
Guest OpEd by Karl Swannie, founder and CEO of Echosec Systems
Threat intelligence.
For security professionals, the term is often synonymous with detecting and mitigating cyber attacks like malware and phishing.
Alongside cyber attacks, online data is becoming more relevant for investigating cyber-enabled threats and physical security risks.
Threat intelligence solutions must integrate data from each of these areas, particularly when they overlap.
When threat intelligence strategies focus only on cyber, they can overlook critical information as cyber risks, cyber-enabled activities, and physical security threats provide context to each other.
(Learn how Echosec Systems can deliver access to one of the most comprehensive breadths of data on the market and continues to integrate new technologies and partnerships to fill security gaps. Courtesy of Echosec Systems and YouTube. Posted on Mar 11, 2021.)
Where some approaches fall short
Threat actors are seldom active in one distinct webspace, such as the dark web.
Breadcrumbs typically span the surface, deep, and dark web, and digital security personnel must consider open-source intelligence across a variety of these sources.
This is not only true for detecting cybercrime, which targets computer systems.
It is also valuable for gaining context when cyber risks implicate physical threats and cyber-enabled crimes (which use the web to commit threats like fraud or theft) as adversaries adopt digital communications.
For example, say the image of an organization’s ID badge, infrastructure map, or SOC room are posted on a social network like Reddit or Twitter.
This information could be used to weaken physical access control.
But it could also give cyber attackers the information they need to compromise a digital system or support a social engineering strategy.
Security teams need to know when this information hits the web and where it migrates.
(Hear directly from Karl Swannie on security tools for analysts, primarily Echosec Systems engineers threat intelligence solutions for organizations with specific, complex intelligence requirements. The company’s software makes hidden online data more accessible by enabling organizations to leverage online chatter to detect both physical threats (like terrorist activity), as well as cyber threats (like ransomware and data breaches), as early as possible. Courtesy of Echosec Systems and YouTube. Posted on Mar 11, 2021.)
Even though online risks involve both digital and physical concerns, security strategies often fail to integrate these use cases.
Digital and physical security teams may be siloed in their approach and communications, and protocols may be fuzzy when digital and physical risks are interconnected.
Threat intelligence tooling, while valuable for cyber defense, can be inaccessible for less technical users investigating cyber-enabled crimes or physical security threats.
Some data sources, such as obscure social media platforms or messaging apps, are also necessary for these use cases but might not be offered by commercial threat intelligence vendors.
This could force analysts to overlook or manually investigate these sources.
Addressing an integrated threat landscape
When strategies and tooling do not reflect the integrated nature of cyber and physical security, risks can be missed and threat intelligence may lack the necessary context.
A more holistic approach can help desegregate security teams in their focus areas as cyber threat intelligence informs other threat types and vice versa.
What does this look like? It might start with revisiting, at a high-level, how security teams organize and communicate within your organization.
Deduce whether a divided approach creates functional gaps in your strategy. But it can also come down to threat intelligence tooling and data source selection.
Security managers should consider what online sources support both digital and physical threat intelligence gathering, and how to integrate any missing sources into their infrastructure.
There is also the accessibility factor: are your tools usable for less technical personnel who still require access to online threat intelligence?
Integrating physical and digital threats has several positive outcomes for your security posture.
Your security teams and the software will likely deliver more timely and contextual threat intelligence for cyber, cyber-enabled, and physical scenarios when they inevitably overlap.
This added context can inform faster, more effective response strategies and help organizations allocate security resources more effectively.
A comprehensive security solution, whether it’s in the public or private sector, requires access to both physical and digital threat intelligence.
Integrating the teams, data sources, and tooling required for these overlapping use cases will help organizations respond more effectively to a diversifying threat landscape.
It will also help them minimize costs and reputational damages associated with these threats—and most importantly, protect the people and assets most at risk.
About the Author
Karl Swannie is the founder of Echosec Systems.
Echosec Systems gives security teams a single access point to real-time risk data across a wide range of social media, deep web, and dark web networks.
To learn more, please visit www.echosec.net.
Related Technologies…
Cobwebs Technologies Takes Platinum in 2020 ‘ASTORS’ Awards
American Security Today’s ‘ASTORS’ Homeland Security Awards program is now in its Sixth Year and continues to recognize the Outstanding Innovations of top firms and agencies in the Homeland Security and Public Safety fields.
2020 was a very challenging year for everyone due to the COVID-19 pandemic and the much heralded AST ‘ASTORS’ Awards Winners Presentations and exclusive Luncheon at the Jacob Javits Center in NYC had to be canceled and rescheduled for 2021 due to the virus.

However, the 2020 ‘ASTORS’ Homeland Security Awards Program was again a huge success and many new categories were added including a section for COVID-19 Detection and Innovation.
Cobwebs Technologies
 Best Web Intelligence Solution
Best Web Intelligence Solution
-
Cobwebs Technologies Web Intelligence Platform
-
Cobwebs Technologies is a specialized web intelligence company that supports national security agencies, law enforcement agencies, and corporate security departments to rapidly identify and locate malicious threat actors on the open, deep, and dark webs.
-
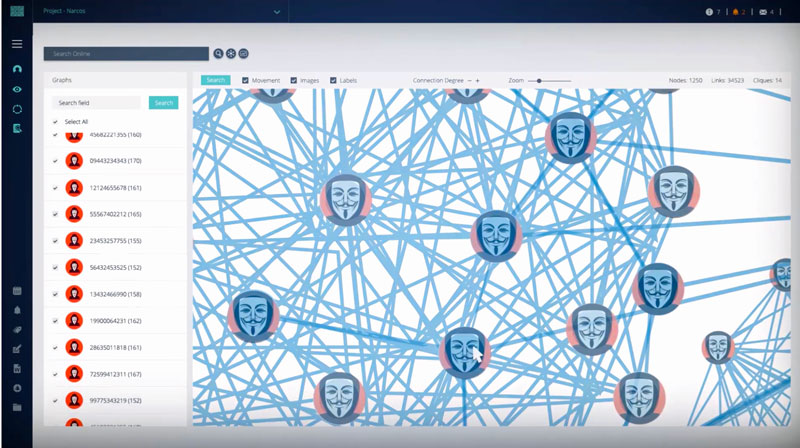
Cobwebs also points investigators in the direction of potential evidence, located on all layers of the web, that could be used to prosecute the threat actors. The platform not only identifies threat actors, it also identifies members and supporters of their network as well as the links that connect them.
-
Online criminal investigations on the open, dark and deep webs that may have taken days or weeks or even months to be conducted can now be successfully completed in mere minutes with little more than a few clicks of a mouse thanks to the Cobwebs platform.
-
The Cobwebs platform helps investigators identify and reconstruct profiles that link suspicious individuals to their contacts, and it reveals how they connect and come together as a group.
-
People outside of a group can also be identified so that investigators can determine if they should be conducting additional investigations.
-
To Learn More, please visit cobwebs.com/products/web-investigation-platform/.
The 2020 ‘ASTORS’ Awards Program was sponsored by ATI Systems, Attivo Networks, Automatic Systems, Desktop Alert, X.Labs and Reed Exhibitions, every one a returning Sponsor from 2020, 2019 and More.
Nominations are now being accepted for the 2021 ‘ASTORS’ Homeland Security Awards at https://americansecuritytoday.com/ast-awards/.
Comprehensive List of Categories Include:
| Access Control/ Identification | Personal/Protective Equipment | Law Enforcement Counter Terrorism |
| Perimeter Barrier/ Deterrent System | Interagency Interdiction Operation | Cloud Computing/Storage Solution |
| Facial/IRIS Recognition | Body Worn Video Product | Cyber Security |
| Video Surveillance/VMS | Mobile Technology | Anti-Malware |
| Audio Analytics | Disaster Preparedness | ID Management |
| Thermal/Infrared Camera | Mass Notification System | Fire & Safety |
| Metal/Weapon Detection | Rescue Operations | Critical Infrastructure |
| License Plate Recognition | Detection Products | And Many Others! |
| COVID Innovations | And Many Others! |
Don’t see a Direct Hit for your Product, Agency or Organization?

With the unprecedented occurrence of the COVID-19 pandemic, the focus of the safety and security industries has realized the need to increase innovations to address the daily growing challenges.
As such AST aims to make sure these firms and professionals are reflected in the 2021 ‘ASTORS’ Awards Program, so we’d like to encourage you to submit appropriate categories recommendations and include COVID-19 Frontline Professionals in your Nominations to see that these Professionals, Facilities, and Vendors receive the Recognition they Deserve!
Submit your category recommendation for consideration to Michael Madsen, AST Publisher at: mmadsen@americansecuritytoday.com.
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace with over 75,000 readers at the Federal, State and local levels of government as well as firms allied to government.
American Security Today brings forward a fresh compelling look and read with our customized digital publications that hold readers eyes throughout the story with cutting edge editorial that provides solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

The AST Digital Publications is distributed to over 75,000 qualified government and homeland security professionals in federal, state and local levels.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches both Private & Public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from Government at the federal, state and local level as well as from private firms allied to government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants & Dams, Bridges & Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting & Concert Stadiums, our Nation’s Schools & Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
To learn more about the 2020 ‘ASTORS’ Homeland Security Award Winners solutions, Check Out the New 2020 ‘ASTORS’ CHAMPIONS Edition Fully Interactive Magazine – the Best Products of 2020 ‘A Year in Review’.
The Annual CHAMPIONS edition includes a review of the ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firms products and services, includes video interviews and more.
 It is your Go-To source throughout the year for ‘The Best of 2020 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
It is your Go-To source throughout the year for ‘The Best of 2020 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware and Networking Security – Just to name a few), the 2020 ‘ASTORS’ CHAMPIONS EDITION has what you need to Detect, Delay, Respond to, and Mitigate today’s real-time threats in our constantly evolving security landscape.
It also includes featured guest editorial pieces from some of the security industry’s most respected leaders, and recognized firms in the 2020 ‘ASTORS’ Awards Program.
-
For a complete list of 2020 ‘ASTORS’ Award Winners, click here.
For more information on All Things American Security Today, and the 2021 ‘ASTORS’ Awards Program, please contact Michael Madsen, AST Publisher at mmadsen@americansecuritytoday.com.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos






















