American Security Today is pleased to Introduce our new Legends in Leadership Awards, which was created to acknowledge leaders who lead with purpose and empower those around them to do the same.
Recipients of this new ‘ASTORS’ Legends Award for Excellence have the knowledge and experience gained throughout their esteemed careers in leadership and, going above and beyond, extend themselves to assist others in embracing their potential through mentorship and inclusion.
American Security Today’s Inaugural 2023 ‘ASTORS’ Legends in Leadership Award Recognized Keechant Sewell, the 45th Police Commissioner of New York’s Finest, and the first woman to oversee the nation’s largest police department, the New York City Police Department (NYPD), as well as the nation’s largest public transportation system.

During her time as commissioner, Sewell executed multiple strategies, reducing crime in most major crime categories.
She also collaborated with federal agencies to enhance counterterrorism workstreams and implemented the use of technology to assist investigations and ensure public safety.
Commissioner Sewell came out to address ‘ASTORS’ Homeland Security Awards Ceremony and Banquet Luncheon attendees, sharing her thoughts following her almost three decades of service.
Commissioner Sewell spoke to changes she’s seen in governing and law enforcement and the impacts of violence on social order.
She also spoke about the importance of maintaining and encouraging future generations to embrace social order with accountability, responsibility, self-discipline, and respect for one another in our lives and communities.
Commissioner Sewell challenged the First Responder Community to continue to excel in their chosen professions and to ensure the social contracts they have made about service, peer support, mental, physical, and moral fitness are inviolable.

She also gave voice to the importance of HOW we choose to spend the time we’ve each been allotted to be on this earth.
“We cannot complain that life is too short, when we do not make best use of the time we do have.”
She applauded AST’s efforts to support our nation’s first responders and government agencies, who ‘show up and do the work each day’ to safeguard our nation and citizens.
She thanked everyone in attendance, first responders and government/private partnerships, in that we are, in fact, using our time well.

Commissioner Sewell joined the Nassau County Police Department in 1997 and graduated from the police academy as the Class Speaker. She worked patrol in the Fifth Precinct in Elmont, New York, where she was selected to become a School Resource Officer and a police liaison to the Wayside Home for Girls.
She worked undercover assignments, was promoted to the rank of Detective, and assigned to the First Squad in Baldwin, where she investigated and assisted with successful convictions in numerous cases.
After being promoted to Sergeant, Commissioner Sewell was assigned as a patrol supervisor and subsequently became an investigator in the Internal Affairs Unit. Sewell became a Detective Sergeant in the First and Narcotics/Vice squads, overseeing drug and gun interdiction and suppression initiatives.
On November 27, 2023, Commissioner Sewell joined The New York Mets in a newly created position as Senior Vice President of Security and Guest Experience, overseeing the organization’s safety and guest experience.

“The opportunity to bring my passions of community building and public safety to the Mets is truly a dream job.”
“I am excited to join the Mets for my first private sector role,” Sewell said.
“The opportunity to bring my passions of community building and public safety to the Mets is truly a dream job. As someone who grew up in Queens, this legendary organization is vital to local communities and so many across the world. I can’t wait to help be a part of building this world-class fan experience.”
AST wishes you the best in your new position with The New York Mets, Commissioner Sewell, and we look forward to following the new heights you will attain in this next step of your accomplished career.
(Continued…)
NEC NATIONAL SECURITY Systems (First of Three)
 Best Facial/IRIS Recognition Solution
Best Facial/IRIS Recognition Solution
-
NEC Face/Iris Capture
-
NEC National Security Systems (NSS), a Foreign Ownership, Control or Influence (FOCI)-mitigated subsidiary under a Special Security Agreement (SSA) with the U.S. Government, provides full-service solutions for large agencies using the intellectual property and resources of the global NEC brand.

-
NEC has partnered with the U.S. Department of Homeland Security’s (DHS) Customs and Border Protection (CBP) agency, the Office of Biometric Identity Management (OBIM), and the Department of State (DoS) Bureau of International Narcotics and Law Enforcement (INL) Digitus project in Mexico, to deploy their two most prominent matching engines, AIM XM and AIM-ES, to the AWS cloud environment.
-
The NEC Face/Iris Capture system combines NEC’s number-one-ranked face recognition technology with its number-one-ranked iris recognition technology to create a highly accurate (false acceptance rate of 1 in 10 billion) identity verification system. In addition to high accuracy, the system quickly authenticates registered users by simply standing in front of the terminal.
-
Even under conditions where individuals may be wearing masks, goggles, or gloves, NEC’s Face/Iris Capture maintains its high accuracy, ensuring convenience to the user without compromising security. The system can be integrated into various access control and payment systems as an added layer of security without disturbing existing workflows.
(NEC’s face recognition technology is now used worldwide to provide safety, security, and new customer value. An endeavor that began decades ago, the path to making face recognition tech practical was paved with untold hardships. How has the effort paid off, and what social values are being created through this technology today? Learn all about NEC Fellow Hitoshi Imaoka and his R&D journey with his team, leading him to win the prestigious Medal with Purple Ribbon in 2023. Courtesy of NEC and YouTube.)
-
This cloud-native architected platform supports the characteristics of cloud computing noted in NIST Special Publication 800-145, The NIST Definition of Cloud Computing—on-demand, self-service, broad network access, resource pooling, rapid elasticity, and measured services.
NEC NATIONAL SECURITY Systems (Second of Three)
 Best Perimeter Protection Solution
Best Perimeter Protection Solution
-
Intelligent Perimeter Intrusion Detection System (IPIDS)
-
The NEC Intelligent Perimeter Intrusion Detection System (IPIDS) combines NEC’s global expertise in transoceanic fiber cable with advances in machine learning-based artificial intelligence to create a cutting-edge perimeter security system.

-
IPIDS can detect physical intrusions and disturbances above ground, underground, and underwater by optical fibers connected to a centrally located interrogator, which sends and receives light to the optical fiber. Physical intrusions like fence climbing or digging create vibrations, which the interrogator interprets as changes in light.
-
Then, the IPIDS machine learning-based AI classifies and locates the physical intrusion and sends an alert to our customizable graphical user interface. The machine learning-based AI can differentiate between anomalies like digging, fencing climbing, fence cutting, human walking or running, vehicles moving, and low-flying aircraft.
-
NEC IPIDScan also pinpoint where the anomaly occurs within 1 m (3 ft). The tuning of these alerts creates a highly accurate alerting system with a low nuisance alarm rate for a reliable perimeter security system with a low cost of ownership.
(NEC NSS IPIDS uses state-of-the-art optical fiber sensing, video analytics, machine vision, computer vision, AI, machine learning, deep learning, and sensor fusion to achieve real-time and ubiquitous situational awareness of physical security threats and anomalies. Courtesy of NEC and YouTube.)
-
IPIDS covertly, quickly, reliably, and accurately detect, locate, and prompt automated video verification and trigger escalated security response. Featuring industry-disruptive probability of detection, nuisance alarm rate, and total cost of ownership, IPIDS can be used in the US Federal government’s various programs and systems, such as Anti-terrorism/Force Protection, Integrated Base Defense, Electronic Security, Emergency Management, Public Safety, Protective Distribution, and Linear Ground Detection.
-
Additionally, NEC’s IPIDS is immune to electromagnetic interference and requires no electrical power in the field, making it ideal for monitoring both near and remote areas, and one interrogator can detect anomalies along up to 160 km (100mi) of optical fiber, contributing to low equipment and installation costs.
NEC NATIONAL SECURITY Systems (Third of Three)
 Best Pedestrian Entrance Control Solution
Best Pedestrian Entrance Control Solution
-
NEC Gateless Entry
-
NEC’s Gateless Entry Solution combines the global No. 1 face algorithm with proprietary person re-identification technology to allow fast and reliable entry control at speed for groups of people.
-
NEC’s Gateless Entry technology provides accurate matching, even if people are facing away from the camera or their bodies are occluded.
(Hear from Frost and Sullivan analyst Danielle VanZandt about how NEC is the leader in pushing the biometric industry forward, about today’s biometric authentication trends, and how it will progress in the future. Courtesy of NEC Corporation and YouTube.)
-
Gateless Entry innovative from NEC eliminates the need for traditional or guarded security gates, reducing bottlenecks and wait times without affecting a site’s or event’s security.
-
NEC’s Gateless Entry allows large groups of people to be authenticated simultaneously, smoothly, without stopping. If a person whose face image has not been registered in advance enters the area, an alert can be displayed above their head or on a security monitor nearby.
-
*AST is delighted to welcome back Returning PLATINUM Awards Sponsor NEC National Security Systems, to the 2023 ‘ASTORS’ Homeland Security Awards Program.
-
NEC National Security Systems is a subsidy of NEC Corporation of America (NECAM), recognized for Six Consecutive Years in the Annual ‘ASTORS’ Homeland Security Awards Programs.
NETSCOUT
 Best Cyber Analytics Solution
Best Cyber Analytics Solution
-
NETSCOUT’s Arbor Edge Defense (AED)
-
NETSCOUT’s Arbor Edge Defense (AED) is an inline security appliance deployed at the network perimeter (i.e., between the internet router and network firewall) to provide an additional cyber defense layer.
-
AED occupies a unique position on the network edge, blocking inbound cyber threats (e.g. DDoS attacks, IOCs) and outbound malicious communication in bulk.
-
This stateless security solution is uniquely powerful because it is backed by NETSCOUT’s unmatched global sensor network with visibility into over half of all internet traffic and machine learning models trained by NETSCOUT’s expert team of security researchers to automatically detect even the most complex attacks.
(Also, in the event of a large DDoS attack, AED is designed to easily integrate with most cloud DDoS protection providers, including Arbor Cloud from NETSCOUT, to intelligently and automatically coordinate attack response between cloud-based, volumetric and on-premise, application-layer protection systems. Courtesy of NETSCOUT and YouTube.)
-
Thankfully, AED can easily screen incoming and outgoing traffic using stateless packet processing technology to block cyber threats in bulk, including low and slow application-layer DDoS attacks that other solutions may miss, along with inbound and outbound indicators of compromise (IOC) indicative of malware infestations.
-
Outside analyst firms have also recognized the superior performance of AED and its key features. For example, in a Forrester Total Economic ImpactTM (TEI) study conducted earlier this year, Forrester found that AED can save network engineers and security analysts more than 2,000 hours while delivering a return on investment of 201%.
NETWRIX
 Best Privileged Access Security Solution
Best Privileged Access Security Solution
-
Netwrix Privilege Secure
-
Netwrix Privilege Secure ensures comprehensive end-to-end security for privileged access management.
-
Its PAM tools can solve access control challenges by creating ephemeral identities for privileged access, reducing the attack surface, and enhancing overall security, empowering IT and security teams to manage privileged accounts securely while providing accountability and proof for auditors.
-
Netwrix PAM tools include Netwrix Privilege Secure for Discovery, Netwrix Privilege Secure for Access Management, and Netwrix Privilege Secure, Privilege Secure IT teams can protect application settings from malicious and inadvertent changes and validate that Group Policy settings are deployed correctly.
(Minimize your attack surface by eliminating the need for standing privilege altogether. Reduce the risk of business disruptions or compliance failures by managing and tracking all privileged activity in one place. Courtesy of NetWrix and YouTube.)
-
Netwrix Privilege Secure is simple to license and install, with everything needed included in one license so that organizations won’t face extra fees for add-ons for databases, appliances, proxies, high availability, or other common needs.
-
Netwrix Privilege Secure also leverages earlier investments by facilitating the use of existing desktop clients for RDP and SSH access, and it integrates with any existing vault solutions, including Microsoft LAPS.
- *Netwrix is a Returning ‘ASTORS’ Awards Champion, having secured Wins in the 2018, 2017, and 2016 ‘ASTORS’ Award Programs.
NEUSHIELD
 Best Disaster Preparedness and
Best Disaster Preparedness and
Disaster Recovery Solution
-
NeuShield Data Sentinel
-
Ransomware has grown to become one of the largest problems in cybersecurity. The FBI has issued multiple advisories, Private Industry Notifications (PINs), and flash alerts warning of ransomware attacks against critical infrastructure, including Healthcare and First Responder networks, Water and Wastewater Systems, the Food and Agriculture sector, and education institutions, and revealed that Ragnar Locker ransomware breached at least 52 critical organizations, Cuba ransomware hit at least 49 U.S. critical infrastructure entities, and BlackByte ransomware was deployed on the networks of at least three others.
-
NeuShield helps governments and Federal agencies deal with this significant threat by doing more than detect and block ransomware attacks; it can recover damaged data from malicious software attacks without a backup, using Mirror Shielding™ to protect files, ensuring that you can instantly recover important data from any ransomware attack. In addition, it leverages Data Engrams™, which allows organizations to view and roll back to previous versions of a file.
(Learn how NeuShield Data Sentinel helps recover from ransomware quickly and easily without a backup. Courtesy of NeuShield and YouTube.)
-
NeuShield prevents ransomware and malicious programs from taking over the boot process and stops wiper malware from erasing all data on the hard drive, and NeuShield’s One-Click Restore makes it easy to undo the damage of a ransomware attack, allowing state and local governments as well as Federal agencies to quickly regain access to computer, files, and data where traditional security and storage methods fail.
-
NeuShield removes known and unknown threats, restores the system to a known good state, and recovers encrypted and corrupted operating system files.
NICE PUBLIC SAFETY (First of Two)
-
Best 911 Recording & Analytics
-
NICE Inform Elite (Part of the Evidencentral Platform)
-
With emergency communications getting more complex, 911 centers need a better way to make sense of growing volumes of incident data.
-
In 911 response, every second counts, and delays can endanger lives. Real-time insight into what’s happening, what’s working, and what’s not has never been more essential. Unfortunately, these insights are often hidden in data stored in different systems.
(Explore the challenges 911 centers face every day, and the many ways that NICE Inform, one of the solutions in NICE’s Evidencentral end-to-end digital transformation platform, can help. Courtesy of NICE and YouTube.)
-
Part of the Evidencentral platform, NICE Inform Elite brings these insights to the surface to help emergency communications center leaders get to the truth faster.
-
By providing a single system of record to capture and make sense of growing data, NICE Inform Elite can positively impact service delivery to citizens and reduce staff turnover.
NICE PUBLIC SAFETY & JUSTICE (Second of Two)
Best Investigation/ Surveillance/ Detection Solution
-
Evidencentral (Including NICE Justice & NICE Investigate)
-
The facts are hard to ignore, with a 4-million-plus backlog in court cases and thousands of cases dismissed due to evidence problems. And with 90% of digital evidence created in just the last two years, the criminal justice system is struggling to keep pace. How can state, county and local governments keep communities safe, arrive at the truth faster, and ensure just outcomes?
-
The truth is – law enforcement agencies, prosecutors, public defenders, and courts all waste enormous amounts of time interacting with digital evidence – storing it, collecting it, copying it, analyzing it, sharing it, making it playable, and even physically transporting it from place to place. They need a more efficient, effective, and fiscally responsive way.
-
NICE’s Evidencentral digital transformation platform can help government entities overcome these obstacles. Evidencentral also connects everyone together so that justice can flow more smoothly from incident to court.
(Whether prosecuting cases, defending clients, or administering justice, digital evidence is central to what you do every day. But as evidence volume and complexity grow, managing it creates inefficiencies and backlogs and gets in the way of delivering timely justice. Whatever your role in the justice process, NICE can help you better manage growing volumes of digital evidence and get to the truth faster. Courtesy of NICE and YouTube.)
-
NICE’s Evidencentral Software-as-a-Service (SaaS) solution digitally transforms how digital evidence is collected, analyzed, and shared from when an incident happens until cases are successfully closed and prosecuted. Evidencentral overcomes the challenges of digital evidence silos and disjointed work processes by integrating systems and enabling justice process stakeholders who rely on digital evidence to work more efficiently on their own and more effectively together.
-
*NICE Public Safety has officially been recognized as a Multiple ‘ASTORS’ Awards Champion in all Eight of the Annual ‘ASTORS’ Homeland Security Awards. Thank you for your continued support in AST!
OMNILERT
-
Best Metal/Weapons Detection Solution
-
Omnilert AI Visual Gun Detect Software
-
Omnilert Gun Detect is an active shooter prevention solution that uses artificial intelligence with existing security cameras to detect firearms and automate response, including mass notifications, initiating IoT systems (including access control), and emergency collaboration.
(Omnilert Gun Detect software is an always-on monitor looking for weapons through thousands of existing cameras and can spot a brandished weapon in less than a second and then, once verified, can instantly activate a robust emergency response plan that could include calling police, notifying students and staff, locking doors and much more. Courtesy of Omnilert and YouTube.)
-
Omnilert Gun Detect technology provides early warning before shots are fired, allowing individuals ample time to seek safety and prevent harm.
-
Omnilert has roots in the U.S. Department of Defense (DoD) and the Defense Advanced Research Projects Agency (DARPA), which are related to the real-time target recognition and threat classification that the military focuses on for high reliability and precision to developing the company’s gun detector AI that goes beyond identifying guns to finding active shooter threats.
-
Omnilert Gun Detect adoption has increased to hundreds of deployments in schools, hospitals, and government in 2023.
ONSOLVE
 Best Unified Situational Awareness Solution
Best Unified Situational Awareness Solution
-
The OnSolve Platform
-
OnSolve is a leading critical event management Software-as-a-Service provider that proactively mitigates physical threats, allowing organizations to remain agile when a crisis strikes.
-
When it comes to thoroughly understanding risk and taking steps to plan for it, platform selection and configuration must prioritize three competencies – the speed at which developing information is gathered, the relevance of that information, and the system’s usability.
-
Using the most trusted expertise and reliable AI-powered risk intelligence, critical communications, and incident management technology, the unified OnSolve Platform enables enterprises, SMB organizations, and all levels of government to detect, anticipate, and mitigate physical threats that impact their people and operations.
(OnSolve has the experience and capabilities to help you save time, money, and lives. In the business of successful results, OnSolve helps you achieve them through the speed, relevance, and usability of our innovative OnSolve Platform for Critical Event Management. With AI-powered risk intelligence, award-winning critical communications, and mobile incident management, see how OnSolve leaves the limitations of traditional critical event management behind. Courtesy of OnSolve and YouTube.)
-
With billions of alerts sent annually and proven support for both the public and private sectors, OnSolve is used by thousands of entities to save lives, protect communities, safeguard critical infrastructure, and enable agility for the organizations that power our economy.
-
*OnSolve is a Returning ‘ASTORS’ Awards Champion for their Fifth year, the most recent Recognized in the 2021 Homeland Security Awards Program.
PROBABLE CAUSE Solutions
 Best Video Analytics Solution
Best Video Analytics Solution
Camera Canvass Tracker
-
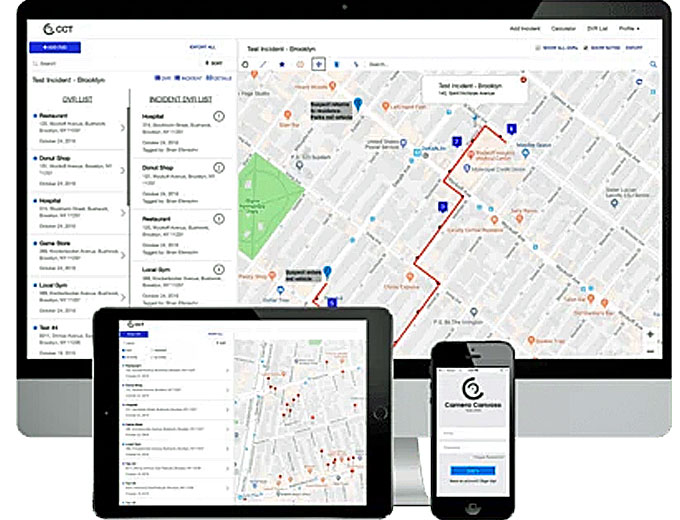
Camera Canvass Tracker, a patented pending technology used to simplify canvassing for surveillance cameras, is a daily task done by investigators.
-
Camera Canvass Tracker automatically builds a database of camera locations and other pertinent information that allows the investigator to calculate time differences, record the DVR/cameras, view the database on a list or on a map, and export the database when needed.
-
With Camera Canvass Tracker you can:
-
-
Map It – Create a centralized database of surveillance cameras within your jurisdiction. Search your database with our interactive geo-coded map.
-
Organize your Data – Store the name, address, and contact information of the custodians of the surveillance cameras. Save all DVR information for future reference.
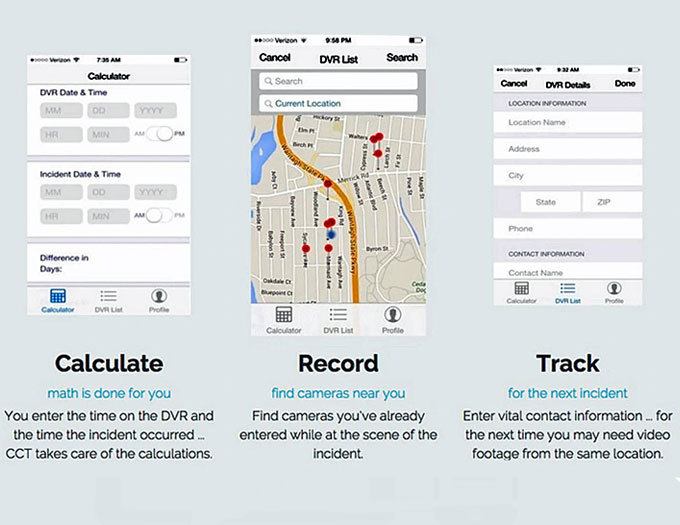
-
Usable Data – Upload camera angle screenshots for future reference. Update the DVR data and add important notes for you and the rest of your agency to benefit from the next time you need it.
-
Calculate – Calculate those difficult time calculations down to the second. Saves valuable time and reduces the risk of human error. Creates a permanent record for future reference and strengthens testimony.
-
-
-
Incident Tracking & Custom Mapping – After creating your Incident, Document the locations visited and create custom maps. Customize the map with various pins and notes while plotting the course of travel.
-
Detailed Exports – Strengthen your case and testimony with proper documentation.
-
Group Plans – Share DVR data across your jurisdiction with everyone in your agency/group. Users can access the database from ANY internet-capable device, including their desktop computer.
-
-
*Probable Cause Solutions has now been recognized as an ‘ASTORS’ Awards Champion for its Seventh Consecutive Year in the Annual Awards Programs.
QUANTUM Corporation
 Best Video Data Storage Solution
Best Video Data Storage Solution
-
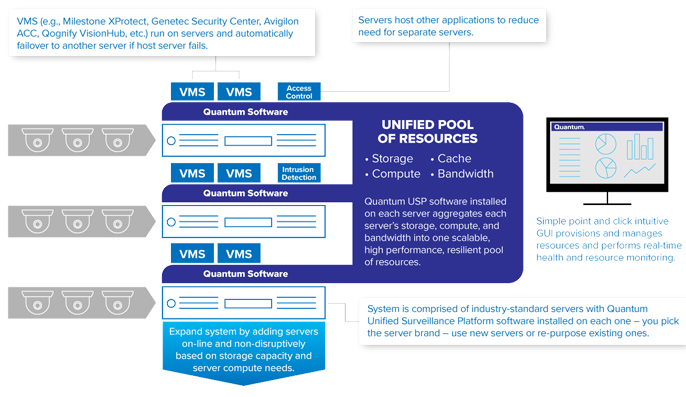
Quantum Unified Surveillance Platform
-
Federal agencies maintain some of the world’s largest surveillance data sets, with massive amounts being ingested and archived daily that require the highest level of security.
-
Data captured by video surveillance cameras puts tremendous demands on infrastructures, driving the need for scalability, resilience, and high performance, particularly for mission-critical Federal video surveillance meant to keep citizens safe.
-
To assist these agencies struggling with the modernization of IT infrastructure, Quantum has introduced USP 5.0, the latest version of Quantum’s Unified Surveillance Platform, offering a more simplified user experience and enhanced monitoring from a single source.
-
Quantum USP 5.0 software uses patented video data reduction techniques to record and store video data at the highest performance with the least amount of hardware required, allowing federal organizations to host more than 10,000 cameras on one single system and transforming the original video surveillance and analytics storage platform into a more resilient, reliable, and intelligent infrastructure.
(Quantum’s end-to-end platform is uniquely equipped to orchestrate, protect, and enrich data across its lifecycle, providing enhanced intelligence and actionable insights. Leading organizations in cloud services, entertainment, government, research, education, transportation, and enterprise IT trust Quantum to bring their data to life because data makes life better, safer, and smarter. Courtesy of Quantum and YouTube.)
-
Through USP 5.0, Quantum provides the highest level of unstructured data archiving and management in the most mission-critical environments, and federal agencies have continuous access to surveillance data regardless of hardware failures, extensive data set sizes, and retention timelines.
-
*Quantum is a Returning ASTORS’ Awards Champion, having secured Multiple Wins in the 2022, 2021, 2017, and 2016 Homeland Security Awards Programs.
QuSECURE
 Best Quantum Cyber Security Solution
Best Quantum Cyber Security Solution
-
QuProtect
-
QuSecure is a leader in post-quantum cybersecurity to protect enterprise and government data from quantum and classical cybersecurity threats.
-
QuSecure’s flagship product, QuProtect, delivers quantum resilient channels over the public internet for data to reach devices securely outside an organization’s data center or cloud environment.
-
For highly transactional industries such as banking and finance, QuEverywhere (part of QuProtect) protects data and transactions on-premises or in the cloud, on a mobile device or desktop browser, or in a networked system without requiring users to install software at the endpoint.
(Learn how to preserve and uphold your customer’s trust and become a pioneer in building your business’ post-quantum cybersecurity foundation, starting with the simple, safe, and compliant QuProtect solution. An all-in-one software-based solution that secures critical data from classical and emerging AI and quantum threats anywhere it travels. Courtesy of QuSecure and YouTube.)
-
QuProtect leverages Quantum-Safe Cryptography for secure communications wherever data travels and empowers you with complete cryptographic control for adaptive protection against classical and emerging threats.
-
QuProtect is the industry’s first flexible, comprehensive post-quantum solution designed to be easily and immediately deployed without rip and replace on legacy and contemporary networks, putting control and insights right into the hands of the user.
(QuSecure’s quantum-safe solutions provide an easy transition path to quantum resiliency across any organization. QuSecure’s customer deployments are in banking/finance, healthcare, space/satellite, IT/data enterprises, data centers, and various Department of Defense agencies. Courtesy of QuSecure and YouTube.)
-
Available through the GSA Multiple Award Schedule (MAS), QuSecure delivers advanced cybersecurity technologies to federal government agencies and the broader public sector, ensuring data protection against the emerging threats of AI (Artificial Intelligence) and quantum computing.
RAJANT Corporation
 Best Wireless Video Surveillance Network Solution
Best Wireless Video Surveillance Network Solution
-
Cardinal BreadCrumb
IP40 Dual Radio Module -
The Cardinal is powerful, lightweight, and notably the smallest within Rajant’s portfolio of industrial wireless nodes.

-
This latest IP40 dual radio BreadCrumb module focuses on robotics, improving Wi-Fi and LTE while enabling connectivity to billions of Wi-Fi IoT devices.
-
Overcome the physical and RF obstructions hindering your fully mobile security and safety operations with the Cardinal’s extended range, which supports high-capacity M2M communications required for mission-critical first responder communications.
-
Designed with automation robots in mind, including collaborative robots, automated storage/retrieval systems, autonomous mobile robots (AMRs), unmanned guided vehicles (UGVs), and more, the Rajant Cardinal can enhance your on-the-move connectivity in the most challenging environments.
(Tailored for warehouse automation and robotics, the Rajant Cardinal Breadcrumb IP40 Dual Radio module solves Wi-Fi and LTE limitations for fully mobile M2M communications. Courtesy of RAJANT and YouTube.)
-
The Cardinal extends the range of traditional Wi-Fi past the limitations of fixed infrastructure with no line-of-sight requirements using two transceivers having a combined data rate of 1.73 Gbps.
-
In addition to robotics and infrastructure in warehouse automation, the Cardinal wireless node has applications as part of irrigation in agriculture, reclosers in energy, PLC controls in oil and gas, drone and UAV in the military and light show markets, and process automation in the manufacturing industry.
-
*AST is delighted to welcome Rajant Corporation back, as a Returning ‘ASTORS’ Award Champion, as well as a Returning Premier Awards Sponsor in the 2023 ‘ASTORS’ Homeland Security Awards Program.
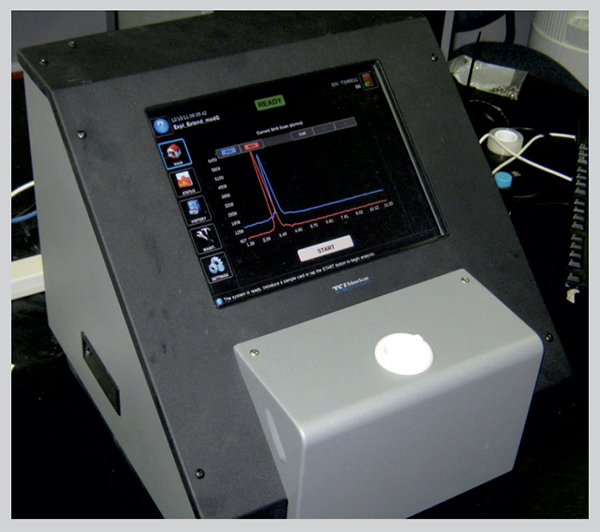
RIGAKU ANALYTICAL Devices
 Best CBRNE Detection Solution
Best CBRNE Detection Solution
-
Rigaku CQL Max-ID
-
The Rigaku CQL Max-ID is a handheld 1064 nm Raman analyzer that offers features and benefits to maximize chemical threat analysis in safety and security applications.
-
With an on-board library of over 13,000 items, the CQL Max-ID provides first responders, border security, and the military with a device that can identify narcotics, explosives, toxic industrial chemicals, chemical warfare agents (CWAs), and more–without the concerns of fluorescence interference.

-
Additional features available on the new CQL Max-ID include:
-
Automatic mixture analysis of up to five components
-
Addition of notes and pictorial evidence using an on-board camera
-
Integrated Chemwatch SDS information
-
Pre-configured setting selections based on the application
-
CommandSuite™ integrated fleet management capability, and more
-
-
The Rigaku CQL Max-ID is built upon the updated CQL platform accepted as part of the U.S. DoD JPEO DR SKO System Modernization Program.
RuggON USA (First of Two)
 Best Vehicle Mounted Security Systems
Best Vehicle Mounted Security Systems
-
VULCAN X: 10.4″ Vehicle Mount Computer
-
Today, law enforcement, EMS, and first responder vehicles serve as mobile quasi-offices.
-
Built around a high-visibility 10.4-inch display, the versatile VULCAN X rugged vehicle-mount computer upgrades any type of vehicle into a valuable, productive asset, allowing first responders to reliably and rapidly report and respond to real-time events.
(Meet the next-generation Vehicle Mount Computer VULCAN X packed with enhancements to I/O interface and wireless communications that ensure reliable and secure operation even under the most severe conditions. Courtesy of RuggON and YouTube.)
-
Based on the 8th gen Intel® Core™ i5-8365UE 1.6GHz, the VULCAN X is compatible with Windows 10 IoT Enterprise.
-
Built to operate around the clock, its fully rugged design makes the most of the IP66, MIL-STD 810H, and IEC-60721-3-5 5M3 certifications, ensuring the VULCAN X keeps working in the harshest environments, including a vast range of temperatures, -22°F to 131°F.
-
The VULCAN X helps law enforcement agencies, emergency services personnel, and first responders work smarter, safer, and more efficiently.
RuggON USA (Second of Two)
 Best Mobile Technology Product Solution
Best Mobile Technology Product Solution
SOL PA501 Fully Rugged Tablet
-
Today, mobile digital devices (tablets, laptops, phones) are a key part of the ‘toolbox’ of items used by law enforcement, first responders, and emergency services personnel, providing two-way, real-time communications and information; capturing photos and videos; scanning license plates; and instantly create and save a permanent record of an event.
-
The AT&T FirstNet certified 10.1” SOL PA501 rugged tablet featuring Android 12 and GMS (Google Mobile Services) certification is the industry’s forerunner of things to come in the rugged Android tablet market. Including these two exciting additions to the unit’s purpose-built adaptabilities further strengthens the PA501’s ability to fit any role in these peril-filled fields requiring an up-to-date, engineered, ruggedly built mobile computing device.
(The RuggON 10.1″ rugged tablet SOL PA501 delivers a wealth of helpful features to enterprise more security and control for IT and users. The RuggON SOL PA501 rugged tablet is FirstNet Ready™ with Band 14. Courtesy of RuggON and YouTube.)
-
Offering exceptional performance, improved efficiency, ultra-durable battery life, and on-the-mark extras, the mobile SOL PA501 rugged tablet is a perfect fit for law enforcement, first responders, and/or emergency services.
-
Mobile devices save lives and time and are indispensable. Naturally, SOL PA501 devices with the latest technology and meaningful features provide the best solution to serve and protect the professionals who perform in the field.
- *RUGGON USA is a Returning Multi-Award Winner from the 2022 ‘ASTORS’ Homeland Security Awards Program.
SEERIST
 Best Threat Intelligence Solution
Best Threat Intelligence Solution
-
Seerist
-
Seerist was designed to mitigate risks and potential disruptions and to provide strategic intelligence for its clients, including governments, NGOs, and commercial operations.
-
The Seerist solution combines adaptive artificial intelligence with 200 on-the-ground geopolitical security and risk experts, enabling organizations to intelligently sift through the noise of global chatter, forecast potential threats, and contextualize threat events to guide strategic decisions.
(Seerist bridges the gaps between tactical and strategic intelligence to help threat and risk intelligence professionals sift through the noise of global chatter, with artificial intelligence with localized geopolitical risk expertise to forecast potential threats and offer insights to enable rapid, reliable decision-making when it matters most. Courtesy of Seerist and YouTube.)
-
The unique combination of AI-driven threat monitoring and expert human analysis allows Seerist to be a one-of-its-kind offering in the industry, effectively providing users greater comfort in the veracity of the data they’re using for critical decisions.
-
Seerist’s robust risk and threat intelligence solution helps security managers and intelligence analysts forecast potential threat events to take the guesswork out of what leaders should do now to protect their people, assets, and reputations.
SELECT ENGINEERING Services (First of Two)
-
Best Personal/Protective Equipment Product
-
Automatic Injury Detection and Personal Emergency Transmitter System
-
The Automatic Injury Detection (AID) System provides help in seconds when a bullet, knife, or shrapnel has pierced the sensing panel.

-
When an AID flexible mylar sensing panel (front and back, comfortably inserted into the wearer’s bulletproof vest) is pierced by either a bullet, knife, or shrapnel from an IED, the communications module will sense the break in the circuit and automatically sends an emergency alert with GPS location to phone, radio or communication system.
-
The automated and instant emergency alerts help save lives by improving the response from medics and backup personnel to stop, apprehend, or contain the attacker, even when the officer is completely incapacitated.
(See how Automatic Injury Detection (AID) Sensors can detect when an individual has been shot, stabbed, or injured by shrapnel from an IED and communicate critical information immediately, even if the wearer is totally incapacitated. Courtesy of Select Engineering Services.)
SELECT ENGINEERING Services (Second of Two)
 Best Alert Notification Solution
Best Alert Notification Solution
-
Personal Emergency Transmitter (PET)
-
-
The Personal Emergency Transmitter (PET) system is a simple and affordable personal safety solution.
-
People at risk who struggle with complex technology or expensive subscriptions to elaborate security solutions can now improve their safety with PET.
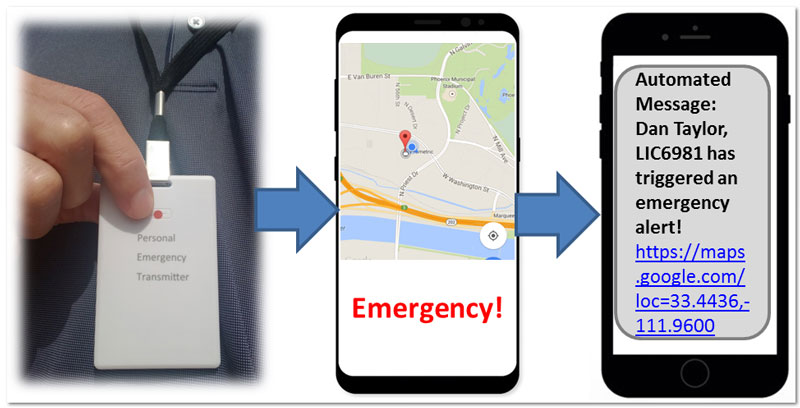
PET improves personal safety in various scenarios, such as when in a panic, under heavy duress, or in a medical emergency. -
With a simple press of the button, PET provides immediate notification to your pre-selected contacts that you are in an emergency situation. During an attack or other emergency, it may be impossible to access your phone, fumble with unlocking and opening an app, or provide updates. An attacker will knock the phone away if the victim attempts to access it.
-
Users can activate PET covertly, so an attacker does not even know that help is on the way, sending your recipients a precise location so they can find you and provide help as soon as possible. The location links the recipient receives can be opened in Google Maps, and they can easily navigate directly to the scene.
-
PET sells for a low, one-time cost with no monthly payments, battery charging, or maintenance required. It’s an ideal security solution for anyone at risk of attack or injury, including probation officers, realtors, social service workers, rideshare drivers, students, seniors, hunters, and off-road vehicle users.
-
*Select Engineering Services has now been recognized as a Multi-‘ASTORS’ Awards Champion for its Seventh Consecutive Year in the Homeland Security Awards Programs.
-
-
SENSTAR
 Best Intrusion Detection & Prevention Solution
Best Intrusion Detection & Prevention Solution
-
Senstar MultiSensor™
-
Senstar’s new MultiSensor™ is an AI-based intrusion detection system that uses an embedded sensor fusion engine to intelligently synthesize data from multiple sensing technologies, including short-range radar, PIR, accelerometer, high-frequency vibration, and optical sensors.
-
The Senstar MultiSensor™ system provides a Probability of Detection (Pd) far exceeding that of traditional sensors while eliminating virtually all nuisance alarms.
-
With real-time location tracking and ground-level image capture capabilities, security personnel maintain situational awareness as events occur.
(Senstar MultiSensor™ is an AI-based intrusion detection system that uses an embedded sensor fusion engine to intelligently synthesize data from multiple sensing technologies, with a Probability of Detection far exceeding that of traditional sensors while eliminating virtually nuisance alarms. Courtesy of Senstar Corporation and YouTube.)
-
Conventional sensor technologies focus on detecting specific physical phenomena and, by themselves, do not take into account the full context in which an event is occurring, which can lead to false positives (nuisance alarms) or, worse, missed detections.
-
Senstar MultiSensor™ takes a new approach to threat detection. Its embedded sensor fusion engine synthesizes data from multiple sensors within a single device (short-range radar, PIR, accelerometer, high-frequency vibration, and video) to understand the full context of when an event occurs, resulting in a higher probability of detection while virtually eliminating nuisance alarms.
-
The context-based approach also assists security personnel with improved situational awareness by providing real-time location tracking and ground-level event images.
SHOOTER DETECTION Systems
 Best Gunshot Detection Solution
Best Gunshot Detection Solution
-
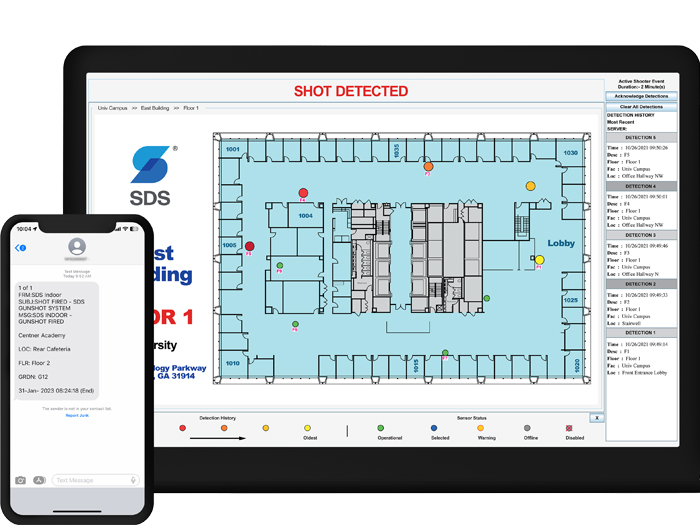
New for 2023, the “SDS Indoor Gunshot Detection System” has added a free new feature.
-
SDS Emergency Response Service now combines the power of SDS’s dual-factor gunshot detection sensors and Noonlight’s SendPolice platform to deliver an advanced emergency response solution that dramatically improves the delivery of relevant data to 911 Call Centers during a gun violence event while greatly reducing the burden on victims to effectively communicate critical information during a crisis.
(Learn about the SDS Indoor Gunshot Detection System, its Government Certifications for performance, and see the many integrations with security systems, including leading Video, Access Control, and Mass Notification Systems plus additional, flexible options to broadcast shot notifications via PA Systems, Digital Security Radio, Emergency Lighting, and Alarm Systems. Courtesy of Shooter Detection Systems and YouTube.)
-
SDS and Noonlight’s engineers have created an instantaneous, two-way data interface between SDS’ Situational Awareness software and Noonlight’s SendPolice Platform. SDS customers will instantly know that the new Emergency Response Service has been activated and that their data is automatically and continuously transmitted to a 911 Call Center.
-
This unique new software service is made possible via a powerful integration between SDS and Noonlight’s SendPolice capability that allows trained operators to have push-button access directly to the 911 center serving the incident location.
-
With the SDS Emergency Response Service, a 911 operator receives real-time updates as an incident unfolds, including if more shots are fired and the changing location of shots detected inside the building. This allows operators to accurately update responding officers regarding the location of the last shots fired.
-
In keeping with SDS’ commitment that every citizen deserves the right to the highest protection against active shooters, these new capabilities are included with the standard SDS software package for new and existing SDS software users. Also new for 2023, is “SDS powered by Alarm.com”.
(Learn more about SDS’ latest developments, including SDS Powered by Alarm.com, a small to medium-sized business solution, and SDS Enterprise, an enhanced, complete gunshot detection solution that now includes a unique, direct-to-911 alerting feature to help first responders get to the scene of a shooting faster and more prepared. Courtesy of Shooter Detection Systems and YouTube.)
-
SDS’s parent company, Alarm.com, offers a specially configured SDS Indoor Gunshot Detection Sensor for small- to medium-sized enterprises. Now, smaller businesses can integrate gunshot detection into their security portfolio at a more economical price.
-
*SDS is a Returning ‘ASTORS’ Champion for their Fourth Year, having secured Wins in the 2022, 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
SIMS Software (First of Two)
 Best Security Workforce Management Solution
Best Security Workforce Management Solution
-
SIMS Software is the leading industrial security information management software provider to some of the world’s most renowned government agencies, defense contractors, high technology giants, academic institutions, and research facilities.
-
For 40 years, its flagship product, Security Information Management System (SIMS), has been the most trusted solution on the market to protect classified and high-value information.

-
As the role of security professional continues to transform with increased responsibilities, evolving compliance requirements, and multifaceted, aggressive threats towards their organization, having a complete solution has never been more imperative.
-
SIMS Software provides security professionals with powerful management-level metrics and a 360° view of their organization at their fingertips: reducing data calls, allowing for tracking of assets specific to the organizational requirements, and providing on-demand trend analysis for early detection and insider threat prevention.
-
Purpose-built, SIMS provides all the features and functionality necessary to run a powerful, paperless industrial security program with a single system of record and includes 17 fully integrated modules for a fully automated 360° view of every physical, virtual and human asset inside your security domain.

-
SIMS is a robust solution that supports the development costs and interoperability issues associated with in-house developed solutions, which are often more expensive and require in=demand IT resources and has been designed to meet the hosting needs of all sizes and types of organizations offering both on-prem and cloud hosting options.
-
Focused on evolving customer needs and government regulations, SIMS Software combines proven performance, consistent innovation, and unmatched customer service to deliver a uniquely powerful security information management system.
-
By equipping security stakeholders with the tools to protect the lifeblood of their organizations, SIMS Software is proud to play a vital role in advancing the interests of our nation and its allies at home and abroad.
-
SIMS provides all the features and functionality necessary to run a powerful, paperless industrial security program with a single system of record, so clients can escape the development costs and interoperability issues associated with in-house solutions.
SIMS Software (Second of Two)
 Best Threat Intelligence Solution
Best Threat Intelligence Solution
-
SIMS Insider Threat Tool
-
The proliferation of insider threats is a complex and persistent challenge for all national security stakeholders. From the surge in super-malicious personas to simple carelessness on the job, insider threats are pervasive and elusive and are increasing at an alarming rate.

-
As the leader of industrial security information management for almost four decades, SIMS Software has elevated insider threat detection into a science, providing a fully automated 360° view of every physical, virtual, and human asset inside a security domain.
-
Companies often operate in siloed cultures and practices across their organization, which may interfere with information sharing; however, SIMS helps to break down those silos to harmonize data and see the patterns for a unique system-of-record for any compliance program where security operations, cyber security, and other functional areas such as HR and Risk Management can work together, share information and track insider threat cases.
-
SIMS includes an Insider Threat Utility that empowers organizations to establish proprietary threat models based on their existing data and the risk indicators that matter most to each unique organization so security professionals can view key metrics across the enterprise, track and catalog cases, view what was reported, investigated, and adjudicated to help the enterprise reduce risk and spot trends.

-
From negligent or disgruntled employees to hostile nation-state actors, the costs and consequences of insider threats can be staggering. SIMS Software offers a strategic opportunity to deliver a genuine ROI for businesses and saves organizations costly expenses by providing security stakeholders the opportunity to deter and mitigate, protect the company brand reputation, and retain customer trust.
-
Focused on evolving customer needs and government regulations, SIMS Software combines proven performance, constant innovation, and unmatched customer service to deliver a uniquely powerful security information management system.
-
SIMS supports all National Industrial Security Operating Manual (NISPOM), Special Access Programs (SAP), and Sensitive Compartmented Information (SCI) requirements and equips security stakeholders with the tools to protect the lifeblood of their organizations, speed detection, improve accuracy, and stay ahead of the threat.
-
*SIMS Software is also a Returning Premier Sponsor for their Third Consecutive Year, and was recognized as an ‘ASTORS’ Awards Champion in their Fourth AST ‘Homeland Security Awards Program.
SINGLEWIRE Software (First of Two)
 Best Access Control & Authentication Solution
Best Access Control & Authentication Solution
-
Visitor Aware
-
Visitor Aware from Singlewire Software provides the tools to screen visitors so government organizations can identify threats when they enter a building and before unwanted guests gain access to sensitive areas. This comprehensive tool helps provide peace of mind to verify visitors so organizations know that the people in their buildings have been given permission to be there.
-
Visitors have their IDs scanned when they enter a building, and Visitor Aware uses the information with encrypted facial recognition to screen visitors against government and sex offender watchlists and active legal injunctions. Potential issues are flagged to prevent guests from further entering a building, and approved guests can proceed to specific areas as appropriate.
(More organizations are realizing that safety starts at the front door. Singlewire Software now offers Visitor Aware, a visitor management and student management software solution that helps schools and organizations enhance safety at the front door. Courtesy of Singlewire Software and YouTube.)
-
Visitor Aware offers several features, innovations, and technical advances that will have a major impact on the security industry that similar solutions do not offer, such as encrypted facial recognition, no proprietary hardware, multi-site communication, and expected visitors can be provided a preregistration link to screen themselves in advance and be given a QR code to easily verify their identity and check-in quickly when they arrive.
-
Visitor Aware also offers interoperability with Singlewire’s InformaCast emergency notification and incident management software so organizations can get even more safety value out of it. It is designed for quick and simple setup and minimal configuration to provide as user-friendly an experience as possible.
SINGLEWIRE Software (Second of Two)
 Best Mass Notification Solution – Application
Best Mass Notification Solution – Application
-
InformaCast Personal Duress Package
-
The InformaCast Personal Duress Package is the latest mass notification innovation from Singlewire Software, allowing organizations to offer their workers personalized protection and notify others when they need assistance.
-
The InformaCast Personal Duress Package offers five types of panic buttons staff can leverage to request assistance and alert safety teams about potential issues, including a mobile app, wearable device, mounted device, keyboard shortcuts, and desk phone soft keys. With the touch of a button, safety teams can know who needs help and where they are located to deliver assistance as quickly as possible. The Personal Duress Package also includes access to all of the emergency notification and incident management capabilities available within InformaCast.
(Learn how the InformaCast Personal Duress Package from Singlewire Software offers two ways workers can trigger notifications to request assistance. Courtesy of Singlewire and YouTube.)
-
The InformaCast Personal Duress Package can enhance security with emergency alerts in any industry that wants to demonstrate that staff safety is a top priority. Organizations can use it to activate lockdowns, request medical assistance, or send alerts about active shooter situations and other emergency scenarios that threaten a worker’s safety.
-
*Singlewire Software has been Recognized as a Multi-‘ASTORS’ Awards Champion for its Sixth Consecutive Year in AST’s Annual Homeland Security Awards Program.
SIREN OPERATED Sensors (SOS)
 Best Fire & Safety System
Best Fire & Safety System
-
-
-
SOS Silent
-
SOS Silent Emergency Gate Access Systems are the fastest way for emergency vehicles to gain access to gated facilities, campuses, and residential communities.
-
-
-
This pure and simple system allows responders to focus their attention on driving and the emergency ahead – without having to push a remote, look up a code, stop to use a key, or change the channel on their radio to trigger the gate.

-
Using RFID the SOS Silent System will open gates quickly, silently, and automatically when emergency response vehicles come within range of the gate and can be adjusted from 10 to 600 feet to customize each gate entrance.
-
The SOS Silent also has a backup entry system to open with the “YELP” siren.
-
SOS Silent ensures first responders can get to community members in need without life-threatening delays. No stopping, no getting out of the vehicle, no codes to remember, no remotes to push, no keys to lose, and no cost to the municipalities.
(The Bexar County fire marshal’s office began routine inspections of siren-operated sensors in 2015 after a Defenders investigation revealed problems with how the equipment was being used or not used. Courtesy of KSAT 12 and YouTube. Posted on Apr 6, 2018.)
-
*Siren Operated Systems is a Returning ‘ASTORS’ Awards Champion for its Sixth Consecutive Years.
SolarWinds Worldwide
Best Security Incident & Event Management Solution (SIEM)
SolarWinds Hybrid Cloud Observability
-
Threats to IT networks continue to accelerate and evolve. While enterprising hackers from external sources test the robustness of network security parameters, internal threats from careless and malicious insiders remain a significant and ongoing concern.
(Learn how the rise of digital transformation has accelerated opportunities and increased challenges for organizations managing complex, diverse, and distributed environments. SolarWinds Hybrid Cloud Observability is designed to take complex IT deployments and make them easy to operate with proactive end-to-end observability. Courtesy of SolarWinds and YouTube.)
-
SolarWinds® Hybrid Cloud Observability was designed to help organizations ensure availability and reduce remediation time across on-premises and multi-cloud environments by increasing visibility, intelligence, and productivity.
-
SolarWinds Hybrid Cloud Observability gives you deep, holistic IT infrastructure and services visibility. It helps you focus on critical issues without a deluge of telemetry data to make better decisions and do more.
-
SolarWinds Hybrid Cloud Observability provides IT agility for today’s distributed environments.
-
By onboarding infrastructure, apps, and services into your monitoring ecosystem, SolarWinds Hybrid Cloud Observability enables you to reduce IT silos, enable cross-domain correlation, and increase collaboration—all while automating visualization, analytics, management, troubleshooting, and compliance tasks.
-
*SolarWinds has been officially recognized with Multiple Award Wins for Eight Consecutive Years. Thank you for your continued confidence in AST!
STELLAR Cyber (First of Two)
 Best Network Security Solution
Best Network Security Solution
-
In most situations, Network Detection & Response (NDR) tools alone are not enough to provide comprehensive security.
-
Analysts must also be able to see logs, real-time traffic, and user behaviors to detect complex attacks. Stellar Cyber’s pre-configured, single-license SecOps platform, powered by Open XDR, delivers built-in NDR and next-generation SIEM, UEBA, and TIP functionality to give analysts a full picture of what’s happening in the network.
-
Today’s cyberattacks occur across multiple vectors, so using a single tool to detect networks, user activities, or endpoints can’t present a complete picture of these attacks. Stellar Cyber Open XDR features enterprise-class NDR capabilities and correlates and analyzes that data with data from its SIEM, UEBA and TIP functions to detect complex attacks before they can do real damage.
(Security products are getting more complicated to deploy, maintain, and use, leaving lean security teams struggling to deliver consistent security across their on-prem, cloud, and hybrid environments. See how Stellar Cyber gives lean security teams a better way to protect their diverse environments, delivering automation that works for them, powered by Open XDR. Courtesy of Stellar Cyber and YouTube.)
-
The Open XDR Platform also democratizes security by combining all this functionality under a single, easy-to-use dashboard that can be trained within a day and operated by lower-level analysts (who are easier to hire in the highly constricted security analyst environment).
-
As such, the platform brings world-class security within reach for SMEs and MSPs looking to expand their offerings with managed security services.
STELLAR Cyber (Second of Two)
 Best Unified Incident & Event Management Solution
Best Unified Incident & Event Management Solution
-
Stellar Cyber’s cybersecurity software makes industry-leading security capabilities accessible to small/medium enterprises (SMEs) that might not have a large staff of security analysts or a large collection of security tools.
-
Stellar Cyber’s pre-configured, single-license SecOps platform, powered by Open XDR, delivers built-in NDR, next-generation SIEM, UEBA, and TIP capabilities and integrates with existing third-party tools such as EDRs.
(Discover how AI and Machine Learning transform security operations in this insightful 1-minute video discussion featuring F5’s Buu Lam and Stephen Salinas, and learn how these advanced technologies empower security teams to achieve better outcomes and enhance cybersecurity strategies. Courtesy of Stellar Cyber and YouTube.)
-
The Open XDR platform automatically normalizes and enriches data from all sources, correlates and analyzes the data with an AI- and machine learning-driven engine, and reports actionable incidents that analysts can immediately act upon to stop nascent attacks before they become a problem.
-
This reduces hacker dwell time in the customer’s network and ensures analysts look at real issues rather than chasing alerts and manually digging through data to find the needles in the haystack.
-
*Stellar Cyber is a Returning ‘ASTORS’ Champion, having secured Wins in the 2022 and 2021 Awards Programs.
SWIMLANE


-
Swimlane Turbine
-
Swimlane Turbine is a breakthrough in low-code security automation that transcends traditional SOAR and unlocks the full potential of extended detection and response (XDR) by capturing hard-to-reach telemetry and expanding actionability beyond the XDR ecosystem.
-
Swimlane Turbine allows U.S. government agencies to improve overall cybersecurity effectiveness while meeting the requirements of Executive Orders M-22-09 and M-21-31.
(Learn why Swimlane is a leader in cloud-scale low-code security automation, and find out how Swimlane Turbine can address your Security Automation Needs. Courtesy of Swimlane and YouTube.)
-
Swimlane has extensive experience supporting security operations for multiple U.S. government agencies; in particular, one of the most-significant US protection agencies faced pervasive challenges that included a security-cleared analyst shortage, an ever-changing threat landscape, and increased risk that stemmed from the adoption of cloud infrastructure.
-
Within the first year of implementation, Swimlane has improved this agency’s security ROI in several areas. The agency was able to automate its tier-1 activities, which included over 100 discrete checklists for triage, analysis, notifications, and escalation of security alerts, so analysts could focus on more advanced, action-centric roles such as incident response and forensics. It also helped overcome operational talent shortages and staff burnout while maintaining both talent and institutional knowledge.

Active. Autonomous. Adaptable. Swimlane Turbine is your system of record, powered by low-code security automation, that delivers on the promise of XDR
-
Swimlane Turbine is built to handle distributed, big data ingestion and can execute on thousands of concurrent automations in a way that is informed by federal agencies’ business logic, enabling U.S. security teams to speed up MTTR and reduce dwell time, which results in security teams gain the ability to respond to threats the instant they occur – not after detection, data aggregation, and manual response processes.
-
A System of Record that provides security with actionable intelligence: Swimlane Turbine delivers a system of record for all security through its case management, dashboard, and reporting applications. As an outcome, U.S. Homeland Security leaders have the insight needed to easily assess their most important SecOps metrics, ROI, and risk posture improvements.
-
*Swimlane, having secured a Win in the 2022 ‘ASTORS’ Awards Program, is a Returning ‘ASTORS’ Awards Champion.
Tanium

Best Device Visibility and Control Solution
-
Tanium Converged Endpoint Management (XEM)
-
In 2022, there were more than 4,100 publicly disclosed data breaches, equating to roughly 22 billion records being exposed. Ransomware attacks increased 13% in 2021 — equal to the last five years’ increases combined.
-
The Tanium Converged Endpoint Management (XEM) platform debuted in 2022 to reverse these trends by enabling customers to protect their people, defend their data, and secure their systems today for better resilience and defense against tomorrow’s threats.

-
Tanium solves this by delivering full visibility and control in real-time for every endpoint—across users, clouds, and IoT devices—enabling CISOs to see instantly whether hundreds of thousands of assets are installed, configured, patched, and used according to corporate policies so they can mitigate risk and reduce complexity using a single platform spanning operations, risk, and security teams.
-
To defend against attack surface proliferation and protect critical information and infrastructure, Tanium XEM offers a convergence of real-time decision-making, management, and remediation across IT, Compliance, Security, and Risk using a single pane of glass for one shared source of truth, a unified set of controls, and a common taxonomy that brings together siloed teams from across an organization.
(See why Tanium, the industry’s only provider of converged endpoint management (XEM), is leading the shift in legacy approaches to managing complex security and technology environments. Courtesy of Tanium and YouTube.)
-
XEM utilizes a patented linear-chain architecture, providing real-time visibility and control at scale, and a fully extensible data model with the ability to customize Tanium in any environment and with any desired integration among existing tools. The lightweight, performant Tanium single agent spans the breadth and depth of all XEM platform capabilities.
-
With Tanium, organizations can identify vulnerabilities instantly and deploy patches at a first-pass success rate that exceeds 99% to keep data safe.
-
*Tanium is a Returning ‘ASTORS’ Award Champion, having secured their first Win in the 2022 ‘ASTORS’ Awards Program.
TEKNOSCAN Systems
 Best Contraband Detection Solution
Best Contraband Detection Solution
-
A Recent trial at a European seaport resulted in the interception of 1.5 tons of cocaine concealed in various cargo. High-volume sampling carried out at the air vent, and through the door gasket allowed aspiration of airborne particles and vapors to be collected and detected onsite.

-
TeknoScan offers practical, rapid, and reliable substance trace detection and identification systems for port security applications.
-
The TSI 3000, mounted in a mobile van, facilitates movement inside the seaport and responds quickly to urgent inspection of newly landed containers.
-
X-ray imaging did not detect the contraband because of its concealment in various commodities, such as fruits, frozen meat, etc. Trace chemical detection as a primary or secondary screening tool with imaging technology can provide a powerful means of intercepting contraband in marine containers.
-
The U.S. Congress mandated that all inbound cargo containers be 100 percent inspected for explosives, narcotics, and other threat substances by 2012 to improve security, yet only a small percentage of cargo containers are inspected for security threats.
-
Since opening each container is not practical, it is necessary to introduce another screening method that will not disrupt the flow of commerce.
-
TeknoScan Systems complements imaging, radiation, and canine solutions with its trace detection technology to rapidly detect and identify explosives, narcotics, and other threat substances.
-
*TeknoScan is a Returning ‘ASTORS’ Champion, having secured an ‘ASTORS’ Award in the 2022 and 2018 Awards Programs.
TELEDYNE FLIR
 Best CBRNE Detection Solution
Best CBRNE Detection Solution
-
The G510x Gas Chromatograph-Mass Spectrometer (GC-MS) is a New Portable Chemical Detector that provides incredibly accurate detection analyses in the field, enabling field agents in Law Enforcement, Border Patrol, and other agencies struggling against the Opioid epidemic to quickly and accurately identify those narcotics in 5 minutes in the field.

-
This device, built on the technology of the 2017 ‘ASTORS’ Best CBRNE Detection System winner, the Griffin G510, was designed to aid in the struggle against this wave of drugs that are affecting Americans in every walk of life.
-
The revolutionary Griffin™ G510x portable chemical detector is specifically designed to analyze and identify explosives and narcotics, including fentanyl, during field operations. This new variant allows front-line personnel to identify street drugs within five minutes confidently.
-
Domestic and international public safety teams widely use Teledyne FLIR’s Griffin G510 platform for real-time in-field chemical threat confirmation. Modifications on the new G510x enable operators to identify trace amounts of narcotics in complex mixtures that are now the norm. Opioids such as fentanyl and the xylazine combination ‘tranq’ pose serious threats to users and emergency responders alike.
(Meet the new Griffin™ G510x. A Portable GCMS Specialized for Detecting Narcotics like Fentanyl and Xylazine. Purpose-built to provide a new tool against the Fentanyl epidemic. Courtesy of Teledyne FLIR and YouTube.)
-
When identifying drugs in the field, confidence levels are crucial to medical staff and police. The Griffin G510x has proven uniquely capable of confirming deadly narcotics ‘hidden’ within other substances. Given the potency of fentanyl and its derivatives, even a microscopic amount can be life-threatening. G510x can spot as little as a two-percent fentanyl concentration mixed in a background of common pain relievers, while other systems might only detect the pain reliever.
*Teledyne FLIR (formerly FLIR Systems, is a Returning ‘ASTORS’ CHAMPION, having secured Wins in all Eight Consecutive Years of the Annual ‘Homeland Security Awards. Thank you for your continued support of American Security Today!
VALOR Systems
 Best Unified Situational Awareness Solution
Best Unified Situational Awareness Solution
-
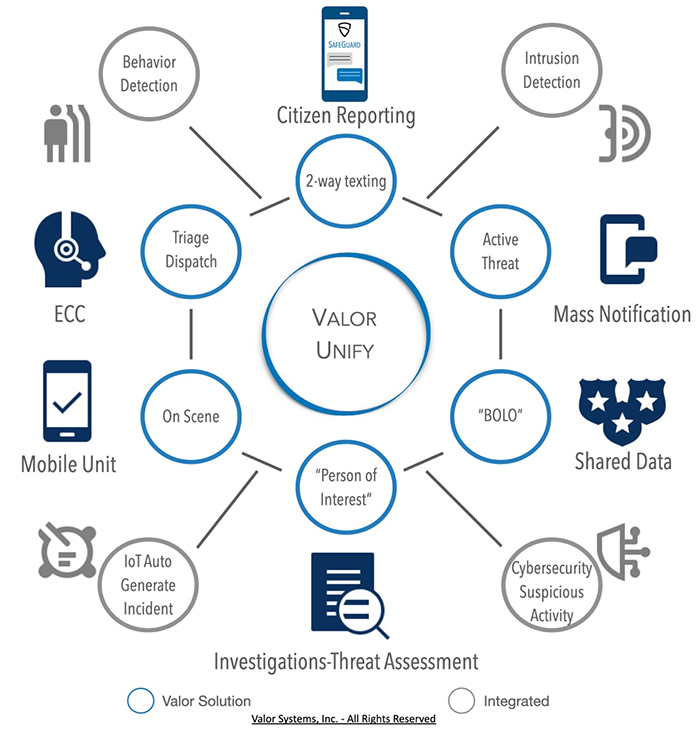
As a component of the Valor Incident Management System Platform, Valor Unify orchestrates seamless integration of technology with stakeholders for a unified security model.
-
Understanding the threat from a unified approach enables real-time, integrated information and increases efficiencies to improve response time and collaboration with Valor CAD. Valor Case Management compiles shared information across your operations to accelerate investigations and mitigate potential threats.
-
The Valor Incident Management System (Valor IMS), is an integrated suite of modern computer programs designed to automate and enhance the flow of critical information amongst communications operators, the response units in the field, support units, and the public, and serves the emergency response and records management needs of government, corporate security, and university safety/security organizations, with an interactive situational awareness incident management platform to complement synergistic operations among all stakeholders.
(The most effective security model begins with a holistic, fluid, crisis preparedness model that includes all stakeholders. Find out how Valor IMS can bring together stakeholders who share a common goal, unite SOPs, and share intelligence, processes, and workflows so Security Operations can proactively mitigate potential threats and manage incidents. Courtesy of Valor Systems and YouTube.)
-
Valor Systems Integrated Public Safety and Security Software Platform offers CAD, RMS, Mobile, and citizen reporting applications that can work independently and/or collectively in concert as one unified platform based on a client’s budget, operational needs, and installation timeframe,

-
Valor SafeGuard is an intuitive smartphone application providing a real-time emergency communication solution integrated into the public safety communication center’s CAD system (Valor or third-party) and is designed to empower a local community to increase their safety.
- Valor Systems component solutions can be installed locally on a customer’s computer network or accessed as a Software as a Service (SaaS) hosted on a CJIS-compliant, secured “cloud” network.
-
*Valor Systems is a Returning ‘ASTORS’ Award Champion, having secured Wins in the 2022 and 2021 Homeland Security Awards Programs.
VERITONE (First of Three)
 Best Identification Management Solution
Best Identification Management Solution
-
Despite public perception (and fictional TV show plots), even when criminals are caught on camera, law enforcement still has their work cut out to identify a suspect and connect them to the crime.
-
Unfortunately, many agencies lack the resources and tools to effectively search against databases of known offenders and previously arrested or booked individuals – causing them to engage in manual processes that require significant time and resources.
-
Because of this, with the vast majority of agencies still manually sifting through masses of arrest records, turning to colleagues for intel, and even promoting cases publicly to identify potential persons of interest (POI) – the AI-powered identification management solution Veritone IDentify is a game changer.
(Veritone IDentify automatically compares your known-offender and person-of-interest records with video and photographic evidence, enabling you to quickly identify potential suspects for further investigation. Harness the power of artificial intelligence to IDentify to catch bad guys. Courtesy of Veritone, Inc., and YouTube.)
-
Built upon Veritone’s proven aiWARE AI platform, IDentify empowers law enforcement agencies to compare photographic and video evidence of a person committing a crime against criminal records databases, substantially streamlining operational workflows and identifying suspects faster than ever before, so law enforcement can accelerate investigations and increase department case clearance rates, underpinning the significant value that Veritone IDentify provides.
-
Veritone IDentify enables a wide range of capabilities including:
-
Search: Investigators can create cases where AI-powered engines automatically compare a perpetrator who appeared in digital evidence of a crime against countless known offender booking records.
-
Filter: LEAs can further filter down potential matches found in existing arrest records by key identifiers already stored in their booking databases, such as gender, age, race, and height.
-

Harness the power of your booking database to identify suspect leads faster and increase case clearance rates.
-
-
Aggregate: Review a list of potential persons of interest for further evaluation or investigation.
-
Consolidate: Veritone IDentify allows LEAs to consolidate information in a centralized and secure web-based platform, including a POI’s appearance in evidence, booking photo, last known address, and more.
-
Collaborate: LEAs can share information with intra- and inter-agency colleagues to process POI data faster with enhanced agency collaboration.
-
Organize: Booking evidence can be organized by case details such as ID, department, officer(s) involved, description, location, time, and notes.
-
-
For example, a Southern California Police Department had an offender database with 20,000 images and growing, and their manual process of identifying suspects was slow, inefficient, and extremely challenging.
-
With Veritone IDentify they were able to automatically compare detected faces in evidence to the agency’s databases, resulting in more and faster case resolutions – saving valuable resources, time, and money. In fact, in just eight months’ time, the police department was able to detect 50 suspect matches – an accomplishment unachievable with their previous manual process.
VERITONE (Second of Three)
 Best License Plate Recognition Solution
Best License Plate Recognition Solution
-
When it comes to investigations, license plate information can be a key source of evidence. It is also something that needs to be handled carefully – and oftentimes redacted to comply with freedom of information laws and other public records requests.
-
In fact, it’s the high cost and resource commitment of redacting sensitive information from media evidence that’s taking its toll on public safety agencies.
-
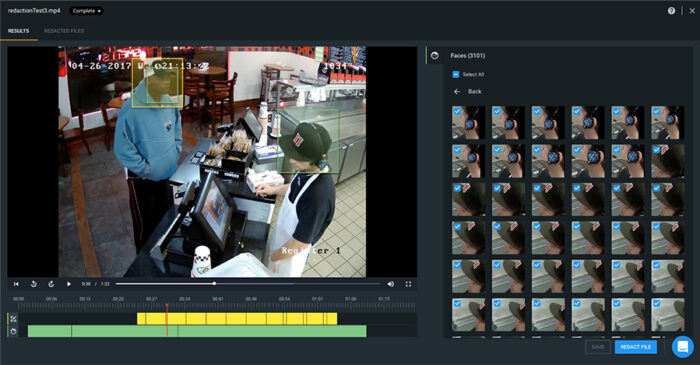
Veritone Redact automatically detects license plates [as well as human heads, laptops, and in-vehicle mobile data terminals (MDTs)] and enables users to define other sensitive imagery and objects within a scene manually, then redacts this information from audio and video evidence.
-
From there, the redacted evidence can quickly be downloaded with audit logs to support chain of custody requirements and shared with colleagues, public defenders, and other key stakeholders.
-
Developed for public safety and justice agencies, cloud-based AI-powered Veritone Redact automates the process of obscuring sensitive imagery like license plates in media evidence – significantly improving manual and time-intensive, frame-by-frame evidence redaction workflows.
-
With automatic tracking of sensitive imagery, Veritone Redact can be used to tackle massive volumes of video content quickly and efficiently. In addition, AI-powered automated redaction reduces the risk of missed redactions that can occur during manual processing due to human error.
(The high cost of redacting sensitive information from evidence is taking its toll on public safety and judicial agencies. Yet doing so is required to keep witnesses safe and comply with freedom of information laws and consent decrees. Veritone Redact systematically detects faces and allows you to define other sensitive imagery within a scene, then automatically redacts this information from your video evidence. From there, you can quickly download the redacted evidence with logs to support chain of custody requirements and share it with colleagues. Courtesy of Veritone, Inc., and YouTube.)
-
Veritone Redact is used by many law enforcement agencies across the country. For example, the Lake Stevens Police Department in Washington implemented Veritone Redact to increase productivity and improve workflow efficiencies while meeting the demands of public records requests. The result was significant – up to 90% time savings compared with manual processes.
-
Veritone Redact is built on Veritone’s proven AI platform – aiWARE – which powers purpose-built applications for public safety professionals. Thousands of law enforcement personnel daily rely upon the enterprise-scale AI capabilities of aiWARE-based applications to accelerate investigations, protect personally identifiable information, and keep their communities safe.
VERITONE (Third of Three)
Best Investigation/ Surveillance/Detection Solution
-
Veritone Tracker is an AI-powered tracking solution that leverages confidence-based similarity detection to track people and objects through video recognition software.
-
Veritone Tracker provides the unbiased insights needed to assess the visual description of a person in a scene, what they are doing, and the context of others in the scene, without performing facial recognition or other biometric identification that would reveal a person’s identity.
-
One of the greatest values of Veritone Tracker is that users can input video files from different cameras to find a person of interest, and then string together these separate video files.

-
As a result, Veritone Tracker enables law enforcement, legal teams, security, and justice organizations to quickly build an understanding of an individual’s activities and associations by assembling a collection of moments in video files to create a timeline. This type of “digital forensics” helps build a narrative around an event or individual captured on video.
-
Video surveillance and evidence review are often performed manually, and can take countless hours to understand where and when people appeared and the context of a scene. AI helps make video evidence review more effective, efficient, and economically competitive; however, technologies such as facial recognition have traditionally brought privacy concerns to the forefront.
-
Veritone Tracker addresses many of these privacy concerns while enabling agencies to keep communities safe while managing the burden of reviewing hours of video footage by helping law enforcement, public safety agencies, and building/event security teams track a person across multiple video sources and camera angles without the use of any biometric markers – and without violating privacy laws or diminishing the integrity of an individual’s personally identifiable information (PII).
-
As a digital forensics tool, Veritone Tracker’s AI engine identifies people as human-like objects (HLOs) in frames across videos and stores those as detections. Tracker returns potential matches from those HLOs identified by the AI engine. Unlike anything on the market today, Veritone Tracker makes video analysis from multiple sources faster and more accurate so that agencies can better serve and protect their communities.
Versa Networks
 Best Network Security Solution
Best Network Security Solution
-
-
-
Versa SASE (Secure Access Service Edge)
-
-
-
Versa is unique among SASE vendors, providing an end-to-end solution that simplifies and secures the modern network.
-
Based on VOS™, Versa SASE delivers a broad set of capabilities via the cloud and on-premises for building agile and secure enterprise networks and highly efficient managed service offerings.
-
Available via the cloud, on-premises, or as a blended combination of both, Versa SASE connects Enterprise branches, teleworkers, and end users wherever they exist securely and reliably to applications in the cloud or data centers worldwide.
(Available via the cloud, on-premises, or as a blended combination of both, see how Versa SASE connects Work-from-Home users to Enterprise branches securely and reliably to applications in the cloud or data centers worldwide. Courtesy of Versa Networks and YouTube.)
-
With tens of thousands of customers, hundreds of thousands of sites, and many very large financial services, retailers, manufacturers, high-tech, public sector, and healthcare customers, Versa has demonstrated itself as a leader in delivering mission-critical secure networking solutions.
-
Customers look to Versa to help them solve some of their most challenging security and networking needs, including support for hybrid work models, multi-cloud connectivity, and mobile 5G and satellite networking.
-
*Versa Networks is a Returning ‘ASTORS’ Award Champion, having secured its first Win in AST’s 2021 Homeland Security Awards Program.
West Virginia American Access Control Systems
 Best Integrated Security Management Solution
Best Integrated Security Management Solution

-
Smart and Secure, the AACS Series 300 security portal is designed to simplify security.
-
Available in single-slide or bi-parting doors, the AACS Series 300 has a throughput of six people per minute. The bi-parting doors reduce wait times and are perfect for high-traffic entrances.
-
Made in the USA with U.S. components, all parts are always readily available. The portal is factory assembled and tested to ensure all corresponding parts fit properly, eliminating the time-consuming problem of field modifications.
-
The electronic panel of the AACS Series 300 security portal (which is now covered by a ten-year warranty) is pre-wired and labeled for plug-and-play use, and AACS Series 300 units do not require a pit to be dug into the floor, eliminating costly and time-consuming construction.
(Hear a client testimonial on the performance and benefits of WVAACS security portals by VarcoMac, a leading electrical contractor providing 24/7 services to the Baltimore-Washington Metro Area for over 40 years. Courtesy of WV Access Control Systems and YouTube.)
-
*WVAACS is a Returning ‘ASTORS’ Awards Champion, having secured Wins in the 2022, 2020, 2019, and 2018 Homeland Security Awards Programs
WSI Technologies
 Best Video Data Storage Solution
Best Video Data Storage Solution
-
iRecord Cloud
-
WSI Technologies’ iRecord Cloud storage solution enhances the efficiency of public safety work by streamlining evidence sharing and modernizing the investigatory process.
-
Introduced in 2021, the solution allows users to store, access, and share recorded interviews digitally securely.
-
With over 20 years of experience in the child advocacy, law enforcement, and healthcare industries, iRecord has created direct solutions to inefficiencies when dealing with interview evidence.

-
Clients that rely on iRecord Cloud’s easy-to-use interface include the Department of Homeland Security Investigations, the Los Angeles Police Department, the Florida Department of Health, and more than 50% of child advocacy centers nationwide.
-
Implemented in more than 600 child advocacy centers, iRecord’s digital recording ecosystem keeps sensitive interview data secure using advanced software methodology.
-
iRecord’s robust cloud solution mitigates the risk of losing data by backing up files using Geo-Redundant Storage replicating the data across two geographically distributed data centers. iRecord Cloud also minimizes open firewall ports and relies on stringent encryption standards and a secure hashing algorithm to protect data at rest and in transit.
(Learn about iRecord – the Company. Courtesy of Vimeo and Andrew Heiser and iRecord.)
-
iRecord Cloud storage solution eliminates the manual process of downloading and sharing files back and forth on USB drives and other physical methods of interview evidence sharing; investigators and prosecutors can access iRecord video recordings anytime and from anywhere.
-
While creating an intuitive and convenient method of storing and sharing interview recordings, iRecord Cloud strictly complies with federal, state, and local requirements for evidence data storage. This includes the FBI’s Criminal Justice Information Services guidelines, the United States Federal Risk and Authorization Management Program, and the Department of Defense Enterprise Cloud Service Broker.
ZeroEyes
 Best Metal/Weapons Detection Solution
Best Metal/Weapons Detection Solution
-
ZeroEyes proactive visual gun detection and intelligent situational awareness platform is based on computer vision and advanced machine learning AI.
-
ZeroEyes’ software is layered over existing digital security cameras to detect guns the instant that they become visible, immediately sending keyframe images of gun detections to the company’s 24/7/365 ZeroEyes Operations Center (ZOC) for human verification.
-
If a positive confirmation is made, ZeroEyes dispatches an automated alert to first responders and local staff that includes accurate and actionable intelligence about the shooter’s appearance, location, and type of weapon – all in as fast as 3 to 5 seconds from detection.
(See how ZeroEyes software is being used across Western New York to turn existing CCTV cameras into a proactive security solution to detect visible firearms. Courtesy of ZeroEyes and YouTube.)
-
ZeroEyes also helps to de-escalate swatting and hoax incidents by determining if the threat is real or fake, providing necessary situational awareness to first responders.
-
The information provided by ZeroEyes is invaluable to first responders, who must act quickly with as much information as possible about a potential active shooter. A common issue seen today when active shooter incidents occur is that first responders lack the situational awareness necessary to locate the shooter, contain the threat, and prevent further loss of life.
-
In most active shooter events, more than one hundred 911 calls are being made with contradictory reports, creating significant confusion (a ‘fog of war’) and making it impossible to gauge the true nature of the threat. ZeroEyes has been shown to cut response time by nearly 2/3rds in training scenarios.
(The Ocean City School District in New Jersey and the city’s boardwalk have implemented new technology developed by ZeroEyes, a company that says it uses AI, paired with human experts, to scan camera feeds for guns. Courtesy of ZeroEyes and YouTube.)
-
The only video analytics company to receive the US Department of Homeland Security SAFETY Act Designation, ZeroEyes’ software has detected more than a thousand fake and real guns being brought into schools and other locations.
-
The company’s founders firmly believe in personal privacy, so they designed the software to identify only guns, not people. The algorithms look for guns, not faces or body types. Until a gun is identified, the monitoring screens in the ZOC stay absolutely blank; the team does not see a live feed from any cameras. Further, ZeroEyes’ platform does not store personal or biometric data or conduct any kind of facial recognition, so there is no risk of bias based on skin color or other personal characteristics.
-
ZeroEyes AI Visual Gun Detection solution is deployed in thousands of buildings for hundreds of customers across 35+ states, including the US Department of Defense, public school districts and universities, commercial property groups, manufacturing plants, Fortune 500 corporate campuses, shopping malls, retail outlets and more.
- *ZeroEyes is also a Returning ‘ASTORS’ Awards Champion, having secured Multiple Wins in the 2022 ‘ASTORS’ Awards Program.
The 2023 ‘ASTORS’ Awards Program is Proudly Sponsored by Platinum Event Sponsor: NEC National Security Systems (NSS)
And Our RETURNING Premier Sponsors:
ATI Systems, Automatic Systems of America,
Guard Dog AI, IPVideo Corporation, Rajant Corporation, RX Global, SIMS Software, and American Security Today!
View Part 1 Winners A – GL View Part 2 Winners GU – M
NEXT Part 4 Government Excellence Part 5 Innovation & Leadership
- **IN A RARE TIE Event – a tie results from extremely differing objectives and/or similar technological applications.
American Security Today would like to Congratulate each and every one of our Outstanding 2023 ‘ASTORS’ Government Excellence Awards Winners!
We look forward to following your future innovations and sharing them with our over 75,000 dedicated AST readers at the Federal, State, and Local levels of Government, Security Professionals, and firms allied to government.
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old-school basics to what is Today – a fast-changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace and brings forward a fresh, compelling look and read with our customized digital publications that hold readers’ eyes throughout the story with cutting-edge editorials that provide solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

AST Digital Publications are distributed to over 75,000 qualified government and homeland security professionals in federal, state, local, and private security sectors.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches Private and public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture, and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from the Government at the federal, state, and local levels, as well as from private firms allied to the government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website, and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants and Dams, Bridges and Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting and Concert Stadiums, our Nation’s Schools and Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
To learn more about ‘ASTORS’ Homeland Security Award Winners solutions, Be On the LookOut for the 2023 ‘ASTORS’ CHAMPIONS Edition Fully Interactive Magazine – the Best Products of 2023 ‘A Year in Review.’
The Annual CHAMPIONS edition reviews ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firm’s products and services, including video interviews and more.

It will serve as your Go-To Source throughout the year for ‘The Best of 2023 Products and Services’ endorsed by American Security Today and can satisfy your agency’s and/or organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection, and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware, and Networking Security – to name a few), the 2023 ‘ASTORS’ CHAMPIONS EDITION will have WHAT YOU NEED to Detect, Delay, Respond to, and Mitigate today’s real-time threats in our constantly evolving security landscape.
It will also include featured guest editorial pieces from some of the security industry’s most respected leaders and recognized firms in the 2023 ‘ASTORS’ Awards Program.
For more information on All Things American Security Today, as well as the 2024 ‘ASTORS’ Awards Program, please contact Michael Madsen, AST Publisher at mmadsen@americansecuritytoday.com.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos