
Rather than building applications from scratch, developers are using third party components to accelerate time to market and lower cost. This is fueling massive growth in reusable code.
A recent Gartner report on software composition indicates that 90% of enterprises are using third party software and 95% of the proprietary or custom software applications they create contain third party components.
The downside to the use of third party software components is that they can introduce security vulnerabilities that can place organizations at risk.
This has created a blind spot in the modern software stack, since without source code there is no way to identify all of the first party components (AKA custom code), vendor libraries (AKA second party code), commercial libraries (AKA third party code), open source software (OSS) in today’s applications.
To overcome this blind spot in assessing third-party software inventory and risk, CodeSentry from GrammaTech, a Platinum Award Winner in the 2020 ‘ASTORS’ Homeland Security Award Winner, which has been nominated to compete in the 2021 ‘ASTORS’ Awards Program, allows security professionals to measure and manage the risk associated with open source vulnerabilities in third-party software quickly and easily.
GrammaTech created CodeSentry, a powerful Binary Software Composition Analysis (SCA) solution, to finally give organizations the ability to identify, track and proactively control components in their applications so that these previously hidden vulnerabilities are detected and can be remediated.
(CodeSentry is a Binary Software Composition Analysis (SCA) tool derived from GrammaTech’s ground-breaking binary code analysis research. This technology achieves deep scalable analysis without the need for source code and is suitable for enterprise wide adoption. Courtesy of GrammaTech and YouTube.)
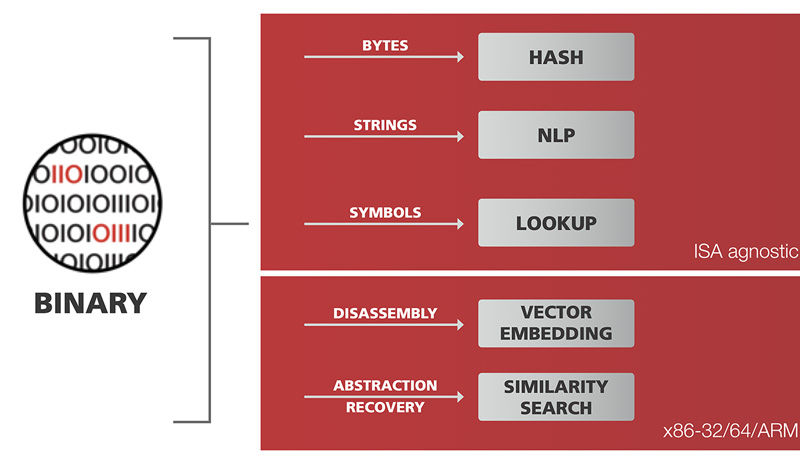
CodeSentry is based on proprietary algorithms developed by GrammaTech that identify all software components, including custom code, vendor libraries, third party code, OSS and API dependencies for software mapping and look-up.
Additionally, CodeSentry continuously tracks vulnerabilities introduced throughout the software lifecycle, including n-day flaws.
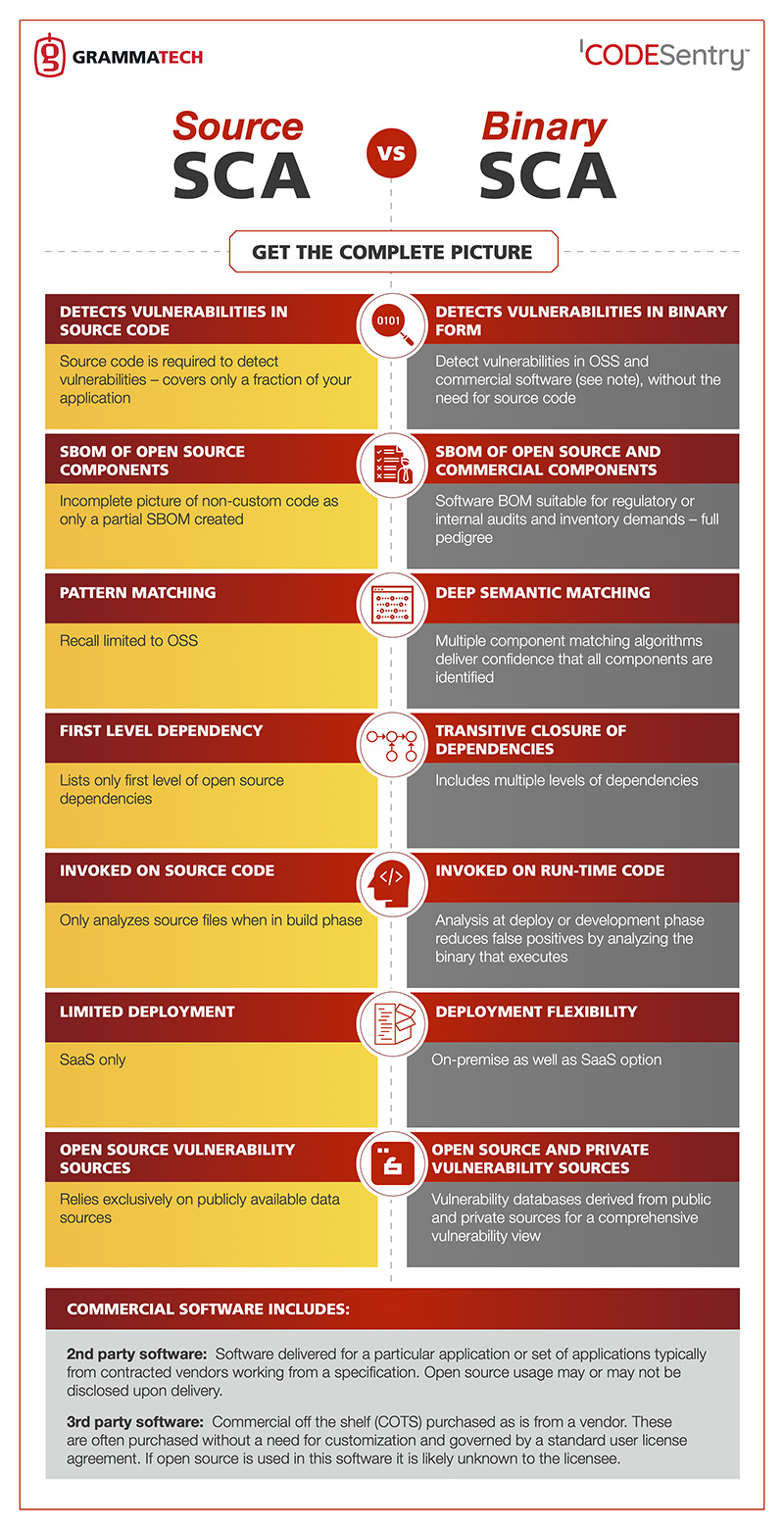
Unlike traditional source code-based SCA tools, CodeSentry applies binary analysis to an application’s build environment, a unique capability that significantly reduces false positives from superfluous code or components that are excluded due to build configurations.
Often source code is not even available, and if it is, the process of setting up a build environment is complex and time-consuming.
CodeSentry saves organizations significant time and resources, and closes an important blind-spot in assessing security risk by providing a detailed software bill or materials (SBOM) that identifies the components that are present in an application and any vulnerabilities, including dependencies.
CodeSentry catalogues components from OSS, custom code, commercial off-the-shelf components, network and GUI components and authentication layers. As an added benefit, CodeSentry enables applications to be audit-ready by embedding the SBOM into the application along with software licensing for third-party software.
CodeSentry’s detailed SBOM allows organizations to quickly and easily assess and manage risk for internal and customer-facing applications from reused software, and provides details of vulnerabilities in identified components, links to CVE reports and offers remediation suggestions.
CodeSentry features an easy-to-use upload interface and multiple output formats that are accessible to IT professionals without programming experience.
With CodeSentry, GrammaTech is solving real-world challenges, not only for application developers, but for organizations that use and rely on modern applications built with third party components.
When software code is developed, it can be used and reused, propagated far and wide, and the vulnerabilities it contains can remain unpatched for many years due to complex or untracked software supply chains.
For instance, last year researchers uncovered 19 vulnerabilities in a 20-year-old Treck library that implements a lightweight TCP/IP stack.
It turned out that these Ripple20 vulnerabilities came to impact hundreds-of-millions of applications that underpin critical infrastructure, including power grid equipment, healthcare systems, industrial, manufacturing, transportation, mobile/satellite communications, commercial aircraft and more. Four of the 19 vulnerabilities are critical and could enable remote code execution.
Similarly, the vulnerabilities known as Urgent/11 were identified in Interpeak AB’s TCP/IP (IPnet) networking stack, another software component that is used widely for IoT and industrial applications.
GrammaTech CodeSentry enables organizations that reuse code to identify and track with high precision any vulnerabilities such as Ripple20, Urgent/11, the notorious Heartbleed Bug and many more that are inadvertently introduced and propagated exponentially throughout software supply chains.
CodeSentry is available both as an on-premise solution for high-security businesses and as a scalable, Software-as-a-Service option is also available, and works with any modern web browser and mobile devices, and accepts native binaries, zip, tar files or other archives.
Binaries do not require debug information and can be of a number of different instruction set architectures (ISAs).
CodeSentry supports multiple output formats including CSV, PDF and XML, and target operating systems include Windows, Linux, MacOS, RTOS and BareMetal.
CodeSentry’s SBOM links to CVEs (Common Vulnerability Enumeration) and CVSS (Common Vulnerability Scoring System) scores, both based on the National Vulnerability Database (NVD).
Identified vulnerabilities can be tracked and annotated, allowing a security researcher to change the CVSS score for a particular vulnerability, should it be inapplicable to the application in development.
GrammaTech recently announced the latest version of CodeSentry reduces software supply chain security risks like those exploited in recent attacks on downstream users of SolarWinds, CodeCov and other applications.
CodeSentry quickly analyzes purchased or commercial off the shelf (COTS) software to identify application components, generate a software bill of materials (SBOM), and detect zero-day and N-day vulnerabilities.
“Most organizations go to great lengths to ensure the safety and security of their physical supply chains yet do very little to assess the integrity of the code used to run their business,” explains Mike Dager, CEO of GrammaTech.
“Recent incidents like the SolarWinds attack have shined a light on software risk and its consequences.”

“CodeSentry enables organizations to discover what components are in the software they are building or using, detect the presence of potential vulnerabilities and mitigate risk.”
“CodeSentry also automates compliance with the SBOM requirement detailed in the recent Executive Order on Cybersecurity.”
Organizations have traditionally trusted software vendors to manage security risk associated with the applications they purchase, but the increasing frequency of software supply chain attacks is forcing enterprises to proactively assess and verify third party software for vulnerabilities that expose them to threats.
Since source code is rarely available for purchased applications, binary analysis is the only alternative for extracting a SBOM to detect underlying risks in commercial software products.
Derived from research conducted for defense and intelligence agencies, CodeSentry provides the following capabilities and benefits:
-
Creates Comprehensive SBOM – binary scanning identifies open source and third-party components and provides a security score, component match details, version information, location, and detailed vulnerability information including CVSS scores
-
Zero- and N-Day vulnerability detection – detects unknown (zero-day) and known (n-day) vulnerabilities in identified open source and third-party components
-
Executive Dashboard – provides a software application risk score based on detected vulnerabilities, CVSS and key performance indicators (KPIs)
-
Advanced reporting – for compliance and risk governance audits
-
Multiple SBOM formats – including industry standard CycloneDX
-
Flexible deployment – native SaaS application with optional on-premises deployment
“The increasing reliance by application developers on open source and third party components is a big reason why the software supply chain is vulnerable to being exploited by attackers,” said Chris Rommel, Executive Vice President for VDC Research.

“Consequently, both application providers and end-user organizations need visibility into the code bases they sell and use so they can continually prove software integrity and proactively detect and mitigate vulnerabilities.”
CodeSentry addresses the following challenges facing both software providers and enterprises:
-
IT Vendor Risk Management – reduce risk to the enterprise by assessing the components and security of commercial off the shelf software (COTS) applications such as financial, HR, video conferencing, messaging and other productivity applications
-
Information Security – ensure a strong security posture by proactively testing COTS applications for vulnerabilities before rolling them out departmentally or across the enterprise
-
DevSecOps – secure the third party code that is brought into the software development life cycle to assure it has been designed and architected with security across the entire stack
Book an Evaluation
The best way to try a SCA solution is to run it on your own codebase and review the results it issues. Book a Free Evaluation and learn how GrammaTech’s technology can rapidly improve your software development capability.
To Learn More, please visit grammatech.com/codesentry-sca.
GrammaTech Returns to Compete in 2021 ‘ASTORS’ Awards Program

 American Security Today’s ‘ASTORS’ Homeland Security Awards program is today in its Sixth Year and continues to recognize the Outstanding Innovations of top firms and agencies in the Homeland Security and Public Safety fields.
American Security Today’s ‘ASTORS’ Homeland Security Awards program is today in its Sixth Year and continues to recognize the Outstanding Innovations of top firms and agencies in the Homeland Security and Public Safety fields.
The Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program highlighting the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition, and keep our Nation safe – one facility, street, and city at a time.

American Security Today is pleased to announce TSA Administrator David Pekoske, will join the organization as a featured speaker at the 2021 ‘ASTORS’ Homeland Security Awards Presentation Luncheon, on November 18, 2021 at ISC East in New York City.
“On the heels of an unprecedented global pandemic, continued unrest in our cities and potentially catastrophic cyberattacks on our nations critical infrastructure, the focus of the 2021 ‘ASTORS’ Awards Luncheon will be on the latest, state-of-the-art innovations that are driving investments in new public security and safety technologies and systems,” said AST Editorial and Managing Director Tammy Waitt.
“As a recognized expert in crisis management, strategic planning, innovation and aviation, surface transportation and maritime security, David Pekoske’s message highlighting his top priorities and challenges for the TSA based on his years of wide-ranging experience will be critical to our attendees internalizing the critical nature of these escalating challenges, and realizing innovative new approaches to meet them.”

From innovative Military Programs, Local, State and Federal Public Safety and Emergency Management Initiatives, New Physical and IT Products and Services, the 2021 ‘ASTORS’ Homeland Security Awards Program is an ideal media platform for your organization to receive the recognition you deserve!
Last year’s program was the largest in our company’s history (see our 2020 ‘ASTORS’ Champions Edition Fully Interactive Magazine at https://tinyurl.com/42yqehj9).
The 2021 ‘ASTORS’ Awards program is already on track for another record-breaking year and the competition is fierce!
The 2021 ‘ASTORS’ Awards Program is proudly sponsored by AMAROK, along with Returning Premier Sponsors ATI Systems, Attivo Networks, Automatic Systems, and Reed Exhibitions.
Nominations are currently being accepted for the 2021 ‘ASTORS’ Homeland Security Awards at https://americansecuritytoday.com/ast-awards/.
Comprehensive List of Categories Include:
| Access Control/ Identification | Personal/Protective Equipment | Law Enforcement Counter Terrorism |
| Perimeter Barrier/ Deterrent System | Interagency Interdiction Operation | Cloud Computing/Storage Solution |
| Facial/IRIS Recognition | Body Worn Video Product | Cyber Security |
| Video Surveillance/VMS | Mobile Technology | Anti-Malware |
| Audio Analytics | Disaster Preparedness | ID Management |
| Thermal/Infrared Camera | Mass Notification System | Fire & Safety |
| Metal/Weapon Detection | Rescue Operations | Critical Infrastructure |
| License Plate Recognition | Detection Products | And Many Others! |
| COVID Innovations | And Many Others! |
Don’t see a Direct Hit for your Product, Agency or Organization?

With the unprecedented occurrence of the COVID-19 pandemic, the focus of the safety and security industries has realized the need to increase innovations to address the daily growing challenges.
As such AST aims to make sure these firms and professionals are reflected in the 2021 ‘ASTORS’ Awards Program, so we’d like to encourage you to submit appropriate categories recommendations and include COVID-19 Frontline Professionals in your Nominations to see that these Professionals, Facilities, and Vendors receive the Recognition they Deserve!
Submit your category recommendation for consideration to Michael Madsen, AST Publisher at: mmadsen@americansecuritytoday.com.
Register for the 2021 ‘ASTORS’ Luncheon Today

Your ‘ASTORS’ Awards Luncheon registration includes complimentary attendee access to ISC East – Thank take advantage of this exclusive luncheon opportunity to take a break from the show – Invite your team, guests, clients and show visitors to a lovely and affordable plated meal event in the heart of New York City, for a fabulous networking opportunity!
Go to https://americansecuritytoday.com/product/awards-luncheon/ to secure your seat or reserve a table.
***Limited space available so Register Today. There will be no on-site registrations.
(2020 was a challenging year due to the COVID-19 pandemic and the ‘ASTORS’ Awards Winners Presentations was canceled and rescheduled for 2021 due to the virus. However, see a brief overview of the 2019 ‘ASTORS’ Awards Presentation Banquet at ISC East.)
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace with over 75,000 readers at the Federal, State and local levels of government as well as firms allied to government.
American Security Today brings forward a fresh compelling look and read with our customized digital publications that hold readers eyes throughout the story with cutting edge editorial that provides solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

The AST Digital Publications is distributed to over 75,000 qualified government and homeland security professionals in federal, state and local levels.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches both Private & Public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from Government at the federal, state and local level as well as from private firms allied to government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants & Dams, Bridges & Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting & Concert Stadiums, our Nation’s Schools & Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
To learn more about the 2020 ‘ASTORS’ Homeland Security Award Winners solutions, Check Out the New 2020 ‘ASTORS’ CHAMPIONS Edition Fully Interactive Magazine – the Best Products of 2020 ‘A Year in Review’.
The Annual CHAMPIONS edition includes a review of the ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firms products and services, includes video interviews and more.
 It is your Go-To source throughout the year for ‘The Best of 2020 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
It is your Go-To source throughout the year for ‘The Best of 2020 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware and Networking Security – Just to name a few), the 2020 ‘ASTORS’ CHAMPIONS EDITION has what you need to Detect, Delay, Respond to, and Mitigate today’s real-time threats in our constantly evolving security landscape.
It also includes featured guest editorial pieces from some of the security industry’s most respected leaders, and recognized firms in the 2020 ‘ASTORS’ Awards Program.
-
For a complete list of 2020 ‘ASTORS’ Award Winners, click here.
For more information on All Things American Security Today, and the 2021 ‘ASTORS’ Awards Program, please contact Michael Madsen, AST Publisher at mmadsen@americansecuritytoday.com.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos
























