
In keeping with tradition, and in addition to Director Steven Dettelbach of the Bureau of Alcohol, Tobacco, Firearms (ATF) and Explosives, AST was honored to welcome Legendary Police Commissioner William Bratton, who expressed his concerns about the complexity of violence and the challenges to leadership across law enforcement and at the national level, and as always his love for the city of New York.
He spoke to the ‘broken windows theory’ and how, in his experience, policing methods that address what some deem as minor or quality-of-life crimes – help create an atmosphere of order and lawfulness, as compared to enabling leniency of visible, anti-social behavior and civic disorder, especially in urban environments, that encourage further lawlessness, disorder, and increasingly serious crimes, as we have witnessed across the nation’s cities.

Commissioner Bratton, the Executive Chairman of Risk Advisory at Teneo, has led six police departments, two of the largest in the country, New York and Los Angeles, including New York twice!
From his earliest days in uniform in Boston, he has been dedicated to identifying the catalysts for crime and working toward prediction and prevention.
Commissioner Bratton is one of the world’s most respected and trusted experts on risk and security issues.
He was recognized as the ‘2019 ‘ASTORS’ Person of the Year’ for his Dedication and Extraordinary Leadership in the Homeland Security and Public Safety arenas.
This year, American Security Today was delighted to honor Commissioner Bill Bratton with the Inaugural 2023 ‘ASTORS’ Lifetime Achievement Award in recognition of his almost 50-year career in Public Safety and Homeland Security – to which he has dedicated his life and continues to drive thought leadership and innovation.

Commissioner Bratton instituted progressive change that brought dramatic drops in crime while leading six police departments, including seven years as Chief of the Los Angeles Police Department and two nonconsecutive terms as the Police Commissioner of the City of New York.
He is the only person who has even been entrusted to lead the police agencies of America’s two largest cities.
Propelled by extraordinary results, Bratton had a dazzling rise, and ultimately a dazzling career, becoming the most famous police commissioner of modern times.

If you haven’t had the opportunity to read his latest book,‘The Profession: A Memoir of Community, Race, and the Arc of Policing in America,’ please pick up a copy today. The Profession is the story of that career in full.
Everywhere he went, Bratton brought his revolutionary data-driven approach and extraordinary leadership skills to bear to slash crime rates and professionalize the vocation of the cop.
But his career has not been without controversy, and central to the reckoning of The Profession is the fundamental crisis of relations between the Black Community and Law Enforcement, a Crisis he now believes has been inflamed by the unforeseen consequences of some well-intentioned policies.
‘Crime exacts a terrible cost on us, but so can punishment.’
Before assuming his role at Teneo Risk Advisory, Commissioner Bratton was the 42nd police commissioner of the City of New York from January 2014 to September 2016, during which he oversaw 32 months of declining crime, including historic lows for murders and robberies.
(Hear directly from Commissioner William Bratton. Courtesy of American Security Today and Vimeo.)
The 2023 ‘ASTORS’ Homeland Security Awards Presentation Luncheon was an exclusive sold-out event featured at ISC East, where over two hundred representatives of law enforcement, public safety, and industry leaders came together to honor the selfless service of those who stand on the front lines – and those who stand beside them – providing the capabilities and technologies to create a safer world for future generations.
Comprehensive collaborations between these private and public sectors have led to the development of innovative intelligence and technologies that serve to protect our Nation.
(Continued…)
GUARDDOG AI (First of Three)
Best Cyber Cloud Platform Solution
-
Fido, vFido with Protective Cloud Service Platform
-
GuardDog AI’s Cyber Security platform combines a simple-to-deploy Fido virtual device, deployable on any network in just minutes, immediately delivering intelligence to the Protective Cloud Service, which within an hour offers cybersecurity analytics on what it sees from a Fido or any number of combined Fidos across an organization’s networks as desired.

Securing Networks & IoT Devices with Autonomous Detection and Response from guardDog AI.
-
GuardDog AI offers a complete incident response plan simple and cost-effective with their AI-driven Threat Intelligence Solution platform, which identifies threats and stops attacks in milliseconds, providing Automated Threat Containment by deploying countermeasures.
-
When combined with simplified analytics provided by guardDog AI’s Protective Cloud Service, analytics report on the risk of exploitation per device on the network. Other risk management solutions do not cover and cannot thwart the attempted exploits detected on networks, leaving the containment step to be accomplished by a service organization or internal IT by shutting down critical infrastructure and making eradication timely and expensive for any organization.
(Hear from guardDog AI founder and CEO Peter Bookman on all things guardDog AI, and why the need to protect your business and family is greater than ever. Courtesy of F1 FibreFast and YouTube.)
GUARDDOG AI (Second of Three)
Best Vulnerability Management Solution
-
Fido, vFido with Protective Cloud Service Platform
-
GuardDog AI’s Cyber Security platform combines a simple-to-deploy Fido, or vFido (virtual) device, deployable on any network in just minutes, immediately delivering intelligence to the Protective Cloud Service (PCS).
-
Using GuardDog AI’s Protective Cloud Service combined with deploying Fidos on any network, organizations can analyze, score, contain, and eradicate cybersecurity incidents through automation, bringing high business resilience.
(See a demonstration of how guardDog AI repels penetration attacks through its sophisticated platform. Courtesy of guardDog AI and YouTube.)
Now, organizations can respond faster than ever to incidents. The guardDog AI Solution exposes invisible threats on networks in ‘edge territory’ and the devices attached to them. It uses patented technology to address and prevent cybersecurity threats before they compromise network environments and business processes.
GUARDDOG AI (Third of Three)
Best Cyber Analytics Solution
-
Fido, vFido with Protective Cloud Service Platform
-
GuardDog AI has provided the world with a cybersecurity platform for visibility to identify the vulnerabilities that threaten network security and containment of attempted exploits.
-
GuardDog AI’s simplified detection, analytics, and containment solution combines a simple-to-deploy Fido or vFido (virtual) device, deployable on any network in minutes, immediately delivering intelligence to the Protective Cloud Service (PCS).

-
The Fido, or vFido device, additionally offers automated containment of attempted exploits using the network in microseconds, stopping them from being successful. GuardDog’s Protective Cloud Service collaborates with a companion Fido unit to simplify cybersecurity risk scoring and attack response for network security and the incident response process.
-
The solution exposes vulnerabilities on networks in ‘edge territory’ and the I.O.T. and Wi-Fi devices attached to them, using patented technology to address and contain attempted exploits before they compromise network environments and organizations.
-
*AST is delighted to welcome back guardDog.ai, as a Returning ‘ASTORS’ Awards Sponsor, and a Returning ‘ASTORS’ Champion for their Third Consecutive Year.
GURUCUL
Best Cyber Security Solution
-
Gurucul Security Analytics
and Operations Platform
-
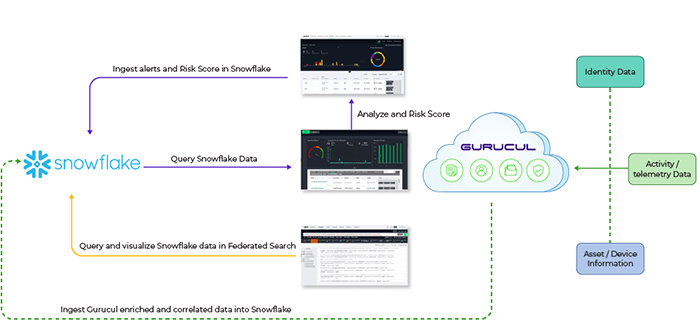
Gurucul Security Analytics and Operations Platform is the first ever cloud-native, unified, and modular platform for consolidating core security operations center (SOC) solutions with the vital addition of Identity Threat Detection and Response (ITDR) to provide a next-gen SOC platform by consolidating the company’s award-winning Next-Gen SIEM, Open XDR, User and Entity Behavior Analytics (UEBA), Network Traffic Analysis (NTA), Security Orchestration Automation and Response (SOAR), and Identity & Access Analytics into a single pane of glass that is aligned with the evolving needs of the modern enterprise threat landscape – where identity has become the new perimeter.
-
Gurucul’s innovative platform is purpose-built to automate and accelerate data collection, event and alert correlation, detection triage, investigation, and response to targeted attacks. It combines threat intelligence with an enterprise-class risk engine, delivering precise contextual detections, prioritized investigation, and risk-driven response actions that drastically reduce mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR).
-
Gurucul’s platform can also support the most complex deployments, including on-premises, hybrid, and cloud (SaaS, private, GovCloud, and multi-cloud including multi-tenancy), addressing the needs of today’s modern enterprise and managed detection and response (MDR) providers.
-
As organizations transform their SOC to support multi-cloud deployments and zero trust programs, they are looking for an end-to-end solution to help them improve security analyst effectiveness in rapidly identifying and confirming threats and alerts and the entire attack campaign.
(Learn how Gurucul’s real-time Unified Security and Risk Analytics Platform combines machine learning behavior profiling with predictive risk-scoring algorithms to predict, prevent, and detect breaches. Courtesy of Gurucul and YouTube.)
-
While other SIEM or XDR solutions are just starting to scratch the surface of identity, Gurucul has been a provider of Identity Analytics solutions for over a decade with robust access analytics, broad integrations with various identity systems such as IAM, PAM, HRMS, CMDB, IDaaS, etc., and risk-based access remediation and authentication.
-
In conjunction with its UEBA capabilities, Gurucul helps customers understand current-state identity access and authorization policies and access usage anomalies and risk exposures to plan out a robust and secure zero-trust strategy.
-
*Gurucul is a Returning ‘ASTORS’ Award Champion, having secured Wins in the 2022, 2020, 2019, 2018, and 2016 Homeland Security Awards Programs.
HAINES’ Security Design School
Best Federal Training Program
for Government or Military
-
Physical Security Engineering Training
and Certification Program -
By encouraging the interdisciplinary dialogue between verticals, Haines Security Solutions (HSS) trains architects, engineers, facility managers, planners, security, and other professionals involved in the building design process on how to integrate security technologies into new construction and major renovation projects.
-
Courses under Haines’ Physical Security Team Training and Certification Program (PSET&C) include Security Concepts for Design Teams, Non-Physlical Elements Essential to Physical Security, the Power of Security Lighting, Hostile Shooter Mitigation Strategies, Safe-Room Security for Public and Private Venues, Security and the Sensitive Treatment of Historic Buildings and Monuments: There is ‘Wiggle Room,’ Physical Security Beyond Crime Prevention through Environmental Design (CPTED), and the Puppy Movement: Hiding Security in Plain Sight, and more.
-
Haines’s proprietary risk analysis methodologies go beyond federal, state, and local regulations in assessing physical security vulnerabilities of buildings and compounds and their supporting energy systems, with formulas that provide unique cost-benefit analyses based on risk reduction and not necessarily project costs.
-
Therefore, decision-makers can implement solutions that affect the highest number of people first.
(See a brief overview of Haines Security Solutions capabilities. Courtesy of Haines Security Engineering and YouTube.)
-
Furthermore, architects and engineering firms seek Haines Security’s advice when solving security engineering issues during the design process, both for new construction and major renovation projects.
-
HSS provides cost-effective mitigation strategies addressing the whole instead of providing protection options piecemeal. Decision-makers prefer the company’s prioritized approach because it allows them to budget short-term, forecast long-term, and implement solutions as funds become available.
HANWHA VISION AMERICA
Best Video Data Storage Solution
-
Hanwha Vision SolidEDGE Camera
-
Government organizations, especially those on a city or local level, can use Hanwha Vision’s SolidEDGE cloud-managed solution to easily customize and expand their surveillance systems with multi-camera recording, remote access, and on-premise security system management.

-
SolidEDGE is the first true serverless camera system with onboard Solid State Drive (SSD) storage and an embedded WAVE VMS server. Each SolidEDGE camera can connect and record up to five additional cameras, and users can also merge up to 30 SolidEDGE systems through WAVE Sync.
-
SolidEDGE cameras feature a quad-core CPU, a dedicated encoder with 4GB of RAM, and an embedded Linux operating system – for powerful serverless edge-based recording, and models are available with 1TB or 2TB onboard rugged SSD storage.
(Hanwha Vision’s New SolidEDGE Camera has a built-in rugged SSD for recording video footage and eliminating the need for other storage devices, an embedded WAVE VMS server for cloud video management, and can record up to 6 cameras. Courtesy of Hanwha Vision and YouTube.)
-
A municipality’s courthouse or town hall might be in the same building or complex as the police department and need to monitor several areas and share footage across multiple departments, or public works and recreational facilities might have fewer than six cameras or be in isolated areas without access to a proper IDF – all environments that could benefit from the scalability and flexibility of SolidEDGE.
HID GLOBAL (First of Two)
Best Smart Card/Reader Solution
-
HID Mobile Access®
-
HID Mobile Access® merges security with convenience by allowing building tenants to use their phones or wearables to access places, spaces, and systems. This trusted technology is key to occupant engagement, sustainability, operational efficiency initiatives, and security in a mobile-first world.
-
This convenient, intuitive access system uses simple, familiar gestures at — and beyond — the front door. Users can access facilities with a simple tap or HID’s very own “Twist & Go” functionality that adds an additional layer of security for easy and convenient access. Credentials are stored either in mobile apps, the phone manufacturer’s secure element, or the native wallet, eliminating the need for the end user to carry multiple access cards. Because mobile credentials eliminate the need for plastic cards, HID Mobile Access helps reduce environmental impact and enables end-users to quickly achieve their ESG goals.
(HID Mobile Access is a modern access control solution that provides choice and convenience for your employees and visitors while simultaneously delivering the efficiency and flexibility you require at the highest levels. Powered by Seos, mobile access works with various mobile devices, including smartphones, smartwatches, and tablets. Best of all, mobile access allows you to create the right program for your organization, whether a purely mobile solution or mobile credentials paired with traditional card credentials. Subscription billing for mobile credentials offers scalability with predictability. Courtesy of HID and YouTube.)
-
HID Mobile Access reduces an organization’s risk in a variety of ways. For example, the HID solution does not rely on PINs that can be easily shared or on legacy systems vulnerable to cloning. Instead, HID Mobile Access supports multi-factor authentication, biometric identification, and other advanced security features beyond legacy cards’ capabilities. Powered by HID’s Seos® credential technology, HID Mobile Access solutions are standards-certified and privacy legislation-compliant, bringing convenience, efficiency and security to physical access control solutions.
HID GLOBAL (Second of Two)
Best Device Visibility and Control Solution
-
HID Linq™
-
HID Linq™ is designed to make the configuration and updates of physical access systems simpler, faster, and more efficient by delivering on the concept of centralized management. Instead of treating each reader as an isolated unit, the platform connects readers deployed on-premises or accessed via the cloud. Even the largest reader fleets can be updated quickly and easily.

-
Traditionally, reader devices — the gatekeepers of physical access control systems — were set up at the factory, installed in the field, and managed individually as needed. However, growing numbers of readers, large and complex facilities, and the pace of technological change render this approach increasingly impractical. Facing security threats, staffing challenges, hybrid work, and demand for mobile access, security professionals need more efficient ways to keep readers up to date. That’s why HID launched HID Linq, a centralized reader management platform for HID Signo™* readers that simplifies and streamlines reader management and updates.
-
Centralizing reader management allows for a single point of control for multiple HID Signo* readers, simplifying deployment and maintenance and helping ensure configuration consistency across all devices. It also reduces physical intervention, which, in turn, saves valuable time and resources. Teams can simultaneously roll out firmware updates to all devices instead of manually updating each reader. And, as the trend toward mobile access grows, HID Linq provides a streamlined pathway to transition readers from cards to mobile.
-
HID Linq has applications for OEMs, security professionals, distributors, and integrators alike. For OEMs, HID Linq reduces the need to develop custom reader management software, enabling OEMs to focus on their core business. HID Linq makes it easy for security professionals to keep readers updated with new features, firmware, and security protections, reducing the time and effort required for reader management.
- *HID Global is a Returning ‘ASTORS’ Awards Champion, most recently a Double Platinum Winner in the 2020 ‘ASTORS’ program, and has been Recognized in Six AST Homeland Security Programs.
HIGH RISE ESCAPE Systems
Best Disaster Preparedness, Disaster Recovery System
-
Guardian Evacuation System
-
The Guardian Evacuation System developed a fixed and/or portable escape system to attach to a structure, designed to mitigate means of egress for anyone living or working above the 2nd floor, including government buildings, embassies, barracks, hospitals, air traffic control towers, apartments, condominiums, hotels, industrial and job sites, theme parks, cranes, oil platforms, ships and more.

-
High Rise Escape Systems (HRES) accomplished this in a combination of several simple, low-tech devices that require no power, are inexpensive, have a long shelf-life, and are easy to use.
-
Using a Controlled Descent Device (CDD), which works like a pulley, a user slides one of two permanently attached escape harnesses over them, exits off of a balcony/roof structure or out of a window, and the CDD slowly lowers them automatically at the rate of 3 feet per second.
-
As the first user descends, the opposite end of the cable automatically retracts and reloads the CDD with the remaining escape harness for the next evacuee.
-
Then, the process repeats. Everyone gets out.
-
The United States Military has been utilizing High Rise Escape Systems Guardian Escape Systems on Air Traffic Control Towers for years, which includes the Ellsworth AFB, Dyess AFB, Vandenburg AFB, Edwards AFB, Tinker AFB, Maxwell AFB, and Patrick AFB as well as Army and Air National Guard installations such as Alpena CRTC, Grayling Air Gunnery Range & Selfridge ANG.
(See the HRES device in action as designed for the Dyess AFB ACT Tower which is much safer than taking the stairs or the elevator. Courtesy of Dyess AFB & YouTube.)
-
*HRES has now been recognized as an ‘ASTORS’ Award Champion in its Seventh Consecutive Homeland Awards Programs, respectively.
HORNETSECURITY
 Best Phishing Defense Solutions
Best Phishing Defense Solutions
-
Security Awareness Service
-
Hornetsecurity’s next-gen Security Awareness Service trains employees using realistic spear phishing simulations and AI-powered e-training, heightening awareness of cyber security risks and threats.
-
Hornetsecurity provides a comprehensive solution that helps customers build a ‘human firewall’ as part of a sustainable security culture so employees learn effectively how to protect themselves and their company. The service is fully automated and easy to use.
-
The Awareness Engine is the technological heart of the Security Awareness product, offering bespoke, needs-based training: each user receives as much training as is necessary.
-
Security Awareness Service is a fully automated, easy-to-use, innovative solution because it is simple rather than maintenance-intensive.
(With advanced AI tools, it has become much easier for cybercriminals to carry out well-crafted social engineering campaigns like spear phishing or business email compromise. While essential, employee training can be a daunting task, learn how it can be done automatically as a continuous and effortless service – And that’s exactly what the Security Awareness Service is! Courtesy of Hornetsecurity and YouTube.)
-
Its Patented Spear Phishing Engine simulates sophisticated attacks to build knowledge of attacks. It uses the Employee Security Index (ESI®) as an industry-wide unique benchmark to measure progress, constantly measuring and comparing organizations’ and employees’ security behavior.
- *Hornetsecurity is a Returning ‘ASTORS’ Award Champion, recognized in their Third Consecutive Year.
HUMAN Security
 Best CNAPP (Cloud-Native Application
Best CNAPP (Cloud-Native Application
Protection Platforms) Solution
-
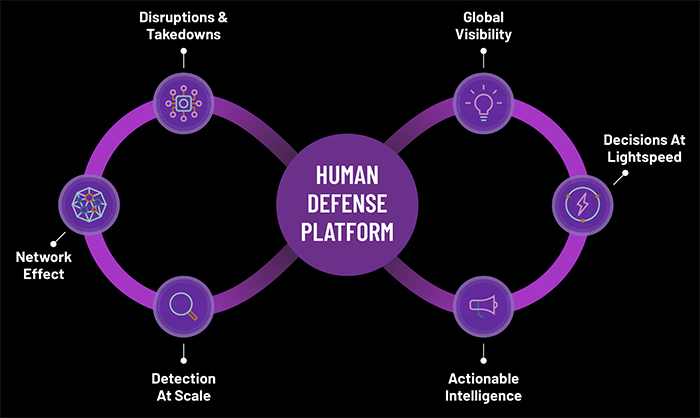
Human Defense Platform
-
The Human Defense Platform is a highly accurate, self-learning solution with real-time decision-making capabilities. It verifies the humanity of 20 trillion interactions per week and observes 3 billion devices monthly, providing visibility for unmatched collective protection.
-
The platform features a combination of over 200 machine-learning algorithms and 140 global machine-learning models that generate a constantly updated library of attack patterns based on interactions with applications, device fingerprinting, and network characteristics.
-
The Human Defense Platform unifies detection and prevention against digital attack surfaces for ad fraud, online fraud, data contamination, risk management, and compliance in a singular platform to safeguard government agencies.
-
HUMAN is an IT or security team extension and offers best-in-class service and responsiveness, fully tailored onboarding, and 24/7/365 security analyst oversight.
(Geoff Stupay, Vice President of Strategy at HUMAN discusses malvertising and the threats it poses for the digital ad ecosystem. Courtesy of HUMAN Security and YouTube.)
-
HUMAN’s Satori Threat Intelligence Team additionally offers data-driven, actionable, evidence-based guidance and context on investigations and bot attacks for customers (confidential) and security practitioners (public), and has led takedowns of several cybercriminal organizations with Google, the FBI, and others, including PARETO, 3ve and Methbot, that caused millions of dollars in damages.
IDENTIV
 Best Cyber Encryption Solution
Best Cyber Encryption Solution
-
uTrust FIDO2 NFC Security Keys
-
Identiv’s uTrust FIDO2 NFC Security Keys embody the epitome of robust cybersecurity in the context of homeland security.
-
With the rise in cyber threats targeting federal, state, and local government institutions, including educational systems, securing sensitive information has become a homeland security concern.
-
These hardware-based security keys offer unprecedented protection against phishing attacks, data breaches, and unauthorized access, making them ideal for educational institutions and a wide range of organizations that constitute the nation’s critical infrastructure.
(uTrust FIDO2 Security Keys are FIDO Alliance-certified. Their cryptographic security model eliminates the risk of phishing, password theft, and replay attacks. They work with everyday devices, including phones, tablets, laptops, and desktops, and across all services, like Facebook, Apple ID, Dropbox, Google, and Microsoft Azure. Courtesy of Identiv and YouTube.)
-
Identiv’s uTrust FIDO2 NFC Security Keys stand out with strong authentication, seamless integration, and a user-friendly experience for homeland security, critical infrastructure security, and identity verification with multi-device compatibility.
-
uTrust FIDO2 NFC Security Keys perfectly align with the nation’s focus on strengthening cybersecurity and meeting the multifaceted needs of homeland security.
- *Identiv is a Returning ‘ASTORS’ Award Champion, Recognized in its Sixth Year, 2021, 2020, 2019, 2018, and 2017, respectively.
INKAS® Aerospace and Defense (First of Two)
 Best Persistent Aerial Monitoring
Best Persistent Aerial Monitoring
for Tactical ISR Solution
-
Lance Heavy Hexacopter
-
The Lance Heavy Hexacopter tethered UAS System offers extended surveillance and overwatch missions thanks to unlimited flight time through a tethered system, ensuring continuous power while maintaining an impenetrable data connection.

-
An excellent choice for persistent surveillance missions on ground vehicles, sea vessels, and fixed sites, providing a comprehensive aerial perspective to enhance security measures, the Lance Heavy Hexacopter is a best-of-breed platform, ideal for multi-payload persistent surveillance missions.
-
The Lance Heavy Hexacopter tethered UAS system is the peak combination of versatility and security, boosting an unlimited flight time, an impenetrable data connection, and the ability to carry large payloads up to 13.2 lbs, perfect for extended surveillance and overwatch missions, carrying multiple payloads even in the harshest weather conditions.
INKAS® Armored Vehicle Manufacturing (Second of Two)
 Best Mobile Surveillance ISR Solution
Best Mobile Surveillance ISR Solution
-
Hudson Recon Tactical Reconnaissance
& Surveillance Armored Vehicle -
The Hudson Recon is a drone-carrying tactical armored vehicle designed to provide superior data-gathering capabilities combined with protection and versatility in the field.

-
Its versatility and advanced features make it an essential asset for military and law enforcement operations, offering exceptional adaptability in the field, combined with protection – the INKAS® Hudson Recon comes standard with CEN 1063 B6 armor, able to withstand shots from a variety of weapons, as well as protection against explosion, yet remains light and highly maneuverable.
-
With an easily transformable command and control center, the INKAS® Hudson Recon can quickly convert into an armored personnel carrier and a medevac vehicle, making it an essential asset for military and law enforcement operations, border patrol, counter-terrorism reconnaissance, and surveillance operations.
(The Hudson Recon, designed for agencies like law enforcement and border patrol, combines the reliability of the Toyota Land Cruiser 79 platform with advanced features. It’s powered by a turbocharged 4.5L V8 diesel engine, offering both left-hand and right-hand drive configurations. Key features include easy maneuverability, an auxiliary air conditioning system for hot climates, and lightweight yet strong armor. The vehicle’s versatility extends to its use as a command center or armored personnel carrier, ensuring operational efficiency and comfort, making it ideal for large fleets and diverse terrain use. Courtesy of Inkas Armored and YouTube.)
-
The INKAS® Group of companies, with its Armored Vehicle Manufacturing and Aerospace & Defense divisions, is recognized as a prominent global authority providing best-of-breed security and defense solutions, earning the trust of governments and organizations, including the US Department of Defense, the Canadian Armed Forces, the United Nations, and numerous international armed and police forces.
-
INKAS® was also Recognized with Multiple ‘ASTORS’ Awards in the 2022 ‘ASTORS’ Awards Program.
INTEGRA Services (First of Two)
 Best Student Threat Assessment Training Solution, and…
Best Student Threat Assessment Training Solution, and…
2023 New Product of the Year
-
Integra Services Student Threat Assessment Process
-
An effective Threat Vulnerability and Risk Assessment (TVRA) is the first step in developing a valuable facility security program, as adequate security starts with a clear understanding of your vulnerabilities.
-
Integra Services can help you gauge your strengths and weaknesses in various scenarios and give your organization the roadmap to enhance your security and ensure that a physical security program is designed to combat those risks.
-
A TVRA is a comprehensive review of the security profile of your physical plant. To accomplish this, their experienced assessors conduct on-site visits to your facility(s) where all emergency policies, plans, equipment, staff training, and layout of the buildings are evaluated for safety and security risks to identify gaps in your security.
(Hear from John Spalthoff about the success his Spring Lake Heights High School staff had with the Threat Vulnerability & Risk Assessment (TVRA) performed by Integra Services. Courtesy of Integra Services and YouTube.)
-
Integra conducts interviews with staff, including the facility administrators/grounds team/facilities officials/employees, and security team, to understand your security profile from every point of view and create the best possible security framework for your organization.
-
Once the assessment is complete, each building receives a written report on all findings and a “Road Map” to mitigate any weaknesses. Also included is a meeting with stakeholders and staff to review findings and recommendations.
-
Using the information from the TVRA and Road Map, the organization can close the security gaps found and do so in a fiscally sound manner.
INTEGRA Services (Second of Two)
 Best Preventative School Security Solution
Best Preventative School Security Solution
-
Integra Services Student Threat Assessment Process
-
A critical need for school safety today is to empower school personnel, SROs, and security personnel to recognize the signs of potential violence exhibited by a student so they can intervene before the violence erupts. This process can save lives.
-
Integra Services, formerly True Security Design, has been Recognized for Multiple ‘ASTORS’ Public Safety for its various threat assessment processes and staff training programs for healthcare, corporate, educational, and government facilities.
(Integra Services’ School Training teaches today’s modern professionals vital skills through courses designed to engage and empower its participants. The goal is to transform security training from the tiresome requirement it has too often become into engaging and productive learning through interactive sessions and real-life role-playing exercises. Courtesy of Integra Services and YouTube.)
-
Integra Services Student-Based Threat Assessment Training helps school personnel develop an in-school team that can respond to any threat, analyze the suspected threat, identify a potentially dangerous person, and take action before an attack occurs.
-
The Student-Based Threat Assessment Program from Integra Services (formerly True Security Design) is the next step in training to ensure the various components of our nation’s educational personnel are equipped to do everything possible to prevent violence before it happens and not just respond to it afterward.
INTELLICENE
Best Unified Intelligence-Driven Security Solution
-
Symphia 8.0 Risk Management & Security Portfolio
-
Symphia is an integrated, intelligence-driven portfolio of security solutions that work in concert to deliver actionable insights for deeper situational awareness, greater command and control, as well as more effective incident management, response, and investigations.
-
Symphia 8.0 incorporates state-of-the-art threat intelligence mechanisms, enabling organizations to effectively detect, analyze, and respond to physical threats.
(Featuring Symphia Intelliview, Intellicene’s unified video gives you much greater visibility across all connected devices and cameras, including any 3rd-party VMS or access control. Greg Skarvelis, Intellicene’s Chief Solution Architect, provides a quick demonstration of the power of orchestrated security operations and shows how Symphia 8.0 opens the door to the Age of Intelligence, enabling you to leverage real-time insight for much quicker and more decisive action that saves lives. Courtesy of Incellicene and YouTube.)
-
A unified security management solution showcasing advanced capabilities and features to bolster cybersecurity efforts, Symphia is an open, scalable, and adaptive approach to video-centric security unlike any other.
-
With seamless integration and user-friendly functionality, the Symphia 8.0 Platform from Intellicene was designed to streamline security operations, enhance threat detection, and empower security teams to mitigate evolving threats.
INTELLIGENT WAVES
Best Secure Network Communication Solution
-
GRAYPATH Next-Generation
Cyber-Defense Solution
-
GRAYPATH (GP) is an award-winning, next-generation of expeditionary communications.
-
Through its patented IP Spread Spectrum technology, GP leverages the cloud to randomize and distribute message packets by using multiple transport paths and encrypted channels.
-
GP algorithms optimize throughput by continuously sensing and adjusting the message flow according to channel availability and bandwidth capacity, creating a smoother connection even for HD video transmissions. GP dramatically lowers the risk of detection and interception and is nearly impervious to disruption.
-
GRAYPATH provides a flexible and secure SD-WAN fabric mesh across both trusted, government-managed connections in the Ubiquitous Black Fabric (UBF) and public commercial connections by creating an equally secure “LAN over commercial WAN” fabric to establish the Ubiquitous Hidden Core (UHC).
(Learn how GRAYPATH uses innovative bandwidth aggregation over any quantity of public and private connectivity services to provide full SD-WAN functionality even over very low bandwidth and denied degraded, intermittent, and latent (DDIL) connections. Courtesy of Intelligent Waves and Vimeo.)
-
GRAYPATH’S architecture enables agencies to securely utilize one Gateway to manage multiple and differing classified enclaves, each having its separate LANs, firewalls, and encryption devices, which improves the manageability of network traffic and reduces cost by eliminating the need for each classified enclave to have its dedicated network circuits for connectivity.
-
*Intelligent Waves is a Returning ‘ASTORS’ Awards Champion, having secured Wins in the 2022 and 2021 ‘ASTORS’ Awards Programs.
IPVIDEO Corporation (First and Second of Four)
Best Alert Notification Solution, and…
2023 New Product of the Year

-
Sentry ERS is a revolutionary lockdown and emergency response system purposely built with schools and campus environments in mind.
-
With a single button push, Sentry ERS initiates lockdown protocols and sends immediate alerts to police for superior incident awareness with live video, voice, text, and GPS location data from areas where traditional video cameras cannot be deployed.
-
Emergency alerts can also be triggered by gunshot detection, panic buttons, aggression detection, and spoken keywords.
-
Sentry ERS offers complete privacy without video, audio, or text transmission until activated and includes a drill mode for practice use.
IPVIDEO Corporation (Third of Four)
 Best Incident Response Solution
Best Incident Response Solution
-
Sentry ERS Lockdown &
Emergency Response System -
With the simple push of the lockdown button on the Sentry ERS base unit, an entire school lockdown protocol is initiated (Door’s lock, PA announcements, strobe lights are activated throughout the facility and on units, audible lockdown messages are played from the unit, location beacons are provided, police dispatch is notified, push notifications are sent to security/administration/ community, etc.) and live audio and video communications are automatically established with first responders to assess and address the critical situation.
(See why SentryERS is such an effective way to protect children, staff, and first responders from death and injury during active shooter and other incidents. Courtesy of IPVideo Corporation and YouTube.)
-
Sensors and patented gunshot detection algorithms have been added to Sentry ERS base units to provide automatic alerting of an active shooter in the event the lockdown button cannot be reached or pushed in a particular location.
IPVIDEO Corporation (Fourth of Four)
 Best Mass Notification Solution – Application
Best Mass Notification Solution – Application
-
Sentry ERS Lockdown &
Emergency Response System -
The SENTRY ERS lockdown and emergency response system also comes with a dedicated mobile smartphone for those in distress to broadcast a secondary video stream and communicate with first responders live, providing all the latest real-time information at the scene.
-
Integrated with IPVideo’s iPanic system, Sentry ERS provides easy-to-use single-button push panic cards that will be recognized by any unit within range and trigger established protocols, including notification of 911 for Alyssa’s law.
(See how the Sentry ERS Lockdown & Emergency Response System is one of three award-winning solutions IPVideo Corporation has introduced to address the active shooter threat. Courtesy of IPVideo Corporation and YouTube.)
-
*Recognized as a Multiple ‘ASTORS’ Awards Champion for Six Consecutive Years in the ‘ASTORS’ Awards Programs, AST is delighted *IPVideo Corporation Returned for the Third Year as a Premier Awards Sponsor in the 2023 ‘ASTORS’ Awards.
IRIS ID Systems
 Best Facial/IRIS Recognition Solution
Best Facial/IRIS Recognition Solution
-
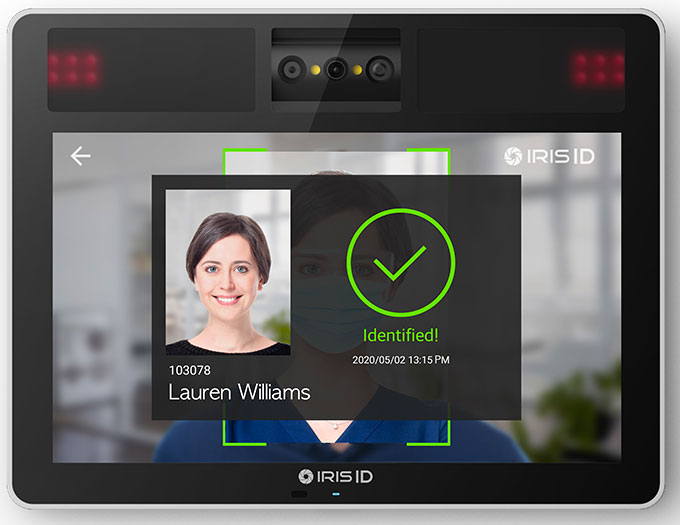
IrisTime™ iT100
-
The IrisTime™ iT100 is a non-contact AI-enabled biometric offering featuring iris and facial recognition technology fused in a small but powerful package.
-
A large capture volume allows for increased flexibility, speed, and convenience, and the IrisTime™ iT100 provides enhanced security so enterprises can fully utilize the device for their customized needs in time, attendance, and access control.
-
IrisTime™ iT100 provides consistent accuracy and offers multiple authentication modes, including iris, face, iris or face, and iris/face fusion for even more ease of use and stronger identification.
-
Even for solutions where biometrics may be an option, the customize authentication mode for each individual can allow certain individuals to use a card or pin only for true flexibility.
The use of biometrics for authentication and security is growing, and Iris ID solutions offer automated, multimodal, multifactor authentication, which can help comply with various state regulations.
(Meet the IrisTime™ iT100, designed so custom applications can connect to enterprise HR data as an interactive tool for employees to access their information on 401K status, vacation time left, overtime, and much more. Courtesy of Iris ID Systems and YouTube.)
-
The IrisTime iTMS Cloud is a complementary solution that cannot be spoofed, and when paired with the IrisTime iT100 Time Clock, it provides users with a superior iris and face fusion solution for capturing employee data.
-
*Iris ID is a Returning ‘ASTORS’ Awards Champion, for their Seventh Consecutive Year.
KEEPER Security (First of Three)
 Best Cyber Security Solution
Best Cyber Security Solution
-
Keeper Security Government Cloud (KSGC)
-
Keeper Security is a secure, certified, tested, and audited password security platform with an award-winning customer experience and holds the industry’s longest-standing SOC 2 and ISO 27001 certifications.

-
Keeper Security Government Cloud (KSGC) is GDPR compliant, CCPA compliant, FedRAMP authorized, StateRAMP Authorized, and is certified by TrustArc for online privacy, using Elliptic Curve Cryptography, which is considered by the InfoSec community to be the most secure level of encryption for information security.
KEEPER Security (Second of Three)
 Best Cyber Encryption Solution
Best Cyber Encryption Solution
-
Keeper Security Government Cloud (KSGC)
-
Keeper’s Enterprise Password Manager is the only solution that uses Elliptic Curve Cryptography (ECC) in its encryption. Considered by the InfoSec community to be the most secure level of encryption for information security, ECC provides many advantages, including Best-in-Class Security, Efficiency, and Fast Computation.
-
Keeper’s encryption model documentation compares the strength of 256-bit elliptic curves against vaults encrypted with password-derived keys, and its model guarantees that all your essential information, like logins, files, and payment details, are secured, allowing you to focus on what matters most without worrying about cyber threats.

-
Keeper’s encryption process is designed with user convenience in mind. It automatically generates strong encryption keys on your device, ensuring privacy and enabling the seamless sharing of records and folders when necessary.
-
No matter how you access your account, whether through single sign-on, passwordless technology, or a master password, Keeper provides an extra layer of security tailored to your needs. Widely adopted by government agencies and public sector organizations, Keeper’s cutting-edge encryption technology offers unparalleled security and ease of use.
KEEPER Security (Third of Three)
 Best Privileged Access Security Solution
Best Privileged Access Security Solution
-
Keeper Security Government Cloud (KSGC)
-
Keeper automatically generates strong encryption keys on your device, ensuring privacy and seamless sharing of records and folders, regardless of how you access your account.
-
Widely adopted by government agencies and public sector organizations, Keeper’s innovative encryption technology offers unparalleled security and ease of use.
(When you switch between devices all day, you need a password manager to move with you. The Apple Circle team explains why they trust Keeper to secure their passwords and information. Courtesy of Keeper Security and YouTube.)
-
Keeper Security Government Cloud (KSGC) protects against ransomware and cyber threats with zero-trust cybersecurity.
-
Keeper Security Government Cloud Password Manager and Privileged Access Manager are FedRAMP Authorized and available in the AWS GovCloud.
KONICA MINOLTA Business Solutions (First of Two)
 Best IT Access Control & Authentication Solution
Best IT Access Control & Authentication Solution
-
Advanced Authentication Manager (AAM)
-
Security is at the forefront for many clients, and the ability to prevent unauthorized access to secure documents held in print management applications has increased due to duplicate IC card authentications.

-
When this occurs, a user swipes their Integrated Circuit (IC) card at a Multi-Function Printer (MFP) and logs in as a different user, allowing them unauthorized access to secure documents, resulting in a security breach.
-
Advanced Authentication Manager (AAM) provides authentication solutions that utilize user biometric identification rather than the standard passwords or IC cards for print management applications running on Konica Minolta Bizhub devices. No biometric data is stored in the fingerprint reader, on the MFP, or within the AAM server.
KONICA MINOLTA Business Solutions (Second of Two)
 Best Biometric Reader Solution
Best Biometric Reader Solution
-
Advanced Authentication Manager (AAM)
-
Konica’s Advanced Authentication Manager (AAM) provides functions such as device and user management required to maintain security.
-
This functionality is supported for customers requesting both fingerprint and standard IC cards on the same MFP and can be used as a transition phase.
-
According to the Society for Human Resource Management (SHRM) 2022 study, “The Future of Biometrics in the Workplace,” 60 percent of consumers feel they have too many passwords to remember, and 41 percent admit to using the same password or simple variations of a single password – and poor password hygiene is responsible for as many as 81 percent of company data breaches.
(Due to duplicate IC card authentication and password sharing, the need to prevent unauthorized access to secure documents held in print management applications has increased. Advanced Authentication Manager provides authentication solutions that utilize user biometric identification rather than the standard passwords or IC cards for print management applications running on Konica Minolta Bizhub devices. Courtesy of KonicaMinoltaUS and YouTube.)
-
Konica’s Advanced Authentication Manager also provides device and user management functions required to maintain security.
-
*Konica Minolta Business Solutions has now been Recognized as an ‘ASTORS’ Awards Champion for its Seventh Consecutive Year in the Annual ‘Homeland Security Awards Program.
LIBERTY DEFENSE
 Best Metal/Weapons Detection Solution
Best Metal/Weapons Detection Solution
-
HEXWAVE Concealed Weapon Body Scanner
-
Using active millimeter wave, video-rate 3D imaging, and AI to detect all types of concealed metallic and non-metallic weapons and other prohibited items, HEXWAVE allows for rapid, automated people screening using a high throughput, contactless, walkthrough portal.
(See a quick overview of Liberty Defense’s HEXWAVE system, which uses millimeter wave, advanced 3D imaging, and AI to detect concealed metallic and non-metallic weapons and other prohibited items such as 3D printed ghost guns and plastic, liquid, and powder explosives – threats that evade today’s metal detectors. The system allows rapid, automated screening using a high throughput, contactless, walkthrough portal. HEXWAVE is safe for public use and maintains privacy. Courtesy of Liberty Defense and YouTube.)
-
The HEXWAVE high throughput, contactless walkthrough portal is non-intrusive, protects the privacy and modesty of those being scanned, and can process people seamlessly in all types of indoor and outdoor venues.
-
No images are stored and are not accessible by the security operator, who sees only HEXWAVE’s Go/No-go screen that provides a clear and visible alert.
-
*Liberty Defense is a Returning ‘ASTORS’ Awards Champion, having secured Wins in the 2022 and 2019 AST Homeland Security Awards Programs.
MARK43
 Best Disaster Preparedness and
Best Disaster Preparedness and
Disaster Recovery Solution
-
Alternate CAD
-
Mark43 Alternate CAD is designed to serve as the backup to a community’s primary CAD, providing the modern technology needed to keep every public safety agency operating and constantly connected.
-
The public safety industry faces heightened pressures and evolving threats, especially when natural disasters and cyberattacks strike. System outages put technology and data at risk, and siloed platforms leave agencies stranded amidst outages and breaches.
-
Mark43’s Alternate CAD provides the solution to ensuring resiliency, sustaining operations, accessing appropriate resources, and collaborating across all necessary channels as these disastrous events transpire.
-
Mark43 offers a resilient, user-friendly cloud-native platform, allowing public safety agencies to continue operating without interruption during natural disasters and other emergencies impacting the city, state, or region.
(Nashville’s 911 center deployed Mark43 Alternate CAD two years after the Christmas Day bombing. “Currently, when the CAD goes down at the center, the backup is a sheet of paper. Dispatchers must record each call by hand, at times logging 100 calls an hour. Now, if it goes down, the Mark43 system will kick in.” Courtesy of Mark43, WSMV and YouTube.)
-
Innovative, reliable, and best-in-class technology is vital so that first responders can keep working when their community needs them the most (when the primary CAD systems have gone down.)
-
When the primary CAD is impacted by extreme weather or a critical incident, having the Mark43 Alternate CAD in place will ensure there aren’t interruptions to potentially lifesaving response.
- *Mark43 is a Returning ‘ASTORS’ Award Champion for their Fourth Consecutive year.
MIMECAST (First of Two)
 Best Email Security Solution
Best Email Security Solution
-
Mimecast Email Security Platform
-
80% of companies increased their email usage over the last 12 months, and 75% saw an increase in email-based threats. Since email is the front door to an organization, and 91% of attacks start with email, having a comprehensive email security solution is business critical.
-
Email Security Cloud Gateway is ideal for organizations that need to manage more complex email environments, including the need for customizable policies and granular controls. Email Security Cloud Integrated, is a brand new, gateway-less solution and can be deployed in minutes providing rapid time to value.
-
Both solutions are backed by Mimecast’s 20 years of experience and the processing of 1.3 billion daily emails. Guided by a customer-centric operational framework, Mimecast allows organizations to seamlessly integrate with native cloud email providers and access in a singular platform, streamlining security processes.
(Deploy world-class email security in minutes to protect your employees from all email-based threats with Integrated Cloud Email Security from Mimecast. Getting real-time threat intelligence and instant remediation makes securing your organization easier than ever. Courtesy of Mimecast and YouTube.)
-
Not having email protection is not a cyber risk; it’s a business risk. Trusted by 40,000 organizations, Mimecast Email Security provides organizations with AI-powered, best-in-class protection. Offering two deployment options, Mimecast enables the flexibility and scalability needed to service organizations of all sizes.
MIMECAST (Second of Two)
 Best Phishing Defense Solution
Best Phishing Defense Solution
-
Mimecast X1 Platform
-
Email is the front door through which nearly all vital business communication flows — and the threat vector through which virtually all cyberattacks begin.

-
The Mimecast X1 Platform powers the Mimecast product suite, transforming email and collaboration security into the eyes and ears of 40,000 organizations worldwide, empowering them to mitigate risk and simplify complexities across a threat landscape driven by malicious cyberattacks, human error, and technology fallibility.
-
Mimecast X1 Platform was designed to protect organizations and the people they serve holistically. Through its Mimecast Email Security, DMARC Analyzer, Awareness Training, and CyberGraph, Mimecast powers businesses with a fully integrated service that delivers industry-leading protection for communications, people, and data by making information actionable and providing the reliability, resilience, and scale that the modern threat landscape demands.
-
*Mimecast was also Recognized in the 2022 ‘ASTORS’ Awards Program.
(To be continued… see below)
The 2023 ‘ASTORS’ Awards Program was Proudly Sponsored by Platinum Event Sponsor: NEC National Security Systems (NSS)
And Our RETURNING Premier Sponsors:
ATI Systems, Automatic Systems of America,
Guard Dog AI, IPVideo Corporation, Rajant Corporation, RX Global, SIMS Software, and American Security Today!
View Part 1 Winners A – GL NEXT View Part 3 Winners N – Z
Part 4 Government Excellence Part 5 Innovation & Leadership
- **IN A RARE TIE Event – a tie results from extremely differing objectives and/or similar technological applications.






















