Guest Editorial by Richard Osborne and Jason Franks
Cybersecurity for public-sector organizations — i.e., those in the public safety and justice communities — is a big, messy problem that is getting bigger and messier daily.
This article examines the five scariest cybersecurity trends every organization should have on its radar screen.
Scariest Trend No.1 — Cyberattackers Keep Getting Better at What They Do
Cyberattackers constantly evolve their strategies and tactics, seemingly at warp speed. For example, they employ increasingly sophisticated, automated software tools that leverage algorithms to identify millions of network, system, and device vulnerabilities every second.
A corollary factor contributing to this trend is that developers find it extremely difficult to create vulnerability-free software.
This is the reason that patches are continually issued.
Now consider that the software utilized by public sector organizations interconnects to all manner of software employed by dozens, even hundreds, of other organizations, and each piece of software contains its own intrinsic vulnerabilities.
It is easy to imagine a cyberattacker exploiting a vulnerability discovered in another organization’s software and then worming their way into your organization’s software, enabling them to attack every connected network, system, and device.
Another is that, in most countries, cyberattacks aren’t considered crimes. The philosophy seems to be, “Shame on you for not having the proper protections in place.” The result is that cyberattackers outside the United States operate with virtual impunity.
For all these reasons and more, cybersecurity fraud is the third-largest economy in the world and will only get bigger. The proverbial monster under the bed keeps every cybersecurity professional working in the public sector up at night — or at least should.
Scariest Trend No.2 — Failing to See the Big Picture
That brings us to the second scariest trend. Public sector organizations only recently have started to understand the severity of the cybersecurity problem. It’s taken them a while — far too long.
For a long time, they seemed to believe that cyberattackers would only target the private sector for ransomware attacks because that’s where the deep pockets capable of paying hefty ransoms to decrypt their files exist.
But over the last couple of years, it has become clear that public sector organizations also are in the crosshairs. So, they are starting to take strong, proactive steps to detect and mitigate cyberattacks.
That’s the good news. But what about the rest of it? Readers might wonder, “What do you mean, the rest of it?” That’s the scary part.
There’s plenty more that public sector organizations can and should be doing regarding cybersecurity— anecdotal evidence indicates that they’re still largely not doing it.
This is a very big and potentially very dangerous problem.
An adage says, “An ounce of prevention is worth a pound of cure,” and it certainly can be applied to cybersecurity.
(More than $8 million has been spent restoring systems in the City of Dallas following a ransomware attack that closed many of the city’s public service offices for most of the month after the cyberattack. Courtesy of CBS Texas and YouTube.)
Scariest Trend No. 3 — Failing to Heed Recommendations
It seems that most public sector agencies fail to adhere to — or even acknowledge the existence of — longstanding cybersecurity recommendations issued by entities with quite a bit of game in this area, for example, the Cybersecurity and Infrastructure Security Agency (CISA) (which was recognized with Multiple Awards in the 2022 ‘ASTORS’ Homeland Security Awards Program), and the National Institute of Standards and Technology (NIST).
CISA, NIST, and their counterparts in Europe and Australia have worked collaboratively for years to ensure that public sector organizations are well-informed regarding emerging threats and the best strategies and tactics for mitigating them.
Yet, many such organizations still aren’t following recommendations made a decade ago, much less following current recommendations.
So, why aren’t more organizations following the recommendations of CISA, NIST, et al.?
Part of the reason, as indicated above, is complacency — many organizations think they won’t suffer a cyberattack. This is extremely wrong-headed thinking — in this environment, it is virtually certain that every public sector organization will eventually suffer a cyberattack, with the risk increasing exponentially for organizations that do not have a sound cybersecurity program.
A bigger factor might be that cybersecurity is still a top-down endeavor for most organizations. If an organization is fortunate enough to have effective information technology (IT)/cybersecurity resources — and most public sector organizations, especially smaller agencies, do not — the requests made by these professionals often are rejected out of hand because those at the leadership level find them too bothersome or too expensive, or both.
This a classic example of thinking that is “penny wise and dollar foolish.” Cybersecurity should be viewed as a lifecycle proposition.
It’s not “one and done” nor “set it and forget it” — it needs to be addressed every day, every week, every month, every year.
We’re reminded of a television commercial for an oil-filter brand from long ago that features an automobile mechanic uttering the iconic catchphrase, “You can pay me now, or you can pay me later.”
The adage works very well today in the public sector — considering the havoc and expense that a cyberattack would generate, can any organization afford not to have a robust cybersecurity posture?
(CISA has released a Hardware Bill of Materials (HBOM) Framework for Supply Chain Risk Management to assist organizations in evaluating and mitigating risks before purchasing new products and technologies. Courtesy of CISA and YouTube.)
Scariest Trend No. 4 — Not Enough Cybersecurity Experts to Go Around
Nearly all public sector organizations deal with acute staffing shortages across the entire enterprise. This includes information technology (IT) and cybersecurity personnel. It should be noted that not every IT professional has the experience and expertise required to work in the cybersecurity realm.
Indeed, cybersecurity professionals possess very specific skill sets, making recruiting, hiring, and retaining them more difficult. Because their skill sets are so specialized, cybersecurity professionals tend to require compensation that puts them out of reach of many public sector organizations, especially if they compete with private-sector organizations with deeper pockets.
A related factor is that smaller municipalities and counties often share cybersecurity personnel across multiple agencies. The result is that personnel typically are spread very thin, so much so that they find it exceedingly difficult, if not impossible, to execute even the most basic elements of a cybersecurity program for a single agency, much less all of them, and to keep pace with constantly evolving threat vectors.
Scariest Trend No. 5 — LMR Systems are Just as Vulnerable as Every Other System
This trend primarily affects public safety agencies, which rely extensively on two-way voice communications during emergency response.
It has been said, with some justification, that the most vital tool that law enforcement officers and fire/rescue personnel carry is their land mobile radio (LMR). In the past, LMR systems, whether analog or digital, have been isolated, standalone, self-contained, and not connected to the internet, which generally meant that no pathway existed for cyberattackers to infiltrate them.
Unfortunately, however, many vulnerabilities exist that exponentially increase the risk profile for LMR systems. This is true even for Project 25 (P25) systems, despite the existence of certain protections that are baked into the standard, such as encryption, use of multiple frequencies, and a feature called “radio inhibit,” which enables system managers to identify a rogue radio and essentially turn it into a brick.
(Basics of P25 presents an overview of interoperability and P25. The video outlines P25’s role in public safety, its value in both daily operations and emergencies involving mutual aid partners and outside agencies, and its advantages for enhancing personnel safety and operational efficiency. Courtesy of CISA and YouTube.)
Arguably, the greatest vulnerability is that the systems used by public safety agencies to backhaul radio traffic from the tower(s) to the facility leverage the Internet Protocol, which has inherent security flaws — ergo, IP-based networks and systems are intrinsically vulnerable to cyberattacks.
The reality is that most public safety agencies think of their LMR systems in terms of radio frequencies and not IP — thus, they fail to grasp the criticality of this vulnerability.
A corollary factor is that public safety agencies often share backhaul systems with other entities, each with its own vulnerabilities. The result is a dramatically diminished cybersecurity posture for all concerned.
What to do
As we wrote in the opening paragraph, cybersecurity is a big, messy problem that will only get bigger and messier.
And there’s no way to keep cyberattackers at bay completely.
There are too many of them, and they are persistent, highly intelligent, and very motivated.
But all is not lost.
There are things that every public sector organization can do to lessen the risk of cyberattacks, starting with implementing strong vulnerability management and cybersecurity-awareness programs as soon as possible.
There is no time to waste. In doing so, embrace the tenets of CISA and NIST.
Then implement as many of the following prevention tactics as your financial and people resources allow:
-
Virtual private networks (VPNs)
-
Access controls such as strong passwords/passphrases and multifactor authentication
-
Quarterly penetration tests and weekly vulnerability scans
-
Network segmentation and segregation
-
Firewalls and intrusion detection/prevention
-
Endpoint protection
-
Patch management

Finally, understand that cybersecurity networks, systems, and device monitoring are not all your organization needs to do.
Without prevention tactics, all monitoring will accomplish is to alert you when a breach has occurred.
That’s far too late in the game — the damage already is done.

About the Authors
Richard Osborne is the director of commercial services for Mission Critical Partners, a firm that provides consulting, management, and cybersecurity solutions to public sector organizations.
He can be reached at RichardOsborne@MissionCriticalPartners.com.
Jason Franks is an MCP cybersecurity analyst. Email him at JasonFranks@MissionCriticalPartners.com.
CISA Nominated to Return in 2023 ‘ASTORS’ Homeland Security Awards Program

American Security Today’s Annual ‘ASTORS’ Awards, is the preeminent U.S. Homeland Security Awards Program, and now in its Eighth Year, continues to recognize industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management and Response, Law Enforcement, First Responders as well as federal, state and municipal government agencies in the acknowledgment of their outstanding efforts to Keep our Nation Secure.
Cybersecurity and Infrastructure Security Agency (CISA)
 Excellence in Public Safety
Excellence in Public Safety
-
Active Assailant Security Branch, Active Shooter Preparedness Program
-
Active shooter incidents are often unpredictable and evolve quickly.
-
Amid chaos, anyone can play an integral role in mitigating the impacts of an active shooter incident. DHS aims to enhance preparedness through a “whole community” approach by providing products, tools, and resources to help you prepare for and respond to an active shooter incident.
(For example, CISA’s “Active Shooter Preparedness: School Security and Resilience” video provides information geared towards educators, school resource officers, and school administrators who serve in important roles in safeguarding schools. Courtesy of CISA and YouTube.)
-
To access the most applicable information, please select the appropriate category for your application from the following: First Responders and Security Professionals, Private Citizens, Critical Infrastructures and Business, Active Shooter Preparedness Workshop/Webinar, Employee Vigilance and De-escalation, Products/Resources.
-
Learn More, through CISA’s series of videos for additional information.
(The DHS Active Shooter PowerPoint Presentation and Webinar video is used by DHS-qualified subject-matter experts as a visual reference to guide critical infrastructure owners and operators with a better understanding of developing an organization’s emergency action plan. Courtesy of CISA and YouTube.)
Cybersecurity and Infrastructure Security Agency (CISA)
 Excellence in Public Safety
Excellence in Public Safety
-
Active Assailant Security Branch, Vehicle Ramming Self-Assessment Tool
-
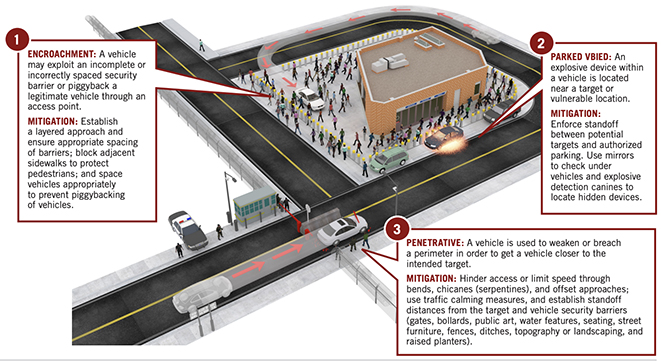
Using a vehicle as a weapon in a terrorist attack is not new.
-
Recent terrorist incidents and violent extremist propaganda demonstrate that using vehicles as a weapon continues to be of interest to those wishing to cause harm.
-
Attacks of this nature require minimal capability but can have a devastating impact in crowded places with low levels of visible security.
-
To aid our nation’s first responders and citizens, CISA offers the following resources: the Vehicle Ramming Self-Assessment Tool, the Self-Assessment Tool Resources, the First Responder Toolbox, General Resources, and videos.
(Learn More. The FBI, DHS, and TSA—in coordination with the Truck Renting and Leasing Association and the American Car Rental Association—have released a short training video to help vehicle rental employees identify suspicious activities and behavior by customers who may wish to use a rented vehicle for nefarious purposes. Courtesy of the FBI – Federal Bureau of Investigation and YouTube. Posted on Aug 3, 2022.)
-
To contact the Vehicle Ramming Attack Mitigation team or to get more information on Vehicle Ramming Attack Mitigation, please contact CISA.ISD.OSP.VehicleRammingMitigation@cisa.dhs.gov.
Nitin Natarajan, Deputy Director, CISA

 Excellence in Homeland Security
Excellence in Homeland Security
-
Nitin Natarajan was appointed as the Deputy Director for CISA on February 16, 2021. Before joining CISA in February 2021, Natarajan served in various public and private sector positions spanning over 30 years.

-
Most recently, he served as an executive at consulting firms providing subject matter expertise on many topics, including IT, cybersecurity, homeland and national security, critical infrastructure protection, environmental emergency management, continuity of operations, and health security matters.
-
Natarajan also held several federal government roles, including serving as the Deputy Assistant Administrator for the Office of Land and Emergency Management at the U.S. Environmental Protection Agency, the Director of Critical Infrastructure Policy at the White House/National Security Council, and the Director at the U.S. Health and Human Services overseeing their critical infrastructure, continuity of operations (COOP), and medical logistics programs.
-
Before serving in the federal government, Natarajan served in positions at the state/local government level and served as a hospital administrator.
-
Natarajan started his career by spending 13 years as a first responder in New York, including service as a flight paramedic. He was the Commander of a federal medical response team based in New York and has extensive experience deploying to natural and man-made disasters nationwide.
-
He holds an undergraduate degree from the State University of New York and a graduate degree from the United States Naval Postgraduate School.
(Hear from Nitin Natarajan to learn more about the Cybersecurity and Infrastructure Security Agency (CISA) is an operational component of the Department of Homeland Security (DHS). Under the leadership of Director Jen Easterly, CISA works to understand, manage, and mitigate risk to the nation’s cyber and physical infrastructure in the public and private sectors. Their virtual mini-Industry Day events allow CISA and industry leaders to have meaningful discussions about cybersecurity, infrastructure, risk management, communications capabilities, challenges, technologies, and future business opportunities. Courtesy of CISA and YouTube.)
As America’s Cyber Defense Agency, the Cybersecurity and Infrastructure Security Agency (CISA), leads the national effort to understand, manage, and reduce risk to our critical infrastructure.
 CISA is the operational lead for federal cybersecurity and the national coordinator for critical infrastructure security and resilience, and was designed for collaboration and partnership.
CISA is the operational lead for federal cybersecurity and the national coordinator for critical infrastructure security and resilience, and was designed for collaboration and partnership.
CISA develops a range of cyber and infrastructure security services, publications, and programs for federal government, SLTT governments, industry, small and medium businesses, educational institutions, and the American public.
To learn about CISA’s layered mission to reduce the nation’s cyber and physical infrastructure risk, please visit www.cisa.gov/about.
(Learn More about the Cybersecurity and Infrastructure Security Agency (CISA). Courtesy of CISA and YouTube.)
Learn More…
LEO’s Needs Better Data Analysis to Stop Tech-Savvy Cybercriminals