FBI Releases the Internet Crime Complaint Center 2018 IC3 Report
The FBI’s Internet Crime Complaint Center (IC3) 2018 Internet Crime Report includes information from 351,936 complaints of suspected Internet crime, with reported losses in excess of $2.7 billion.
The top three crime types reported...
ObserveIT 7.7 Competes in 2019 ‘ASTORS’ Awards Program
ObserveIT, a leading insider threat management provider recognized in the 2018 ‘ASTORS’ Homeland Security Awards Program, is pleased to announce the company’s ObserveIT introduced its newest solution, ObserveIT 7.7 has been nominated to compete...
Encryption Is Key in the World of BYOD USB Flash Drives
Guest Editorial by Richard Kanadjian, Encrypted USB Business Manager at Kingston Technology
Today, government entities are filling their workplace environments with all sorts of interesting, novel perks in an attempt to keep staff...
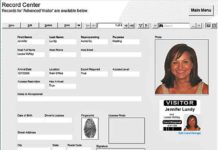
X-Force Red Finds Security Threats in Visitor Management System Kiosks
March 4, 2018 – In Breaking News – WIRED
DANIEL CROWLEY HAS a long list of software platforms, computers, and internet-of-things devices that he suspects he could hack.
As research director of IBM’s offensive security group...
NIST Guide to ‘Mobile Device Security: Cloud and Hybrid Builds’ Now Live
NIST Cybersecurity Practice Guide SP 1800-4 Mobile Device Security: Cloud and Hybrid Builds, is now final.
If sensitive data is stored on a poorly secured mobile device that is lost or stolen, an attacker...
Stomp Out Security Threats with Canon’s Latest Enterprise Solutions
With organizations honing in on IT security and compliance efforts with data privacy regulations, Canon U.S.A., a Double Award Winner in the Annual ‘ASTORS’ Homeland Security Awards Program for two consecutive years, has debuted...
Drowning in a Tsunami of Digital Evidence? Here’s Your Lifeline
By Rod Guy, VP of Strategy, NICE Public Safety
Today, crime solving hinges on digital evidence and the volume, velocity and variety of digital evidence is growing exponentially.
From body-worn cameras and CCTV,...
DHS S&T Awards $1.14M for New Cyber Data Privacy Tools
Cyber-threats are rapidly shifting and privacy-related breaches are increasing in frequency and impact.
To address these concerns, the Department of Homeland Security (DHS) Science and Technology Directorate (S&T), a multiple Platinum Honoree in the...
Arming Against Attack: Three Strategies to Fight Foreign Hackers
By Paul Parker, Chief Technologist, Federal and National Government, SolarWinds
As we move closer to the United States midterm elections, cybersecurity has become a hot topic of conversation.
From Facebook to the Department...
Axiomatics Federal Named a Finalist in 2018 ‘ASTORS’ Awards (Videos)
Axiomatics Federal, the leader in fine-grained dynamic authorization for customers and partners of the federal government, is delighted to announce Axiomatics' Policy Server has been named a Finalist in the 2018 'ASTORS' Homeland...