Detection and Innovation.
‘ASTORS’ Awards Winners were selected by our American Security Today Panel of Judges, and the ‘ASTORS’ Homeland Security Awards are presented at the Platinum, Gold, Silver and Bronze levels.
Why the 2020 ‘ASTORS’ Homeland Security Awards Program?
American Security Today’s comprehensive Annual Homeland Security Awards Program is organized to recognize the most distinguished vendors of physical, IT, port security, law enforcement, and first responders, in acknowledgment of their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.’
 American Security Today would like to express our deep gratitude to our 2020 ‘ASTORS’ Awards Premier Sponsors for their continued support.
American Security Today would like to express our deep gratitude to our 2020 ‘ASTORS’ Awards Premier Sponsors for their continued support.
ATI Systems, Attivo Networks, Automatic Systems, X.Labs and Reed Exhibitions, every one a returning Sponsor from years past whose products and services will be featured in the 2020 CHAMPIONS EDITION.
The Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program highlighting the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition, and keep our Nation safe – one facility, street, and city at a time.
 90% of ‘ASTORS’ Award Winners return to compete in the Annual ‘ASTORS‘ Homeland Security Awards Program, and 100% of ‘ASTORS’ Sponsors have returned year to year to reap the benefits of their participation in the industry’s largest and most comprehensive Annual Awards Program.
90% of ‘ASTORS’ Award Winners return to compete in the Annual ‘ASTORS‘ Homeland Security Awards Program, and 100% of ‘ASTORS’ Sponsors have returned year to year to reap the benefits of their participation in the industry’s largest and most comprehensive Annual Awards Program.
And without further ado, American Security Today is proud to introduce the 2020 ‘ASTORS’ Homeland Security Awards Winners.
1st Detect Corporation
Best CBRNE Detection System
-
Tracer 1000
-
As terrorists continue to find new ways to threaten global aviation security, the TRACER 1000, with its virtually unlimited and instantly updatable threat library, enables aviation security operators to stay ahead of the ever evolving explosive and narcotic threats.

-
The TRACER 1000™ is the first ECAC certified mass spectrometer trace (ppb/ng) analyzer used to detect explosives, narcotics and chemical warfare agents (CWAs) serving the worldwide security needs for airports, ports of entry, border crossings, secure buildings, public events, and the military to significantly improve passenger flow and safety.
-
The TRACER 1000 is serving the worldwide security needs for airports, ports of entry, border crossings, secure buildings, public events, and the military.
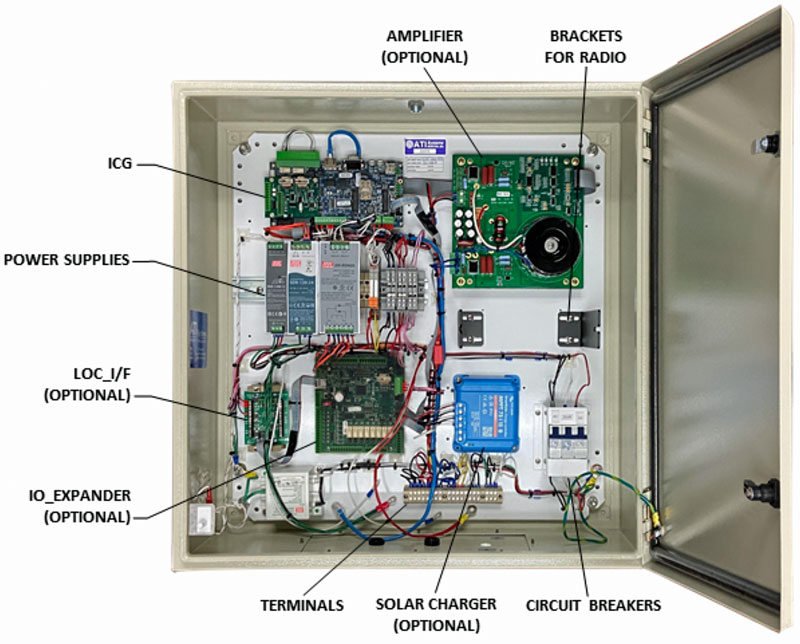
Acoustic Technology Inc. (ATI Systems)
Best Mass Notification System – Hardware
-
The Universal Indoor Speaker Unit
-
When an emergency strikes, effective dissemination of information in a timely manner can be critical.
-
ATI’s new Universal Indoor Speaker Unit (UNI-ISU) provides more flexible, intelligent end points to customers’ critical indoor Mass Notification requirements.
-
Through acoustic design and modeling, the company provide’s optimal sound coverage and superior voice intelligibility for both outdoor and indoor areas to ensure the safety of our clients worldwide.
(Learn More about ATI Systems, they design, manufacture, integrate, and install reliable emergency warning and mass notification systems, and have successfully deployed their innovative systems to colleges and universities, communities, ports, refineries, power plants, military bases all around the globe. Courtesy of AST and YouTube.)
*ATI Systems is also a Returning Premier Sponsor for the Fourth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a 2019, 2018 and 2017 ‘ASTORS’ Platinum Award Winner.
Advanced Detection Technology
Best Under Vehicle Surveillance System
-
LowCam® VI100 Under Vehicle Inspection System (UVIS)
-
Every day poses a new security challenge, whether that’s protecting a nation’s borders, facilities, monuments, airports, or its people, so to help minimize these threats, Advanced Detection Technology has introduced the first-ever, battery-powered UVIS for use during ad hoc situations.

-
The LowCam® VI100 “No Strings Attached” UVIS – touting no cables and no cords, not to mention a self-contained battery and military-grade equipment – lets you take this level of improvised security with you.
-
Portable, affordable, and all-inclusive, LowCam VI100 provides well-defined, ultra-high definition, and side-to-side daylight views, wirelessly displayed on a tablet with 15X zoom capabilities.
-
*Advanced Detection Technology was also recognized in the 2019, 2018, and 2017 ‘ASTORS’ Homeland Security Awards Program.
Aeroturn, LLC
 Best Pedestrian Entrance Control Solution
Best Pedestrian Entrance Control Solution
-
Hardened Zero-Maintenance Turnstiles
-
Aeroturn worked with a national footprint security integrator to provide the most robust turnstile solution available to be deployed in both regional and national GSA State & Federal Courthouses, where location must be customizable to match the increasing level of required security and life safety content and at the same time be part of an overall integrated national footprint solution.

-
With a performance specification of 10-million cycles, 5-year warranty, zero-maintenance mechanics, 100% Made in USA, 10-year MTBF, no preventative maintenance requirements, factory direct delivery & installations, 20-year minimum expected service life, Aeroturn was the only manufacturer who met GSA requirements.
-
The integrated turnstile solution has also been proven in GSA buildings since 2004 with a perfect track record as the basis for this most recent decision.
-
*Aeroturn LLC was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
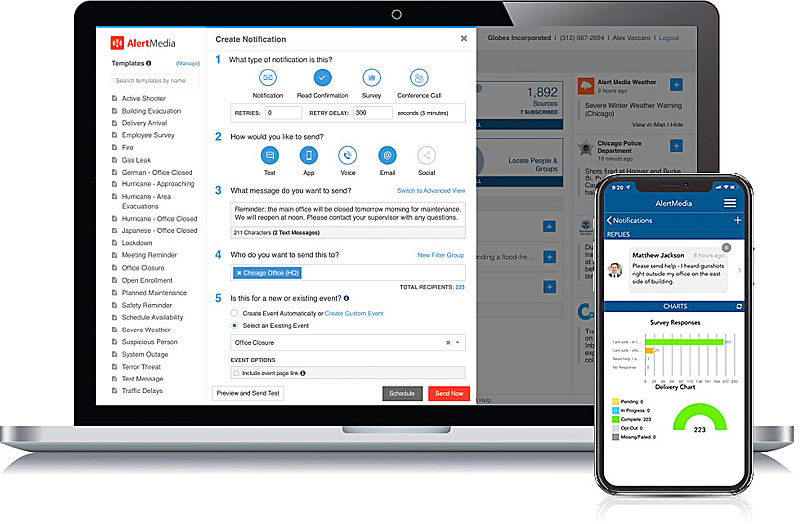
AlertMedia (First of Four)
 Best COVID-19 Communications Solution (Tie)
Best COVID-19 Communications Solution (Tie)
-
AlertMedia
-
AlertMedia helps organizations save lives and minimize loss by facilitating timely, accurate, and relevant communications during critical events, and exists to support organizations during emergencies like COVID-19.
-
The company immediately jumped into action, building capabilities into their product and creating resources that would help customers right away, such as the AlertMedia’s Global Threat Intelligence map featured the latest COVID-19 developments.
-
They integrated new data sources from Johns Hopkins to get the latest COVID case counts into the system, and also added a COVID-19 filter—so that organizations could filter out the sea of pandemic news to clearly see what other emergent threats could impact their organization.
(AlertMedia provides an easy-to-use interface, two-way messaging that works across all of your devices, and an unparalleled customer success team to help keep your people safe through all phases of an emergency. It’s the reason customers in 90+ countries have chosen AlertMedia to improve communications around any incident. Courtesy of AlertMedia and YouTube.)
AlertMedia (Second of Four)
Best Threat Intelligence Solution
-
AlertMedia Global Threat Intelligence
-
AlertMedia’s Global Threat Intelligence solution bridges the gap between emerging threats and critical communication for organizations all over the world.
-
Their Global Threat Intelligence offering distills breaking news into actionable, bite-sized summaries and provide organizations with software they can use to quickly take action and communicate with impacted employees.
-
AlertMedia’s Global Threat Intelligence offering provides their customers with the tools they need to shorten the time between threat identification and communication to change outcomes; from providing calculated impact radius, analyst summaries, implications on nearby subways or road closures, and actionable advice for people who might be in the area.
AlertMedia (Third of Four)
Best Handheld Mobile Device Solution
-
AlertMedia Mobile App
-
The AlertMedia Mobile App is an ideal solution for emergency mass notifications, business communication, operations and logistics.
-
The AlertMedia app monitors your communications, your people, and other critical events that may impact your business or people. Employers and subscribers can receive customized alerts from third-party sources that our team curates and delivers to you via the app.

-
For emergency mass notifications, business communication, and operations and logistics, the AlertMedia app provides an additional way to facilitate and manage two-way conversations with any-sized audience.
-
Users are able to easily manage incoming messages and responses to notifications from one streamlined view.
-
Organizations can give their communications subscribers access to the app, empowering people to signal for help with their location automatically attached, send in messages, or reply to notifications directly from the app.
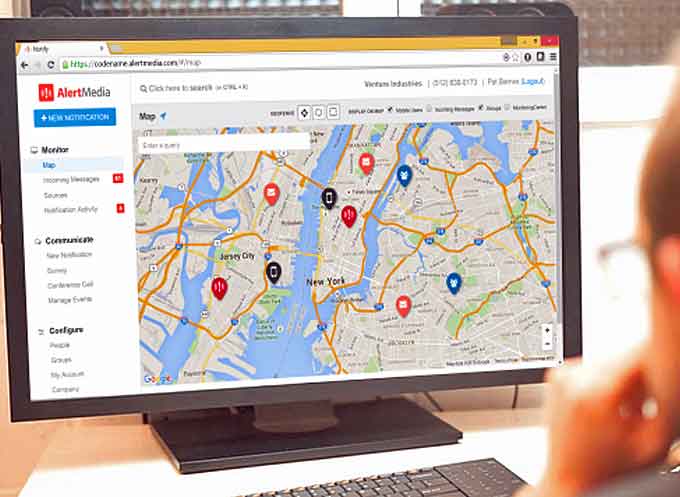
AlertMedia (Fourth of Four)
Best Mass Notification System – Software
-
AlertMedia Mass Notification
-
AlertMedia mass notification enterprise software enables your organization to ensure fast, reliable delivery of mass notifications to any audience, over any device, streamlining notifications and benefits from monitoring services that help improve your people’s safety during Critical Events.
-
AlertMedia provides an easy-to-use interface, two-way messaging that works across all of your devices, and an unparalleled customer success team to help keep your people safe through all phases of an emergency. It’s the reason customers in 90+ countries have chosen AlertMedia to improve communications around any incident.
-
*AlertMedia was also recognized with Multiple ‘ASTORS’ Awards in 2019, 2018 and a 2017 ‘ASTORS’ Homeland Security Awards Programs.
Allied Universal (First of Two)
Best Airport/Aviation Security Program
-
AUS – Miami International Airport (MIA)
-
MIA encompasses 3,230 acres of operational space with more than 100 airlines serving MIA to approximately 150 destinations around the globe.
-
Due to the expansive nature of MIA, the risk for insider threat is greatly increased due to the volume of individuals legitimately accessing the secure areas of MIA on a continual basis. The possibility of employees gaining access to secure areas, via non-secure areas, is a serious area of concern and needed to be addressed.

-
Additionally, the potential for the introduction of prohibited and/or illegal items via employee belongings can potentially be multiplied by the number of employees accessing the facility, at any given time. These vulnerabilities are known by adversaries (both domestic and foreign-influenced), and represent security challenges that are unique to aviation.
-
Allied Universal assumed the role of security partner and provider in 2008 and is the largest provider of internal security services at MIA and has established a sound working relationship with multiple MIA partners and takes pride in the agency’s reputation of professionalism, competence, and integrity of operations.
-
The MIA Aviation Security Program is recognized as being on the cutting edge of internal/employee screening, and a premier service provider in this market.
Allied Universal (Second of Two)
Best Maritime/Seaport Security Program
-
AUS – Port of Houston
-
Each year, more than 241 million tons of cargo move through the greater Port of Houston, carried by more than 8,200 vessels and 223,000 barges, and the port is consistently ranked 1st in the United States in foreign waterborne tonnage; 1st in U.S. imports; 1st in U.S. export tonnage and 2nd in the U.S. in total tonnage, as well as the nation’s leading breakbulk port, handling 41 percent of project cargo at Gulf Coast ports.

-
The expansive area of coverage includes over 25 miles of a perimeter fence line, 26 active security checkpoints, 39 TWIC controlled turnstiles, 8 facial recognition stations, and 4 traffic control points.
-
Being the largest bulk cargo facility in North America comes with several challenges and threats, and Allied Universal Professionals are the front line in deterring and detecting narcotics, counterfeit goods, and human trafficking.
-
Additionally, cybersecurity threats have grown exponentially over the past three years, and Allied Universal Security Professionals are responsible for managing the systems which provide clearance and access control for visitors and employees of the Port of Houston.
-
Allied Universal Programs have been recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
AM TRACE LLC (TRACE)
Best COVID-19 Emergency Response Solution
-
TRACE
-
TRACE, a public health firm that supports state and local health department efforts to face the massive burden of effectively managing the rapid spread of COVID-19 to help slow the spread.

-
Knowing where COVID-19 infections are concentrated and spreading is crucial for effective control and eradication efforts.
-
TRACE works with local leaders and communities to design and implement surveillance studies and programs that can inform and guide the concentration of limited resources to control the spread of COVID-19.
-
Helping people who may have been exposed to COVID-19 get tested as well as asking people to self-isolate if they have COVID-19 or self-quarantine if they are a close contact of someone with COVID19, prevents and mitigates the spread of COVID-19.
AMAROK
Best Perimeter Protection System
-
FORTIFEYE featuring The Electric Guard Dog Fence
-
AMAROK, formerly Electric Guard Dog, introduced FORTIFEYE in 2020 to enhance their physical perimeter security deterrent offering.

-
FORTIFEYE integrates electric security fencing, video surveillance, and video monitoring to create an ultimate crime prevention solution for commercial businesses and industrial sites.
-
FORTIFEYE has multiple layers of integrated security to protect your business, starting with the Electric Guard Dog Fence which delivers 7,000 volts to would-be thieves.
-
Cameras capture and record every second of activity in real time, from initial approach to flight and finishes with remote video monitoring to validate the breach and dispatch authorities.
-
*Electric Guard Dog, now AMAROK was also recognized in the 2019 ‘ASTORS’ Homeland Security Awards Program.
American Signal Corporation
 Best Mass Notification System
Best Mass Notification System
-
Campus Alert System
-
American Signal Corporation’s Campus Alert System combines the latest technology to keep individuals safe on health care, corporate and education campuses. Whether indoors or out, ASC’s Campus Alert System reaches individuals, notifying them of a variety of threats.

-
The integrated system includes ASC’s new Clarity siren, which is designed for exceptionally clear voice and tone alerts designed with the end user in mind.
-
Additionally, the system includes the customizable ASC AWARE desktop and connected device notification technology to warn individuals indoors. The technology interrupts computer stations, laptops, television monitors and other devices connected to the Internet, plus ASC Sentinel mobile device alerts, reach out individuals on their cell phones: this two-way system also allows individuals to directly alert authorities of dangerous or suspicious activity.

-
ASC’s advanced integrated and comprehensive Campus Alert System is a best option for health care, corporate or education campuses looking to keep individuals safe with an affordable and effective solution.
-
*American Signal Corporation was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
AmpliVox Sound Systems
Best Long Range Acoustic Hailing System
-
Mega Hailer Sound Packages
-
The AmpliVox Mega Hailer Mobile PA System is a 50-watt, totally wireless, highly intelligible, lightweight rechargeable battery powered loudspeaker system for general PA applications in areas that are not equipped with a PA.

-
The new 96-channel wireless receiver systematically changes channels for reduced channel interference.
-
The horizontally aligned horn broadcasts crystal clear voice announcements and reinforces sound to make it louder to audiences over large wide areas. Built-in Bluetooth® module allows you to wirelessly stream sound from any Bluetooth® capable device.
-
The system includes an AC power-cord for continuous operation when connected to a standard AC wall-outlet, and facilitates charging the included internal sealed lead acid (SLA) batteries. On a full charge, the system will operate up to ten hours on its SLA batteries’ power.
-
*AmpliVox was also recognized in the 2018, 2017 and 2016 ‘ASTORS’ Homeland Security Awards Programs.
Apricorn

Best Data Storage Security Solution
Even before the COVID-19 pandemic, remote and mobile working was on the rise.
-
As the global workforce shifted from office to home practically overnight due to COVID-19, it became abundantly clear that workers would use a variety of devices at their disposal outside of their corporate firewall.

-
To comply with corporate security policy and protect data in the remote workforce, Apricorn developed a portable, encrypted USB-C storage device that could securely store and move sensitive data regardless of work location, as well as serve as a safe data conduit between consumer devices (smartphones, tablets) and work hardware.
-
Apricorn’s Aegis Secure Key 3NCX, is the first and only encrypted hardware storage solution of its kind with a USB-C connector that works across the next generation of laptops, smartphone, tablets and hubs without the need for an A-to-C USB adapter.
-
*Apricorn was also recognized in the 2019, 2018 and 2016 ‘ASTORS’ Homeland Security Awards Programs.
Atlas Training & Consultancy
Best Homeland Security Education Program
-
The B.L.A.C.K. Philosophy
-
The B.L.A.C.K. (Behavior. Learning. Assertive. Contact. Knowledge) methodology was recently observed and monitored at a strategic level by the United States’ armed forces during a mission in Afghanistan.
-

taught during the toughest training of the Royal Dutch Army and at the Air Manoeuvre Brigade of the Royal Netherlands Army.
-
B.L.A.C.K, teaching includes in part, awareness of personal behavior effects and the appliance of this knowledge, to gain control of a critical situations. It is taught during the toughest training of the Royal Dutch Army and at the Air Manoeuvre Brigade of the Royal Netherlands Army.
-
*Atlas Training & Consultancy, (a CPK United Company) was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
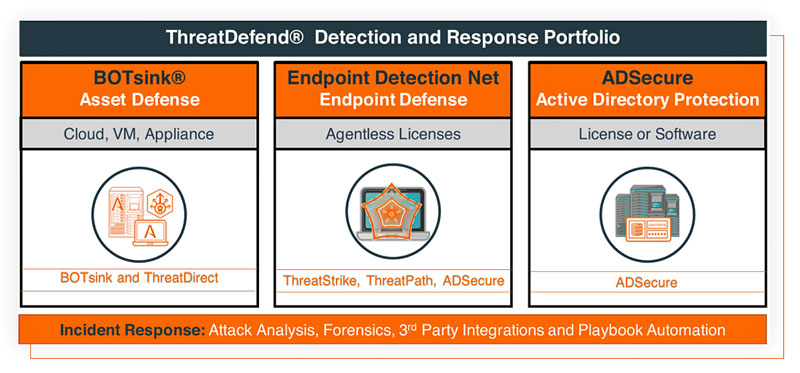
Attivo Networks (First of Three)
Best Intrusion Detection & Prevention Solution
-
Endpoint Detection Net (EDN)
-
The Attivo ThreatDefend® Platform EDN suite strengthens endpoint defensive capabilities by detecting and alerting on attack tactics that attackers use once they manage to compromise a system to spread to other devices on the network. The EDN suite helps reduce the cost of the attack and minimizes the personnel needed to respond to incidents.
-
Built on layered detection technology, the Attivo EDN offering makes every endpoint a decoy designed to disrupt an attacker’s ability to break out and further infiltrate the network.
-
It does this without requiring agents on the endpoint or causing disruption to regular network operations. Attivo used historical attack data and the MITRE ATT&CK framework as a way to understand the various methods attackers use to spread laterally from an endpoint.
-
The company then created a comprehensive solution designed to increase MITRE Security Assessment scores and to detect and stop unwanted intruders quickly.

-
The Endpoint Detection Net solution elevates security control by accurately raising alerts and taking proactive measures to derail attackers.
-
Of particular interest are the many EPP/EDR partners that the solution integrates with that can block an infected system to prevent further compromises, such as McAfee, Crowdstrike, Forescout, and many more. The platform adds visibility and detection to existing security solutions, and the partner integrations enhance and accelerate investigations and incident response.
-
The EDN solution also enhances current EPP and EDR solutions by adding coverage for attack tactics, techniques, and procedures that bypass existing controls. While EPP and EDR work to prevent a compromise, if the attacker does succeed, the EDN solution is there to keep the attacker from laterally moving while remaining undetected.
Attivo Networks (Second of Three)
Best IT Threat Intel Solution
-
ThreatDefend Platform with Informer UI
-
The Attivo Networks ThreatDefend® platform is a comprehensive detection solution for attack activities inside the network that offers in-network visibility and detection for on-premises, cloud, and remote locations across all attack surfaces and against any attack vector.
-
It detects lateral movement activity such as discovery and reconnaissance, port and service scans, data gathering from Active Directory, Man-in-the-Middle attacks, credential theft and reuse, and mapped share traversal.
-
The platform does this by deploying network, endpoint, application, data, and AD decoys and deceptive assets to create a fabric that misdirects and misinforms attackers.
-
The decoys record all attack activity while alerting security teams to the attack, reducing investigation and response times while capturing network, memory, and disk forensic data for intelligence development.
-
With the forensic capture of all attack data on the decoys, organizations gain robust data to develop threat intelligence for attacks that are targeting them specifically.
-
The platform includes analysis and filtering tools that correlate the attack data in chronological order and can display the attack in a graphical replay.
-
The ThreatDefend platform includes the Informer dashboard to accelerate investigations. The Informer dashboard correlates all information about a single in-network attack source and displays it in a simple, easy to use interface.

-
The readout includes the details about the system (such as system name, IP address, logged on user, etc.), a timeline view, and the events originating from the system in reverse chronological order that includes all event data.
-
Additionally, the dashboard shows first, second, and third-order hops from the system based on stored credentials and misconfigurations, and a means to initiate a partner integration to isolate the endpoint.
-
It even includes direct links to any forensic files and data captured by the decoys for quick downloads, such as packet capture files, malware analysis reports, memory forensics analysis, and the data and binary files themselves.
-
This dashboard aids in analysis and investigations by putting all the details the investigator would need in a single source, fully correlated, and ready to action.
-
Few providers can offer network, disk, and memory forensic capture at the time of the attack, coupled with the correlation of all event data and forensic evidence to create adversary intelligence to such a degree.
(Sophisticated attackers are targeting credentials to escalate privileges. See how Attivo Networks provides an innovative solution that finds, cleans and monitors exposed credentials to reduce attack surfaces. Courtesy of Attivo Networks and YouTube.)
Attivo Networks (Third of Three)
Best Privileged Access Security Solution
-
ADSecure
-
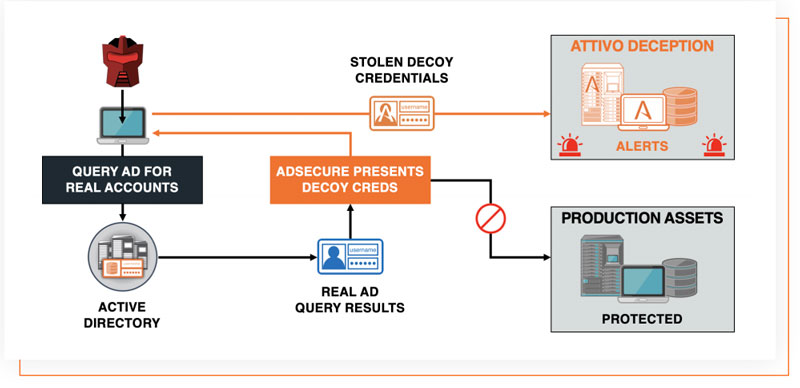
Inherently, there is no ideal way to secure Active Directory environments, however, the Attivo Networks ADSecure solution dramatically reduces risk by hiding real AD objects and returning fake data to an attacker, which, if used, diverts the attacker to a decoy environment.
-
When deployed as part of the Attivo Networks ThreatDefend® Platform, defenders can gather adversary intelligence as the solution redirects queries and activities into the decoy environment. They now gain the ability to collect and take action on company-centric threat intelligence.
-
The ADSecure solution is truly a revolutionary way to protect against successful Active Directory attacks, without interfering with production AD operations, requiring logs, or complex rights and permissions management.
-
Additionally, one of the best things about deployment is that one doesn’t have to touch or alter production Active Directory controllers for it to work. Implementation is exceptionally straightforward, with the majority of the setup time spent on strategy for how in-depth one wants to make the fake ADSecure environment and information.
ADSecure can be deployed as a standalone product or easily installed as an add-on license to the ThreatDefend Platform.
-
This method of prevention is an invaluable deterrent as attackers can no longer trust what they see or the tools they rely on.

*Attivo Networks is also a Returning Premier Sponsor of the 2020 ‘ASTORS’ Homeland Security Awards Program, and a Multi-Platinum Award Winner in the 2019, 2018 and 2017 ‘ASTORS’ Awards Program.
Authomize
Best Cloud Identity and Access Management
-
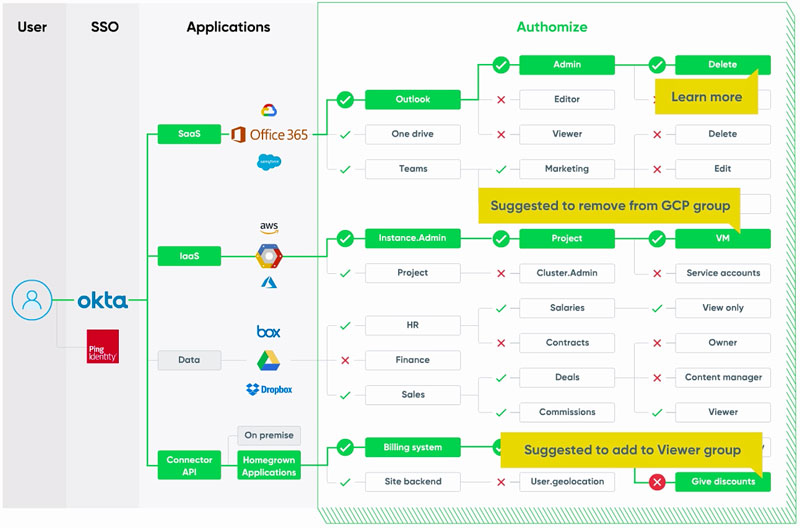
Authomize Automated Authorization Management Solution
-
Authomize enables organizations to manage and secure complex and vastly different applications across hybrid environments with an intelligent Prescriptive Analytics engine that helps IT and security teams flawlessly automate operations around authorizations to prevent permission sprawl, maximize productivity, and simplify identity lifecycle management.
-
The company’s unique technology grants unparalleled transparency into the various application authorization “layers” across hybrid environments.
-
Using proprietary prescriptive analytics engine, Authomize learns the correlation between permissions, identities, and usage to deliver data-backed intelligent suggestions and identify the root cause of access and permissions issues.
-
Teams can make informed authorization decisions based on the intelligence provided or automate the authorization management lifecycle process, minimizing IT strain and optimizing security posture.
-
Authomize’s targeted market is companies with 2,000 employees and more cross-industries, with a current focus on North America and The UK and is suitable to IAM leaders and CIOS and CIOs.
Automatic Systems (First of Two)
Best Contactless Pedestrian Entrance Control Turnstile
-
SlimLane EPW Touchless
-
Automatic Systems continues to evolve their award winning SlimLane swing optical barrier turnstiles.
-
With the current social distancing and contactless requirements, this SlimLane can offer a fully touchless solution while protecting its users.

-
The hand “wave” and facial recognition readers were easily integrated and offer a fully contactless solution while the UL 2593 Certified SlimLane offers a highly reliable (10 Million MCBF) physical access control turnstile.
-
With its 5 year standard warranty, and infinite customizations, the SlimLane continues to be a perfect solution for lobby entrances.
-
Selected as the “standard” for multiple financial institutions, we are confident that the SlimLane will continue to answer any pedestrian access control requirements for your years to come.
(Automatic Systems SlimLane EPW Touchless swing glass turnstiles offer custom integration provides an innovative and effective solution with multiple biometric authentications during continuous movement. Courtesy of Automatic Systems and YouTube.)
Automatic Systems (Second of Two)
Best Vehicle Security Entrance control Gate
-
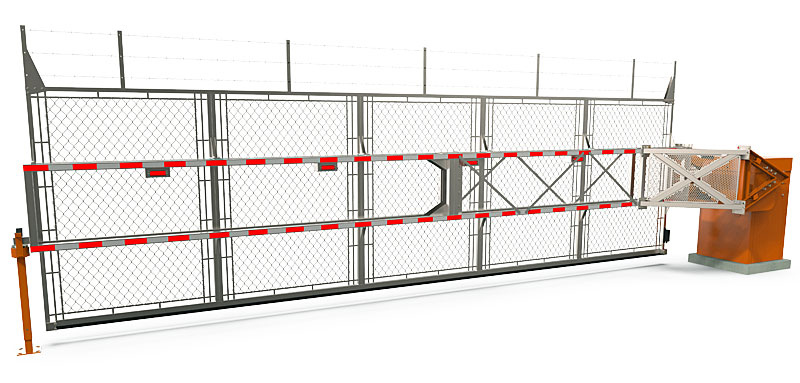
BLG 77 ETL Rising Fenced Barrier Gate
-
Automatic Systems newly redesigned BLG 77 is now ETL Listed to UL325 specifications which requires that, after sensing an obstruction, reversing must begin within two seconds to ensure user safety.

-
BLG 77 are full height automatic gates recognized for their reliability and low cost of ownership, while providing long-term access control to a facility’s perimeter.
-
One of the fastest full height automatic gates on the market, it is capable of opening a passage width of 20 feet in seven seconds and is an ideal solution for high traffic applications that require strict entry control.
-
These barriers are used at sensitive sites requiring a high level of security such as ports, airports, logistics companies, and military installations.
-
Recognized for its reliability and low cost of ownership, the BLG77 is a great investment for the long term access control of your perimeter.
 *Automatic Systems is also a Returning Premier Sponsor for the Fourth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a Platinum-Award Winner in their Fifth Annual ‘ASTORS’ Awards Program.
*Automatic Systems is also a Returning Premier Sponsor for the Fourth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a Platinum-Award Winner in their Fifth Annual ‘ASTORS’ Awards Program.
Axis Communications (First of Three)
Best Body Worn Video Solution
-
Axis Body Worn Solution
-
Recognizing the benefits of body worn cameras in capturing evidence, deterring criminal behavior and training officers within law enforcement and the private security sector, Axis Communications introduced the flexible Axis Body Worn System.
-
With an open architecture, the solution allows customers to seamlessly integrate their existing third-party Video Management Systems (VMS) and Evidence Management Systems (EMS), on premise or in the cloud, ensuring prior investments are not wasted.

-
AXIS W100 Body Worn Camera captures video up to 1080p @30fps and features wide dynamic range technology (WDR), producing high-resolution images even in the most challenging light conditions.
-
Equipped with numerous built-in features including dual microphones, a GPS/GNSS receiver for location tracking, Bluetooth Low Energy 4.1 capabilities, IEEE 802.11 b/g/n and a 6-axis gyro and accelerometer, the system offers users unmatched benefits.
-
Operating with an internal storage capacity of 64GB and a battery life of 12 to 17 hours, depending on HD resolution, the camera is designed to outlast the average field officer’s shift, and with dual microphones, the camera offers high quality of speech and reduced noise.
-
The Axis body worn system offers a reliable option for law enforcement and security personnel in wearable surveillance, leveraging the quality & innovation of Axis to extend existing security systems.
Axis Communications (Second of Three)
Best IP Video Surveillance Solution (Tie)
-
AXIS Q1615-LE Mk III Network Camera
-
The AXIS Q1615-LE Mk III Network Camera is a top-of-the-line outdoor-ready camera that is ideal for city surveillance, transportation and industrial applications.
-
With 120 fps in HDTV 1080p, the network camera offers exceptional video quality while capturing clear, detailed images of fast-moving objects and/or people regardless of challenging light conditions.

-
The camera is ideal for installation on the side of roadways or in poorly lit industrial lots, and is equipped with Axis Lightfinder 2.0 and Axis Forensic WDR, which produces high quality images with excellent color, detail and sharpness, even when images are recorded in dark settings to ensure reliable surveillance up to 196 feet or more in pitch darkness.
-
AXIS Q1615-LE Mk III is equipped with advanced security functionality to safeguard the system and prevent unauthorized access.
-
With deep learning on the edge, the AXIS Q1615-LE Mk III platform is designed for third-party applications and allows analytics to run directly on AXIS Q1516-LE Mk III (on the edge), allowing for a faster, more scalable system.
-
With this ability to process powerful analytics, the camera is capable of edge-based automatic incident detection, counting and anomaly detection, among others functions.
Axis Communications (Third of Three)
Best IP Video Surveillance Solution (Tie)
-
AXIS Q1798-LE Network Camera
-
The AXIS Q1798-LE Network Camera offers a large-scale surveillance solution for wide, spacious scenes. With 4x zoom and electronic image stabilization (EIS), ensuring stable video despite vibration, the camera is ideal for open spaces such as sport stadiums, amphitheaters, parks, and other cultural gathering centers, to name a few.

-
To combat difficult and inconsistent lighting at these locations, the AXIS Q1798-LE is equipped with an ultra light-sensitive large format 4/3” image sensor that offers 10 MP resolution at up to 20 fps and 4K resolution at up to 30 fps, enabling quality forensic images with high pixel density.
-
The camera incorporates a Canon lens with a focal length of 12 – 48 mm offering a maximum horizontal field of view of 90° and auto-focus to allow operators to tailor the scene to their needs real-time during an incident.
-
Often deployed in outdoor areas, the AXIS Q1798-LE has IP66, IP67and IK10 ratings, and operates in temperatures ranging from -40 °F to 140 °F, plus with shock detection, corridor format with auto-rotation and barrel distortion correction, the camera can guarantee great image quality despite the harshest of conditions.
-
*Axis Communications, a Canon Company has been recognized in the 2018 and 2017 ‘ASTORS’ Awards Programs respectively.
BeyondTrust
Best Privileged Access Security Solution
-
BeyondTrust Universal Privilege Mgmt-Integrated Solution
-
According to the White House, strengthening the cybersecurity of federal networks, systems, and data is one of the most important challenges the United States faces as a nation.

-
Controlling, monitoring, and auditing privileged access is extremely important to accomplish this mission by mitigating the risks posed by insider threats, preventing data breaches, and meeting compliance requirements.
-
With BeyondTrust agencies can keep pace, cost-effectively reduce IT security risk, confidently embrace innovation, and simplify the path to meet federal compliance mandates.
-
BeyondTrust’s Universal Privilege Management approach consists of three privilege pillars: Privileged Password Management, Endpoint Privilege Management, and Secure Remote Access.
-
*BeyondTrust was also recognized in the 2019, 2018 and 2016 ‘ASTORS’ Awards Programs.
BriefCam
Best Video Analytics Solution
-
BriefCam Video Content Analytics Platform
-
The BriefCam Video Content Analytics Platform is a comprehensive and extensible platform that makes video searchable, actionable and quantifiable based on state-of-the-art machine learning techniques.

-
Analyzing surveillance video, the platform detects, extracts, identifies, classifies and indexes the objects that appear and empowers organizations to leverage this data for accelerating investigations, improving situational awareness and deriving operational intelligence.
-
The BriefCam Video Content Analytics Platform is designed to meet the safety, security, and operational efficiency needs of today and tomorrow, helping diverse organizations accelerate investigations, attain situational awareness, and derive operational intelligence.
-
*BriefCam was also recognized in the 2019 and 2018 ‘ASTORS’ Awards Programs.
Brinqa (First of Two)
Best Cyber Security Risk Management
-
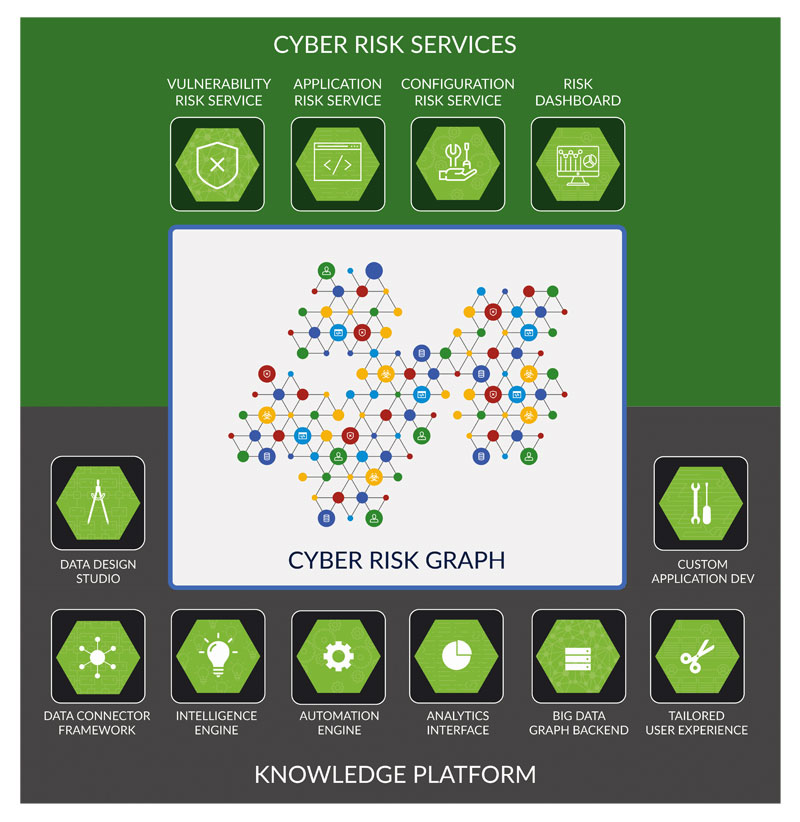
Brinqa Cyber Risk Services
-
Brinqa Cyber Risk Services empower organizations to implement a knowledge-driven approach to measure, prioritize, remediate and manage cyber risk.
-
Brinqa’s unique platform-based approach to cyber risk management leverages Knowledge Graph technology to incorporate all relevant information into a single source of truth – with complete coverage of infrastructure, apps, containers, IoT and OT.
-
Data from all sources is collated into an organization’s unique Cyber Risk Graph — a real-time representation of infrastructure and apps, delineation of interconnects between assets and to business services, and knowledge of overall cyber risk.
-
The solution provides a truly open data model and completely configurable risk scoring methodology.
-
Brinqa ecosystem spans over 100 integrated solutions, including vulnerability management, application security, asset discovery and management, cloud security, certificate management, configuration management, container security, database security, endpoint detection and response, IT service management, IAM (LDAP, PIM), network management, patch management, SIEM and threat intelligence.
Brinqa (Second of Two)
Best Vulnerability Management
-
Brinqa Vulnerability Risk Service
-
Brinqa Cyber Risk Services offers organizations the advantage of understanding and measuring true cyber risk, eliminate critical threats with prioritized cyber risk remediation, track key risk and performance indicators, monitor historical trends, and provide real-time insights to all cyber risk stakeholders.
-
Brinqa Cyber Risk Services enable these advantages through the ability to connect all context, security and threat intel into a single knowledge source that powers cyber risk management, provide an open model for prioritizing risk that sets common ground across teams for what matters and how to talk about it, and automate cyber risk management processes (including remediation) to achieve efficiencies required.

-
The resulting knowledge and common language transforms conversations, as security partners with business to provide IT and development with guidance and insights on proactively remediating vulnerabilities while delivering on technology initiatives.
-
The solution continuously measures risk, and proactively informs and engages stakeholders at different stages of the cyber risk management process – reducing response times and threat exposure windows, to ensure accountability and enable organizations to identify and address critical risks early, before they turn into costly breaches or compliance failures.
-
This enables organizations to establish company-wide cyber risk management programs that make cybersecurity tools and processes risk-aware, and unify view of risk across attack surfaces, because increasing numbers of attack surfaces mean less visibility/control.
-
*Brinqa was also recognized with Multi-Awards in the 2019 ‘ASTORS’ Award Program.
Canon U.S.A. (First of Two)
Best Email Security Solution
-
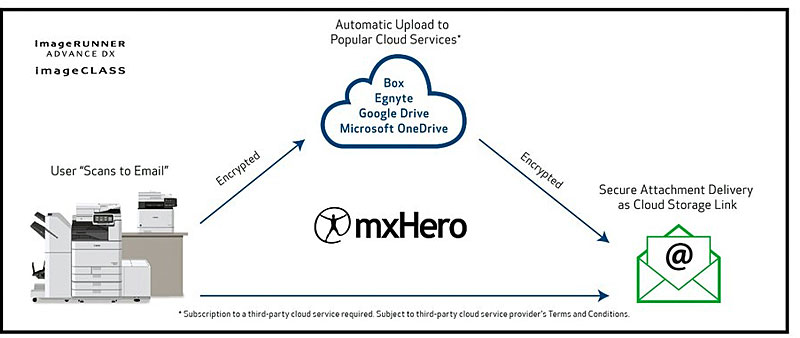
mxHero + Canon MFP
-
A cloud service for intelligent email management, mxHero™, can integrate onto a Canon multifunction printer (MFP) to help customers safely collaborate, govern, manage and share information.
-
By leveraging powerful storage platforms like Box (purchased separately), it can help create a cost-effective solution superior to single-purpose, document/email management products by replacing inbound and outbound email attachments with secure file links.
-
This solution is made to be compatible with most devices, helps to minimize end user effort, provides security measures to help control access to attachments (even when outside of the company) and can help screen malicious content.
-
Especially in today’s environment where solutions designed to help team’s collaborate while working in multiple places is important, services such as mxHero™ can help companies implement security features, govern and manage attachments while people aren’t able to physically connect face-to-face.
Canon U.S.A. (Second of Two)
Best Access Control & Authentication System
-
imageRUNNER ADVANCE DX Series + uniFLOW Online + Print via Cloud
-
The latest edition of the imageRUNNER ADVANCE platform, the imageRUNNER ADVANCE DX series with uniFLOW Online, is designed to help prepare its customers for the future of work through its simple, flexible design, advanced scanning, strong security, enhanced cloud features and user-friendly enhancements, like soft number keys similar to a smartphone or tablet.

-
To help limit unauthorized use of devices and keep valuable and confident information safe, uniFLOW requires users to identify themselves at the solution.
-
Its Secure Print functionality allows users to send sensitive documents to compatible network printers from desktops and compatible mobile devices. When using this function, regardless of how users submit a print job, documents only print when the user is physically standing at the device and authenticates.
-
*Canon U.S.A. was also recognized with Multi-Award Wins in the 2019, 2018 and 2017 ‘ASTORS’ Platinum Award Winner.
-
Additionally, Axis Communications, a Canon Company has been recognized in the 2019, 2018 and 2017 ‘ASTORS’ Awards Programs respectively.
Cellbusters
 Best Cell Phone Detection Solution
Best Cell Phone Detection Solution
-
Zone Protector
-
The Zone Protector™ from Cellbusters provides maximum protection for your environment by continuously scanning for cell phone and user selectable RF transmissions, and is far more sophisticated than a cell phone detector.
-
Comparable to a spectrum analyzer, the Zone Protector™ has the ability to scan user-definable frequency ranges along with the ability to alert, notify, control a third party device, or simply log as soon as it detects relevant transmission activity.

-
Precise frequency filtering technology, managed and controlled by a 32-bit microprocessor, enables the Zone Protector™ to deliver accurate detection with virtually zero false positives.
-
Once cellular or appropriate RF activity is detected, the Zone Protector™ can be set to activate a choice of alerting options or to silently log all detected activity.
-
Additionally, Cellbusters Zone Protector has now been updated to detect 5G phones, proving a leading edge in the market, and protects investment in this technology for years to come.
-
*Cellbusters was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Awards Programs.
CHERRY Americas
 Best Smart Card/Reader System
Best Smart Card/Reader System
-
CHERRY Smart Card Reader Solutions
-
CHERRY’s Smart Card Reader portfolio offers a complete system that provides a full set of integrated solutions for government security requirements.
-
The system, which includes the CHERRY SmartTerminal ST-1144, the CHERRY SECURE BOARD 1.0 and the KC 1000 allows users to obtain the right device or combination of devices to fulfill their all of their secure data entry requirements.

-
Today, it is impossible to imagine access control to sensitive areas without smart cards. CHERRY’s SmartTerminal ST-1144 with USB connection supports allows user to protect sensitive data in a straight-forward and reliable way.
-
Whether access controls, network logon, or chip card-based internet transactions – the SmartTerminal ST-1144 makes a valuable contribution to protecting sensitive data.
-
The Department of Defense has been relying on CHERRY’s smart card terminals for many years.
-
The SmartTerminal ST-1144 is durable and robust, and is designed for around 100,000 mating cycles.
-
SECURE BOARD 1.0: The go-to first step of data security is usually through the use of passwords – which are unfortunately all too easily forgotten, changed too rarely or accidentally disclosed to third parties due to negligence – with all the negative consequences.

-
This TAA Compliant security keyboard ensures maximum protection from “BadUSB” attacks via use of a secure mode, meaning that the authenticity of the device is verified on a certificate-based basis, and the key transmission is encrypted.
-
The SECURE BOARD 1.0 makes it impossible for hardware keyloggers to access sensitive access data and passwords by blocking the standard keyboard channel, “BadUSB” attacks are a thing of the past: USB sticks that log onto the system as a keyboard cannot inject uncontrolled entries and malicious codes.
-
The SECURE BOARD achieves higher security through two-factor authentication using a smart card. As a rule, the terminal with which the card is read out is required when processing smart card data.

-
KC 1000: The CHERRY KC 1000 keyboard features an integrated high-quality Smart Card terminal. These reliable and long-life keyboards feature an intelligent and ergonomic design, secure PIN entry, state-of-the art security technology and a USB connection.
-
These keyboards are known for long-lasting reliable operation – over 10 million key operations The KC 1000 keyboard is also a leading solution for government security applications.
-
*Cherry was also recognized in the 2017 and 2016 ‘ASTORS’ Awards Programs.
Cobwebs Technologies
 Best Web Intelligence Solution
Best Web Intelligence Solution
-
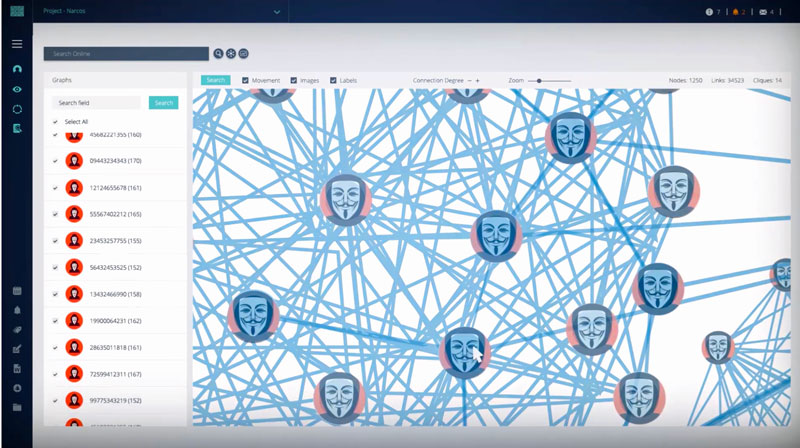
Cobwebs Technologies Web Intelligence Platform
-
Cobwebs Technologies is a specialized web intelligence company that supports national security agencies, law enforcement agencies, and corporate security departments to rapidly identify and locate malicious threat actors on the open, deep, and dark webs.
-
Cobwebs also points investigators in the direction of potential evidence, located on all layers of the web, that could be used to prosecute the threat actors. The platform not only identifies threat actors, it also identifies members and supporters of their network as well as the links that connect them.
-
Online criminal investigations on the open, dark and deep webs that may have taken days or weeks or even months to be conducted can now be successfully completed in mere minutes with little more than a few clicks of a mouse thanks to the Cobwebs platform.
-
The Cobwebs platform helps investigators identify and reconstruct profiles that link suspicious individuals to their contacts, and it reveals how they connect and come together as a group.
-
People outside of a group can also be identified so that investigators can determine if they should be conducting additional investigations.
Crotega, LLC
 Best Less Lethal Tactical Equipment
Best Less Lethal Tactical Equipment
-
REPULS
-
The patented REPULS is a new generation of chemical irritant unlike any other irritant on the market.
-
REPULS has a pungent odor and the same irritant qualities as pepper spray, OC, CS, which causes involuntary eye closure, highly irritating to the eyes, nose, nasal passages, throat, lungs, and skin.

-
REPULS can be mitigated with one bottle of water poured over the suspects head, and when the spray dries, the irritating agent is no longer active, unlike pepper spray, which remains in the environment until deep cleaned.
-
Arresting officer can deploy REPULS, approach and detain a subject without contamination.
-
Additionally, an arresting officer can bring the suspect to booking without the need for de-contamination of either the suspect or the officer’s squad car, saving hours of time for officer as compared to the decontamination time with pepper spray.
-
*Crotega was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Award Programs.
CyberArk
 Best Privileged Access Security Solution
Best Privileged Access Security Solution
-
CyberArk Privileged Account Security Solution
-
The CyberArk Privileged Access Security Solution is used to protect more than 130+ installations across all three branches of the U.S. federal government – including multiple Department of Defense deployments.

-
CyberArk delivers a comprehensive privileged access management solution designed to eliminate advanced cyber threats by identifying existing privileged accounts across networks, then proactively managing, monitoring and protecting those accounts to reduce risk and improve security and compliance.
-
CyberArk continuously scans and monitors environments to discover and manage privileged credentials, isolates those credentials so they are never exposed to an end user, isolates privileged sessions to safeguard critical systems and automatically records and stores those sessions to enhance audit capabilities.
-
Time and time again, federal and state agencies look to safeguard their networks and incredibly sensitive data and assets by mitigating the top-threat to their organizations – compromised privileged access – with the help of CyberArk.
-
*CyberArk was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Award Programs.
Data Theorem
 Best Application Security
Best Application Security
-
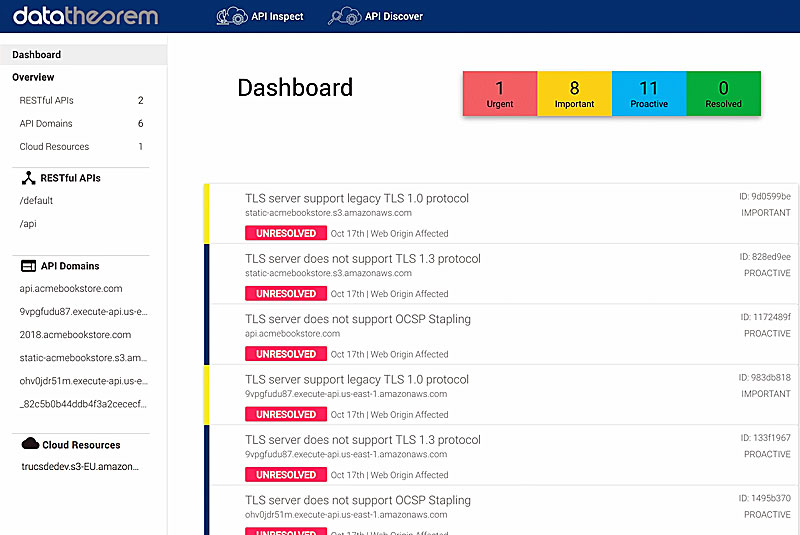
API Discover and API Inspect
-
Data Theorem products help organizations build safer applications that maximize data security and brand protection.
-
The company has detected more than 300 million application eavesdropping incidents and currently secures more than 4,000 modern applications for its Enterprise customers around the world.
-
Data Theorem uniquely addresses threat models related to modern apps, helping to identify issues related to privacy and application-layer attacks and the potential loss of sensitive data.
-
Traditional API security checks are not enough in today’s environment. API Discover and API Inspect do not depend on agents, proxies, or gateways that are common with legacy API security tools.
-
To address these and other industry issues, Data Theorem delivers automated API discovery and security inspection solution aimed at addressing API security threats introduced by today’s enterprise serverless and microservices applications, including Shadow APIs.
-
The industry is seeing a rapid rise of new applications built with modern tools such as Amazon Lambda, Google Cloud Functions and Azure Functions, which allow developers to build applications at scale with less infrastructure complexity and lower costs.
-
Data Theorem uniquely addresses threat models related to modern apps, helping to identify issues related to privacy and application-layer attacks and the potential loss of sensitive data.
Data Theorem (Second of Two)
 Best API Security Inspection Solution
Best API Security Inspection Solution
-
API Discover and API Inspect
-
The rapid growth of modern applications has led to a dramatic increase in the number of APIs developers are creating.
-
Cloud platforms such as Amazon Web Services, Microsoft Azure and Google Cloud Platform have introduced serverless services allowing developers to build applications at scale with less infrastructure complexity and lower costs.

-
However, as adoption of these new cloud serverless services grows, it allows for the creation of rogue APIs called shadow APIs that operate outside of enterprise security. The ephemeral nature of serverless based applications often makes legacy API security tools irrelevant and unusable, and traditional security approaches allow these shadow APIs to go undetected.
-
Data Theorem’s API Discover enables security and operations teams to discover shadow APIs in public cloud environments, as their cloud-based Analyzer Engine continuously scans the serverless applications to find shadow APIs.
-
Data Theorem’s API Inspect leverages their Analyzer Engine to continuously conduct security assessments on API authentication, encryption, source code, and logging, ensuring the operational function of users’ APIs matches their respective definitions.
-
Security teams are alerted of important and critical vulnerabilities caused by insufficient security protections. API Discover and API Inspect work together to bring visibility to shadow APIs and ensure that security standards are being met.
DataTribe
 Best Vulnerability Management
Best Vulnerability Management
-
Code Dx
-
Code Dx pioneered a key category that Gartner now refers to as Application Security Orchestration and Correlation (ASOC).
-
ASOC tools are critical to the vulnerability management process as they ease software vulnerability testing and remediation by automating the most time-intensive workflows security teams face, which helps security focus on key vulnerabilities, instead of spending the majority of their time on laborious tasks.

-
Originally funded by the Department of Homeland Security under a series of Small Business Innovation Research (SBIR) grants focused on securing the software supply chain, Code Dx now helps some of the largest Fortune enterprises and government agencies release secure software more quickly through automation.
-
Code Dx has built an end-to-end platform that allows AppSec teams to keep pace with DevOps and continuously assess software security risks across the entire spectrum of AppSec processes from running security tests through vulnerability remediation and system deployment.
-
Their new machine learning capability for AppSec triage, called Triage Assistant, automates vulnerability prioritization to reduce the number of false positives that AppSec practitioners need to analyze.
-
Code Dx was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
DetectaChem (First of Two)
 Best COVID-19 Detection Innovation (Tie)
Best COVID-19 Detection Innovation (Tie)
-
MobileDetect Bio BCC19 COVID-19 test kit
-
Earlier this year as the coronavirus pandemic gripped the United States, DetectaChem, a global leader in innovative portable threat detection technologies developed a smartphone-based MobileDetect Bio (MD-Bio) BCC19 COVID-19 test kit which received FDA (Food and Drug Administration) EUA (Emergency Use Authorization) and was being utilized across the nation.
(COVID-19 testing results from a nasal swab in just 30 minutes (up to 96 tests in 30 minutes). Perfect for large scale testing purposes, and easily deployable on the go with the company’s Mobile Field Lab (MFL) test kit configuration.)
-
The BCC19 test kit utilizes portable laboratory-grade molecular diagnostic technology that detects nucleic acids from the 2019-nCoV virus to determine positive or negative results and then utilizes the free MobileDetect App for Apple and Android platforms to generate result reports with time, date, images, patient info, GPS mapping and more.
-
Test reports can then be immediately sent via email or text to healthcare providers, laboratories or any other desired recipient. The BCC19 test kit achieved 100% positive and negative detection accuracy during FDA testing with comparable results and limits of detection to RT-PCR laboratory equipment.
-
As many testing sites can take 24 hours or much longer to produce tefst results, asymptomatic positive patients waiting for results can unknowingly infect countless others however with the BCC19 test kit’s 30-minute cycle and diagnostic-level results for asymptomatic and symptomatic patients, the window for spreading COVID-19 is drastically reduced from hours or days-to minutes resulting in greater safety for organizations and their communities at large.
DetectaChem (Second of Two)
Best CBRNE Detection System
-
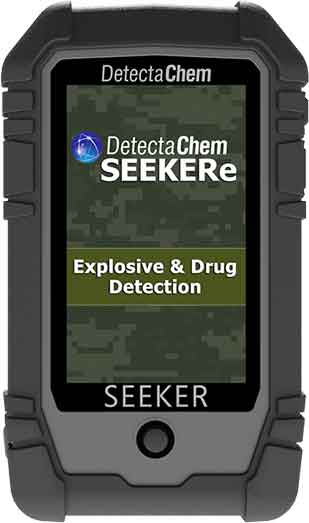
SEEKERe
-
SEEKERe is a hand-held detector using colorimetric technology, designed to be rugged and portable, to test for drug and explosives in the field, and also allow for trace and bulk detection.

-
This innovative Inorganic Nitrate card detects ultra-low trace amounts of Black Powder explosive material, the most common and easiest to produce homemade explosive material, and also rapidly identifies Ammonium Nitrate, another major explosive precursor that law enforcement agencies globally need the capability to identify in ultra-low trace amounts, as well as Urea Nitrate and more.
-
DetectaChem’s SEEKERe detects military-grade explosives, homemade explosive materials, precursor materials, fentanyl, heroin, synthetics, methamphetamine and more down to non-visible trace levels.
-
Its automated detection technology evolves globally recognized colorimetric technology which delivers reliable, legally-recognized and repeatable results better than any other trace detection products on the market.
-
The SEEKERe is used daily by law enforcement and military agencies, bomb squads and hazardous material teams for explosive and drug detection at airports, border crossings, ports of entry, sporting and event arenas and more across the United States, and is actively purchased and used by every branch of the Department of Defense and all applicable Department of Homeland Security agencies.
-
DetectaChem was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
EAGL Technology (First of Two)
Best Body Worn Gunshot Detection System
-
BlueFly Gunshot Detector (GSD)
-
EAGL Technology’s patented, zero false alarm, gunshot detection technology has now been extended to those who “Protect and Serve” in the form of a body-worn gunshot detector which gives the same instant, autonomous, and accurate notification that the FireFly and DragonFly gunshot detectors have been offering for over two years.

-
The new “BlueFly GSD” gives notification to those who need it within seconds of detecting a gunshot that is fired either by the wearer or by an adversary up to 100 feet away.
-
This device also monitors the wearer’s physical attitude and will immediately and autonomously send a notification of a “Man-Down” whether from a fall, a take-down, injury, or worse.
-
These notifications are then delivered by the EAGL System using EAGL’s proven Adaptive Response Technology. Notifications can be text, email, voice, and live display and optionally can include ballistics and live streaming video directly from a body-worn or dash camera.

-
The device is battery powered and uses EAGL’s long range RF technology for communications offering up to a 500ft range through a building and up to two miles outdoors depending on the terrain.
-
This smart device self-tests daily checking its electronics, communications, and battery life, reporting its findings back to the EAGL system which is continuously monitoring each unit’s status.
EAGL Technology (Second of Two)
Best Gunshot Detection Solution
-
EAGL Gunshot Detection & Lockdown System
-
EAGL Technology is the only gunshot detection system to have both indoor & outdoor gunshot detection technologies.

-
EAGL’s sensors are wireless, battery operated (7 year battery life), and use both Ballistic Energy Detection and Waveform Analysis to eliminate false alarms.
-
Additionally the EAGL system can deliver ballistic analysis, live streaming video, automatic lockdown and geofencing, full notification using text, email, voice, live notification via the systems GUI interface, and directly into any CAD or management system using the EAGL application programming interface (API).
(Learn More about the EAGL gunshot detection system. EAGL can also integrate with facility access control, live streaming IP cameras, public address, mass communication, and local emergency notification systems. Courtesy of EAGL Technology and YouTube.)
-
EAGL Technology was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
Evolv Technology
Best Weapons Detection Solution
-
Evolv Express™
-
-
Evolv Express is a touchless high-speed smart firearm and bomb detection system that screens over 3600 people per hour (60 people per minute) and gets smarter over time.
-
-
-
With Evolv, it is possible to deter and prevent active shooters and bombers from entering a venue without sacrificing the visitor experience.

-
With Evolv’s advanced sensors and machine learning, organizations can automatically screen for concealed weapons on all employees, contractors and visitors entering a workplace, facility, building, etc., without slowing down operations.
-
Evolv Express is a proven solution for fast, contactless weapons screening while offering a hassle-free visitor experience and the social distancing necessary in these uncertain times.
-
Second only to the TSA, organizations using Evolv have screened more than 50 million people to-date in a rapid, undisruptive manner while preventing more than 5,000 weapons from entering schools, sports stadiums, concert halls, places of work, houses of worship, government facilities and other public venues.
-
Evolv’s AI-based, free-flow weapons-screening and threat detection systems work at the pace of life to accommodate thousands of individuals and groups per hour.
-
Evolv Technology was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
FLIR Systems
Best COVID-19 Detection Innovation
-
FLIR EST Series Cameras
-
The FLIR EST™ thermal screening solutions, including the FLIR Axxx-EST, FLIR T5xx-EST, and FLIR Exx-EST series cameras, provide frontline screening at building entries and in high traffic areas to improve safety and help curb the spread of COVID-19.

-
This series of cameras are designed to simplify the screening process, reducing the burden on screening operators and adhering to recommended social distancing guidelines.
-
To further improve accuracy, the updated Screen-EST mode automatically generates a sample baseline temperature average and compares individuals’ skin temperature against that baseline, reducing measurement uncertainty from natural body temperature fluctuations and environmental effects.

-
This mode can sound or display an alarm when the camera detects an elevated temperature above a set threshold. If the screening mode detects an individual with elevated skin temperature, they should then be evaluated using a medical device such as a thermometer.
-
FLIR Axxx-EST Series: The A500-EST and A700-EST cameras are designed for permanent, fixed-mounted installations and can be deployed as a single, standalone screening station or in a network. The cameras can be connected to most video management systems while the camera housing features multiple mounting points to support tripod or permanent installations.

-
FLIR T5xx-EST Series: The T540-EST and T560-EST are designed to operate in either a mobile or more permanent setting. The flexible form factor enables a cable-free mobile operation with up to four hours of battery life or hands-free use with an integrated tripod mount.
-
FLIR Exx-EST Series: Light, ergonomically designed for handheld use, and battery-powered, the E54-EST and E86-EST offer the capability for mobile screening settings with a bright, easy-to-use integrated touchscreen display. Tripod mounts are also available for the Exx-EST models.
-
*FLIR Systems has now been recognized in their Fifth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards.
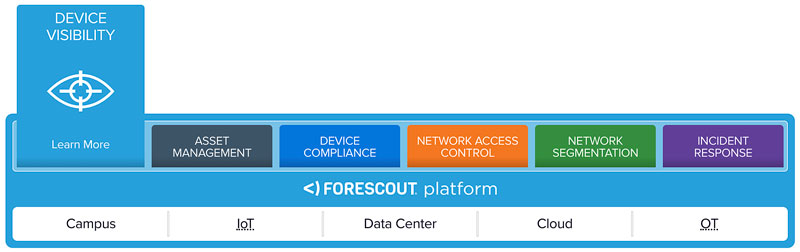
Forescout Technologies
Best Cyber Critical Infrastructure Solution
-
Forescout Device and Visibility Control Platform
-
With the explosive growth of non-traditional endpoints on government networks, it is critically important to gain a consolidated view not only of all government-owned PCs, laptops, servers and mobile devices, but also connected contractor and guest devices, IoT endpoints, operational technology (OT) systems, virtual machines — even rogue devices.
-
The recently updated Forescout platform offers a unique, agentless approach to network security, enabling government agencies to see all of these devices on their networks; continuously discovers profiles and classifies devices, users, applications and operating systems while monitoring managed devices, personally owned devices and other endpoints.
-
The Forescout platform uses this contextual device intelligence to apply policy-based controls upon devices and orchestrate incident response and device remediation among multiple third-party security solutions.
-
The solution currently scales to two million devices per deployment across the extended enterprise, including: campus, IoT, data center, cloud and OT.
-
Government agencies and contractors have a multitude of commercial technologies to consider for their network security, but often choose Forescout for the comprehensive device visibility and control capabilities it provides.
-
With the release of SilentDefense 4.1 the Forescout platform now is the first network security monitoring tool to intelligently combine all security and operational risk factors into a single, impact-based scoring framework.
-
By providing secure network access for a wide range of devices and user populations, the Forescout platform helps government agencies protect their confidential data and support compliance with mandated policies and regulations such as FISMA, NERC ISO/IEC 27001 and the GDPR.
-
*Forescout was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
Fortanix
Best Encryption Solution
-
Runtime Encryption® Platform
-
Runtime Encryption® from Fortanix enables a fundamentally new level of security and privacy allowing organizations with sensitive workloads to operate in untrusted environments such as the public cloud and remote clouds.
-
Encryption is an effective data protection control, however it’s use is currently limited to data at rest and data in motion. When, an application starts to run, it’s data in use is vulnerable to a variety of attacks including malicious insiders, root users, credential compromise, OS zero-day, and network intruders.
-
Runtime encryption provides deterministic security with hardware-aided memory encryption for applications to protect data in use.
-
Through optimization of the Trusted Computing Base (TCB), it enables encrypted data to be processed in memory without exposing it to the rest of the system which reduces the risks to sensitive data and provides greater control and transparency for users.
-
The holy grail of security has been to offer deterministic security to applications regardless of how the attacks originate. Runtime Encryption® provides deterministic security with runtime memory encryption for applications to protect data in use.
-
*Fortanix was also recognized in the 2018 ‘ASTORS’ Homeland Security Awards Program.
Fūsus
Best Investigation/Surveil-lance/Detection Product
-
Fūsus Real-Time Crime Center In The Cloud
-
Fūsus is the first company to extract and unify live video and data feeds from virtually any source, creating a Real-Time Crime Center In The Cloud that enhances the situational awareness and investigative capabilities of law enforcement and public safety agencies.
-
Whether it’s a drone, a traffic camera, a private cell phone video, a building security camera, or a bomb disposal robot, FUSUS can extract the live video feed and send it to your emergency operations center and officers in the field.

-
The company’s public safety ecosystem combines public & private camera feeds, including internal building cameras into a single real-time feed, enabling Law Enforcement and Public Safety agencies to function with improved operational intelligence.
-
Fūsus creates a public safety ecosystem that includes a registry map of all the public and private cameras in your region and a multi-media tips line for the public, and feeds collected evidence into a cloud-based digital evidence vault for investigators, enabling them to operate more efficiently.
Gallagher Security (First of Two)
Best Enterprise Access Control
-
Gallagher Command Centre
-
Gallagher Command Centre runs at the heart of Gallagher’s enterprise access control system.
-
This world-class security site management software has been proven to protect lives, create efficiencies, and save businesses thousands of dollars each year.
When the Harrisburg School District in South Dakota was the target of a shooting, Command Centre saved the lives of hundreds of students by placing physical barriers between them and the active gunman.
-
After the emergency button was activated, it took just four seconds for Command Centre to lock down the school, secure doors, notify district authorities via an automated message, and limit building access to emergency responders only.
(This is Command Centre from Gallagher Security.)
-
Gallagher Command Centre is the chosen platform for many of the world’s most high-consequence sites and is trusted to manage the security requirements of military and defense sites, federal, state, and local government, commercial, industrial, healthcare, transportation, and academic organizations.
-
Complex yet user-friendly, Command Centre is fully customizable and configurable to meet the unique needs of sites of all sizes and security requirements. Command Centre allows operators to configure, manage, and report on all aspects of their system.
-
It has been proven over and over to save organizations time, resources, energy, and money, all while delivering superior security that keeps people safe.
Gallagher Security (Second of Two)
Best Risk, Crisis Management Product
-
Proximity and Contact Tracing Report
-
In the current pandemic-climate, the health and safety of colleagues, customers, visitors, and contractors is at the forefront of business considerations.
-
Responding quickly to the COVID-19 crisis, Gallagher developed the Proximity and Contact Tracing Report – an innovative tool to support organizations with fast and efficient contact tracing, to keep people safe by reducing further spread of the virus.

-
Released in May 2020, if an employee or visitor were to be identified as having a contagious illness, such as COVID-19, the site’s access control operator enters specific information – including the origin cardholder (the person identified as being a health risk) and the dates where there was a risk of exposure – into the Proximity and Contact Tracing Report utility, quickly producing a report listing all other cardholders who shared an area with the contagious cardholder.
-
This information allows organizations to act rapidly and to proactively inform their employees of the potential risk of infection, allowing them to take action, seek testing, and minimize spread of the virus.
-
In doing so, Gallagher’s Proximity and Contact Tracing Report reduces the need for an entire site to shut down if a positive case of COVID-19 were identified – helping to safeguard business revenue, employee income, and operations.
-
*Gallagher was also recognized in the 2019 ‘ASTORS’ Homeland Security Awards Program.
Genasys Inc. (First of Two)
Best Long Range Acoustic Hailing System
-
LRAD 500X-RE
-
Compact, lightweight and designed for applications ranging from fixed security installations to mid-sized vehicles and vessels, the LRAD 500X-RE long range highly intelligible acoustic hailing system easily mounts and transports to provide law enforcement, homeland security, and defense personnel unparalleled long-range communication and safe, scalable non-kinetic escalation of force.

-
The U.S. Navy and U.S. Army’s acoustic hailing device (AHD) of choice for small vessels and vehicles, the extended frequency range of the LRAD 500X-RE ensures broadcasts are clearly heard and understood on the ground, from the air or at sea in all environments.
-
LRAD 500X-RE is rugged, with military tested contstructions, has low power requirements, is suitable for all-weather and is simple to operate.
-
With highly intelligible communication of up to 2,000 meters, the LRAD 500X-RE safely communicates beyond stand-off distances to determine intent and creates instant acoustic standoff perimeter.
Genasys Inc. (Second of Two)
Best Mass Notification System (Hardware)
-
Genasys 360XL
-
Powered by Genasys’ patented XL driver technology, the 360XL mass notification system and emergency warning system packs more audio output and broadcast range into smaller, lighter system configurations.
-
Genasys 360XL systems feature Genasys’ industry-leading voice intelligibility and provide approximately twice the audio output and broadcast range of Genasys 360X systems.

-
The Genasys 360XL delivers exceptionally clear voice and warning siren broadcasts with uniform 360° coverage over distances up to 5.3 sq. kilometers, and the Genasys 360XL emitters can be mounted on buildings and/or standalone poles.
-
The Genasys 360XL also has an integrated, fully self-contained, ruggedized trailer option for mobile deployments, and each 360XL 2RU amplifier module drives two emitters.
-
The 360XL is built to withstand wind speeds of up to 200 mph, is field upgradeable for added area coverage, and features flexible power options including battery, generator and solar.
-
An optional TCP/IP network control interface is available for remote activation and control of multiple 360XL systems from a single location.
-
*Genasys Inc. (formerly LRAD) has now been recognized in their Fifth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards.
Global Elite Group
Best Airport/Aviation Security Program
-
Aviation Security Services
-
Global Elite Group oversees the security of over 60 clients across the aviation industry, including international airlines, and regional airports.
-
In the 17 years since the company was founded, a lot of growth has taken place and this once regional provider has a far-reaching reputation for delivering outstanding value and a customized approach for each client’s needs.

-
Most recently, Global Elite Group has been acquired by Securitas Transport Aviation Services USA for USD$22 million reflecting the growth and value of the company since it began.
Global Elite’s reputation outside of its aviation security offerings is excellent for delivering security services, emergency management and consulting services to governments and businesses throughout the world.
-
Global’s foundation offerings focus on aviation security, which makes up 95% of its business portfolio and has been the driver for developing a complete range of AVSEC services that are tailored to the express needs of each customer from aircraft guarding and airside escorting, baggage pilferage investigations/prevention and cargo guarding, escorting & screening, to emergency response support, passenger behavioral assessments & verification and even explosives/narcotics canine units.
-
*Global Elite Group was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs, respectively.
GrammaTech
Best Application Security Testing
-
CodeSonar® Static Application Security Testing
-
Today, development teams are under constant pressure to meet aggressive deadlines for delivering new software, with rolling releases and agile development practices pushing new features and code quickly into production.
-
This has led to a sea change in software development where security is being baked-in earlier to release cycles, and to help organizations navigate this new “shift left” culture GrammaTech developed the CodeSonar® Static Application Security Testing (SAST) platform to organically support each stage of the software development cycle and integrates with tool chains, methodologies and processes.

-
Using CodeSonar, organizations can develop and release high quality and secure software that is free from harmful defects and exploitable weaknesses that can cause system failures, enable data breaches, and increase liability.
-
Unlike alternatives including testing tools, compilers, configuration management, etc., the CodeSonar SAST platform can be integrated into the application development process at any stage with ease, so organizations can simply attach CodeSonar to their existing build environments.
-
CodeSonar provides validation of coding standards and best practices including MISRA, JPL, CERT-C and static verification using formal method concepts to find defects including runtime errors, buffer overruns, API misuse, misuse of socket API, suspicious behavior, dead code unused variables.
-
GrammaTech CodeSonar is being used by some of the world’s most security conscious organizations, including application developers in the defense (DOD, DARPA, Army, Navy), automotive, aerospace, industrial and medical device sectors to test embedded software for security and safety vulnerabilities, and helps federal defense, intelligence and federal civil agencies tackle their most complex cybersecurity challenges.
Gurucul
Best Cyber Security Risk Management
-
Gurucul Unified Security & Risk Analytics
-
Gurucul Unified Security & Risk Analytics is a cloud-native data science driven platform that unifies key Cyber Defense Center functions to enable contextual, risk-prioritized decisions for automating security controls.
-
It enables organizations to predict, detect and prevent cyber security breaches by ingesting and analyzing massive amounts of data from virtually any source, including network, IT systems, cloud platforms, applications, IoT, and more.
-
Gurucul provides a comprehensive view of user/entity behaviors and detects risky outliers using a library of advanced machine learning (ML) models and identity-centric data science, artificial intelligence (AI), anomaly detection and predictive risk-scoring algorithms to identify abnormal behaviors and activities indicative of security threats.
-
By generating contextual, risk-prioritized alerts in real-time, Gurucul Unified Security & Risk Analytics can automatically mitigate threats before damage occurs from a wide range of cyber security threats including malicious insiders, privileged access abuse, fraud, account compromise/ hijacking/ sharing, data exfiltration, DLP and IP protection, trusted host and entity compromise, ransomware, and APT/stealth attacks that lay dormant between various stages of a cyberattack.
-
Gurucul Unified Security and Risk Analytics combines intelligent threat hunting, log aggregation, network traffic analysis, SIEM (Security Information and Event Management), SOAR (Security Orchestration, Automation and Response) and UEBA (User and Entity Behavior Analytics) capabilities into one integrated platform to address both known and unknown threats, identify risky user behavior and automatically respond to security incidents.
-
*Gurucul was also recognized in the 2019, 2018 and 2016 ‘ASTORS’ Homeland Security Awards Programs.
Haines Security Solutions
Best Multi-Discipline Security Education Program
-
Haines Security Design School Virtual Classroom/On-line Training/Mentoring
-
Haines’ Security Design School is a virtual classroom training platform for those involved in developing mitigation strategies to deter, detect and defend against a variety of man-made threats.

-
The classroom provides in-depth instruction in access control concepts, antiterrorism and crime prevention through environmental design, electronic security systems design and vulnerability assessment and risk analysis.
-
Training can be accomplished by attending an instructor lead course or through self-study with or without a mentor.
-
Once the academic requirements are satisfied the designations of Antiterrorism Design Engineer (AtDE) or Physical Security Engineer (PSE) are awarded to architects, emergency managers, engineers, facility managers, planners and security professionals.
-
HSDS is part of the Physical Security Engineer Training and Certification [PSET&C] program (Platinum ‘ASTOR’ Award for Best Homeland Security Education Program in 2017).

-
The PSET&C consists of three parts; academic studies, published materials and public speaking. The program differentiates itself from other credentialing programs as PSET&C accepts any related training from an accredited provider (college/university, corporation, DOD/DHS, etc.) for award of Antiterrorism Design Engineer or Physical Security Engineer designation.
-
In order to qualify for the Senior and Master levels of AtDE or PSE designation the applicant must have been published in a security related media and presented at a regional or international conference.
-
*Haines Security Solutions was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Hanwha Techwin America (First of Two)
Best CCTV Technology
-
PNV-A9081R4K Network AI IR Vandal Dome Camera
-
The PNV-A9081R is an AI-based camera that captures pristine images at up to 4K resolution while including powerful, in-camera deep learning algorithms for advanced object detection, classification and error and license-free analytics.
-
Utilizing object recognition versus motion detection all but eliminates false alarms while also providing valuable business and operations insight.

-
The PNV-A9081R dome camera is NDAA compliant and comes in a modular form factor with an open platform for 3rd party applications, and key features include WDR (120dB), Simple focus, H.265/H.264/MJPEG, WiseStreamⅡ compression technology, USB port for easy installation, Advanced video analytics and sound classification, True D/N, Dual SD card, Hallway view, DIS using a Gyro sensor.
-
Video Analytics based on AI, Object detection and classification(Person, Face, Vehicle, License Plate), Attribute, BestShot, Compatible with Wisenet Retail Insight v2.0 for business intelligence, age/gender-based people counting, heatmap, queue management, modular structure for easy installation, POE+/12VDC.
-
The new face mask detection analytic can detect if people are wearing/not wearing a face mask and provide notification to compatible VMS/NVRs. Face Masks are now part of the face attribute metadata for easy forensic review.
Hanwha Techwin America (Second of Two)
Best COVID-19 Detection Innovation
-
Occupancy Monitor Open Platform Application for P – Series AI Cameras
-
The Hanwha Techwin Occupancy Monitoring System combines 4K camera resolution with edge-based AI video analytics so you can easily maintain safe building occupancy levels to protect employees and customers.
-
The application provides government facilities with highly accurate, real-time data on the number of people entering and leaving a building, and also provides retailers, houses of worship, museums, entertainment facilities, restaurants and more with highly accurate, real-time data on the number of people in a facility at any given time.
(Easily monitor public spaces to maintain safe occupancy levels. The Hanwha Techwin Occupancy Monitoring System combines 4K camera resolution with edge-based AI video analytics so you can easily maintain safe building occupancy levels to protect employees and customers. Courtesy of Hanwha Techwin America and YouTube.)
-
When a pre-set maximum capacity level is reached, the application generates alarm outputs to control automatic doors or a traffic light beacon.
-
The Occupancy Monitoring System also generates red “wait” or green “enter” customizable text messages that can be displayed on monitors.
-
The system aggregates occupancy data from up to 8 cameras at 8 entrances/exists simultaneously, making it suitable for not only small business but also large enterprise.
-
*Hanwha Techwin America was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
HID Global (First of Two)
Best Law Enforcement Mobile Device
-
HID NOMAD™ 30 Pocket Reader
-
HID Global’s HID NOMAD 30 Pocket Reader is an affordable, single fingerprint mobile identification solution for efficient and dependable biometric capture and database verification.

-
Its portability eliminates the need for obtaining fingerprints at a fixed location and facilitates biometric capture in the field, and the ergonomic design easily provides comfortable singlehanded use by the operator and fingerprints can be collected without physical contact with the subject.
-
Law enforcement agencies use the NOMAD 30 solution to efficiently identify individuals in public areas. This helps keep custody suites free to house confirmed offenders—rather than those awaiting identification—and reduces overall processing costs and keeps police officers patrolling the streets.
-
One police department in a major city estimates savings of more than $600,000 in the first year of deployment and has positively identified more than 12,000 persons of interest.
-
The convenience and mobilization of the suspect identification process that the HID NOMAD 30 Pocket Reader enables has improved relations and built trust between the police force and the community it serves.
HID Global (Second of Two)
Best Identification Management Solution
-
WorkforceID™
-
WorkforceID by HID Global is a new identity management cloud service that provides an ever-expanding set of workforce and visitor identity management applications that help customers address their evolving cyber and physical security, compliance and business challenges.
-
WorkforceID digitally transforms how enterprises manage physical access identities and credentials for their workplace, big or small.
-
Based on the enterprise-grade HID SAFE™ physical identity access and visitor management software, WorkforceID takes the best of HID SAFE and makes it better.
-
Simple to use, WorkforceID™ offers streamlined and automated service set-up and account on-boarding and off-boarding, with no complex software to install/configure/support on-premise.
-
*HID Global was also recognized with in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Awards Programs.
High Rise Escape Systems
Best Disaster Preparedness, Disaster Recovery System
-
Guardian Evacuation System
-
The Guardian Evacuation System developed a fixed and/or portable escape system to attach to a structure, designed to mitigate means of egress for anyone living or working above the 2nd floor, including: government buildings, embassies, barracks, hospitals, air traffic control towers, apartments, condominiums, hotels, industrial and job sites, theme parks, cranes, oil platforms, ships and more.

-
High Rise Escape Systems (HRES) accomplished this in a combination of several simple, low-tech devices that require no power, are inexpensive, have a long shelf-life and are easy to use.
-
Using a Controlled Descent Device (CDD) which works like a pulley, a user slides a one of two permanently attached escape harnesses over them, exits off of a balcony/roof structure or out of a window and the CDD slowly lowers them automatically at the rate of 3 feet per second.
-
As the first user descends, the opposite end of the cable automatically retracts and reloads the CDD with the remaining escape harness for the next evacuee.
-
Then the process repeats. Everyone gets out.
-
The United States Military has been utilizing High Rise Escape Systems Guardian Escape Systems on Air Traffic Control Towers for years, which includes the Ellsworth AFB, Dyess AFB, Vandenburg AFB, Edwards AFB, Tinker AFB, Maxwell AFB and Patrick AFB as well as Army and Air National Guard installations such as Alpena CRTC, Grayling Air Gunnery Range & Selfridge ANG.
-
*HRES was also recognized with in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Awards Programs.
iboss
Best Network Security Solution
-
iboss Cloud
-
iboss cloud secures user Internet access on any device, from any location, in the cloud, shifting the focus from following perimeters to following users so that consistent cloud security is applied while users are in the office, on the road or working from home.
-
Built on a proprietary containerized architecture designed 100% for the cloud, iboss users are always connected to iboss cloud, regardless of device or location, to ensure all Internet traffic is secured for compliance, web filtering, malware defense and data loss at all times.
-
Since iboss cloud lives in the cloud, security goes where users go with elastic and instant scaling to meet the demands of the cloud-first future.
-
The iboss’ SaaS solution significantly reduces management costs and offers a faster, more distributed alternative to previous on-premise gateways.
Identiv
Best Video Analytics Solution
-
3VR
-
3VR is a next-generation, intelligent video solution that utilizes a searchable, data-driven approach to video that enables valuable insights for both security and business with deep, real-time insights into consumer behavior and site operations.

-
Identiv’s 3VR data platform solves problems associated with searching video content and gathering real-time intelligence from the unstructured data produced by a single camera or a global network of cameras.
-
3VR is the standard for hundreds of global customers in financial services, retail, government, critical infrastructure and hospitality, and the company’s surveillance solutions include facial recognition, advanced object tracking, license plate recognition, dwell and loitering, people counting, queue management analysis, and demographics.
-
The analytics program works with IP, analog and megapixel cameras and is tightly integrated with data and search, which means no separate hardware is needed and results are ready immediately.
-
*Identiv was also recognized with in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Awards Programs.
Intrado Corporation (First of Two)
Best COVID-19 Communications Solution
-
-
-
Schools across North America are leveraging the Intrado Safety Shield™ solution to help them navigate the challenges associated with the COVID-19 pandemic as students return to school.
-
-

-
Intrado Safety Shield is an end-to-end safety management platform designed to provide prevention, preparation, and active response for threats faced by educational organizations of all kinds, leveraging the company’s comprehensive and secure notifications capabilities along with connectivity to the entire public safety ecosystem and access to expanding sources of threat-relevant data.
-
This unique and powerful combination provides information and insights to 911 dispatchers, first responders, and educational leaders, allowing them to make more informed decisions and ultimately protect their communities more effectively.
Intrado Corporation (Second of Two)
Best COVID-19 Emergency Response Solution
-
Intrado Safety Shield
-
Intrado Safety Shield offers a set of tools to help educational institutions enhance school safety and improve their emergency response capabilities.
-
Intrado Safety Shield unites Intrado’s 911 and mass notification capabilities with panic button, first responder collaboration, and emergency response planning solutions to create a comprehensive crisis prevention and response offering.
-
Additionally, Intrado Safety Shield provides a single operational view and integrates with other relevant software to create a simplified hub for emergency response activities.
-
Unlike point solutions that only address part of the problem, or which lack a well-established connection to 911 infrastructure, Intrado Safety Shield offers a complete solution that helps schools prevent, prepare for, respond to, and recover effectively from school emergencies large and small.
-
Intrado has long-term relationships with thousands of public safety answering points, government agencies, and other relevant organizations, and with over 63,000 schools on its client roster and decades of experience in K-12 education, Intrado has more experience serving educational institutions than any other provider.
INTRUSION Inc.
Best Cyber Security Solution
-
INTRUSION Shield™
-
INTRUSION Shield doesn’t merely alert to cyber threats but immediately neutralizes them, keeping businesses safe without the need for human intervention.
-
Unlike other solutions which focus on keeping out malicious incoming traffic, Shield works on the premise that cybercriminals already exist within your network, meaning Shield is constantly monitoring all incoming and outgoing traffic.

-
Shield employs the use of this real-time AI to analyze INTRUSION’s threat-enriched, Big Data Cloud – the world’s largest inventory of IP relationships, and using its Process-flow Technology™, the solution applies signatures and rules based on DNS, TCP, UDP – and the connections between DNS and IPV4 and IPV6 addresses – to learn the behavior and patterns of cybercrime activity.
-
Shield then uses this intelligence while it continuously monitors incoming and outgoing traffic to identify new threats.
-
Finally, the solution goes beyond monitoring by instantly blocking traffic to and from any malicious sources, protecting companies from ransomware, viruses, malware, data theft and more.
IPVideo Corporation (First of Two)
Best Alert Notification System
-
HALO SMART SENSOR 2.2
-
HALO SMART SENSOR 2.2 now includes sound alert incident management including alerts for spoken key words, advanced gunshot detection and includes chemical incident detection and can assist with the workplace return from COVID 19.
-
Individuals under duress can now utilize a spoken keyword to send instant alerts to security for help in privacy areas that cannot have a camera, areas like bathrooms, hotel rooms, patient rooms, dorm rooms, locker rooms, dressing rooms, apartments, et al.

-
Now a daughter in her dorm room, a hotel housekeeper, a patient under duress, a student in a hazing incident or your elderly parent living by themselves can alert security to an attack or emergency situation in real time by shouting a keyword like “HALO HELP”.
-
The audio is still not being recorded maintaining privacy, but the alerts are automatically sent to security for immediate response. To help diffuse situations, the alerts can also trigger an audible message that an emergency has been declared and security has been notified.
-
Another new feature is the addition of machine learning capabilities to establish audible level “normalcies”. Advanced gunshot detection audio analytics can trigger a facility lock-down and an emergency call response via the integration of third-party security applications when detected.
-
HALO SMART SENSOR 2.2 also includes chemical incident detection and can assist with the workplace return from COVID 19.
(HALO IOT Smart Sensor 2.0 New features include gunshot detection, key word alerting, air quality monitoring and more. Courtesy of IPVideo Corp and YouTube.)
IPVideo Corporation (Second of Two)
Best Sound and Chemical Incident Detection System
-
HALO SMART SENSOR 2.2
-
Additional new features of the award-winning HALO IOT Smart Sensor also now include air quality monitoring, BACnet integration and cleaning chemical signature verification.
-
The multi-sensor is now a vape and THC detector, gunshot detector, security device for privacy areas, chemical detector, air quality monitor and a smart building guide in a single device, all the more valuable as air quality and air filtering is of great concern with the return to work and school.

-
HALO will now monitor and send alerts based on Indoor Air Quality (IAQ) measurements and will report the Air Quality Index (AQI), based on the EPA’s regulated standards, for the indoor environment.
-
It will identify if the environment is in the danger zone for the spread of disease at the location of each sensor.
-
The integration with BACnet will allow communication of building automation and control systems for applications such as heating, ventilating, and air-conditioning control (HVAC), lighting control, access control, and fire detection systems and their associated equipment. HALO alerts and sensor readings can now communicate to these varied control systems to address and make improvements in response to the alerts received.
-
*IPVideo Corporation was also recognized in the 2018 ‘ASTORS’ Homeland Security Awards Program.
Iris ID
Best Facial/Iris Recognition System
-
IrisTime Management System & iT100 platform
-
IrisTime is an easy-to-use platform with fast auto focus and iris/face capture at distances of up to 24 inches. Identity authentication takes only a second.
-
IrisTime™ is a fully customizable biometric identification platform designed to meet the needs of organizations small and large.
-
It is a product of Iris ID, the global leader in iris recognition technology for 20 years. It is designed to enable development of best-of-class applications that will reside on the device.
-
The fully customizable IrisTime platform also enables a user to design its own applications.
-
Device management tools will be part of the application console. IrisTime includes the iTMS (IrisTime Management Service) application to manage the device on networks.
-
iTMS functionality will also be available in API form to enable software developers to integrate device management in custom applications.
-
Iris ID was also recognized with Platinum Award Wins in the 2019, 2018 and 2016 ‘ASTORS’ Awards Programs.
Kiernan Group Holdings
Best Homeland Security Education Program
-
GOT Preparedness Online Training for Remote Workers
-
Kiernan Group Holdings (KGH), led by CEO Dr. Kathleen Kiernan, launched a new ‘GOT Preparedness’ Online Training website in October of 2020 built specifically for dispersed, deployed and remote workforces.
-
Built by practitioners, for practitioners who bring a common-sense approach to the most complex problems confronting society, KGH believes that the first line of defense is always a prepared individual from the classroom to the boardroom.

-
KGH has delivered operational and educational capabilities to thousands of individuals domestically and internationally on active shooter preparedness and workplace violence prevention, and has developed a methodological based approach to the resiliency cycle at an individual and organizational level.
-
Preparedness Without Paranoia® fosters an educated, engaged, and resilient public. The online courses are certificate-based, designed specifically for the adult learner in remote or dispersed working environments. Learner-centric and self-paced, each course contains checks on learning and a certificate upon successful completion.
-
Participants of the training gain a heightened situational awareness to understand today’s multidimensional threat environment, recognize telltale signs of an evolving threat, be empowered to take effective action, and understand how to recover and resume one’s daily activities in an effective manner.
Kingston Technology (First of Two)
Best Data Storage Security Solution
-
KC2500 NVMe PCIe SSD
-
Kingston Technology’s KC2500 NVMe PCIe SSD offers superior performance using the latest Gen 3.0 x 4 controller and 96-layer 3D TLC NAND.
-
This compact M.2 SSD provides greater flexibility, increasing storage but also saving space.
-
With read/write speeds up to 3,500/2,900MB/s this drive delivers outstanding endurance improving the workflow in desktop, workstations, and high-performance computing systems.
-
KC2500 sets a new bar for high-performance client usage, enabling tech enthusiasts to handle intensive workloads.
(Learn More about the KC2500 NVMe PCIe SSD. Courtesy of Kingston Technology and YouTube.)
Kingston Technology (Second of Two)
Best Encryption Solution
-
Available in capacities up to 2TB, Kingston’s KC2500 NVMe PCIe SSD is a self-encrypting drive with end-to-end data protection using XTS-AES 256 bit Hardware-based encryption.
-
Supporting a full-security suite it allows the usage of independent software vendors with TCG Opal 2.0 security management solutions such as Symantec, McAfee, WinMagic and others, protecting and securing your data.
-
For those that demand speed and reliability, but also don’t want to sacrifice performance for security KC2500 NVMe PCIe SSD is the ultimate upgrade.
-
Kingston Technology also also recognized in the a 2019 and 2017 ‘ASTORS’ Homeland Security Awards Program.
Konica Minolta Business Solutions
Best Thermal, Infrared Camera System
-
Konica Minolta and Mobotix Thermal Screening Station
-
Thermal radiometry imaging technology measures infrared energy quickly and efficiently. The Konica Minolta and Mobotix Thermal Screening Station is an all-in-one system comes with everything you need to establish a front-line screening process.
-
Visitors and employees face the camera and to allow for the inner canthus eye screening, the most accurate point for surface temperature in thermal radiometry, while an operator can view the thermal image on the screen.
-
Screen alerts in red will identify those screening out of your prescribed range who may need additional temperature testing.
-
The Konica Minolta and Mobotix Thermal Screening Station’s thermal screening images differentiate between hot objects and face objects, and thumbnail images with temperature data are saved on the local dashboard with clear green or red indicators of pass or fail.

-
Along with the thermal screening is an optional Mass Text Alert Notification with Video Management System.
-
This VMS enables remote business managers to review and analyze an entire company or organization’s screening information aggregating information from all of the cameras in place.
-
*Konica Minolta Business Solutions was also recognized with Multiple Awards in the 2019, 2018, and a 2017 ‘ASTORS’ Homeland Security Awards Programs.
LenelS2
Best Access Control & Authentication System
-
LenelS2 OnGuard access control system version 7.6
-
LenelS2, part of Carrier Global Corporation’s, OnGuard® access control system is an integrated security platform that works with third-party software and hardware to provide enhanced protection through advanced technologies and innovative products.
-
The OnGuard system version 7.6 expands cloud deployment options and provides enhanced operability and convenience.
-
Extensive enhancements create a more scalable, accessible and cloud-compatible enterprise security platform, and enriches essential operations, including IT compliance, cybersecurity, reader and card technology and browser client usability.
-
Innovative new features, expanded browser support and usability improvements to the OnGuard system’s suite of web-based clients and modules enhance ease of use, intuitive operation, and convenience for end users who monitor alarms, validate access requests and host visitors. In particular, the next generation visitor management suite provides unparalleled ease of use, increased mobility and seamless integration across a range of devices, from mobile to desktop.
-
Cybersecurity enhancements make the OnGuard system version 7.6 the most secure release yet and include use of the TLS 1.2 protocol to encrypt email and browser client communications, while new rules eliminate default passwords from the system.
-
LenelS2 was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
ManTech
Best Federal Government Security Program
-
ManTech’s Space Range
-
Today, every facet of space, from complex ground stations to data transport facilities, to the spacecraft themselves, faces the challenge of cyberattacks that can disable systems vital to national & homeland security and military situational awareness.
-
Space assets are equally important to critical infrastructure sectors from healthcare, emergency services, financial transactions, energy and water supply, which rely on space-driven GPS, accurate timing and other essential functions.

-
The number one responsibility of the space community is to safeguard our space assets with advanced cybersecurity solutions that anticipate and defeat attacks.
-
ManTech’s Space Range applies their cyber range technology to the challenge of identifying and capturing the unique threats and vulnerabilities in space, and expands upon the company’s robust, scalable and hyper-realistic range to encompass the unique requirements of a cyber infrastructure supporting a space enterprise.
-
ManTech’s Space Range provides “the right stuff” for customers to train to defend America’s vital space enterprise from the ground up, and most importantly, provides leaders with the confidence that critical space communications, navigation and intelligence gathering capabilities will be available and reliable when needed most.
-
*ManTech was also recognized in the 2019 ‘ASTORS’ Homeland Security Awards Program.
Mark43
 Best COVID-19 Communications Solution (Tie)
Best COVID-19 Communications Solution (Tie)
-
Pandemic Preparedness Package
-
In April 2020, Mark43, a leading cloud-based public safety software company, rolled out its Pandemic Preparedness Package for any interested public safety agency in the United States.

-
The software package enables agencies to seamlessly capture data on how COVID-19 is affecting the agency itself and the community which it protects and serves.
-
While Mark43’s software typically costs hundreds of thousands or millions of dollars (one of their latest contracts was $3.6 million, for example), the company’s Pandemic Preparedness Package is an entirely free one-year offering.
-
During the COVID-19 pandemic, local police and first responders found themselves struggling to understand the scope of the pandemic in their own communities and track the virus’s impact amongst their own ranks.
-
In record time, Mark43 created the Pandemic Preparedness Package that includes Potential Exposure Reports, an Exposure Status Update Report, and a COVID-19 Potential Exposure Dashboard, which allows first responders to record instances where they may have been exposed to COVID-19 so that they can take appropriate distancing measures.

-
The technology seamlessly addresses a number of pandemic-specific pain points for agencies, including workforce management, documentation for benefits and posterity, and data tracking for FEMA reimbursement requests to cover costs expended during national disasters, and Mark43’s technology adheres to the highest government standards for security, confidentiality, and availability.
-
Mark43’s Pandemic Preparedness Package embodies the highest caliber technical innovation developed specifically to help public safety agencies and their communities in the wake of the COVID-19 pandemic.
-
*Mark43 was also recognized in the 2019 ‘ASTORS’ Homeland Security Awards Program.
Marshalls Landscape Products North America (First of Two)
 Best Perimeter Barrier/Deterrent System (Bollards/Gates)
Best Perimeter Barrier/Deterrent System (Bollards/Gates)
-
RHINOGUARD® 72/30 ULTRA SHALLOW 50™ BOLLARD
-
Requiring just a 50mm excavation depth, the RhinoGuard® Ultra Shallow 50™ bollard series has been successfully crash tested in two different foundations under the IWA-14.1 standard and is capable of stopping a 7.2 ton vehicle traveling at 30mph.
-
Tested on both a typical footpath installation, and cycle segregation foundation, the bollard series successfully performs in both environments, immobilizing the vehicle and achieving a stopping distance of only 1.1m.
(The RhinoGuard® Ultra Shallow 50™ bollard series has been successfully crash tested in two different foundations under the IWA-14. Courtesy of Marshalls LP.)
-
Both tests demonstrate a real life scenario by impacting a single bollard at 30 degrees which is considered to be the most likely angle of attack on long linear runs of Hostile Vehicle Mitigation (HVM) protection.
-
Using just 7 easy to install bollards that are simply bolted together allows for quick and flexible deployment opportunities and the requirement of just 50mm of foundation makes the Ultra Shallow 50™ the perfect solution for use on bridges and other areas where underground service and utilities affect installation. Individual modules can be added to the system to cover the required length of any project.
Marshalls Landscape Products North America (Second of Two)
 Best Perimeter Protection System
Best Perimeter Protection System
-
Marshalls LP Protective Street Furniture
-
An alternative solution to temporary security, Marshalls Landscape Protection (Marshalls LP) launched its RhinoGuard® GateKeeper® range in 2019 to provide government and businesses with an effective, temporary solution to the threat posed by hostile, criminal and errant vehicles.

-
Quick and easy to transport, install and remove, this modular system – which is tested to the International Workshop Agreement (IWA) 14.1 standard, the latest specification for assisting in vehicle terror prevention – has been used by sports and music venues in the US, among a range of other firms across multiple sectors.
-
The need to protect the public from this threat rose quickly up the agenda for planners and security consultants following high-profile terrorist assaults in New York, Virginia and Ohio in recent years, but also the rise in criminal attacks and accidental collisions.
-
Permanent solutions built to mitigate this risk have long been available, but until the GateKeeper® range, there was a lack of temporary solutions available for use at events that witness short-term upticks in footfall.

-
The system can stop a 2.5 ton vehicle traveling up to 30mph while being completely permeable, allowing pedestrians to move freely through spaces rather than filtering through access points, achieving a free flowing, less fortified space in the process.
-
It’s vital that the public is safe, not scared when it comes to frequenting busy areas and the GateKeeper® range ensures this remains the case in projects and schemes where temporary measures are required.
-
*Marshalls LP was also a Winner in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
N2WS
 Best Cloud Computing/Storage Solution
Best Cloud Computing/Storage Solution
-
N2WS Backup & Recovery
-
As more enterprises move to the cloud, data loss, outages and malicious attacks become inevitable vulnerabilities. Scaling data and varying requirements become complex, as is the need to meet compliance regulations and optimize costs. This breeds an environment too complicated for manual scripts.
-
N2WS allows customers to ‘set it and forget it’, and effortlessly manage petabytes worth of data, recover quickly from attacks/outages/errors and manage storage costs, by leveraging N2WS’ secure, rapid data recovery and easy management for key services – all from a single console.
-
N2WS leverages AWS-native snapshot technology to fully automate backup of Amazon EC2, EBS, RDS, Redshift, Aurora, DynamoDB, EFS and S3. It has been the leading storage solution on the AWS Marketplace since 2012, providing very flexible backup scheduling and 1-click disaster recovery to restore a single file or entire environment in less than 30 seconds, across multiple regions and/or accounts.
-
N2WS optimizes RTO/RPO, supports multi-tenancy for large, complex environments and enables customers to lifecycle EBS snapshots into Amazon S3 and/or Glacier for long term retention.
-
N2WS Backup & Recovery has been dubbed the Next Generation Backup and Recovery for AWS due to its unique Disaster Recovery orchestration, data lifecycle management and cost savings capabilities. With N2WS, exponentially scaling data is now tantamount to managing complex backup schedules for thousands of AWS EC2 instances.
-
*N2WS was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
NICE Public Safety
 Best 911 Recording & Analytics
Best 911 Recording & Analytics
-
NICE Inform
-
Getting incident response right has always been critical to policing, but with today’s increased media attention on incident response and policing, it has become even more important than ever.

-
With 9-1-1 telecommunicator annual turnover approaching 19% in the United States, overstressed, overworked and inexperienced 9-1-1 telecommunicators are making ‘life or death’ judgement calls every day, and are taught to dispatch for the worst case scenario, which can lead to police ‘over response.’
-
Statistics show that somewhere between 20-40% of all incidents are downgraded by police following the initial classification by 9-1-1, and over-responses can cause reputational damage for 9-1-1 centers, waste scarce police budget dollars, and even unnecessarily escalate incidents.
-
NICE Inform can help 9-1-1 centers address these challenges to improve downstream police response, so 9-1-1 centers can gain better visibility into how telecommunicators are handling incidents so they can spot issues (e.g. over-response to calls) early on.
-
Over three thousand public safety agencies rely on NICE Inform for incident recording, Quality Assurance and Incident Intelligence solutions to provide better service to citizens, partner agencies and DAs.
NICE Public Safety
 Best Investigation/Surveil-lance/Detection Product
Best Investigation/Surveil-lance/Detection Product
-
NICE Investigate
-
As early as the 1960’s police departments have envisioned ways to harness data and put it to work to improve policing but no one could have imagined then the sheer volume, velocity and variety of digital data that would be available today.
-
A study by IDC estimates that the size of the digital data universe is doubling two years, and policing is no exception.
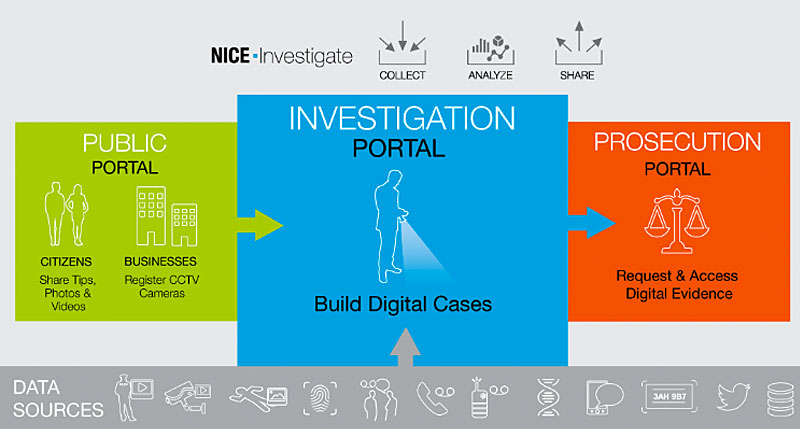
-
Technological innovations are creating more data every day – body-worn cameras, license plate readers, in-car cameras, surveillance cameras, gunshot detection, drones, internet connected devices, cell phones, social media.
-
While all this data has value, it has a downside too, having become a culprit of inefficiency, slowing down everyone in its path – from officers and records managers, to investigators and prosecutors. To drive efficiency up, police departments must cut down on the manual processes involved in managing digital data, and the data overload is coming at a time when departments are facing budget cuts.
-
As data grows and budgets decrease, police departments are turning to digital transformation to accomplish more with less.
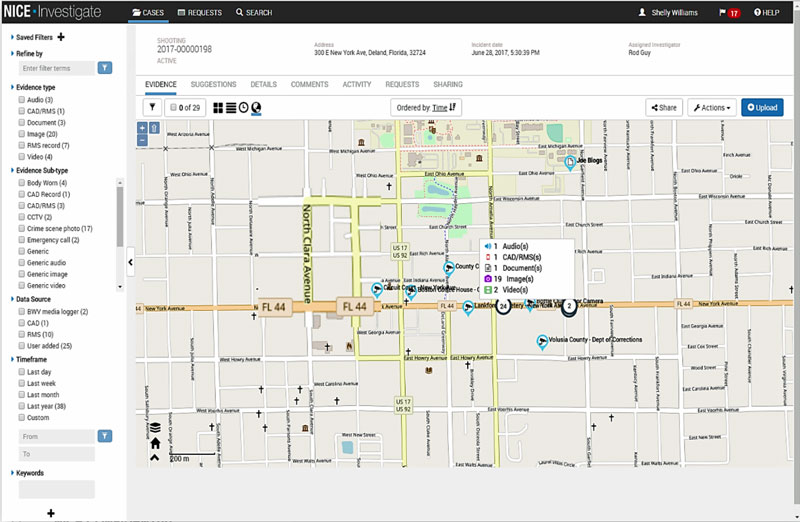
-
NICE Investigate can help police departments stretch their limited budget dollars without compromising service quality, by automating digital evidence collection, analysis and sharing.
-
Departments are able to realize a ten-fold plus savings in productivity, and use technology as a force multiplier to help officers spend more time in the community, and more time investigating cases, without adding extra overhead and costs.
-
In an age of COVID-19, officer safety is another key justification point for digital transformation. In-person interviews with eye-witnesses, driving from location to location to collect evidence, hand-delivering case files, all fly in the face of social distancing.
-
Beyond transforming how officers work, NICE Investigate is also enhancing productivity across the entire criminal justice continuum.
-
*NICE has now been recognized with Multiple Awards in their Fifth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards.
NYC Health & Hospital Corporation
 Best Emergency Response Program for Federal/State or Local
Best Emergency Response Program for Federal/State or Local
-
Bellevue Hospital Office of Emergency Management
-
Bellevue Hospital (officially NYC Health + Hospitals/Bellevue and formerly known as Bellevue Hospital Center) is the oldest public hospital in the United States.
-
It is also one of the largest hospitals in the United States by number of beds, and home to FDNY EMS Station 08.

-
Bellevue is a safety net hospital, providing healthcare for individuals regardless of their insurance status or ability to pay, and handles over half a million patient visits each year.
-
Mr. Boyd Dixon, the director of emergency management for Bellevue Hospital in the NYC Health+Hospitals System, created an emergency management program that contests with terrorist incidents, VIPs, the United Nations General Assembly, and multiple trauma cases.
-
This system was taxed to the fullest during the COVID-19 epidemic when the hospital had to manage transfer patients who required intensive care treatment, a massive need for additional Personal Protective Equipment (PPE), respirators, and shortages of staff and supplies.
-
The Hospital Incident Command System (HICS) that Mr. Dixon put in place managed all of this with efficiency and accuracy.

-
When Mr. Dixon was struck with COVID, the system he put in place continued to function throughout the pandemic, saving countless lives under the direction of Mr. Ghazanfer Ali Quddus.
-
*Bellevue Hospital was also recognized in the 2017 ‘ASTORS’ Homeland Security Awards Program.
OnSolve (First of Two)
Best Mass Notification System
-
OnSolve Critical Communications Suite
-
OnSolve Critical Communications technology is key in enabling enterprises, SMB organizations, and government entities to effectively monitor, manage, and respond to disasters and crisis events, such as wildfires, tornadoes, active shooters, IT issues and even pandemic-related notifications.
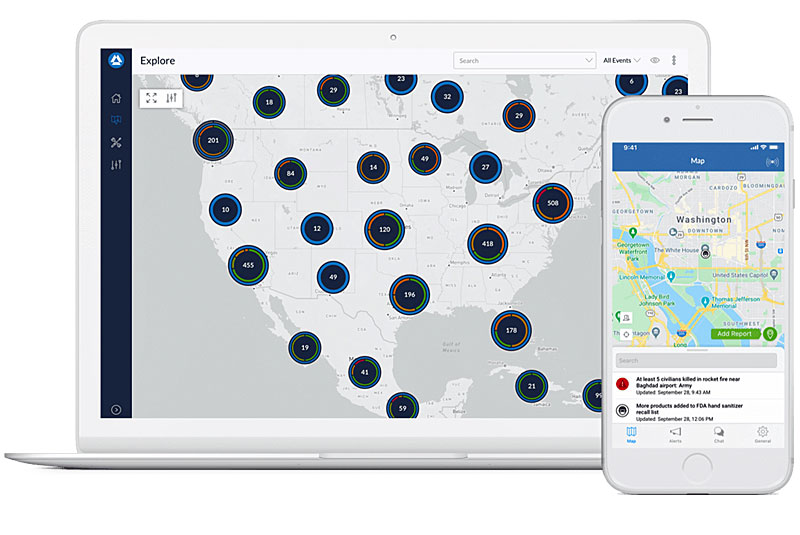
-
The company’s Critical Communications technology keeps citizens and employees safe and informed through targeted, real-time alerts and notification.
-
OnSolve’s Critical Communications software is relied upon by thousands of federal, local and state government entities and enterprises throughout North America which includes 50% of the top Fortune 500 companies, 7 of the 10 largest insurance providers, 3 of, 5 largest energy companies, 8 of 11 petroleum producers, and 3 of 5 largest commercial banks.
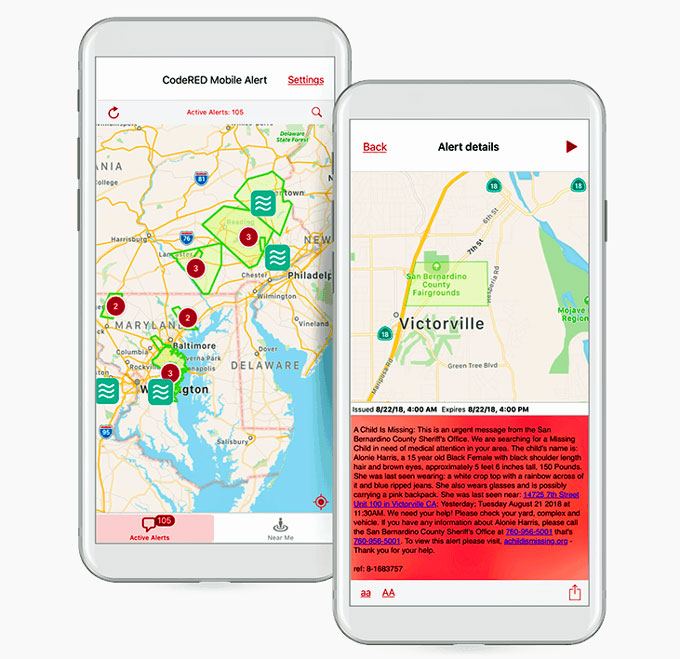
The CodeRED Mobile Alert app has hundreds of thousands of users, enabling clients to deliver public alert messages to mobile subscribers within their area.
-
In this year of uncertainty and unprecedented, evolving crises, OnSolve’s Critical Communications technology has sent 1.5 billion notifications, helped to find nearly 3,000 missing persons, and powers critical communications for 27,000 customers in 170+ countries worldwide.
-
Key technology features include geo-location, secure encrypted messaging, reporting and interaction, and messaging.
-
OnSolve’s Critical Communication CodeRED is a partner for National Center for Missing and Exploited Children, to power Amber Alerts.
-
OnSolve has also been recognized with Multiple Awards in the 2019 and 2018 ‘ASTORS’ Awards Program.
OnSolve (Second of Two)
Best Risk, Crisis Management Product (Tie)
-
OnSolve offers a suite of AI-powered risk intelligence, critical communications and incident management capabilities, so organizations can control the entire critical event management process, keep ahead of change, monitor disasters and be empower to make quicker, more accurate decisions during the times that matter most.
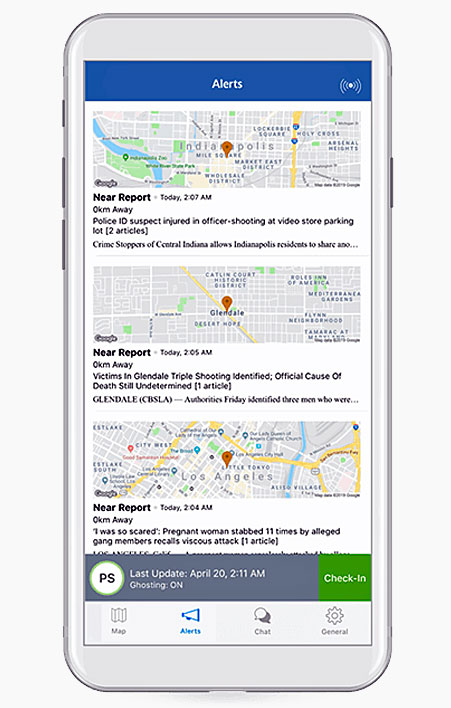
-
Organizations are able to gain risk intelligence information that allows them to prepare in advance for disasters and ensure business resiliency, send out mass alerts to notify the right people at the right time during a crisis, leverage a mobile incident management platform to retain full control during emergencies, and more.
-
Before, during, and after a critical event strikes, organizations now have the power of AI to inform timely and accurate situational awareness, the relevance and speed of leading mass notification services to manage critical communications, and the ability to holistically and seamlessly manage critical events through incident management – all from OnSolve.
-
OnSolve risk intelligence technology continues to keep people safe and informed, allowing them to better protect themselves, their employees and communities.
-
*OnSolve was also recognized with Multiple Wins in the 2019 and 2018 ‘ASTORS’ Awards Programs.
Orolia


-
VersaSync
-
Pos
itioning, Navigation and Timing (PNT) solutions ensure that government agencies and armed forces have the situational awareness data needed for rapid, informed decision-making in all conditions. -
At the heart of today’s government and military infrastructure lie precision time and frequency platforms, which are critical for continuous and accurate PNT data. Time-stamped data and synchronized networks support a wide range of diverse applications from video surveillance to radio communications, radar systems, and missile defense. Field operations present even greater challenges, with advanced technology requirements that must perform in remote and rugged conditions worldwide.

-
Orolia’s VersaSync is a mobile time and frequency reference solution to synchronize critical military and security operations where failure is not an option. Combining precision master clock technology with exceptional flexibility, VersaSync delivers accurate, software configurable time and frequency signals under any circumstances, including GPS-denied environments. Its small SWaP (size, weight and power) and rugged form factor make VersaSync ideal for mobile applications in the harshest conditions. Its small footprint and universal design enable easy integration of resilient timing and mission synchronization functionality into defense systems architecture.
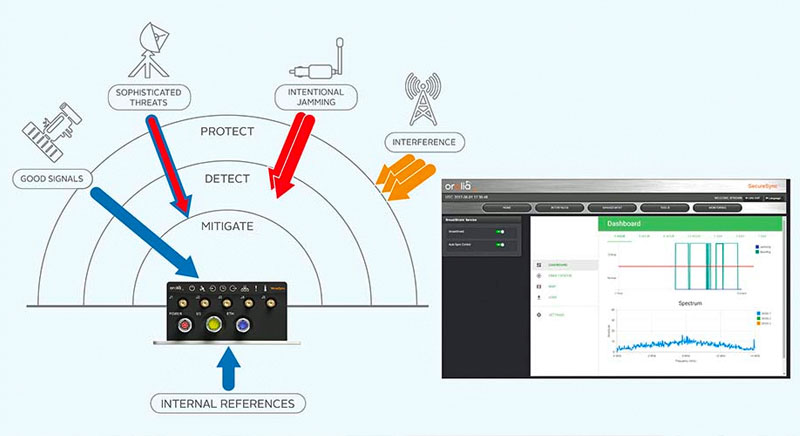
-
VersaSync also offers built-in PNT cybersecurity at no additional cost, as well as network-centric functionality including NTP/PTP precise time transfer over Ethernet with security protocols that prevent network vulnerabilities. For additional security, more options can be integrated including GPS jamming and spoofing detection software, SAASM encrypted signals and Low Earth Orbit satellite connectivity.
-
VersaSync currently supports a variety of DoD air, land and sea programs for time stamping and military network synchronization related to Test Ranges, ISR (Intelligence, Surveillance and Reconnaissance) Missions, UAV Payloads, Sensor Support (Radars, Sonars, Optronics) Tactical Vehicles Network Synchronization, and Cyber/Electronic Warfare.
-
*Orolia was also recognized with Multiple Wins in the 2019, 2018 and 2017 ‘ASTORS’ Awards Programs.
PC Matic
 Best Cyber Security Solution
Best Cyber Security Solution
-
PC Matic Pro
-
PC Matic Pro lacks complacency. The world of cyber threats continues to grow at an exponential rate, and PC Matic Pro believes security solutions must evolve as well.
-
In Q4 of 2019, approximately 54% of ransomware attacks were executed through remote desktop protocol (RDP) ports, a hole the cyber security industry must address.

-
PC Matic Pro did just that with the addition of RDP Lifeline, available at no additional cost for all PC Matic Pro customers and includes the ability to enable and disable RDP ports across the network, schedule when RDP ports are to be enabled, as well as displays a full report of all RDP port activity.
-
Additionally, IT professionals are notified in real-time via the alert system when a new, unauthorized RDP session attempts to execute, so they can then either enable or disable the session right there from their phone or computer.
-
PC Matic Pro also deploys a two-part security component to prevent unauthorized users from uninstalling its security solution which successfully limits the threat of an unauthorized user exploiting a hole within the network and removing the security solution to execute malicious activities.
-
*PC Matic was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Pelco


-
Pelco Spectra Enhanced 7 PTZ IP Camera
-
Pelco’s New Spectra Enhanced 7 PTZ IP Cameras are the latest product evolution in the legacy Spectra family providing fast and accurate pan and tilt, 30X optical zoom, up to 2MP 60 FPS video, with next-generation SureVision and deep learning capabilities.

-
The Spectra Enhanced 7 PTZ IP Cameras were purpose-built for difficult lighting conditions, leveraging true WDR, ultralow light performance, and image stabilization and always delivering sharp footage.
-
This solution also comes with Pelco Smart Compression and h.265 encoding, which enables lower bit rates without compromising image quality, so users can reduce storage and bandwidth costs by compressing up to 70% depending on complexity and level of motion in the scene.
-
The Spectra Enhanced 7 cameras include the Pelco Enhanced Analytics suite to enable users to quickly focus on situations needing immediate attention for faster response times, and with Deep Neural network capabilities, enables improved detection, tracking and counting of people and vehicles, which allows operators to review situations needing immediate attention or to analyze information to improve operation efficiencies.
-
The superior accuracy enabled by Deep Learning in Spectra Enhanced 7 PTZ IP Cameras, improves the camera’s ability to easily categorize objects within the scene.
Pivot3


-
Pivot3 Virtual Security Operations Center
-
The Pivot3 Virtual Security Operations Center (SOC) is an ideal solution to virtualize security workstations, optimize SOC operations and provide mobile and remote access.
-
The Pivot3 Virtual SOC delivers fully secure video streams to any device, anytime, anywhere, regardless of system manufacturer, so customers are able to overcome the limitations of manufacturer-specific PC workstations and reduce the need to invest in expensive, graphics-enabled clients workstations.

-
Customers are also able to reduce costs and mitigate risk by mobilizing their entire security suite. The flexibility of permissions-based distributed security data enables new operational models for surveillance.
-
*Pivot3 was also recognized in the 2018 and 2016 ‘ASTORS’ Homeland Security Awards Programs.
PlateSmart Technologies


-
PlateSmart ARES
-
PlateSmart ARES® ushered in a new era of software-only LPR that can work with virtually any video management system (VMS) or IP camera.
-
ARES AI-based automatic license plate recognition (ALPR)/vehicle recognition software includes cutting-edge deep learning technology which allows PlateSmart ARES to deliver true object recognition for more actionable vehicle data.
-
This includes the license plate as well as the state jurisdiction, vehicle make, color, orientation and type.

-
*PlateSmart Technologies has now been recognized in their Fifth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards.
Point 2 Point Communications Corporation


-
nanoFIBER armor
-
Airport information, security, video surveillance, alarms and fire suppression systems plus communication pathways fiber optics must pass through miles of overhead trays, countless wall conduits and pathways as well as conduits carrying miles of cable between buildings, concourse terminals and towers.

-
To support an airport’s infrastructure for communication and connectivity, in addition to their airport security systems – they cannot afford downtime due to faulty cables due to vermin attacks, crimping, and breaking, etc.
-
They require the smallest outer diameter (OD) fiber optic jacket qualified to protect the inner fragile glass fiber optics that can be prone to cracking and breaking, while also being cognizant of future cabling requirements without the need to disturb existing cables.
-
Point 2 Point’s newly CPR Certified LSZH Stainless Steel Armored nanoFIBER fiber optic cables provide the safest and Secure armored cable solution in aviation the market today.
-
The U.S. patented U.L. approved small OD high flex armor protects the fragile glass and the CPR rated LSZH jacket protects the environment.
-
The nanoFIBER fiber optic cable provides aviation with a very small OD secure cable that is crush resistant, hard to cut through, and safest for humans in a fire scenario.
-
The stainless-steel armored cable is impervious to harsh weather and ideal for indoor and outdoor environments, and when pulling nanoFIBER throughout aviation security and building management systems, the cable takes up minimal space and simplifies installation.
-
Additionally, nanoFIBER has the highest-level EU certification for low smoke zero halogen outer jacket that provides the best security to protect life in case of a fire at the airport or in a plane.
Probable Cause Solutions


-
Camera Canvass Tracker
-
Camera Canvass Tracker, a patented pending technology used to simplify canvassing for surveillance cameras, a task done by investigators everyday.
-
Camera Canvass Tracker, automatically builds a database of camera locations along with other pertinent information that allows to the investigator to calculate time differences, record the DVR/cameras, view database on a list or on a map and export the database when needed.
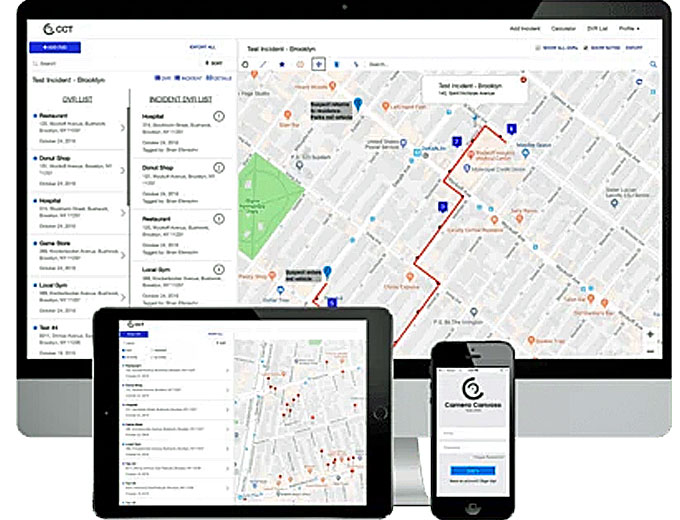
-
With Camera Canvass Tracker you can:
-
-
Map It – Create a centralized database of surveillance cameras within your jurisdiction. Search your database with our interactive geo-coded map.
-
Organize your Data – Store the name, address, and contact information for the custodians of the surveillance cameras. Save all DVR information for future reference.
-
Usable Data – Upload camera angle screenshots for future reference. Update the DVR data and add important notes for you and the rest of your agency to benefit from the next time you need it.
-
Calculate – Calculate those difficult time calculations down to the second. Saves valuable time and reduces the risk of human error. Creates a permanent record for future reference and strengthen testimony.
-
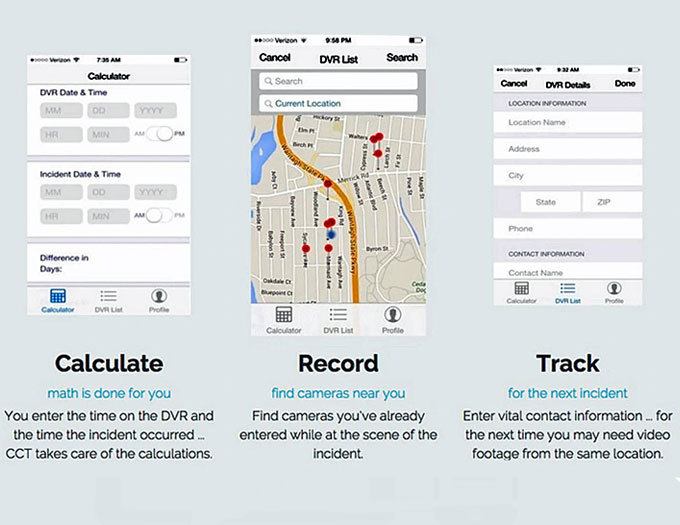
-
-
Incident Tracking & Custom Mapping – After creating your “Incident” Document the locations visited and create custom maps. Customize the map with a variety of pins and notes while plotting the course of travel.
-
Detailed Exports – Strengthen your case and testimony with proper documentation.
-
Group Plans – Share DVR data across your entire jurisdiction with everyone in your agency/group. Users can access the database from ANY internet capable device, including their desktop computer.
-
-
*Probable Cause Solutions was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
PureTech Systems (First of Five)


-
PureActiv
-
With expertise from 15 years of real-world deployments, and cutting-edge innovation, PureTech Systems patented Video Analytics are AI Deep Learning and Geo-spatially boosted providing real-time detection, classification, and tracking of perimeter security threats.
-
PureActiv integrates with a vast array of short- and long-range perimeter sensors such as radar, buried or on-fence fiber detection systems, and ground sensors either singularly or combining them to provide just the right level of protection to cost effectively meet the most secure perimeter requirements.
(Learn More about PureTech’s Automated Detection Systems for wide-area perimeter protection. Courtesy of PureTech Systems and YouTube.)
-
Many times, the right detection solution is not a single sensor technology.
-
In addition to its AI Video Analytics, PureActiv integrates with other perimeter sensors such as radar, buried or on-fence fiber detection systems, and ground sensors either singularly or combining them to provide just the right level of protection to cost effectively meet your perimeter requirements.
-
Additionally, given the extensible open-architecture approach, additional sensors can be added when needed or budgets permit.
-
The right sensors are easily integrated to ensure a perfect fit to your needs so your organization is not wasting money on too much or too little capability.
PureTech Systems (Second of Five)


-
PureActiv for Borders
-
Controlling national borders is an important part of national security, and the ability to effectively monitor vast areas in varied weather conditions and terrain, while accurately identifying potential threats at great solarwidistances is a complicated scenario.
-
The solution calls for knowledgeable personnel and accurate sensors that work together to quickly assess a situation and enable border agents to effectively intervene.
-
PureActiv® uses geo-spatial (GIS map-based) map technology to display camera, radar, and other sensors locations and their field-of-views, alarm events, and target tracks.
-
In addition to live and recorded video and live radar tracks, the user interface includes map tools such as the ability to add and share place-markers, point-and-click on the map to steer cameras to geolocations, fire laser range finders, range-to-target indicator, and a distance measuring tool.
-
This combination of real-time data on a map-based interface, provides the user a high level of situational awareness, which aides them in effective interdiction.
-
PureActiv boasts of some of the longest detection ranges in the industry (over 5 miles), which reduces system infrastructure; thereby lowering total cost of ownership.
-
Combining of tracks from multiple radars and PureActiv AI Video Analytics, eliminates duplicate tracks on the GIS map and alarms from the same intrusion events; reducing clutter and improving situational awareness.
-
Similarly, PureActiv Auto-verify™ feature ensures only detections that are AI verified as targets of interest are alarmed upon, eliminating up to 95% of nuisance alarms.
-
Additionally PureActiv integrates with GPS for blue force (friend/foe) classification and tracking to aid interdictions. This extensible solution enables organizations to start small and expand the system capabilities as time and budgets permit making PureTech a trusted leader in the security of the most critical perimeters and borders.
PureTech Systems (Third of Five)


-
PureActiv
-
PureTech Systems patented Video Analytics are AI Deep Learning and Geo-spatially boosted providing the highest probability of detection with the lowest nuisance alarm rate for electronically securing perimeters around facilities, infrastructures, and country borders.
-
PureActiv AI analytics also provides false alarm filtering for central monitoring stations; reducing false alarms by as much as 95%.
-
With expertise from 15 years of real-world deployments, and cutting-edge innovation, PureTech Systems patented Video Analytics are AI Deep Learning and Geo-spatially boosted providing real-time detection, classification, and tracking of perimeter security threats.
-
Additionally PureActiv integrates with GPS for blue force (friend/foe) classification and tracking to aid interdictions.
-
This extensible solution enables organizations to start small and expand the system capabilities as time and budgets permit making PureTech a trusted leader in the security of the most critical perimeters and borders.
PureTech Systems (Fourth of Five)
Best Maritime Perimeter Protection System
-
PureActiv
-
PureTech’s PureActiv wide area and perimeter protection solutions help port authorities improve the safety and security of seaports with a tangible Return on Investment.
-
PureTech’s wide-area perimeter protection solutions automate the protection of land and water-side perimeters to help ensure the safety and security of personnel and critical assets.

-
By detecting intrusion events at the perimeter, before they result in more catastrophic events, loss of life, and operational downtime, port authorities and law enforcement can intervene to deescalate situations and quickly return to normal operations.
-
The PureActiv system provides detection, alerting, and proactive deterring of potential safety and security events, which helps protect lives, cargo, and critical assets.
-
With 15 years of field deployments and continuous innovation, PureTech’s patented AI Neural Net based video analytics provides very high probability of detection with a very low nuisance alarm rate.
-
Additionally, PureTech Systems solutions include and combine integrations with other sensor systems to provide the most effective and affordable safety and security solutions. The solutions scale incrementally so that you only pay for the capabilities you need when you need them.
PureTech Systems (Fifth of Five)
Best Video Analytics Solution
-
PureTech Systems patented Video Analytics are AI Deep Learning and Geo-spatially boosted providing the highest probability of detection with the lowest nuisance alarm rate for electronically securing perimeters around facilities, infrastructures, and country borders. PureActiv AI analytics also provides false alarm filtering for central monitoring stations; reducing false alarms by as much as 95%.
-
PureTech Systems product solutions uses Convolutional, Neural Network Deep Learning and Geo-spatial data for high fidelity classification.

-
Higher accuracy – Industry leading Probability of Detection and low Nuisance Alarm Rate and object geo-location on map enhances situational awareness.
-
Seamless integration with market leading VMS systems including Genetec, Milestone, PureActiv AlertView, and others and camera agnostic, deploys on edge devices and/or servers.
-
Easily scales to fit your needs today and tomorrow.
-
*PureTech Systems was recognized with a Record 5 Wins in the 2020 ‘ASTORS’ Homeland Security Awards Program, and also won a Platinum ‘ASTORS’ Award in the 2018 ‘ASTORS’ Awards Program.
Rajant Corporation


-
Rajant ES1 BreadCrumb
-
Enabling highly mobile, IoT applications for public safety and security, the Rajant ES1 BreadCrumb is a compact, lightweight IP67 network node that provides Ethernet and Wi-Fi access point interfaces for critical frontline M2M and man-to-machine data, voice, and video communication.
-
Ideal for wearable technology, like the Vorbeck HD4 Harness, the Rajant ES1 connects Hot Zone to Cold Zone in the harshest communication environments in real-time.

-
The ES1 supports cryptographic options used for data and MAC-address encryption and per-hop, per-packet authentication.
-
With robust reliability, information is securely networked between on-site responders, their equipment, and Incident Command.
-
Deployment of the multi-band, multi-radio ES1 is easy and cost-effective.
-
Untethering emergency response, man and machine can be connected on-the-go for comprehensive situational awareness anywhere response is required – land, air, or sea – above and underground.
Rave Mobile Safety (First of Four)


-
Rave Guardian
-
The COVID-19 pandemic has made businesses, healthcare organizations and universities alike reconsider what employee and student safety really means.
-
However, even in uncertain times, clear communication and quick response can prove effective in any emergency. Businesses, schools and other institutions need easy-to-manage tools to facilitate that, now more than ever.
-
Rave Guardian, a leading custom-branded personal safety app, helps organizations quickly connect and protect employees, students or staff wherever they are located.
-
Rave Guardian allows organizations to communicate directly with different populations by providing two-way communications, safety assistance and resources during an emergency. With the Rave Guardian mobile app, employees, students and others can take a proactive approach to their safety through confidential tip texting, a virtual escort, an emergency call button and other resources that keep them informed.
-
Rave Mobile Safety helps Higher Education Connect, Engage and Safeguard your Community so they’ll be Prepared and become Empowered about their Safety. The customizable app helps drive engagement, while also providing better protection and information to employees, in both emergency and non-emergency situations, and while traditional communication channels work well during business hours, businesses especially need communication tools that can reach employees at any time.
-
Tools like Rave Guardian are critical amid the reopening process to ensure the safety of employees—who need updates on everything from specific guidance on who can be in the office when to urgent alerts about changes to operations if an employee tests positive for the coronavirus.
-
Without solutions like Rave Guardian, organizations will not be able to effectively reopen and stay open.
Rave Mobile Safety (Second of Four)


-
Rave Alert
-
The COVID-19 pandemic proved that the spread of misinformation happens quickly, and that businesses, universities and public agencies alike need to get the right information out to the right people quickly and reliably to get ahead of the spread of bad information.
-
In order to do this, these organizations need a reliable way to communicate effectively with their communities in both emergency and nonemergency situations, often through multiple channels, to ensure that the right message is fully disseminated.
-
Rave Alert, a leading emergency notification solution, is proven to help organizations deliver unlimited messages to unlimited recipients.
-
Rave Alert’s easy-to-use interface speeds up delivery, allowing organizations to reach all recipients quickly through text, email, voice calls, desktop alerts, public address systems, digital signage and more. Organizations trust Rave Alert, knowing it will get the right message to the right user from any internet-connected device in a matter of seconds.
(Hear from higher education CIOs how they have overcame their top challenges and increased efficiencies to support their higher education institutions’ goals. Courtesy of Rave Mobile Safety and YouTube.)
-
Rave Alert has been used throughout the pandemic by numerous states and cities, like Louisiana, Suffolk County, NY and the city of Seattle, and universities like Notre Dame to deliver reliable updates to citizens and students, providing guidance, critical updates and facts during this uncertain time not only to quell fears but to direct their attention to accurate information.
-
State and local governments, businesses, healthcare facilities and higher education institutions across all 50 states trust Rave Alert.
Rave Mobile Safety (Third of Four)


-
Rave Panic Button
-
Used in 47 states across the country, Rave Panic Button is the most widely-used and trusted school safety app.
-
By deploying Rave Panic Button in schools statewide, Louisiana, Oklahoma, Michigan, Delaware and Washington D.C. are providing equal protection to all their students, teachers and staff, regardless of their district or zip code.
-
Rave Panic Button has been credited with expediting emergency response efforts that ultimately saved a student’s life in Oklahoma when she had difficulty breathing at school, and getting immediate medical attention to an athlete who suddenly collapsed on a sports field in Arkansas by alerting a school nurse who was able to give CPR.
-
In seconds, Rave Panic Button clearly communicates an emergency to 9-1-1, on-site personnel and first responders simultaneously, improving communication and decreasing response times. And, as schools across the country weigh reopening plans amid the coronavirus outbreak, Rave Panic Button serves as a critical tool to communicate with teachers and staff, and to check in on their health status.
-
In the event of an on-site crisis—from a shooting threat to a medical incident–any authorized user can activate the Rave Panic Button mobile app by pushing one of the five emergency button types.
-
Rather than having a single option to press, users can notify 9-1-1 of a fire, medical emergency, active assailant or other emergencies that require an immediate response. When one of the buttons is pushed, 9-1-1 call takers and first responders can view detailed caller location, floor plans, entrance and exit locations, emergency contacts and key procedures to help coordinate a more effective response.
Rave Mobile Safety (Fourth of Four)
 Best Risk, Crisis Management Product
Best Risk, Crisis Management Product
-
Rave Prepare
-
The coronavirus pandemic has impacted vulnerable populations on a massive scale.
-
The elderly, those with respiratory illnesses and others with underlying conditions that put them at greater risk were the hardest hit when the virus surged this spring.
-
Yet often, public safety agencies don’t know the location of these vulnerable populations in their communities, making it difficult to proactively identify and communicate with those at risk and respond to their needs appropriately.
-
Rave Prepare, Rave’s web-based vulnerable needs registry, helps emergency managers, public safety and health leaders understand the individuals most at-risk within a community to enable faster coordination and more efficient communication during a critical event.
-
Rave Prepare enables public safety and health agencies to plan ahead and proactively respond to disasters and other emergencies, including power outages, transportation interruptions, evacuations, community health crises, pandemics and shelter resource planning.
-
As the coronavirus pandemic surged across the country, Rave Prepare was quickly updated to ensure public safety and health agencies had the insight into their communities needed for managing their response to the virus, which includes identifying individuals who are self-quarantined or have pre-existing conditions or are over the age of 65, identifying trends and potential hotspots, and mobilizing resources where needed most.
-
*Rave Mobile Safety was also recognized with Multiple Platinum Award Wins in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Regroup Mass Notification


-
Regroup Mass Notification
-
Regroup Mass Notification® empowers better mass communication to keep people safe and informed during critical and daily events.
-
Founded at Stanford University in 2006, the award-winning, cloud-based platform is used every day by thousands of organizations to save lives, improve safety for entire communities, respond to potential hazards, prepare for emergencies and more.
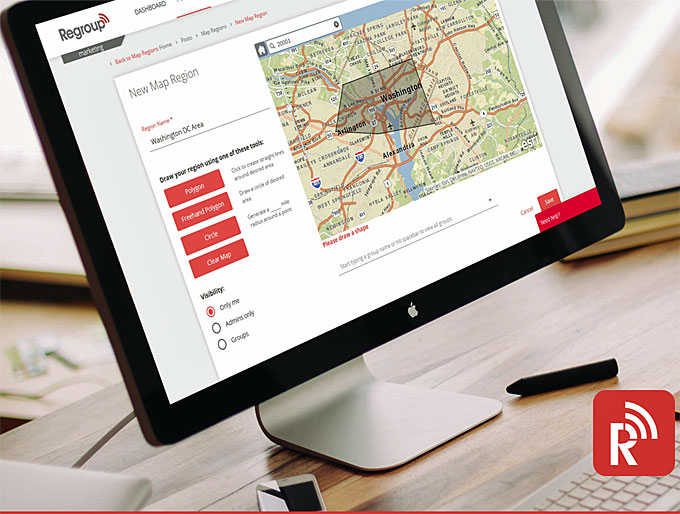
-
Regroup’s easy-to-use system enables administrators to send up to 20,000 voice calls, 65,000 SMS, 100,000 emails, and 540,000 push notifications per minute, rapidly alerting large groups of recipients to danger.
-
Administrators can also expand their reach by distributing messages via websites, PA systems, digital signage and more. Whether used for emergency or routine communications, Regroup Mass Notification helps organizations across America communicate quickly to improve homeland security, strengthen operational resilience, mitigate risk, and thrive in an increasingly unpredictable world.
-
As our nation and the world is reeling from the impacts of the COVID-19 Pandemic, Regroup has responded proactively to make our system available to as many American cities, counties, and states as possible by offering a 90-day risk-free access to the platform, at cost.
-
As the United States faces daily growth in the number of cases and an uncertain economic future, local governments are seeking reliable ways to quickly and efficiently communicate with citizens, staff, service providers and visitors about supply distribution, aid, testing sites, and more.
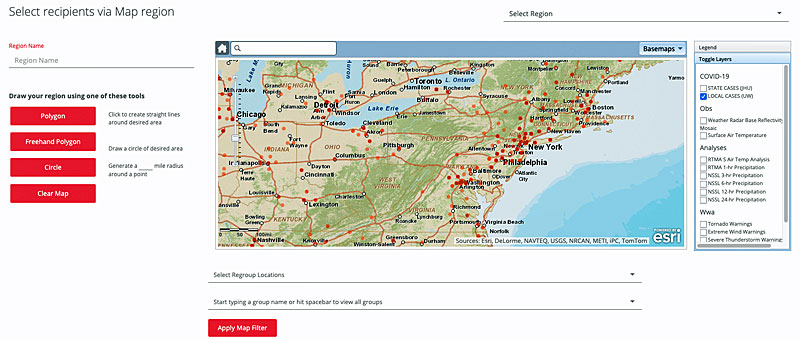
-
Regroup has released new COVID-19 mapping layers that work in conjunction with their geo-targeted messaging capabilities in response to the pandemic, which allow admins to visualize the spread of COVID-19 at state and local levels, enabling them to view the impacts of the pandemic as they relate to their own staff, offices, and other important locations.
-
Regroup has developed this new tool in an effort to equip clients to respond to the current global pandemic, increase situational awareness, and inform their communities, which they’ve made a free addition to the platform rather than an optional upgraded feature.
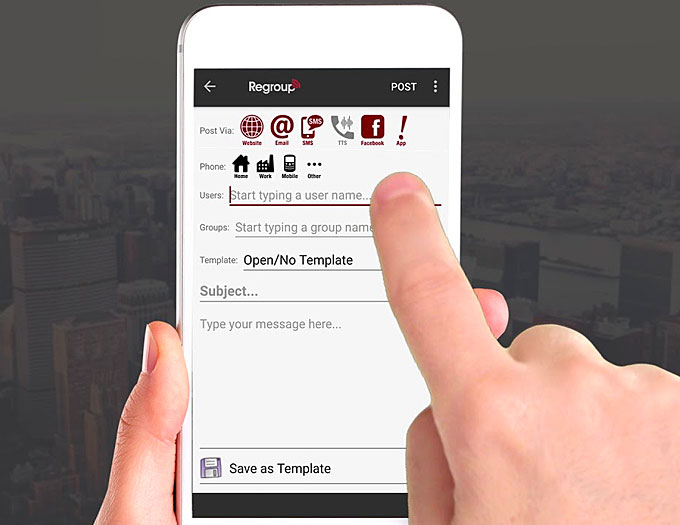
-
The new version of AlertManager enables admins to send and receive multimodal alerts via text/SMS, text-to-speech, voice, email and push notifications while being able to access instant reporting for detailed delivery statistics. Regroup has also provided enhanced biometric security features to ensure only authorized individuals can send alerts.
-
Regroup Mass Notification‘s dedication to making our nation more resilient and secure has never been more evident than within the last year, with decisions and actions to aid throughout the Coronavirus Pandemic which is impacting so many people, communities, and businesses in our nation.
-
*Regroup Mass Notification was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
SafeLogic


-
CryptoComply
-
CryptoComply has quickly become the preferred encryption module deployed by technology vendors into the Public Sector.
-
By combining cryptographic technology with FIPS 140-2 validation expertise, SafeLogic has perfected a drop-in crypto bundle for regulated industries.
-
Vendors develop their products around the CryptoComply core, focusing on what they do best, while the SafeLogic team ensures FIPS 140-2 validation, the benchmark certification for encryption in the federal government.
-
The validation (administered by NIST) is delivered in less than 8 weeks, a huge competitive advantage for clients who are facing rivals in procurement RFPs as well as any pursuing additional compliance initiatives like FedRAMP, Common Criteria, DoDIN/UC APL, or the upcoming CMMC.
-
*SafeLogic was recognized in the 2018 ‘ASTORS’ Homeland Security Awards Program.
Select Engineering Services (First of Two)


-
Automatic Injury Detection (AID) system
-
The Automatic Injury Detection (AID) system provides help in seconds when the sensing panel has been pierced by a bullet, knife or shrapnel.

-
When an AID flexible mylar sensor panels (front & back, comfortably inserted into the wearer’s bullet proof vest) is pierced by either a bullet, knife or shrapnel from an IED, the communications module will sense the break in the circuit and automatically sends an emergency alert with GPS location to phone, radio or communication system.
-
The automated and instant emergency alerts help save lives by improving the response from medics and backup personnel to stop, apprehend or contain the attacker, even when the officer is incapacitated.
Select Engineering Services (Second of Two)
 Best Alert Notification System
Best Alert Notification System
-
Personal Emergency Transmitter (PET)
-
The Personal Emergency Transmitter (PET), is a wearable device that automatically sends alert text messages, with your personal info and a link to your GPS location in the event of an emergency.
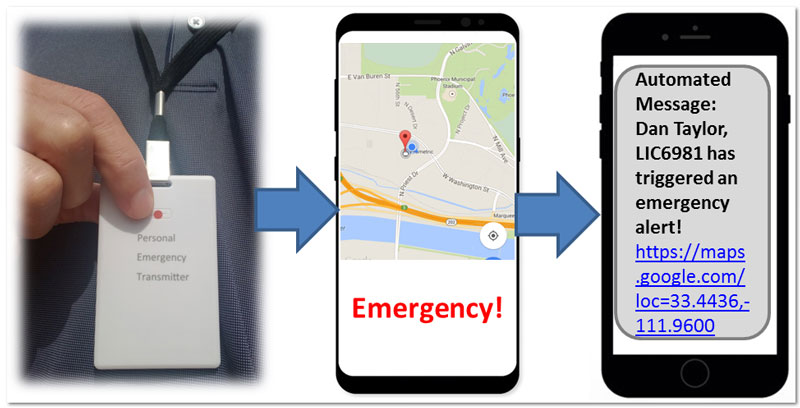
-
The PET system provides a covert method to summon help when you are faced with a dangerous situation and it’s impossible to call help without alerting your attacker (i.e. reaching for your cell phone).
-
The PET system allows you to avoid escalating a potentially dangerous confrontation and have backup on the way in seconds.
-
*Select Engineering Services was also recognized with Multiple Award Wins in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Semperis (First of Three)


-
While back-up, business continuity and disaster recovery can be different for every company, involving numerous strategies and tactics, there is no doubting the need for solutions to support over-arching BDR plans.
-
Almost daily, organizations of all sizes are getting hit with ransomware threats, for example, which puts whole systems, databases, files and more at risk.
-
Nation state attacks and unexpected weather events have also prompted companies to be more prepared for down-time and quick recovery to keep their businesses up and running.
-
Semperis Active Directory Forest Recovery (ADFR) fully automates the entire forest recovery process with just a few clicks – ensuring fast, clean, and painless restores, and their “cyber-first” recovery approach saves millions of dollars in unnecessary business interruption.
(Recover an entire Active Directory forest with just a few clicks. Automate every aspect of forest recovery, such as cleaning up metadata, rebuilding the Global Catalog, and restructuring site topology. Avoid human errors and reduce downtime to minutes instead of days or even weeks. Avert costly business interruption. Courtesy of Semperis and YouTube.)
-
Recovery has traditionally taken a back seat to prevention and detection for malware protection, but today – with ransomware being the leading cause of organizational IT disruption – rapid, automated restoration of sensitive systems and data is the most effective and proactive defense against corporate Armageddon.
-
For organizations that can’t tolerate lengthy outages or degraded service, Semperis Active Directory Forest Recovery (ADFR) orchestrates a fully automated forest recovery process – prohibiting errors, reducing downtime to minutes instead of days or even weeks, and eliminating the risk of malware re-infection.
Semperis (Second of Three)
 Best Intrusion Detection & Prevention Solution
Best Intrusion Detection & Prevention Solution
-
Semperis DSP
-
Business applications on-premises and in the cloud rely on Active Directory, making it a critical piece of your IT infrastructure.
-
Directory changes must be scrutinized, and unwanted changes – whether accidental or malicious – immediately undone.
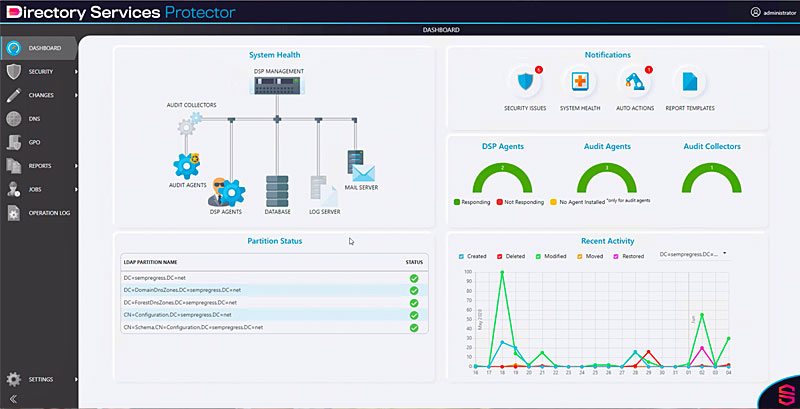
-
Unlike tracking tools that rely on agents and security logs, Semperis Directory Services Protector (DSP), tracks changes and eliminates holes in your audit log and allows you to quickly identify and undo suspicious changes, so you can minimize disruption to users and damage from cyberattacks.
Unlike recovery tools that rely on backups, Semperis DSP provides instant recovery (no need to mount or restore a backup). So, while other tools might make it possible to restore individual objects and attributes, Semperis DSP makes it practical to actually do so.
In addition, Semperis DSP can restore to any point in time (not just to a previous backup).
Semperis (Third of Three)
Best Cyber Security Solution
-
Today, cyber disasters inflict more business damage than natural disasters and strike more frequently. Wipers like NotPetya, Shamoon, Destover and ransomware such as Petya, WannaCry, and LockerGoga have crippled organizations around the globe, encrypting their IT infrastructure and sending them back to manual operations until, or if, they can recover their systems.
-
In a cyber disaster, Microsoft’s Active Directory (AD) – the distributed security system that controls user authentication and systems authorization in over 90% of the world’s medium and large organizations – is mission-critical because it’s foundational to recovering everything else on the network.
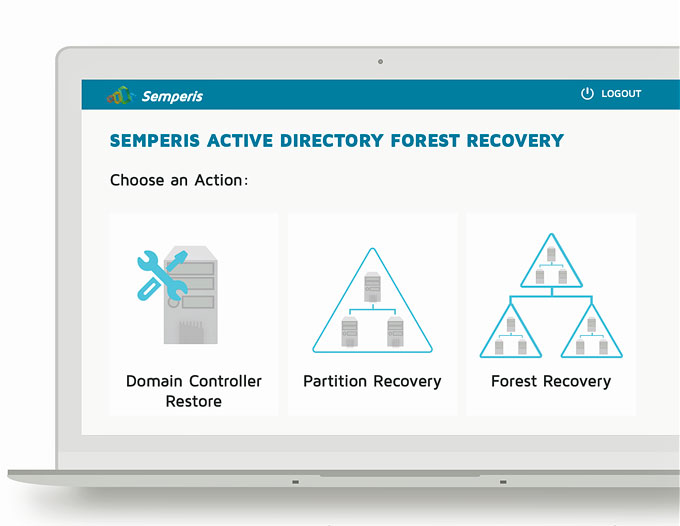
Restoring Active Directory manually would take days or even weeks – and you could still be left with malware in your environment. But with Semperis ADFR, you can get your business back in business in less than an hour.
-
Legacy protocol for AD recovery demands a resource-intensive and error-prone process that cost organizations days or even weeks of downtime however, Semperis Active Directory Forest Recovery (ADFR) fully automates the entire forest recovery process with just a few clicks – ensuring fast, clean, and painless restores. Our “cyber-first” recovery approach saves millions of dollars in unnecessary business interruption.
-
With its Semperis ADFR product, Semperis introduced the only “cyber-first” approach to AD disaster recovery, purpose-built to combat today’s evolving cyber threat landscape.
-
Being the only “cyber-first” solution on the market purpose-built to recover Active Directory (AD) from cyberattacks, Semperis Active Directory Forest Recovery (ADFR) is postured to continue experiencing rapid adoption from organizations big and small, and today protects millions of identities.
-
The product has been adopted by customers in the Fortune 500, government, financial, healthcare, and other industries worldwide.
ShotSpotter (First of Two)


-
ShotSpotter® Connect™ is AI-driven software that helps law enforcement deter crime by pro-actively directing patrol resources to specific locations that have the highest likelihood of crime that day.

Research shows that high visibility patrols are an effective deterrent to crime. Agencies receive precise locations to patrol based on AI that is superior to traditional hot spot analysis.
-
Connect develops risk assessments for future crimes by collecting and analyzing three sources of data: historical crime data from a police jurisdiction; public data such as weather, transportation points, locations of parks, schools, and liquor establishments; and exclusive ShotSpotter gunfire data.
-
Machine learning determines the areas of highest risk and the forecasts are turned into data-driven patrol plans by shift and beat every day, and disseminated electronically to officers in the field, and carefully meters out recommended time spent on a directed patrol, suggests tactics by crime type, and automatically randomizes patrol locations to minimize the possibility of over or under policing any area.
-
ShotSpotter Connect has been proven to reduce crime by 33%, measured over a period of 90 days in one part of a district where patrol officers use the software and compared to crime levels where officers in a neighboring part of the district do not use the software.
-
ShotSpotter Connect gives command staff unprecedented insight into where their patrol cars have been, the tactics officers are using, and the results they are getting which enables them to better understand which tactics have the highest impact on crime.
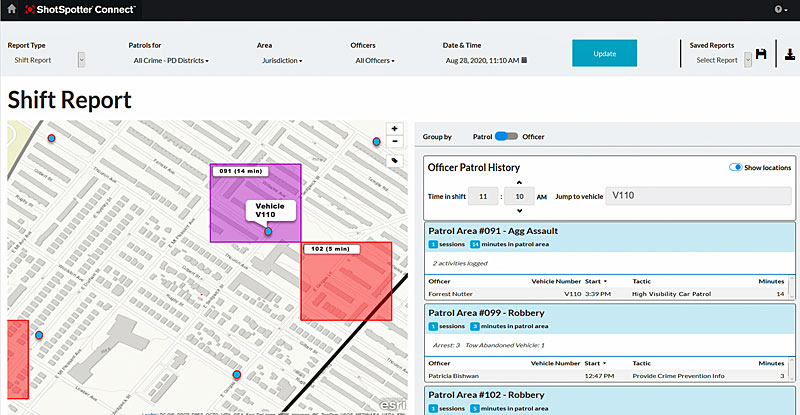
A robust suite of reports provide command staff with insights into where officers were and what they were doing that help optimize patrol strategies and ensure officer accountability.
-
In these times of reduced police forces due to the pandemic, ShotSpotter Connect helps agencies use their existing resources most efficiently, so police patrols can be at the right place at the right time to deter crime before it happens and keep our communities safer.
ShotSpotter (Second of Two)
 Best Gunshot Detection Solution
Best Gunshot Detection Solution
-
Many cities across the country face a gun violence problem and 80% of gunshot incidents are never reported to 911.
-
ShotSpotter’s technology detects, locates and alerts law enforcement agencies to gunfire incidents in real-time.
-
It is used by more than 100 cities across the U.S., including nearly half of which are top 50 metro areas including Cincinnati, New York City, Miami, Denver and Oakland.
(See a brief overview of ShotSpotter Flex – Gunshot Detection for Cities. Courtesy of ShotSpotter and YouTube.)
-
In 2019, ShotSpotter detected over 140,000 gunshot incidents across the US with a 97% accuracy rate.
-
ShotSpotter’s real-time alerts notify police precisely when and where gunshot incidents occur, within 60 seconds, with critical data such as number of rounds fired, number of shooters, and type of weapons used.
-
This results in a faster, more accurate response to the scene to better recover evidence, interview witnesses, and attend to gunshot victims—improving overall police effectiveness.
-
By working with ShotSpotter, law enforcement agencies can better connect with their communities and bolster their mission to protect and serve.
-
ShotSpotter was also recognized in the 2019 and 2018 ‘ASTORS’ Awards Programs.
Simeio Solutions, LLC
 Best Identification Management Solution
Best Identification Management Solution
-
Simeio IO is a single-pane-of-glass identity platform that provides one platform for managing identities, simplifies the operation of complex functionalities and supports multi-vendor identity and access management (IAM) platforms for privileged access management (PAM), federated identity management (FIM), and identity governance and administration (IGA).

-
Simeio IO is a complete and powerful IAM virtualization solution available via web and mobile interfaces. Instead of multiple, disparate systems, versions and interfaces to learn, Simeio IO gives you a single unified web-based interface with easy-to-use dashboards and workflows for managing identities and access privileges.
Simeio IO doesn’t replace your IAM systems – it simplifies the way you manage them, making it easier and less costly to support IAM, security, enterprise and SaaS applications from multiple vendors, and to freely add or switch to different versions or different vendors – including migrating to “as a service” solutions – without changing the way you manage identities, control access privileges, or monitor and audit their usage.
Singlewire Software (First of Three)


-
-
-
InformaCast Fusion with Microsoft Teams
-
-
InformaCast Fusion with Microsoft Teams from Singlewire Software gives the 500,000 organizations utilizing Microsoft Teams the ability to leverage the mass notification power of InformaCast Fusion for security and communication.
-
In an emergency, every moment matters, and organizations need communication systems that reach all their people quickly, and the faster a message goes out, the more time security personnel have to respond to and manage the situation at hand.
-
(InformaCast emergency mass notification integrates with Microsoft Teams to simultaneously bring key personnel into a Microsoft Teams Incident Response Channel to manage crisis situations. Courtesy of Singlewire Software and YouTube.)
-
-
Using InformaCast Fusion, Microsoft Teams users can now trigger mass notifications that reach all of their people without ever leaving the Teams interface.
-
Because Teams are leveraging InformaCast Fusion, notifications get sent to a wide range of devices and systems including other Microsoft Teams users, mobile phones, desk phones, IP speakers, overhead paging, door access controls, desktop computers, digital signage, strobe lights and more, increasing the likelihood that everyone is aware of potentially dangerous situation.
-
Following the alert distribution, key security team members can also receive a prompt to join a Microsoft Teams channel where they can collaborate and follow up on the situation.
-
InformaCast Fusion with Microsoft Teams can be used to enhance security with emergency alerts in K12, higher education, enterprise businesses, healthcare, manufacturing and other industries that need assistance reaching all of their people quickly during a crisis, and use it to activate lockdowns, share details about approaching severe weather and send alerts about active shooter situations, as well as other emergency scenarios they are likely to face.
-
Singlewire Software (Second of Three)
 Best 911 Recording & Analytics
Best 911 Recording & Analytics
-
InformaCast Fusion with CallAware gives organizations the ability to record and receive alerts about 911 calls placed from within their buildings.
-
When 911 is dialed from an on-premises phone, it will trigger an alert via InformaCast, which can go out throughout an entire building or hit a select group of personnel who can best respond to the situation.

-
Alerts can be delivered to overhead speakers, other desk phones, desktop computers, mobile devices, email and more to ensure that no one misses a message. The alert can include the name of the phone that placed the call, as well as the time the call was placed, and the number of the dialer so people within the organization can deploy a response team to assist with the situation.
-
When an emergency occurs, the two most important factors are speed and reach. InformaCast helps reach everyone within an organization that can assist with information that a 911 call has been placed as soon as it is dialed. This means organization leaders can respond quickly and can direct first responders when they arrive.
-
To help better understand the situation taking place and to assess responses after an incident has occurred, CallAware can also record the 911 call so organization leaders can review it.

-
InformaCast Fusion also gives system administrators the ability to listen into in-progress calls if they being recorded to get a better context for the situation taking place so they can assess the severity of the event and determine an appropriate response.
-
CallAware alerts can be customized to include the groups and details most relevant for an organization to provide assistance and isn’t limited to monitoring for 911 calls. The system can be configured to monitor and send alerts for whatever number is relevant to an organization, with flexibility that offers a wider range of safety applications that organizations can deploy to protect their people.
Singlewire Software (Third of Three)
Best Risk, Crisis Management Product (Tie)
-
InformaCast Fusion is used by organizations to assist with risk and crisis management, by preparing for all kinds of emergency situations from active shooters to severe weather, to pandemics and fires.

-
To adequately manage these crises when they occur, organizations need to be able to communicate critical safety information to keep people safe, minimize panic and chaos, and help operations return to normal as quickly as possible.
-
InformaCast offers organizations the ability to customize messages for any kind of scenario they need to prepare for and can designate exactly what groups and devices receive messages to maximize efficiency when working to manage a crisis.
-
InformaCast Fusion delivers information to mobile and on-premises devices such as desk phones, overhead speakers, mobile devices, desktop computers, digital signage and more, with text and audio messages, to ensure no one misses a message.
-
InformaCast Fusion helps organizations fulfill their duty of care and know they have a viable tool in place that can be easily deployed to assist with risk and crisis management.
-
*Singlewire Software was also recognized in the 2019 ‘ASTORS’ Homeland Security Awards Program.
Siklu and Skywire
Best COVID-19 Communications Solution
-
Pandemic Response – Temporary Gigabit Wireless Access Networks
-
Implementing a wireless network to establish or expand broadband communications services in emergency situations (such as replacing the capacity lost in damaged networks and establishing new broadband connections to locations such as field hospitals in parks and temporary hospitals in large convention centers or even large ships docked in the harbor) can be a tricky endeavor.

-
It’s not uncommon for these wireless networks to struggle to handle large amounts of data not the least of which is generated by cameras, temporary Wi-Fi hotspots, IoT-enabled medical equipment and increased services for first responders, which results oftentimes, in network that lags, or complete failure.
-
More and more wireless broadband, often at Gigabit speeds, comes courtesy of millimeter wave (mmWave) networks (especially those operating at 60 GHz and above), which provide fiber quality and reliable communications without interference, unlike lower, legacy band wireless spectrum (e.g., 5 GHz), which is open and often times over saturated with traffic.

-
mmWave wireless technology performs well as it uses narrow beams which are basically immune to radio interference and network jamming and feature high security as well, and stands in contrast to wide-beam wireless systems that need to use multiple coding and frequency hopping strategies to perform in dense areas.
-
Furthermore, mmWave systems and their narrow beams offer more flexible connection options as emergency response networks can be set up in a relatively short time using point to multipoint systems with built-in “beam steering,” which greatly reduces the engineering requirements.
-
In uncertain times like today we don’t know where or what the next crisis or emergency will unfold, however we do know that there will be a critical need for reliable gigabit communication services, and mmWave solutions deliver.
-
Siklu was also recognized in the 2017 ‘ASTORS’ Awards Program.
Siren Operated Sensors (SOS)


-
-
-
SOS Silent
-
SOS Silent Emergency Gate Access Systems are the fastest way for emergency vehicles to gain access to gated facilities, campuses and residential communities.
-
-
-
This pure and simple system allows responders to focus on driving and on the emergency ahead without pushing a remote, looking up a code, stopping to use a key or changing the channel on their radio to trigger the gate.

-
Using RFID the SOS Silent System will open gates quickly, silently, and automatically when emergency response vehicles come within range of the gate and can be adjusted from 10 to 600 feet to customize each gate entrance.
-
The SOS Silent also has a back up entry system to open with the “YELP” siren.
-
SOS Silent ensure first responders can get to community members in need with no life-threatening delays. No stopping, no getting out of the vehicle, no codes to remember, no remotes to push, no keys to lose, and no cost to the municipalities.
-
*Siren Operated Systems was also recognized for Four Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Programs.
SolarWinds Worldwide, LLC (First of Three)


-
Threats to IT networks continue to accelerate and evolve and while enterprising hackers from external sources test the robustness of network security parameters, internal threats in the form of careless and malicious insiders remain a major and ongoing concern.
-
It is critical that agencies take steps to combat these threats—and SolarWinds® Security Event Manager (SEM), formerly Log & Event Manager is a powerful weapon. This comprehensive SIEM solution delivers dynamic, real-time log collection and analysis for immediate and actionable threat intelligence.
(See a brief, high-level overview of the capabilities of SolarWinds Security Event Manager and how you can use the SIEM tool to detect threats, quickly respond to cyber incidents, and report compliance from a consolidated interface. Courtesy of Solarwinds Worldwide and YouTube.)
-
SEM can capture and analyze log data in real-time from multiple sources and specific incidents, allowing users to quickly identify and remediate threats, uncover policy violations, and resolve vital network issues, and users can quickly shut down breached systems, block IP addresses, kill unexpected processes, and disable user accounts.
-
SEM includes an easy-to-use, point-and-click interface and data visualization tools to quickly search log data, perform event forensics, and identify the cause of security incidents or network problems.
-
Like all SolarWinds software, SEM is built to scale and can support IT environments of all sizes, and employs a node-based license model that allows users to stay within their planned budgets as they deploy and expand their IT infrastructures across multiple data centers and geographies.
-
SolarWinds SEM is used by nearly every U.S. federal civilian agency, DoD branch, and intelligence agency. It is available on the U.S. General Services Administration (GSA) Schedule, and other contract vehicles.
SolarWinds Worldwide, LLC (Second of Three)


-
-
-
SolarWinds Access Rights Manager
-
-
-
SolarWinds Access Rights Manager (ARM) is designed to assist IT and security admins to understand and act on high-risk access and minimize the impact of insider threats.

SolarWinds® Access Rights Manager (ARM) is designed to deliver customized Active Directory (AD) and Azure AD reports—showing who has access to what, and when they accessed this data.
-
SolarWinds ARM enhances security by monitoring, analyzing, and auditing Active Directory®, Azure AD, Exchange™, SharePoint, OneDrive, and file servers to see what changes have been made, by whom, and when those changes occurred, and customized reports can be generated to demonstrate compliance with most regulatory requirements.
-
The solution also provisions and deprovisions users using role-specific templates to help assure conformity of access privilege delegation in alignment with security policies.
-
ARM helps prevent data leaks and unauthorized changes to sensitive files and data through visualization of permissions on file servers.
-
SolarWinds ARM reduces IT workload through a web-based self-service portal, put access rights of data in the hands of data owners instead of admins.
SolarWinds Worldwide, LLC (Third of Three)
Best Access Control & Authentication System
-
-
-
SolarWinds Network Configuration Manager
-
-
-
Successful threat mitigation requires continuous real-time monitoring of network configuration changes and potential policy violations, and alerts for automated detection and remediation of harmful security violations is essential.
-
SolarWinds® Network Configuration Manager (NCM) offers compliance auditing and leverages baselines and differential viewers to help ensure that devices are configured correctly, with an automated change control workflow, bulk configuration updates, and automatic vulnerability assessments to help teams efficiently identify and fix vulnerabilities – all in a single solution.
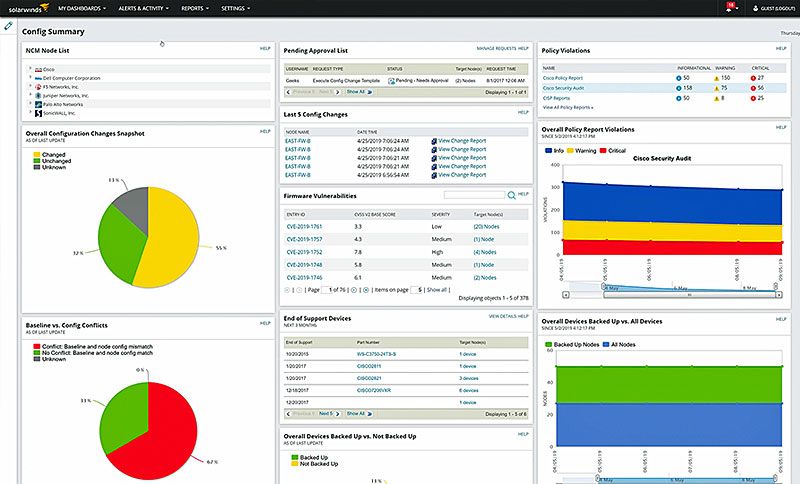
-
NCM offers several unique and powerful features to help agency IT professionals protect against vulnerabilities and prevent unauthorized network configuration changes, and uses Cisco® IOS® and ASA vulnerability scanning and NIST FISMA, DISA STIGs, and DSS PCI compliance assessments to improve network security.
-
The software itself features hundreds of built-in compliance reports to help meet major auditing authority requirements, including DISA STIGs, NIST FISMA, and more, and THWACK®, SolarWinds’ online user community, provides a number of free report templates that can be used to prepare for an inspection.
-
NCM is built for IT environments of all sizes and can easily scale to meet growing infrastructure needs. Licensing depends on the total number of devices an IT pro manages, including firewalls, routers, switches, or any other device that supports remote access and a command line interface.
-
SolarWinds has been recognized with Multiple Awards in all Five Annual ‘ASTORS’ Awards Programs.
Spectrum Solutions (First of Two)
 Best COVID- 19 Testing Device (Saliva)
Best COVID- 19 Testing Device (Saliva)
-
COVID-19 testing is a two-part process, the first requires the collection of a viable biosample, which historically has been a painful nasal swab, and the second is the sample processing by a lab.
-
Spectrum has innovated a new viral-testing solution by engineering a technically superior saliva collection device for both DNA and viral RNA molecular diagnostic applications, and has demonstrated the devices unique ability to inactivate the live virus from collected samples.
-
The Spectrum SDNA-1000 device eliminates the painful nasal swab process with a pain-free saliva collection process – which has been FDA cleared for at-home testing – significantly reducing exposure to health care providers.
- This 100% Made in America patented preservation solution maintains sample integrity by eliminating bacterial contamination that could compromise test results, then stabilizes the sample for shipping and transport over long distances and at extreme temperatures for over 14 days.
-
Spectrum SDNA-1000 delivers 100% inactivation of the live virus once cap is secured and solution is mixed, reducing risk of exposure to anyone who handles the samples downstream including transport, medical, and clinical laboratory staff.
(Utah-based Spectrum Solutions saliva collection device used in new COVID-19 testing. Courtesy of abc4utah and YouTube. Posted on Apr 6, 2020.)
Spectrum Solutions (Second of Two)
 Best COVID- 19 Detection Innovation
Best COVID- 19 Detection Innovation
-
Unlike other threats to our national security, the COVID-19 pandemic is being fought on the front lines of medical advancement and innovation.
-
When the leaders of Spectrum Solutions learned that the threats to America were heightened by a global shortage in testing supplies, they stood up and entered the fight by introducing a creative solution that not only changed the scope of how Americans and others around the world are tested for the virus, but also potentially how a wide variety of diseases are diagnosed in the future.

-
At the onset of the pandemic, the gold standard for testing required a healthcare worker to insert a long naso-pharyngeal swab deep into the patient’s nasal cavity then turning of the swab to collect a sample of secretions from the uppermost part of the throat, behind the nose.
-
The worker then removes the swab, risking potential exposure to themselves, and placing it into a vial which is then transported to a lab for testing.
-
This method of testing required a healthcare worker to be within close proximity to potentially infected patients and directly handle live virus samples.
-
Furthermore, the global inventory of swabs and personal protective equipment (PPE), was in critically short supply which stalled and stymied efforts for widespread testing.
-
Spectrum SDNA-1000 saliva collection devices where able to completely eliminate the need for nasopharyngeal swab to collect and preserve saliva samples, creating an altogether new and completely different diagnostic option.
(Engineered to significantly reduce user self-collection error, and exposure risk to medical professionals this technically superior saliva DNA/RNA collection and preservation device from Spectrum DNA is FDA cleared for at home COVID-19 testing. Courtesy of Spectrum Solutions and YouTube.)
-
Independent studies from industry-leading institutions like Rutgers University, Yale, Princeton, Johns Hopkins, MD Anderson, Stanford, and many others from across the nation quickly poured in, each echoing support that saliva collected and preserved with Spectrum’s SDNA-1000 was a remarkable solution.
-
Studies included side-by-side tests to compare swabs and saliva, and although the nasopharyngeal swabs continued to return false-negative results, the saliva collection samples with the Spectrum’s SDNA-1000 devices were able to consistently detect the present infection, which the swab had missed.
-
Researchers studies showed that saliva was, in fact, more sensitive to detecting the infection, which increased testing accuracy, especially in the very early stages of infection. Key knowledge to have when you consider that every day an infected person goes undiagnosed, they continue the spread the virus to others unknowingly putting people at risk.
TCOM, L.P.
Best Persistent Aerial Monitoring Solution
-
TCOM’s lighter-than-air Best Persistent Aerial Monitoring Aerostats are providing the U.S. Homeland Security and U.S. Army communities with the most cost-effective aerial persistent surveillance solutions with the promise of integration of new ISR sensors that can watch borders, maritime, and other scenarios efficiently and with cutting-edge innovation.

-
Persistent surveillance aerial aerostats remain in critical military demand, particularly at a tactical level as part of an all of the above doctrines of Intelligence, Surveillance & Reconnaissance (ISR).
-
For example, in late September 2019, the US Department of Defense awarded a $979 million contract to TCOM – to perform work on the Persistent Surveillance Systems – Tethered (PSS-T) program, a range of medium and large tactical aerostats that provide ISR, force protection and communications capabilities to a range of users.
-
The PSS-T aerostat fleet provides a flexible and affordable capability comprising both medium and large size aerostats to provide persistent, integrated, networked, and multi-sensor information collection via long periods of operation at an altitude that maximizes lines of sight and field of regard on onboard systems.
-
TCOM’s systems support requirements for Homeland Security on the U.S. southwestern border, as well as in Afghanistan, Iraq, and the Horn of Africa, providing persistent surveillance, force protection, and ISR missions, as well as communications extensions.
-
The primary advantage of the platforms is their ability to provide extended time on mission and at an advantageous cost, with aerostats providing great flexibility for operating multiple capabilities simultaneously.
-
TCOM, LP was also a recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
West Virginia American Access Control Systems

Best Pedestrian Entrance Control
-
The American Access Control Systems (AACS) Series 400 makes security easy.

-
Designed to easily replace existing swing doors without additional construction, the AACS Series 400 is a fully customizable, ADA compliant security portal solution, trusted to meet the high-security needs of America’s most secure facilities for years.
-
Additionally, the AACS Series 400 portal with Temperature Scanning capabilities automatically scans the user’s body temperature, and if the temperature exceeds the threshold the user is denied access to the building.
-
AACS security portals are made in the USA with US components.
-
*AACS was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
X.Labs (First of Three)

Best Law Enforcement Tactical Equipment Product
-
Anchored on the Blockchain, ShoX is a breakthrough in less-than-lethal ballistic products for law enforcement, military and anti-terrorism operations.
-
ShoX is a human electro muscular incapacitation (HEMI) projectile which aims to bridge the gap between less lethal tools such as nightsticks, tasers or bean bags and lethal weaponry.
-
ShoX offers a superior range of up to 100 feet, can incapacitate a target for a minimum of thirty seconds, can penetrate light materials and attach to the human body with a dual barbed probe system.
-
Unlike a taser, ShoX is a non-tethered electro-shock round capable of being fired from conventional less lethal weapons including Pepperball launchers.

-
A ShoX bullet discharges an electrical shock at 260 pulses per second over a 30 second period at a pulse duration of 100 microseconds to deliver an average current of 5 milliamps, which upon impact and disrupts the nervous system.
-
No external source of power is needed to charge or keep the projectiles charged.
X.Labs (Second of Three)
 Best Thermal, Infrared Camera System
Best Thermal, Infrared Camera System
-
Feevr is a quick and effective artificial intelligence (AI) based system for screening and detecting individuals with elevated temperature in a crowd.

-
A fever is an indicating symptom of an infectious disease like COVID19 (Coronavirus), and the solution enables the user to identify individuals with a fever efficiently and effectively.
-
When Feevr detects an individual with high or abnormal temperatures, it will be captured on the screen and an alert will be triggered discreetly to notify the authority to bring the potential infected individual in for further medical examination.
-
Feevr is non contact handheld detection device that does not make direct body contact with individuals being tested, minimizing the risk of infectious disease cross-contamination.
X.Labs (Third of Three)
 Best Handheld Mobile Device Solution
Best Handheld Mobile Device Solution
-
Restaurants now have less tables to increase the distance between customers, health clubs and gyms now require gloves before members can workout, and businesses need to ensure their employees are in good health, as an extra security measure before they even scan their badges.
-
Even the mom and pop ice cream shops will have to take action to ensure customers that enter their shop are safe, such as taking precautionary screening measures to ensure customers are safe to serve, and which may present a higher health risk.
-
But unlike airports and other companies that are used to funneling large crowds through required screening measures, most small businesses are not prepared resulting in long lines and even longer wait times just to get in.
-
To combat this, X.Labs introduced the Precheck app so that customers of the company’s flagship B2B product “Feevr”, can now offer their employees, customers, and fans FEEVR Pre-Check.
-
FEEVR Pre-Check allows employees, students, customers and fans to take their temperatures on their own and sync the results to access systems like employee/school badges, tickets, reservations, and more.
 *X.Labs (formerly SWORD), is also a Returning Premier Sponsor for the Third Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a Platinum-Award Winner in their Fifth Annual ‘ASTORS’ Awards Program.
*X.Labs (formerly SWORD), is also a Returning Premier Sponsor for the Third Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a Platinum-Award Winner in their Fifth Annual ‘ASTORS’ Awards Program.
Yubico
Best Cyber Security Solution
-
YubiKey 5C NFC
-
With billions of stolen credentials on the illegal market and rampant phishing scams, secure logins are a must-have feature on modern devices, including mobile.

-
Today, the strongest form of account protection is offered by hardware authenticators, which provides the best defense against phishing in combination with a seamless user experience.
-
In fact, a recent Google study found that hardware security keys were the only method to stop account takeovers 100% of the time.
-
The Yubikey 5C NFC is one of the most long-awaited and top-requested keys among the Yubico community.
-
Now that modern work-flows typically involve moving between devices to complete tasks and access applications, the YubiKey 5C NFC is the all-in-one security key that provides users with flexible authentication options across modern devices.
-
The YubiKey 5C NFC hardware authenticator has a USB-C connector, is NFC enabled, and provides multi-protocol support. While there are other USB-C and NFC compatible security keys, the YubiKey 5 Series is the only line of authenticators to support six authentication protocols in one device, which includes WebAuthn, FIDO2, FIDO U2F, OTP, PIV (smart card), and OpenPGP.
-
This unique multi-protocol support, combined with USB-C and NFC functionality, enables the YubiKey 5C NFC to work out of the box with hundreds of services, delivering strong two-factor or passwordless authentication for simple and secure logins. For this reason, it is difficult to find a competitor delivering a singular solution more flexible, cost-effective, simple, and secure than the YubiKey 5C NFC.
-
Yubico was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Program.
2020 ‘ASTORS’ EXCELLENCE AND GOVERNMENT AWARD RECIPIENTS
U.S. Department of Homeland Security (DHS)

Excellence in Homeland Security
-
The Blue Campaign is a national public awareness campaign, designed to educate the public, law enforcement and other industry partners to recognize the indicators of human trafficking, and how to appropriately respond to possible cases.
-
Blue Campaign works closely with DHS Components to create general awareness training and materials for law enforcement and others to increase detection of human trafficking, and to identify victims.
-
Located within the Office of Partnership and Engagement, the Blue Campaign leverages partnerships with the private sector, Non-Governmental Organizations (NGO), law enforcement and state/local authorities to maximize national public engagement on anti-human trafficking efforts.
-
Blue Campaign’s educational awareness objectives consists of two foundational elements, prevention of human trafficking and protection of exploited persons.
Department of Homeland Security (DHS) Science and Technology (S&T) Directorate

Excellence in Homeland Security
-
The COVID-19 pandemic is a global threat with life and death consequences, the enormity of which many of us have never seen before.
-
It is also a scientific challenge in need of innovative solutions and S&T is using every tool at its disposal to join the fight; including harnessing the knowledge of it’s experts on technology deployments, international collaboration, scientific breakthroughs, and support for America’s frontline workers.
-
S&T has focused its efforts on laboratory research and providing valuable resources to inform the broader response community and help keep front line responders safe.
-
Highlights of S&T’s response efforts can be found in our Battling the Invisible Enemy report.
DHS S&T Chemical Security Analysis Center (CSAC)

Excellence in Homeland Security
-
CARD, a chemical synthesis and chemical informatics centric data system (e.g. boiling point, melting point, toxicity, or spectroscopic information) containing both unclassified and classified data, is accessible from a classified website maintained on a server hosted by the Department of Defense.
-
The website is available to appropriately cleared personnel from DHS, Department of Justice (e.g. FBI), other United States Government interagency offices, and state and local agencies, and provides information on how chemicals of interest could be produced.

-
There is a detailed description of how each chemical is prepared to include information relevant to each step, the reagents and reactants that are needed and the conditions necessary for the reactions to take place, such as time, temperature, mixing—like a recipe.
-
If law enforcement were to discover a table full of labeled chemicals in a clandestine laboratory, they would put these names as a list in CARD to find out what the suspects are making – illicit drugs, poisons, or warfare agents.
-
CARD can be used the other way around. If police find an illicit drug or a warfare agent, they can search in the website to see what chemicals can be used to make it.
-
For example, if police capture a suspect with a vial of sarin gas (a nerve agent that can kill in minutes after inhalation), they can use CARD to determine which chemicals are used to make it. Police can then search the suspect’s illicit lab for those chemicals and obtain further evidence of wrongdoing.
DHS S&T National Urban Security Technology Laboratory (NUSTL)

Excellence in Public Safety
-
-
Hoist Rescue Gloves for Aerial Rescue
-
-
Rescue helicopter hoist operators need gloves to protect the hand that guides the hoist cable during rescue descents and ascents, using a significant amount of force to mitigate the cable swinging for situations from hurricane evacuations and dive rescues to rescuing stranded hikers on a mountain side, missions vary and no two are ever alike.
-
A partnership between S&T and Higher Dimension Materials, Inc. (HDM) resulted in an enhanced rescue hoist glove with increased flexibility, durability, and dexterity.
-
The glove design uses cushioning materials offering protection to the thumb crotch (purlicue) area, the index and little finger, and a leather guard to alleviate inconsistent glove performance when wet,” said Jones-Holt.
(See the enhanced Hoist Rescue Glove in action. Courtesy of DHS Science and Technology Directorate and YouTube.)
Department of Homeland Security (DHS) Science and Technology (S&T) Directorate

Excellence in Homeland Security
-
The Slash CameraPole is a self-triggering platform with wireless data retrieval to detect and give warning of suspicious activities at the U.S.-Canada border, specifically a cleared stretch of land at the border that is approximately 20-feet wide, 1,349 miles long, and is referred to as the “Slash.”

-
This man-made, treeless zone is mandated by the International Boundary Commission and presents a formidable surveillance challenge, against such threats as illegal crossings, drug and illegal contraband smuggling and human trafficking.
-
Using the Slash CameraPole system, Border Patrol has been able to establish an advanced border surveillance capability where none existed before.
-
Partnering with MIT Lincoln Laboratory and several private companies to create the Slash CameraPole with numerous ingenious features, such as solar panels and a back-up fuel cell system make it independent of the power grid, multiple infrared cameras (two long-range, one foreground, and one base imager with a fisheye lens) mean it doesn’t miss a thing.
-
An in-ground cement foundation and electrical enclosure ensures it can withstand brutal winter conditions. Should its unobtrusive appearance manage to draw the attention of would-be vandals, the Slash CameraPole is resistant to small arms fire and other tampering.
-
The Slash CameraPole also employs advanced motion detection algorithms and automated alerts designed to improve classification of targets and lower the chance of false alarms from factors such as wild animals or vegetation moving in the wind.
-
*DHS S&T Programs have now been recognized in their Fifth Annual ‘ASTORS’ Awards Program.
Centers for Disease Control and Prevention (CDC)

Excellence in Homeland Security
-
The CDC has provided Law enforcement and EMS who must make contact with individuals confirmed or suspected to have COVID-19 with guidance to help safeguard their health while performing their duties.

-
Different styles of PPE may be necessary to perform operational duties. These alternative styles (i.e. coveralls) must provide protection that is at least as great as that provided by the minimum amount of PPE recommended.
-
Law enforcement who must make contact with individuals confirmed or suspected to have COVID-19 should follow CDC’s Interim Guidance for EMS.
-
To Learn More, please visit the CDC’s answers to frequently asked questions about law enforcement and COVID-19 by clicking this link.
U.S. Immigration and Customs Enforcement (ICE)

Excellence in Homeland Security
-
ICE Enforcement and Removal Operations (ERO) is charged with enforcing the nation’s immigration laws in a fair and effective manner.

-
ERO identifies and apprehends removable aliens, detains these individuals when necessary and removes illegal aliens from the United States.
-
ERO transports removable aliens from point to point, manages aliens in custody or in an alternative to detention program, provides access to legal resources and representatives of advocacy groups and removes individuals from the United States who have been ordered to be deported.
-
ERO’s mission is to protect the homeland through the arrest and removal of aliens who undermine the safety of our communities and the integrity of our immigration laws.
Department of Justice (DOJ) Office of Personnel Management (OPM)

Best Federal Government Security Program
-
-
Federal Risk Management Process Training Program
-
-
The Federal Risk Management Process Training Program (FedRMPTP), Newly available Online – is Interagency Security Committee certified for Facility Security Officials, Federal Security Supervisors and those involved with Federal facility acquisition, construction, and renovation projects.

-
On October 19, 1995, six months after the Oklahoma City bombing of the Alfred P. Murrah Federal Building, President Clinton issued Executive Order 12977, creating the Interagency Security Committee (ISC) to address continuing government-wide security for federal facilities.
-
Prior to 1995, minimum physical security standards for non-military federally owned or leased facilities.
Federal Bureau of Investigation (FBI)

Excellence in Homeland Security
-
The IC3 serves as the FBI’s central hub to receive, develop, and refer criminal complaints regarding the rapidly expanding occurrences of Internet crime
-
IC3 provides the public with a reliable and convenient reporting mechanism to submit reports of suspected Internet-facilitated criminal activity and to develop alliances with law enforcement and industry partners.
(Actress Kirsten Vangsness, who plays tech-savvy FBI analyst Penelope Garcia on the show Criminal Minds, is promoteing the awareness of Internet crimes and scams and encourages the public to report suspected criminal cyber activity to the FBI’s Internet Crime Complaint Center (IC3). Courtesy of the FBI and YouTube.)
-
Information is analyzed and disseminated for investigative and intelligence purposes to law enforcement and for public awareness.
-
Since 2000, the IC3 has received complaints crossing the spectrum of cyber crime matters, to include online fraud in its many forms including intellectual property rights (IPR) matters, computer intrusions (hacking), economic espionage (theft of trade secrets), online extortion, international money laundering, identity theft, and a growing list of Internet facilitated crimes.
-
It has become increasingly evident that, regardless of the label placed on a cyber crime matter, the potential for it to overlap with another referred matter is substantial.
-
IC3 develops leads and notifies law enforcement agencies at the federal, state, local and international level.
Federal Protective Service in Collaboration with the Argonne National Laboratory

Best Risk, Crisis Management Solution
-
-
Modified Infrastructure Survey Tool (MIST) – COVID-19 Telematics Capabilities
-
-
DHS’s Federal Protective Service (FPS) provides integrated security and law enforcement services–including conducting security assessments and detecting and mitigating threats–to over 9,500 federal facilities. To accomplish this mission, FPS leverages the Modified Infrastructure Survey Tool (MIST), a joint solution developed in partnership with Argonne National Laboratory.

-
Argonne and FPS have continuously sought ways to improve the tool’s ability to assess, detect, and mitigating threats, and this year, no threat was more pervasive in this country than COVID-19.
-
To confront the threat that COVID-19 posed to the FPS workforce, MIST was enhanced to allow FPS Headquarters and FPS Management to track and display each federal building affected by COVID-19, and to analyze local hospitals and EMS facilities in relation to federal buildings and office locations.
-
Additionally, the map capability within MIST was expanded to allow for many additional layers, allowed FPS a granular understanding of the number of facilities impacted by the virus, and much more.
-
Ultimately, the new COVID-19 telematics capabilities offered FPS decision makers the ability to make better informed decisions on moving personnel and security equipment to best protect people and property, while ensuring safety of their staff.
-
The Federal Protective Service and Argonne National Laboratory have also been recognized in the 2019, and 20188 ‘ASTORS’ Awards Programs respectively.
-
To Learn More, please visit the DHS Federal Protective Service at https://www.dhs.gov/topic/federal-protective-service.
John Verrico

Excellence in Homeland Security
-
-
Chief of Media and Community Relations, DHS Science & Technology Directorate
-
-
John Verrico, who is also the former President of the National Association of Government Communicators, has nearly 40 years of experience as a public affairs professional in federal and state government agencies, working extensively in media, community and employee relations, with significant emphasis in science, engineering and the security fields.

-
A retired Navy Master Chief Journalist, John’s career has been focused on helping government agencies tell their stories and share important news with the public. He takes special care to ensure government information is accessible and that complex issues are easily understood.
-
John has also worked as a freelance journalist, stand-up comic, and motivational speaker, among other fields where he learned not to take life too seriously and to experience everything life has to offer.
-
As an under-sized youth and victim of bullies, John found hope in classic monster movies and ‘B’ flicks where he learned that the little guy could win. Drawing from these lessons, John helps every day unsung heroes get recognition for their work.
-
As an international speaker and leadership coach, John helps people keep their motivational torches lit so they can face their own ‘monsters.’
Kathleen Kiernan, Ed. D

Excellence in Homeland Security
-
-
Kiernan Group Holdings CEO
-
-
Dr. Kathleen Kiernan is the Founder and CEO of national security, education, risk management and compliance firm Kiernan Group Holdings, Chair Emeritus of InfraGard National Members Alliance, and adjunct faculty member at Johns Hopkins University and Naval Post Graduate School.

-
Preparedness without Paranoia® the experience-based training in awareness, preparedness, response and recovery training for active assailant and workplace violence prevention is delivered on a learning management system.
-
GOT Preparedness® (Got Online Training), was built specifically for dispersed and remote workforces and we have trained thousands of individuals domestically and internationally.
-
She has delivered operational and educational capabilities across the globe and developed a methodological based approach to the resiliency cycle at an individual and organizational level.
Joseph Pangaro

Excellence in Public Safety
-
-
CEO at True Security Design
-
-
As the owner and CEO of Pangaro Training and Management, Joseph Pangaro, concentrates on providing the best and most up to date training programs for the Law Enforcement, School and Business communities.

-
True Security Design (TSD) law enforcement training programs are centered around supporting today’s modern professionals’ by teaching them vital skills through courses designed to engage and empower its participants.
-
A 27-year veteran police lieutenant and experienced school security director, Lt. Pangaro is uniquely qualified to provide law enforcement training programs that are centered around supporting today’s modern professionals’ by teaching them vital skills through courses designed to engage and empower its participants.
-
Pangaro Training also teaches in police academies and police agencies throughout New York, New Jersey, and Pennsylvania.
New Jersey City University

Excellence in Public Safety
-
NJCU is one of the few programs nationally in higher education designated an Intelligence Community Center of Academic Excellence (CAE) per the Office of the Director of National Intelligence (ODNI) and a Cyber Defense CAE per the National Security Agency.

-
The Department of Professional Security Studies focuses on a student–centered, scholar-practitioner approach to education.
-
It’s mission is to facilitate access, create opportunities and provide a supportive environment for achieving academic success through learning and appreciation of subject matter, professional and personal growth and the development of identified and marketable global and disciplinary competencies.
-
The New Jersey City University (NJCU) Cybersecurity program is an interdisciplinary center for cybersecurity education, training and research, which aims to provide current and future professionals with the knowledge and skills necessary to strive and compete within the cyber security community outreach.
-
NJCU students’ foundation is built through their degree program, certificates and research opportunities.
New York City Emergency Management

Excellence in Homeland Security
-
-
New York City Emergency Management (NYCEM), is under the guidance of Commissioner Deanne Criswell, a former FEMA official and head of OEM for the city of Aurora, CO, who is responsible for oversight and development of the city’s emergency management plans.
-
NYCEM regularly tests plans by conducting drills and exercises, and responds to emergencies to ensure that other agencies not only follow these plans, but to foster communication amongst the responding agencies.
-

-
-
NYCEM also operates the city’s Emergency Operations Center (EOC) where city, state and federal agencies join representatives from the private and nonprofit sectors to coordinate complex responses to emergencies and disasters.
-
The agency also developed and runs the Notify NYC emergency alert program, by which citizens can sign up to receive phone and email alerts about emergencies and events happening in their neighborhoods.
-
NYCEM is also the administrator of New York City’s community emergency response teams. Each community emergency response team (CERT) is coterminous with one or more New York community boards.
-
The agency also maintains the Citywide Incident Management System which is based on the National Incident Management System.
-
U.S. Coast Guard Auxiliary

Excellence in Public Safety
-
U.S. Coast Guard Auxiliary (CGAUX) boating courses provide instruction to boaters at all levels, from the fundamental to the advanced.

-
The agency’s courses (virtual and classroom) are taught by experienced and knowledgeable CGAUX instructors committed to the highest standards of the U.S. Coast Guard Auxiliary.
-
They are offered in two modalities: virtual, video conference with CGAUX Virtual PE Instructors, and classroom setting with CGAUX PE Instructors.
2020 ‘ASTORS’ PERSON OF THE YEAR
Douglas Haines

-
‘2020 ASTORS Person of the Year’
-
Extraordinary Leadership in Homeland Security and Public Safety
-
-
Doug Haines, owner of Haines Security Solutions, LLC (HSS), is a United States Air Force veteran with over 45 years of law enforcement and security related experience, which includes teaching building design principles to architects, engineers, facility managers, planners, and security professionals.

-
He has served as a distinguished judge on the Annual ‘ASTORS’ Homeland Security Awards Judges Panel for Five Years, and is a regular expert contributor to AST, sharing his years of experience and insights with our 75K+ readers.
-
Doug’s company HSS, is recognized as a center of expertise within the security community for risk assessment, providing services for many federal; State, local government agencies and private companies around the globe, and is a founding member of International Centers of Security Training Excellence (ICSTE).
-
Each ICSTE member company offers courses in one of several security verticals yet provides a location for other members to present their courses upon request.
-

Haines River Park Training Facility – Los Angeles
-
At its River Park facility in Oxnard, CA architects, engineers, facility managers, planners and security professionals learn about antiterrorism countermeasures in building design, the integration of security technologies in the built environment, and risk analysis strategies.
-
The CPK-United BV (also an ICSTE founding member) training facility in Hilversum, The Netherlands gears its curriculum towards fashion retail, hospitality (hotel and nightclubs) and port security guard activities and executive protection.
-
Tactics for patrolman and SWAT are taught by former police officers at the Greenville, NY training center, where a firing range and urban mock-up are on site.
-

Haines Hilversum training facility
-
In 2017, HSS’s Physical Security Engineering Training and Certification (PSET&C) program was recognized as the Best Homeland Security Education Program, by American Security Today and received a coveted Platinum ‘ASTORS’ Award.
-
Doug is also the author of ‘The Solutions Matrix: : A Practical Guide to Soft Security Engineering for Architects, Engineers, Facility Managers, Planners and Security Professionals’.
To Learn More visit here. To check out the book, please click this link.
-
More information about PSET&C, ABRA, CAIRA, ICSTE or other services can be found on the company’s website at www.hainessecuritysolutions.com.
2020 ‘ASTORS’ EXTRAORDINARY LEADERSHIP AND INNOVATION AWARD RECIPIENTS
Automatic Systems
-
2020 Extraordinary Leadership and Innovation Award
-
For over 50 years Automatic Systems has enabled innovative secure access management, for fluidity of movement, security of people and infrastructure through the design and manufacture of automated pedestrian, vehicle and passenger access systems.
X.Labs

-
2020 Extraordinary Leadership and Innovation Award
X.Labs has worked to create a world class team with a mission to save lives, by developing the world’s first affordable, safe and non-invasive, mobile threat detection platforms integrating the latest in state-of-the-art technologies to identify concealed threats and known threat actors.
ATI Systems (Acoustic Technology Inc.)

-
-
2020 Extraordinary Leadership and Innovation Award
-
-
ATI Systems has demonstrated a continued commitment to designing, manufacturing, integrating, and installing innovative, reliable, cost-effective, and compact emergency warning and notification systems to colleges and universities, communities, ports, refineries, power plants, military bases all over the world.
Attivo Networks
-
2020 Extraordinary Leadership and Innovation Award
-
Attivo Networks has illustrated the company’s continued innovation in the field of advancing deception technology, developing advanced network security threat detection technology for deployment on premise or as a cloud service, as well as their ongoing development and investment to the ThreatDefend™ Deception & Response Platform.
Congratulations to each and every one of our outstanding 2020 ‘ASTORS’ Homeland Security Awards Winners!
Why the 2020 ‘ASTORS’ Homeland Security Awards Program?
American Security Today’s comprehensive Annual Homeland Security Awards Program is organized to recognize the most distinguished vendors of physical, IT, port security, law enforcement, and first responders, in acknowledgment of their outstanding efforts to ‘Keep our Nation Secure, One City at a Time.’
In 2019 over 200 distinguished guests representing Federal, State and Local Governments, and Industry Leading Corporate Firms, gathered from across North America, Europe and the Middle East to be honored among their peers in their respective fields which included:
- The Drug Enforcement Administration (DEA)
- National Center for Missing and Exploited Children (NCMEC)
- United States Marine Corps
- The Federal Protective Service (FPS)
- Argonne National Laboratory (ANL)
- United States Postal Inspection Service
- DHS S&T
- United States Marshals Service (USMS)
- The Port Authority of New York & New Jersey Police (PAPD)
- The Department of Justice (DOJ)
- The New York State Division of Homeland Security & Emergency Services (NYS DHSES)
- United States Border Patrol
- AlertMedia, Ameristar Perimeter Security, Attivo Networks, Automatic Systems, Bellevue University, BriefCam, Canon U.S.A., CornellCookson, Drone Aviation, FLIR Systems, Hanwha Techwin, HID Global, IPVideo Corp., Konica Minolta Business Solutions, LenelS2, ManTech, Regroup Mass Notifications, SafeLogic, SolarWinds, Senstar, ShotSpotter, Smiths Detection, TCOM LP, Trackforce, Verint, and More!
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace with over 75,000 readers at the Federal, State and local levels of government as well as firms allied to government.
American Security Today brings forward a fresh compelling look and read with our customized digital publications that hold readers eyes throughout the story with cutting edge editorial that provides solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

The AST Digital Publications is distributed to over 75,000 qualified government and homeland security professionals in federal, state and local levels.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches both Private & Public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from Government at the federal, state and local level as well as from private firms allied to government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants & Dams, Bridges & Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting & Concert Stadiums, our Nation’s Schools & Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
To learn more about the 2020 ‘ASTORS’ Homeland Security Award Winners solutions, please be on the lookout for the 2020 ‘ASTORS’ CHAMPIONS Edition Fully Interactive Magazine – the Best Products of 2020 ‘A Year in Review’.
The ‘ASTORS’ Champion Edition is published annually and includes a review of the ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firms products and services, includes video interviews and more.
 It is your Go-To source throughout the coming year for ‘The Best of 2020 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
It is your Go-To source throughout the coming year for ‘The Best of 2020 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware and Networking Security – Just to name a few), the 2020 ‘ASTORS’ CHAMPIONS EDITION will have what you need to Detect, Delay, Respond to, and Mitigate today’s real-time threats in our constantly evolving security landscape.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos



























