
American Security Today’s Annual ‘ASTORS’ Awards, the preeminent U.S. Homeland Security Awards Program, now in its Eighth Year, recognizes industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management and Response, Law Enforcement, First Responders, as well as federal, state and municipal government agencies in the acknowledgment of their outstanding efforts to Keep our Nation Secure.
An exclusive sold-out event featured at ISC East, well over two hundred representatives of law enforcement, public safety, and industry leaders came together to honor the selfless service of those who stand on the front lines – and those who stand beside them – providing the capabilities and technologies to create a safer world for future generations.
Comprehensive collaborations between these private and public sectors have led to the development of innovative intelligence and technologies that serve to protect our Nation.

Steven Dettelbach, Director of the Bureau of Alcohol, Tobacco, Firearms (ATF) and Explosives, delivered the keynote address at the 2023 ‘ASTORS’ Homeland Security and Excellence in Public Safety Awards Ceremony and Banquet Luncheon.
Director Dettelbach spoke with passion on the epidemic of Gun Violence by Illegal Guns taking place across the United States, which results in over 125 deaths daily and impacting generations of families – leaving open chairs at holiday events.
Firearm injuries were the leading case of death for children for the third year in a row, he explained, and have doubled in the U.S. since 2021, levels that are simply intolerable.
Director Dettelbach spoke about the contagion of active assailant events across the country that happen with such frequency that they have become nearly invisible – which is also intolerable in a civilized society.

He spoke to the ATF’s National Integrated Ballistic Information Network (NIBIN), which automates ballistics evaluations and provides actionable investigative leads in a timely manner.
NIBIN is the only interstate automated ballistic imaging network in operation in the United States and is available to most major population centers in the United States.
Through the NIBIN, the ATF can share ballistics intelligence across the United States, making law enforcement resources more effective, and can help incarcerate the armed violent offenders plaguing our communities.
Director Dettelbach lauded the strong partnerships with Federal, State, Local, and Tribal Policing that ATF has earned and relies upon to reduce violence and spoke with admiration as a former prosecutor on the selfless sense of mission and drive that is universal across the entire First Responder Community.

Originally from Cleveland, Ohio, the Director was the United States attorney for the Northern District of Ohio for over six years during the Obama administration.
From 2016 to 2022, he was a partner at BakerHostetler, serving as co-leader of the firm’s national White Collar Defense and Corporate Investigations team. In July 2022, he was appointed by President Biden and confirmed by the Senate as the director of the ATF.
As Director, Mr. Dettelbach is responsible for leading an agency of men and women charged with protecting the public by enforcing laws and regulations related to firearms, explosives, arson, and alcohol and tobacco trafficking.

The prestigious Annual ‘ASTORS’ Homeland Security Awards Program highlights the most cutting-edge and forward-thinking security solutions coming onto the market today to ensure our readers have the information they need to stay ahead of the competition and keep our Nation safe – one facility, street, and city at a time.
The ‘ASTORS’ was specifically designed to honor distinguished government and vendor solutions that deliver enhanced value, benefit, and intelligence to end-users in a variety of government, homeland security, enterprise, and public safety vertical markets.

“‘ASTORS’ nominations are evaluated on their technical innovation, interoperability, specific impact within the category, overall impact to the industry, relatability to other industry technologies, and application feasibility outside of the industry,” explained AST’s Editorial Director Tammy Waitt.
“‘ASTORS’ Awards Winners are selected by our American Security Today Expert Blind Panel of Judges, and the ‘ASTORS’ Homeland Security Awards are presented at the Platinum, Gold, Silver, and Bronze levels,” at the Annual ‘ASTORS’ Awards Ceremony and Banquet Luncheon in NYC.
(See some highlights of the 2023 ‘ASTORS’ Homeland Security and Government Excellence Awards Ceremony and Banquet Luncheon on November 16th, 2023 in New York City. Courtesy of AST, My Pristine Images, and Vimeo.)
Without further ado, American Security Today is Proud to Introduce the 2023 ‘ASTORS’ Homeland Security and Excellence in Public Safety Awards Winners:
1KOSMOS
 Best Phishing Defense Solutions
Best Phishing Defense Solutions
-
1Kosmos BlockID
-
1Kosmos developed the BlockID platform to know with certainty the identity of users accessing digital services and, in doing so, it eliminates passwords, gives users control over their personal data, simplifies login experiences, and reduces cyber and compliance risks to the organization.

-
For every access attempt, 1Kosmos BlockID proves the identity of the individual behind the digital connection, replaces passwords with non-phishable MFA, and helps organizations move toward a zero-trust architecture by establishing an indisputable identity as a pillar for all downstream security measures.
-
It enables enterprises and government organizations to modernize cybersecurity with identity-based authentication delivered as a secure cloud service.
-
1Kosmos BlockID merges identity proofing and passwordless multi-factor authentication and is certified for iBeta Biometric PAD-2 Liveness, NIST 800-63-3, and FIDO2. It is also certified to ISO 27001 and compliant with GDPR and SOC2 standards.
365Labs
 Best Handheld Mobile Device Solution
Best Handheld Mobile Device Solution
-
365 CAD/RMS
-
365Labs’ Mobile Apps extend CAD & RMS to handhelds and phones, using patented technology for ease of use and to simplify user interactions.
-
The real-time and offline technology improves situational awareness and officer safety, reduces response time, and simplifies workflows for first responders.
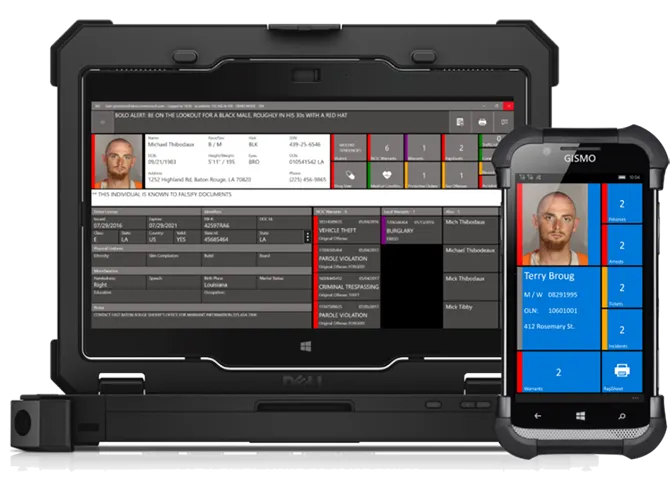
-
365Labs builds software and processes to modernize Public Safety, Criminal Justice, and First Responders. 50+ integrated modules create an operating system for Law Enforcement agencies.
-
The 365Labs™ Public Safety Cloud Platform for LEOs, Prosecutors, and Corrections software tightly connects with Microsoft 365 and brings the advantages of CLOUD and CoPilot AI. With rapid implementation, teams are empowered, and operations are streamlined.
-
The complete CAD/RMS/JMS/Case Management System for modern Law Enforcement, Criminal Justice, and First Responders uses both Artificial Intelligence and common sense.
908 Devices
 Best CBRNE Detection Solution
Best CBRNE Detection Solution
-
MX908 Beacon
-
The MX908 Beacon provides identification of aerosol and vapor chemical warfare agents and pharmaceutical-based agents, leveraging the MX908 high-pressure mass spectrometer and the Aero module to empower intelligence gathering remotely while ensuring greater safety for the public and responders.
(Learn more about the MX908 Beacon area monitoring accessory for MX908 with Aero. MX908 Beacon provides continuous remote area monitoring for chemical warfare and pharmaceutical-based agents. Courtesy of 908 Devices and YouTube.)
-
MX908 is deployed by militaries and first responders around the world to detect and identify chemical threats. With the addition of Beacon, operators can provide real-time identification of aerosol and vapor CWAs and PBAs for extended durations, adding a layer of protection for special events, hazmat response, and critical infrastructure.
-
With threat categories such as A-series agents (Novichoks), V-series agents, G-series agents, HD Mustard, and other chemical agents, MX908 Beacon provides superior coverage for the most toxic threats.
-
*908 Devices is a Returning ‘ASTORS’ Award Champion, having secured a Win in the 2021 Awards Program.
911inform
 Best Mass Notification Solution – Application
Best Mass Notification Solution – Application
-
911inform Notification and Security Management Platform
-
911inform enables full situational awareness and communication across multiple platforms, allowing for total transparency into any situation where a 911 request for emergency services occurs, including both landline and wireless calls.
(Walk through a scenario from when a 911 call is placed, the direct communication lines between the building personnel and first responders, and the overall conclusion of the emergency. With full situational awareness across multiple platforms and no need for additional equipment, 911Inform puts first responders FIRST. Courtesy of 911Inform and YouTube.)
-
When 911 is dialed from within a 911inform building or geofenced area, an emergency event will be generated within the 911inform software. Once the emergency event is triggered, 911inform will notify individuals based on pre-configured protocols.
-
The public safety personnel being notified could include the following: 911 dispatch, law enforcement, fire, medical, private security, and building staff.
Acoustic Technology Inc. (ATI Systems)
 Best Mass Notification System – Hardware
Best Mass Notification System – Hardware
-
ATI Next Generation Product Line
-
Effective dissemination of information promptly can be critical when an emergency strikes, and emergency communications for disasters require rapid deployment of Giant Voice (GV), Indoor, and flexible Control Solutions.

-
ATI Systems, a world-leading provider of reliable emergency warning & mass notification systems (MNS), offers outstanding Giant Voice Solutions for Military, Community, and Campus clients with the essential tools for emergency planning and preparedness, which includes their Mobile High Powered Speaker Station (HPSS) which is Rapidly Deployable on an Outdoor Siren Trailer, their Transportable High Powered Speaker Station (THPSS), and their Deployable High Powered Speaker Stations (DHPSS).
-
Mass notification systems typically cover large outdoor areas, but alerting people inside the buildings is also important. ATI’s Indoor Speaker Unit (ISU) offers customers intelligent, flexible solutions for complicated indoor Mass notification scenarios.

-
Additionally, a robust communication and control backbone is provided by ATI’s award-winning REACT5000 Central Control Unit (CCU) and MassAlert software, which contains an intuitive graphic display of the entire system. ATI equipment supports multiple communication options to ensure a reliable system.
-
Through acoustic design and modeling, ATI Systems provides optimal sound coverage and superior voice intelligibility for outdoor and indoor areas to ensure the safety of its clients worldwide.
 *ATI Systems is also a Returning Premier Sponsor for the Seventh Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a 2022, 2021, 2020, 2019, 2018, and 2017 ‘ASTORS’ Platinum Award Champion. Thank you for your continued support of American Security Today!
*ATI Systems is also a Returning Premier Sponsor for the Seventh Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a 2022, 2021, 2020, 2019, 2018, and 2017 ‘ASTORS’ Platinum Award Champion. Thank you for your continued support of American Security Today!
ADASHI Systems
Best Fire & Safety Solution
-
Adashi Public Safety Software
-
Adashi Systems, a Versaterm Public Safety Company, is a digital toolkit that allows supervisors of firefighters and other first responders to enhance accountability, achieve a unified command structure, and aid in employees’ mental health.
-
Incorporating real-time intelligence and analytic insights, Adashi empowers departments to respond to emergencies effectively, mitigate line-of-duty deaths, and proactively identify staff who require mental health resources.
(Learn why over 1500+ public safety agencies use Adashi’s emergency response and incident command software to improve operations and save lives. Courtesy of Adashi and YouTube.)
-
Adashi Systems provides public safety software to 1,500+ emergency services organizations worldwide. Its complete public safety platform gives agencies the tools to staff, respond to, and manage critical incidents safely and efficiently.
-
The company’s products are specifically designed for the distinct requirements of the public safety industry, giving first responders technology that adapts to their needs, no matter what kind of incident they are facing.
AEGIX Global
Best Security Incident & Event Management Solution
-
AEGIX AIM
-
AEGIX AIM (Active Incident Management) allows users to manage facility-specific emergencies with a desktop, laptop, Chromebook, tablet, mobile phone, and web applications, making AIM an empowering tool to prevent and mitigate emergency and non-emergency related incidents and security issues with detailed accuracy.
(In a world with over 600 mass shootings a year, AEGIX has developed a comprehensive incident response that includes all the people involved, including dispatch, law enforcement, and first responders. If an incident happens, AEGIX is ready to help. Courtesy of AEGIX and YouTube.)
-
AIM contains a unique, robust cloud-based system that supports customizable incident notifications, interactive mapping, accountability and safety tools, and emergency plans and reporting.
-
The AEGIX AIM platform includes a user-friendly push-button app to manage emergencies from a desktop, laptop, or smartphone, and allows individuals in an organization such as a school, state capitol building, hospital, or private office building to notify others of an emergency with the touch of a button.
-
Key law enforcement and other first responders can see an interactive map of a building and instantly have room-by-room situational awareness to know exactly what the emergency is and where they need to go. This cuts through the chaos to remove guesswork and delays, which saves precious time.
ALLIED UNIVERSAL (First of Three)
 Best Machine Learning & Artificial Intelligence Solution
Best Machine Learning & Artificial Intelligence Solution
-
LISA
-
LISA is Allied Universal’s Live Interactive Support AI, offering optional support through text messaging to help resolve timekeeping issues and assist with various tasks, like answering questions or offering extra shifts.
-
LISA enhances support and convenience for branch employees while promoting safe texting practices.

ALLIED UNIVERSAL (Second of Three)
 Best Mobile Technology Product Solution
Best Mobile Technology Product Solution
-
MERCURY
-
Mercury is a highly customizable propriety app that establishes a direct line of contact to your security team through its secured online network that minimizes human delays and maximizes efficiency, so Operation Managers and Shift Leaders benefit from quick and responsive checks and balances.
ALLIED UNIVERSAL (Third of Three)
 Best Security Workforce Management Solution
Best Security Workforce Management Solution
-
HELIAUS
-
HELIAUS® is a sophisticated Artificial Intelligence (AI)-driven solution that goes beyond the outmoded “detect and respond” risk management model and optimizes security operations by providing intelligent recommendations to minimize risks.

-
More than just a tour or incident management system, HELIAUS® is a comprehensive workforce management solution that uses powerful algorithms to generate risk-averse advisements to keep your security professionals connected and engaged, situationally informed, and armed with the right recommendations to create safer, more secure environments effectively.
-
The bottom line is HELIAUS® can help reduce security and safety incidents by up to 20%, all while improving profitability and your bottom line, by providing real-time communication and insights to security leaders, enhancing protection for people, brand, and assets.
-
*Allied Universal and its subsidiaries have been Recognized for Five Years in the Annual ‘ASTORS’ Awards Program.
AMAROK
 Best Perimeter Protection System
Best Perimeter Protection System
-
FORTIFEYE™ featuring the Electric Guard Dog™ Solar-Powered Fence
-
FORTIFEYE™ provides multiple layers of integrated protection security, starting with AMAROK’s award-winning Electric Guard Dog™ fence, an intimidating 10-foot tall barrier looming behind an existing perimeter fence. It’s a full-perimeter, solar-powered electric fence that delivers 7,000 volts of memorable but non-fatal shock.

-
Flexible and fully monitored, FORTIFEYE™ includes an alarm panel and keypad to permit controlled access.
-
Diligently protect your commercial property with FORTIFEYE – the nation‘s first fully integrated perimeter security solution using electric fencing, video surveillance, and video monitoring.
-
AMAROK’S full-perimeter solar-powered electric fences and integrated security solutions cost up to 90 percent less than traditional security guards and are truly an ultimate crime prevention solution.
(Protect your commercial property with FORTIFEYE – the nation’s first fully integrated perimeter security solution using electric fencing, video surveillance, and video monitoring. Deter, detect, and detain criminals from breaching your perimeter with AMAROK. Courtesy of AMAROK and YouTube.)
-
*AMAROK has been Honored for their Sixth Year in the Annual ‘ASTORS’ Awards Program.
AMERICAN SIGNAL Corporation
 Best Disaster Preparedness and
Best Disaster Preparedness and
Disaster Recovery Solution
-
CompuLert™ NEXGen
-
CompuLert NEXGen is built to provide mobility, reliability, and performance as an industry-leading mass notification platform.
-
Cloud-enabled, available as SaaS (Software as a Service), or on-premises, CompuLert™ NEXGen is a multi-threat detection multi-channel mass notification platform capable of interfacing with virtually any threat detection device and communicating life safety information over a myriad of technologies.

-
CompuLert™ NEXGen provides simple, effective solutions to monitor and control emergency siren systems while maintaining a user-friendly administration interface.
-
From one siren system to thousands of sirens located in separate geographic regions, CompuLert™ NEXGen provides intuitive command and control capabilities.
-
CompuLert™ NEXGen’s integration capabilities also provide advanced detection and warning capabilities to pre-existing system networks.
-
The CompuLert™ NEXGen platform includes both hardware and software, and is fully-integrated with ASC’s full line of emergency warning sirens, and can also be interfaced with numerous sensing and detection devices.
ARMIS
Best Vulnerability Management Solution
-
Armis Centrix™ Asset Intelligence Platform
-
The Armis Asset Intelligence platform is an agentless SaaS platform that automatically collects and analyzes asset data, delivering comprehensive asset intelligence.
(Armis Centrix™, the cyber exposure management platform, is powered by the Armis AI-driven Asset Intelligence Engine, which sees, secures, protects, and manages billions of assets worldwide in real-time. Its seamless, frictionless, cloud-based platform proactively mitigates all cyber asset risks, remediates vulnerabilities, blocks threats, and protects your entire attack surface. Courtesy of Armis and YouTube.)
-
Armis seamlessly works with existing IT management and security solutions and network infrastructure to discover, classify, assess, and continually monitor every connected asset— managed or unmanaged—in an environment supporting Zero Trust security.
ATHENA Security (First of Two)
 Best Gunshot Detection Solution
Best Gunshot Detection Solution
-
Athena Weapons Detection System
-
Athena’s Weapons Detection System is an active walk-through metal detection, induction lidar, and visual camera with AI, allowing both auditory and visual alert options, and can be set up outdoors and easily transported for event security or conveniently situated permanently in an indoor space.
-
Athena Weapons Detection System can protect your business, school, and/or community and can be deployed at scale around entire cities.
(Learn how to keep your employees and guests safer by connecting Athena’s Weapons Detection System to your Smart Door Control/Access Control. Save money on doorways that are not high volume, like employee entrances or even low volume side doors, as it can eliminate the need for staff at every entranceway. Courtesy of Athena Security and YouTube.)
ATHENA Security (Second of Two)
 Best Metal/Weapons Detection Solution
Best Metal/Weapons Detection Solution
-
Athena Weapons Detection System
-
More than 3000 weapons in 2022 were identified by Athena’s Concealed Weapon Detection System in hospitals, schools, and casinos throughout the United States.

-
When combined with Athena’s Visitor Management System, Entrance Pass, the system will allow your patients and visitors to enter your facility fast and friction-lessly while maintaining a high level of security at your entranceway.
-
A Visitor Management system that can talk to your Weapons Detection System is key for security.
AUTOMATIC SYSTEMS AMERICA
Best Pedestrian Entrance Control Solution
-
FirstLane PLUS Speed Obstacle Gate
-
Automatic Systems America continues to evolve its award-winning FirstLane obstacle swing door speed gate to offer customized solutions that meet customer requirements for even the most unique installations.

-
The FirstLane provides a modern design combining glass and various materials and finishes and interactive lighting for a more intuitive user experience.
-
These newest models to the Automatic Systems pedestrian portfolio feature an attractive minimalist design, which allows them to fit perfectly in environments where a medium level of security is required.
-
With this expansion, the FirstLane speed gates are now available in an outdoor model called the FirstLane PLUS.
-
The new FirstLane PLUS speed gate was designed with aerodynamic obstacles to withstand outdoor conditions (IP44). Models are available with obstacles of heights from 35 to 7- inches, thus helping to prevent fraud by physically blocking access to unauthorized persons attempting to jump over the equipment.
(See the FirstLane PLUS speed gate’s great success at ISC WEST 2023 in Las Vegas. Discover the wrap-up interviews of Nicolas Saillé, CEO of Automatic Systems, and David Enderle, President of Automatic Systems America. Courtesy of Automatic Systems and YouTube.)
-
The FirstLane series provides high bi-directional throughput without compromising the user’s safety.
*Automatic Systems is also a Returning Premier Sponsor for the Seventh Consecutive Year in the ‘ASTORS’ Awards Program, and a Platinum ‘ASTORS’ Awards Champion in all Eight Homeland Security Awards Programs. Thank you for your continued support of American Security Today!
AXIS Communications (First of Three)
 Best Image Technologies Solution
Best Image Technologies Solution
-
AXIS Q6225-LE PTZ Camera
-
The AXIS Q6225-LE is a robust PTZ network camera ideal for wide and long-distance surveillance.
-
A heavy-duty camera, it ensures reliable operation in the toughest conditions and is enclosed in a vandal-resistant casing that can withstand winds up to 152 mph.
(Ideal for wide and long-distance surveillance, AXIS Q6225-LE is specially designed with high precision PTZ and long-range OptimizedIR. It features a ½” sensor, 30x optical zoom, and built-in analytics to alert you when needed. Courtesy of Axis Communications and YouTube.)
AXIS Communications (Second of Three)
 Best Thermal, Infrared Camera Solution
Best Thermal, Infrared Camera Solution
-
AXIS Q1961-TE Thermal Camera
-
The AXIS Q1961-TE Thermal Camera can remotely measure temperatures from -40 °F to 660 °F and can trigger a notification whenever the temperature passes a set threshold – or if the temperature increases or decreases too rapidly.
-
The AXIS Q1961-TE Thermal Camera supports up to 10 configurable polygonal detection areas, making monitoring areas for specific temperature levels possible.
(Ideal for patrolling large sites, this robust thermal camera lets you remotely monitor temperatures and trigger temperature-based events. It also offers early fire detection analytics and built-in cybersecurity features. Courtesy of Axis Communications and YouTube.)
AXIS Communications (Third of Three)
Best Intrusion Detection & Prevention Solution
-
AXIS Q1656-DLE Radar-Video Fusion Camera
-
The AXIS Q1656-DLE Radar-Video Fusion Camera delivers deep learning-powered object classification based on the fusion of two powerful technologies: video and radar,
-
The AXIS Q1656-DLE is ideal for accurate 24/7 detection and wide-area intrusion protection, delivering improved scene intelligence combined with the forensic value of video.
(Get wide-area intrusion protection and reliable 24/7 detection with a fusion of two powerful technologies: video and radar. This unique device provides state-of-the-art deep learning-powered object classification for next-level detection and visualization. Courtesy of Axis Communications and YouTube.)
-
For over 30 years, Axis Communications has been an established network video and security innovator. As a team pioneering intelligent network technology, the company strives to continue to push the limits with leading network video solutions, access control solutions, audio solutions, training, and technical support – all working together for a smarter, safer world.
-
*Axis Communications, a Canon Company, has also been recognized as an ‘ASTORS’ Awards Champion for their Seventh Consecutive Year in American Security Today’s Homeland Security Awards Programs.
BACKBOX
 Best Vulnerability Management Solution
Best Vulnerability Management Solution
-
Network Vulnerability Manager
-
The BackBox Network Vulnerability Manager is the first platform that combines network automation and network device vulnerability management in a way that is purpose-built for network teams to discover vulnerabilities in their network easily, prioritize them according to the risk to their own environment, and automate multiple levels of remediation, no matter the network complexity.
(Watch the demo with Tech Field Day to learn more. Courtesy of BackBox Software and YouTube.)
-
BackBox is trusted to automate network and security device upgrades and critical tasks on over 5000 networks worldwide.
-
NetOps teams use BackBox Network Vulnerability Manager to understand the risk profile of their exact network device inventory and automate the updates that minimize their network vulnerabilities.
-
*BackBox is a Returning Competitor to the 2023 ‘ASTORS’ Awards Program, having secured Multiple Wins in 2022 Homeland Security Awards.
BROTHER International (First of Two)
 Best Device Visibility and Control Solution
Best Device Visibility and Control Solution
-
BRAdmin Professional 4
-
The BRAdmin Professional 4 is a useful fleet management tool used across industries by many businesses of different sizes.

-
This tool lets IT administrators view all machine statuses within the company’s network on a single platform.
-
The BRAdmin Professional 4 is ideal for managing and deploying Brother network-connected devices from one central location and allowing users to push security settings to a fleet of Brother printers.
BROTHER International (Second of Two)
Best IT Access Control & Authentication Solution
-
BRAdmin Professional 4 users can see how their printer fleet is performing and change device settings for the entirety of their fleet in one single step, including automatic configuration when a new Brother device is detected on the network.
-
For direct cloud management of select Brother devices with no software installed locally, BRAdmin Professional 4 supports Microsoft Azure.
(Introducing the BRAdmin Professional 4 fleet management tool. Courtesy of Brother and YouTube.)
CANON U.S.A. (First of Two)
 Best IP Video Surveillance Solution
Best IP Video Surveillance Solution
-
Canon MS-500 Camera
-
Canon’s relationships in the government and security industries proved that there was a need for camera technologies to capture images at long distances, in the dark, and in adverse conditions.
-
The Canon MS-500 is designed to be a robust addition to a high-precision monitoring system that addresses these requirements.
-
In areas with extremely high-security levels, such as seaports, public infrastructure facilities, and national borders, high-precision monitoring systems are required to accurately surveil targets both day and night.
(Find out how the Ultra-High-Sensitivity MS-500 multi-function camera with the SPAD (Single Photon Avalanche Diode) sensor innovates long-range surveillance even in dark conditions. Courtesy of Canon U.S.A. and YouTube.)
-
The new MS-500 camera is the world’s first ultra-high-sensitivity camera equipped with a SPAD sensor, achieving a minimum subject illumination of 0.001 lux3.
-
When combined with ultra-telephoto broadcast lenses, it may be possible to capture clear color videos of subjects at a distance of several miles, even at night.
CANON U.S.A. (Second of Two)
 Best IT Access Control & Authentication Solution
Best IT Access Control & Authentication Solution
-
uniFLOW Online
-
uniFLOW Online is recognized for its usability, flexible and straightforward design, advanced scanning, and extensive security features.
-
uniFLOW Online is designed to help customers keep control over access to their systems and critical information, as well as to give them the dual advantage of staying connected while having the flexibility to work from their office or home.
-
Combining multifunctional devices with a print management solution is intended to help limit unauthorized use and help users implement security features around their valuable and confidential information.
(Did you know that using cloud-based servers for your document workflows saves you money? uniFLOW Online gives you this and much more, such as providing a user-friendly interface to manage and track your organization’s print activity. Courtesy of Canon and YouTube.)
-
uniFLOW Online can be used as part of an organization’s Zero Trust efforts, enabling users to release print jobs after authentication. Organizations can use the requirement to use login credentials to connect with uniFLOW Online as part of their Zero Trust efforts with respect to verification.
-
Offering multiple levels of privileged access and the ability to assign access by role can be part of an organization’s Zero Trust efforts to use least-privileged access.
-
*Canon U.S.A. has now been recognized as a Multiple ‘ASTORS’ Awards Champion for their Eighth Consecutive Year in the Annual Homeland Security Awards Program.
CELLBUSTERS
Best Cell Phone Detection Solution
-
Zone Protector
-
The Zone Protector™ from Cellbusters provides maximum protection for your sensitive environments by continuously scanning for cell phone and user-selectable RF transmissions and is far more sophisticated than a cell phone detector.
-
Comparable to a spectrum analyzer, the Zone Protector™ can scan user-definable frequency ranges and alert, notify, control a third-party device, or simply log as soon as it detects relevant transmission activity.

-
Precise frequency filtering technology, managed and controlled by a 32-bit microprocessor, enables the Zone Protector™ to deliver accurate detection with virtually zero false positives.
-
Once cellular or appropriate RF activity is detected, the Zone Protector™ can be set to activate a choice of alerting options or to log all detected activity silently.
-
Additionally, Cellbusters Zone Protector has now been updated to detect 5G phones, proving a leading edge in the market, and protecting investment in this technology for years to come.
(See a quick overview of the Zone Protector and the Zone Manager, both cell phone detection technology from Cellbusters. Courtesy of Cellbusters and YouTube.)
-
*Cellbusters has officially been recognized as an ‘ASTORS’ Award Champion in all Eight ‘ASTORS’ Awards Programs. Thank you for your continued support of American Security Today!
CENSYS
 Best Cyber Security Solution
Best Cyber Security Solution
-
Censys Attack Surface Management (ASM)
-
Censys, a leader in Attack Surface Management (ASM), enables organizations to continuously monitor, discover, inventory, classify, and prioritize sensitive external assets within an agency’s IT infrastructure.
-
Built from best-in-class Internet Discovery Algorithms and cloud connectors, the Censys ASM Platform arms organizations with the critical information they need to find, monitor, and understand their Internet-facing assets to identify and remediate advanced threats and exposures.
-
The most dangerous threat to any federal agency is the unknown – and a great ASM tool helps illuminate the risks you never knew you had, like Shadow IT assets, S3 Bucket misconfigurations, and more.
(See how Censys Attack Surface Management (ASM) continually uncovers unknown assets ranging from Internet services to cloud storage buckets and comprehensively checks all your public-facing assets for security and compliance problems regardless of where they’re hosted. Courtesy of Scientific Analytical Tools and YouTube.)
-
The threat environment is rapidly evolving, and bad actors are adjusting their tactics at alarming rates. As a result, agencies need to be vigilant to protect themselves and their customers from harmful breaches. With Censys, agencies can get the most accurate data available, enabling teams to take down threats as close to real-time as possible.
-
This isn’t security by defense. This system of vigilant offense constantly looks at everything – including HTTP hosts, message brokers, remote desktop exposure, and network printers – and seeks potential breaches, shoring up leaks in your protocols, and maps out any potential weak points. Censys helps you stay one step ahead of the adversary by identifying threats before they become complications.
-
Censys continually checks all of your Internet assets (even the ones you didn’t know about) for misconfigurations and security problems regardless of provider.
CLOPAY Corporation (First of Two)
Best Fire & Safety Solution
-
CrossingGard® Grille and Door with ThreatProtect™
-
Clopay Corporation, a leader in closure products for commercial, residential, industrial, institutional, and retail applications, introduces CrossingGard™ with ThreatProtect™ available on grilles, doors, or insulated doors through its Cornell and Cookson brands.

-
CrossingGard with ThreatProtect creates lockdown zones within a building when a hostile event alarm is triggered or opens to allow freedom of movement in the event of a fire alarm.
-
ThreatProtect controls are determined by end-user protocol based on the building design & emergency management plans. The operating system uses two alarm inputs and a self-contained backup power supply to provide ultimate flexibility in managing threatening situations.
-
Ideal for educational facilities, medical complexes, and large venues, CrossingGard with ThreatProtect can help restrict an intruder from moving freely about the building, obstruct an intruder’s view, or open egress for evacuation.
CLOPAY Corporation (Second of Two)
Best Integrated Security Management Solution
-
CrossingGard® Grille and Door with ThreatProtect™
-
CrossingGard with ThreatProtect is a versatile alarm-triggered rolling door or grille that serves a dual purpose: deploying to establish secure lockdown zones during hostile incidents or opening for unhindered movement through escape routes during fires.

-
ThreatProtect’s adaptable controls are tailored to user specifications, meeting the unique needs of a specific building’s architecture and emergency strategy. This innovation is especially suited for educational and government establishments.
-
It not only hinders intruders by limiting their movement and visibility but also facilitates swift evacuation. Unlike conventional products that typically close upon alarm activation, CrossingGard with ThreatProtect equips operators with the capability to fluidly alternate between alarm inputs, addressing real-time threats more effectively.
-
Its adaptability extends to all areas of a building’s response plan, helping response teams mitigate and neutralize real-time threats more efficiently.
-
*Clopay Corporation is a Returning ‘ASTORS’ Awards Champion, having secured Wins in the 2022, 2021, and 2019 Homeland Security Awards Programs.
CLOUD RANGE
 Best Cyber Defense (TEAM) Training Solution
Best Cyber Defense (TEAM) Training Solution
-
FlexRange™ Cyber Range and Simulation Training Program
-
With an acute shortage of cybersecurity professionals worldwide, organizations are challenged to find, hire, and retain experienced cyberdefenders.

It is a live, virtual, instructor-led simulation exercise where SOC/IR/DFIR teams can practice and hone their skills on unlimited attack scenarios in a safe, controlled cyber range environment.
-
Just as pilots must train in a flight simulator, Cloud Range uses simulation exercises to improve technical proficiencies and soft skills, including hands-on labs, assessments, and real-world cyber attack detection, remediation, and incident response to reduce the organization’s risk.
-
Cloud Range’s core solution, FlexRange™ Cyber Range and Simulation Training is a full-service program of immersive, simulation-based training missions and lab exercises. FlexRange is for customers who want to ensure an ongoing and consistent program for their teams that ensures preparedness for the most complex cyber-attacks.
-
Cloud Range provides a customized, comprehensive, immersive cyber simulation learning experience that uses live-fire simulation exercises to train, test, assess, and solidify the capabilities of cyber professionals on an ongoing basis and as a team to keep up with the ever-changing threat landscape.
(Cloud Range CEO and founder Debbie Gordon shares her thoughts on preparing security operations teams and highlights the importance of readiness when confronting cyber threats in enterprise security. Courtesy of Cloud Range, TAGCYBER, and YouTube.)
-
95% of Cloud Range customers report that Cloud Range’s FlexRange simulation exercises help them and their team be more prepared for future events. Additionally, Cloud Range has a 99% customer renewal on program subscriptions.
COBWEBS Technologies
 Best Web Intelligence Solution
Best Web Intelligence Solution
-
Tangles Web Open-Source Intelligence Platform
-
With a team of experts comprised of leading military and intelligence masterminds, Cobwebs is revolutionizing cyber intelligence with AI-driven solutions.
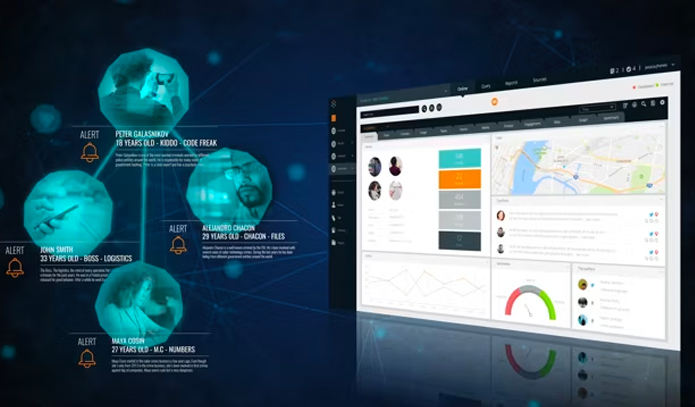
-
Its award-winning technologies are tailored to solve complex real-world challenges and to produce valuable insights from oceans of big data. This team creates powerful cyber intelligence software to support smooth, seamless, and smarter operations and investigations in national security agencies, law enforcement, and private sectors, ultimately making the world safer.
-
Cobwebs Technologies’ Web Intelligence Platform (Tangles) is a powerful open-source intelligence solution that searches online activity, collecting and analyzing data from endless digital channels – from the open, deep, and dark web.
-
The Cobwebs platform provides access to the most updated data with worldwide coverage and allows users to collect publicly available data across all layers of the World Wide Web. This includes the latest digital platforms, darknet, traditional media, multimedia and video, global information registries, millions of corporate profiles, blogs, and dynamic forums, and billions of data points and risk entities.
(Cobwebs Technologies delivers AI-powered open-source intelligence for the most comprehensive multi-layer investigation platform. Organizations worldwide rely on Cobwebs Technologies to enhance security operations, make risk-based decisions, and protect from threats. Courtesy of Cobwebs Technologies and YouTube.)
-
Its customers harness this web intelligence technology to strengthen their risk profiles and gain true threat intelligence to neutralize crime and cyberattacks with agility and accuracy. Cobwebs allows corporate security teams to bridge the digital and physical world with its ability to deanonymize threat actors anywhere, and this battle-proven technology is used by law enforcement agencies and homeland security departments worldwide.
-
Cobwebs also partners with non-profits and agencies to provide access to valuable intelligence to increase the potential of identifying concrete threats. The use of this platform increases the ability to locate missing persons and victims of human trafficking as well as identify criminals in cases such as fraud and extortion.
CODESECURE
 Best Software Supply Chain Security Solution
Best Software Supply Chain Security Solution
-
CodeSentry
-
CodeSentry is a Binary BCA solution that identifies open-source components and shared dependencies in binaries, including firmware, containers, and mobile or desktop applications.
-
The resulting component inventory is reported through an SBOM, also mapped to VulnDB, the industry’s most complete database of software vulnerabilities.
-
CodeSentry is CodeSecure’s leading Binary Composition Analysis (BCA) solution for gaining component inventory and insights into vulnerabilities and software risk, generating SBOMs, supporting Vulnerability Disclosures, and responding to Software Supply Chain Security (SSCS) risks.
(CodeSecure (formerly the product division of GrammaTech) is a global provider of application security testing solutions, including static analysis (SAST) and software composition (SCA) products. Their products, CodeSonar and CodeSentry, help organizations develop and release higher quality and more secure software – free of harmful defects and exploitable weaknesses that cause system failures, enable data breaches, and increase corporate liability. Courtesy of CodeSecure and YouTube.)
-
*CodeSentry was also recognized in the 2022, 2021, and 2020 ‘ASTORS’ Homeland Security Awards Programs, respectively.
CONCENTRIC.ai
 Best Big Data Analytics Solution
Best Big Data Analytics Solution
-
Semantic Intelligence for
Data Security Posture Management (DSPM)
-
Concentric’s Semantic Intelligence is a SaaS-based, data security posture management and access governance solution that utilizes deep learning to automatically discover and classify sensitive data, identify risk, and remediate issues.
-
Concentric provides agentless connectivity to various data repositories so you can govern access to your data wherever it resides, processing both structured and unstructured data in the cloud or on-premises.
(Learn how Concentric protects the millions of reports, financial documents, spreadsheets, and other business-critical documents your employees use daily, with the Semantic Intelligence© solution for unstructured data security. Courtesy of Concentric AI and YouTube.)
-
The Semantic Intelligence Solution finds and catalogs file content, metadata, usage patterns, location, regulated data, and security context to give you a crystal-clear picture of a file’s sensitivity and role within your organization. Concentric’s deep learning engine works autonomously, accurately, and without end-user involvement, unlike other solutions that use rules or regular expressions.
-
Concentric’s data security posture management enables organizations to gain a clear view of the where, who, and how of their sensitive data: where it is, who has access to it, and how it has been used.
CORDONIQ
 Best Secure Video Workforce Management Solution
Best Secure Video Workforce Management Solution
-
Cordoniq Secure Video Conferencing Platform
-
Cordoniq’s secure, smart enterprise video collaboration platform addresses enterprise business needs beyond standard legacy video conferencing software and toward truly secure video collaboration solutions.
-
Cordoniq provides custom interfaces that free organizations from privacy issues, broken APIs, and meeting room expirations, with unique web content and sharing that enables clients to use not just their screen – but their actual browser inside meetings to collaborate with teams and clients.
(Created by software developers for developers, Cordoniq is designed to integrate easily with your tech stack’s APIs, apps, and software products. Never compromise meeting security when you have all the tools and controls you need to video collaborate with team members and business clients. Courtesy of Cordoniq and YouTube.)
-
Cordoniq is designed to integrate into businesses in a way that makes the experience feel as if it is seamlessly blended into the overall environment.
-
Cordoniq is a video collaboration platform for private, hybrid cloud trusted by the Department of Defense, the Pentagon, Special Operations Forces, and the National Guard.
-
Cordoniq provides up to military-grade video conferencing security.
CROTEGA Safety Solutions
 Best Personal/Protective Equipment Product
Best Personal/Protective Equipment Product
-
SentriPac 64 Backpack with Repulse
-
Crotega Safety Solutions SentriPac is a battery-powered backpack chemical irritant tactical defense and crowd control tool.
-
This patent-pending powerful sprayer, using the 2021 ‘ASTORS’ Award Champion REPULS chemical irritant, reaches 35 plus feet with a ballistic stream of highly irritating chemical irritants, causing immediate involuntary eye closure without causing distress to breathing.
-
SentriPak carries 64 oz. of REPULS that can quickly be reloaded by replacing the disposable bag with a full 64 oz. bag of REPULS.
-
SentriPak will provide 60 plus two-second bursts from one 64 oz supply of REPULS compared to 32 two-second bursts from the nearest MK-60 competitor.
(See the power and distance of the SentriPac Backpack for law enforcement and the distance of the spray. The spray can spray up to 30′, dispensing the patented self-defense “Repuls” solution that Crotega uses to neutralize active shooters and attackers in a non-lethal way and save lives. The SentriPac is used in larger crowds to control those causing trouble and disruption. Courtesy of Crotega and YouTube.)
-
*Crotega is a Returning ‘ASTORS’ Award Champion, having secured Wins in the 2021, 2019, and 2018 Homeland Security Awards Programs.
CYEMPTIVE Technologies (First of Seven)
Best Anti-Malware Solution
-
Cyemptive Endpoint Command
-
Cyemptive Endpoint Command protects endpoints with sophisticated and pre-emptive technology.
-
Advanced forms of unknown Ransomware can go undetected in targeted systems and require a multi-level approach with a unique detection technology.
-
Cyemptive combines Perimeter Command, Endpoint Command, Infrastructure Command, and Cyemptive Security Command solutions to solve Ransomware.

Have total empowerment using military-grade layers of pre-emptive technology that stops the threats in seconds before infiltration.
CYEMPTIVE Technologies (Second of Seven)
Best Cyber Critical Infrastructure Solution
-
Cyemptive Infrastructure Command
-
Infrastructure Command utilizes the Cyemptive DNS Fortress and Cyemptive Time Fortress layers to secure the most critical protocols compromised by bad actors, prevent damage, and secure critical infrastructure with ZeroStrike capabilities.
-
Layered with the Cyemptive Perimeter Fortress, the Infrastructure Command creates a powerful, ultra-secure infrastructure for the organization, allowing clients to stay in command of their security.
-
CYEMPTIVE Technologies (Third of Seven)
Best Data Storage Security Solution
-
Cyemptive Data & File Command
-
Cyemptive’s Data & File Command, using CyberScan technology, is a revolutionary platform that scans all files in an environment to detect encryption and stop ransomware before it enters and harms operating systems or networks, stopping infiltration even from insider threats.
-

CYEMPTIVE Technologies (Fourth of Seven)
Best Cloud Computing/Storage Solution
-
Zerostrike Cloud Command
-
Cyemptive’s ZeroStrike Cloud Command provides secure cloud protection for cloud providers and protects their clients’ data from ransomware and even previously unknown Zero-Day attacks.
-
CYEMPTIVE Technologies (Fifth of Seven)
 Best Network Security Solution
Best Network Security Solution
-
Cyemptive Perimeter Command
-
Cyemptive Perimeter Command provides complete network and endpoint protection for ZeroStrike protection, reducing risk and protecting critical perimeters to stop threats and quantum attacks while providing pre-emptive security on the network and perimeter level.
-
CYEMPTIVE Technologies (Sixth of Seven)
 Best SIEM (Security Incident & Event Management) Solution
Best SIEM (Security Incident & Event Management) Solution
-
Cyemptive Security Command
-
Cyemptive Security Command manages the entire cyber security environment with a self-protected command center leveraging ZeroStrike, architected with End-to-End Zero Trust, deployed on-premises, and available with optional SOC service offerings.

CYEMPTIVE Technologies (Seventh of Seven)
 Best Zero Trust Cyber Solution
Best Zero Trust Cyber Solution
-
Cyemptive Zerostrike Solutions
-
Cyemptive’s Zerostrike Cloud Command safeguards cloud infrastructure and allows customers to build a reputation for security excellence. Cyemptive’s multi-level solutions prevent and eliminate threats to data in flight, in use, and at rest. Zerostrike Cloud Command stops and eliminates threats in private, hybrid, and public cloud environments.
-
CYTTA CORP. (First of Three)
 Best Emergency Response Program for Federal/State or Local
Best Emergency Response Program for Federal/State or Local
-
CyttaCARES (Crisis Alert and Response Emergency System)
-
CyttaCARES is Cytta Corp’s revolutionary SOS mobile app solution that enables schools and educational institutions to immediately connect with all designated First Responders through video and audio.
-
CyttaCARES provides real-time alerts, rapid two-way secure video communication, and efficient response coordination, ensuring the well-being of students, staff, and faculty.
-
With its user-friendly, simple interface, CyttaCARES users can quickly initiate emergency notifications through a designated app and other channels like SMS, emails, and push notifications.
(Cytta CARES (Crisis Alert and Response Emergency System) is an innovative software-as-a-service solution designed to enhance safety and security in educational institutions, especially during emergency situations. Courtesy of Cytta Corp. and YouTube.)
-
CyttaCARES enables two-way communication, allowing individuals to report incidents or request assistance instantly, and provides live location tracking to emergency response teams, enabling better coordination and resource allocation.
-
By leveraging technology, CyttaCARES empowers educational institutions to proactively address emergencies, mitigate risks, and safeguard their community effectively.
CYTTA CORP. (Second of Three)
 Best Security Incident & Event Management Solution
Best Security Incident & Event Management Solution
-
CyttaCOMMS
-
The Cytta IGAN 2.0 application and system – now known collectively as CyttaCOMMS – is a highly secure, SaaS-based advanced system that offers near real-time, integrated communications for multiple video and voice devices.
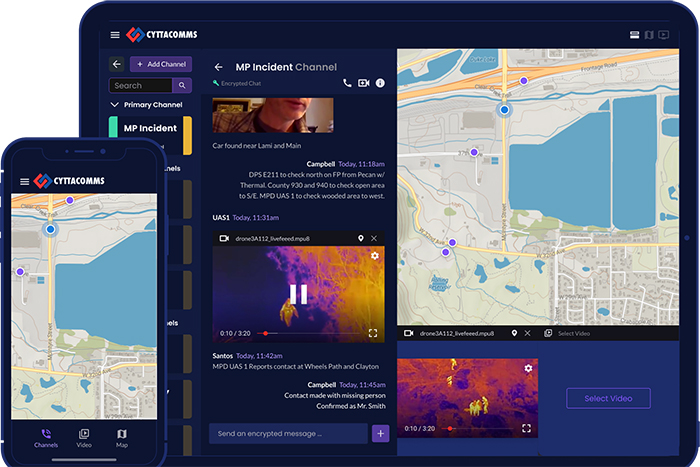
-
CyttaCOMMS integrates various video and audio streams, including drones, body cams, fixed cameras, and cell phones, to provide law enforcement with near real-time situational awareness and actionable intelligence to enhance their operations.
CYTTA CORP. (Third of Three)
 Best Wireless Video Surveillance Network Solution
Best Wireless Video Surveillance Network Solution
-
CyttaCOMMS
-
Cytta Corp.’s proprietary CyttaCOMMS (IGAN 2.0) software video streaming solution has been significantly expanded and deployed with multiple organizations.
-
CyttaCOMMS cloud-based SAAS communication network provides an interactive desktop/mobile user interface for quick visual reference and multiparty collaboration with streaming video, location maps, messages, and communications (video/voice/text).
-
The IGAN collaborative video, voice, chat, and media integration tool makes it easy to share and store critical real-time data, such as video feeds, images, chat, files, messages, location maps, and media.
(See CyttaCOMMS (IGAN v2.0) for yourself. Courtesy of Cytta Corp. and YouTube.)
-
CyttaCOMMS is a practical, valuable, and irreplaceable tool for police, firefighters, first responders, emergency medical workers, industry, environmental and emergencies, security, military, and their command centers in a crisis.
-
It also allows venues such as schools, malls, event venues, and religious locations to be connected and monitor their situations, as well as immediately make their data directly available to law enforcement during emergencies.
-
*Cytta Corp. is a Returning ‘ASTORS’ Award Champion, having been Recognized in the 2022 Homeland Security Awards Program.
D-FEND Solutions
 Best Counter-UAS Solution
Best Counter-UAS Solution
-
EnforceAir2
-
EnforceAir’s non-jamming, non-kinetic, no-line-of-sight required counter-UAS technology avoids collateral damage, interference, disruption, and disturbance, preserving communications and operational continuity.
-
The new EnforceAir2 brings enhanced, expanded, and extended counter-UAS capabilities with even more power, performance, portability, and range, all in a compact footprint.
(D-Fend Solutions is the leading RF cyber-based counter-drone takeover technology provider for sensitive and challenging environments. Focused on the most dangerous drone threats, the company’s EnforceAir non-jamming, non-kinetic system avoids collateral damage and disruption while providing end-to-end detection and mitigation for situational awareness, operational continuity, and safe controlled outcomes. Courtesy of D-Fend and YouTube.)
-
EnforceAir now reaches new heights in enabling full control, safety, and continuity during rogue drone incidents with the introduction of EnforceAir2, the next-generation high-performance cyber counter-UAS system with seamless operational flexibility.
-
D-Fend’s cyber takeover capabilities provide end-to-end detection and mitigation for situational awareness and operational continuity.
-
*D-Fend is a Returning Champion, having secured Wins in the 2022 and 2021 ‘ASTORS’Awards Programs.
DATA Theorem
 Best CNAPP Solution
Best CNAPP Solution
-
Cloud Secure
-
Cloud Secure is an automated, continuous security service combining CNAPP + AppSec capabilities across all your multi-cloud (public and private) assets.
-
Cloud Secure monitors your cloud configs (CSPM) against audit/compliance policies, identifies vulnerabilities (SAST/DAST/SCA/IaC) in your code repositories, and helps to prevent data breaches and exploits with attack path analysis across APIs, cloud services, and software supply chains.
-
Using the underlying Analyzer Engine, Cloud Secure continuously discovers and publishes an inventory of all cloud assets, including APIs, containers, databases, storage, serverless, and secrets management. CSPM, KSPM, CIEM (IAM), and a variety of CNAPP issues are available via dashboards and alerts.
(Watch as Doug Dooley, COO at Data Theorem, analyzes the future of cloud security and explains how Data Theorem’s Cloud Secure expands beyond CSPM’s protection of infrastructure and network to a more app-centric approach to protect core assets like code and serverless functions through offensive and defensive toolkits. Courtesy of Data Theorem and YouTube.)
-
Hacker Toolkits allow customers to conduct automated red-team, pen-testing exercises across the various attack surfaces within their cloud-native application stack. Hacking the cloud is a powerful form of attack surface management that reduces the probability of a preventable data breach.
-
Automated protections and runtime observability of cloud-native applications help customers remediate problems faster in their multi-cloud environments. Data Theorem’s SDK libraries allow for real-time telemetry collection and policy-based blocking across cloud-native APIs and applications. Unlike many competitors, with Cloud Secure the detection and prevention is done without the use of any traditional agents or network firewalls.
DATABUOY Corporation
 Best Outdoor Gunshot Detection Solution
Best Outdoor Gunshot Detection Solution
-
Shotpoint® and Shotpoint® Vertical
-
Databuoy’s Shotpoint® outdoor gunshot detection system has been a valuable life safety asset in high-profile areas like the Fremont Street Experience in Las Vegas, enabling responders to have immediate situational awareness surrounding gunshot incidents.
-
Shotpoint’s wide-area outdoor coverage is unique, with sensors up to 165 ft. apart and often located in the most volatile environments imaginable (see the Fremont Street Experience white paper).
(See an investigative report by KLAS Channel 8 in Las Vegas on the Shotpoint system installed at the Fremont Street Experience, featuring commentary from Nick Jones, Chief Sales Officer at Databuoy. Courtesy of Databuoy, KLAS, and YouTube.)
-
Shotpoint® integrates with the customer’s video management and access control systems, allowing real-time reports and notifications to be delivered to mobile devices and third-party systems without slow and unreliable human interaction.
-
In addition to reliability, accuracy, and automated real-time notifications, Shotpoint® is the only gunshot detection solution capable of identifying and resolving the trajectory angle of an elevated shooter.
(See a demonstration of Databuoy’s ability to localize an active shooter in a 3D environment in a proof of concept that was not only the first of its kind in the gunshot detection and localization industry but also the first step in what is now recognized as the best system by security experts. Courtesy of Databuoy and YouTube.)
-
Its unique capability to detect sniper shots and locate shooters in vertical space based on the bullet’s trajectory is particularly valuable in urban environments where echoes and other false detections easily fool other shot detection solutions.
-
Shotpoint® can remove false detections with extreme precision and deliver actionable information in seconds, so the system is being deployed for security at sporting venues like Little Caesars Arena in Detroit and events like the NFL Draft in Las Vegas.
-
*Databuoy is a Returning ‘ASTORS’ Award Champion having secured a Win in the 2021 Homeland Security Awards Program.
DEDRONE (First of Three)
 Best Machine Learning &
Best Machine Learning &
Artificial Intelligence Solution
-
DedroneTracker.AI
-
Dedrone delivers an end-to-end counter-drone solution, from detection, tracking, and identification (DTI) – to mitigation where allowed.
-
Dedrone’s advanced AI-driven autonomous C2 platform goes beyond the limits of simple sensor correlation to incorporate advanced algorithms and proprietary machine learning techniques, such as behavior model filters, neural networks, and AI-based imagery through over 18 million images.
(Advancements in technology have led to the harmful use of Unarmed Aircraft Systems (UAS), commonly known as drones. Serving as the common link between a prison drug run and delayed flights at your local airport, rogue drones have become a serious concern, posing significant risks to both national security and public safety. Take a closer look at Dedrone’s counter-drone technology and see how Dedrone delivers the full counter-drone kill chain to fortify your defenses against this threat. Courtesy of Dedrone and YouTube.)
-
Dedrone has virtually eliminated false positives in its drone detection system by leveraging these sophisticated methods, providing unmatched accuracy and reliability. The company’s cutting-edge platform and continuous commitment to innovation are changing the game for lower airspace security.
DEDRONE (Second of Three)
 Best Critical Infrastructure Protection Solution
Best Critical Infrastructure Protection Solution
-
DedroneTracker.AI
-
DedroneTracker.AI provides security teams with the best-in-class sensor-fusion AI-powered command and control for automated drone detection, identification, tracking, and mitigation.
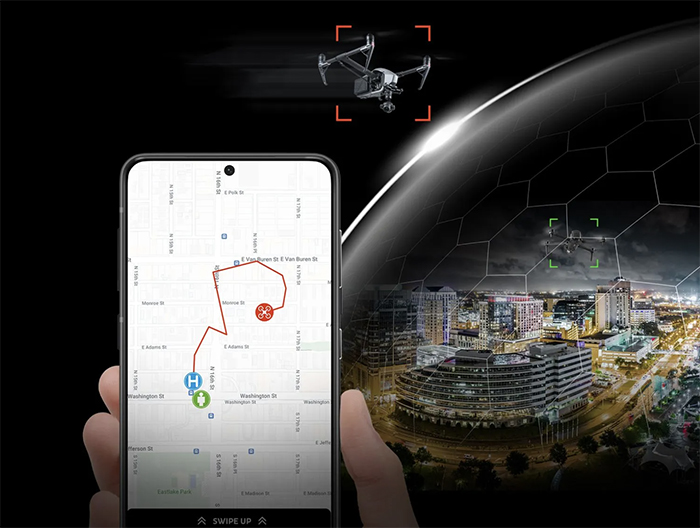
-
DedroneTracker .AI confirms drone presence and the precise location of both drone and pilot and delivers a single queue of prioritized targets through autonomous background interrogation of unauthorized drones while simultaneously tracking multiple friendly drones.
-
DedroneTracker.AI software, hosted in the cloud or on-premise, uses the DedroneDNA database to recognize and classify RF, WiFi, and non-WiFi drones.
-
DedroneTracker.AI also integrates with 3rd-party sensors and triggers alerts and countermeasures.
DEDRONE (Third of Three)
 Best Persistent Aerial Monitoring Solution
Best Persistent Aerial Monitoring Solution
-
Dedrone delivers an end-to-end counter-drone solution, from detection, tracking, and identification (DTI) to mitigation where allowed.
(During emergencies, quick access for law enforcement can mean the difference between life and death. Drones are valuable first responders but have operational limits. Conventional drones must be within the operator’s line of sight and struggle to operate in bad weather. That’s where Dedrone, the leader in airspace security, introduces DedroneBeyond – a groundbreaking drone solution. DedroneBeyond empowers local law enforcement to reach any location within the city, even BVLOS (Beyond Visual Line of Sight), cutting down the response time by a third. This is possible through cutting-edge sensors and a multifaceted platform designed with the modern urban landscape in mind. Watch how Dedrone’s technology facilitates the use of good drones and safeguards the airspace against potentially malicious Unmanned Aircraft Systems (UAS). Courtesy of Dedrone and YouTube.)
-
Dedrone’s technology has been implemented across 40 countries, including four of the G-7 nations, to accommodate the needs of law enforcement and security professionals.
-
*Dedrone is a Returning ‘ASTORS’ Award Champion, Recognized in its Third Year.
DISPERSIVE Holdings
 Best Cyber Critical Infrastructure Solution
Best Cyber Critical Infrastructure Solution
-
Dispersive Stealth Networking
-
Dispersive Stealth Networking is a modern security solution for all the mixed environments of today’s Apps, Users, and Data grounded in a simple principle: “You can’t hack what you can’t see”.
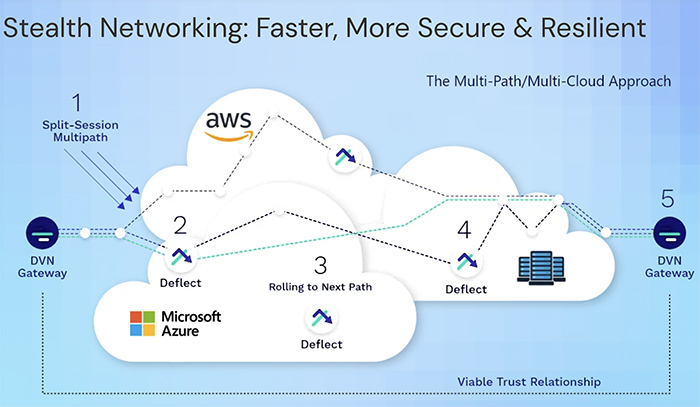
-
Dispersive replaces or augments VPNs, firewalls, and cloud-edge network access with a military-grade secure networking solution that sets up in seconds and works for all Users and Apps, even in the most hostile environments.
-
*Dispersive Holdings is a Returning ‘ASTORS’ Champion, having been Recognized in the 2022 ‘ASTORS’ Awards Program.
DRAGOS
 Best ICS/SCADA Cyber Security Solution
Best ICS/SCADA Cyber Security Solution
-
From keeping the lights on in homes to ensuring water flowing out of taps hasn’t been tampered with, Dragos protects critical infrastructure, enabling civilizations to function from cyberattacks that aim to cause massive disruption to those industrial systems.
-
Dragos is one of the most trusted cybersecurity companies in the ICS/OT market, with an unparalleled depth of OT cyber and industry expertise combined with superior technology, world-class OT-specific intelligence, and a broad range of professional services, giving customers the confidence they will realize superior value.
-
Dragos protects hundreds of key industrial organizations globally, including nine of the ten largest electric utilities in the U.S. and seven of the ten largest oil and gas companies worldwide.
-
Dragos is also the first industrial cybersecurity “unicorn,” having secured Series D funding of $200M, bringing its valuation to $1.7B. Funding rounds have been led by some of the most notable venture capital firms and industrial organizations globally, including Koch Disruptive Technologies, BlackRock, Emerson, Hewlett Packard Enterprise, National Grid Partners, and Rockwell Automation, sending a huge market signal about the size, scope, and relevance of the ICS/OT Security market.
(Learn why the Dragos Platform has the best defensive tools to combat industrial cybersecurity adversaries. Courtesy of Dragos: ICS Cybersecurity and YouTube.)
-
On September 18, 2023, Dragos announced an extension to its Series D funding round with an additional $74 million investment led by WestCap to accelerate continued geographic expansion globally and support further expansion across diverse industries.
ELECTROSOFT Services (First of Two)
 Best ICAM Lab Solution
Best ICAM Lab Solution
-
GSA Federal Identity, Credential and Access
Management (FICAM) Testing Laboratory
-
The Federal government aims to improve the security of federal systems and data while providing employees and contractors reliable access to the systems they need to do their jobs and to serve and protect our nation’s citizens.

-
Electrosoft operates the Federal government’s one and only FICAM Testing Laboratory to determine product compliance with FIPS 201, Personal Identity Verification (PIV) Guidelines, and related National Institute of Standards and Technology (NIST) Special Publications. Compliant products are placed on the Federal Approved Product List (APL), which Federal agencies must use when selecting FICAM solutions that help secure logical resources and physical facilities.
-
Operating the state-of-the-art GSA FICAM Testing Laboratory from its headquarters, Electrosoft conducts formal and rigorous technical testing of Physical Access Control (PAC) vendor products for placement on the Federal APL. For those PAC products that pass the tests, Electrosoft assures that they will properly authenticate Federal workforce access cards and fail authentication from bad access.
-
In 2022, Electrosoft stood up and started operating the GSA FICAM Testing Laboratory, quickly introducing operational efficiencies and technical innovations that saved the taxpayers’ money while providing higher value to the Federal IT enterprise.
ELECTROSOFT Services (Second of Two)
 Best Security Operations Center (SOC)
Best Security Operations Center (SOC)
-
Federal Agency SOC Transformation
Strengthens Cyber Resilience
-
For one federal civilian agency, a worldwide presence and high-profile mission to help maintain the health of the U.S. economy means it is a prime target for cyberattacks. When Electrosoft started working with the agency, its leaders emphasized a desire to become more proactive in managing the security and privacy of their data and systems.

-
Electrosoft supported the agency through a digital transformation.
-
Guiding the planning and execution of risk-based methodologies to protect the critical IT assets for the agency, the Electrosoft team set up a security operations center and supporting technologies that ensure the confidentiality, integrity, and availability of data and systems while providing privacy protections and meeting compliance mandates.
-
Significant changes included Automation, Cultural Changes, Third-Party Testing, Privacy Controls, and Compliance Support. Ultimately, Electrosoft supported the agency’s transformation to implement continuous monitoring and improvement of its information security operations, a robust privacy program, and a culture of support for information system security risk management.
-
Electrosoft’s activities helped ensure the agency’s compliance with applicable security and privacy laws and regulations, and it also increased efficiencies through automation, increased transparency through issue tracking, frequent communication and collaboration with stakeholders, and is continually updating the agency’s systems with powerful, secure technologies.
EVERBRIDGE
 Best Integrated Security Management Solution
Best Integrated Security Management Solution
-
Everbridge Control Center 5.57
-
Everbridge Control Center 5.57 connects disparate security systems to enable faster response to critical events affecting your people, facilities, and assets, anywhere in the world.

-
Control Center 5.57 correlates events from disparate safety and security systems into a common operating picture to focus people’s attention on what really matters, providing users with actionable alerts, next-step actions, automated reporting, and dashboards to better manage risks, ensure compliance with operating procedures and support your business continuity.
-
Automated workflows ensure rapid, consistent responses, reducing the risk of human error. It also facilitates device activation, ensuring you are always in operational control and protecting your people. Dynamic reports and dashboards provide real-time, actionable insights for your operations teams and senior executives.
(For many organizations, physical security management can be a daunting task. Threats are on the rise, and risks are becoming increasingly diverse. Operations also continue to grow, involving more systems, data, and users. Control Center’s continuously growing library of 250+ subsystem connectors to various safety and security technologies provides a holistic common operating picture and delivers immediate benefits to key sectors, including critical national infrastructure, energy, transportation, emergency services, and finance. Courtesy of Everbridge and YouTube.)
-
Control Center integrates seamlessly with the wider Everbridge Critical Event Management (CEM) platform. Integration with Mass Notification and Incident Communications extends your on-premises solution to communicate with relevant people such as employees, visitors, residents, or citizens.
-
Critical information can be distributed in a timely manner, and any feedback is automatically received back to factor into the workflow for any situation. Control Center also broadens the scope of your CEM capabilities, by enabling the on-premises data from your various systems to create hyper-relevant risk event feeds directly to the Everbridge CEM orchestration engine.
-
With Control Center, your organization can be safe, secure, and in operational control, now and in the future.
-
*EVERBRIDGE is a Returning ‘ASTORS’ Award Champion, Recognized in its Sixth Year.
FIBER SENSYS
 Best Perimeter Protection Solution
Best Perimeter Protection Solution
-
EchoPoint EP9300™ Series
-
The latest innovations from Fiber SenSys, EchoPoint EP9300™ Distributed Acoustic Sensors, utilize the latest technologies in fiber optic sensing and machine learning algorithms to provide an advanced solution for applications requiring long-range, point-locating intrusion detection sensors.
(Learn more about Fiber SenSys’ new EchoPoint EP9300™ Distributed Acoustic Sensors (DAS). Courtesy of Fiber SenSys and YouTube.)
-
These advancements make EchoPoint sensors a key part of the solution in large sites where precise intrusion location is needed.
-
The EchoPoint EP9300™ Series is an outstanding choice for large sites, most suitable for fence-mounted, buried, wall-top, and pipeline deployments.
-
*Fiber SenSys is a Returning ‘ASTORS’ Award Champion, Recognized in the 2020 and 2016 Awards Programs.
FIVECAST
 Best Web Intelligence Solution
Best Web Intelligence Solution
-
Fivecast ONYX Global Open-Source Intelligence Software
-
Fivecast deploys advanced data collection and AI-enabled analytics to solve complex intelligence challenges using a proprietary data collection that delivers superior data access across the surface, deep, and dark web.
-
Fivecast ONYX delivers valuable insights into open-source platforms and the ability to quickly zero in on the riskiest content to help national security, law enforcement, and defense market analyst teams progress investigations faster and achieve their missions.
(Fivecast is a world-leading provider of open-source intelligence (OSINT) solutions that enable the world’s most important public and private organizations to explore masses of data, uncovering actionable insights which are critical to protecting global communities. Courtesy of Fivecast and YouTube.)
-
Covering the end-to-end intelligence process, Fivecast ONYX is a completely scalable solution with the power to seamlessly and rapidly increase the vision of your targets without needing more skilled staff to carry the load.
-
Targeted, automated, and obfuscated data collection in real-time across a broad range of online platforms is combined with a customizable and AI-enabled risk assessment framework that automates complex intelligence analysis.
FORCEPOINT
 Best Zero Trust Cyber Solution
Best Zero Trust Cyber Solution
-
Zero Trust Content Disarm and Reconstruction
-
Forcepoint is leading the shift from outdated and ineffective malware and ransomware detection strategies to a proven prevention strategy rooted in zero-trust principles.

-
With its Zero Trust Content, Disarm, and Reconstruction (ZT CDR) solution, Forcepoint gives IT and security teams a new way to proactively protect their organization from ever-increasing malware and ransomware threats.
-
Forcepoint ZT CDR differentiates itself from traditional security inspection solutions by, instead of trying to detect the presence of malware, assuming nothing can be trusted. It extracts only valid business information from files – either discarding or storing the originals and any malware they might contain – and then builds brand-new, fully functional files to carry the information to its destination.
-
Pivoting from detection to prevention in this way is especially important with the recent evolution in hybrid workforces and digital transformation and their resultant usage of content and electronic information everywhere.
-
By leveraging a data-first approach to malware threat removal, ZT CDR is revolutionary for mitigating the threat of compromised data that could lead to breaches.
(Traditional antivirus solutions only protect your organization from known threats. See how Forcepoint’s Zero Trust CDR protects you from threats you don’t know about. Courtesy of Forcepoint and YouTube.)
-
*Forcepoint is a Returning ‘ASTORS’ Champion, having secured Wins in the 2022, 2021, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs, respectively.
FORTEM Technologies
Best Persistent Aerial Monitoring Solution
-
Fortem Technologies SkyDome® Manager
-
Fortem Technologies’ SkyDome® Manager is a purpose-built airspace monitoring and counter-UAS command and control software. Leveraging AI technology, SkyDome Manager directly empowers security personnel with 3D airspace awareness, delivering detection, tracking, and mitigation of drone threats.
-
The SkyDome system classifies and mitigates threats autonomously with its interceptor drone, DroneHunter®. With over 5,000 captures, the DroneHunter F700 is a counter-UAS weapon that captures surveillance and reconnaissance drones by shooting a net around them to either ground or tow the system away.
(Fortem Technologies digitizes, defends, and safeguards the world’s airspace by detecting and defeating dangerous drones to keep public venues from sports stadiums to airports to critical infrastructure such as oil refineries, dams, and nuclear plants safe, exposed to the growing threat of small, low flying drones that can easily be armed with a weapon or can cause harm accidentally. Courtesy of Fortem Technologies and YouTube.)
-
Fully autonomous, radar-guided, and purpose-built for superior speed and agility, the SkyDome system stops rogue drones without resulting in costly collateral damage.
-
*Fortem Technologies is a Returning ‘ASTORS’ Awards Champion, having secured a Win in the 2021 ‘ASTORS’ Awards Program.
FORTIOR Solutions
 Best Access Control & Authentication Solution
Best Access Control & Authentication Solution
-
The Fortior Solutions RAPIDGate Program is a patented, award-winning, and SAFETY Act-Designated identity, access, and security solution that boasts 99.97% uptime and serves the government, military, and critical infrastructure sectors, fulfilling end-to-end identity management needs and accommodating a wide set of compliance specifications.

-
The RAPIDGate program is a complete vendor management solution that includes verification of company sponsorship, company enrollment, multi-language kiosk-based registration, individual biographic and biometric collection, equipment, commercial background screenings, DOJ/FBI NCIC/III checks (subject to the approval of the relevant government authorities)
-
The RAPIDGate® and RAPID-RCx® programs provided unparalleled perimeter control at some of the most security-conscious organizations in the world, including the U.S. Army, U.S. Coast Guard, U.S. Navy, U.S. Marine Corps, and NASA, among others.
(See RAPIDGate®, a high-assurance identity management program for vendors, contractors, and service providers who require escorted or authorized access to secure facilities or sensitive corporate resources and guard against threats such as unauthorized access, identity theft, fraud, or cyber-crime. Courtesy of Fortior Solutions and Vimeo.)
-
*Fortior Solutions (formerly SureID) is also a Returning Premier Sponsor for their Third Consecutive Year and a Returning ‘ASTORS’ Award Champion Recognized in 2022, 2021, and 2016 Homeland Security Awards Programs, respectively.
Best Investigation/ Surveillance/Detection Solution
-
Fūsus Real-Time Crime Center in the Cloud
-
The Fūsus Real-Time Crime Center in the Cloud’s (RTC3s) is now the most widely used & trusted Real-Time Crime Center platform in U.S. Law Enforcement. It is a unique solution, the only truly open, technology-agnostic platform on the market.
-
RTC3 enables law enforcement and security agencies to create a unified intelligence ecosystem that integrates and enhances all public safety and investigations assets.
-
Scalable and affordable for agencies of any size, it can integrate public and private cameras, ALPR systems, gunfire detectors, CAD, and much more into a single platform.
(Fūsus RTC3 extracts and unifies live video, data, and sensor feeds from virtually any source, enhancing law enforcement agencies’ situational awareness and investigative capabilities. Courtesy of Fusus and YouTube.)
-
The Fūsus Real-Time Crime Center in the Cloud’s (RTC3s) video intelligence and map-based awareness interface is the central integration point for Law Enforcement agencies’ surveillance, security, and life safety technology.
-
Whether it’s a UAV, a traffic camera, a private cell phone video, a building security camera, or a bomb disposal robot, Fūsus can extract the live video feed and send it to your emergency operations center and officers in the field.
-
Fūsus RTC3 creates a public safety ecosystem that combines video with other utilities like Computer Aided Dispatch (CAD) data, gunfire detectors, real-time officer geolocator feeds, a registry map of all the public and private cameras in your region, a multi-media tips line for the public, and a digital evidence vault for investigators.
(See how Fūsus Real Time Crime Center In The Cloud Works in Collaboration with Connect Atlanta, a new public safety program enabling the people of Atlanta to help keep their community safe. Participation greatly enhances emergency preparedness by enabling police, fire, and public safety professionals to better assess and rapidly respond to criminal activity and emergency situations. It also enables investigators to gather evidence easily in the event of an incident. Courtesy of Fusus and YouTube.)
-
*Fūsus is a Returning ‘ASTORS’ Champion, having secured Wins in the 2022, 2021, and 2020 ‘ASTORS’ Homeland Security Awards Programs.
GALLAGHER Security
Best Integrated Solution for HSP D-12/FIPS 201 Compliance
-
Gallagher Command Centre v8.90
-
Command Centre v8.90, is Gallagher’s latest release of its award-winning security site management software, is a prime example of this people-first approach. It introduces several exciting new features and enhancements, including the IDEMIA VisionPass integration for secure contactless facial recognition access, Okta synchronization, Security Health Check enhancements, Open Supervised Device Protocol (OSDP) for the Controller 7000 Single Door, which is Gallagher’s newest controller offering, and more!

-
Gallagher Command Centre PIV is an enterprise-grade Physical Access Control System (PACS) that provides robust, real-time authentication of all federally issued high-assurance credentials. It natively supports reading and verifying the complete secure certificate information on government cards and is scalable to meet organizational requirements – no matter how big the site, or the number of cardholders involved.
-
Command Centre is the chosen platform for many of the world’s most high-consequence sites, and it’s easy to see why. Across military and defense, federal, state, and local government, commercial, education, healthcare, and transportation, Command Centre’s curb-to-core technology has been proven to protect lives, create efficiencies, and save organizations thousands of dollars each year.
(Gallagher Command Centre delivers an enterprise-grade Physical Access Control System (ePACS), offering robust, high assurance certificate-based credential authentication with Curb-to-Core capabilities. Courtesy of Gallagher and YouTube.)
-
Command Centre PIV is an access control solution that does it all, enabling federal organizations to manage complete site security from one highly intelligent platform and has been proven to save time, resources, energy, and money, all while delivering superior security that keeps even the most sensitive of sites protected.
-
*Gallagher is a Returning ‘ASTORS’ Champion, having been Recognized in their Fifth Consecutive ‘ASTORS’ Awards Programs.
GENASYS
Best Long-Range Acoustic Hailing Solution
-
LRAD Mobile Sound Shield
-
The LRAD Mobile Sound Shield broadcasts powerful warning tones and highly intelligible voice commands in a 360° radius of 100 meters.
-
Using an optimized driver and waveguide technology, the LRAD Mobile Sound Shield surrounds an equipped vehicle with an acoustic security barrier and provides an attention-commanding communication capability.
-
LRAD systems deliver live or recorded voice messages with exceptional clarity for any operational scenario. Optimized to the primary hearing range, LRAD’s Advanced Driver and Waveguide Technology ensure every broadcast is clearly heard and understood, even above the crowd, engine, and background noise.
(See why LRAD systems are in service in more than 100 countries and 500 U.S. cities in diverse applications. Courtesy of Genasys Inc. and YouTube.)
-
Genasys is the global leader in Long Range Acoustic Hailing Systems, with systems in service in more than 100 countries and 500 U.S. cities in diverse applications, including Public Safety, Law Enforcement, Defense, Border and Homeland Security, Critical Infrastructure Protection, Fire Rescue, Emergency Management, Maritime and Port Security, and Wildlife Control and Preservation.
-
*Genasys Inc. (formerly LRAD) has been Recognized as an ‘ASTORS’ Awards Champion for Eight Consecutive Year in the Annual ‘Homeland Security Awards Program. Thank you for your continued support of American Security Today.
GETAC Technology Corporation
Best Mobile Technology Product Solution
-
B360
-
The Getac B360 is a modern, full-size, and fully rugged laptop designed for field service, utilities, manufacturing, military, and public safety markets that require both the raw computing power and the versatility and mobility that comes with a lighter, more compact, fully rugged package.

-
The Getac B360 delivers all the benefits of a fully rugged device, and yet it’s not larger or heavier than traditional semi-rugged laptops.
-
The B360 delivers top-of-the-line capabilities in all areas, is easy to carry, comfortable to use, and is certified fully rugged, with cutting-edge wireless capabilities and a 1,400-nit screen readable even on the brightest days. With its dual user-removable PCIe NVMe SSDs (up to 4TB), the B360 enables enhanced data security for industries such as Public Safety, Utilities, and Manufacturing.
(The B360 runs the latest Intel® Core 12th generation i5/i7 processor with integrated Intel® Iris Xe graphics for remarkable performance, responsiveness, and rich visuals. A standard 256GB PCIe NVMe SSD (with an option of up to 4TB) offers ample storage. At the same time, the 13.3″ FHD LumiBond® display with Getac Sunlight Readable Technology (1,400 nits) and capacitive touchscreen help maintain productivity around the clock. Courtesy of Getac Rugged Solutions and YouTube.)
GLOBAL ELITE Group
Best Airport/Aviation Security Solution
-
Global Elite Airport/ Aviation Security Solution
-
Global Elite Group, a Securitas company, is a New York-based aviation security company offering protection for individuals, businesses, events, and properties worldwide.
-
The company oversees the security of over 60 clients across the aviation industry, including international and regional airlines.
-
Since Global Elite Group was founded, a lot of growth has taken place, and this once-regional provider has a far-reaching reputation today for delivering outstanding value and a customized approach for each client’s needs.

-
Global Elite Group was acquired by Securitas Transport Aviation Services USA for USD $22 million, reflecting the growth and value of the company since it began.
-
Global Elite’s reputation outside of its aviation security offerings is excellent for delivering security services, emergency management, and consulting services to governments and businesses around the globe.
-
Global Elite’s foundation offerings focus on aviation security, which makes up 95% of its business portfolio and has been the driver for developing a complete range of AVSEC services that are tailored to the express needs of each customer, from aircraft guarding and airside escorting, baggage pilferage investigations/prevention and cargo guarding, escorting & screening, to emergency response support, passenger behavioral assessments and verification, and even explosives/narcotics canine units.
-
*Global Elite Group has now been Recognized for the Seventh Consecutive Year as an ‘ASTORS’ Award Champion in the Annual Homeland Security Awards Program
(To be continued… see below)
The 2023 ‘ASTORS’ Awards Program was Proudly Sponsored by Platinum Event Sponsor: NEC National Security Systems (NSS)
And Our RETURNING Premier Sponsors:
ATI Systems, Automatic Systems of America,
Guard Dog AI, IPVideo Corporation, Rajant Corporation, RX Global, SIMS Software, and American Security Today!
NEXT View Part 2 Winners GU – M View Part 3 Winners N – Z
Part 4 Government Excellence Part 5 Innovation & Leadership
- **IN A RARE TIE Event – a tie results from extremely differing objectives and/or similar technological applications.


















