Gurucul Cybersecurity & Fraud Analytics Hit Record Growth in 2018
Gurucul, a leader in behavior based security and fraud analytics technology, and a Winner in the 2018 ‘ASTORS’ Homeland Security Awards Program, achieved record business results in 2018 which includes a 200% increase...
What Are the Most Secure VPN Proto-cols & Why? (Learn More, See Video)
By Howard Dawson, Writer & Tech Enthusiast
Virtual Private Networks (VPN) are vital applications for those who want to keep their Web browsing data private.
They allow for safe surfing of the internet and to...
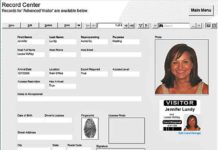
X-Force Red Finds Security Threats in Visitor Management System Kiosks
March 4, 2018 – In Breaking News – WIRED
DANIEL CROWLEY HAS a long list of software platforms, computers, and internet-of-things devices that he suspects he could hack.
As research director of IBM’s offensive security group...
How Can Federal Agencies Secure Data Services in the Cloud
By Gerry Gebel, VP of Business Development at Axiomatics
As businesses continue their mass migration of data, applications, workflows and other business assets to the cloud, federal agencies are following suit, and...
The FBI: At the Heart of Combating Cyberthreats (See Video Interview)
By the FBI
With cyber threats to the United States and across globe reaching unprecedented levels, the FBI uses a full spectrum of expertise, technology, and partnerships to root out cyber criminals,...
Encryption Is Key in the World of BYOD USB Flash Drives
Guest Editorial by Richard Kanadjian, Encrypted USB Business Manager at Kingston Technology
Today, government entities are filling their workplace environments with all sorts of interesting, novel perks in an attempt to keep staff...
ASC Sounds Alarm of Relying Exclusively on Mobile Device Alerts
American Signal Corporation (ASC), a Milwaukee-based company that develops a variety of sirens and emergency alert systems, and Two-Time Winner in the 2018 'ASTORS' Homeland Security Awards Program, is sounding the alarm...
The Cognitive Science Behind Cybersecurity
Guest Editorial by Margaret Cunningham, Principal Research Scientist, Forcepoint
Artificial intelligence, cognitive computing, and machine learning are among the most discussed technologies in the cybersecurity realm, but what do these solutions really...
SolarWinds Access Rights or Access Risks? In 2019 ‘ASTORS’ Awards
Webcast: Access Rights or Access Risks?
Date: Tuesday, April 30, 2019
Time: 11 am - 12 pm CT
Access rights management is often viewed as a “nice-to-have” solution within IT security...
SIEM, UEBA, and SOAR – What’s the Difference?
By Limor Wainstein
The term ‘Information Security’ refers to the protection of the information environment in its entirety.
Data is not the only aspect that needs to be secured, but the defensive system...