How SASE Adoption Today – Can Resolve Tomorrow’s Threats
Guest Editorial by Ben Smith, CTO, Netwitness
Cyberattacks and cyber warfare have only worsened as geopolitical tensions rise and digital proxy battles rage.
But while these threats have remained ubiquitous for more...
Rajant Sparrow for Heavy-Duty & Light-Duty Vehicle Applications
RAJANT Corporation, the pioneer of Kinetic Mesh® wireless networks, and Multi-Award Winner in the 2022 ‘ASTORS’ Homeland Security Awards Competition, recently Nominated in the 2023 'ASTORS' Program, debuted its new Sparrow BreadCrumb® on...
Fūsus Competes in Fourth ‘ASTORS’ Homeland Security Awards
Fūsus, the company that took Platinum in the 2022 'ASTORS' Homeland Security Awards Program for Best Investigation/ Surveillance/Detection Solution, is pleased to announce its Real-Time Crime Center in the Cloud (RTC3)...
BackBox Launches Cisco CIS Benchmark Automation Templates
BackBox, a market leader in network automation, security, and management solutions that took Platinum for Best Network Automation Solution in the 2022 'ASTORS' Homeland Security Awards Program, is pleased to announce it...
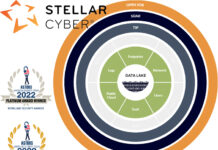
Stellar Open XDR Nominated for Two 2023 ‘ASTORS’ Cybersecurity Awards
In most situations, Network Detection & Response (NDR) tools alone are not enough to provide comprehensive security. The analysts must also be able to see logs, real-time traffic, and user behaviors...
Establishing a Legacy of Wins in the Annual ‘ASTORS’ Awards Program
American Security Today’s Annual ‘ASTORS’ Awards, the preeminent U.S. Homeland Security Awards Program, now in its Eighth Year, recognizes industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management...
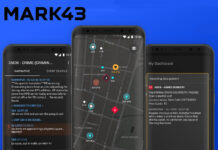
Mobility is a Necessity in Today’s Public Safety Software Environment
Guest Editorial by Matt Polega, Cofounder and Head of External Affairs at Mark43
In 2023, community members expect their local first responders to have the same mobile, modern technology that civilians use...
Chinese Researchers Say They Broke RSA Encryption. Will That Affect You?
Guest editorial by Petko Soyanov, Global CTO of Forcepoint
Late last year, Chinese researchers claimed to use quantum computing to break an RSA public-key encryption algorithm.
While many quantum experts expressed skepticism, the...
How to Protect Yourself From Increasingly Sneaky Hacking Tactics
Guest Editorial by Dr. Brian Gant, Assistant Professor of Cybersecurity at Maryville University
It turns out that an effective way for hackers to infiltrate networks is not by targeting those networks directly...
Intelligent Waves’ Returns to Compete in Third Consecutive ‘ASTORS’
Intelligent Waves, a leading tech integrator that delivers mission-focused multi-domain operational expertise and innovation to the Government through high-impact technology solutions, is pleased to announce its GRAYPATH Next-Generation Cyber-Defense Solution has been...