
American Security Today’s Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program, and now in its Sixth Year, continues to recognize industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management and Response, Law Enforcement, First Responders, as well as federal, state and municipal government agencies in the acknowledgment of their outstanding efforts to Keep our Nation Secure.

An exclusive event featured on the opening day of ISC East, the Northeast’s largest security industry event, and the inaugural Natural Disaster and Emergency Management (NDEM) Expo, two hundred representatives of law enforcement, public safety, and top industry leaders came together to honor the selfless service of those who stand on the front lines, and those who stand beside them – providing the capabilities and technologies to create a safer world for generations to come.

AST Honors Thomas Richardson, FDNY Chief of Department; Dr. Kathleen Kiernan, President of NEC National Security Systems; and Richard Blatus, FDNY Assistant Chief of Operations, at the 2021 ‘ASTORS’ Awards Luncheon at ISC East.
The United States was forever changed 20 years ago on September 11th, and we were fortunate to have many of those who responded to those horrific tragedies join us at the 2021 ‘ASTORS’ Awards Luncheon.
In the days that followed 9/11, the critical needs of protecting our country catapulted us into new and innovative ways to secure our homeland – which is how many of the agencies and enterprise organizations that are today ‘ASTORS’ Awards Champions, came into being.
This year marks the 20th anniversary of Homeland Security as we know it today, including the 20th anniversary of the Transportation Security Administration (TSA), who gathered with us to celebrate new ways of thinking about responsibility, new legislation, and comprehensive collaborations between private and public sectors that have led to developing intelligence and technologies which serve to protect our nation.

We were delighted to welcome representatives of the TSA and Federal Air Marshals Service (FAMS), which included the Assistant Administrator for Strategic Communications & Public Affairs; the Deputy Branch Manager of Aviation Programs Branch, the Assistant Federal Security Director of Screening, an Explosive Detection Canine Handler and K9 Warren, the Federal Security Director, a Supervisory Transportation Security Officer, and a Transportation Security Inspector in addition to members of the Office of the Administrator.

We were also pleased to have join us Chief of Department FDNY Thomas Richardson, Assistant Chief of Operations FDNY Richard Blatus, Doug Farber, National Board Member at InfraGard National (INMA); Assistant Chief Jeffrey Carroll of the Washington DC Metropolitan Police Department, Captain James Albrecht of the NYPD (Ret), U.S. Marshal Derrick Driscoll (Ret); Patrick Burke, the executive director of the Washington DC Police Foundation and former Assistant Chief of the MPDC; Jeff Wohler, Chief Executive Officer at San Diego Harbor Police Foundation, and representatives of the Naval Postgraduate School Center for Homeland Defense and Security, to name a few.

Our keynote speaker featured a moving and informative address from TSA Administrator and Vice-Admiral of the United States Coast Guard (Ret), David Pekoske; to our attendees who traveled from across the United States and abroad, on the strategic priorities of the 64,000 member TSA workforce in securing the transportation system, enabling safe, and in many cases, contactless travel.
Administrator Pekoske addressed the topics of ensuring smooth and timely holiday season traveling, COVID-19 mandatory vaccinations, how the TSA is addressing increasing inflight passenger disturbances, which include a ‘Crew Member Self Defense Training Program’ initiated and developed by the Federal Air Marshal Service, and new regulations imposed upon those travelers who become combative during flights.
Administrator Pekoske also educated attendees as to the overall critical missions of the TSA, and innovative new approaches his administration has undertaken since taking office.
(See an ‘American Security Today Exclusive Interview’ with TSA Administrator David Pekoske facilitated by Dr. Kathleen Kiernan, President of NEC National Security Systems at the 2020 ‘ASTORS’ Awards Presentation Luncheon in New York City on November 17, 2021. Courtesy of My Pristine Images, and Vimeo.)
Additionally, Legendary Police Commissioner William Bratton of the New York Police Department, the Boston Police Department, and former Chief of the Los Angeles Police Department, was also live at the event, meeting with attendees and signing copies of his latest work ‘The Profession: A Memoir of Community, Race, and the Arc of Policing in America,’ courtesy of the generosity of our 2021 ‘ASTORS’ Awards Premier Sponsors AMAROK, ATI Systems, Attivo Networks, Automatic Systems of America, Fortior Solutions, Reed Expositions, and SIMS Software.

At the conclusion of the luncheon, both Administrator Pekoske and Commissioner Bratton graciously spent time with attendees discussing their most critical concerns of the day and posing for photographs with their peers, old friends, and event sponsors and guests.
The prestigious Annual ‘ASTORS’ Homeland Security Awards Program highlights the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition and keep our Nation safe – one facility, street, and city at a time.

The program is specifically designed to honor distinguished government and vendor solutions that deliver enhanced value, benefit, and intelligence to end-users in a variety of government, homeland security, enterprise, and public safety vertical markets.
‘ASTORS’ nominations are evaluated on their technical innovation, interoperability, specific impact within the category, their overall impact to the industry, relatability to other industry technologies, and application feasibility outside of the industry,” said AST’s Publisher, Michael J. Madsen.
‘ASTORS’ Awards Winners are selected by our American Security Today Expert Panel of Judges, and the ‘ASTORS’ Homeland Security Awards are presented at the Platinum, Gold, Silver, and Bronze levels.
(See just a few highlights of American Security Today’s 2021 ‘ASTORS’ Awards Presentation Luncheon at ISC East. Courtesy of My Pristine Images and Vimeo.)
The vast majority of ‘ASTORS’ Award Winners return to compete in American Security Today’s Annual Homeland Security Awards Program each year to build upon their legacy of achievement, and we’ve been fortunate that our ‘ASTORS’ Awards Premier Sponsors return year to year to reap the benefits of their participation in the industry’s largest and most comprehensive Annual Awards Program.
American Security Today would like to express our deepest gratitude for the generosity of our New and Returning ‘ASTORS’ Awards Premier Sponsors for their continued support, and assistance in ensuring that our program continues to grow and to delight attendees at our Annual ‘ASTORS’ Awards Presentation Luncheon.
The 2021 ‘ASTORS’ Awards Program was Proudly Sponsored by AMAROK, Fortior Solutions, and SIMS Software, along with Returning Premier Sponsors ATI Systems, Attivo Networks, Automatic Systems, and Reed Exhibitions.
And without further ado, American Security Today is Proud to Introduce the 2021 ‘ASTORS’ Homeland Security Awards Winners.
2021 ‘ASTORS’ Homeland Security Award Winners in Industry Are…
908 Devices
 Best CBRNE Detection System
Best CBRNE Detection System
-
MX908
-
New to the Annual ‘ASTORS’ Awards Program, the MX908 is a multi-mission handheld mass spectrometer for Chemical/Biological/Radiation/Nuclear/Explosive detection which can identify compounds at trace levels with a high level of sensitivity and selectivity, to provide elite responders conducting chemical, explosive, priority drug, and HazMat operations actionable intelligence fast.
-
The MX908 accurately discriminates priority threats from the broad range of interferents that lead to false alarms with other technologies.
-
The recently introduced MX908 Aerosol Module for military and civilian responders with Bluetooth further expands the capabilities of the field-deployable MX908 to detect and identify aerosolized and vaporized chemical threats, including chemical warfare agents, fourth-generation agents, pharmaceutical-based agents, and more.
(Learn More about how this first-of-its-Kind Aero Module Detects Aerosolized Chemical Threats; New Targets Added Including Cathinones and Cannabinoids; New MX908 Mobile App Provides Responders Rapid Access & Data Sharing. Courtesy of 908 Devices and Vimeo.)
Acoustic Technology Inc. (ATI Systems)
Best Mass Notification System – Hardware
-
Mobile Solutions for Giant Voice
-
When an emergency strikes, effective dissemination of information in a timely manner can be critical, and emergency communications for disasters require rapid deployment of Giant Voice (GV) systems.

-
ATI Systems, a world-leading provider of reliable emergency warning & mass notification systems (MNS), offers excellent Giant Voice Solutions for Military, Community, and Campus clients with the essential tools for emergency planning and preparedness, which includes their Mobile High Powered Speaker Station (HPSS) which is Rapidly Deployable on an Outdoor Siren Trailer, their Transportable High Powered Speaker Station (THPSS), and their Deployable High Powered Speaker Stations (DHPSS).
-
Through acoustic design and modeling, the company provides optimal sound coverage and superior voice intelligibility for both outdoor and indoor areas to ensure the safety of our clients worldwide.

*ATI Systems is also a Returning Premier Sponsor for the Fifth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a 2020, 2019, 2018 and 2017 ‘ASTORS’ Platinum Award Winner.
Actuate AI
 Best Video Analytics Solution (Tie**)
Best Video Analytics Solution (Tie**)
-
Actuate AI Software
-
Actuate’s cloud-based AI software, turns any existing security camera into a intruder- and threat-detecting smart camera with no additional hardware required.
-
The software identifies safety and security threats in real-time and issues automatic alerts to dramatically reduce the time it takes for security teams and law enforcement to respond.
- When an emergency strikes, effective dissemination of information in a timely manner can be critical.
(See how Actuate builds Gun Detection AI that Reacts Before Shots are Fired, to turn your existing security cameras into threat-detecting smart cameras with 99%+ accuracy. No servers required. Courtesy of Actuate AI and YouTube.)
Advanced Detection Technology
Best Under Vehicle Surveillance System
-
LowCam® VI100 Under Vehicle Inspection System (UVIS)
-
Every day poses a new security challenge, whether that’s protecting a nation’s borders, facilities, monuments, airports, or its people, so to help minimize these threats, Advanced Detection Technology has introduced the first-ever, battery-powered UVIS for use during ad hoc situations.

-
The LowCam® VI100 “No Strings Attached” UVIS – touting no cables and no cords, not to mention a self-contained battery and military-grade equipment – lets you take this level of improvised security with you for anywhere event security management.
-
Portable, affordable, and all-inclusive, LowCam VI100 provides well-defined, ultra-high-definition, and side-to-side daylight views, wirelessly displayed on a tablet with 15X zoom capabilities.
(Meet the LowCam® VI100, the only battery-powered Under Vehicle Inspection System, or UVIS as we the company likes to say, and offers “no strings attached” portability, touting no cables and no cords. Courtesy of Advanced Detection Technology and YouTube.)
-
*Advanced Detection Technology was also recognized in the 2020, 2019, 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Aeroturn, LLC
Best Pedestrian Entrance Control Solution
-
Contactless Biometric Turnstile Entry & Exit System
-
Aeroturn continues to lead the way in perimeter protection solutions even through a global pandemic.

-
Aeroturn along with security integrator partner, Siemens-Beltsville, developed the integration of a facial recognition system with French-based Idemia for a complete and customized biometric credential access control system for one of the largest financial lenders in the world, which required state of the art locking turnstiles coupled with a built-in Covid compliant credential system, to ensure health safety during these highly infectious times.
-
Aeroturn accommodated the biometric facial recognition turnstile deployment’s aggressive timeline set for completion and commissioning, as the staff had a set date to return to the buildings in the complex.
-
Over the last year Aeroturn has also catered to its government clients by developing a hybrid touchless system for military bases in the Atlantic, and Aeroturn’s team continues to educate the end-user and integrator about the importance of quality turnstiles with touchless solutions.

-
*Aeroturn LLC was also recognized in the 2020, 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
AlertMedia
Best Mass Notification Solution – Software
-
AlertMedia Emergency Communication Software
-
Every day, businesses face an increasing number of threats to their people and operations—from severe weather events and security incidents to global health crises.

-
Keeping employees safe during these critical events requires a modern and reliable emergency communication solution.
-
It’s why companies in more than 130 countries across a range of industries—from Fortune 500 companies to small and mid-size organizations—have turned to AlertMedia for help.
-
AlertMedia‘s emergency communication software is more than just a mass notification system. Their robust solution integrates with internal systems and connects an entire organization to allow them to communicate with precision, interact with their audience, and confirm a resolution.
(Every day, organizations face a wide array of threats. Learn how AlertMedia can help you quickly identify emerging threats and send fast, effective emergency communications to employees in harm’s way. Courtesy of AlertMedia and YouTube.)
- *AlertMedia was also recognized with Multiple ‘ASTORS’ Awards in 2020, 2019, 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Allied Universal (First of Three)
Best Machine Learning & Artificial Intelligence (Tie**)
-
HELIAUS
-
HELIAUS® is a sophisticated Artificial Intelligence (AI)-driven solution that goes beyond the outmoded “detect and respond” model of risk management.

-
More than just a tour or incident management system, HELIAUS® is a comprehensive workforce management solution that uses powerful algorithms to generate risk-adverse recommendations to keep your security professionals connected and engaged, situationally informed, and armed with the right recommendations to effectively create safer, more secure environments.
-
The bottom line is HELIAUS® can help reduce security and safety incidents by up to 20%, all while improving profitability and your bottom line.
(Learn about HELIAUS®, a revolutionary integrated solution beyond the archaic “detect and respond” model of risk management. It’s not just a tour or incident management system. HELIAUS® is a comprehensive workforce management solution with AI technology at its core. Courtesy of Allied Universal and YouTube.)
Allied Universal (Second of Three)
Best Airport/Aviation Security Solution
-
AUS – CMH
-
The John Glenn Columbus International Airport (CMH) is a medium hub facility, which proved challenging to implement mitigation measures having been built in the 1950s when certain security needs were never contemplated, and encompassing 2,265 acres of operational space; plus Rickenbacker International Airport (LCK) which covers 4,342 acres.

-
Allied Universal fulfills a unique opportunity at the John Glenn Columbus International Airport by continually analyzing Security Professionals routes and schedules not only to better interact with the facility and the public – but also to mitigate insider infiltration threats by using their HELIAUS® workforce management tool to identify risk patterns and behaviors that would otherwise not be visible.
-
By keeping their Security Professionals fluid, Allied Universal Officers can routinely roam the facility to conduct random security measures of employees, and with an average of 3,000 badged personnel, in 2020, conducted more than 50,000 checks.In partnership with Public Safety leadership at CMH, Allied Universal serves as the mobile eyes, ears, and badge readers.
Allied Universal (Third of Three)
Best Security Workforce Management Platform
-
HELIAUS
-
HELIAUS is Allied Universal’s AI-powered workforce management solution that streamlines security operations at client’s sites, generates intelligent recommendations to help mitigate risk, and provides real-time communication and insight into the hands of clients Security Leadership to better protect their people, brand, and assets.
(Inspired by the power of the sun and Helios, the sun god of Greek mythology, Allied Universal’s proprietary HELIAUS® platform is the smart technology of tomorrow that places insight into the hands of your Security Professionals to better protect your people, brand, and assets. Courtesy of Allied Universal and YouTube.)
-
Allied Universal Programs have been recognized with Multiple Awards in the 2020, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs.
AMAROK
Best Perimeter Protection Solution – Physical
-
FORTIFEYE featuring the Electric Guard Dog Fence
-
AMAROK, formerly Electric Guard Dog, introduced FORTIFEYE in 2020 to enhance their physical perimeter security deterrent offering.

-
FORTIFEYE integrates electric security fencing, video surveillance, and video monitoring to create an ultimate crime prevention solution for commercial businesses and industrial sites.
-
FORTIFEYE has multiple layers of integrated security to protect your business, starting with the Electric Guard Dog Fence which delivers 7,000 volts to would-be thieves.
-
Cameras capture and record every second of activity in real time, from initial approach to flight and finishes with remote video monitoring to validate the breach and dispatch authorities.
(AMAROK is the Ultimate Perimeter Security Solution. See how their full-perimeter solar electric fences paired with the company’s integrated security systems stop crime before it happens. Courtesy of AMAROK and YouTube.)

-
*AMAROK (formerly the Electric Guard Dog), is also a New Premier Sponsor in the 2021 ‘ASTORS’ Homeland Security Awards Program and was recognized in the 2020, and 2019 ‘ASTORS’ Homeland Security Awards Program.
American Signal Corporation (ASC)
Best Mass Notification Solution – Software
-
CompuLert NEXGen
-
American Signal Corporation’s CompuLert NEXGen is a premier control platform for mass notifications, allowing emergency managers to receive updates in real-time and quickly alert individuals who are in potentially hazardous situations.
-
CompuLert NEXGen’s robust technologies allows a variety of sensor inputs, detecting wind speed, water levels, chemical spills, lightning strikes and more. The system can then automatically notify residents through alerting devices, like ASC’s outdoor notification sirens as well as its ASC AWARE desktop alerts and ASC Sentinel mobile notification.

-
Furthermore, ASC’s CompuLert NEXGen seamlessly interfaces with National Weather Service Alerts and FEMA’s Integrated Public Alert Warning System, both of which can automatically activate alerts based on the threat or emergency. Emergency managers can customize their system to allow only relevant alerts and activate devices in designated areas to reach only those in immediate danger.
CompuLert NEXGen can been deployed for any application, including campuses, military installations, nuclear facilities, cities and counties, and more, and can be installed on a single PC, or on several servers to ensure availability during disasters.
(Understanding the changes and benefits of CompuLert™ NEXGen. Courtesy of John Coultas ASC and YouTube.)
-
*American Signal Corporation was also recognized in the 2020, 2019, 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Apricorn

Best Data Storage Security Solution
-
Aegis Padlock SSD
-
Even before the COVID-19 pandemic, remote and mobile working was on the rise however, as the global workforce shifted from office to home practically overnight due to COVID-19, it became abundantly clear that workers would use a variety of devices at their disposal outside of their corporate firewall.

-
To comply with corporate security policy and protect data in the remote workforce, Apricorn developed the portable Aegis Padlock SSD, a software-Free, 100% hardware-based 256-bit AES XTS encrypted, onboard keypad PIN authenticated, and ultra-fast USB 3.1 (3.0) data transfer speeds.
-
The Aegis Padlock SSD also thrives where software-authenticated encrypted devices can’t even function, such as embedded systems, machines without a keyboard, and equipment in possession of a powered USB port and storage file system.
-
All internal componentry is protected from physical tampering with a layer of hardened epoxy, and its firmware is locked down to prevent any modifications making it impervious to malware attacks such as BadUSB.
-
The Aegis Padlock SSD keeps your Sensitive Data Secure On the Go, Encrypting on The Fly.
(The remake of the ultra-compact, 256 bit AES XTS hardware-encrypted Padlock SSD USB 3.2, is still smaller than a deck of cards with its extruded aluminum enclosure, membrane style keypad, and FIPS 140-2 level 2 validation, and is nearly twice as fast as its predecessor, clocking in at up to 350 MB/s, and comes in five capacities from 240GB up to 4GB. And while the speeds and sizes have doubled and quadrupled, respectively, the cost of the Padlock SSD from then to now has come down to be about 1/3 of what they were back then. Courtesy of Apricorn and YouTube.)
-
*Apricorn was also recognized in the 2020, 2019, 2018 and 2016 ‘ASTORS’ Homeland Security Awards Programs.
AttackIQ
Best Breach & Attack Simulation
-
AttackIQ Security Optimization Platform
-
New to the ‘ASTORS’ Awards Program, the AttackIQ Security Optimization Platform enables risk and security practitioners to continuously assess and improve critical security controls within their production environment, optimizing their end-to-end security posture and providing trend reporting for demonstrable improvement over time.
-
By surfacing better, automated insights, teams are able to make smarter investment decisions and deliver on both business continuity and greater program effectiveness.
(Learn how AttackIQ’s Security Optimization Platform helps security teams achieve cybersecurity readiness through automated security control validation. Courtesy of AttackIQ and YouTube.)
Attivo Networks (First of Three)
Best Identity Detection & Response Solution
-
IDR Suite of Products
-
Attivo Networks®, a leader in identity detection and response, has expanded its portfolio to include cloud identity security.
Organizations provision human and non-human identities (applications, virtual machines, serverless functions, and such) on the network and in the cloud, which attackers target early in the attack cycle to progress their attacks.
-
By stealing these identities, they can impersonate authorized users, access resources, move laterally throughout the network and cloud environments, conduct reconnaissance, elevate privileges, identify targets, and compromise data.

-
While many tools intend to keep networks secure, Identity Detection and Response (IDR) gives organizations a critical new weapon in their arsenal to find and fix credential and entitlement weaknesses and detect live attacks on a real-time basis.
-
As modern cybercriminals attempt to exploit vulnerable credentials and entitlements to move through networks undetected, IDR solutions play a meaningful role in stopping them, whereas other tools simply cannot.
-
Attivo Networks IDR Suite of Products can seamlessly extend to the cloud and deliver detailed entitlement visibility for identities – including users, applications, containers, serverless functions, and other assets.
Attivo Networks (Second of Three)
Best Intrusion Detection & Prevention Solution
-
IDR Suite of Products
-
Attack surfaces have expanded dramatically with the shift toward remote work putting identity at the forefront of security, a major shift from traditional perimeter-based strategies.
-
Organizations must now defend identities across the entire enterprise with identity-based, least-privilege access programs and defenses capable of detecting attack escalation and lateral movement on-premises and in the cloud.

-
Attivo Networks has leveraged its deep experience in privilege escalation and lateral movement detection to become a significant player in the Identity Detection and Response space.
-
In the last year, the company has secured its leadership position based on its broad portfolio of capabilities that focus on unprecedented visibility to exposures and misconfigurations of identities and entitlements and early detection of credential theft, misuse, and privileged escalation activities.
(The Attivo ThreatDefend® Platform delivers unparalleled attack prevention, detection, and adversary intelligence collection based on cyber deception and data concealment technologies for an informed defense. The platform efficiently derails attacker discovery, lateral movement, privilege escalation, and collection activities early in the attack cycle across endpoints, Active Directory, and network devices on-premises, in clouds, and on specialized attack surfaces. Courtesy of Attivo Networks and YouTube.)
Attivo Networks (Third of Three)
Best Cloud Security Solution
-
IDEntitleX
-
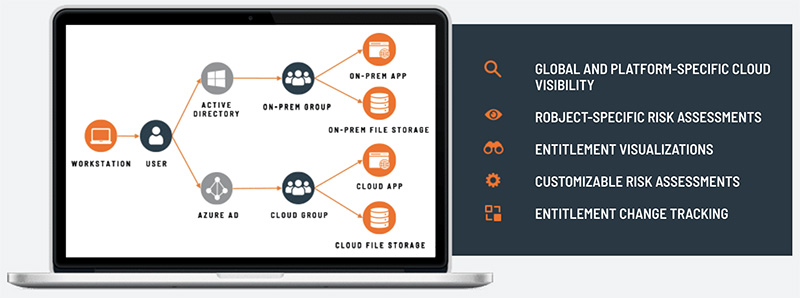
IDEntitleX is Attivo Networks’ Cloud Infrastructure Entitlement (CIEM) solution, which provides unprecedented visibility for cloud permissions management.
-
Customers gain actionable visibility to cloud identity risks and entitlement exposures so they can address risky entitlements and drift from security policies.
-
This solution makes it easy to identify and reduce risk by providing intuitive and interactive graphical visualizations for cloud identities, roles/permissions, and resources.
-
Defenders now gain the visibility needed to see misconfigurations and excess permissions attackers can leverage to create attack paths and persistence within the cloud environment.

*Attivo Networks is also a Returning Premier Sponsor of the Annual ‘ASTORS’ Homeland Security Awards Program for the Fourth Year, and a Multi-Platinum Award Winner in the 2020, 2019, 2018 and 2017 ‘ASTORS’ Awards Programs.
Automatic Systems America
Best Pedestrian Entrance Control Solution
-
SlimLane Optical Barrier Turnstile
-
Automatic Systems America continues to evolve its award-winning SlimLane swing optical barrier turnstiles to offer customized solutions able to meet customer requirements for even the most unique installations.
-
The variety of speedgate cabinets range from the sleek standard unit and evolve to the SlimLane EP model or the rounder SlimLane EPR.
-
Larger biometric peripherals such as facial recognition and frictionless fingerprinting offer a contactless alternative to proximity readers and can easily be integrated within the SlimLane EPW or NK cabinets.
(Automatic Systems’ Slimlane EPW speed gates offer extended integration capabilities, allowing us to offer contactless identification solutions, with best-in-class #biometric readers such as the MorphoWave Compact device from IDEMIA. Courtesy of Automatic Systems and YouTube.)
-
With the current social distancing and contactless requirements, the SlimLane EPR. while protecting its users.
-
The hand “wave” and facial recognition readers were easily integrated and offer a fully contactless solution while the UL 2593 Certified SlimLane offers a highly reliable (10 Million MCBF) physical access control turnstile.
-
With its 5-year standard warranty and infinite customizations, the SlimLane continues to be a perfect solution for lobby entrances.
-
Selected as the “standard” for multiple financial institutions, we are confident that the SlimLane will continue to answer any pedestrian access control requirements for your years to come.
(Automatic Systems SlimLane EPW Touchless swing glass turnstiles offer custom integration provides an innovative and effective solution with multiple biometric authentications during continuous movement. Courtesy of Automatic Systems and YouTube.)
*Automatic Systems is also a Returning Premier Sponsor for the Fifth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a Platinum-Award Winner in their Sixth Annual ‘ASTORS’ Awards Program.
Axis Communications (First of Three)
Best Body Worn Video Solution
-
AXIS W100 Body Worn Camera
-
The AXIS W100 Body Worn Camera produces sharp images and clear audio, thanks to dual microphones with noise suppression, is lightweight, robust, and water-resistant, starting and stopping quickly with a single touch, buffers up to 90 seconds before it’s switched on so users can catch entire encounters, and features a silent mode for discrete recording.

-
The AXIS W100 Body Worn Camera features Axis Zipstream technology so users can store as much footage as needed without compromising video quality – onsite or in the cloud, lives up to official FBI standards for cybersecurity with end-to-end encryption, and it’s easy to add as many cameras as needed at any time with open standards and cost-efficient docking stations.
-
The AXIS W100 Body Worn Camera comes with an easy-to-use mobile app – the AXIS Body Worn Assistant – for viewing and labeling in the field, making it easier to find and retrieve evidence, and enables users to start reporting out in the field by categorizing a recording and attaching notes to it.
-
The AXIS W100 Body Worn Camera offers a reliable option for law enforcement and security personnel in wearable surveillance, leveraging the quality & innovation of Axis to extend existing security systems.
(AXIS W100 Body Worn Camera is an easy-to-use, lightweight and robust body-worn camera that lets you store and manage video your way. It plugs right into your own Axis system or another system of your choice. Courtesy of Axis Communications and YouTube.)
Axis Communications (Second of Three)
Best Video Analytics Solution
-
AXIS Q1615-LE Mk III Network Camera
-
The Axis Zipstream technology Network Camera is a top-of-the-line outdoor-ready camera that is ideal for city surveillance, transportation, and industrial applications.
-
With 120 fps in HDTV 1080p, the network camera offers exceptional video quality while capturing clear, detailed images of fast-moving objects and/or people regardless of challenging light conditions.

-
The camera is ideal for installation on the side of roadways or in poorly lit industrial lots and is equipped with Axis Lightfinder 2.0 and Axis Forensic WDR, which produces high-quality images with excellent color, detail, and sharpness.
-
AXIS Q1615-LE Mk III is equipped with advanced security functionality to safeguard the system and prevent unauthorized access.
-
With deep learning on the edge, the AXIS Q1615-LE Mk III platform is designed for third-party applications and allows analytics to run directly on AXIS Q1516-LE Mk III (on the edge), allowing for a faster, more scalable system.
-
With this ability to process powerful analytics, the camera is capable of edge-based automatic incident detection, counting, and anomaly detection, among other functions.
Axis Communications (Third of Three)
 Best IP Video Surveillance Solution
Best IP Video Surveillance Solution
-
AXIS Q6135-LE PTZ Network Camera
-
The AXIS Q6135-LE is a high-speed PTZ camera that offers OptimizedIR up to 250 m (820 ft) as well as Lightfinder 2.0 for clear, sharp overviews and excellent details in demanding light conditions.
It’s ideal for city surveillance in any unlit or low-light area – such as parks and alleys– eliminating the need for additional lighting.
(The AXIS Q6135-LE is a high-speed PTZ camera that offers OptimizedIR up to 250 m (820 ft) as well as Lightfinder 2.0 for clear, sharp overviews and excellent details in demanding light conditions. And, AXIS Object Analytics lets you detect and classify humans and vehicles. Courtesy of Axis Communications and YouTube.)
-
*Axis Communications, a Canon Company has been recognized in the 2020, 2019, 2018, and 2017 ‘ASTORS’ Awards Programs respectively.
BeyondTrust
Best Privileged Access Security Solution
-
Universal Privilege Management Solutions
-
According to the White House, strengthening the cybersecurity of federal networks, systems, and data is one of the most important challenges the United States faces as a nation.

-
Controlling, monitoring, and auditing privileged access is extremely important to accomplish this mission by mitigating the risks posed by insider threats, preventing data breaches, and meeting compliance requirements.
-
With BeyondTrust agencies can keep pace, cost-effectively reduce IT security risk, confidently embrace innovation, and simplify the path to meet federal compliance mandates.
-
BeyondTrust’s Universal Privilege Management approach consists of three privilege pillars: Privileged Password Management, Endpoint Privilege Management, and Secure Remote Access.
(See a brief overview of BeyondTrust Universal Privilege Management Solutions. Courtesy of BeyondTrust and YouTube.)
-
*BeyondTrust was also recognized in the 2020, 2019, 2018 and 2016 ‘ASTORS’ Awards Programs.
BriefCam
Best Video Analytics Solution (Tie**)
-
BriefCam Video Analytics for Multi-Site Architectures
-
When it comes to deploying video surveillance systems, businesses with multiple sites or branches face several challenges.

-
From major retail chains to banks, utilities, transit agencies, among others, these organizations need the ability to record video locally on-site, but also seek to gain valuable insights through advanced video analytics across sites.
-
BriefCam’s innovative multi-site deployment architecture supports businesses with multiple locations or branches, enabling them to analyze cross-site surveillance video and realize the value of their video content.
-
Organizations can receive real-time alert notifications from across all locations, as well as visualize business intelligence from multiple sites into centralized dashboards, all while significantly reducing video processing bandwidth requirements.
(BriefCam introduces the new deployment option of a multi-site architecture. This enables businesses with multiple, distributed locations to view aggregate data from all remote sites to uncover trends across locations, optimize operations and boost real-time alerting and response – all while continuing to reap the benefits of BriefCam’s powerful analytics platform for making video searchable, actionable and quantifiable. Courtesy of BriefCam and YouTube.)
-
*BriefCam was also recognized in the 2020, 2019 and 2018 ‘ASTORS’ Awards Programs.
Canon U.S.A. (First of Two)
Best Email Security Solution
-
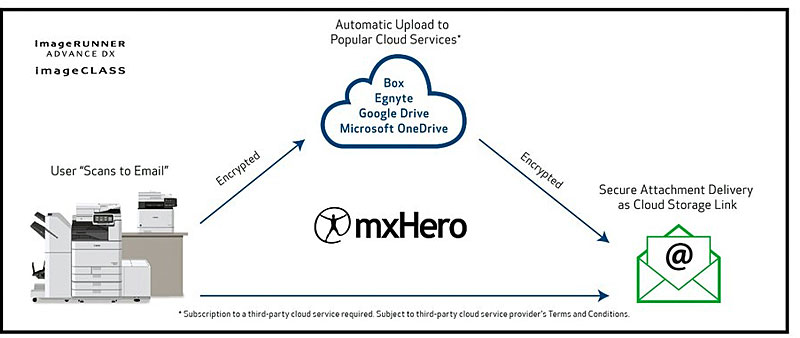
mxHero + Canon MFP
-
A cloud service for intelligent email management, mxHero™, can integrate onto a Canon multifunction printer (MFP) to help customers safely collaborate, govern, manage and share information.
-
By leveraging powerful storage platforms like Box (purchased separately), it can help create a cost-effective solution superior to single-purpose, document/email management products by replacing inbound and outbound email attachments with secure file links.
-
This solution is made to be compatible with most devices, helps to minimize end user effort, provides security measures to help control access to attachments (even when outside of the company) and can help screen malicious content.
-
Especially in today’s environment where solutions designed to help team’s collaborate while working in multiple places is important, services such as mxHero™ can help companies implement security features, govern and manage attachments while people aren’t able to physically connect face-to-face.
Canon U.S.A. (Second of Two)
Best IT Access Control & Authentication System
-
mxHero + Canon MFP
-
The latest edition of the imageRUNNER ADVANCE platform, the imageRUNNER ADVANCE DX series with uniFLOW Online, is designed to help prepare its customers for the future of work through its simple, flexible design, advanced scanning, strong security, enhanced cloud features and user-friendly enhancements, like soft number keys similar to a smartphone or tablet.
-
The uniFLOW/uniFLOW Online platform is an end-to-end device management solution that can help improve the control and efficiency of imageRUNNER ADVANCE and other compatible multifunction print solutions through its security features.

-
The platform provides business employees the ability to control and monitor access to sensitive information with its enhanced authentication and user tracking features.
-
To help limit unauthorized use of devices and keep valuable and confident information safe, uniFLOW requires users to identify themselves at the solution, and its Secure Print functionality allows users to send sensitive documents to compatible network printers from desktops and compatible mobile devices.
-
When using this function, regardless of how users submit a print job, documents only print when the user is physically standing at the device and authenticates.
-
Through uniFLOW Online’s ability to store print jobs and release them only when users are in front of the supported Canon print device, solutions such as this help to limit document contamination, which is especially important in our current environment where mitigating contact between individuals is vital.
(Having the needs of the end-user in mind, we started to create a brand-new device user interface (UI) for uniFLOW Online. With a modern look and feel, uniFLOW Online focuses primarily on the login process on Canon imageRUNNER ADVANCE DX devices. It introduces the possibility of adapting the UI to suit customers’ own corporate identity. Subsequent development will expand the optimized user experience to secure printing and scanning functionalities. Courtesy of uniFLOW and YouTube.)
-
*Canon U.S.A. was also recognized with Multi-Award Wins in the 2020, 2019, 2018 and 2017 ‘ASTORS’ Awards Programs.
-
Additionally, Axis Communications, a Canon Company has been recognized in the 2020, 2019, 2018 and 2017 ‘ASTORS’ Awards Programs respectively.
Cellbusters
 Best Cell Phone Detection Solution (Tie**)
Best Cell Phone Detection Solution (Tie**)
-
Zone Protector
-
The Zone Protector™ from Cellbusters provides maximum protection for your environment by continuously scanning for cell phone and user-selectable RF transmissions, and is far more sophisticated than a cell phone detector.
-
Comparable to a spectrum analyzer, the Zone Protector™ has the ability to scan user-definable frequency ranges along with the ability to alert, notify, control a third party device, or simply log as soon as it detects relevant transmission activity.

-
Precise frequency filtering technology, managed and controlled by a 32-bit microprocessor, enables the Zone Protector™ to deliver accurate detection with virtually zero false positives.
-
Once cellular or appropriate RF activity is detected, the Zone Protector™ can be set to activate a choice of alerting options or to silently log all detected activity.
-
Additionally, Cellbusters Zone Protector has now been updated to detect 5G phones, proving a leading edge in the market, and protects investment in this technology for years to come.
(See a quick overview of the Zone Protector and the Zone Manger, both cell phone detection technology from Cellbusters. Courtesy of Cellbusters and YouTube.)
-
*Cellbusters was also recognized in all Six ‘ASTORS’ Awards Programs, respectively.
Certified Multi-Media Solutions
 Best Railroad/Mass Transit Security Solution
Best Railroad/Mass Transit Security Solution
-
TiniFiber
-
Certified Multi-Media Solutions Ltd, is being recognized for a complex installation of hybrid TiniFiber cable consisting of a 12-conductor power cable and a 12 strand Micro Armored Fiber Optic Cable under one jacket for the NYC Transit System to accommodate its CCTV camera system which is located below ground.

-
The project required a specific design and installation which would be minimally intrusive and incorporate both power and fiber under a single jacket due to space utilization and rodent protection.
-
Certified Multi-Media Solutions worked with the NYC, MTA’s design team to design and install this complex solution for the NYC, MTA.
CIS Mobile
Best Handheld Mobile Tech Solution
-
altOS
-
Smartphones are highly effective productivity tools, unfortunately, consumer mobile phones create an electronic trail that can put government employees at risk because they are built around collecting data to monetize the user.

-
Eliminating or minimizing these data trails is fundamentally at odds with the business models of the consumer-centric mobile eco-system which depends on data collection from mobile devices to sell targeted advertising, and OEM smartphones put government data at risk.
-
Additionally, it’s difficult to fully control the electronic trail left by consumer mobile phones, further exposing the presence and identity of individuals working in sensitive government, military, and intelligence roles.
-
In response, CIS Mobile developed altOS which was built exclusively for secure government use, using Android as a base but adding policy controls, secure containers, and management features into the platform.
-
In essence, it puts a new OS on the existing device to overcome the security challenges mentioned here to deliver the productivity of smartphones without the accompanying risk.
(Even approved government-certified devices leak user location, application use, and metadata back to 3rd party collectors however, altOS is different. It was built exclusively for secure government use, using Android as a base but adding policy controls, secure containers, and management features into the platform. Courtesy of CIS Mobile and YouTube.)
Cloudastructure
 Best Video Analytics Solution
Best Video Analytics Solution
-
Cloudastructure Video Surveillance Solution
-
Cloudastructure is a cloud-based surveillance platform integrated with powerful analytics, that uses machine learning (ML) computer vision to recognize objects, faces and more, to allow users to rapidly search video footage much like one does on the web through the company’s sophisticated object tagging capabilities.
-
The Cloudastructure cloud-based platform also offers an alternative to on-premises solutions, which can be costly to operate and scale and require on-site monitoring.
-
Cloudastructure, clients can securely store their recorded and live video feeds in the cloud through a browser, so they can safely store, index, access, monitor and review their surveillance footage in the cloud, 24/7 from any internet-enabled device.
(Cloud-based video surveillance keeps the enterprise safe and secure. Securely store, index and access footage in the cloud, so users always know what is happening, 24/7 from any internet enable device. Courtesy of Cloudastructure and Vimeo.)
CornellCookson (First of Two)
Best Vehicle Security Entrance Control
-
Extreme MicroCoil Grille
-
When you need security in an opening with limited vertical space, the Extreme High Performance MicroCoil® Grille – 500K Cycles is the answer.

-
Perfectly engineered to occupy the smallest amount of headroom on the market, this high-performance compact grille not only coils in nearly 50% less room than other security grilles but also provides higher performance, and engineered to handle at least 500,000 cycles (opens/closes) at speeds of up to 24” per second.
-
But, with the MicroCoil Grille, higher speeds do not mean you get a loud and clunky security grille, this low headroom parking security grille’s patented nested link system actually minimizes noise and vibrations – making it one of the quietest and smoothest coiling parking garage gates available today.
(See the Extreme High-Performance MicroCoil Grille – 500 Cycle in Action. Courtesy of CornellCookson and YouTube.)
CornellCookson (Second of Two)
Best Perimeter Protection Solution – Physical
-
StoreDefender Door
-
Created to provide immediate security to store and building owners during times of unrest or unoccupied hours, the StoreDefender is not only a better choice for instant protection, but it can also be more cost-effective than other means of protection (such as plywood board-ups).

-
The StoreDefender™ Door was engineered to be a reliable solution to prevent theft and property damage, protecting against riot events and mob attacks.
-
More rigid and robust compared to traditional security doors, StoreDefender was created to be lift and impact-resistant and has been tested to withstand more than 4,500 pounds of effort to lift 3” and resists more than 2,500 pounds of pull force without exiting the guides.
-
Designed to safeguard property, merchandise, and most importantly, lives, the door ensures pharmaceutical facilities, cannabis dispensaries, high-end retail, and big-box chain stores can fortify perimeters against looting events and burglaries.

-
*CornellCookson, was also recognized in 2019 ‘ASTORS’ Awards Program.
CyberArk
Best Identification Management Solution
-
CyberArk Identity Security Platform
-
The CyberArk Identity Security Platform is an end-to-end identity access management solution that enforces privilege, enables access, and secures DevOps.
-
The CyberArk Identity Security platform is centered on privileged access management and offers the most complete and flexible set of least privilege-based identity and access capabilities, and is used to protect agencies across all three branches of the U.S. federal government – including multiple Department of Defense deployments

-
The CyberArk Identity Security platform is centered on privileged access management and offers the most complete and flexible set of least privilege-based identity and access capabilities, and is used to protect agencies across all three branches of the U.S. federal government – including multiple DoD deployments.
-
CyberArk delivers a comprehensive privileged access management solution designed to eliminate advanced cyber threats by identifying existing privileged accounts across networks, then proactively managing, monitoring, and protecting those accounts to reduce risk and improve security and compliance.
-
CyberArk continuously scans and monitors environments to discover and manage privileged credentials, isolates those credentials so they are never exposed to an end-user, isolates privileged sessions to safeguard critical systems, and automatically records and stores those sessions to enhance audit capabilities.
(In today’s hybrid and multi-cloud world, where every identity represents a potential attack path to an organization’s most valuable assets, traditional network barriers are not enough to secure the perimeter. That’s the importance of a robust Identity Security strategy. See how your organization can embrace a Zero Trust approach to protecting an ever-expanding number and diversity of identities. Courtesy of CyberArk and YouTube.)
- *CyberArk was also recognized in the 2020, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs.
Cyberpion (First of Two)
Best External Attack Surface Management
-
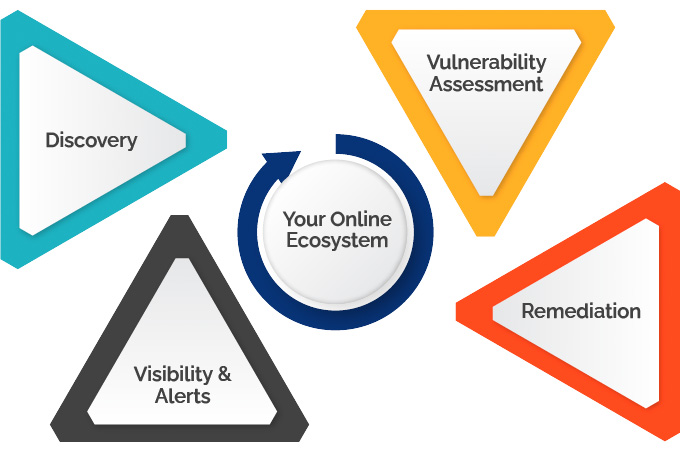
Every asset your customers and employees access when interacting with your company online makes up your online ecosystem.
-
These assets may be owned by your organization, owned and operated by a third-party vendor, or exist somewhere in your long chain of Nth-degree vendors, and this ecosystem represents an organization’s external attack surface.
-
Cyberpion’s leading Ecosystem Security platform continuously discovers, assesses, and alerts on vulnerabilities within your third-party, internet-facing assets, to provide security teams the opportunity to identify critical vulnerabilities within their online supply chains, infrastructure, and elsewhere, and remediate them before malicious actors exploit and abuse them.
-
Cyberpion’s continuous process of discovery, assessment, reporting, and protection across your entire ecosystem gives the necessary awareness for security teams to effectively protect the enterprise.
Cyberpion (Second of Two)
Best Cyber Security Risk Management Solution
-
Cyberpion Ecosystem Security
-
What Do You Really Know About the Security Posture of Your Digital Ecosystem?
-
-
What about the security posture of your third-party vendors?
Cyberpion’s continuous process of discovery, assessment, reporting and protection across your entire ecosystem gives the necessary awareness for security teams to effectively protect the enterprise.
-
See the risks you’re exposed to with a Complimentary Cyberpion Online Ecosystem vulnerability assessment scan to help you assess and evaluate the vulnerabilities that threaten your cybersecurity, and gain a more accurate picture of your threat posture to reduce false positives.
-
Cyberpion assesses all of your organization’s owned (known and unknown) public-facing assets and their connected supply chain, to ensure that your security team takes action on accurate and reliable information.
Cyemptive Technologies (First of Two)
Best Anti-Malware Solution
-
Zero Trust Access Solutions
-
Cyemptive Zero Trust Access (CZTA) enables an unprecedented additional protection layer and provides a revolutionary approach for VPNs (Virtual Private Networks).

-
Cyemptive was the first to detect VPN networks being compromised and quickly informed the DHS of the issues, and have discovered more than 10 security holes in existing VPN technologies that are not getting detected by current leading technology perimeter defense firewalls.
-
CZTA is an optional add-on module to Cyemptive Perimeter Fortress technology solution leading a revolutionary defense for VPNs and your remote workforce.
-
This Cyemptive protection tool is prepared for, and can prevent, quantum computing-based attacks from penetrating VPNs.
Cyemptive Technologies (Second of Two)
Best Cyber End-to-End Encryption Solution
-
Cyemptive Perimeter Fortress
-
The experience of having your firewall compromised and fooled in real-time is a common problem that often goes unnoticed.
-
If you are not seeing thousands of attacks per day defended in your current firewall, then there is a high chance you are not seeing or detecting the ones getting through.

-
Cyemptive’s Perimeter Fortress (CPF) defense technology successfully stops many of today’s most advanced global hackers in seconds.
-
CPF handles root-level attacks and base firmware attacks with ease using their patented cyberslice technology, and found over 300 zero days in 2019 alone.
-
The company’s integrated protection platform prevents the most elite hackers from compromising your perimeter defenses.
Cymulate
Best Breach & Attack Simulation
-
Continuous Security Validation Platform
-
Cymulate SaaS-Based Continuous Security Validation enables companies to challenge, assess, and test their security control simply and continuously even from their home.
-
Plug & Play. 7 Minutes to Deploy. Assure daily the operational effectiveness of your security stack that protect your IT environment, cloud initiatives, and critical data against threat evolutions.
-
Schedule a private demo today to see the benefits for your organization.
(See how you can operationalize threat intelligence and the MITRE ATT&CK framework for continuous purple teaming, to continuously challenge, assess, and optimize your security controls across the full cyber kill chain. Automated, comprehensive & prescriptive. Courtesy of Cymulate and YouTube.)
- *Cymulate was also recognized in the 2019 ‘ASTORS’ Homeland Security Awards Program.
D-Fend Solutions
Best Persistent Aerial Monitoring Solution
-
EnforceAir
-
National and homeland security personnel face a wide variety of scenarios and drone threats, so the EnforceAir anti-drone product, features counter-drone, cyber, radio frequency (RF)-based takeover technology to provide users with operational agility and flexibility.
-
EnforceAir, in either autonomous or manual mode, detects, locates, and identifies rogue drones in your airspace and then neutralizes the threat by allowing you to take full control over the drone and land it safely in a predefined zone.
-
Since the system does not rely upon jammers or kinetic technology, EnforceAir avoids collateral damage, interference, disruption, and disturbance, and continuity prevails as communications, commerce, transportation, and everyday life smoothly proceed.
-
EnforceAir is lightweight and its core elements can be easily transferred, mounted, and configured within minutes, enabling personnel to go anywhere at any time, including vehicle, stationary and tactical installations.
(D-Fend Solutions focuses on the real threats from potentially dangerous drones so that varied organizations around the world can maintain full control of drone incidents in complex environments and be prepared for future threats. The EnforceAir anti-drone system, automatically executes radio frequency, cyber takeovers of rogue drones for safe landings and safe outcomes. Courtesy of D-Fend Solutions and YouTube.)
Data Theorem (First of Two)
Best Vulnerability Management Solution
-
API Secure
-
The rapid growth of modern applications has led to a dramatic increase in the number of APIs developers are creating.
-
Cloud platforms such as Amazon Web Services, Microsoft Azure and Google Cloud Platform have introduced serverless services allowing developers to build applications at scale with less infrastructure complexity and lower costs.
-
However, as the adoption of these new cloud serverless services grows, it allows for the creation of rogue APIs called shadow APIs that operate outside of enterprise security.
(See how Data Theorem approaches API security. Identify your entire attack surface by discovering all APIs, hacking beyond the perimeter, and maintaining a superior security posture. We empower our customers with proactive ways to hack their APIs before attackers do. Courtesy of Data Theorem and YouTube.)
Data Theorem (Second of Two)
Best Breach & Attack Simulation
-
Cloud Secure
-
For cloud security, application & infrastructure teams need to address issues simultaneously using a full-stack approach, from cloud infrastructure to cloud applications.
-
Data Theorem’s Cloud Security product is CSPM + AppSec all-in-one to monitor users Cloud configs (CSPM), applications, microservices, serverless functions, key stores/keyvaults, Virtual Machines, Storage assets, Databases, etc.

-
Cloud Secure also ‘Hacks the Cloud’ on a daily basis in search of security vulnerabilities that can lead to data breaches, and ‘Protect the Cloud’ by preventing data breaches sourced from Cloud assets and configs.
-
Data Theorem’s Cloud analyzer continuously discovers vulnerabilities in multi-cloud environments and provides mitigation solutions in real-time.
-
As companies expand their global and cloud footprints, security teams are seeking new solutions to discover, inspect, and remediate their greatest internet-facing risks. This helps lock in stronger visibility across all modern apps and APIs, preventing data breaches.
-
Attack Surface Management extends beyond manual pen testing to provide a view into dangerous misconfigurations and process failures that can allow attackers easy access into cloud or web apps, or allow access to valuable data.
(Data Theorem delivers automated security for DevOps, ushering in a new era of DevSecOps, to help teams grow faster with fewer application security exposures. Courtesy of Data Theorem and YouTube.)
- *Data Theorem was also recognized in the 2020 ‘ASTORS’ Homeland Security Awards Program.
Databuoy Corporation
Best Gunshot Detection Solution
-
Shotpoint
-
Shotpoint is a highly-accurate gunshot detection and localization sensor network system first developed under research sponsored by DARPA, and is installed and protecting some of our most vulnerable citizens here in the United States.
-
Applicable for both indoor and outdoor environments, Shotpoint’s patented sensor mesh approach does more than just reliably detect shots, they fuse data from multiple sensors to localize on the source of gunfire in 3D.
-
Shotpoint works for all types of small arms, from handguns to rifles, and their patented fusion technique successfully eliminates all false alarms – and does not report echoes as shots.
(As gun violence continues with 2021 on pace to be the worst year in decades, Databuoy offers the Shotpoint® gunshot localization technology and Geofob™ mobile panic button to provide affordable, reliable, and field-proven technology with the highest performance standards in the industry. Courtesy of Databuoy and YouTube.)
Dedrone
-
Best Airport/Aviation Security Solution (Tie**)
-
Dedrone
-
DedroneTracker counter-drone software, which can be hosted in the cloud or on-premise, uses the DedroneDNA database to recognize and classify RF, WiFi, and non-WiFi drones, plus triggers alerts and countermeasures.

-
DedroneTracker seamlessly integrates with a variety of 3rd-party sensing and threat mitigation technologies, enabling users to customize their platform and meet their specific needs and threat level.
-
A major metropolitan city in Southern Europe recently deployed less than a dozen DedroneSensors to detect, track and locate drones and their pilots across the city center.
-
The protected area includes internationally renowned tourist destinations, corporate and shopping districts, residential areas, and a port encompassing 50 square kilometers.
-
With Dedrone, organizations of all sizes can select and combine best-in-class sensors to personalize their airspace security solutions to protect their vulnerable airspace and effectively address their specific threat profile.
(See why Dedrone is a market leader in airspace security, protecting people, property and information against unauthorized and malicious drones. Courtesy of Dedrone and YouTube.)
- *Dedrone was also recognized in the 2019 ‘ASTORS’ Homeland Security Awards Program.
Durabook Americas (First of Two)
Best Handheld Mobile Tech Solution
-
Managing and securing sensitive data is critical to Homeland Security Professionals, so to meet their data management requirements the Durabook U11 features an SSD that’s quick and easy to remove – without having to open any covers – saving you time and effort.
-
Both Hardware and software-based encryption options are available based on each customer’s unique requirements.

In the field, portability equals productivity. The S14I weighs only 5.07 lbs and is 33% slimmer than the previous generation.
-
Durabook U11 is compact yet delivers reliability, power and functionality needed in today’s challenging environments. Equipped with its high-capacity battery, you can take advantage of non-stop operation for up to 24 hours with a single battery, making the U11 the market leader in power supply.
-
In addition, its hot-swappable battery enables Homeland Security professionals in the field to operate without interruption when charging isn’t possible.
-
In addition, this tablet is MIL-STD-810G certified, ANSI 12.12.01 C1D2 certified, and IP65 rated, assuring shock, 6-foot drop, and vibration protection, as well as the ability to withstand use in a wide range of temperatures.
-
What’s more, the unique, fanless design with 0 dBA means the U11 operates dependably and quietly.
U11 can easily be expanded to add functionality or another layer of security via an RFID reader, ExpressCard54, or PCMCIA Type II.
-
In addition, the U11 comes optionally with an embedded smart card reader. It is the only rugged tablet available today with the option of adding a second smart card reader via a built-in expansion module, which is useful for Homeland Security professionals who operate in the field or those collecting and transferring sensitive data and information.
(The U11 fully rugged tablet delivers superb performance with Intel® 10th Generation CPUs and features a unique fanless design, the U11 provides the perfect blend of functionality, performance, and reliability. Plus, the high-speed data transmission capability of Intel® Dual Band Wireless AC 9260 and Bluetooth® V5.0 means smooth, congestion-free data processing at all times. For field operatives everywhere, the next generation of rugged mobile solutions has arrived. Courtesy of Durabook Federal and YouTube.)
Durabook Americas (Second of Two)
Best Data Storage Security Solution
-
S14I Laptop Rugged Laptop
-
For Homeland Security applications the Durabook S14I rugged laptop is widely used as an edge device in the frontend for data collection/data processing, source data visualization, Machine to Machine Communication, etc. (Edge Computing).
-
The S14I is engineered to combine military-grade durability, mobile functionality, computing performance, and long battery life for non-stop use, making it suitable for use in locations where rain or dust may be a regular occurrence.

-
For professionals who rely on drones for intelligence, the Durabook S14I has the data processing and storage power to analyze and map data from multiple drones from right from the Edge-decentralized data processing in close proximity to the devices themselves.
-
Additionally, the Durabook S14I can combine other in-field data, for example, from IoT and external sources, such as weather information, to help plan new aerial flight paths or arrange an instant repair.
-
The Durabook S14I is equipped with a smart card reader, fingerprint scanner, and hardware-based encryption (Trusted Platform Module (TPM 2.0)) to ensure storage security for sensitive data.
-
S14I is equipped with the latest NVMe PCIe SSD technology providing up to 1TB of storage, and can accommodate two additional internal SATA III SSD drives to maximize the onboard data storage.
-
The S14I’s media bay offers the user several setup options; instead of an optical disk drive, a third SATA III SSD storage can be mounted in the compartment, adding additional security using onboard RAID 0 & RAID 1 feature.
(The all-new Durabook S14I features the latest 11th Generation Intel® CPUs and class-leading 4’ drop spec/IP53 rating, pushing semi-rugged devices to a whole new level. The S14I is engineered to combine military-grade durability, field-worker functionality, computing performance, and long battery life for non-stop use, making it suitable for use in locations where rain or dust may be a regular occurrence. Courtesy of Durabook Federal and YouTube.)
- *Durabook (formerly GammaTech Computer Corporation), was also recognized in the 2017 ‘ASTORS’ Homeland Security Awards Program.
NEXT View Part 2 Winners E – Na View Part 3 Winners NE – Si
View Part 4 Winners SI – Govt View Part 5 Winners Excellence

















